Data transmission method and device based on key authentication
A data transmission method and key technology, which is applied in the field of data transmission methods and devices based on key verification, can solve problems such as leaking, increasing private keys, and easy leaking of private keys, so as to ensure security and reduce the probability of leaking Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
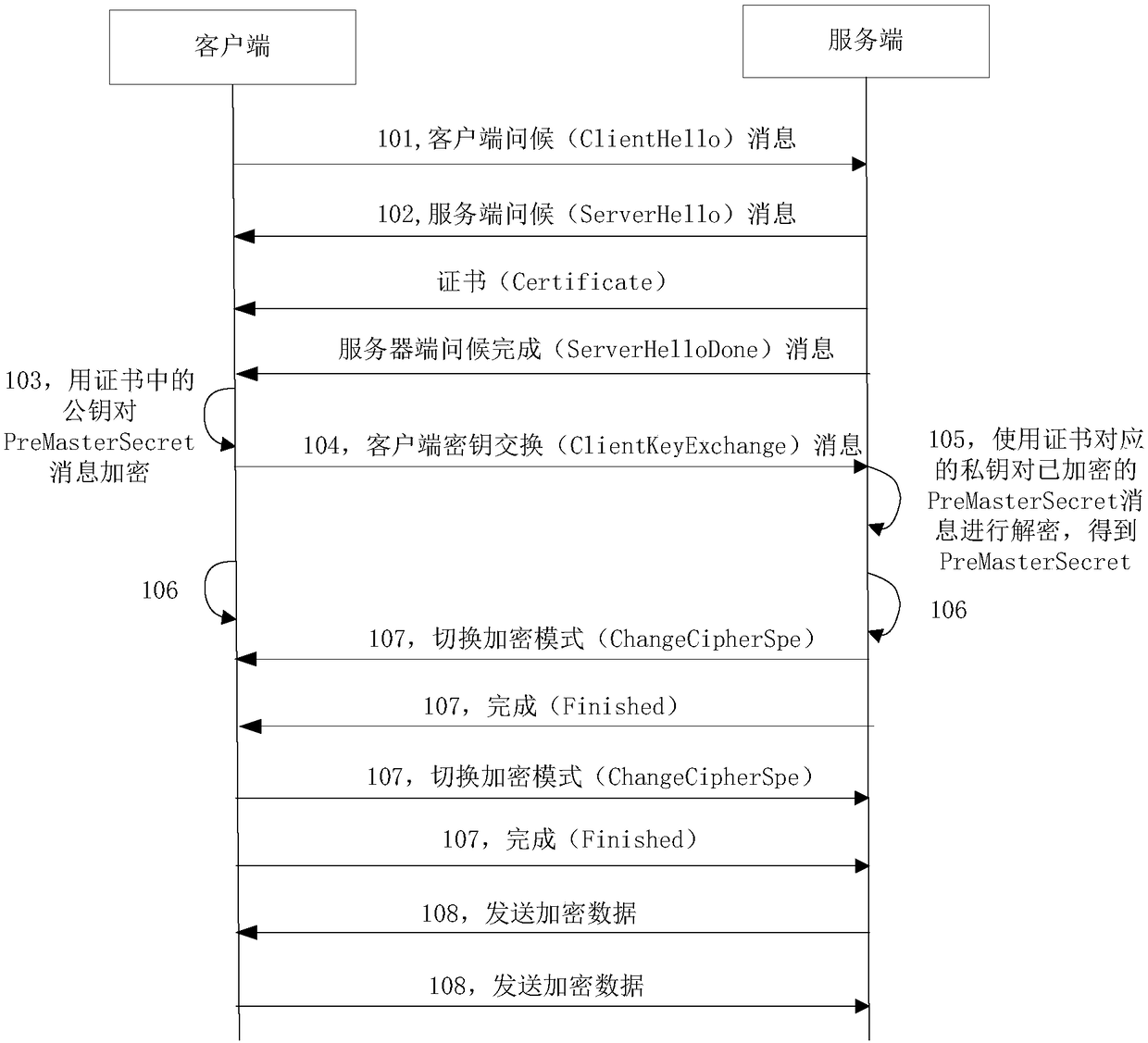
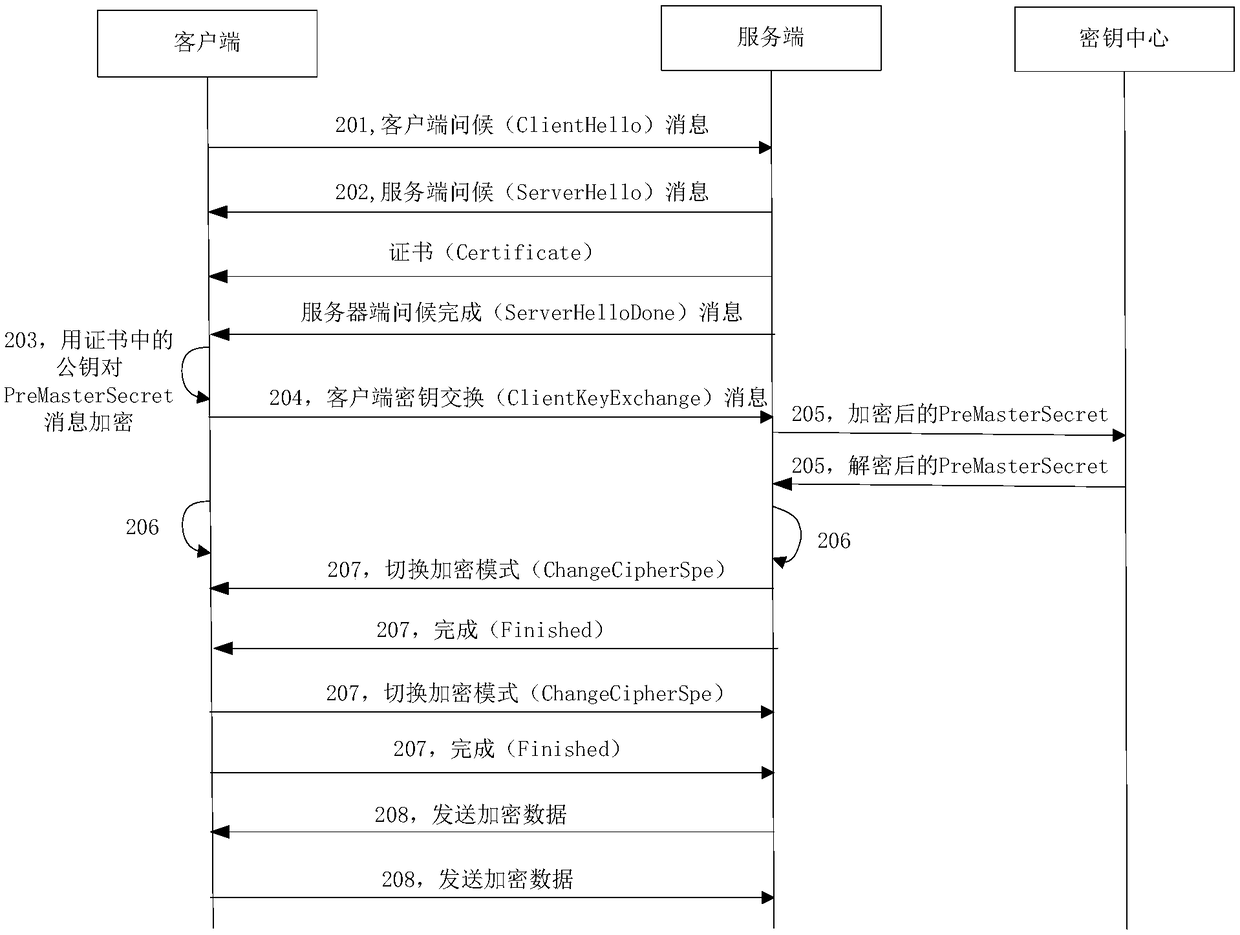
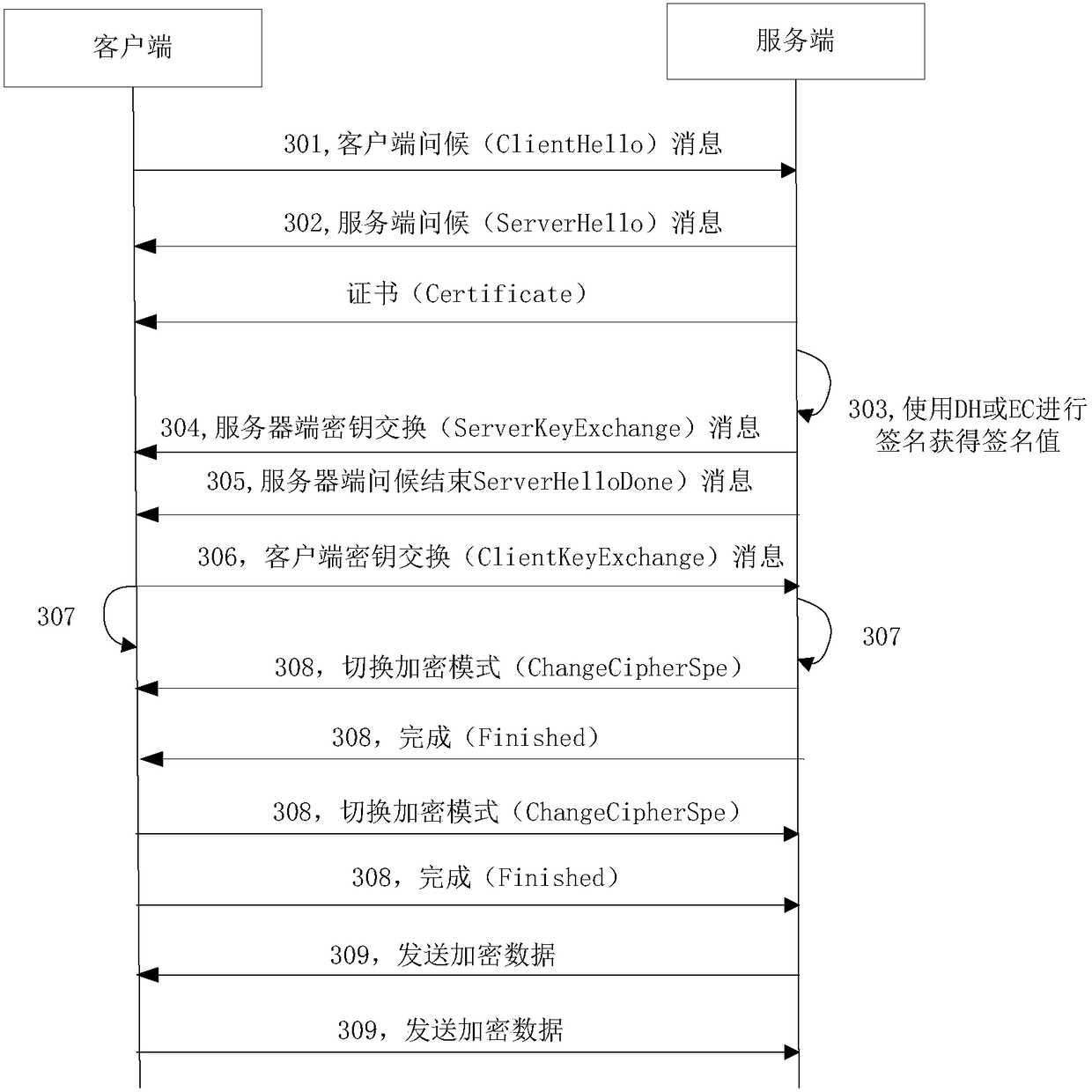
[0145] Such as Figure 8 As shown, the data transmission method based on key verification in this specific embodiment includes the following steps:
[0146] Step 801, the client generates a client shared key (key_share) and determines a signature algorithm (signature_algorithm). The client initiates a TLS1.3 handshake, and sends a client hello (ClientHello) message to the server, which includes the client's shared secret key and signature algorithm (signature_algorithm).
[0147]Step 802, the server receives the client hello (ClientHello) message, and parses the client shared key (key_share) and signature algorithm (signature_algorithm) from the message. The server generates a server-side shared secret key, sends a server-side greeting (ServerHello) message to the client, and carries the server-side shared secret key in this message.
[0148] Step 803, the client and the server respectively generate a handshake secret (Handshake Secret) and an application secret (Application...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com