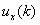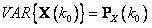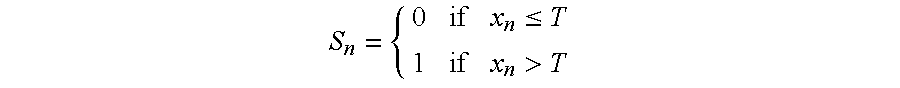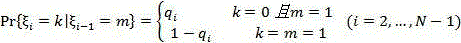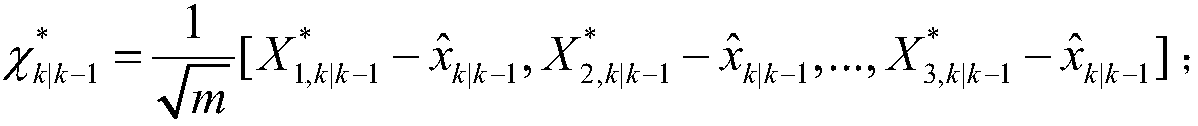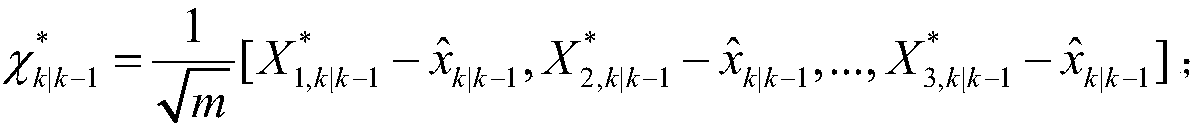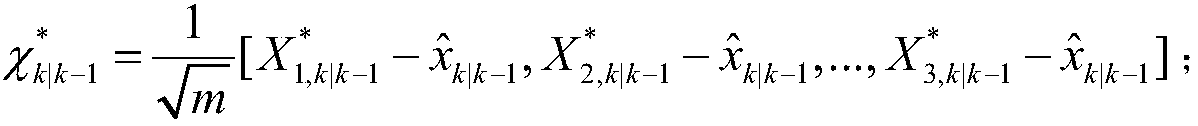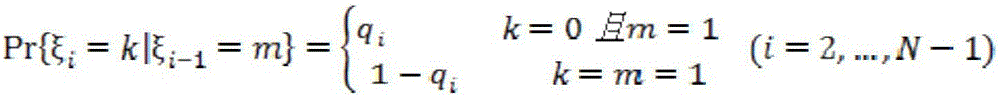Patents
Literature
49 results about "Markov transition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Markov chain is a mathematical system that experiences transitions from one state to another according to certain probabilistic rules. The defining characteristic of a Markov chain is that no matter how the process arrived at its present state, the possible future states are fixed.
Method and system for statistical filters and design of statistical filters
InactiveUS7184938B1Less dataLess signalDigital variable displayNoise figure or signal-to-noise ratio measurementFrequency spectrumFilter system
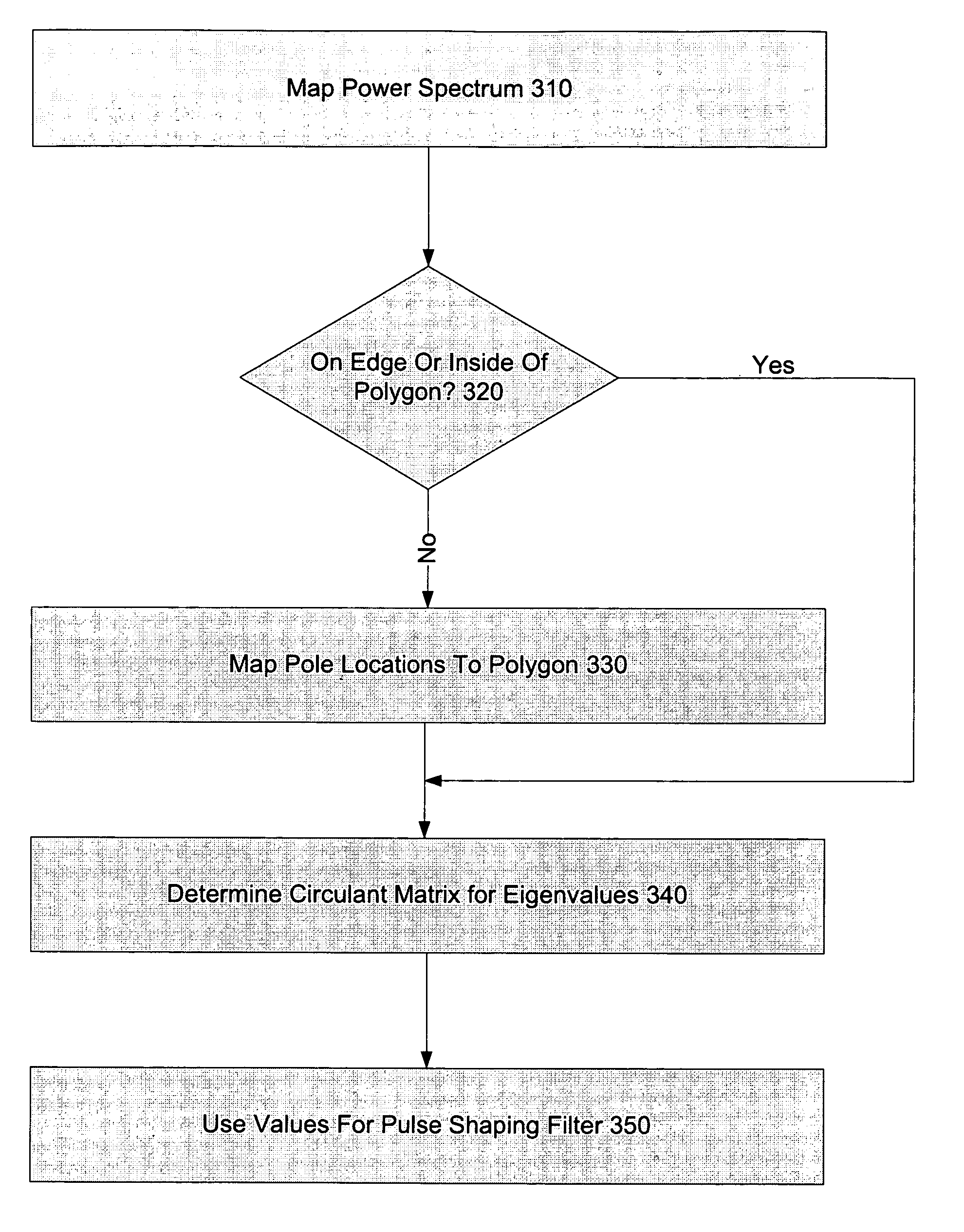
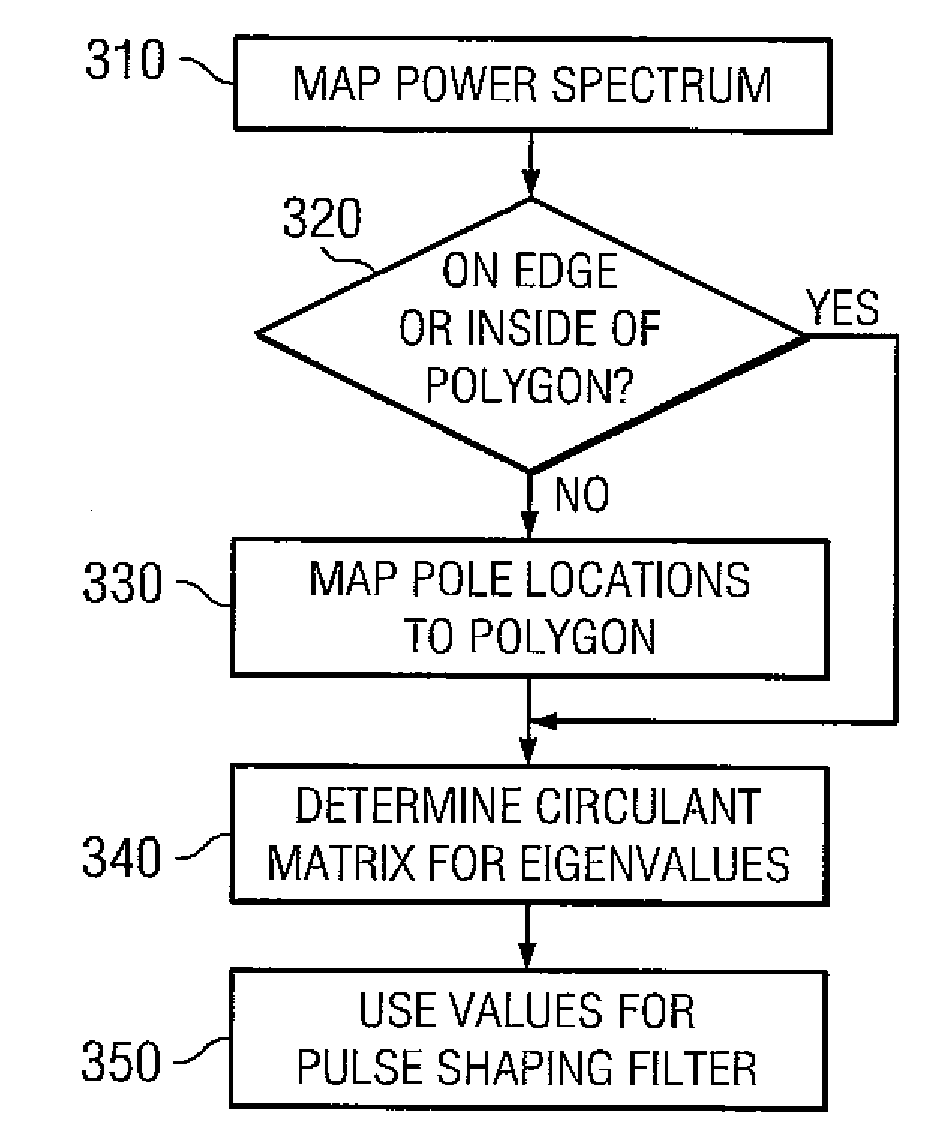
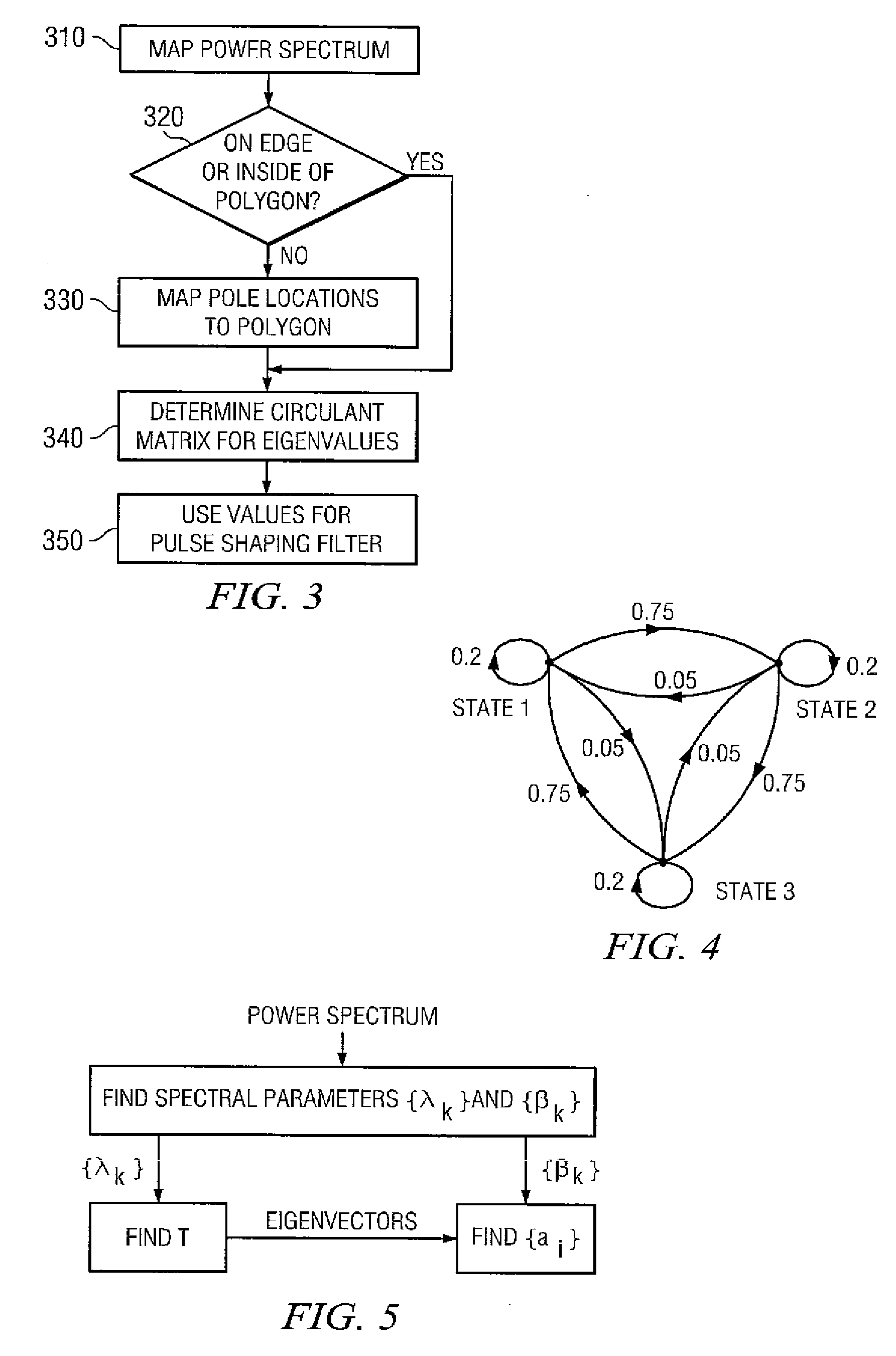
Systems and methods for the design or implementation of statistical filters for use in the spectral shaping of transmissions are disclosed. A desired power spectrum may be mapped to find pole locations that approximate the desired spectrum. These pole locations may then be mapped to the edge or inside of an equilateral polygon lying inside a unit circle, the equilateral polygon having the same number of sides as the order of the statistical filter desired and one vertex mapped to unity, to yield a set of eigenvalues. These eigenvalues may be the eigenvalues of a stochastic matrix the elements of which may be the Markov transition probabilities for use in a statistical filter designed to achieve the desired power spectrum. Use of a statistical filter employing these Markov transition values may be utilized to shape UWB or other signals to achieve the desired power spectrum.
Owner:ALEREON
Tracking algorithm for high maneuvering targets
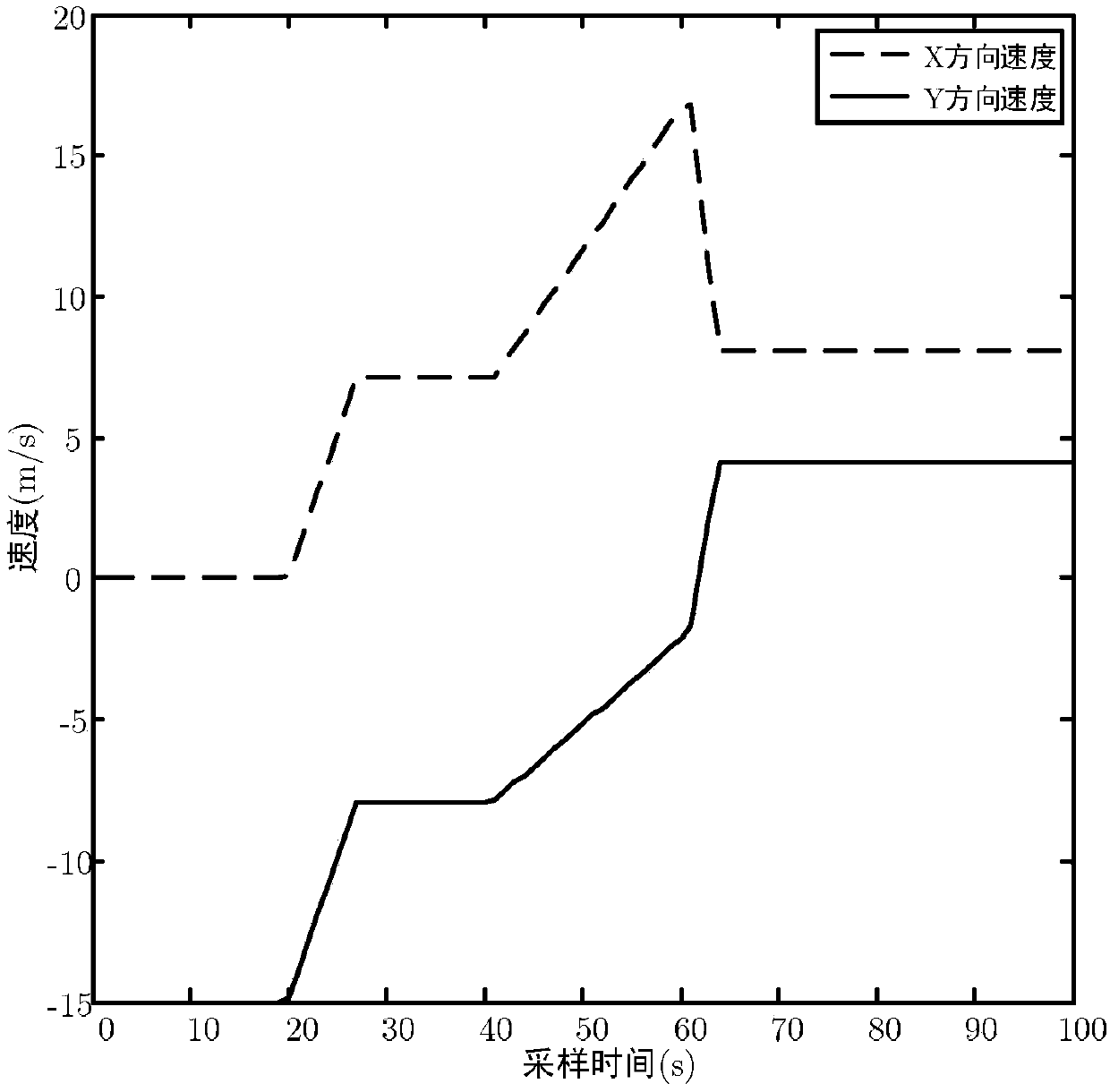
The invention discloses a tracking algorithm for high maneuvering targets. Under the colored noise condition, a target movement model and an observation model are established; the maneuvering targets are tracked by adopting an interactive multi-mode (IMM) algorithm-based Kalman filter; and a 'current' statistical model which is self-adaptively adjusted by acceleration in the IMM algorithm is combined with CV and CA models. The integral IMM algorithm performance is improved; by using system mode information in the current measurement, a Markov transition probability is calculated on line in real time, so that an accurate posterior estimate is obtained, and the model fusion precision is improved.
Owner:NANCHANG HANGKONG UNIVERSITY
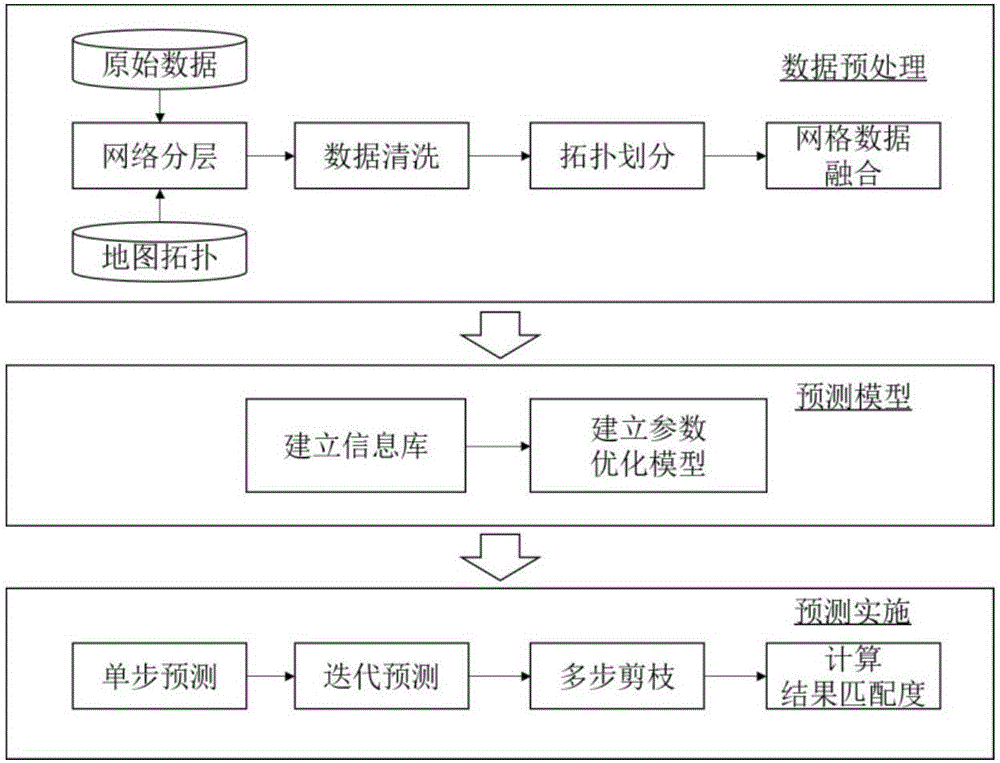
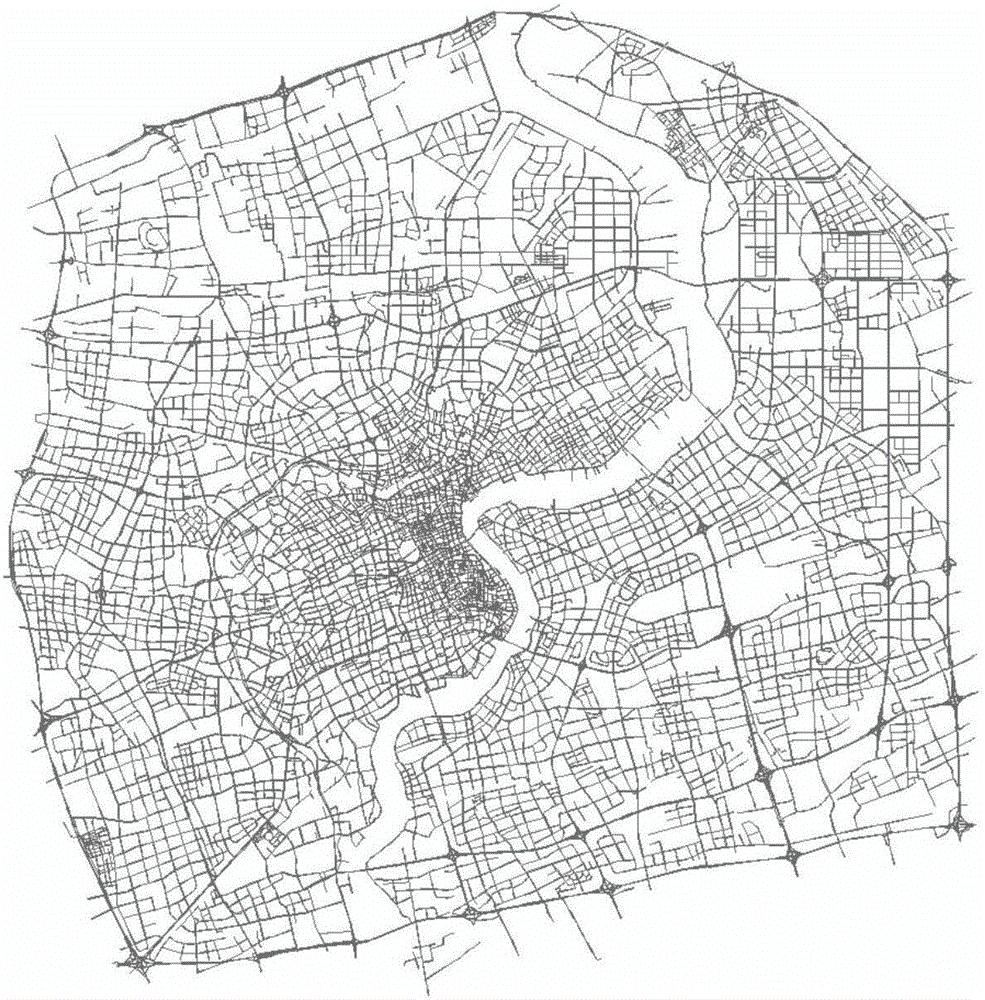
Three-dimensional urban traffic road network global state prediction method under large data environment
ActiveCN106251625AGet forecast results quicklyImprove accuracyDetection of traffic movementForecastingTraffic characteristicInformation repository
A three-dimensional urban traffic road network global state prediction method under a large data environment is disclosed. Aiming at a coupling multi-layer large-scale urban traffic road network, a global traffic mode containing coupling information is defined, a method of extracting a main road network characteristic is provided, a high dimension state time sequence is converted into a discrete state type sequence, and difficulties of high dimension data in processing and prediction aspects are simplified. From aspects of traffic periodicity, delay performance and other characteristics, a historical state transfer information database containing a multielement traffic characteristic is constructed, mass data information and a data driving idea are fully used and a Markov transition probability theory is applied so as to realize multi-step global traffic state prediction. Through the global traffic prediction, a traffic state of each area can be acquired one time. Compared to an existing traffic prediction method, by using the method of the invention, a long-term prediction result is acquired rapidly and a good prediction output effect is possessed.
Owner:SHANGHAI JIAO TONG UNIV
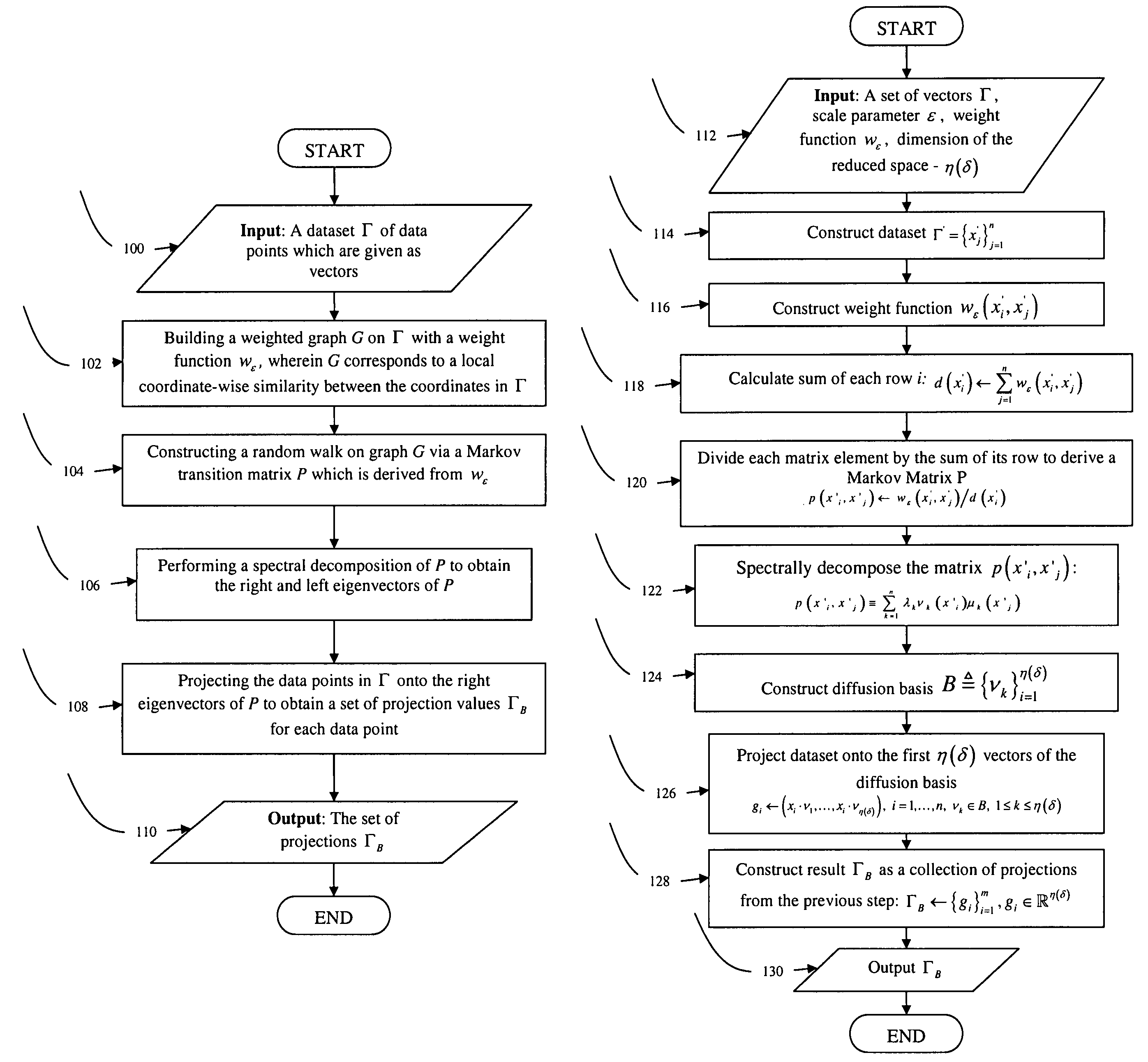
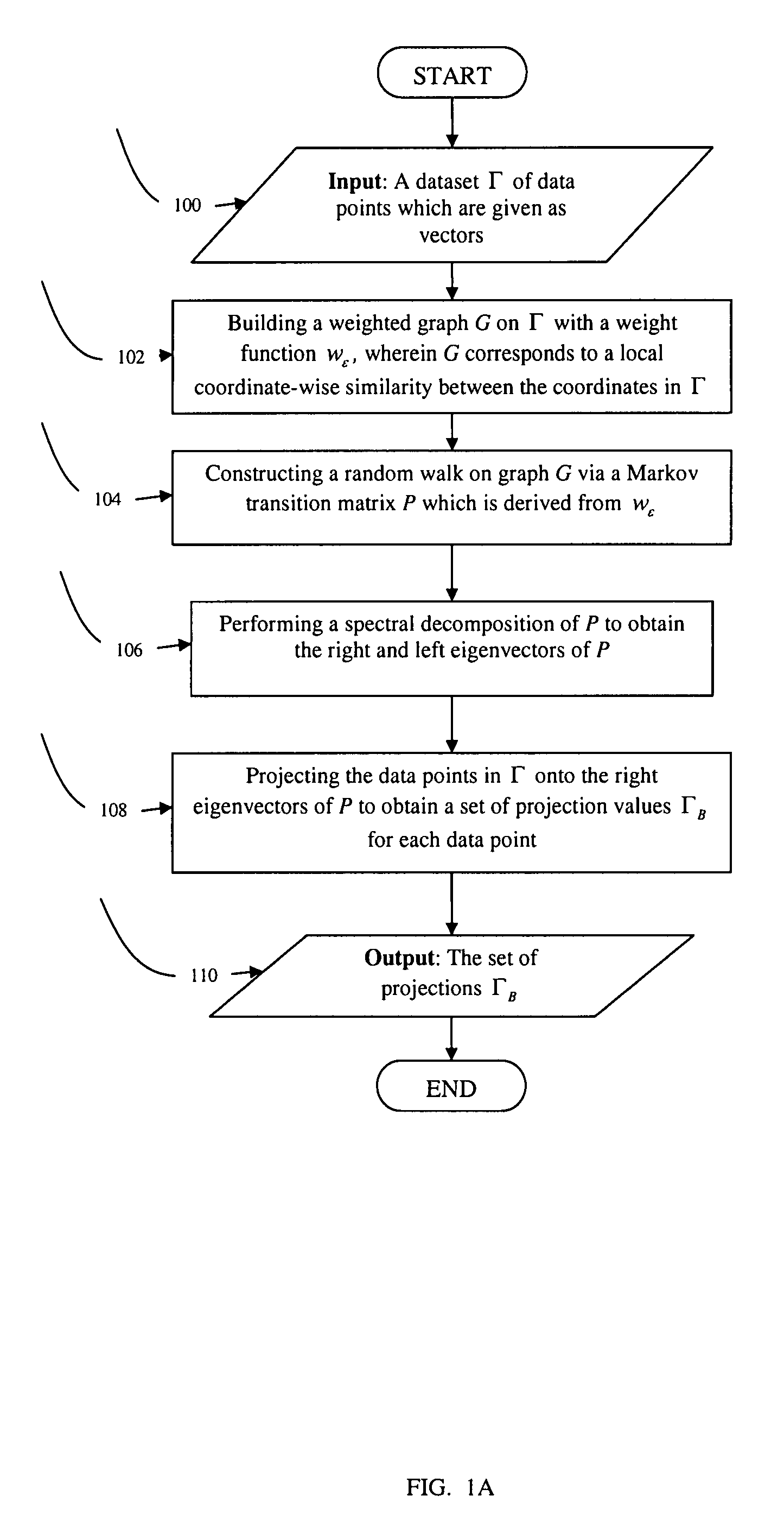
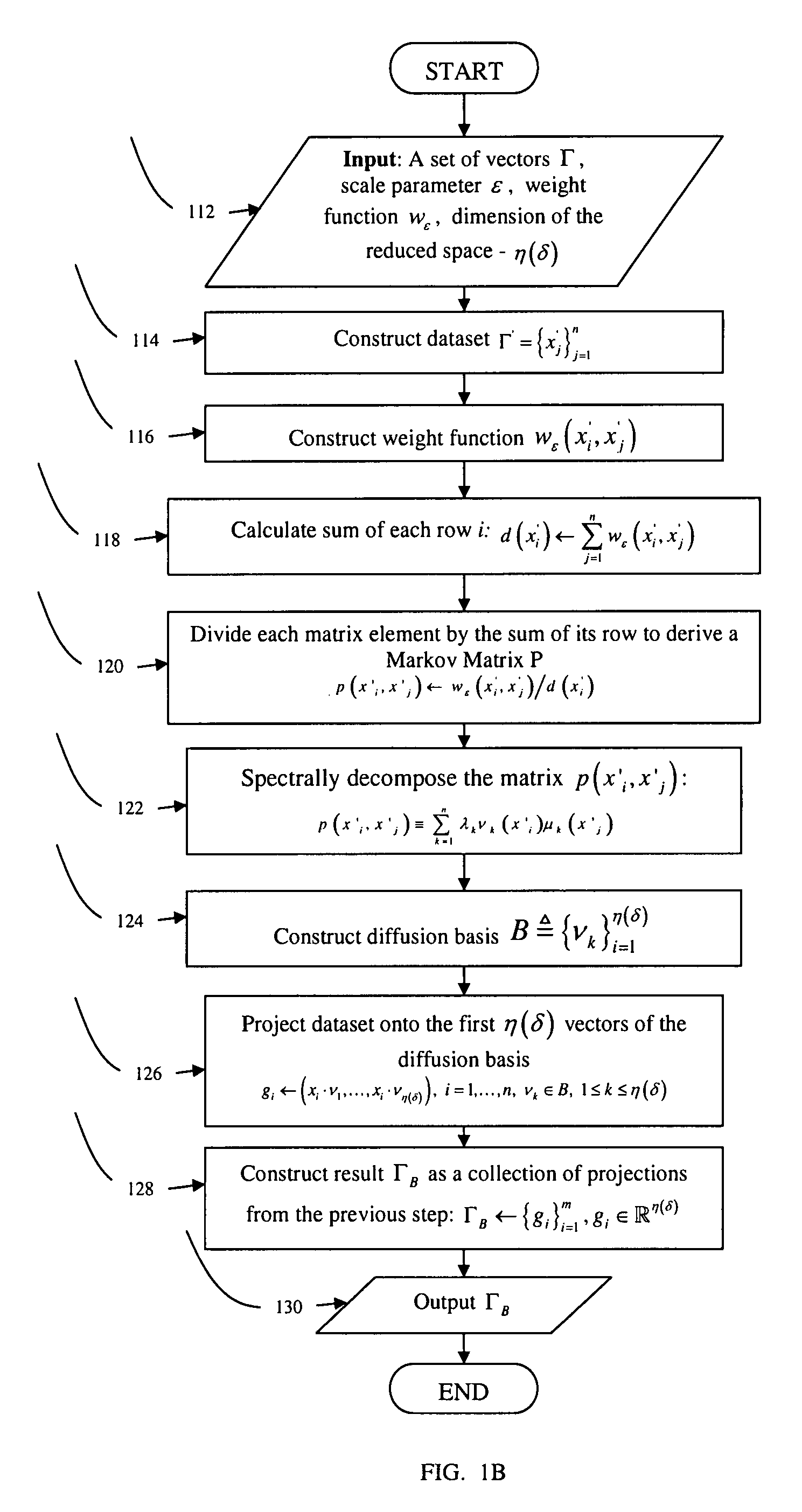
Diffusion bases methods for segmentation and clustering
InactiveUS20080181503A1Reduce dimensionalityEasy to handleCharacter and pattern recognitionBiological testingDiffusionFeature vector
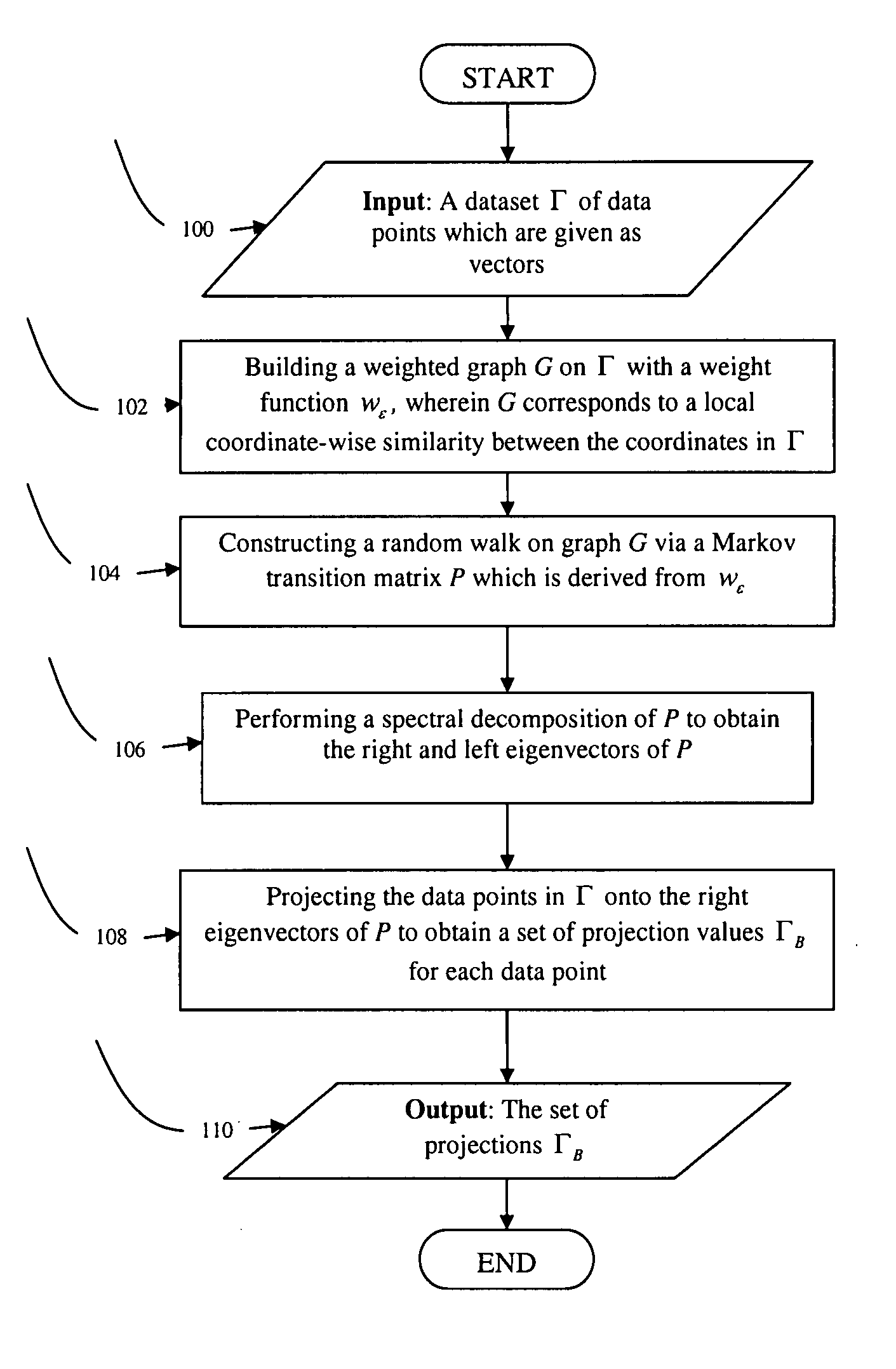
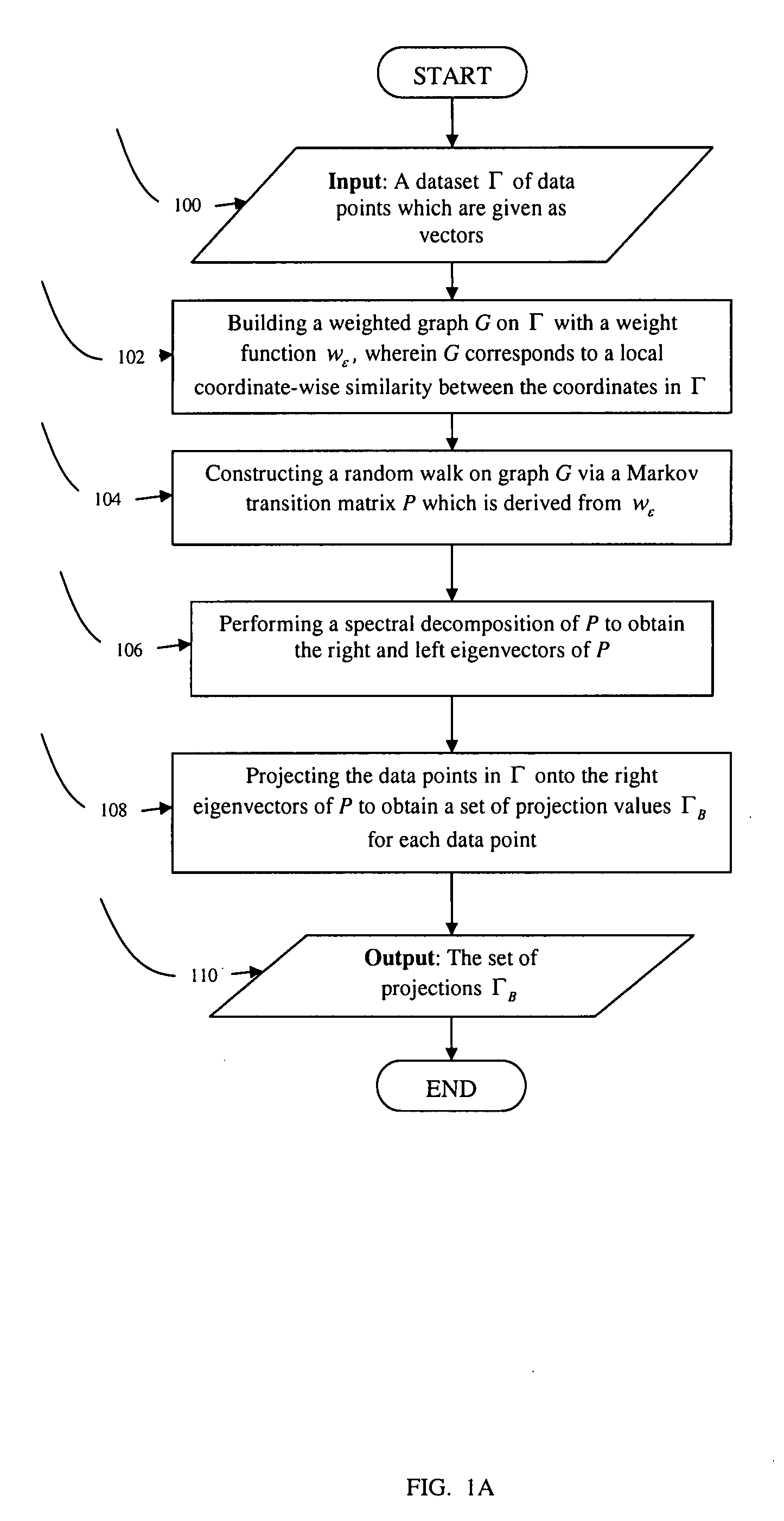
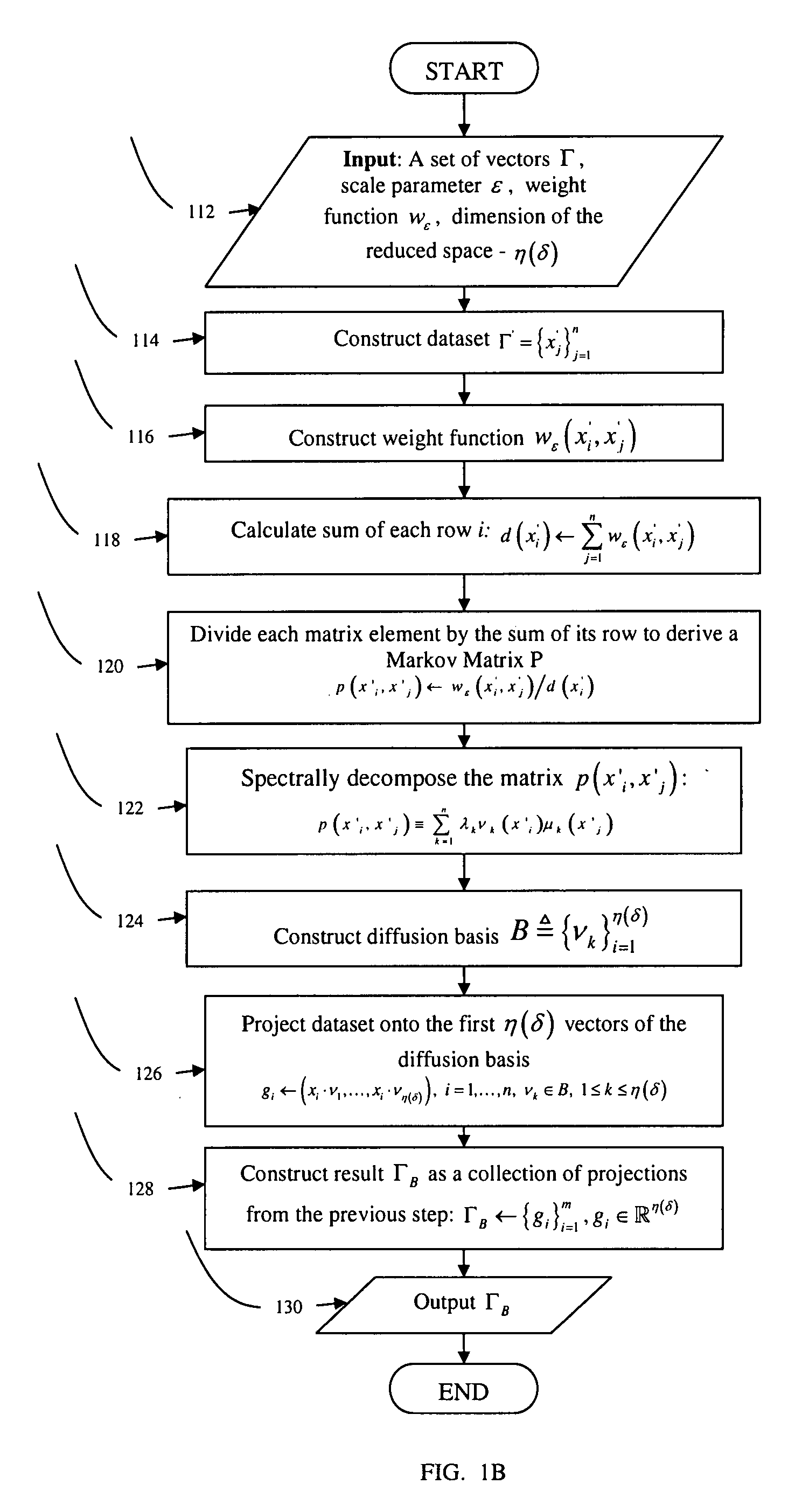
Methods for dimensionality reduction of large data volumes, in particular hyper-spectral data cubes, include providing a dataset Γ of data points given as vectors, building a weighted graph G on Γ with a weight function wε, wherein wε corresponds to a local coordinate-wise similarity between the coordinates in Γ; obtaining eigenvectors of a matrix derived from graph G and weight function wε, and projecting the data points in Γ onto the eigenvectors to obtain a set of projection values ΓB for each data point, whereby ΓB represents coordinates in a reduced space. In one embodiment, the matrix is constructed through the dividing each element of wε by a square sum of its row multiplied by a square sum of its column. In another embodiment the matrix is constructed through a random walk on graph G via a Markov transition matrix P, which is derived from wε. The reduced space coordinates are advantageously used to rapidly and efficiently perform segmentation and clustering.
Owner:SCHCLAR ALON +1
Method for classifying encrypted traffic and server, and computer readable storage medium
ActiveCN108768986AEasy to classifyIncrease differentiationData switching networksTraining phaseData stream
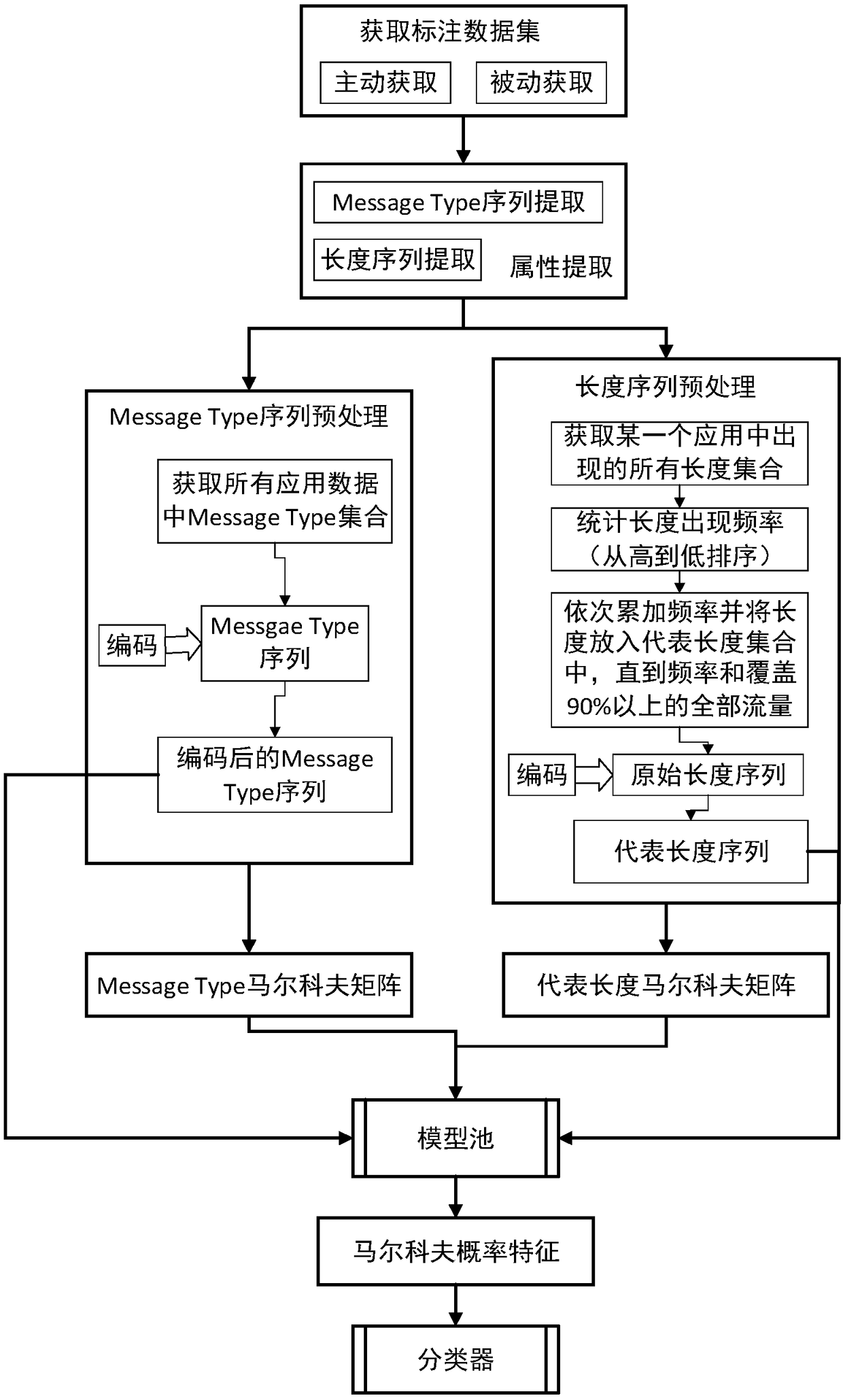
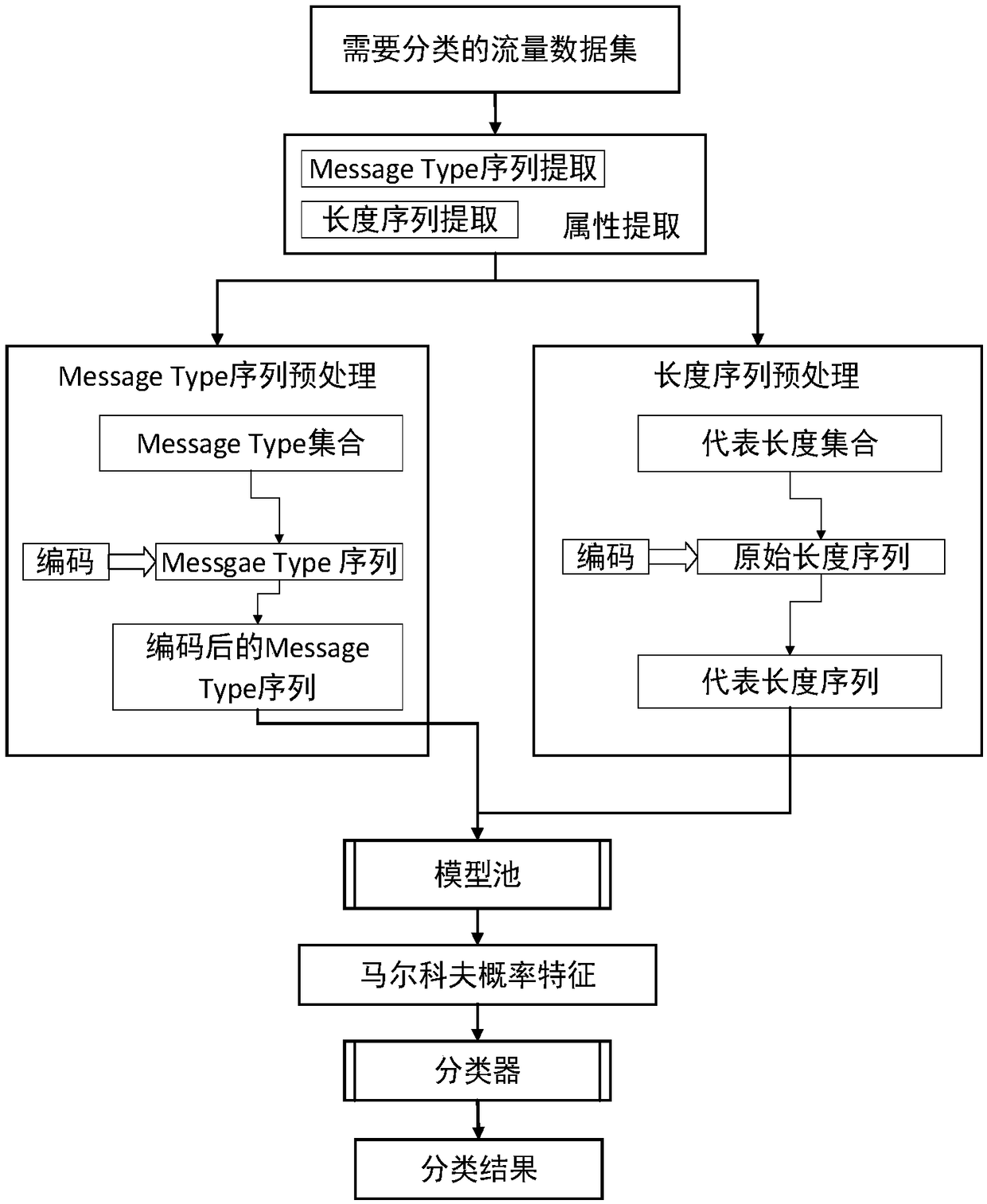
The invention discloses a method for classifying encrypted traffic and a server, and a computer readable storage medium. The method comprises a training phase and a classification phase, wherein the training phase comprises: obtaining and labeling the encrypted traffic of encrypted applications to obtain a training set; respectively extracting, from the training set, message type sequences of eachencrypted application and converting the sequences into corresponding coding sequences, and calculating the representative length sequence of the applications according to the packet length sequencesof the applications; constructing the Message type Markov transition matrix by using the coding sequences of each application, and constructing the length Markov transition matrix according to the representative length sequence; inputting the coding sequence and the representative length sequence respectively into corresponding transfer matrixes, to generate fingerprints corresponding to the encrypted traffic of the applications; and inputting each fingerprint into the classification model for training to obtain a classification model; and the classification phase comprises: for the data stream to be classified, inputting the fingerprint of the data stream into the trained classification model for classification.
Owner:INST OF INFORMATION ENG CAS
Prediction method and device for opportunity network link, and readable storage medium
ActiveCN109120462AData switching networksWireless communicationDeep belief networkTransition probability matrix
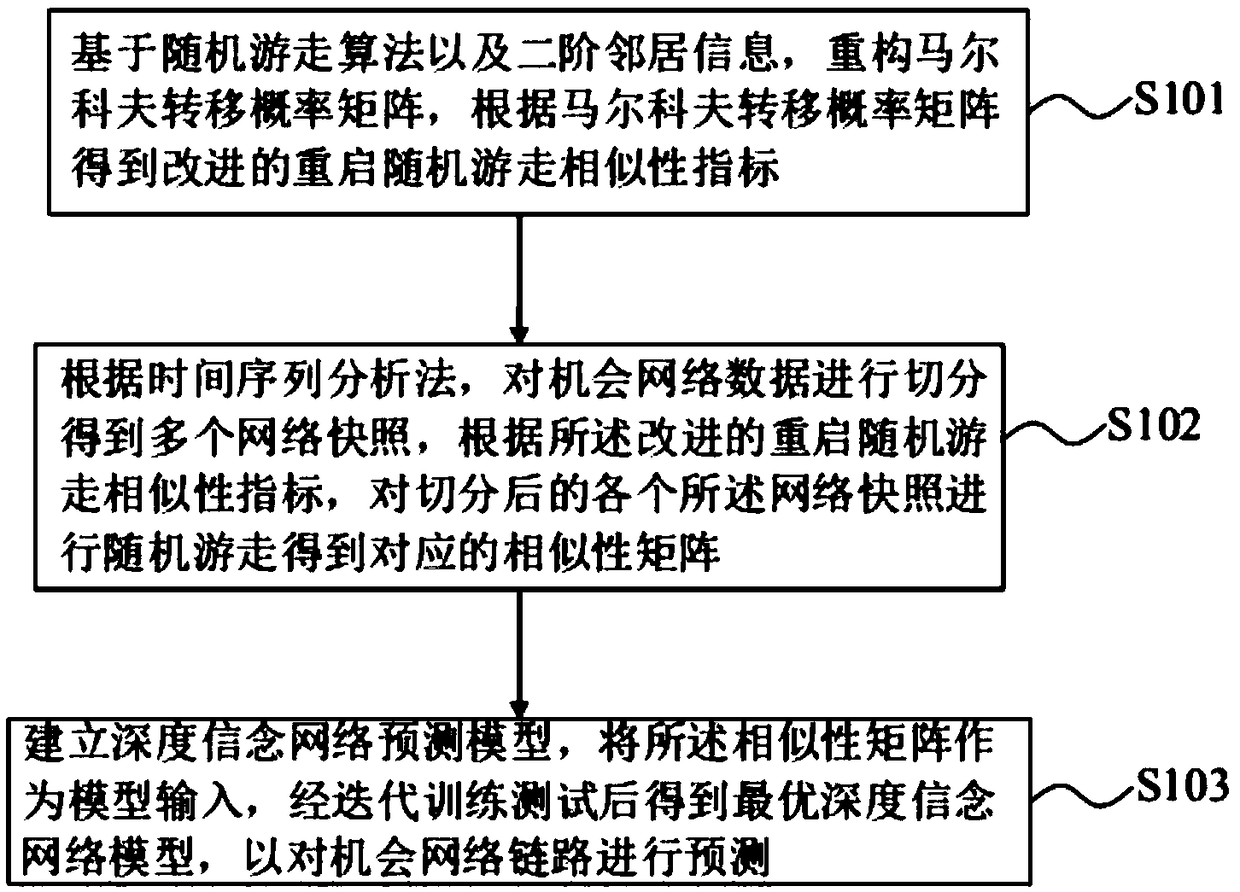
The invention relates to a prediction method and device for an opportunity network link, and a readable storage medium. The method comprises the steps: reconstructing a Markov transition probability matrix based on a random walk algorithm and second-order neighbor information, and obtaining an improved restart random walk similarity index according to the Markov transition probability matrix; segmenting the opportunity network data to obtain multiple network snapshots according to a time series analysis method, and performing the randomized walk of each of the segmented network snapshots to obtain a corresponding similarity matrix according to the improved restart random walk similarity index; establishing a deep belief network prediction model, taking the similarity matrix as the model input, and obtaining a lowest-energy deep belief network prediction model to predict the opportunistic network link after the iterative training test. The method provided by the invention can achieve the precise prediction of the network link.
Owner:NANCHANG HANGKONG UNIVERSITY
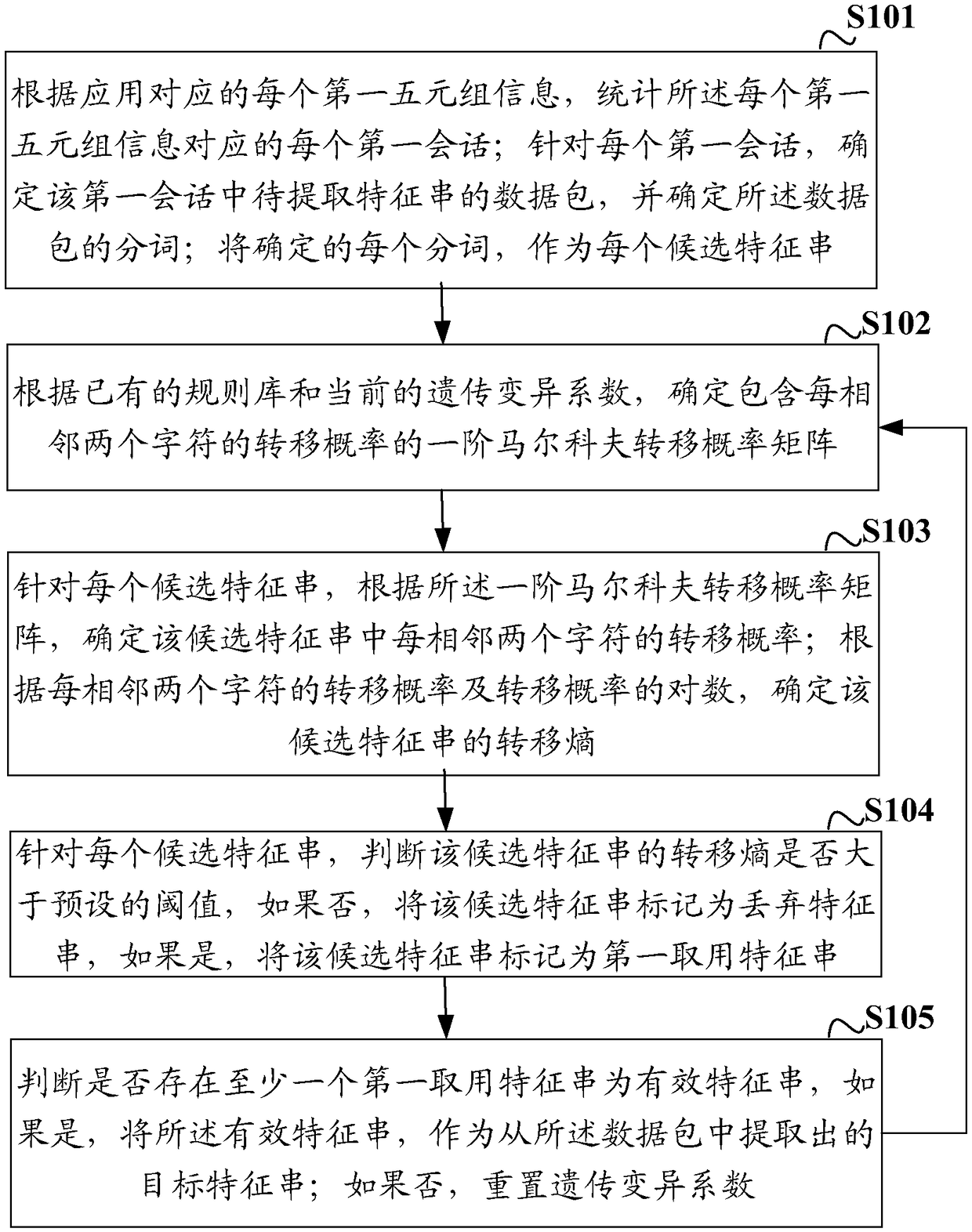
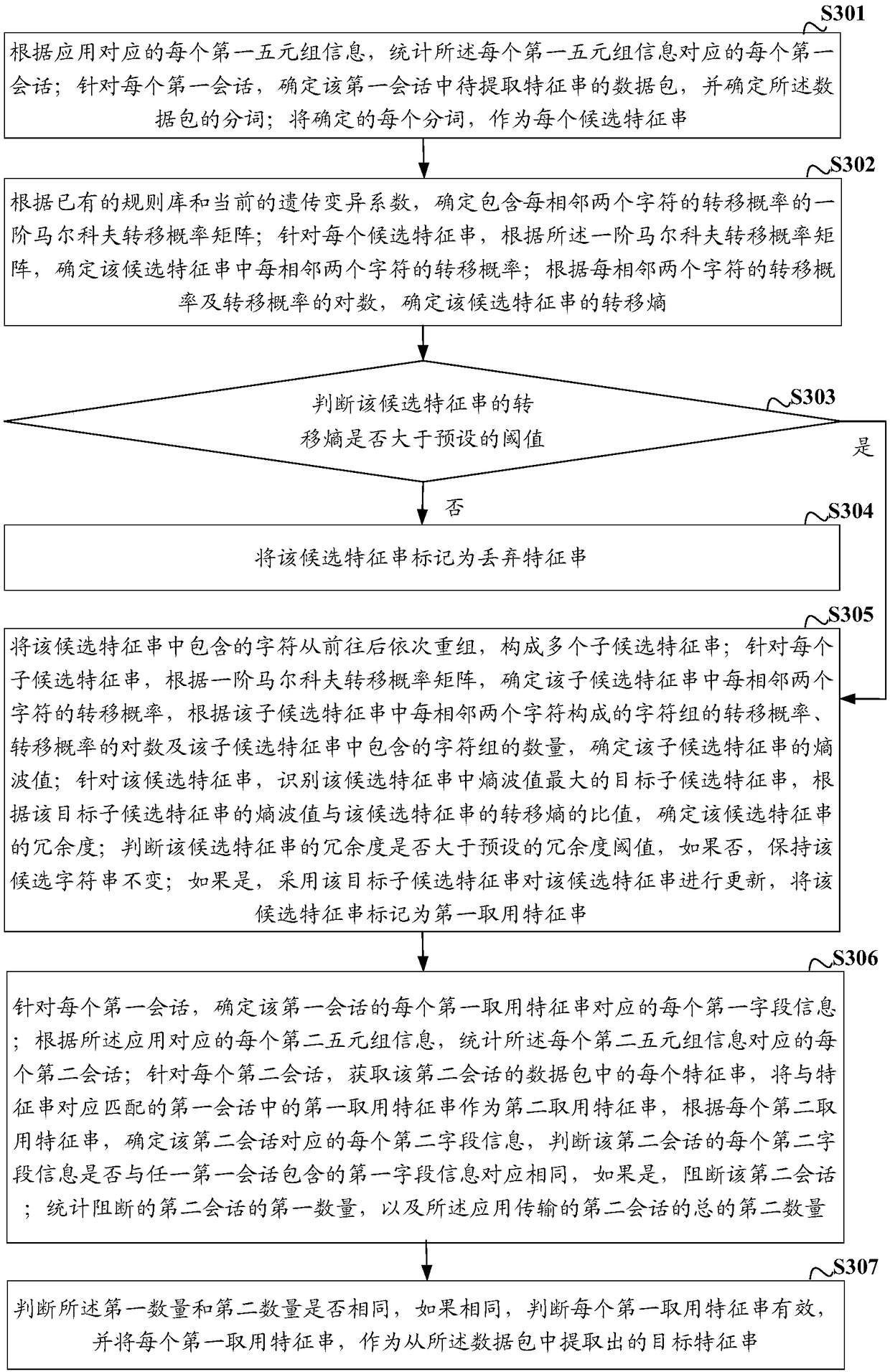
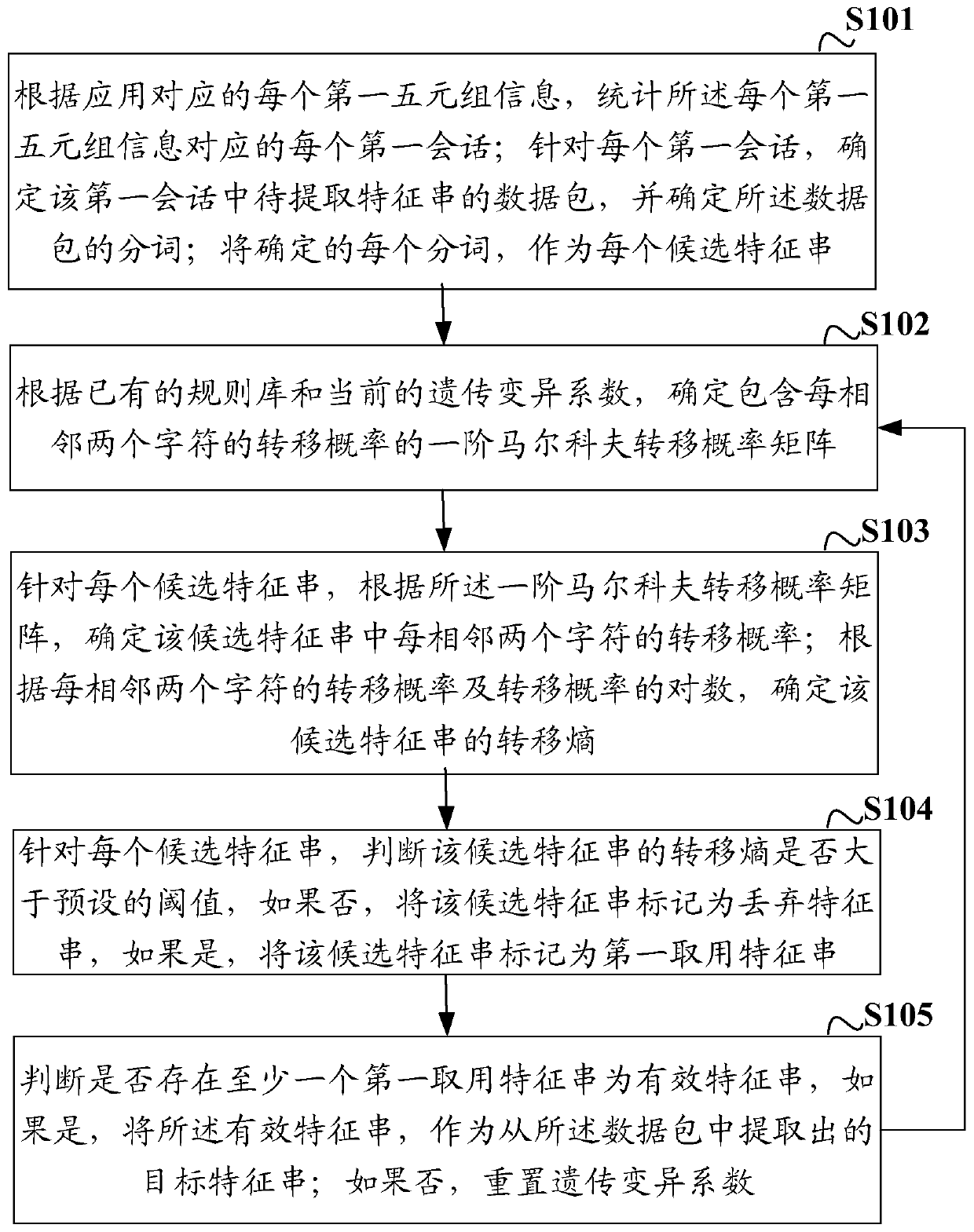
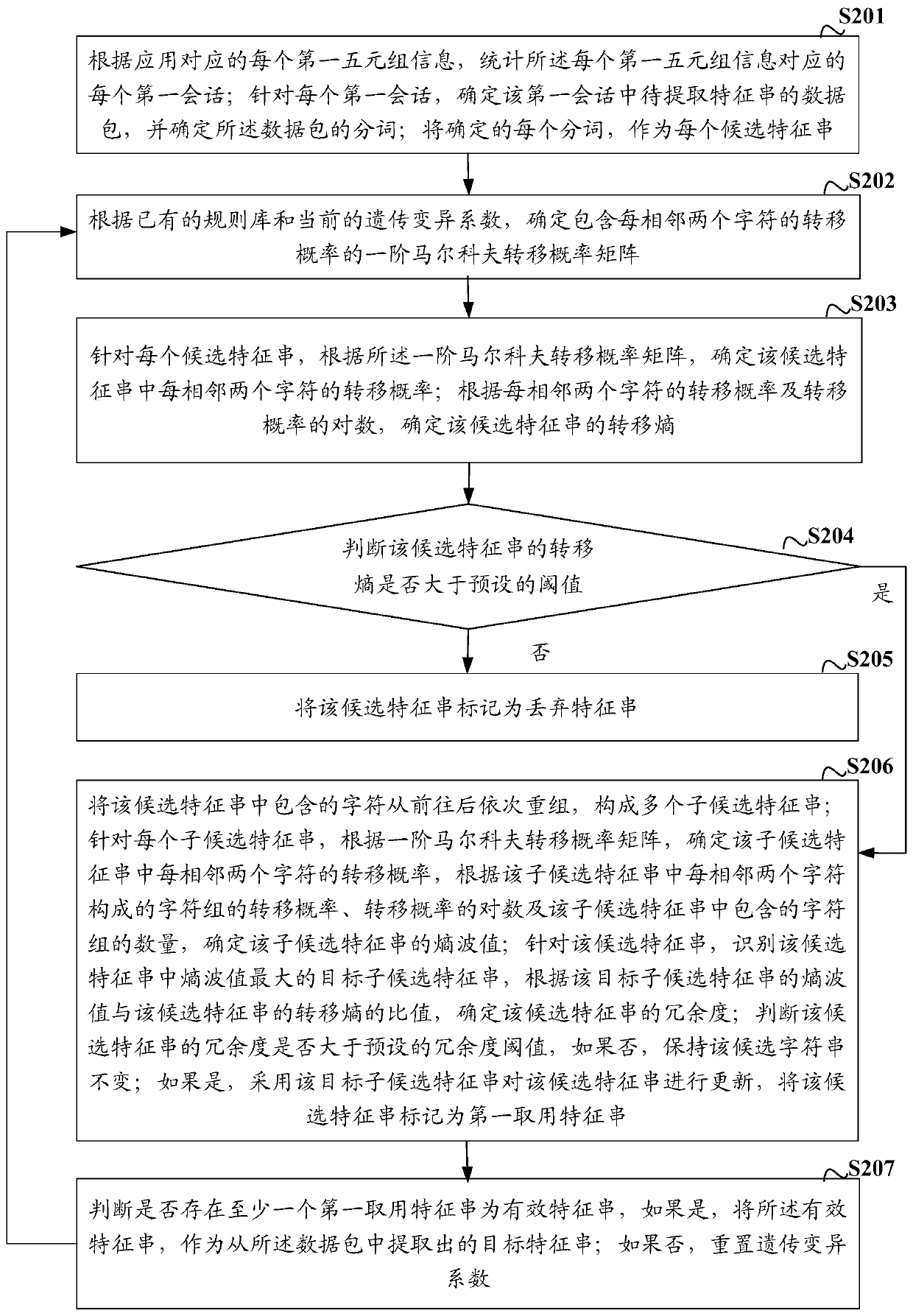
Method and device for extracting characteristic string, network equipment and storage medium
ActiveCN108234347ARealize automatic extractionNatural language data processingData switching networksTransition probability matrixNetwork packet
The invention discloses a method and a device for extracting a characteristic string, network equipment and a storage medium. The method comprises the steps of determining a transition probability ofeach two adjacent characters in a candidate characteristic string according to a first-order Markov transition probability matrix for each candidate characteristic string; determining a transition entropy of the candidate characteristic string according to the transition probability of each two adjacent characters and a logarithm of the transition entropy; and recording the candidate characteristic string of which the transition entropy is more than a preset threshold as a first taking characteristic string, and using the effective first taking characteristic string as the extracted target characteristic string. According to the method and the device provided by the embodiment of the invention, according to the first-order Markov transition probability matrix, the transition entropy of thecandidate characteristic string of the data packet can be determined, the candidate characteristic string meeting the transition entropy requirement is recorded as the first taking characteristic string, and the effective first taking characteristic string is used as the extracted target characteristic string. According to the method for extracting the characteristic string provided by the embodiment of the invention, automatic extraction of the characteristic string can be completely achieved without manual intervention.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
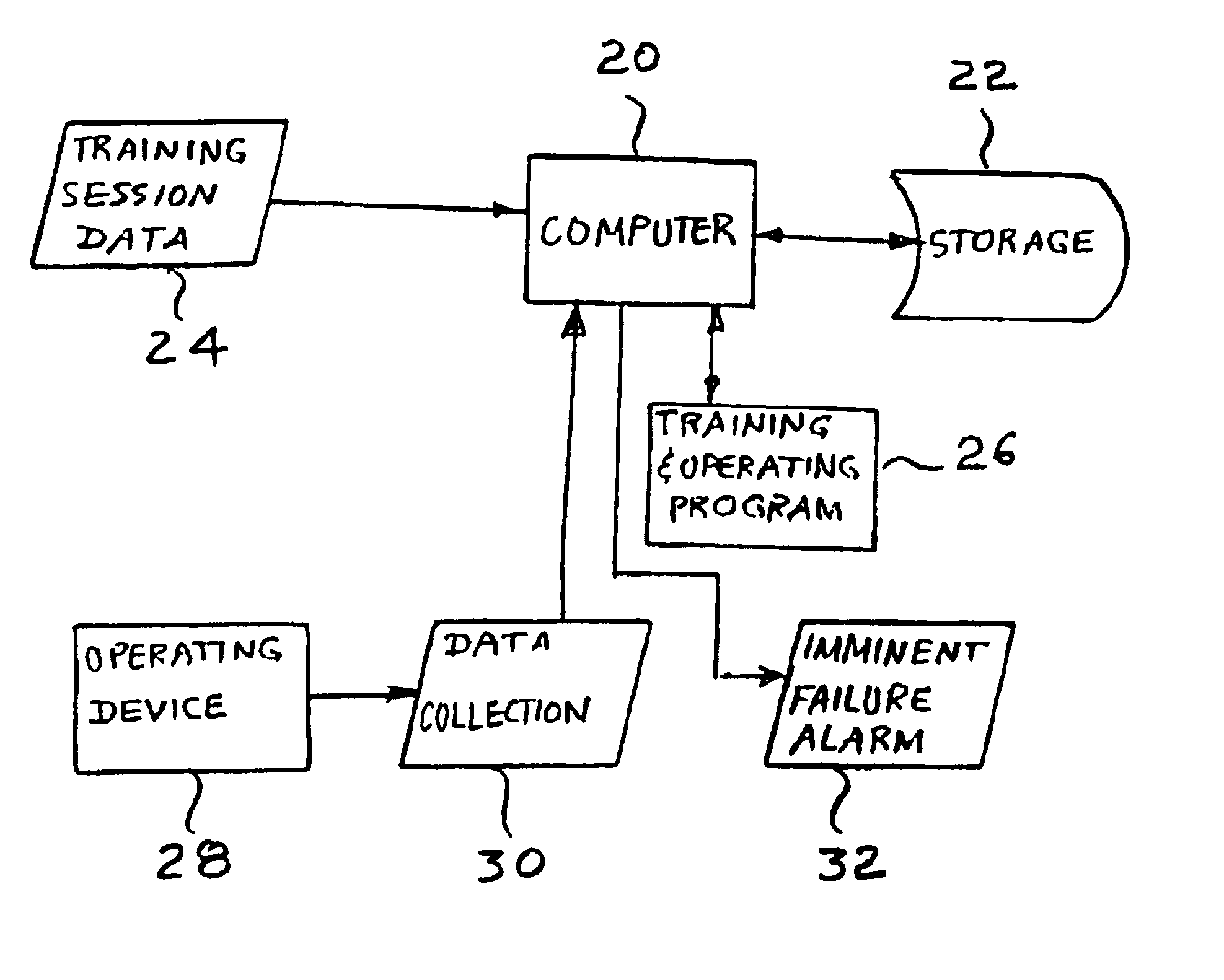
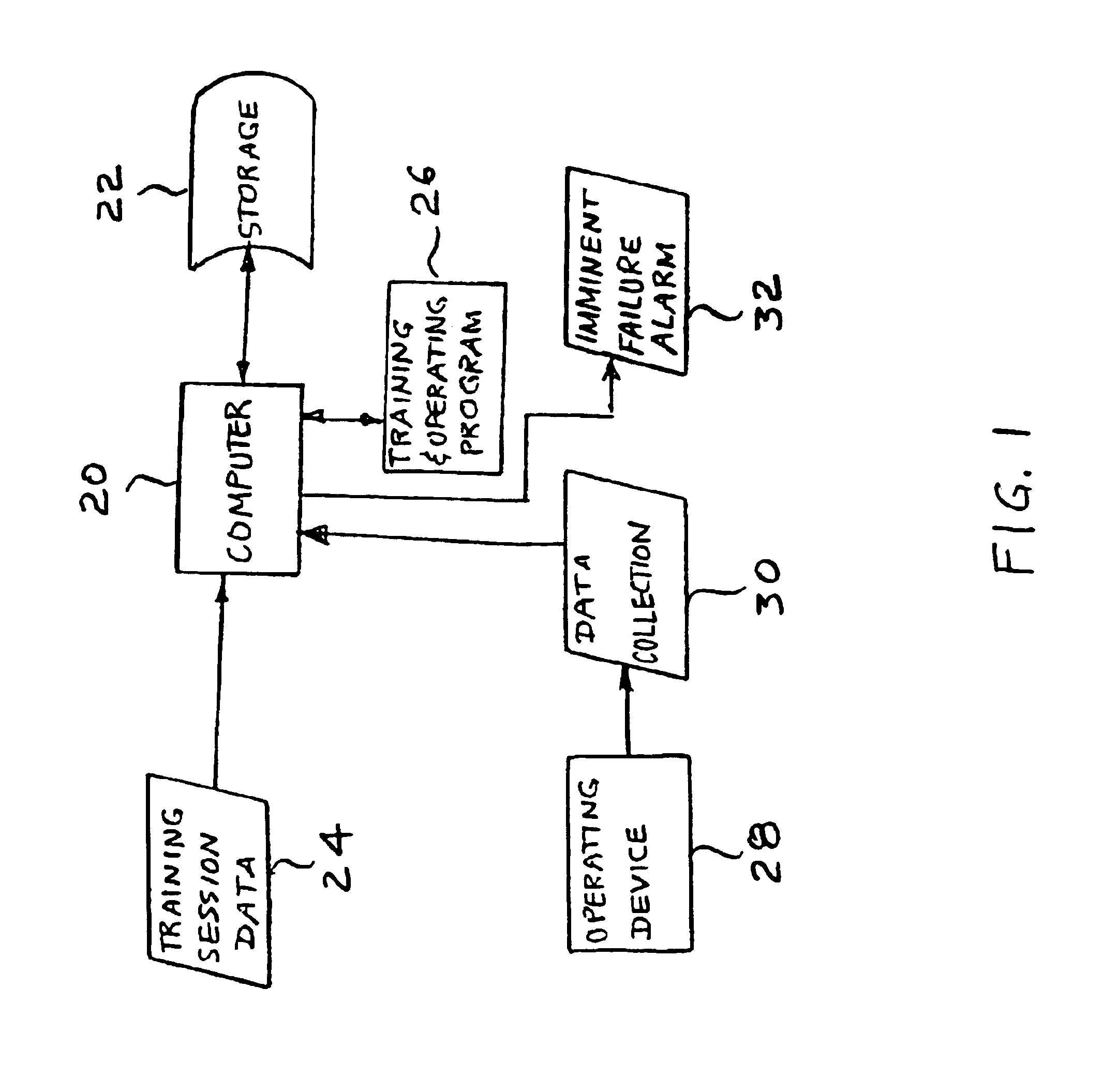
Method and apparatus for providing predictive maintenance of a device by using markov transition probabilities
A method for providing predictive maintenance of a device, comprises the steps of modeling as a time series of a discretely sampled signal representative of occurrences of a defined event in the operation of the device, the time series being modeled as two-state first order Markov processes with associated transition probabilities, wherein one state applies when the number of the occurrences exceeds a certain threshold, and the other state applies when the number of the occurrences falls below the certain threshold; computing the four transition probabilities the last N states Sn, where N is a predetermined number, conducting a supervised training session utilizing a set of J devices, which have failed due to known causes and considering the two independent probabilities and, the training session comprising computing the two-dimensional feature vectors for the initial M windows of N scans, computing the two-dimensional feature vectors for the final N number of scans, plotting a scatter-diagram of all 2D feature vectors, and deriving a pattern classifier by estimating the optimal linear discriminant which separates the two foregoing sets of vectors; and applying the classifier to monitor the persistence of occurrences of the defined event in the operation of the device.
Owner:SIEMENS CORP
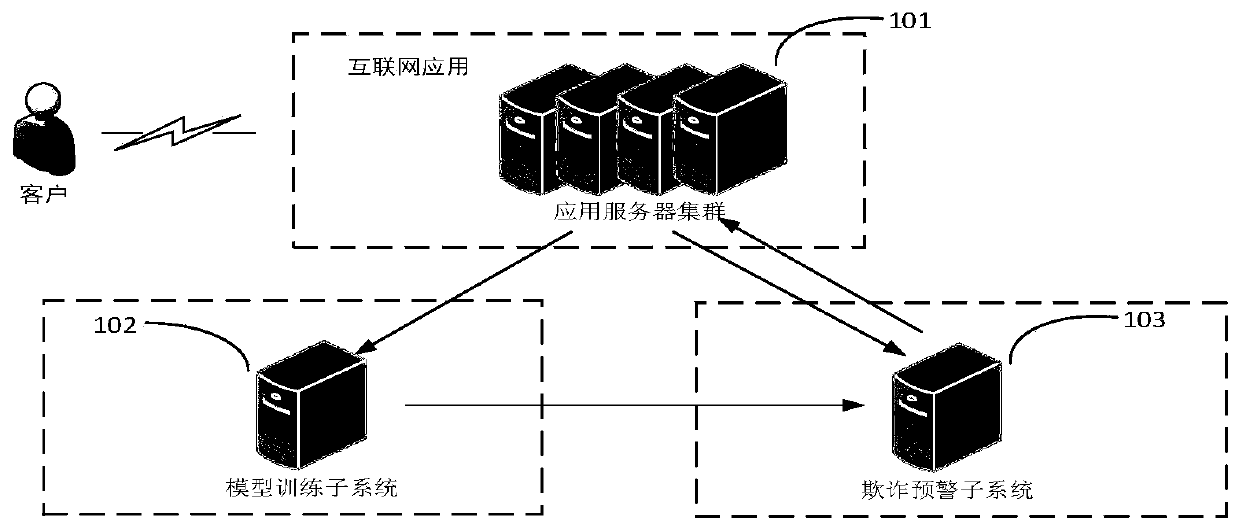
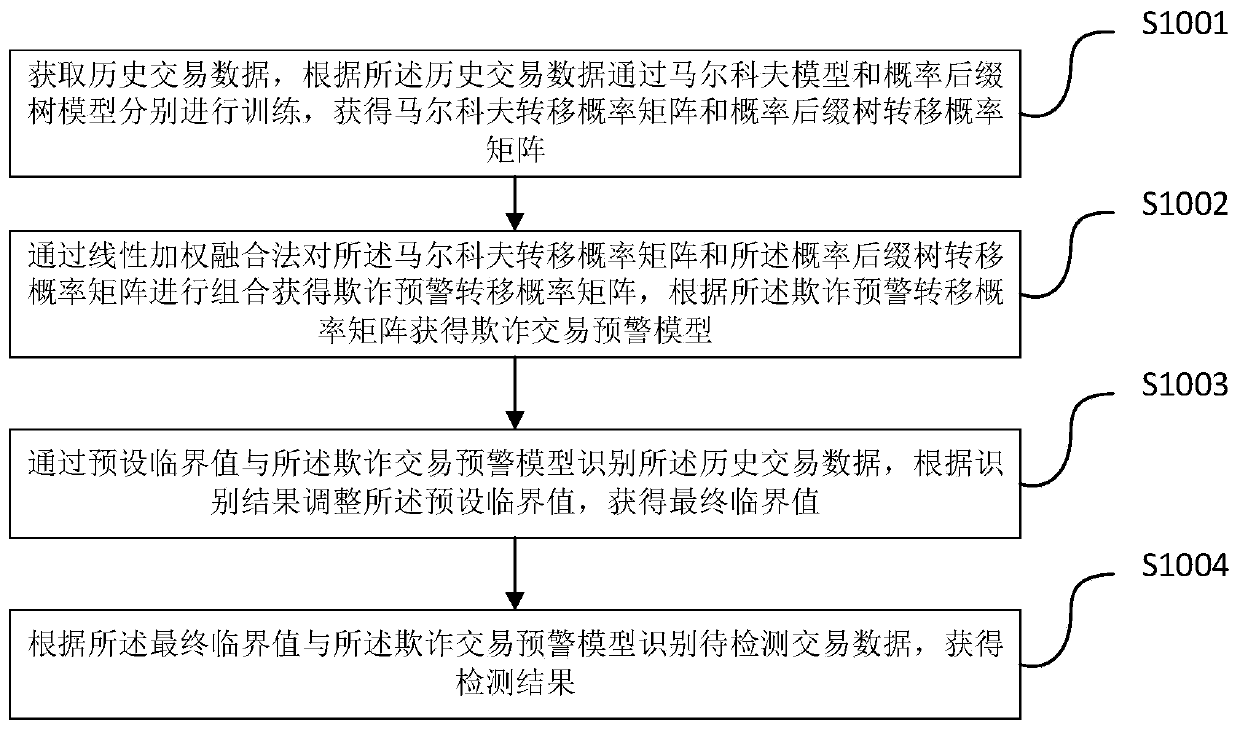
User abnormal behavior detection method and system
ActiveCN109889538ARecognition is accurate in advanceAccurate identificationCharacter and pattern recognitionTransmissionAlgorithmTransition probability matrix
The invention provides a user abnormal behavior detection method and system, and the method comprises the steps: obtaining historical transaction data, carrying out the training through a Markov modeland a probability suffix tree model according to the historical transaction data, and obtaining a Markov transition probability matrix and a probability suffix tree transition probability matrix; combining the Markov transition probability matrix and the probability suffix tree transition probability matrix through a linear weighted fusion method to obtain a fraud early warning transition probability matrix, and obtaining a fraud transaction early warning model according to the fraud early warning transition probability matrix; identifying the historical transaction data through a preset critical value and the fraud transaction early warning model, and adjusting the preset critical value according to an identification result to obtain a final critical value; and identifying to-be-detectedtransaction data according to the final critical value and the fraud transaction early warning model to obtain a detection result.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
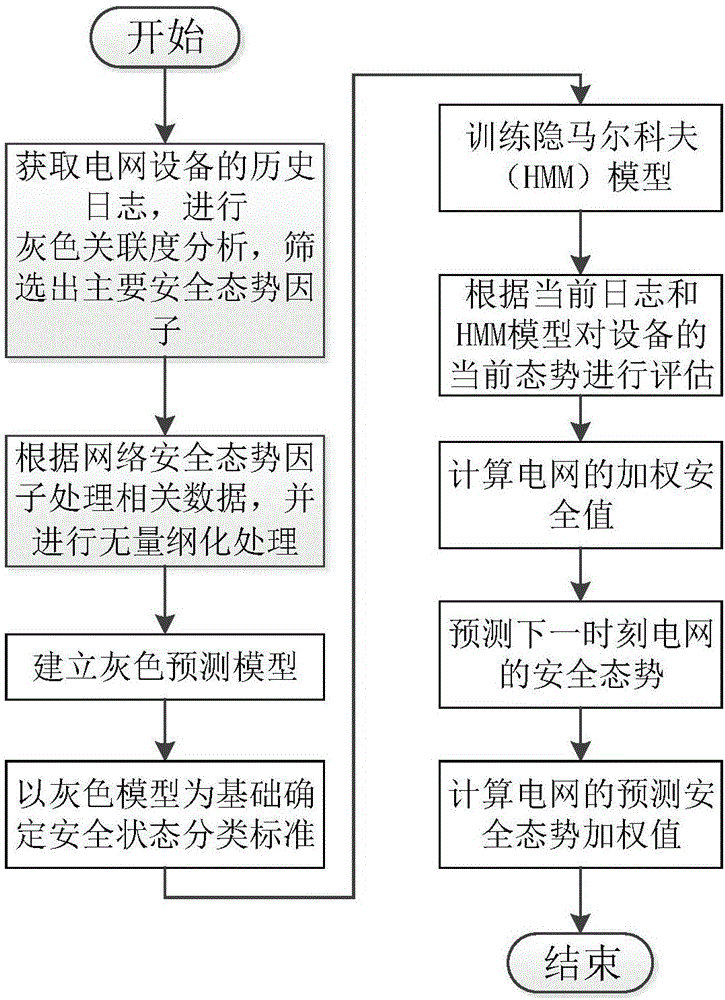
Power grid security risk prediction method
ActiveCN106372799AReduce workloadAlleviate huge problemsResourcesData switching networksAlgorithmHide markov model
The invention relates to a power grid security risk prediction method. The method comprises steps that screened network security posture factors are processed; security posture state classification standards are determined; a hidden Markov model is constructed according to actual power grid conditions; hidden Markov model parameters are updated according to present security posture of equipment; security posture of an integral electric power network is calculated; a prediction risk value of the equipment and a weight prediction risk value are calculated. Through the method, the network security posture factors are deeply researched, the factors having greatest influence on the security posture are screened out, data processing workload is reduced, model training is carried out through utilizing the data relevant to the security posture factors, a problem of over-hugeness of a hidden Markov transition matrix is effectively alleviated, moreover, problems of non-high prediction precision and parameter determination difficulty are alleviated.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Method and system for detecting illegal data implantation internal attack in smart power grid
ActiveCN104638762AEfficient detectionRealize insider attack behavior analysisCircuit arrangementsTransmissionSmart gridSmart power
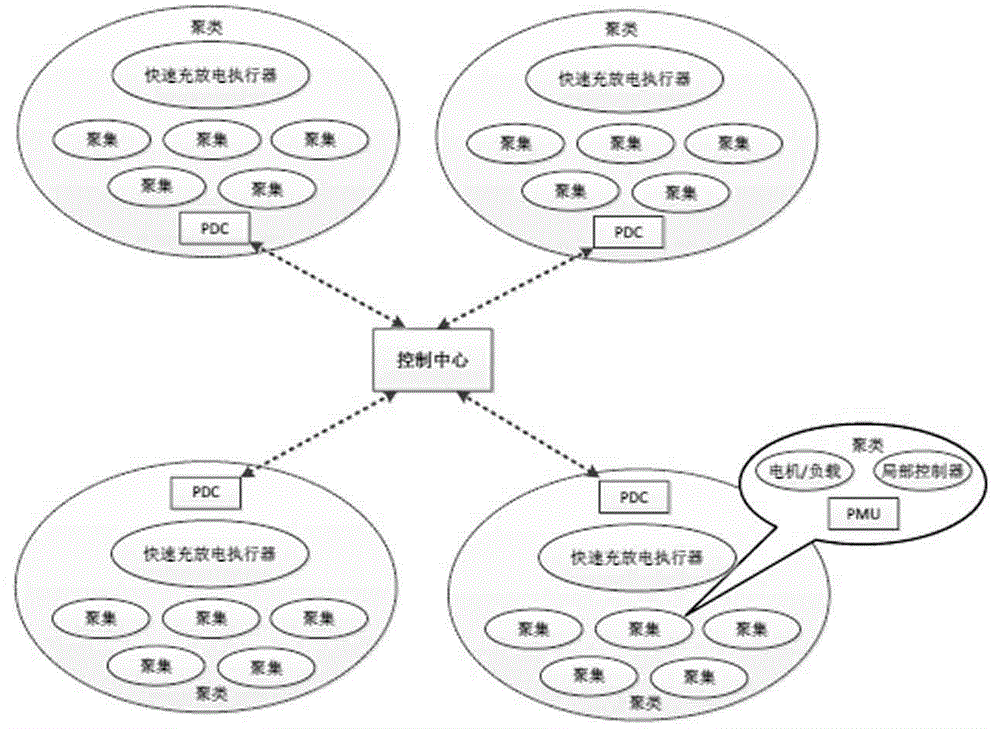
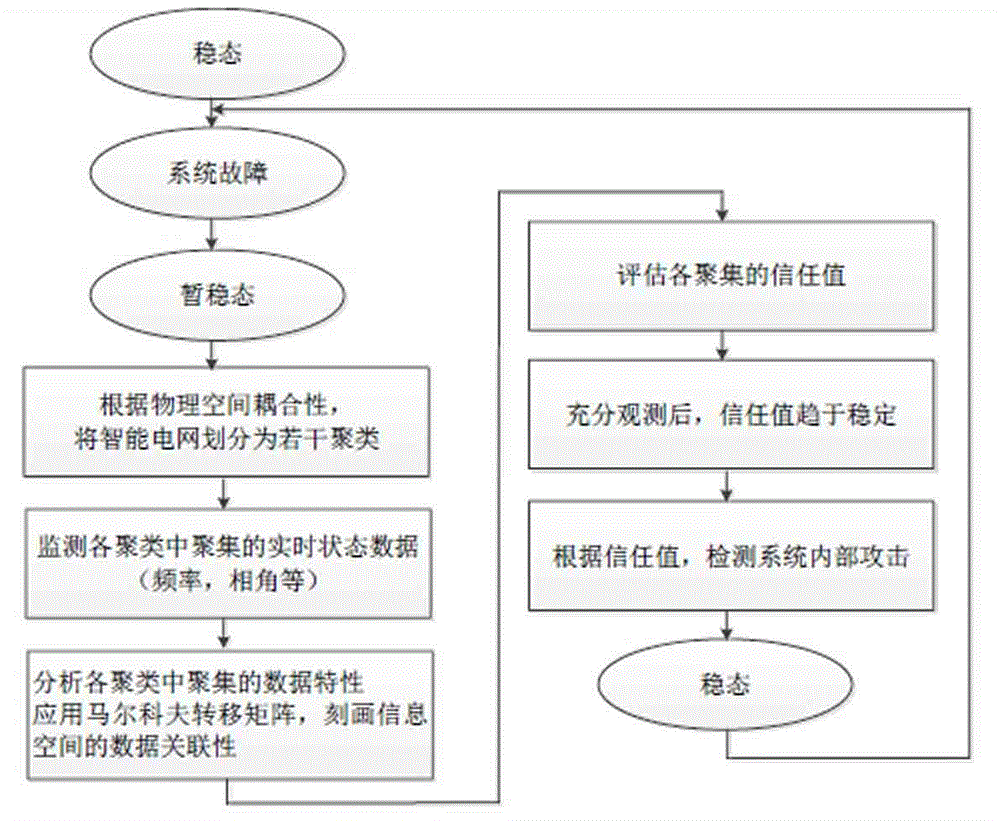
The invention discloses a method and a system for detecting illegal data implantation internal attack in a smart power grid. The method adopts a bidirectional channel architecture consisting of gathering, clustering and control centers. The method comprises: (1) a gathering classification module; (2) a system initialization module; (3) a local trust evaluation module; (4) a global trust evaluation module; (5) an internal attach detection module. According to the method and the system, a trust model and a behavior model detection method are focused, and a monitoring and detection system for the illegal data implantation internal attack of the smart power grid is realized by utilizing the intrinsic characteristics of physical coupling and data consistency of the smart power grid on the basis of a graph theory, biotic community, power grid system characteristic vector and characteristic value, markov transition probability matrix theory and technology. The system can resist the internal attack of the smart power grid with high imperceptibility and powerful attack capacity; the implantation attack of illegal data can be high efficiently and accurately detected in the transient stable state process caused by external disturbance or faults.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Design method of radar maneuvering target tracking waveform
ActiveCN107390199AImprove accuracyGood freedomWave based measurement systemsNonlinear filterCompound matrix
The invention belongs to the technical field of radar communication and particularly relates to a design method of a radar maneuvering target tracking waveform. The method includes: building a movement model for a maneuvering target, calculating filter update matrix weight, the mixed input state of the movement module and a corresponding estimation error covariance matrix, using a linear or nonlinear filtering algorithm to acquire the local unbiased filter estimation value and target state estimation error covariance matrix of each submodel, performing compound matrix updating to obtain optimal state estimation and fusion estimation error covariance matrix, acquiring transmission waveform rotation parameters on the basis, using fractional Fourier transformation to rotate the waveform set by a user to obtain a new measuring error ellipse and transmission waveform, and performing Markov transition probability matrix updating to achieve good tracking precision. By the design method applicable to the radar communication technology, the problem that maneuvering target tracking is poor in robustness and low in accuracy is solved.
Owner:HARBIN INST OF TECH AT WEIHAI +1
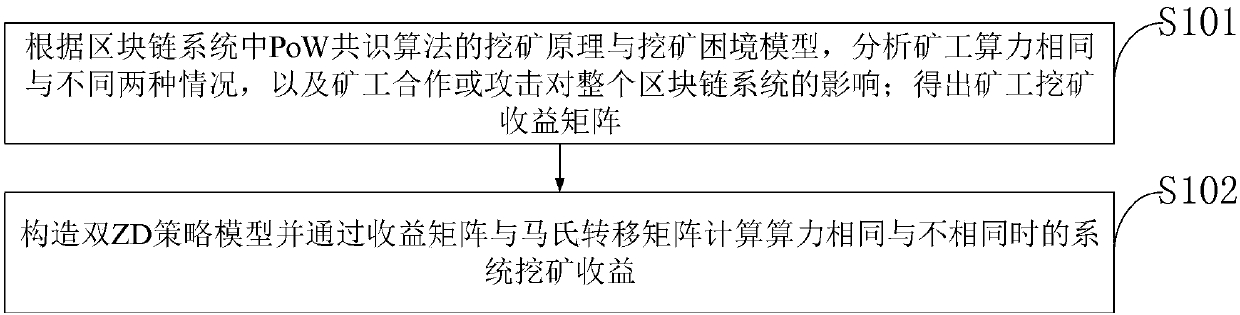
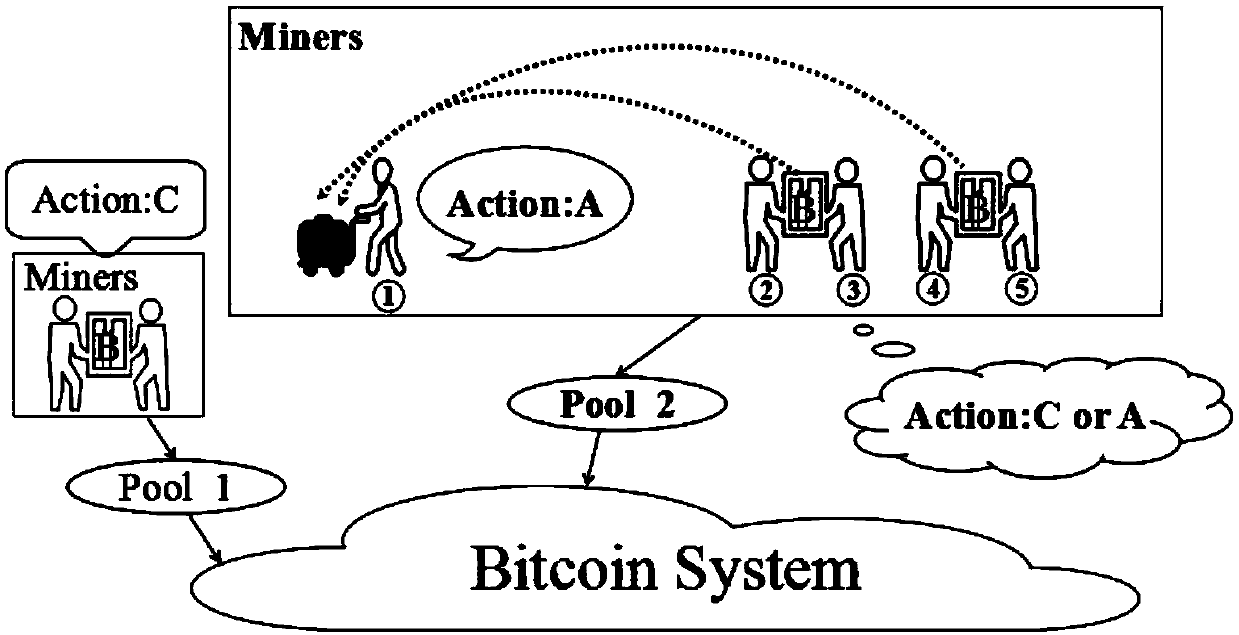
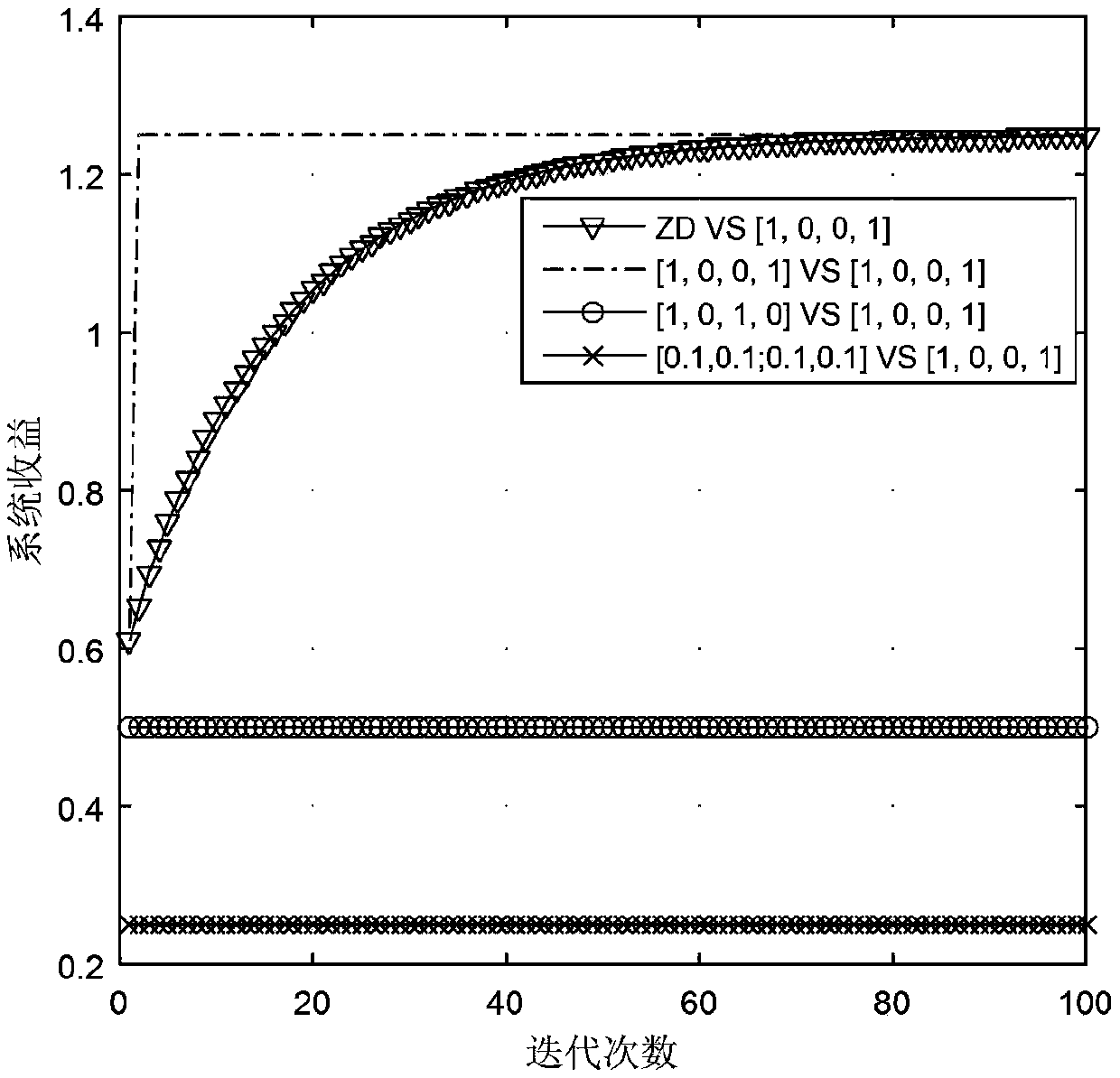
New method and system for improving mining profits
ActiveCN107819756AGuaranteed cooperative miningIncrease mining incomeArtificial lifeTransmissionData treatmentComputer science
The invention belongs to the technical field of data processing and discloses a method and system for improving mining profits. Two conditions that miner proof of work is the same and miner proof of work is different are analyzed according to a PoW consensus algorithm and a dilemma model, thereby obtaining a miner mining profit matrix; and a ZD-free policy model, a single-ZD policy model and a double-ZD policy model are established, and system mining profits are calculated according to a profit matrix and a Markov transition matrix when the proof of work is the same and the proof of work is different. Compared with [1,0,1,0], [0.1,0.1,0.1,0.1] (a single-ZD policy), a double-ZD policy provided by the invention has the advantage that the mining profits are improved by 68% and 287%; and whenthe proof of work is different, compared with the other two policies, the single-ZD policy has the advantage that the mining profits are improved by 35% and 355%, and compared with the other two policies, the double-ZD policy has the advantage that the mining profits are improved by 48% and 139%. According to the double-ZD policy, each miner is guaranteed to carry out cooperation mining, and further the system mining profits reach the maximum value.
Owner:ZHEJIANG NORMAL UNIVERSITY
Diffusion bases methods for segmentation and clustering
InactiveUS7961957B2Easy to handleReduce dimensionalityCharacter and pattern recognitionBiological testingDiffusionFeature vector
Methods for dimensionality reduction of large data volumes, in particular hyper-spectral data cubes, include providing a dataset Γ of data points given as vectors, building a weighted graph G on Γ with a weight function wε, wherein wε corresponds to a local coordinate-wise similarity between the coordinates in Γ; obtaining eigenvectors of a matrix derived from graph G and weight function wε, and projecting the data points in Γ onto the eigenvectors to obtain a set of projection values ΓB for each data point, whereby ΓB represents coordinates in a reduced space. In one embodiment, the matrix is constructed through the dividing each element of wε by a square sum of its row multiplied by a square sum of its column. In another embodiment the matrix is constructed through a random walk on graph G via a Markov transition matrix P, which is derived from wε. The reduced space coordinates are advantageously used to rapidly and efficiently perform segmentation and clustering.
Owner:SCHCLAR ALON +1
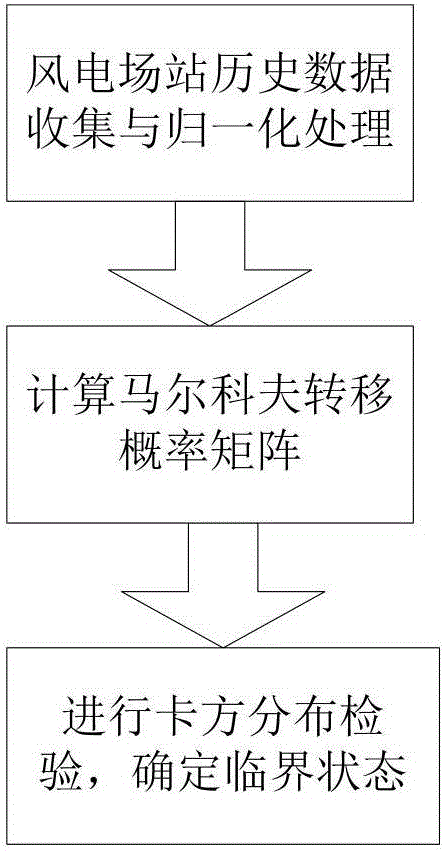
Determination method and system for wind power state number upper limit in wind power generating algorithm
PendingCN106780134AGood effectHigh precisionData processing applicationsElectricityChi-squared distribution
The invention relates to a determination method and system for a wind power state number upper limit in a wind power generating algorithm based on MCMC. According to the method, first, historical wind power exerting data is collected and sorted out, the data is divided into exerting states in different numbers, a state transition frequency number and a state transition probability matrix of all wind power exerting data points under the exerting states in different numbers are calculated respectively, a chi-square test is performed on the exerting states to determine a critical exerting state number conforming to Markov transition characteristics, and the critical exerting state number serves as a dividable exerting state number upper limit. A theoretical basis is laid for profound research of wind power exerting time sequence modeling. Through the chi-square distribution test method, a maximum wind power state number needing to be divided can be determined, and the precision of a wind power sequence generated through the MCMC method is improved to the maximum extent.
Owner:CHINA ELECTRIC POWER RES INST +2
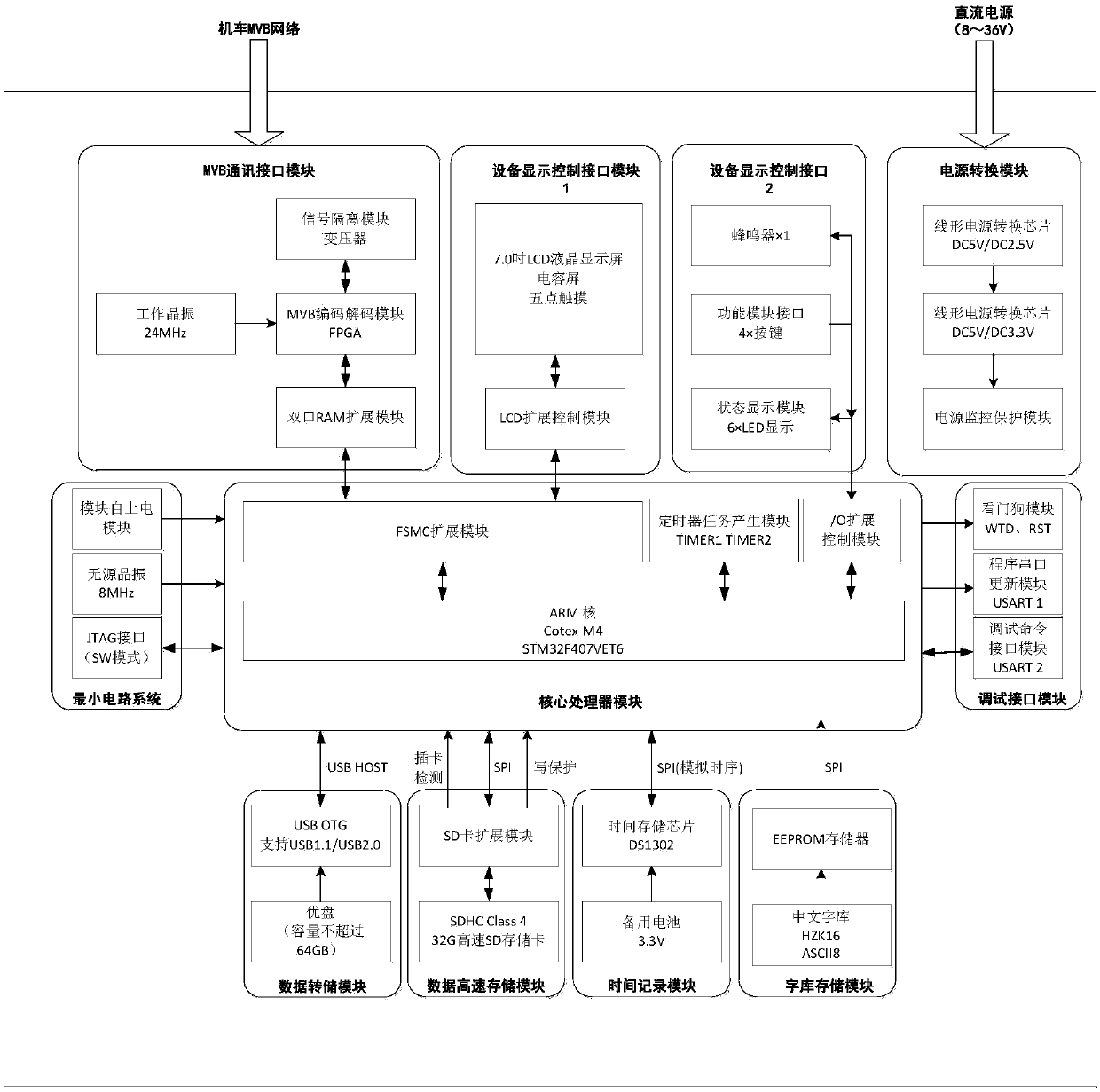
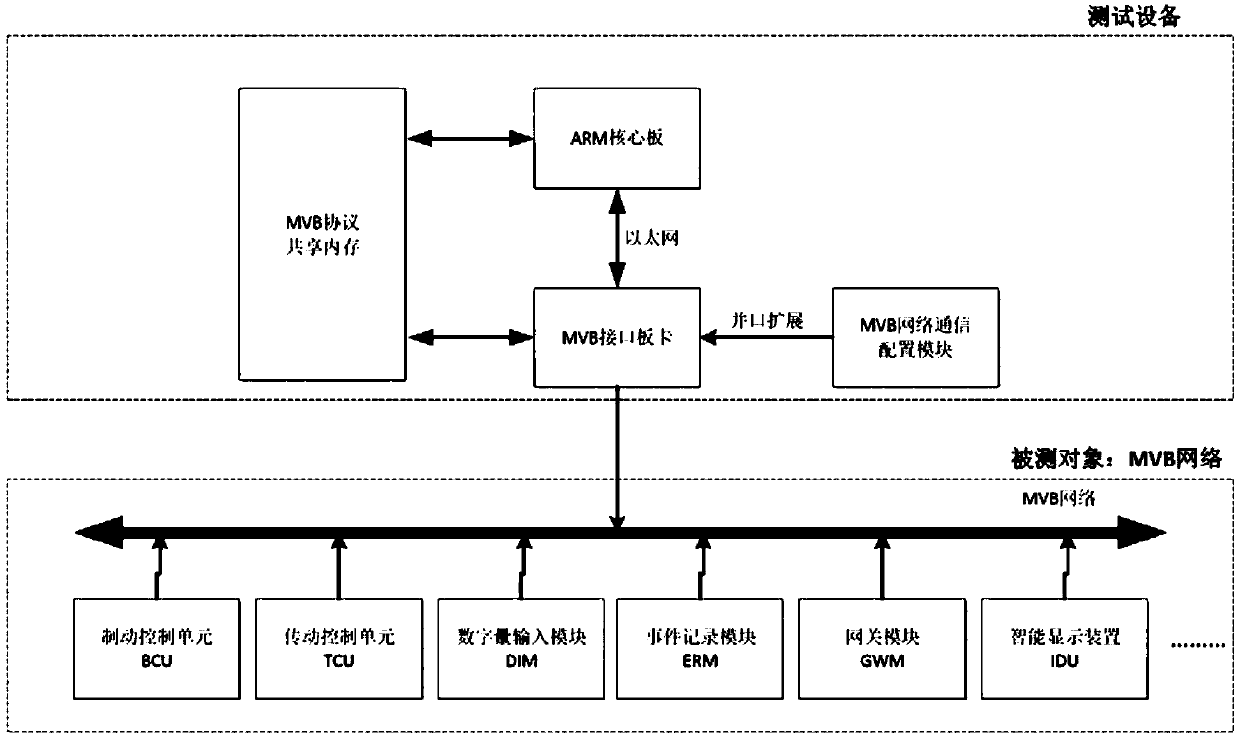
Method and device for diagnosing faults of rail locomotive network control systems
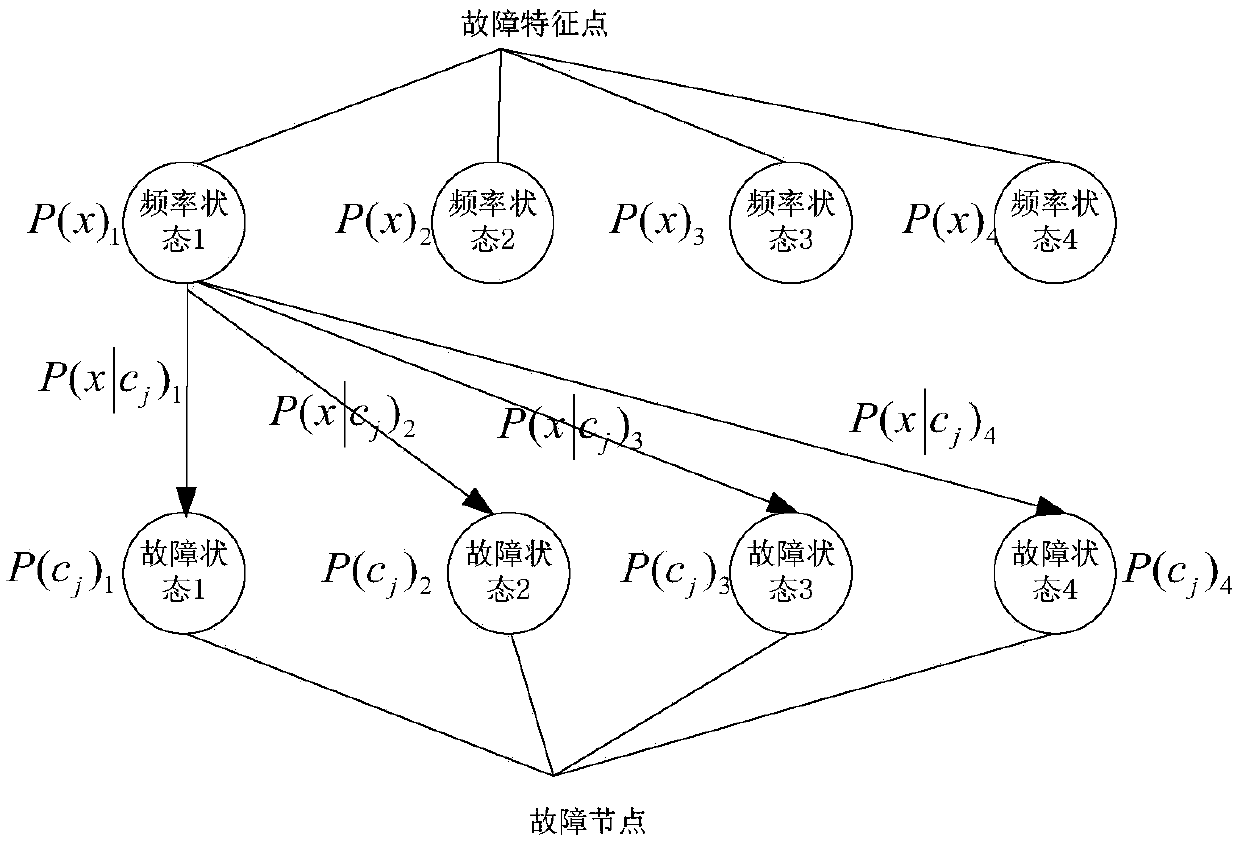
ActiveCN109656239AReduce performanceGood decision supportElectric testing/monitoringAlgorithmMarkov transition
The invention discloses a method and a device for diagnosing faults of rail locomotive network control systems. The method includes building fault state identification models on the basis of Bayesiannetworks and Markov transition matrixes; acquiring MVB (multifunctional vehicle bus) data packet on MVB in real time, acquiring occurrence frequencies corresponding to fault feature points in currentmonitoring standard calibration time delta t and acquiring fault feature occurrence probability and mapping probability of the fault feature points on the basis of the occurrence frequencies; computing prior probability of fault nodes, which correspond to fault features, in four fault states by the aid of prior probability transition models and ultimately computing posterior probability of the fault nodes, which correspond to the fault features, in the four fault states on the basis of prior probability and mapping probability parameters by the aid of probability conversation formulas. The fact that the fault states corresponding to the highest posterior probability are current states of the fault nodes is the highest in reliability.
Owner:CHANGSHA RUIWEI ELECTRIC
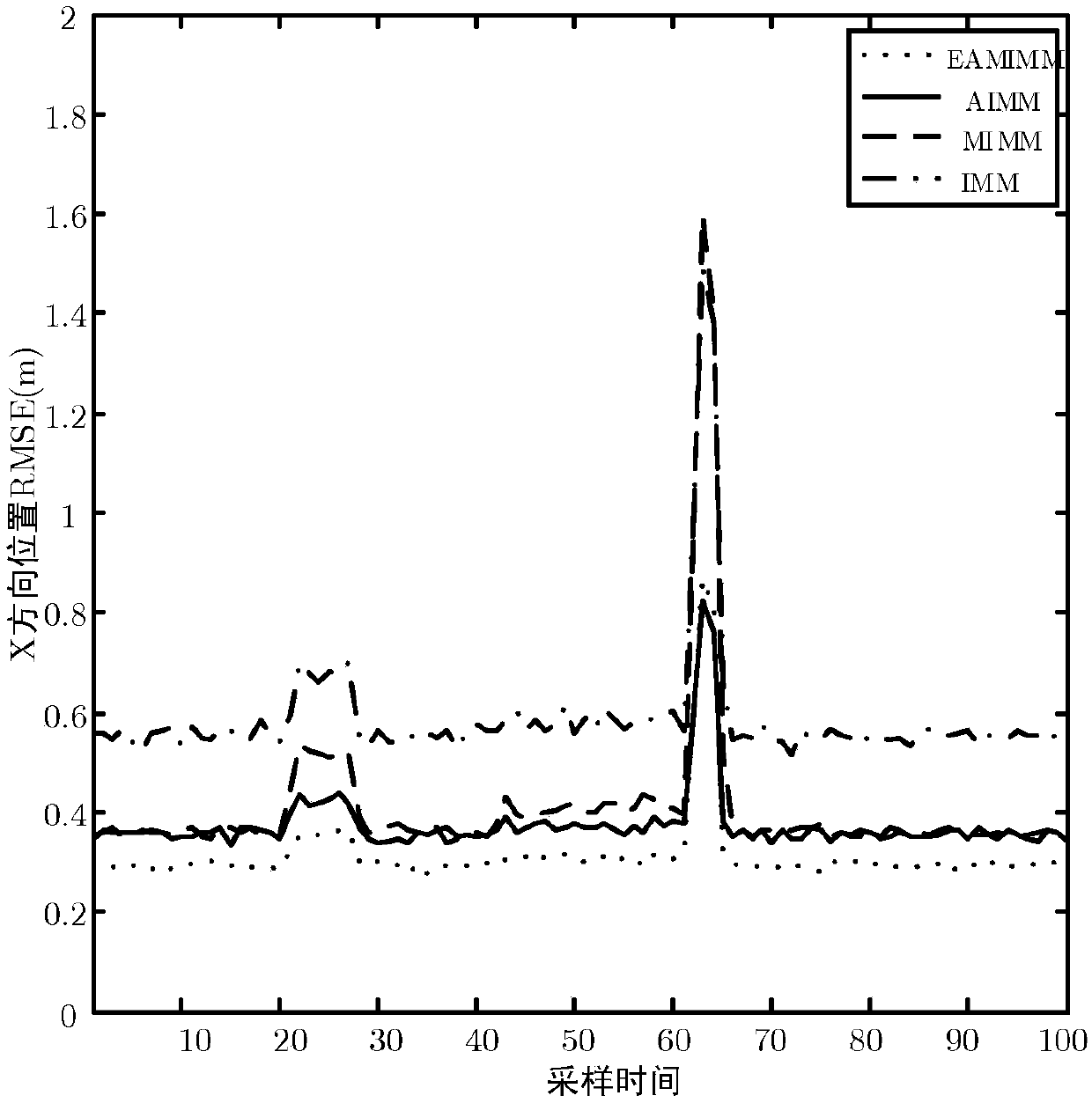
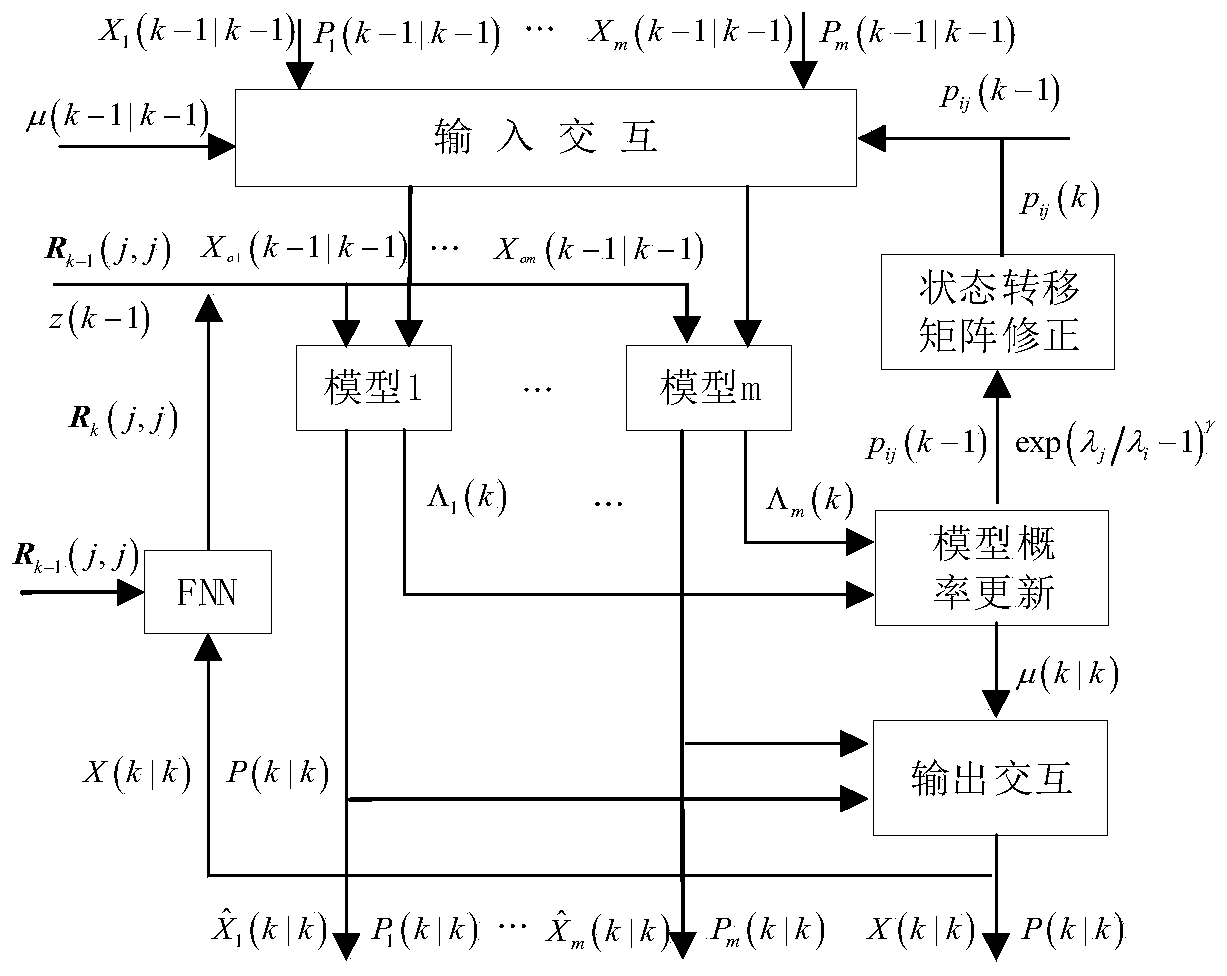
IMM (Interacting Multiple Model) target tracking method and device capable of carrying out real-time correction on the basis of model probability in WSN (Wireless Sensor Network)
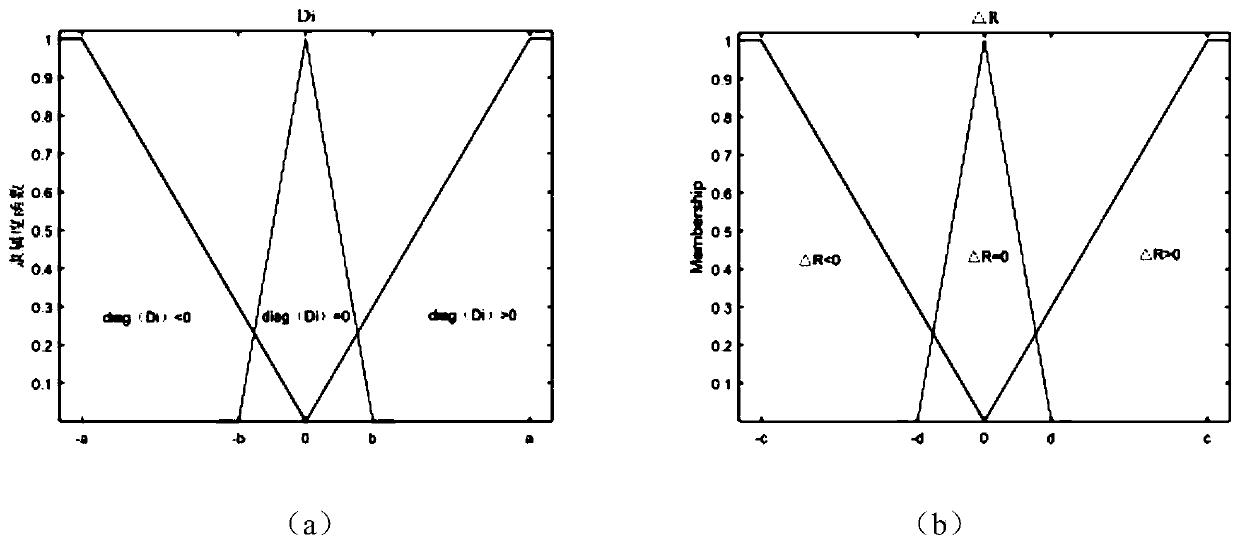
ActiveCN110426671AGood effectImprove tracking accuracyNetwork topologiesPosition fixationAlgorithmReceived signal strength indication
The invention discloses an IMM (Interacting Multiple Model) target tracking method and device capable of carrying out real-time correction on the basis of a model probability in a WSN (Wireless SensorNetwork). The method comprises the following steps that: firstly, collecting RSSI (Received Signal Strength Indication) in a monitoring area to establish a radio fingerprint database, and utilizing asupport vector regression algorithm to train to obtain an observation model; then, importing a fuzzy neural network, and adaptively regulating and measuring an error covariance matrix in a model output stage; and finally, according to a ratio of model probabilities between continuous time points in an IMM submodel, correcting a Markov transition probability. By the implementation of the invention, the algorithm has good performance on the aspects of instantaneity, tracking accuracy and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
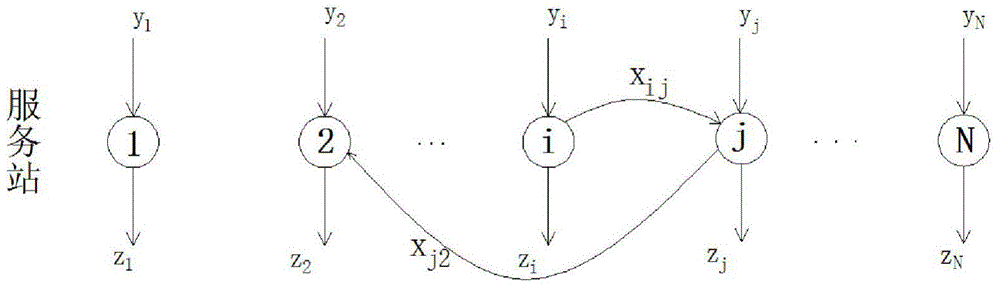
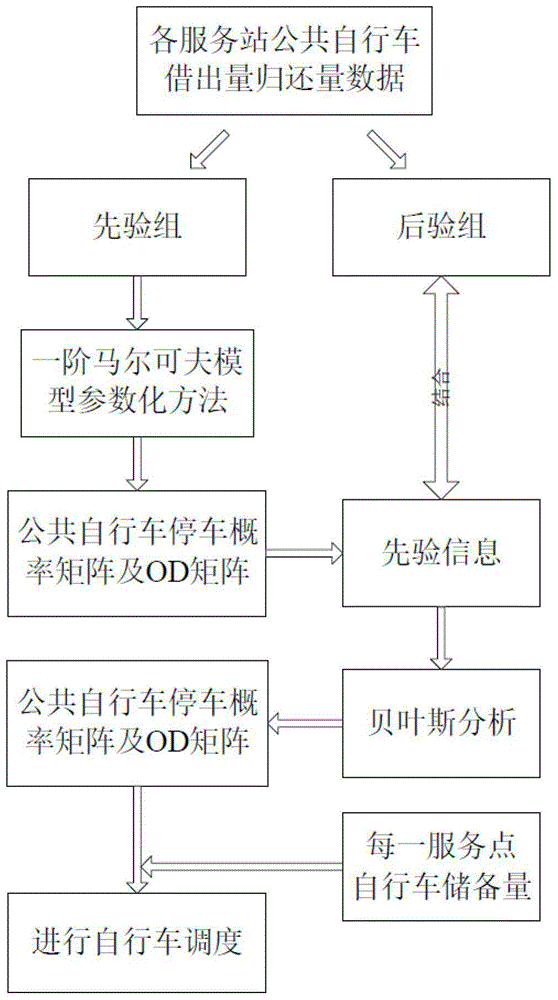
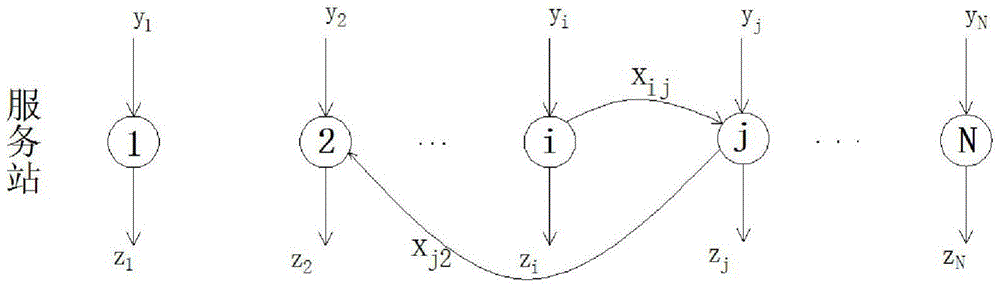
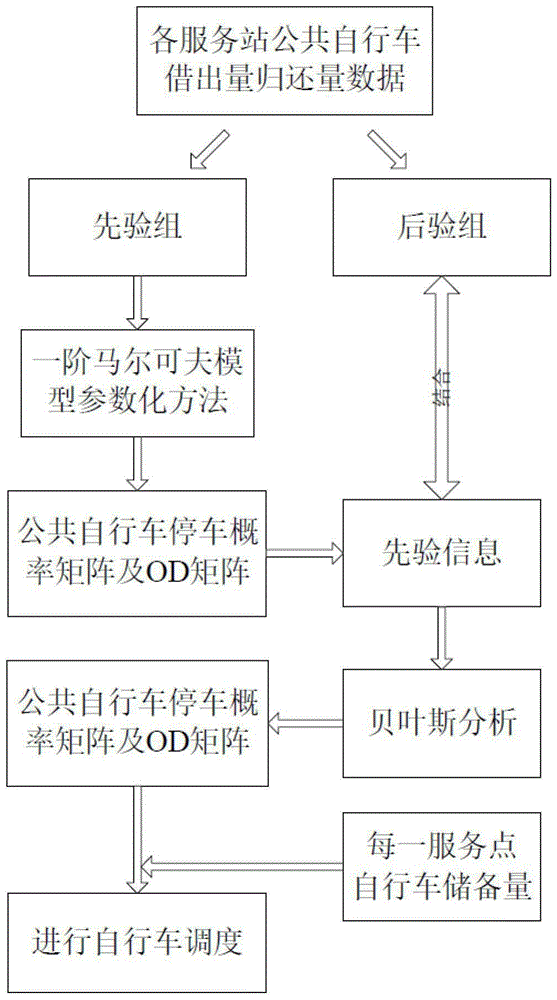
Public bicycle system regulation and control method based on Markov model
InactiveCN104916124AReduce acquisition timeReduce collection costsRoad vehicles traffic controlSpecial data processing applicationsAlgorithmTransition probability matrix
The invention discloses a public bicycle system regulation and control method based on a Markov model. The public bicycle system regulation and control method comprises the steps of: (1) acquiring bicycle lending and returning statistics through a public bicycle information center; (2) dividing the acquired bicycle lending and returning statistics into a prior group and a posterior group, and calculating the statistics of the prior group by using a first-order Markov model parameterize method to obtain prior information used for subsequent inference; (3) combining the prior information with data of the posterior group, and utilizing Bayesian reasoning combined with the Markov model to obtain a Markov transition probability matrix; (4) inferring a public bicycle system OD matrix on the basis of the Markov transition probability matrix; (5) and conducting public bicycle system scheduling by using the OD matrix. The public bicycle system regulation and control method based on the Markov model utilizes the OD matrix statistical inference for conducting public bicycle system scheduling in real time, can obtain data easily, avoids solving the unclosed problem, effectively utilizes the prior information and improves accuracy of the obtained data.
Owner:SOUTHEAST UNIV
Slot-cutting evidence obtaining method based on LBP and extended Markov features
InactiveCN107977964AEasy to detectImprove detection rateImage enhancementImage analysisMain diagonalFeature vector
The invention belongs to the technical field of image processing and digital image evidence obtaining, proposes an algorithm for more effective detection of slot-cutting tampering, and solves an insensitive problem when the conventional Markov features are used for detecting the slot-cutting tampering proportion. A slot-cutting evidence obtaining method based on LBP and extended Markov features comprises the steps: respectively calculating Markov transition probability matrixes with the differential two-dimensional JPEG matrix steps q=1 and q=4 in four directions in the LBP domain: horizontaldirection, vertical direction, leading diagonal direction and secondary diagonal direction; carrying out the fusion of the features obtained under the condition q is equal to one and the features obtained under the condition q is equal to 4; extracting 648(324*2)-dimensional features, and carrying out the mathematic modeling of the 648-dimensional features in the obtained transition probability matrixes; taking the model as a feature vector, and carrying out the training and detection of the feature vector through an SVM (support vector machine), so as to detect whether the slot-cutting tampering of the image is carried out or not. The method is mainly used in an image processing occasion.
Owner:TIANJIN UNIV
Method and system for statistical filters and design of statistical filters
InactiveUS7536282B1Less dataLess signalAmplifier modifications to reduce noise influenceDigital technique networkFrequency spectrumStochastic matrix
Systems and methods for the design or implementation of statistical filters for use in the spectral shaping of transmissions are disclosed. A desired power spectrum may be mapped to find pole locations that approximate the desired spectrum. These pole locations may then be mapped to the edge or inside of an equilateral polygon lying inside a unit circle, the equilateral polygon having the same number of sides as the order of the statistical filter desired and one vertex mapped to unity, to yield a set of eigenvalues. These eigenvalues may be the eigenvalues of a stochastic matrix the elements of which may be the Markov transition probabilities for use in a statistical filter designed to achieve the desired power spectrum. Use of a statistical filter employing these Markov transition values may be utilized to shape UWB or other signals to achieve the desired power spectrum.
Owner:ALEREON
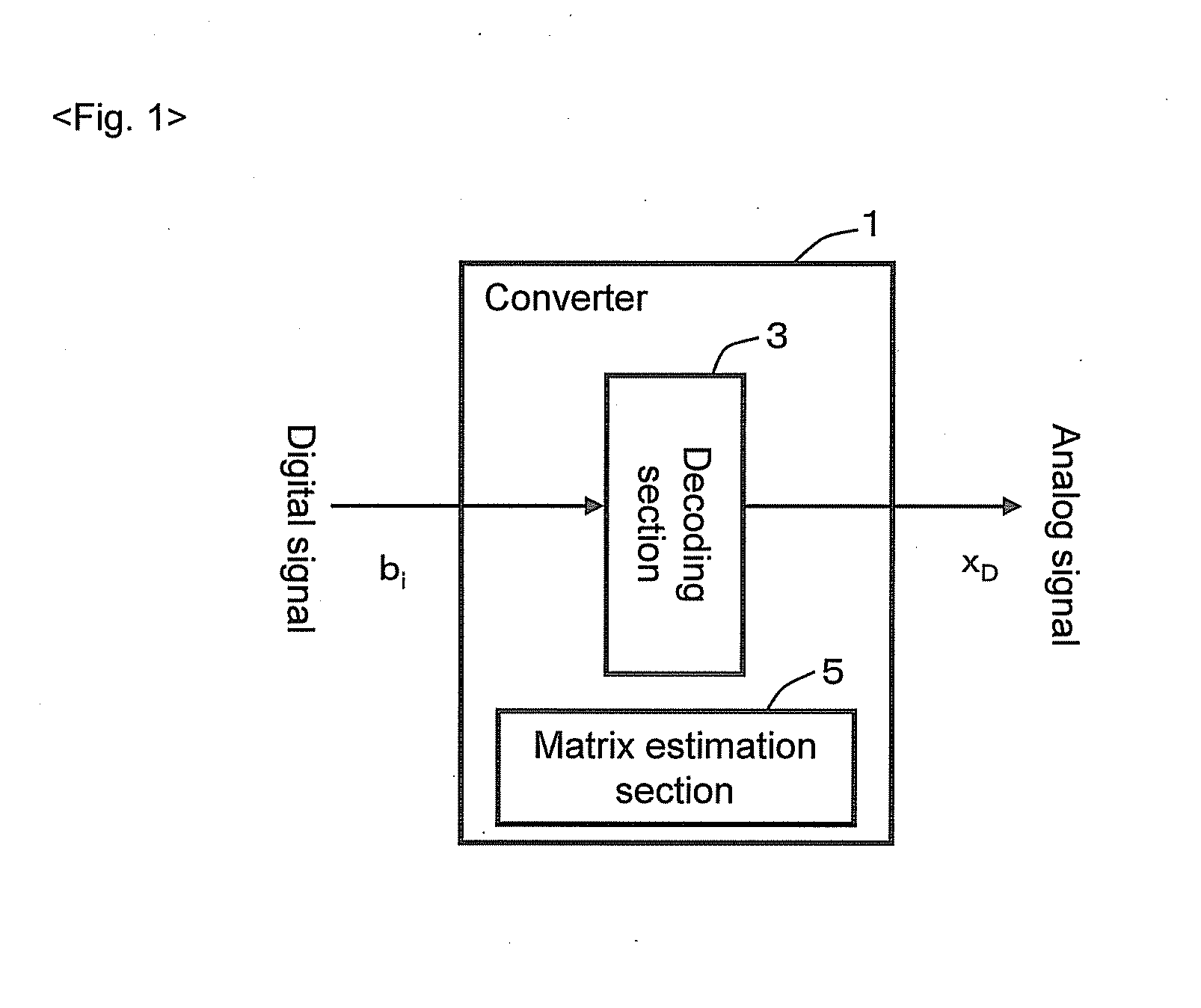
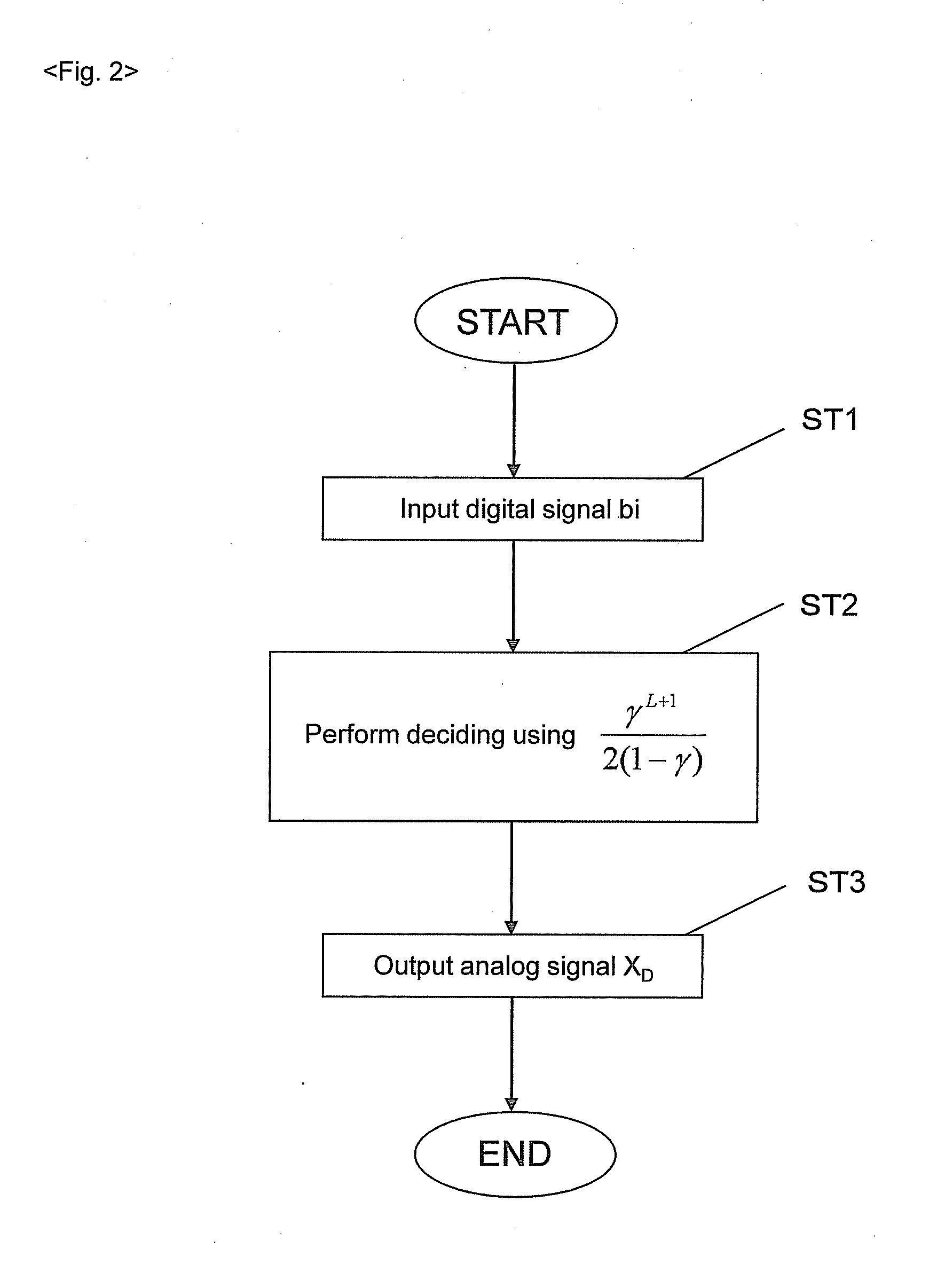
Converter, conversion method, program, and recording medium
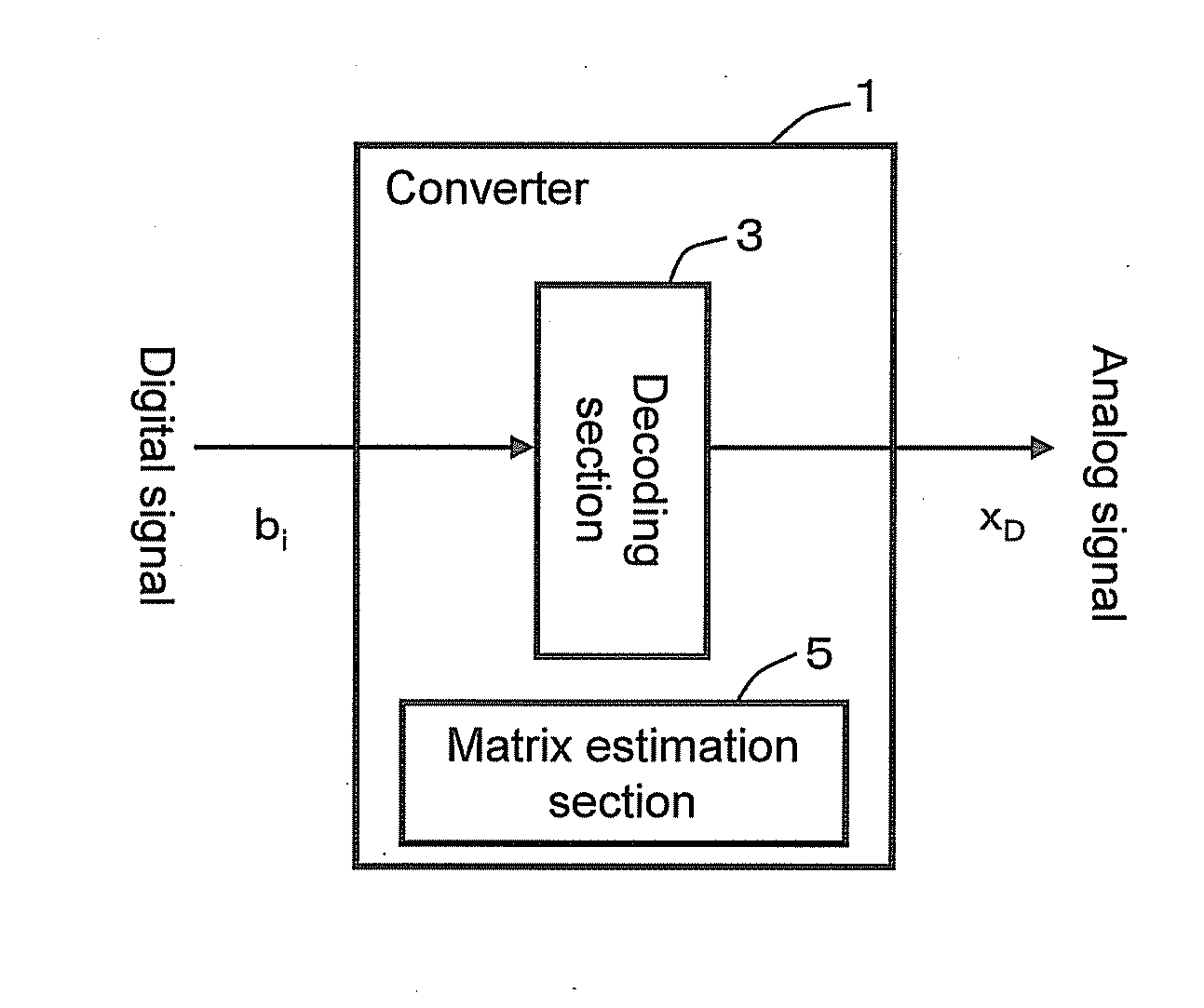
Provided is a highly accurate converter and the like that makes up for the instability of circuit elements, by focusing on a relationship between the Markov chain and β conversion. A converter 1 that determines the decoded value of a sample value x based on L-bit number bi (i=1, . . . , L) includes a decoding section 3 to determine the decoded value xD for γ=1 / β (where 1<β<2) using equation (eq1). Further, the converter 1 also includes a matrix estimation section 5 to determine the Markov transition matrix based on bi. Unlike a conventional method that pays attention to the lower limit of an interval, the decoding section 3 using equation (eq1) pays attention to the center of the interval, and this point is a significant difference.xD=∑i=1Lbiγi+γL+12(1-γ).(eq1)
Owner:JAPAN SCI & TECH CORP +1
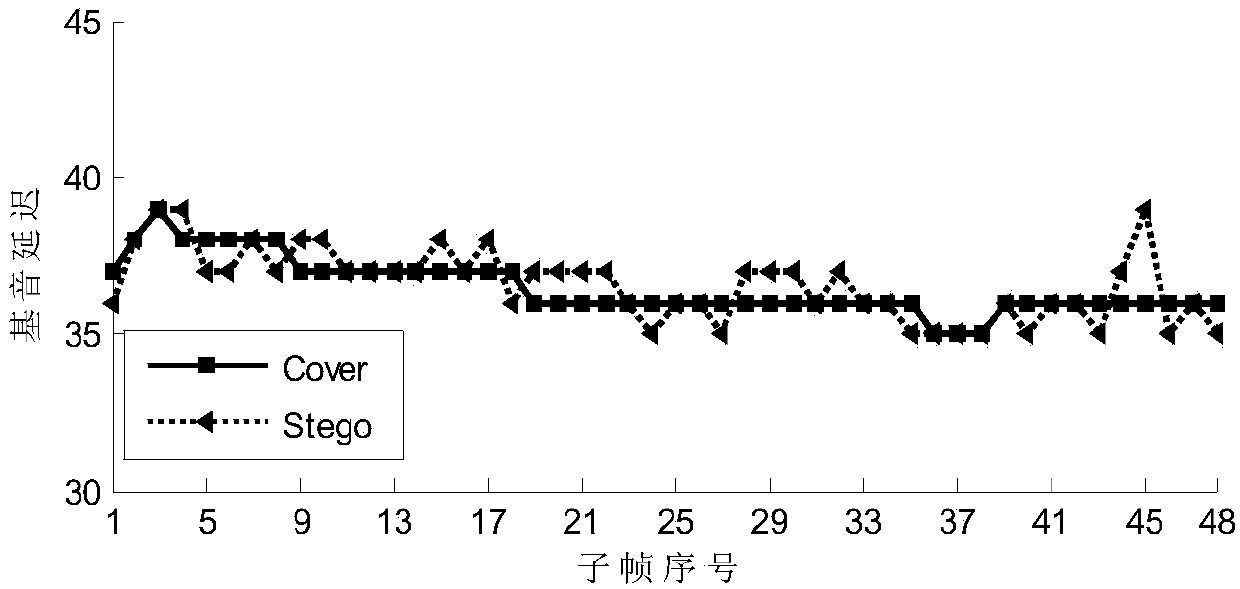
AMR fundamental tone delay steganalysis method based on difference value Markov transition probability characteristic in fundamental tone delay sub-frame group
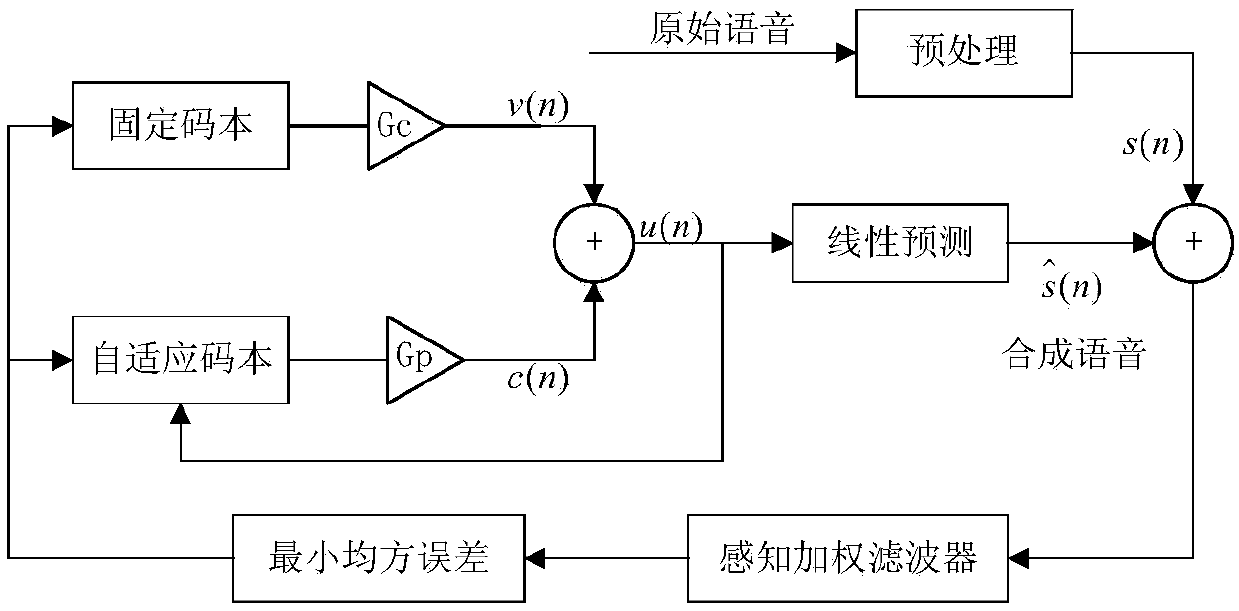
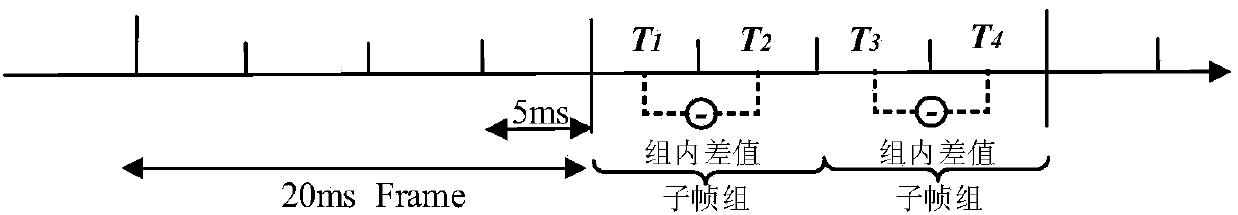
The invention discloses an AMR fundamental tone delay steganalysis method based on a difference value Markov transition probability characteristic in a fundamental tone delay sub-frame group. For thetwo steganographic algorithms for modifying fundamental tone delay in speech coding, the method provides an AMR steganalysis characteristic based on a difference value Markov transition probability ina fundamental tone delay sub-frame group. The method perform classification prediction by using a support vector machine, and achieves a steganalysis method oriented to AMR fundamental tone delay. Compared with two conventional steganographic methods oriented to fundamental tone delay, the method of the invention can achieve a detection rate more than 95% in case of a relative embedding ratio of50%.
Owner:WUHAN UNIV
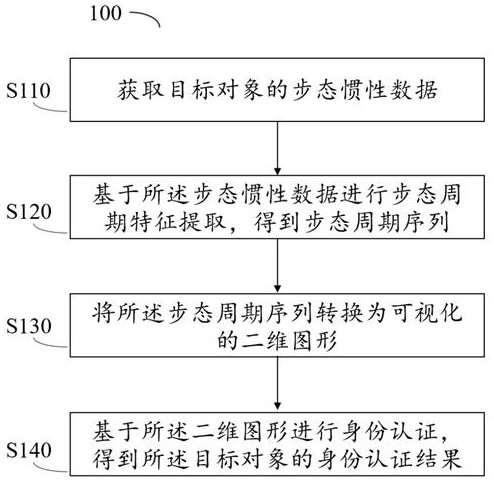
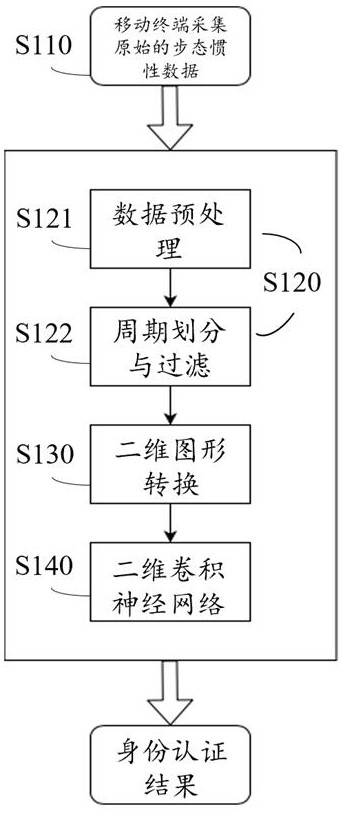
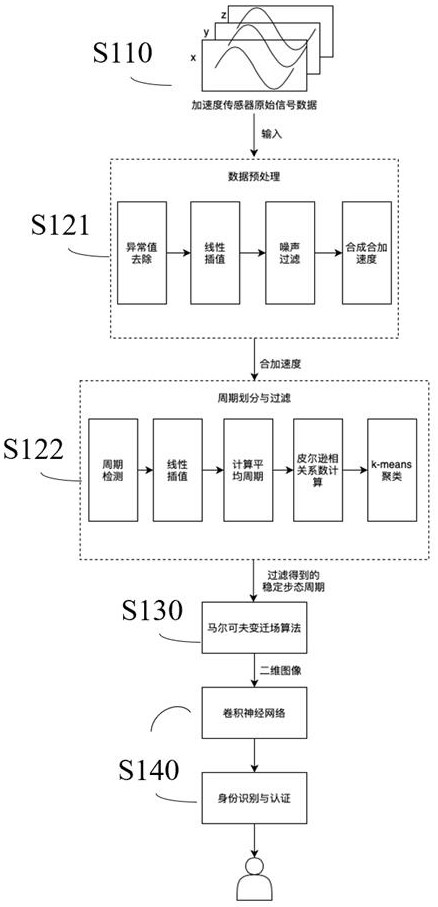
Identity authentication method and device based on gait behavior, equipment and storage medium
ActiveCN112560002AImprove accuracyImprove efficiencyCharacter and pattern recognitionDigital data authenticationGraphicsFeature extraction
The invention provides an identity authentication method and device based on gait behaviors, equipment and a storage medium. The method comprises the steps of acquiring gait inertia data of a target object; based on the gait inertia data, performing gait period feature extraction to obtain a gait period sequence; converting the gait period sequence into a visual two-dimensional graph, including: performing visualization processing on the gait period sequence to obtain a two-dimensional graph based on a recursive graph, a Markov transition field or a Gram angle field; and performing identity authentication based on the two-dimensional graph to obtain an identity authentication result of the target object. According to the method and the device, the stable gait period is obtained by performing feature extraction on the gait inertia data of the target object, the gait period sequence is formed, and then the gait period sequence is converted into the visual two-dimensional graph, so that the two-dimensional neural network can be effectively utilized, and the accuracy and efficiency of identity authentication are improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Target advanced predicting and tracing method
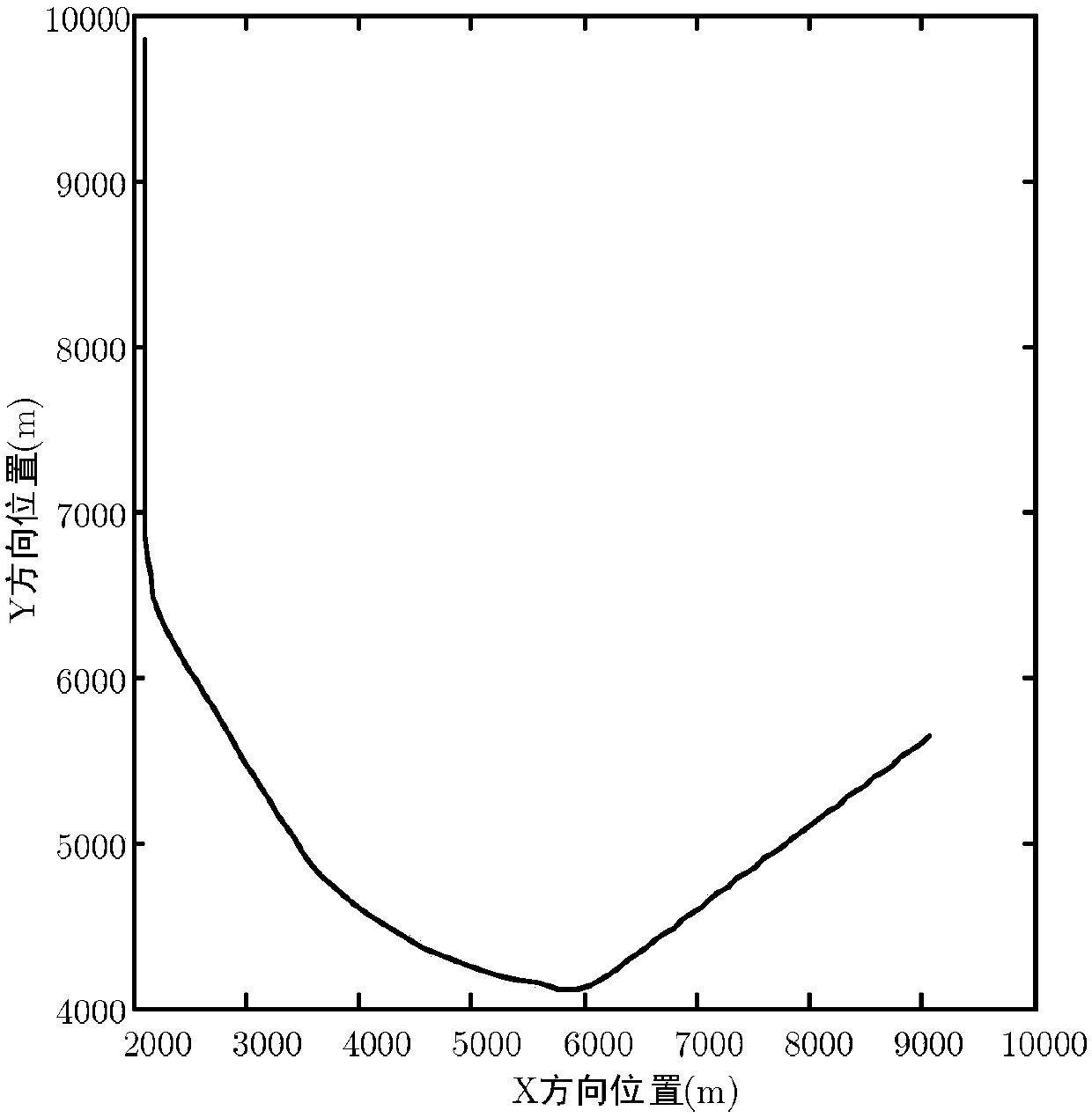
The invention discloses a target advanced predicting and tracing method. A motion state of a target can be predicted in advance under the condition of low observation noise influence. The target advanced predicting and tracing method comprises the steps of firstly building a motion model for a moving target; then carrying out advanced prediction, that is, priori estimation, for the motion state ofthe target in the next moment by adopting a square root volume kalman filter method; building a Markov transition probability model by counting an error sequence between the priori estimation value and an observation value before the current moment; predicting a priori prediction error at the next moment by using the Markov transition probability model and correcting an advanced prediction valueat the next moment by using the error. The advanced predicting and tracing method can predict the motion state of the target in advance and can provide a target state prediction value in advance for atracing control system; and the control system can act in advance based on the advanced prediction value to overcome tracing lag and can keep continuous tracing for the target based on the advanced prediction value when the target is shielded.
Owner:WUHAN UNIV OF SCI & TECH
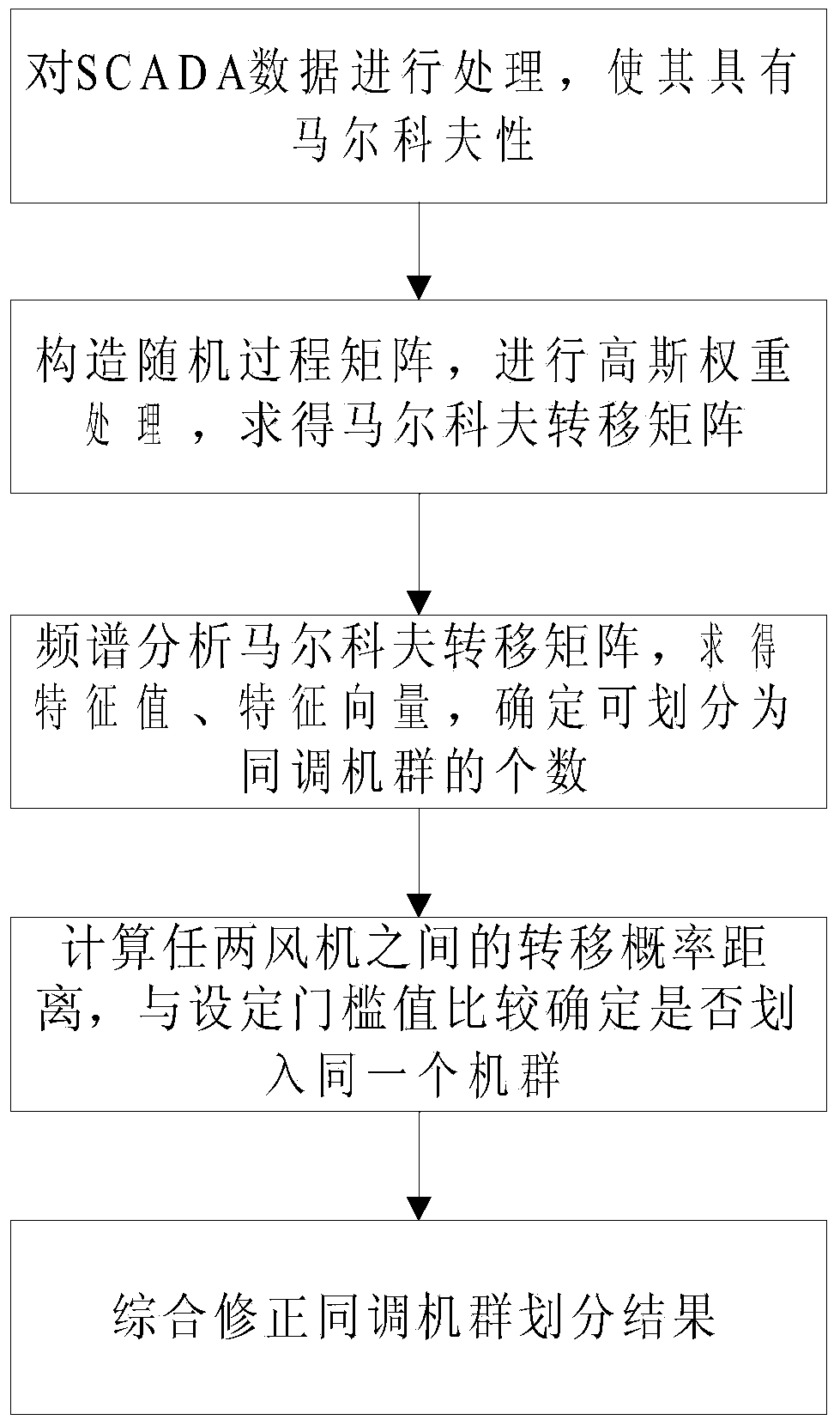
Markov chain based method for classifying coherent generator groups of wind power plant
InactiveCN104143013AReflect the real characteristicsGuaranteed uptimeSpecial data processing applicationsFrequency spectrumAlgorithm
The invention relates to a Markov chain method for classifying coherent generator groups of a wind power plant. The method comprises the steps as follows: active data and reactive data of wind turbine generators in the wind power plant are processed to enable the data to have the Markov property; a random process matrix is built, Gaussian weight processing is performed, and a Markov transition matrix is obtained; the Markov transition matrix is subjected to spectral analysis to solve a feature value, a left feature vector and a right feature vector, and the number of the classified coherent generator groups is determined; a transition probability distance between any two wind turbine generators is calculated and compared with a set threshold value to determine whether the two wind turbine generators are classified in the same generator group; and the classification result of the coherent generator groups is corrected comprehensively. The classification method utilizes actual physical data of the wind power plant, the real characteristics of the wind power plant can be reflected better, the foundation is established for completely and accurately analyzing the influence of scale type wind power plant grid connection on grid operation, and the method has positive influence on improvement of grid operation level.
Owner:STATE GRID CORP OF CHINA +1
MP3 audio steganalysis method and device
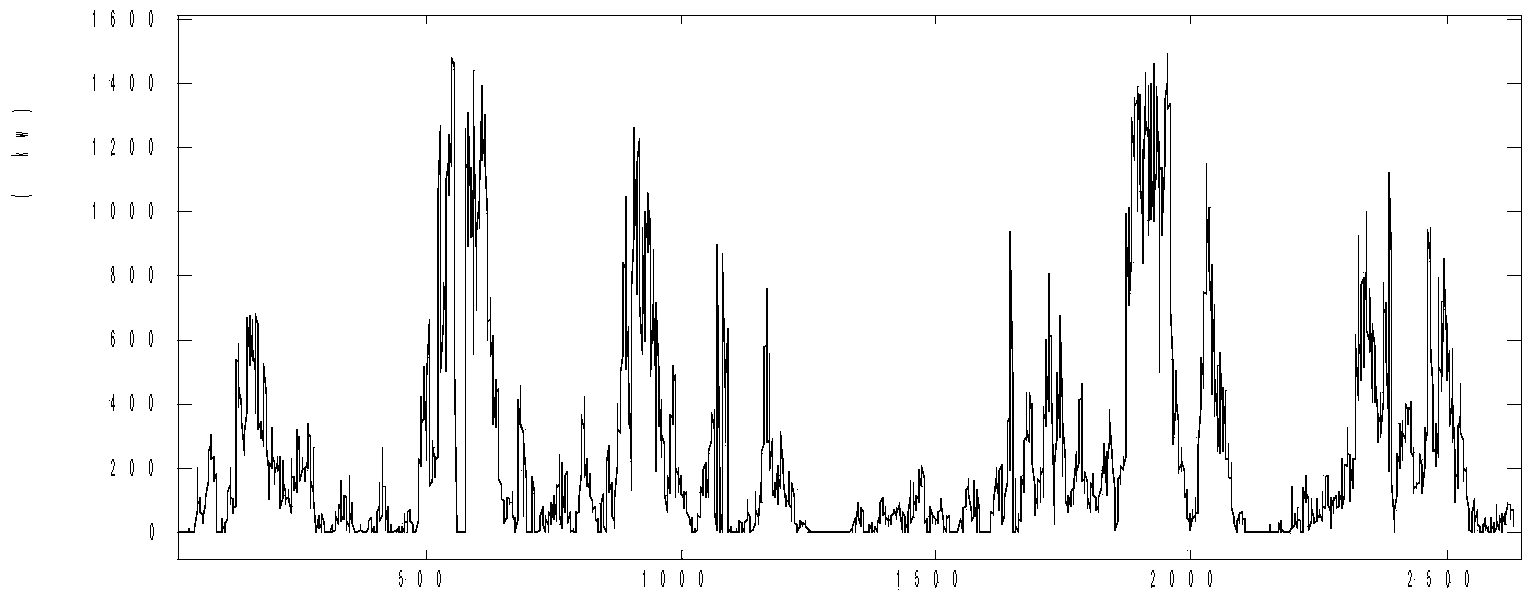
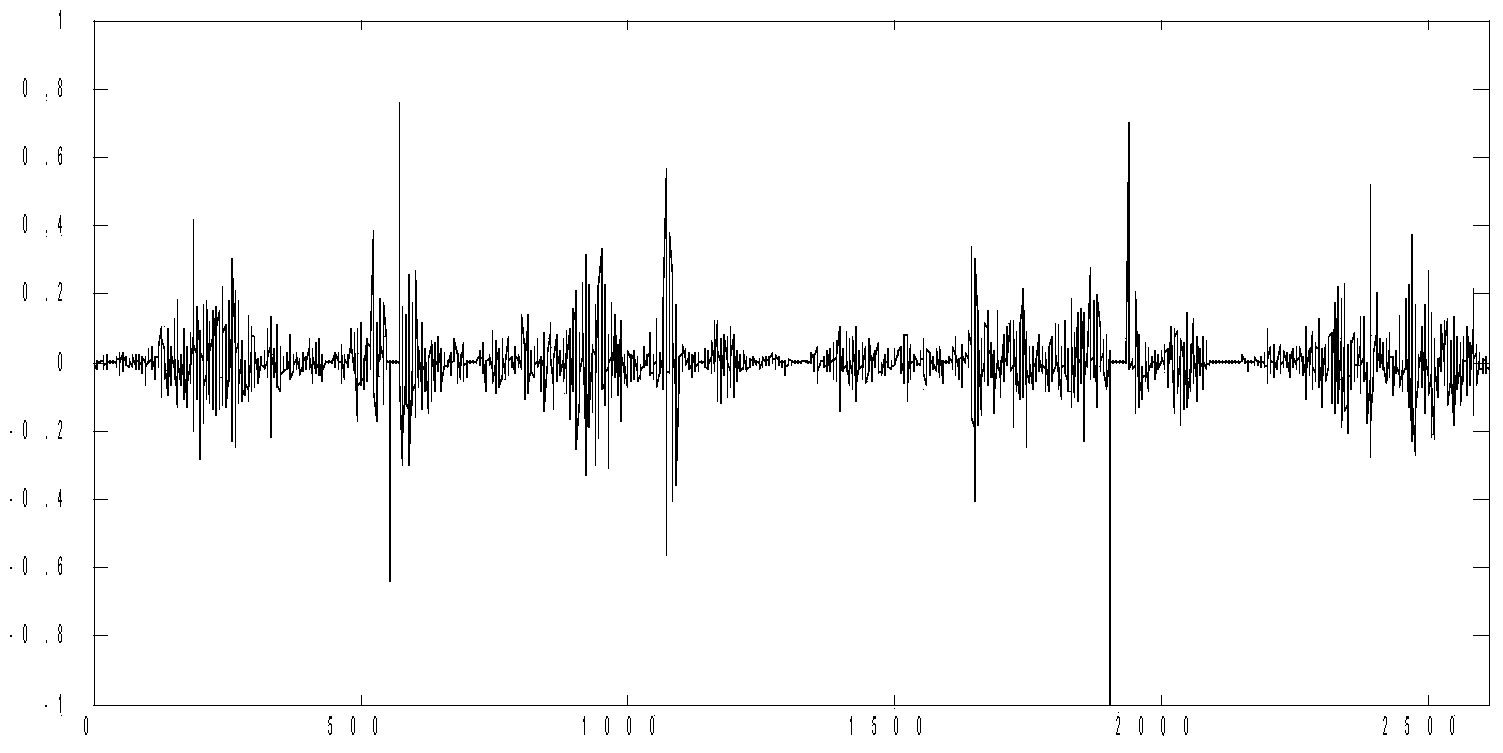
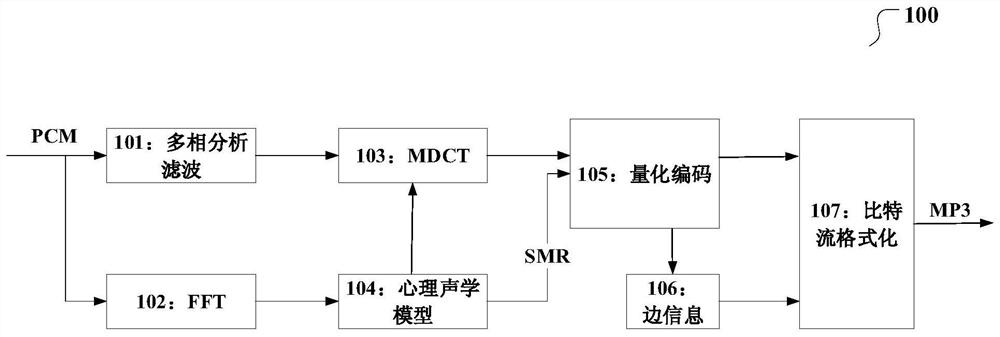
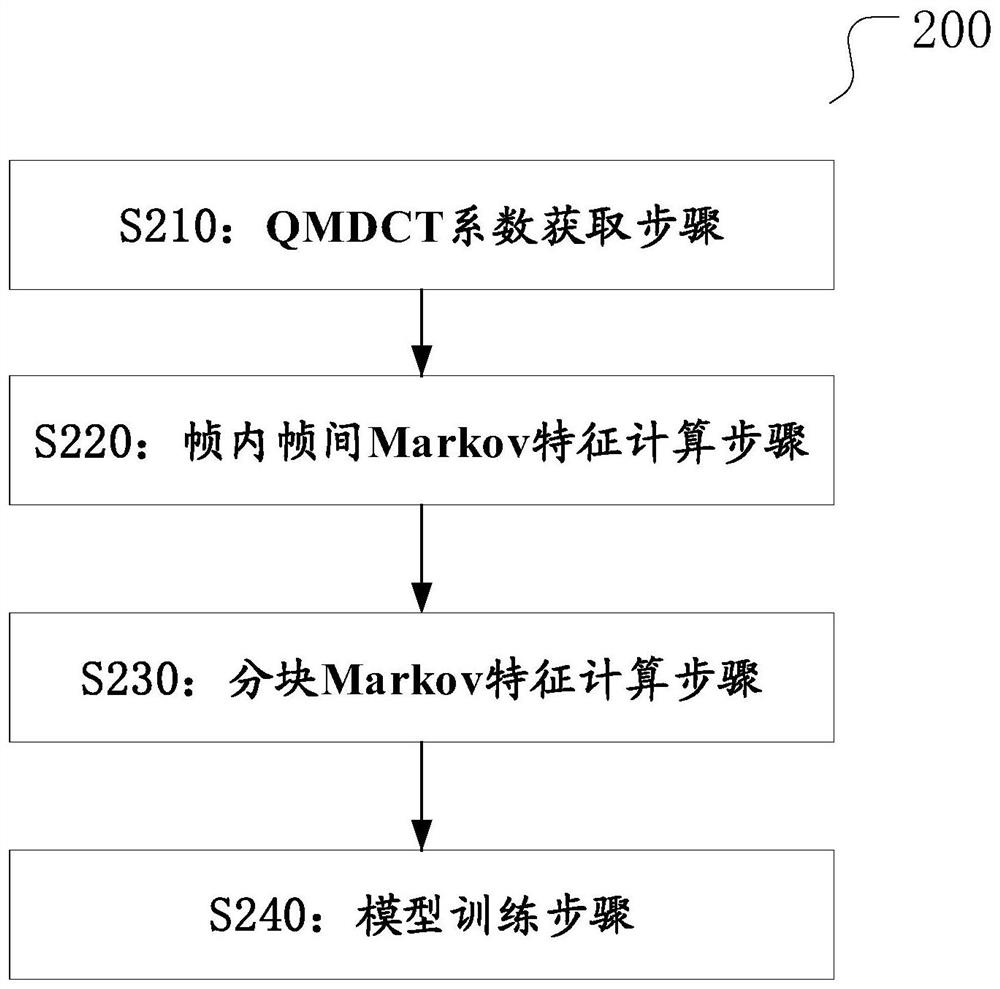
PendingCN114495955AImprove detection accuracyStrong generalizationSpeech analysisSteganalysisFeature vector
The invention relates to an MP3 audio steganalysis method and device, and the method comprises the steps: obtaining a QMDCT coefficient of an MP3 audio to be analyzed, and obtaining a QMDCT coefficient matrix, i.e., a matrix MQMDCT, and a corresponding QMDCT coefficient absolute value matrix, i.e., a matrix MAQMDCT after preprocessing; the Markov transition probability of the matrix MQMDCT and the Markov transition probability of the matrix MAQMDCT in the row and column directions are calculated, and intra-frame and inter-frame Markov features are obtained; respectively carrying out downsampling on the matrix MQMDCT and the matrix MAQMDCT, respectively calculating the Markov transition probability of each downsampling matrix in the row and column directions, and obtaining a block mean Markov feature; and using the truncation threshold T to obtain a feature vector F, and training through an SVM classifier to obtain an MP3 audio steganalysis detection model.
Owner:CHINA TELECOM CLOUD TECH CO LTD
Regulation method of public bicycle system based on Markov model
InactiveCN104916124BReduce acquisition timeReduce collection costsRoad vehicles traffic controlSpecial data processing applicationsPrior informationTransition probability matrix
Owner:SOUTHEAST UNIV
Data enhancement method for vibration signals of converter transformer
ActiveCN113537247ALow resolution accuracyCharacter and pattern recognitionNeural architecturesFeature extractionData set
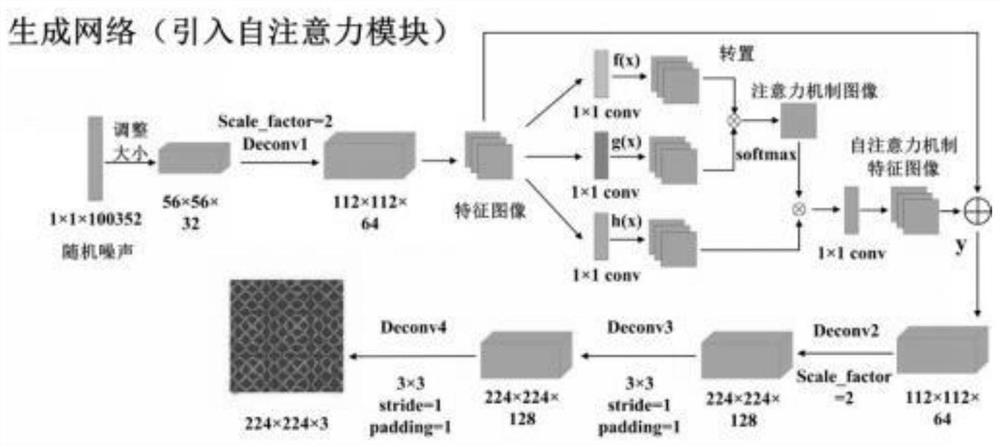
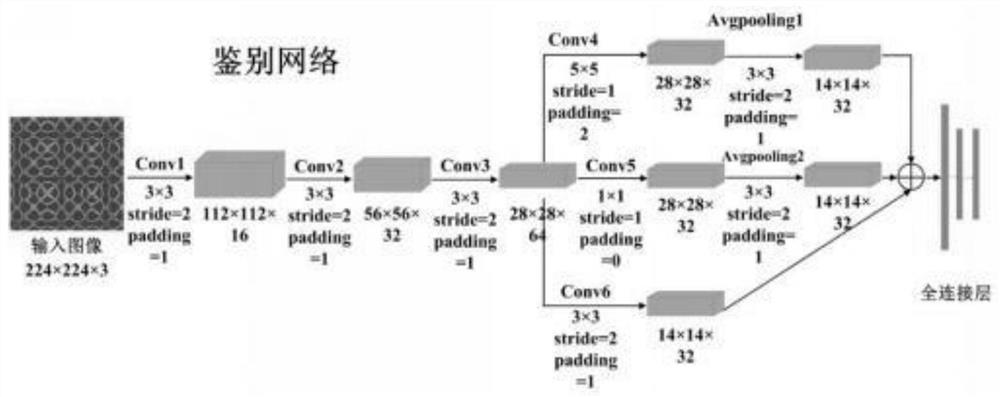
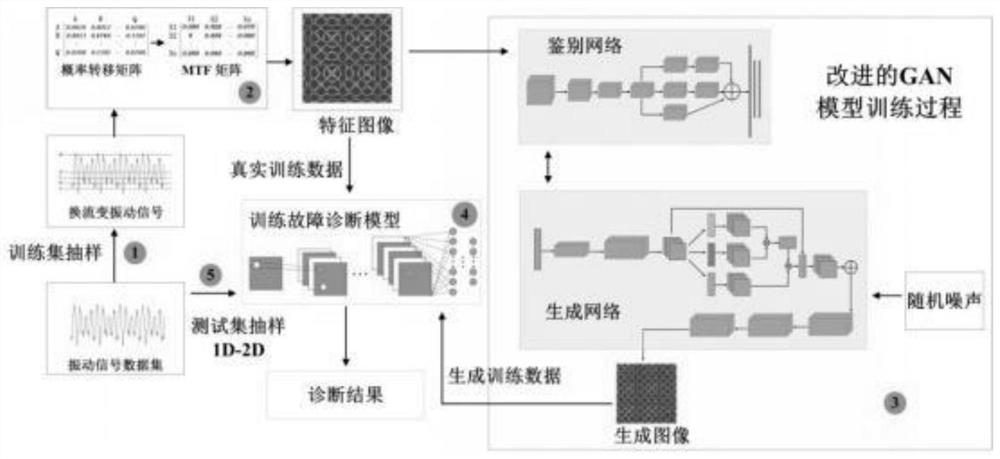
The invention relates to a data enhancement method for vibration signals of a converter transformer, and belongs to the field of electric power. The method comprises the following steps: firstly, a Markov transition field (MTF) matrix of a vibration signal sequence is calculated, and the matrix is converted into a two-dimensional feature map to retain the correlation of a time sequence; and on this basis, a self-attention module is introduced to optimize a generative network, which can accept information between long-distance pixel points and realize a global receptive field between the pixel points. Meanwhile, the identification network adopts convolution kernels of different sizes for parallel feature extraction so as to increase the range of a receptive field and obtain deeper features. According to the model, a two-dimensional image data set is established according to actually measured converter station vibration signals, effective training data can be further generated, and the problem that the converter transformer state recognition accuracy is low due to the fact that the number of data sets is unbalanced is solved.
Owner:CHONGQING UNIV
Weak and small target detection method based on Gaussian Markov random field motion direction estimation
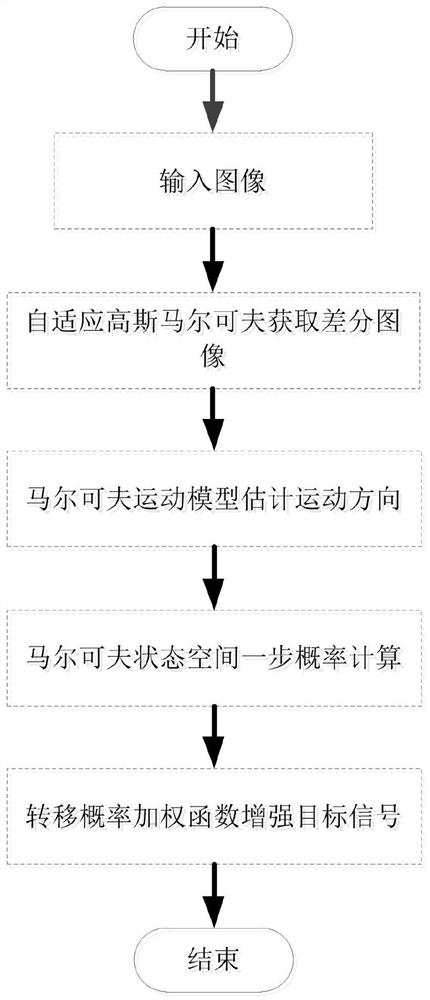
ActiveCN114155425AEffective filteringGood difference imageCharacter and pattern recognitionHigh level techniquesTarget signalGaussian markov random fields
The invention discloses a weak and small target detection method based on Gaussian Markov random field motion direction estimation, which comprises the following steps of: firstly, establishing a new self-adaptive Gaussian weighted Markov random field filtering model to obtain a difference image of an image, and then, constructing a target Markov transition probability model according to an established motion model; in this way, the motion direction of the target is estimated, and the target signal is enhanced in a transition probability weighting mode along the motion direction. Compared with similar algorithms, the algorithm has good advancement, and a better detection effect is obtained.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
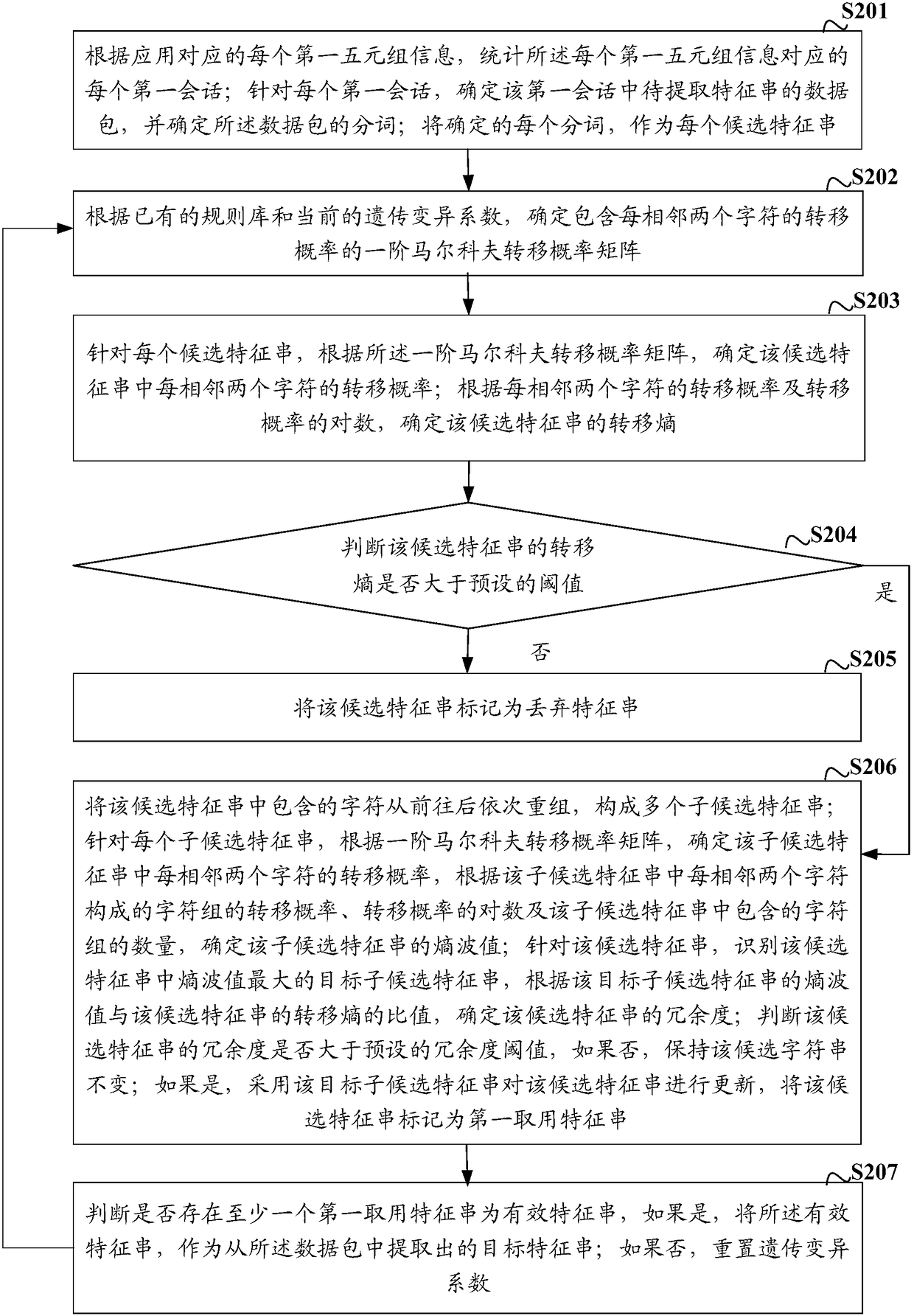
A method, device, network equipment and storage medium for extracting feature strings
ActiveCN108234347BRealize automatic extractionNatural language data processingData switching networksData packAlgorithm
The invention discloses a method, device, network equipment and storage medium for extracting a feature string, including: for each candidate feature string, according to the first-order Markov transition probability matrix, determine every two adjacent characters in the candidate feature string transition probability; according to the transition probability of every two adjacent characters and the logarithm of the transition probability, the transition entropy of the candidate feature string is determined; the candidate feature string whose transfer entropy is greater than the preset threshold is marked as the first feature string to be used , using the effective first feature string as the extracted target feature string. In the embodiment of the present invention, according to the first-order Markov transition probability matrix, the transition entropy of the candidate feature string of the data packet can be determined, and the candidate feature string whose transfer entropy meets the requirements is marked as the first access feature string, and the effective The first feature string is used as the extracted target feature string. The method for extracting a feature string provided by the embodiment of the present invention does not require manual intervention, and can completely realize the automatic extraction of the feature string.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com