Method and system for detecting illegal data implantation internal attack in smart power grid
An internal attack and data injection technology, applied in transmission systems, information technology support systems, electrical components, etc., can solve the lack of research and solutions for smart grid illegal data injection internal attack detection, analysis, and inability to apply smart grid physics- information system issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
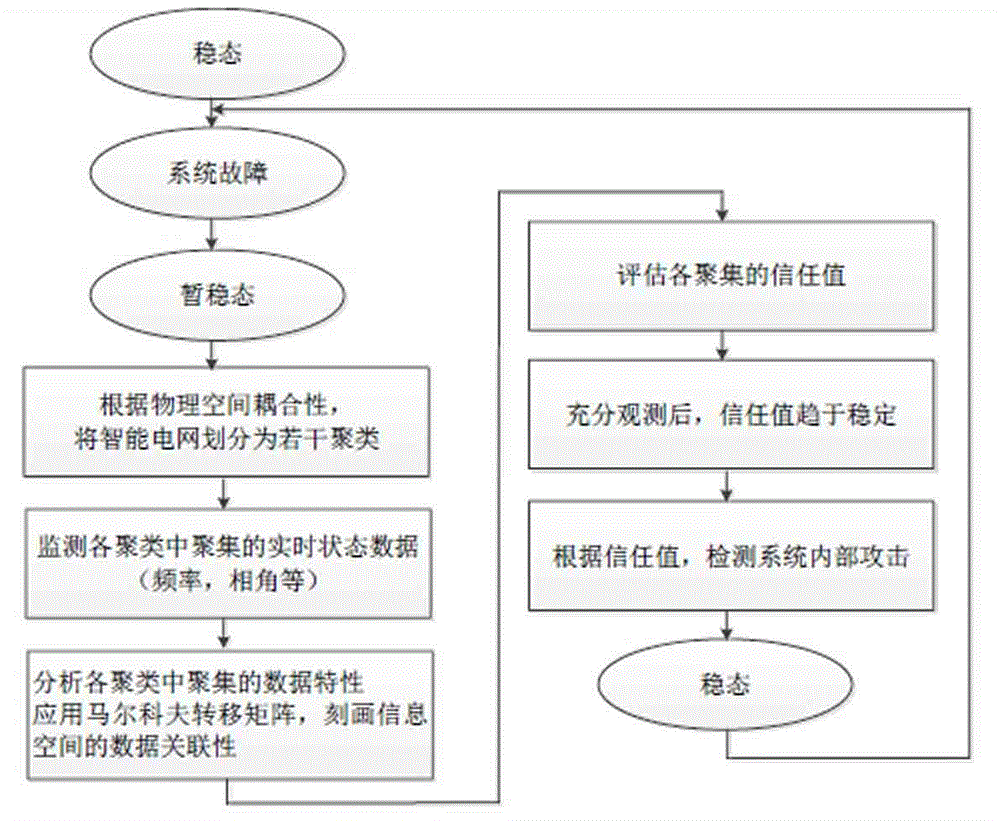
[0042] The present invention is described in further detail below in conjunction with the accompanying drawings.
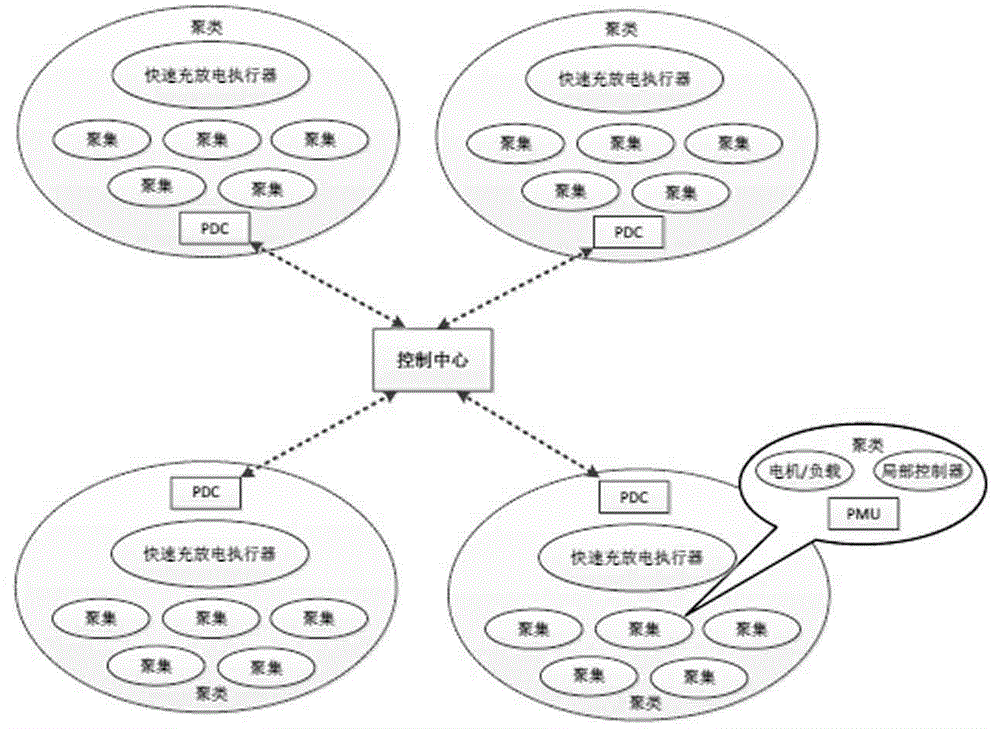
[0043] Such as figure 1 As shown, the overall architecture of the present invention: the inner and outer layer double-layer two-way communication architecture, the inner layer architecture includes several aggregations of physical coupling belonging to the same cluster, and the aggregations are connected through multi-hop network links connected to the source node and the destination node. Carry out data communication, and finally through PDC (Phase Angle Data Controller): aggregate all data in the cluster; the outer layer connects the data aggregation nodes PDC of each inner layer to form a local area network and communicate with each other to realize different Data exchange between clusters. Its specific components: aggregation: including generator / load, PMU (synchronous phase angle measurement unit), local controller; clustering: according to the physical coup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com