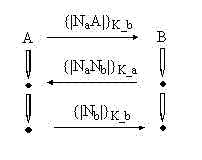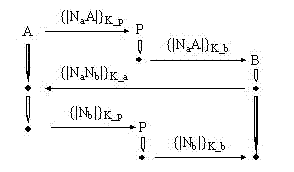Radio-frequency-fingerprint-based challenge-response authentication protocol method
A radio frequency fingerprint and authentication protocol technology, applied in user identity/authority verification, security devices, electrical components, etc., can solve problems such as attacks, and achieve the effect of solving the problem of key leakage detection and disclosure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
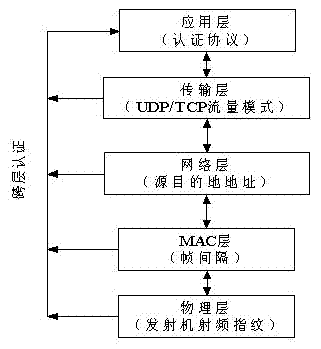
[0041] The protocol method of the present invention is divided into two stages of initialization and operation, and the structure and operation process of the protocol can be found in Figure 4 , 5 . This embodiment is a verification experiment of the method of the present invention. The challenger uses IEEE 802.11b / g wireless transmission equipment, and the PLCP (Pysical Layer Convergence Procedure) preamble of the transmitted radio frequency signal is spread by 1Mbit / s with 11chips Barker code (10110111000) The DBPSK modulation method transmits the information to be transmitted, so the transmitted radio frequency signal preamble envelope has a periodicity with a basic period of 1usec and a DSSS (Direct Sequence Spread Spectrum) preamble of IEEE 802.11b.
[0042] During the initialization phase:
[0043]The responding party obtains the radio frequency signal sent by the challenger through the wireless medium, detects the radio frequency fingerprint RFF of the challenger, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com