Byzantine fault tolerance optimization method based on aggregate signature and storage medium
A Byzantine and memory pool technology, which is applied in the field of optimized Byzantine fault tolerance methods and storage media based on aggregated signatures.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
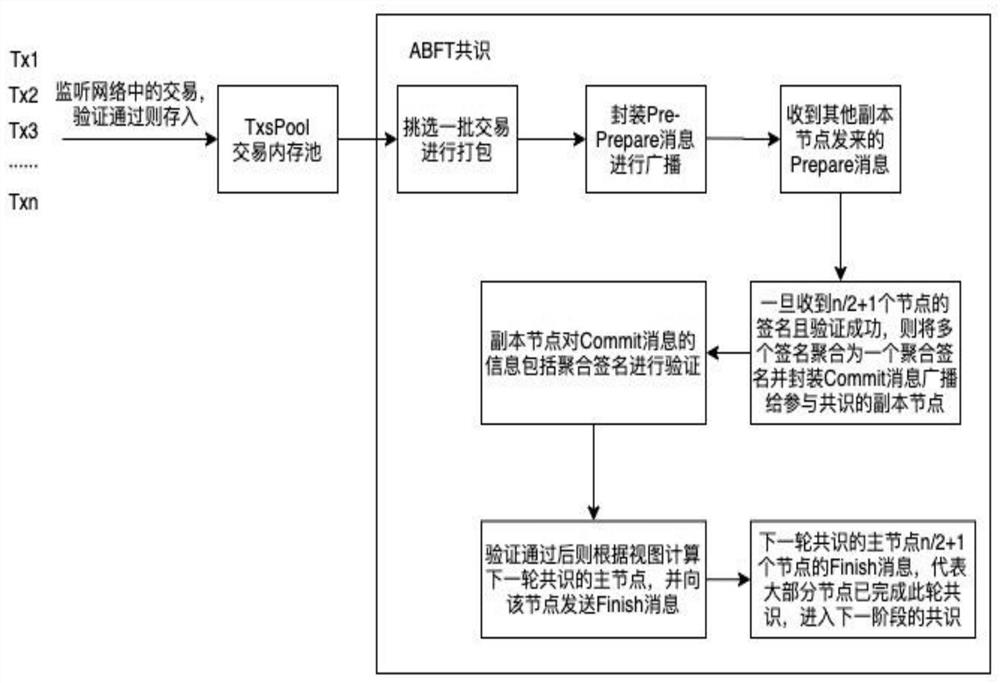
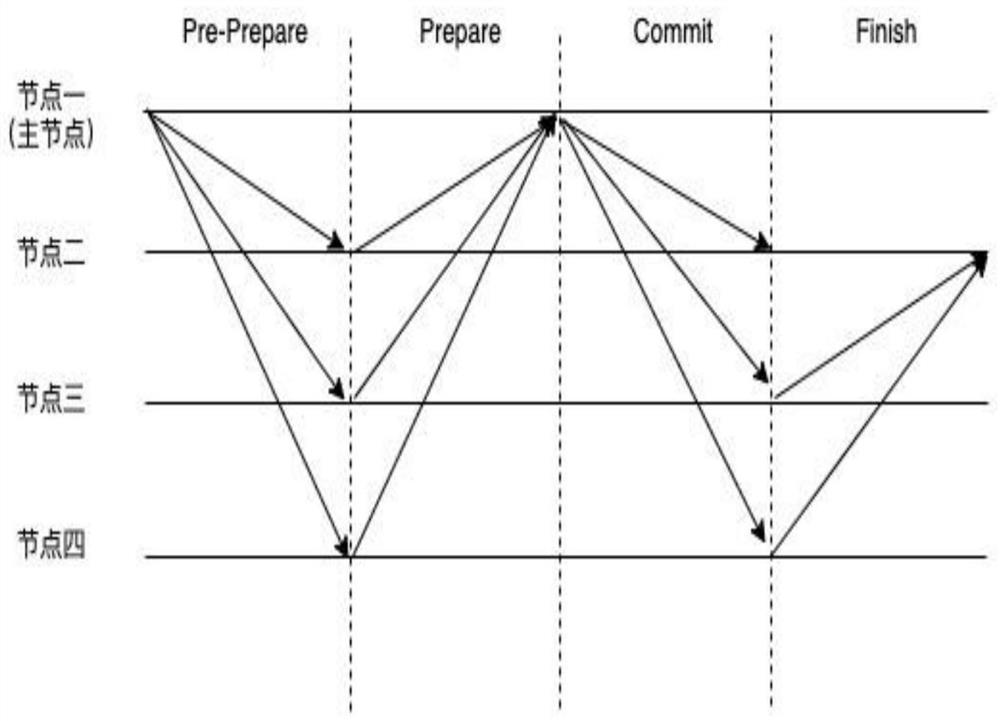
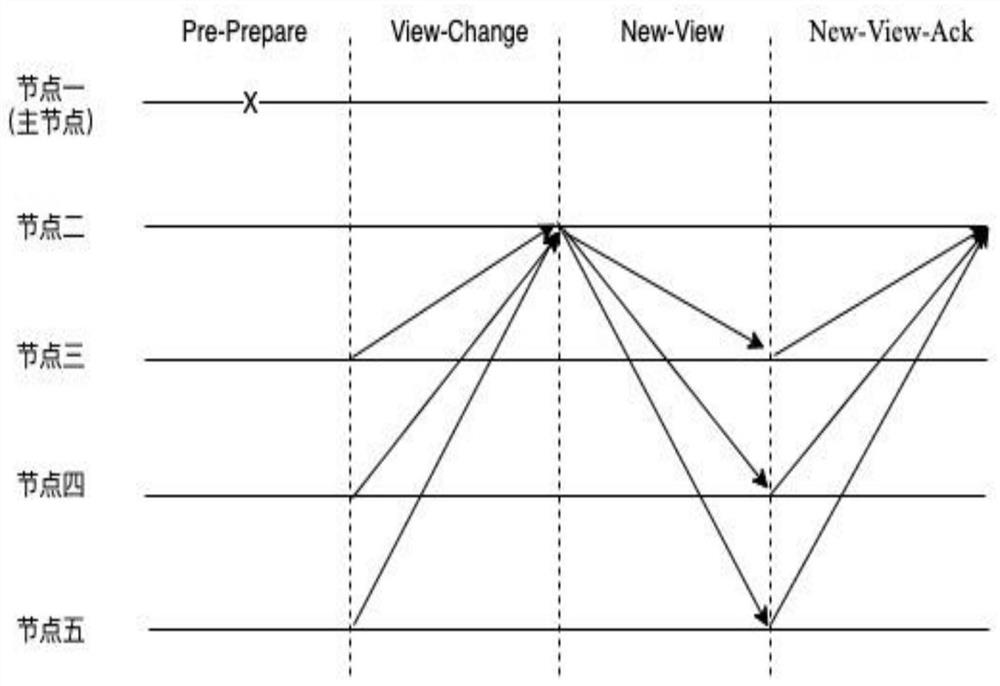
[0042] Such as figure 1 , 2 As shown in and 3, an optimized Byzantine fault tolerance method (Aggregate-Signature Byzantine Fault Tolerance, ABFT) based on aggregated signatures includes steps:
[0043] S1, Pre-Prepare stage: the master node collects transactions in the transaction memory pool, packs the transactions into blocks and broadcasts them to each replica node for consensus; in step S1, a message broadcast by the master node is a Pre-Prepare message, and the Pre- The Prepare message includes: h stands for the block height, v stands for the view number, d stands for the digest of the block, which is the hash value of the block, and the block is the content of the entire block, including the collected transactions and the signatures of all transactions.
[0044] S2. Prepare stage: After receiving the Pre-Prepare message sent by the master node, all replica nodes will send a Prepare message back to the master node; in step S2, all replica nodes will receive the Pre-Prep...
Embodiment 2
[0057] Such as figure 1 , 2 As shown in , 3 and 4, the BLS signature algorithm is an algorithm that can realize the collection of multiple signatures. It can aggregate all the signatures in the block into one, easy to realize m-n multi-signature, and can also avoid redundant communication between signers . By aggregating signatures, the master node can aggregate the signatures of other nodes, and the replica node can re-verify the merged signature once it receives the information of the master node containing the aggregated signature. Using the BLS signature algorithm can well solve the problem of too high communication complexity of the PBFT algorithm.
[0058] The BLS signature algorithm mainly relies on the function also known as bilinear maps (Bilinear maps), which requires a certain understanding of the pairing function. Here is a brief introduction, define the pairing function e(P,Q), P and Q are two points of a curve (or two different curves), the pairing function sa...
Embodiment 3
[0077] ABFT algorithm implementation scheme of optimized Byzantine fault tolerance method based on aggregate signature:
[0078] In order to verify the efficiency of the improved ABFT algorithm in this paper, the ABFT algorithm is implemented based on the Golang language, and the multi-machine multi-node simulation consensus is used for this experiment. This experiment is performed on a Intel Xeon (Cascade Lake) Platinum8269CY@2.5GHz / 3.2GHz, 32v CPU , 32G memory, and the operating system is CentOS 7.6 64-bit cloud server. The account system uses the same secp256k1 signature scheme as Bitcoin, while the public and private keys and signatures between blockchain nodes use the BLS signature scheme. In the experiment, 1000 transactions are set for each block. In this system, the PBFT algorithm and the ABFT algorithm proposed in this paper are verified, and the PBFT algorithm and the ABFT algorithm are analyzed from the aspects of consensus delay and throughput. Experiments were co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com