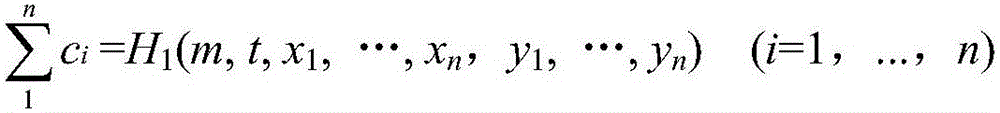Traceable anonymous authentication method based on elliptic curve
An elliptic curve, anonymous authentication technology, applied in wireless communication, public key of secure communication, user identity/authority verification, etc., can solve the problems of untraceable identity of signers, leakage of privacy of sending nodes, etc., and achieve resistance and denial of service effect of attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] It will be further described below in conjunction with the accompanying drawings and specific embodiments.
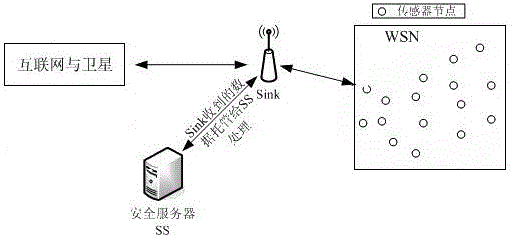
[0060] Please refer to figure 1 , the application basis of the traceable anonymous authentication method based on the elliptic curve of the present invention is: the Sink in the wireless sensor network is a convergence node, which is mainly responsible for the connection between the sensor network and the external network, and can also be regarded as a gateway node; the sink node can Complicated calculations are entrusted to the security server for processing, which is the gateway connecting the wireless sensor network and the external network;
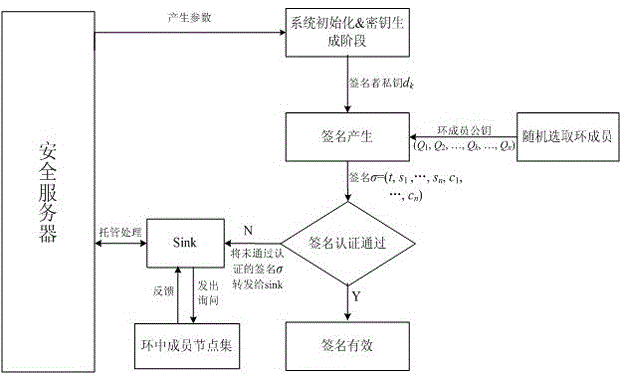
[0061] refer to figure 2 , before the method of the present invention is applied, the system is initialized first, and the security server generates initialization parameters, and the security server is responsible for generating, storing, and distributing security parameters in the entire signature and authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com