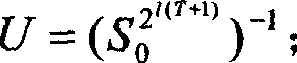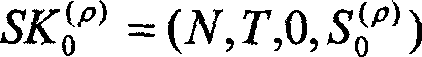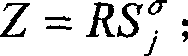Threshold digital signature method and system having forward security
A digital signature and forward security technology, applied in the field of information security, can solve the problems of long signature key and verification key, invalid signature, difficult calculation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0103] In our forward-secure threshold digital signature system, all participants including n signature servers (participants in the scheme) use P i It means that 1≤i≤n, they are all located on a broadcast network, and there is a secure channel between them for confidential communication. Such a channel can be implemented on the broadcast channel using encryption technology, and the encryption algorithm used should be the previous one. Toward a secure public key encryption algorithm. In addition, the system also includes a trusted distributor. The signature server and distributor can carry out broadcast communication or point-to-point encrypted communication. Any one of the signature servers can accept the signature request, initiate and organize a signature, and finally send the generated signature to the signature requester. Finally, we require the system to be synchronized, and they can send their information synchronously at a certain stage of the agreement.
[0104] The content...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com