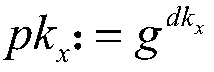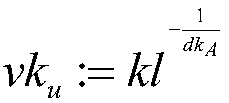Linkable ring signature method based on anonymous broadcast encryption
A technology of broadcast encryption and ring signature, applied in the field of information security, can solve the problems of inability to guarantee the anonymity of linkable verifiers, insufficient security, and narrow application range, so as to improve the efficiency of verification, improve security, and increase the scope of application Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
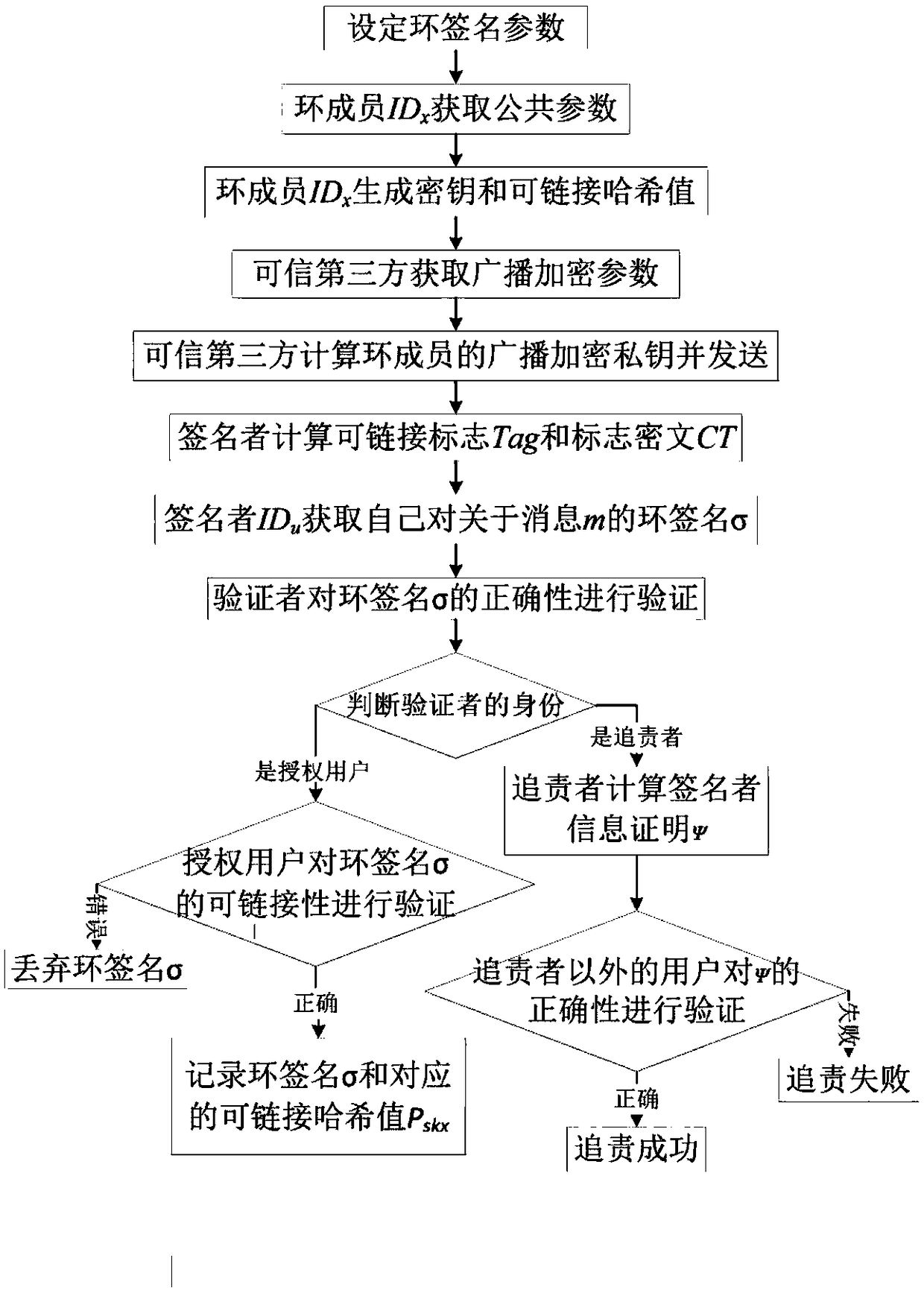
[0045] refer to figure 1 , a linkable ring signature method based on anonymous broadcast encryption, including the following steps:
[0046] Step 1) Set ring signature parameters:
[0047] Set the number of ring members to be n, n≥2, take n=5 in this embodiment, and the identity of each ring member is ID x , x is the label of the ring member, x=[1,5]; set the one-way function sent by the trusted third party to the ring member as f;
[0048] Step 2) Ring Member ID x Get public parameters:
[0049] Step 2a) Ring Member ID x Using the group generation algorithm of probabilistic polynomial time, the group parameter gk of the ring signature is generated through the security parameters of the ring signature x :gk x =(G,q,g), wherein, G is a group whose order is a prime number q and whose generator is g;
[0050] In this step, the gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com