Patents
Literature
98results about How to "Ensuring privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
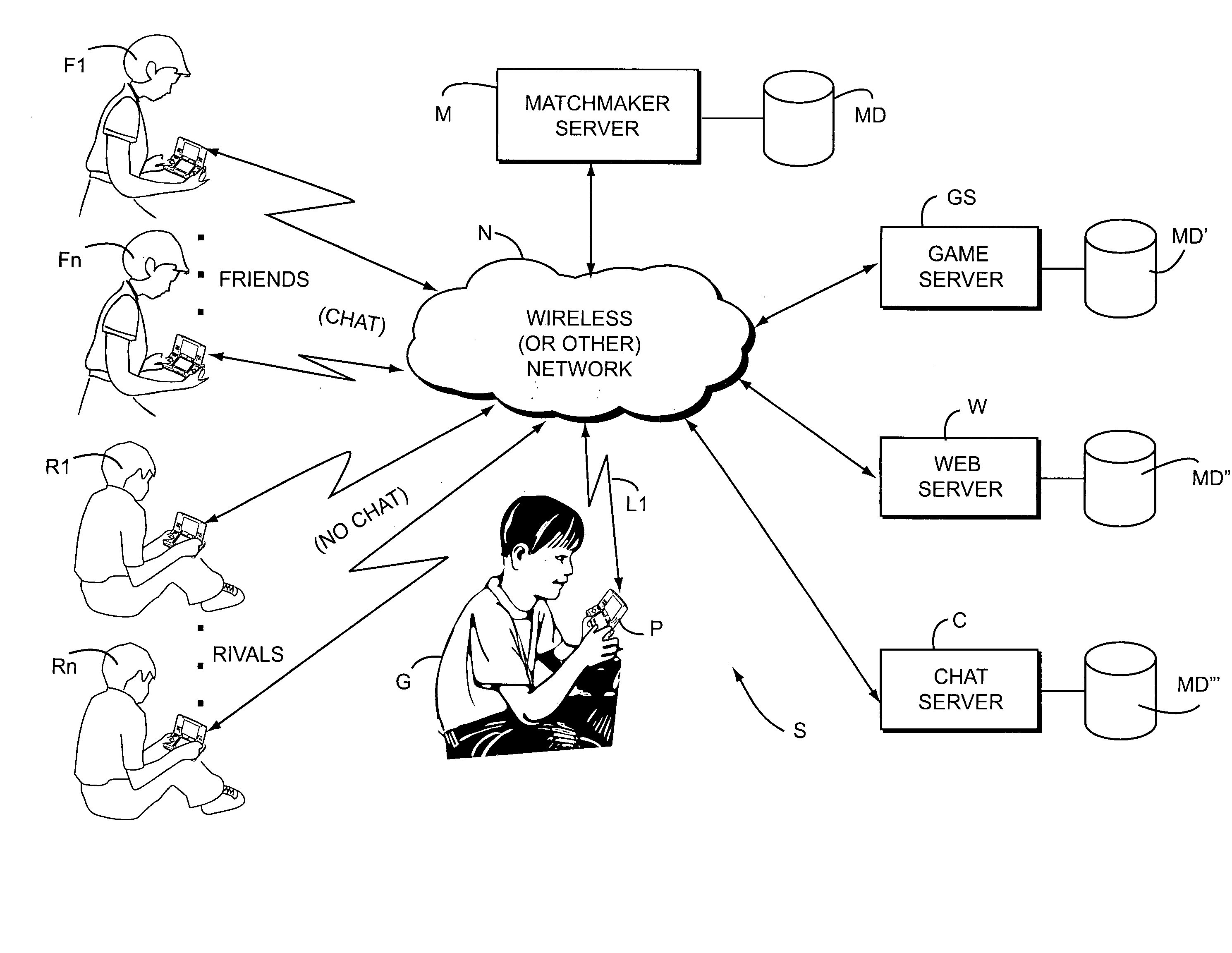
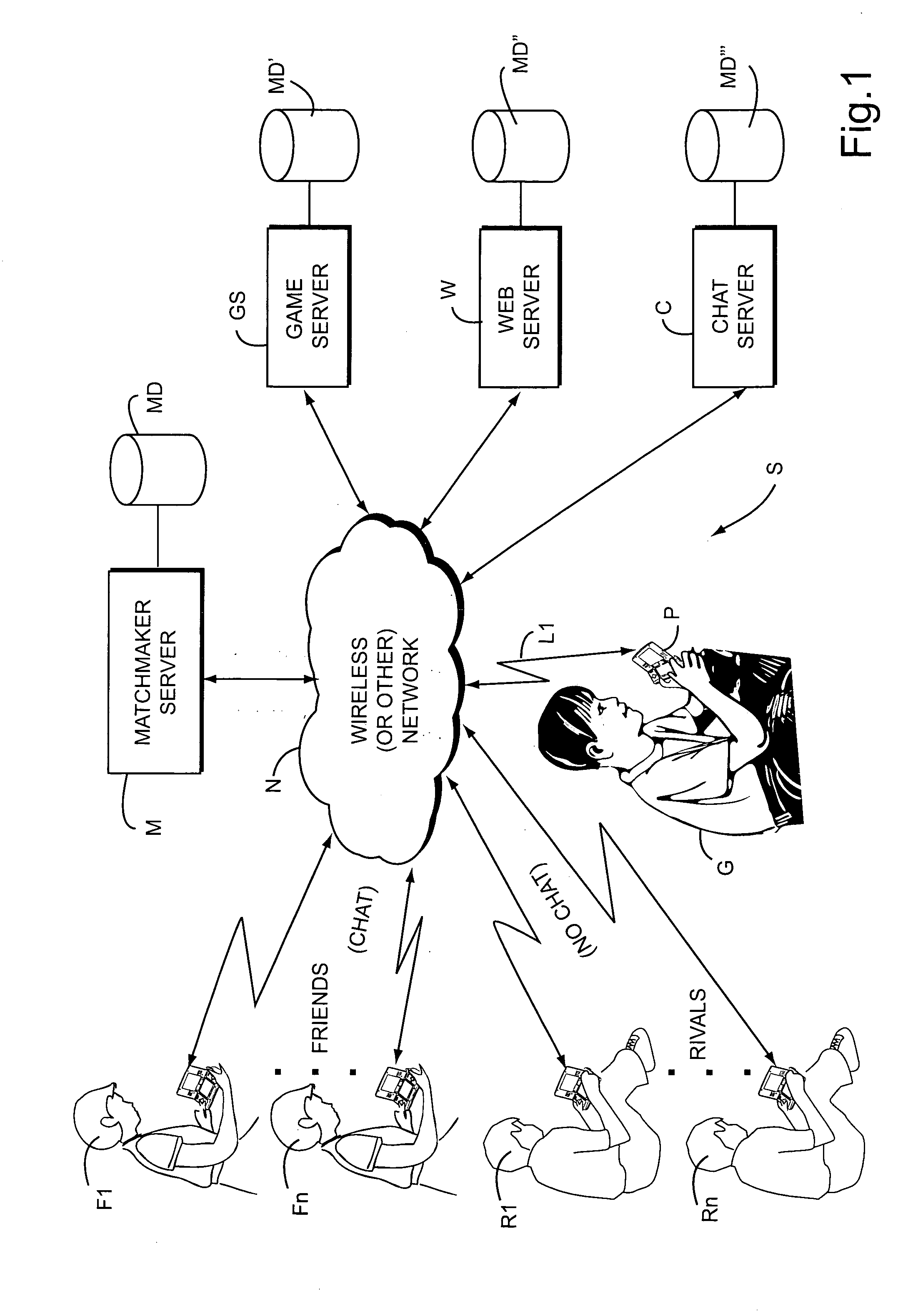
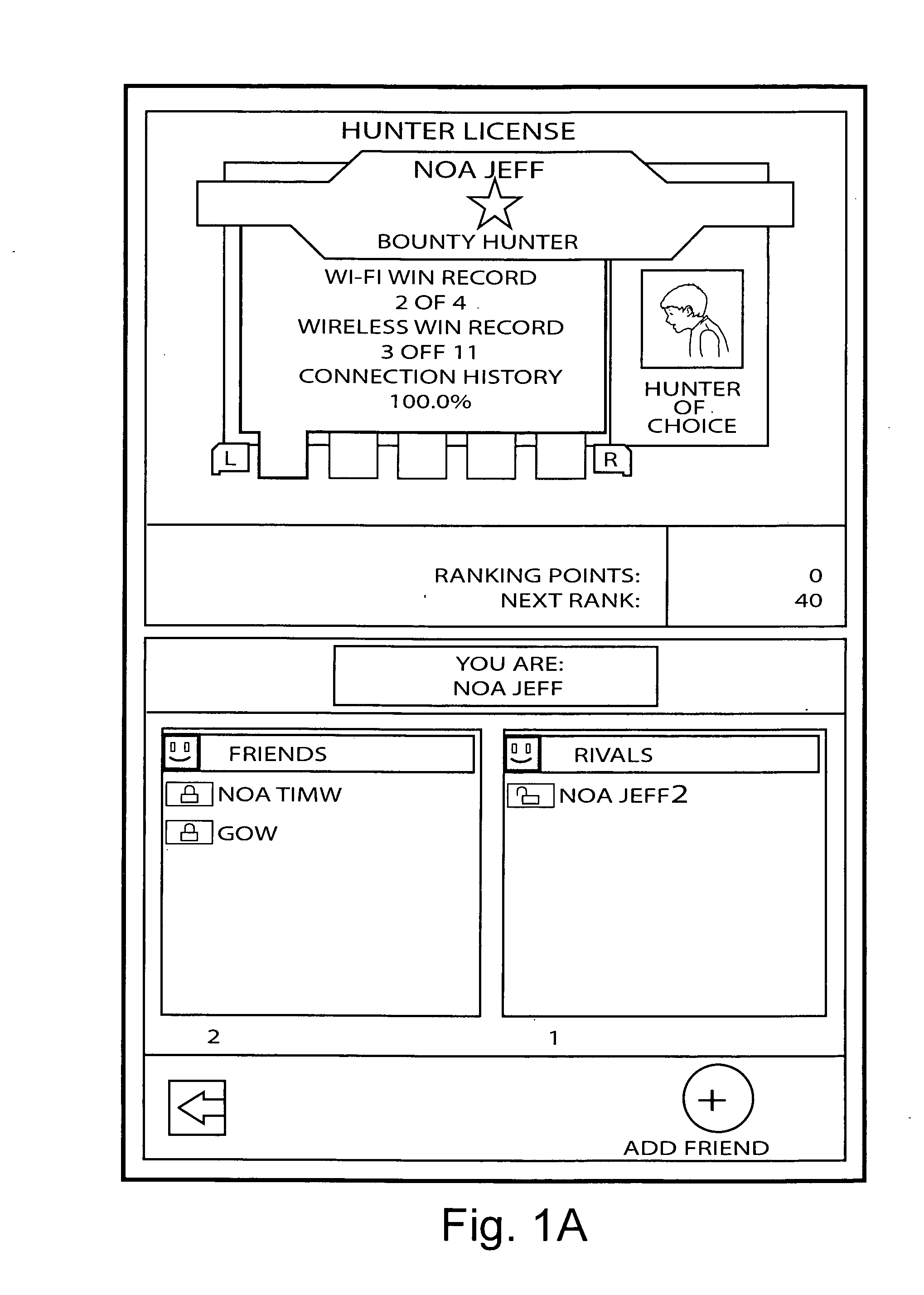
Systems, methods and techniques for safely and effectively coordinating video game play and other activities among multiple remote networked friends and rivals
ActiveUS20070218997A1Meet the selection requirementsEnsuring privacyVideo gamesSpecial data processing applicationsGame playerDirect communication
Real time interactive networked gaming is provided with two different classes of bookmarked online game players: “Friends” and “Rivals.”“Friends” are game players that are known personally. “Rivals” are game players who are not known personally but whom one has played against in the past in an online gaming scenario. Game software may allow chatting or other direct communication with “Friends” but not with “Rivals.” Rivals may be tracked to a limited degree so that for example it is possible to play against the Rival when he or she is online. Rivals may for example be players who you wish to track or keep track of, but in a manner that is safe for both you and the “rival.” When a player goes online again, he or she can see whether his or her Rivals are online and invite them to play another game. Inviting Rivals to play may be selectable, so an online player can invite Friends, Rivals or both to play.
Owner:NINTENDO CO LTD
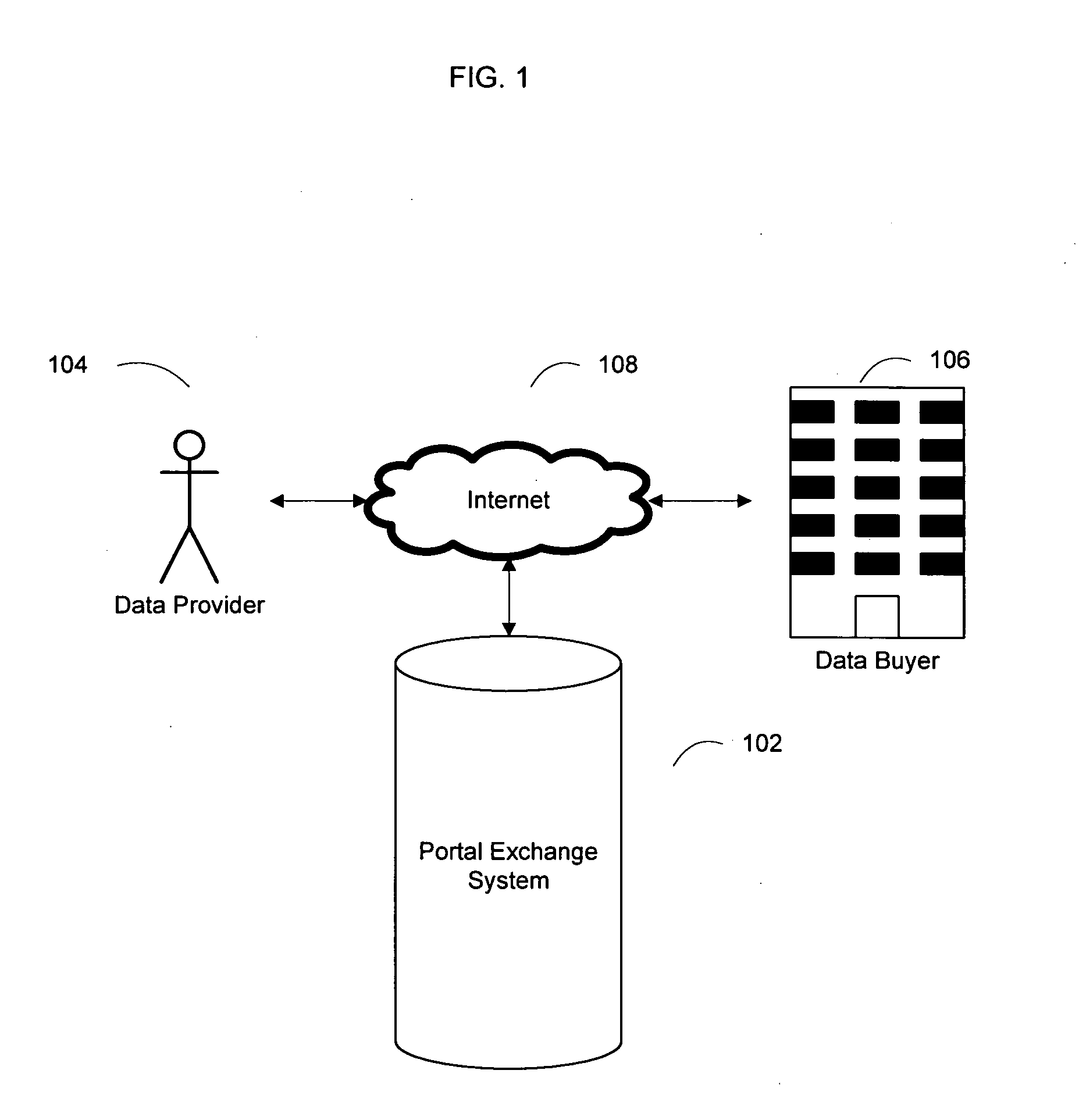
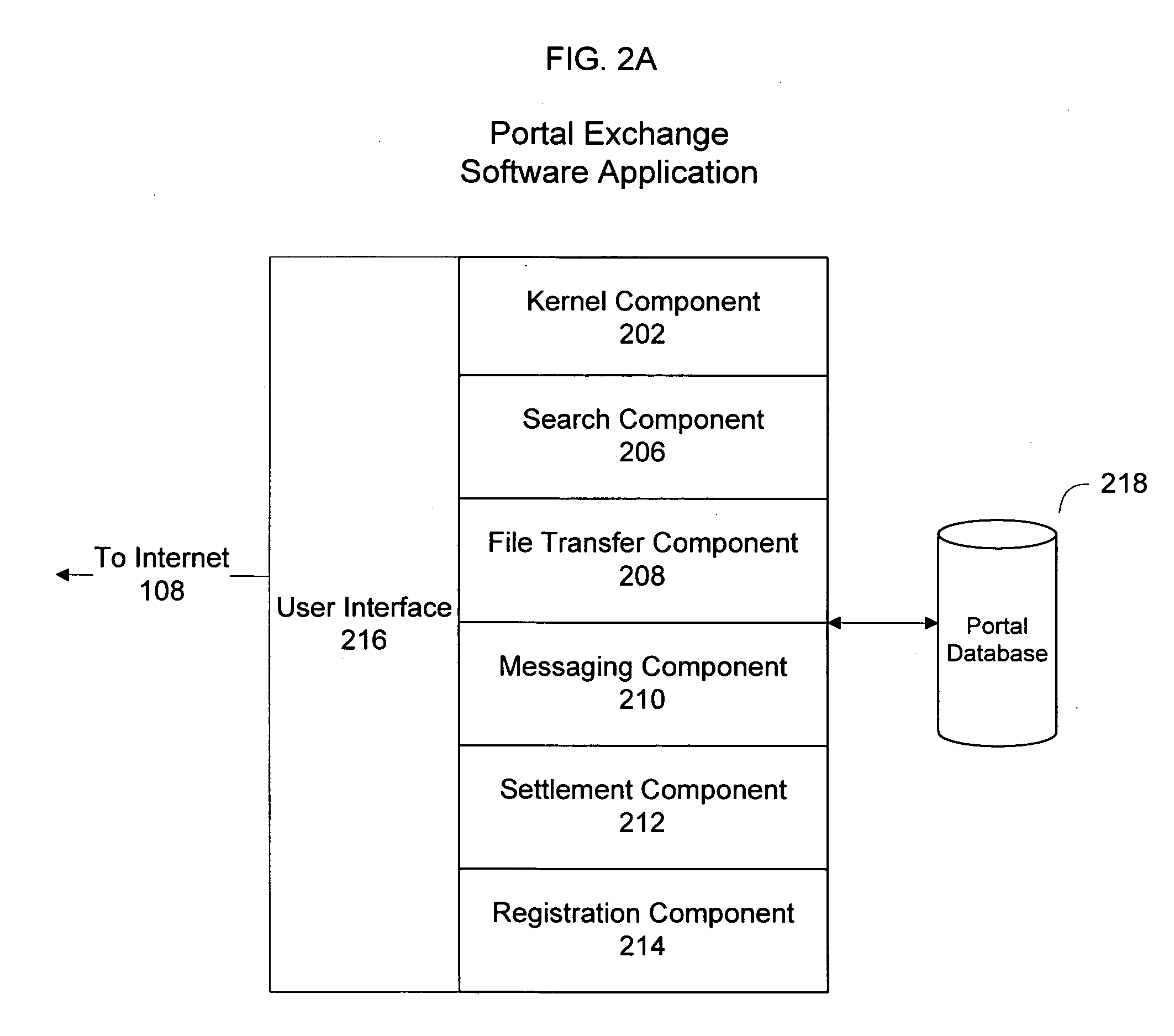
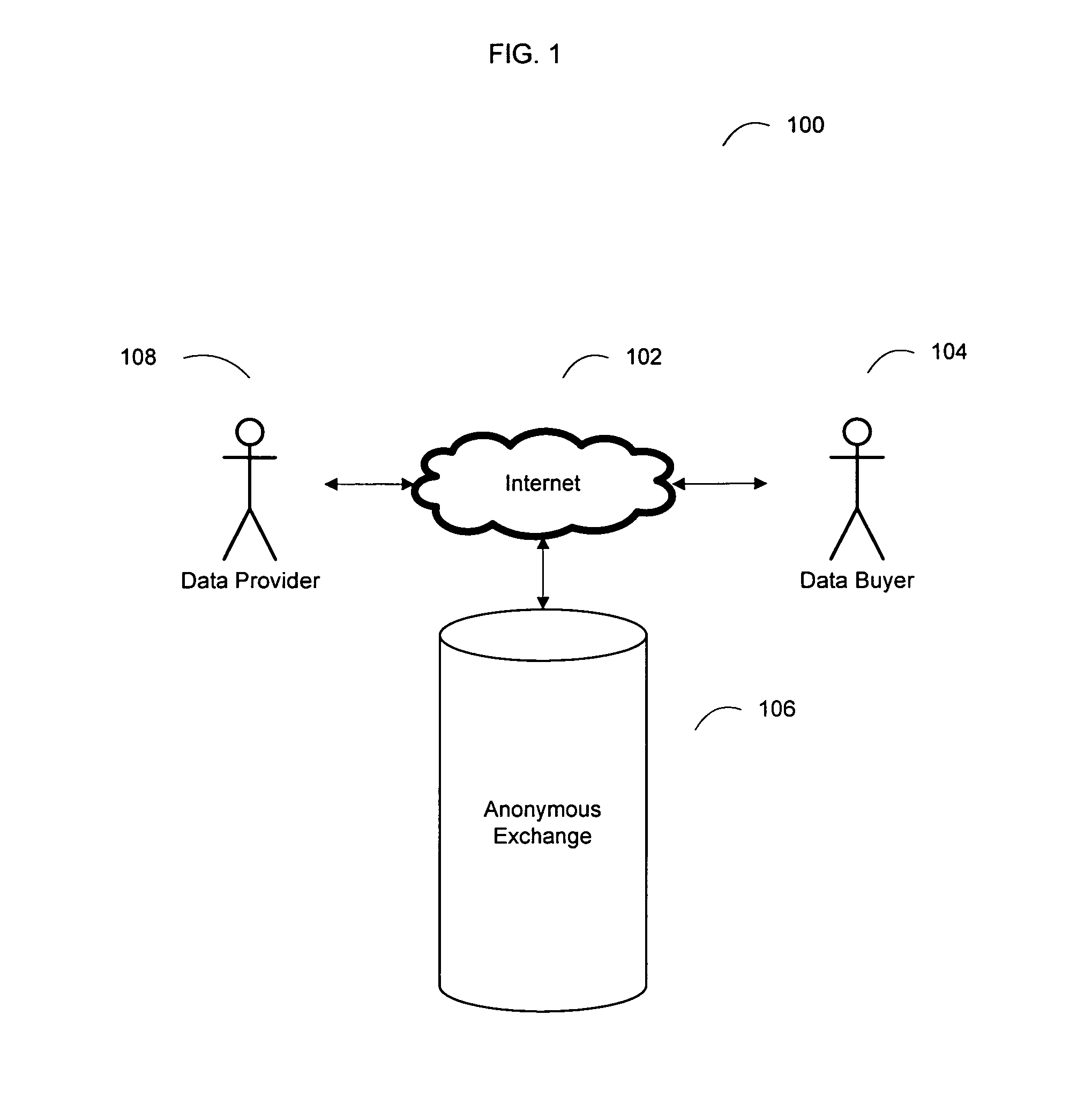
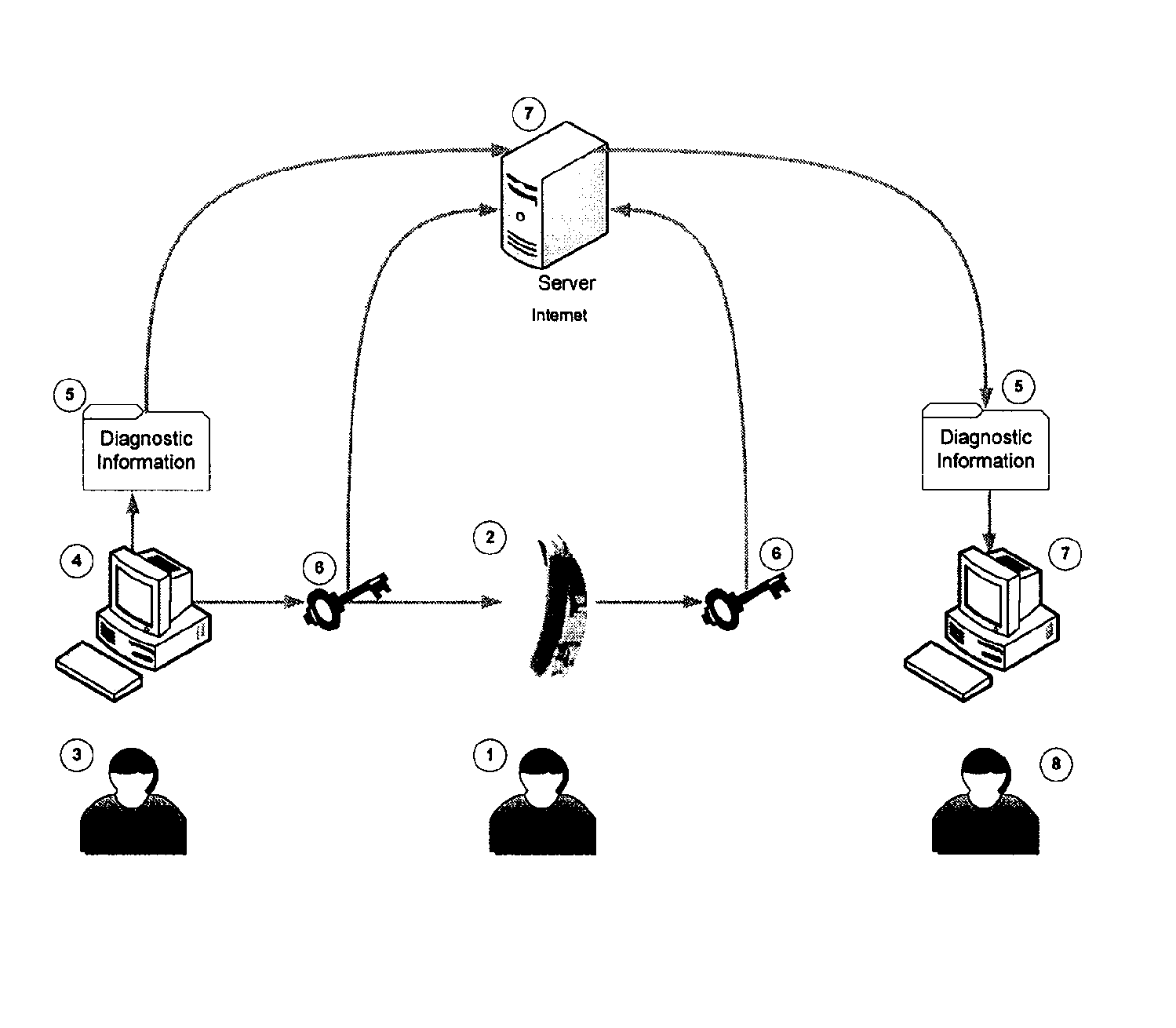
System and method for an online exchange of private data
Based on the small world theory of networking, the present invention provides access to a previously unavailable source of private data, necessary for commerce, by facilitating the sale of private data from members of the general public. For example, the seeker of private data, such as consumer information, submits a data request to an online portal system. The request submission includes legal representations stating the legally permissible purpose for seeking the information. The portal system may display the data request to registered data providers, based on their demographic data. The system facilitates the exchange between the data buyer and the data provider. A payment invoice can be generated and electronically presented by the portal system. The payment may be electronically debited from the designated account of a data. In addition, a portion of such funds may be retained by the portal entity.
Owner:CREDIGY TECH
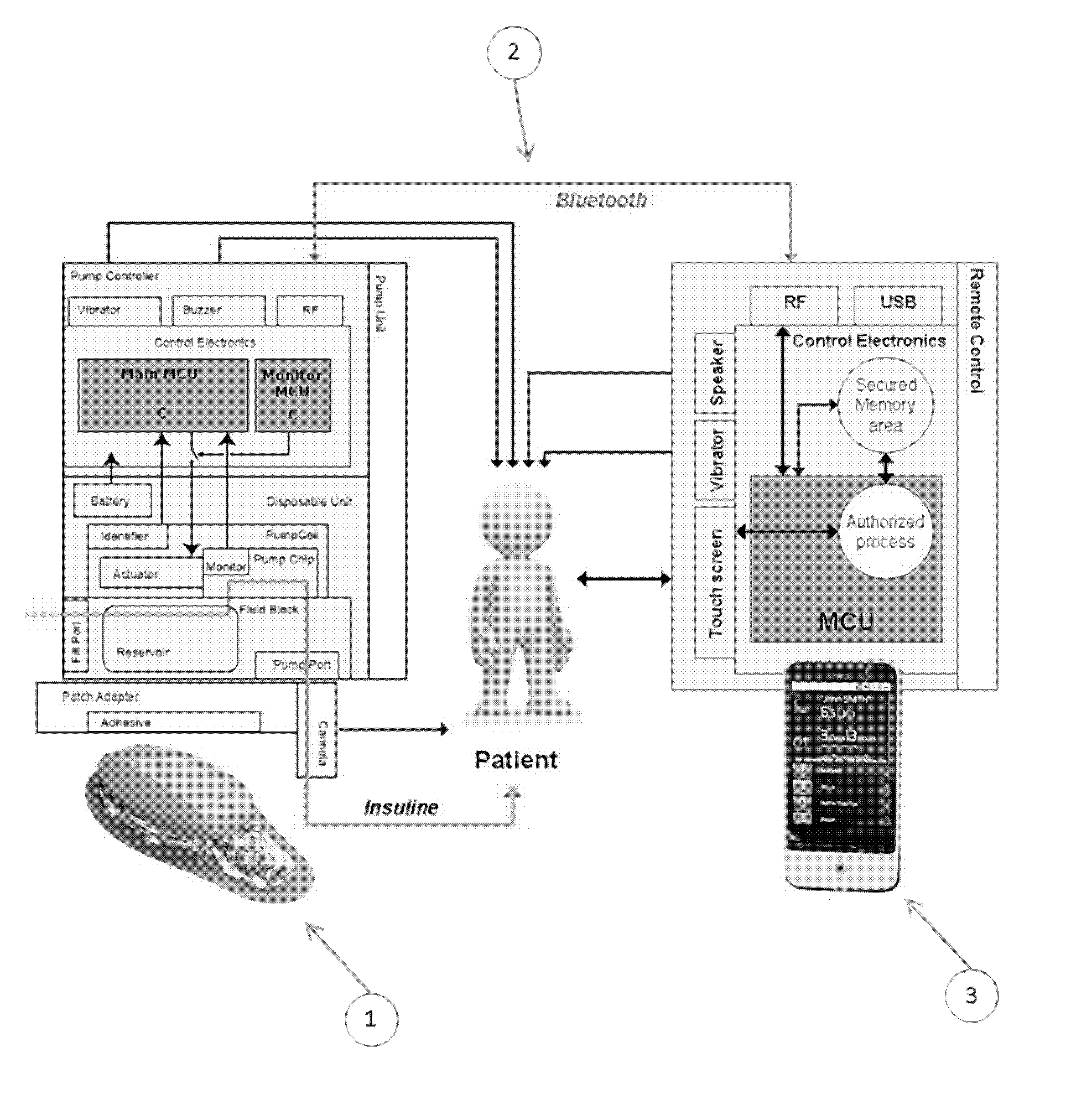
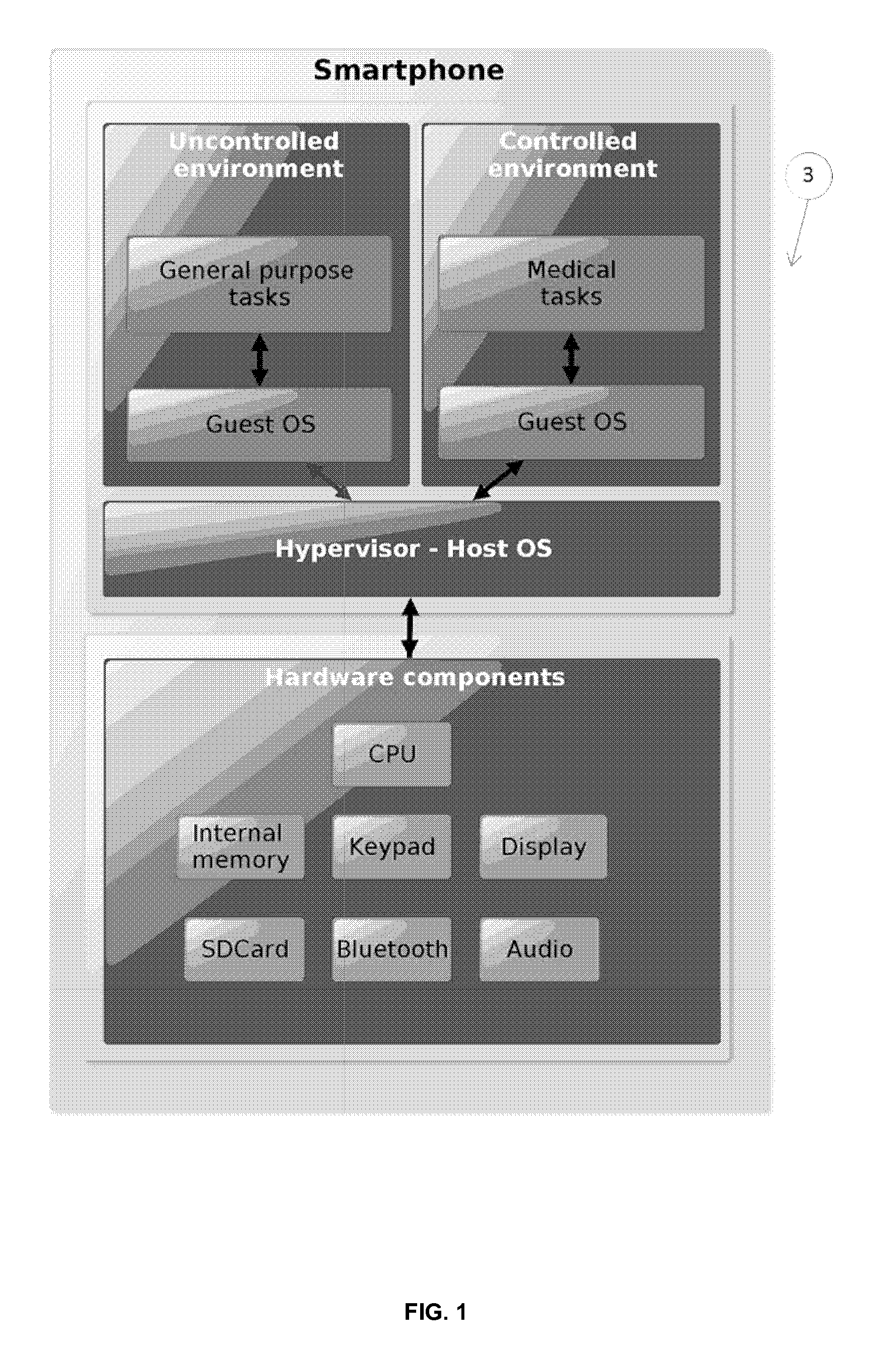
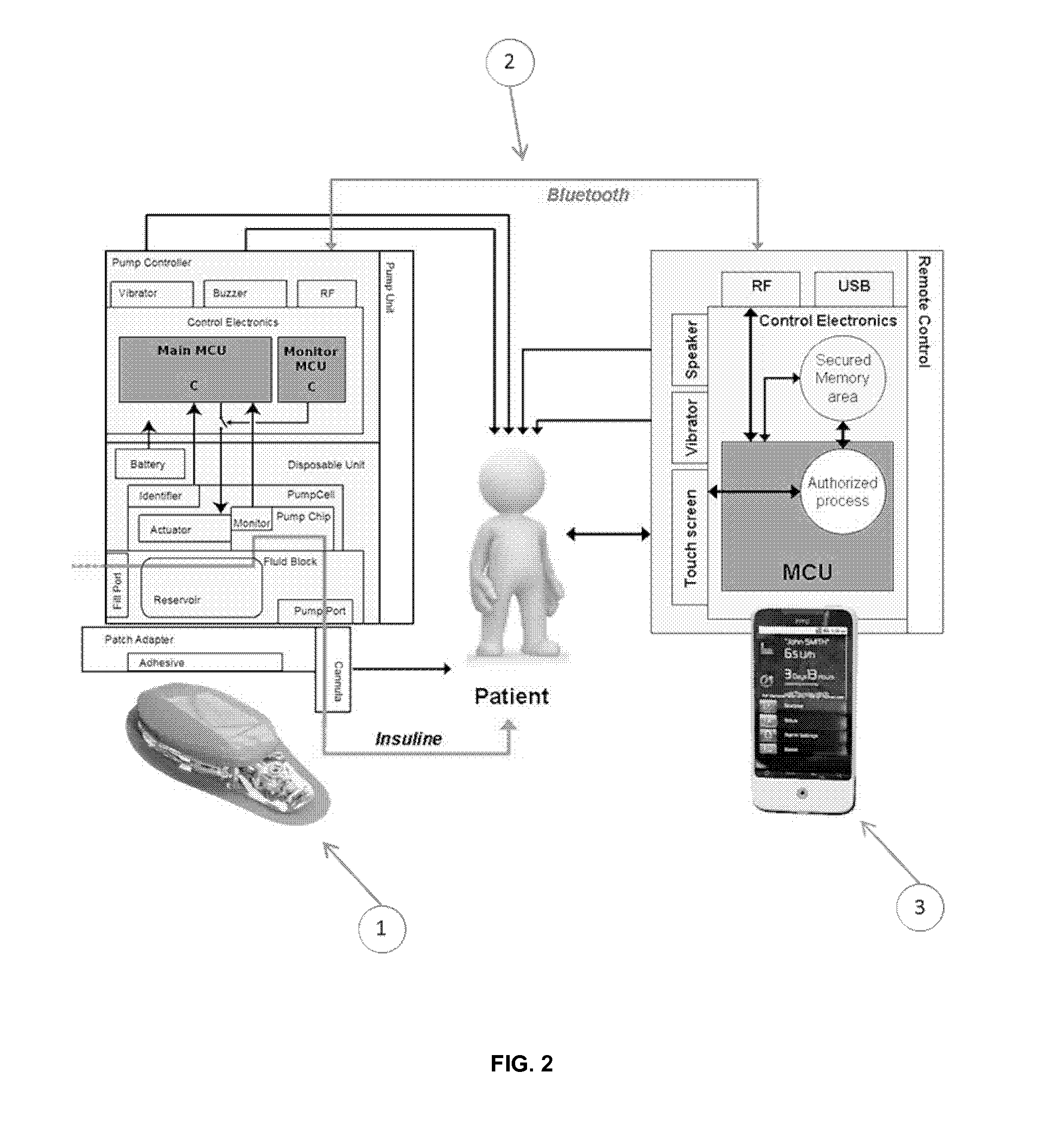
Communication secured between a medical device and its remote control device
InactiveUS20150207626A1Low production costImprove remote control performanceTransmission systemsPublic key for secure communicationRemote controlMedical device
The invention comprises a medical assembly composed by a medical device and a remote control which communicate in a secure and wireless manner. The remote control is connected to at least one security token. Key information stored in the medical device and the security token is used to establish a connection and to communicate in a secure manner.
Owner:DEBIOTECH SA
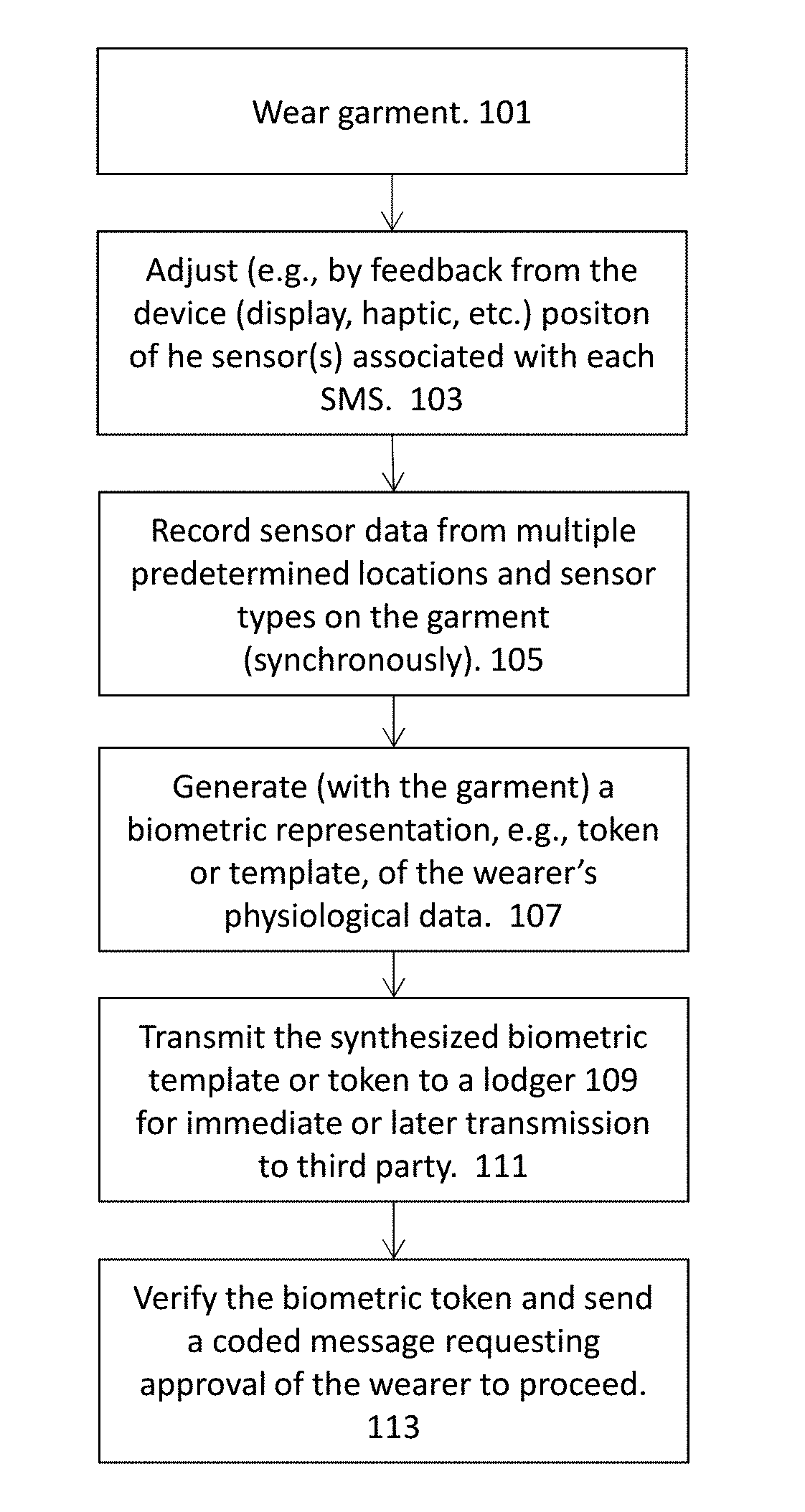
Biometric identification by garments having a plurlity of sensors
ActiveUS20180000367A1Reduce gapEasy to measureElectrocardiographyPerson identificationDiagnostic Radiology ModalityEngineering
Biometric identification methods and apparatuses (including devices and systems) for uniquely identifying one an individual based on wearable garments including a plurality of sensors, including but not limited to sensors having multiple sensing modalities (e.g., movement, respiratory movements, heart rate, ECG, EEG, etc.).
Owner:L I F E
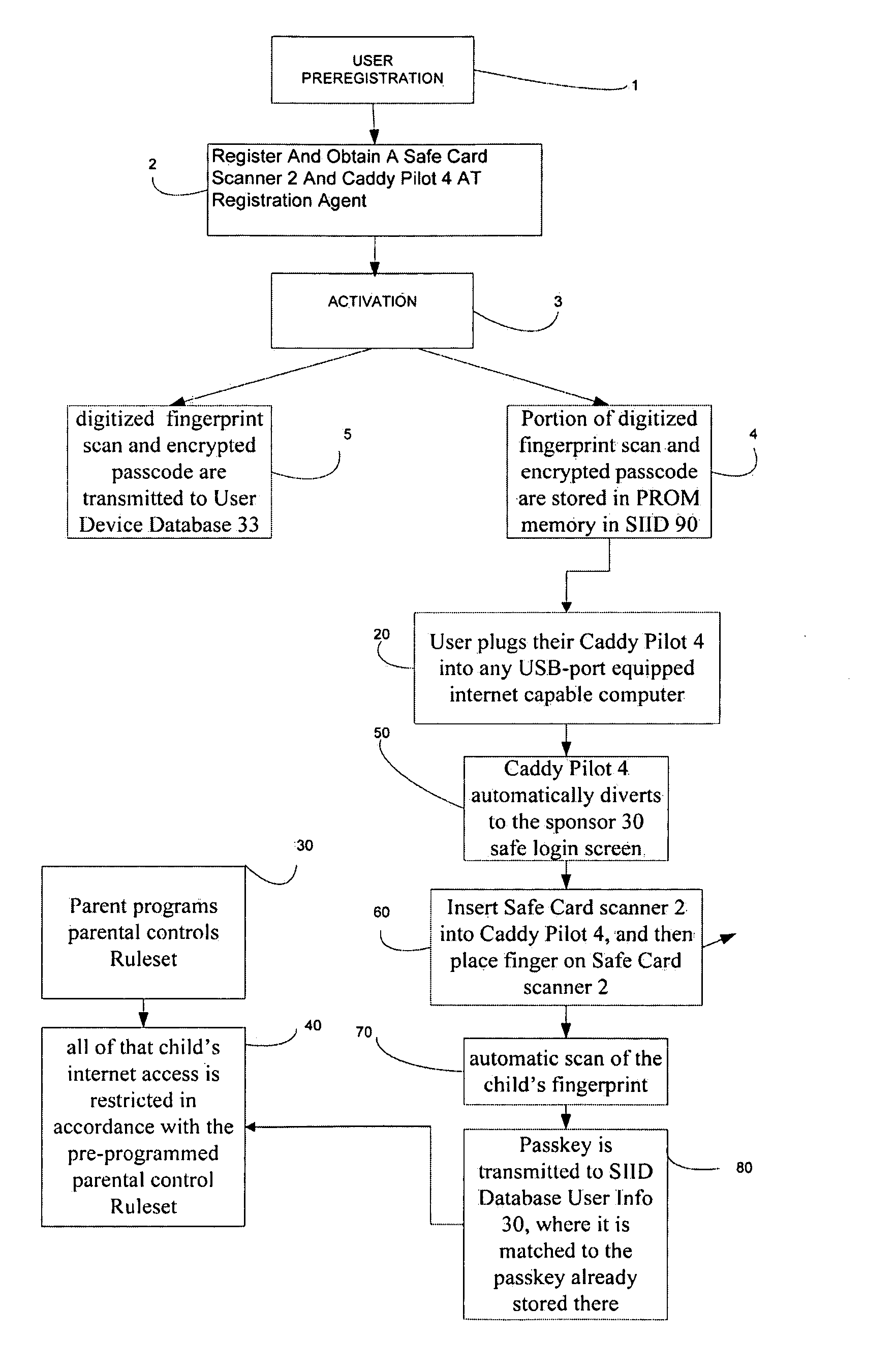
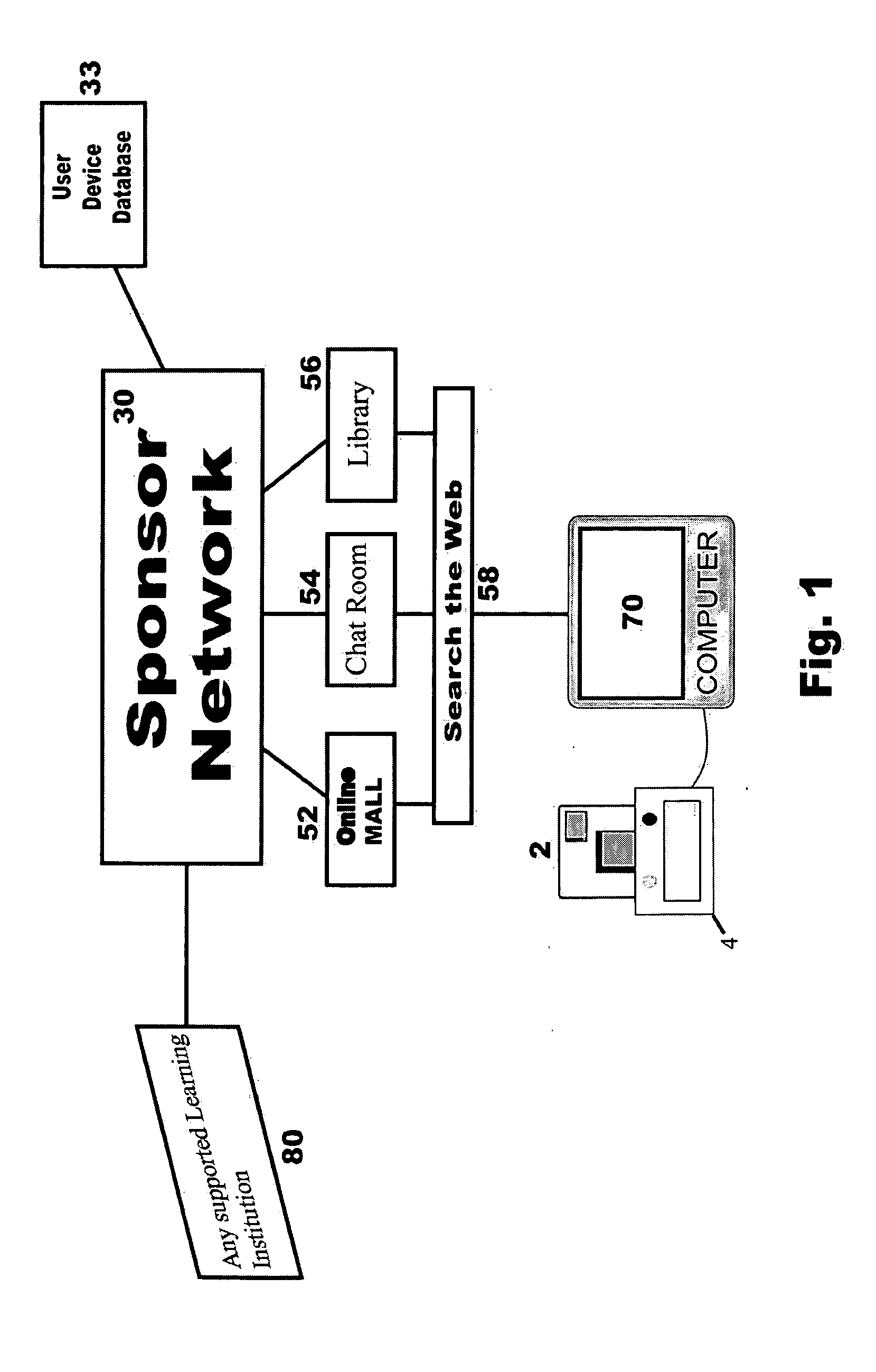
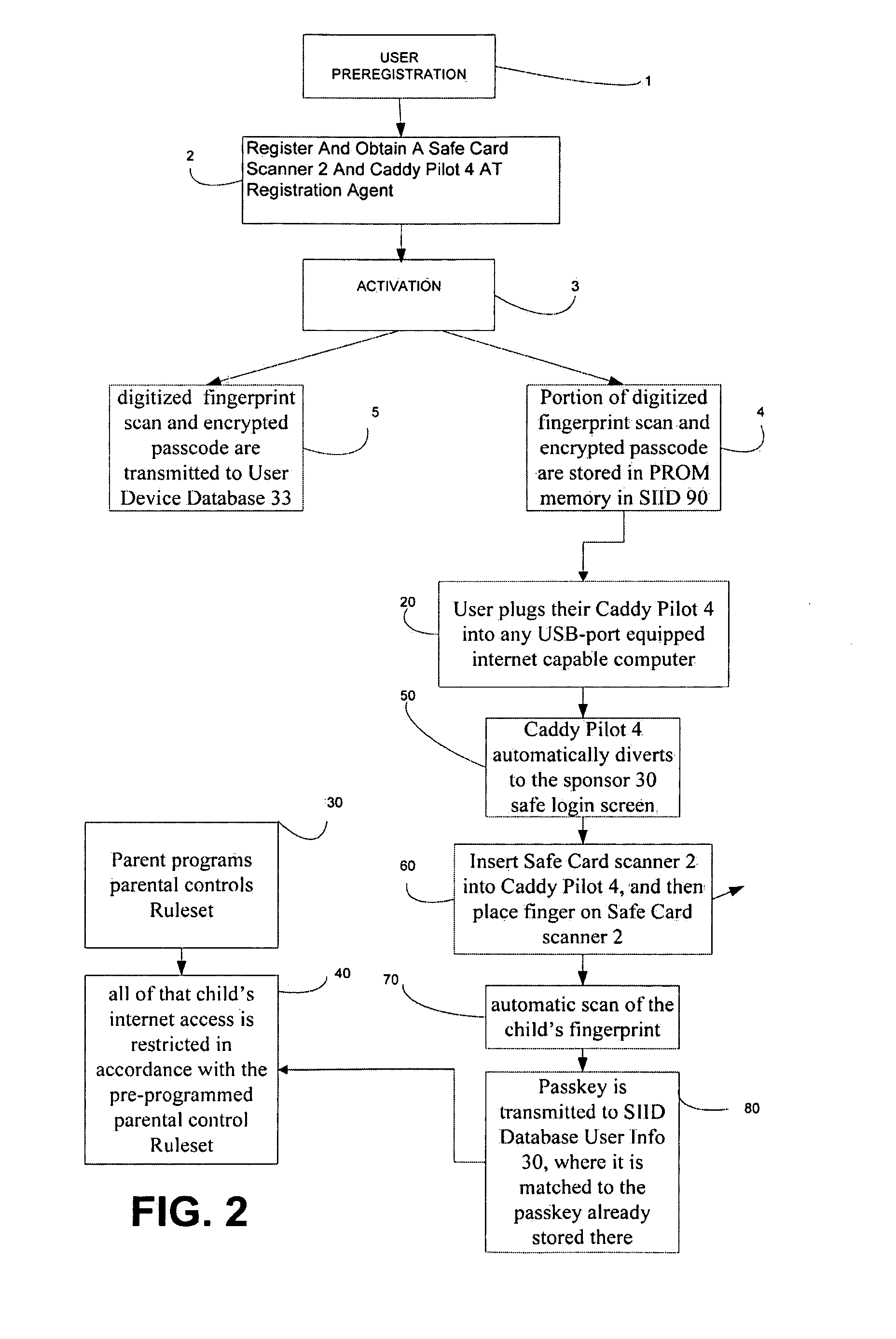
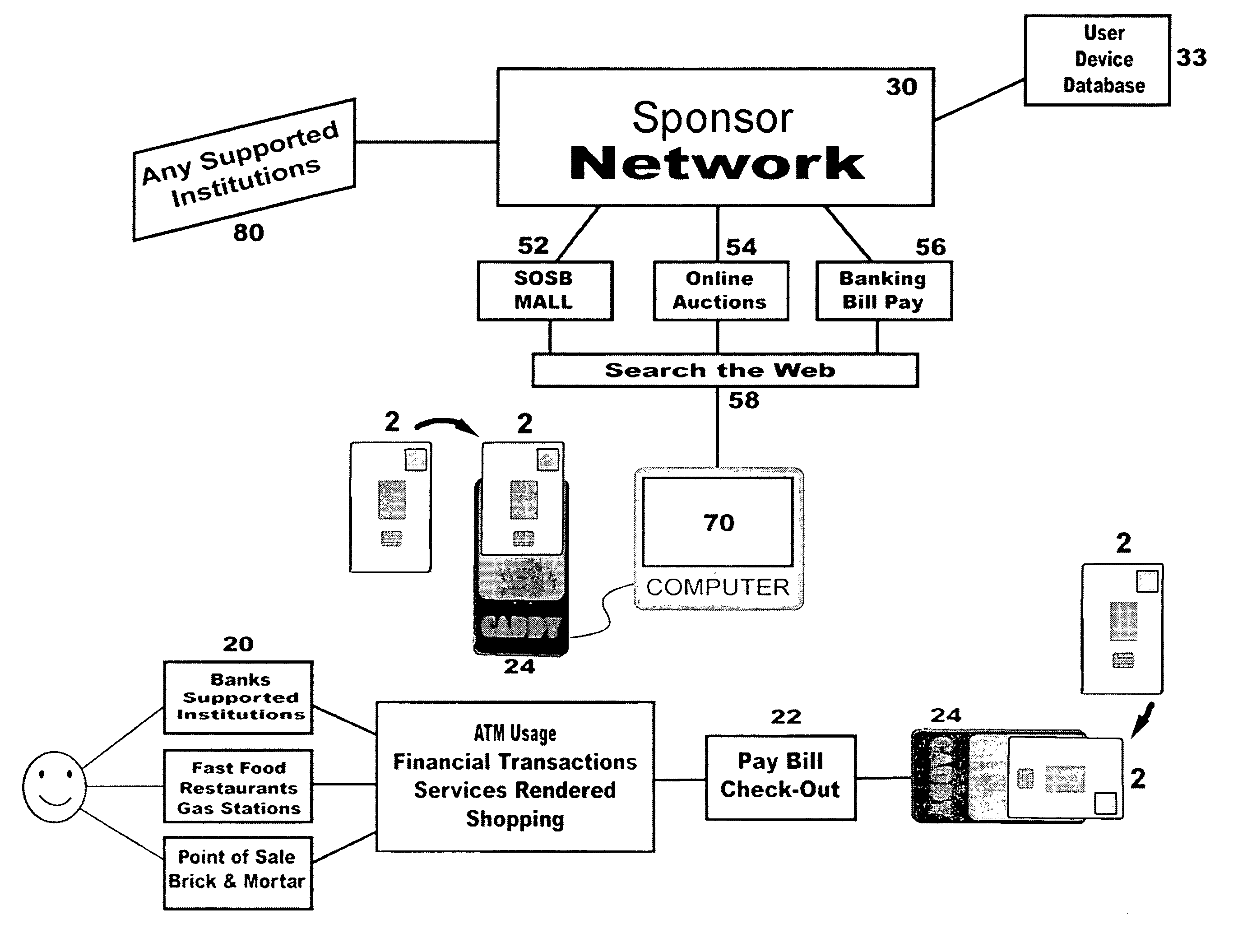
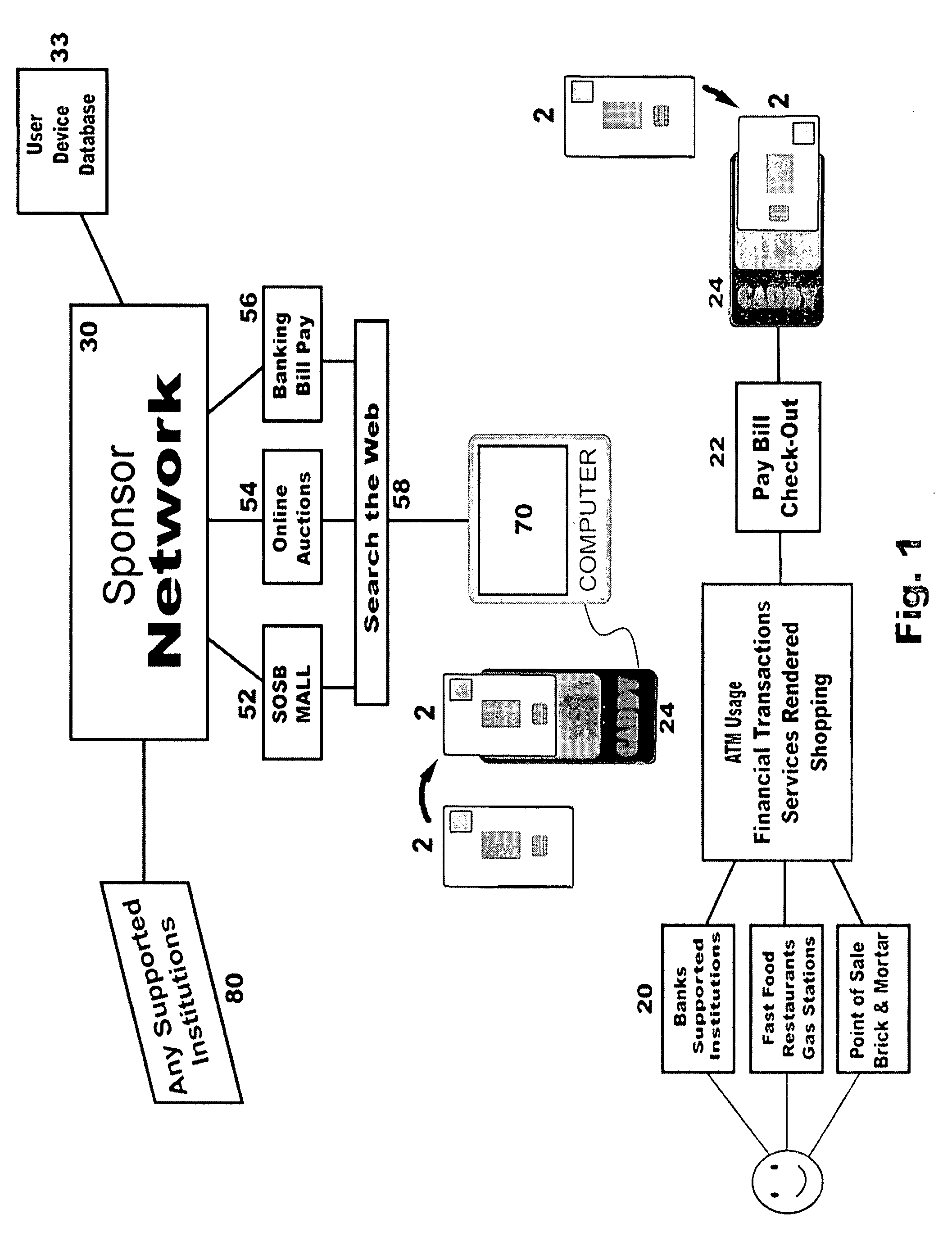
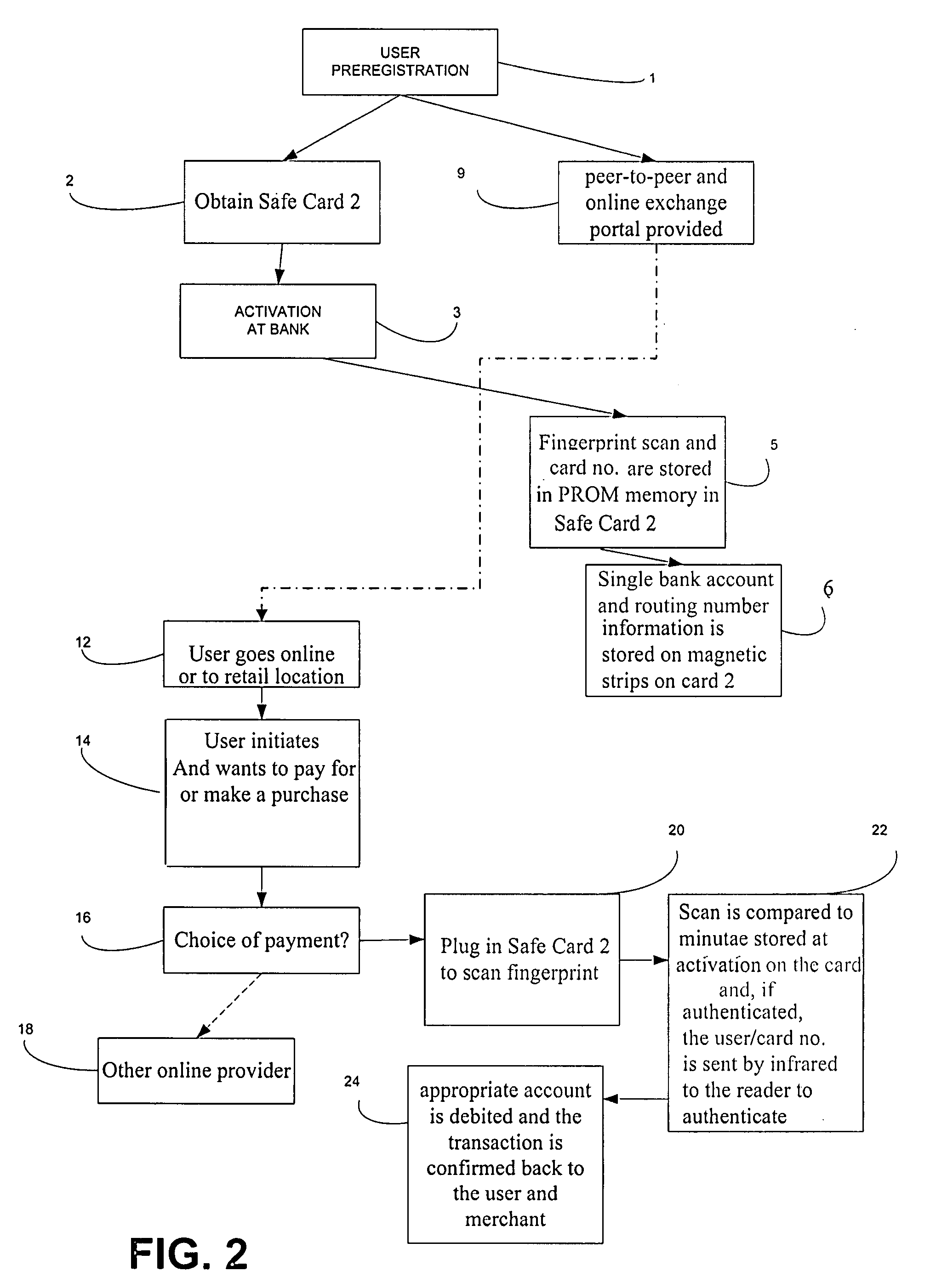
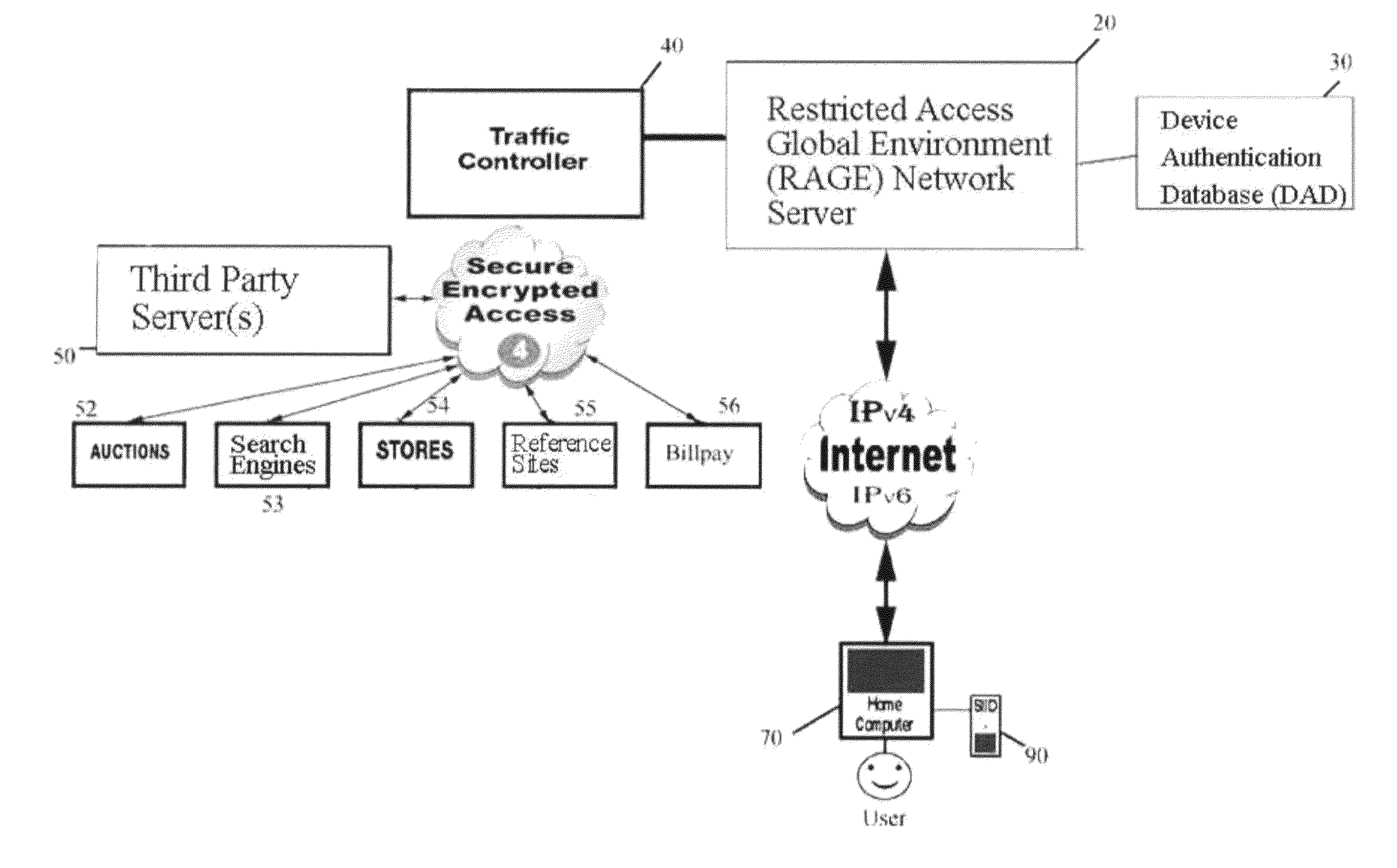
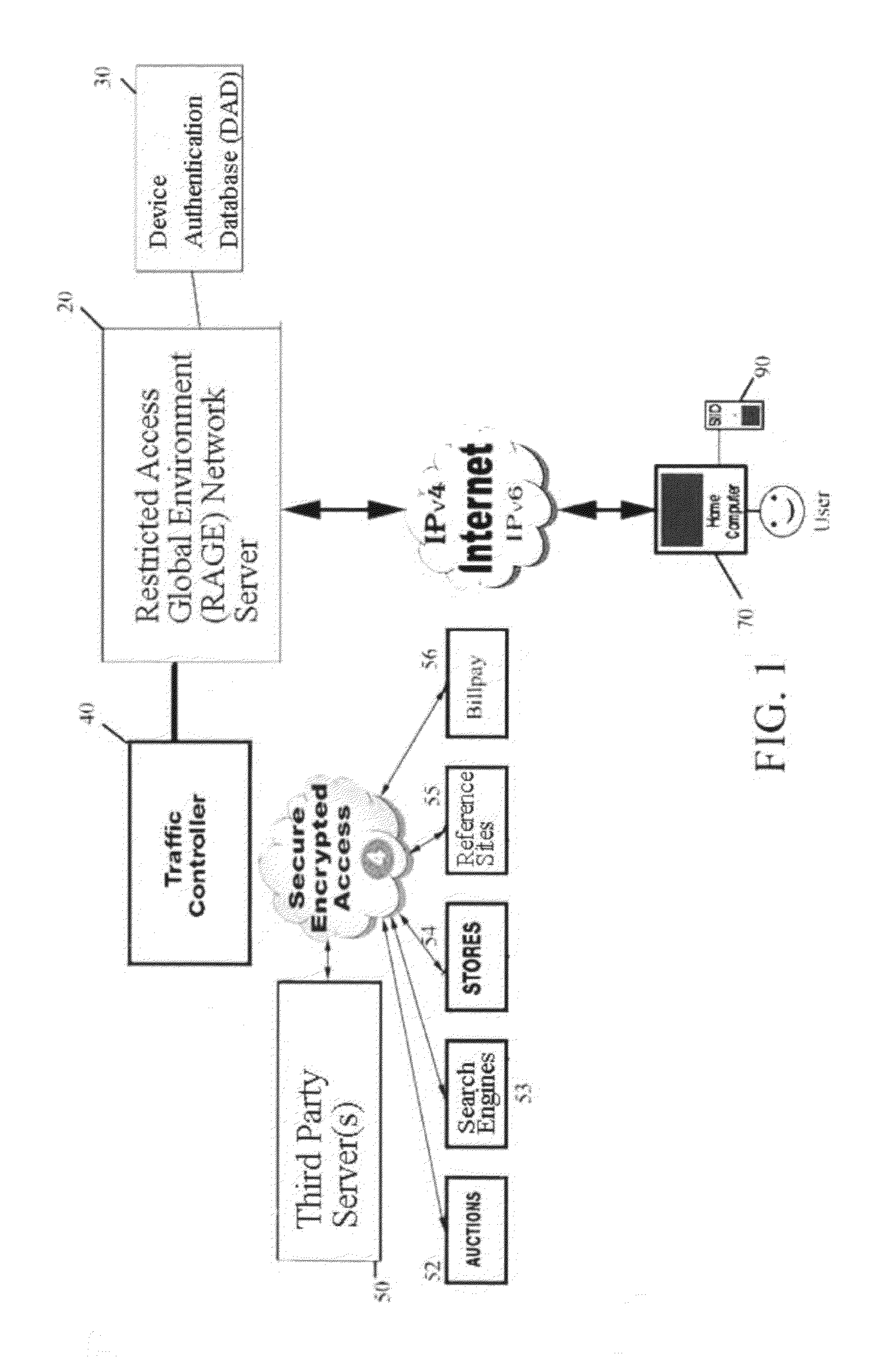
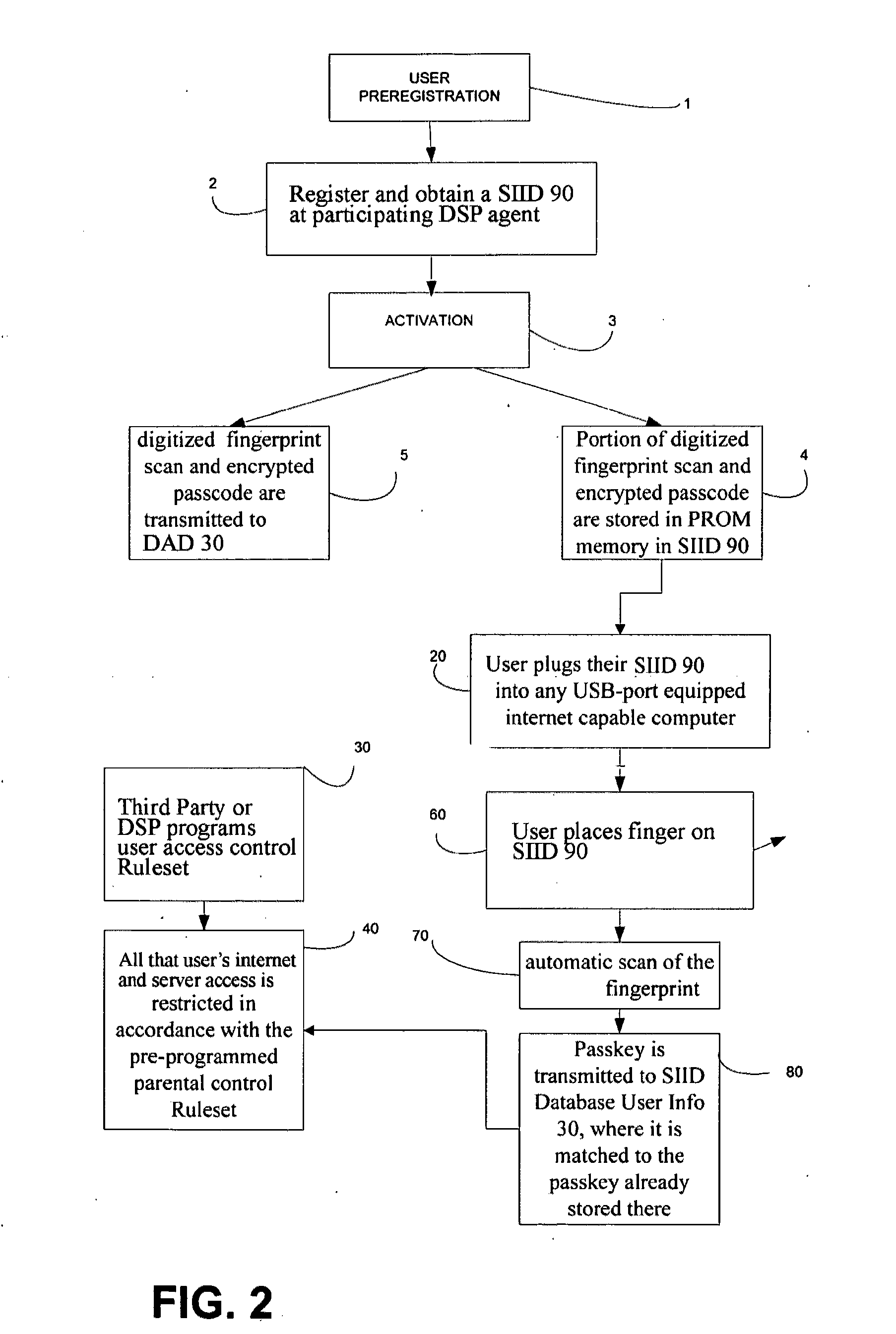
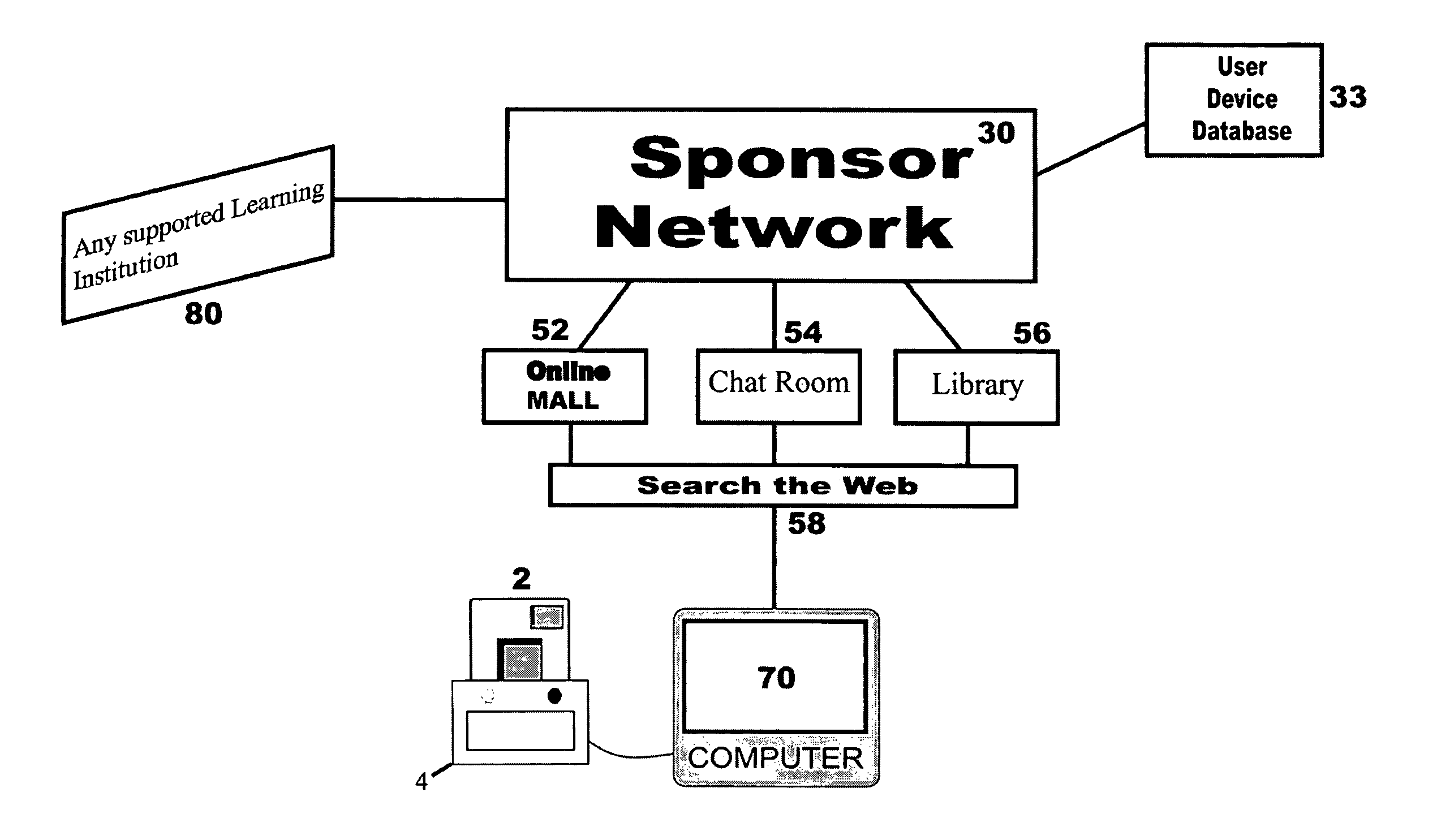
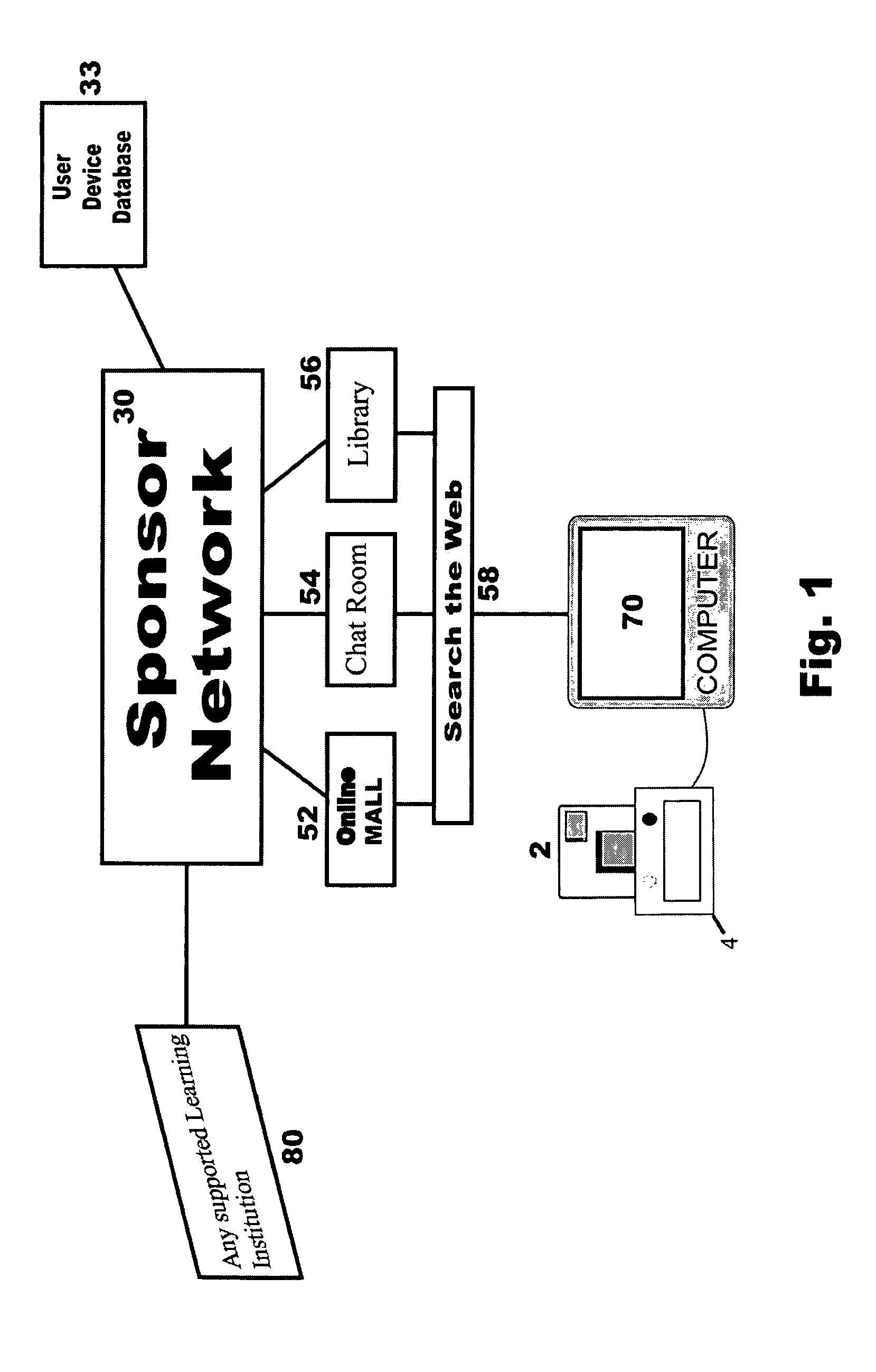
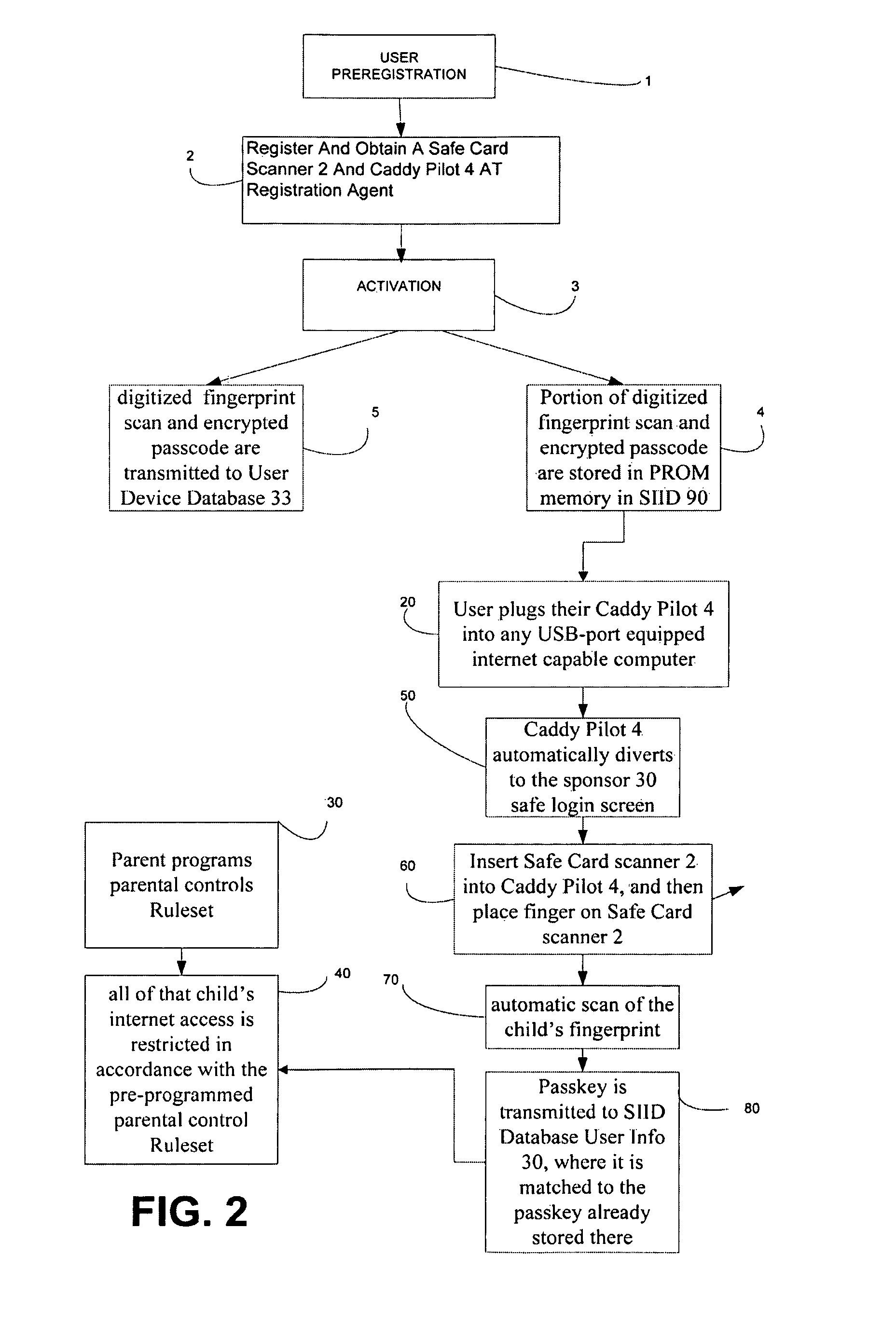
System for secure internet access for children
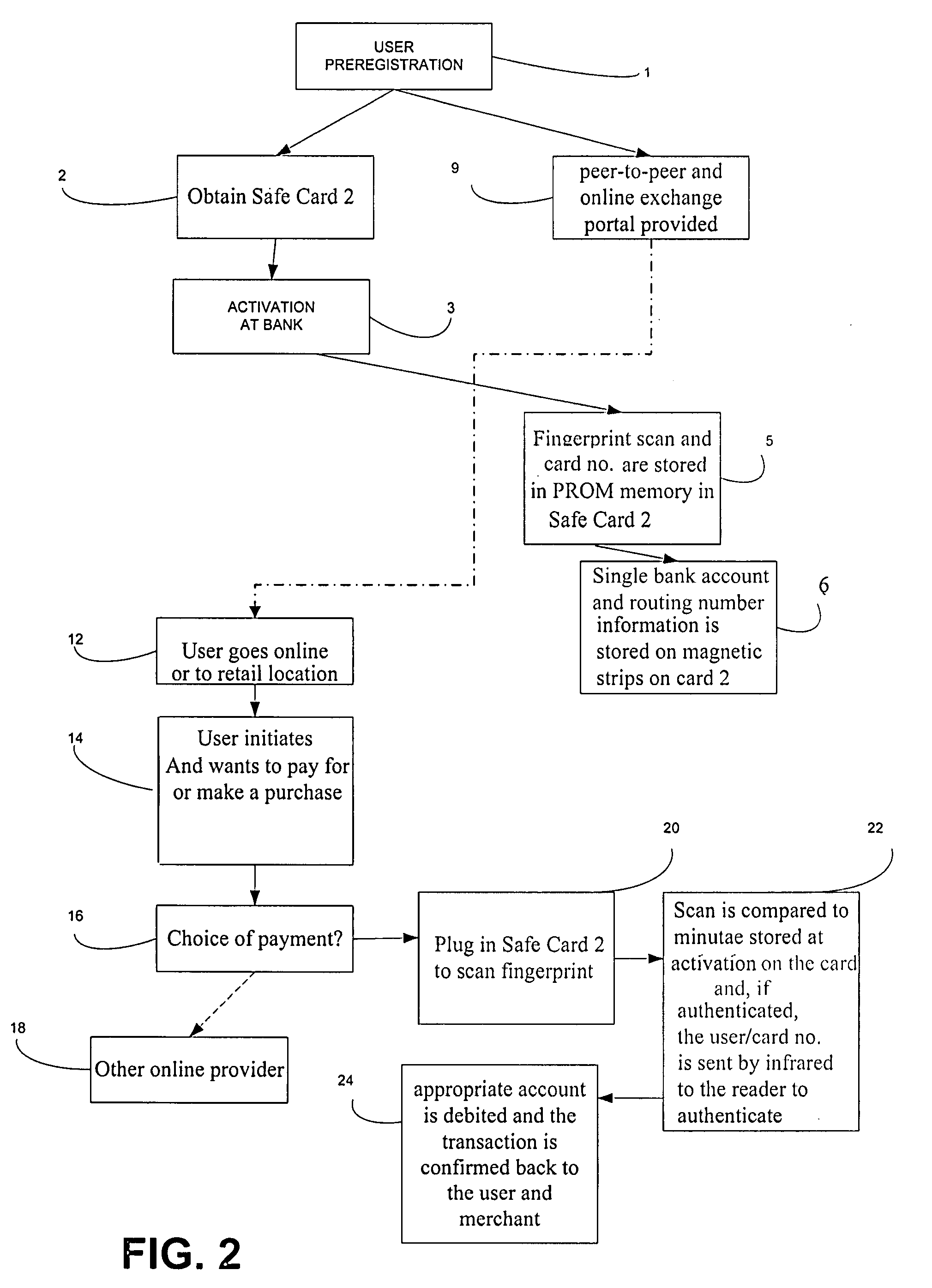
InactiveUS20090064302A1Ensuring privacyDigital data processing detailsUser identity/authority verificationInternal memoryDocking station
A system and method for secure internet access by children that assigns each child a Safe Card Scanner with integral fingerprint scanner and a Caddy-Pilot for Kids (intelligent card reader and docking station) into which the Safe Card Scanner docks for biometric-secure internet access for children. Both the Safe Card Scanner and Caddy-Pilot for Kids have internal memory and device ID numbers stored therein. At registration each child is assigned a user ID corresponding with card ID number and a registration record is compiled including the assigned user ID and photo data plus the Safe Card Scanner and Caddy-Pilot for Kids ID numbers. Parents author a parental ruleset for their child and the ruleset is stored by a host ASP. The child then activates their Safe Card scanner by an initial fingerprint scan, a portion of which is stored locally on the Safe Card scanner (along with the assigned device ID number). Given a registered / activated Safe Card scanner, the child can access the internet from any web-enabled computer simply by plugging the Caddy-Pilot for Kids into the computer's USB port. The Caddy-Pilot for Kids automatically opens a browser program and loads the URL of the sponsoring ASP. The child than inserts their Safe Card scanner into the Caddy-Pilot for Kids, which automatically initiates a scan of their fingerprint, which instantaneously captures a portion of their fingerprint minutia and compares it to the minutia stored previously at enrollment activation, thereby authenticating that child as the authorized user of that Safe Card Scanner. Once a local authentication has taken place the Safe Card scanner checks the assigned user ID plus the Safe Card Scanner and Caddy-Pilot for Kids ID numbers to the registration record, authenticates the child user, and pre-loads the parental control ruleset. The child-users then have a restricted safe and secure but full internet experience including online shopping malls, Chat Rooms, Libraries, games, sports, etc.
Owner:COLELLA BRIAN A
Method of individually fitting a hearing device or hearing aid
ActiveUS20100205447A1Improve acoustic propertiesSimple modelDigital data processing detailsUnauthorized memory use protectionHearing aidHearing apparatus
The present invention provides a method of providing parameters for the fitting process of individually shaped or customized hearing devices by collecting and storing fitting parameters during a fitting process by a local fitting computer; generating an individual encryption key related to the hearing device; sending the stored fitting parameters encrypted with the encryption key to a remote database; storing the encryption key in the memory of the hearing device; reading out the encryption key from the hearing device; reading out data from the remote database using the encryption. Thus, the privacy of the individual fitting data of a hearing device is secured.
Owner:SONOVA AG
System for secure payment and authentication
InactiveUS20070214093A1Robust user authenticationEconomical and reliableDebit schemesIndividual entry/exit registersOn boardUser identifier
A system and method for biometric-secure point-of-sale or online transactions and / or authentication and ID verification for restricted access that simplifies the checkout process and eliminates fraudulent transactions. The system employs a credit-card-sized device with integral fingerprint reader, on-board memory with pre-designated card number, infrared coder, power strip, plus at least one magnetic strip (encoded with designated financial account to be used for transactions, including routing number), one magnetic strip for personal medical and identification information and a bar code and photo ID for security. The card scanner is activated by an activation scan in which a subset of “minutia” are stored locally. To consummate a transaction (after registration), the user simply plugs their card scanner into a multi-function reader, and scans their own fingerprint. Upon authentication the card transmits the card / user ID to the reader as authentication of the transaction, the reader reads the encoded account numbers and routing information, offers a choice of account to charge to, verifies the total charge and completes the transaction. The process is fully secure.
Owner:COLELLA BRIAN A
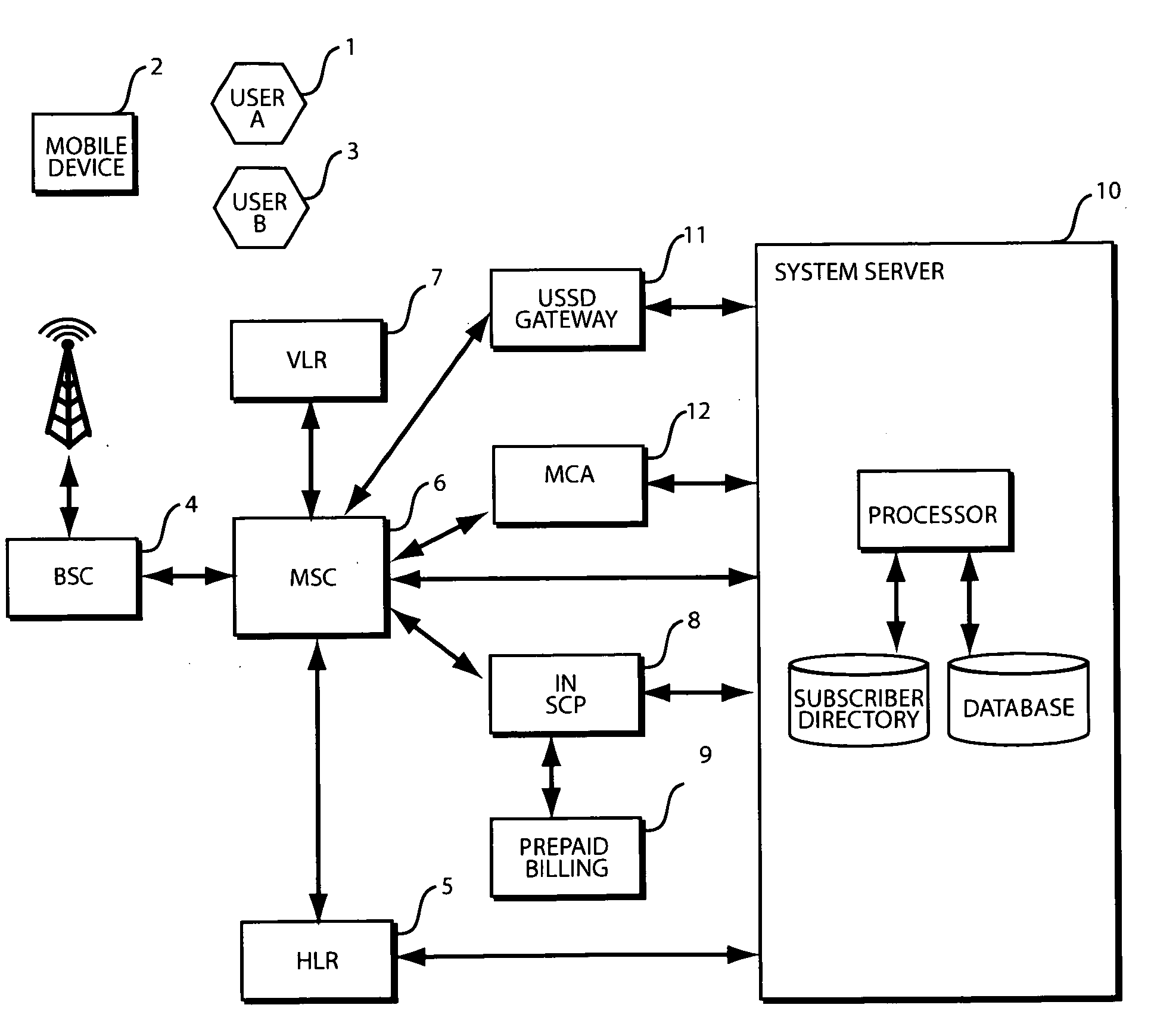
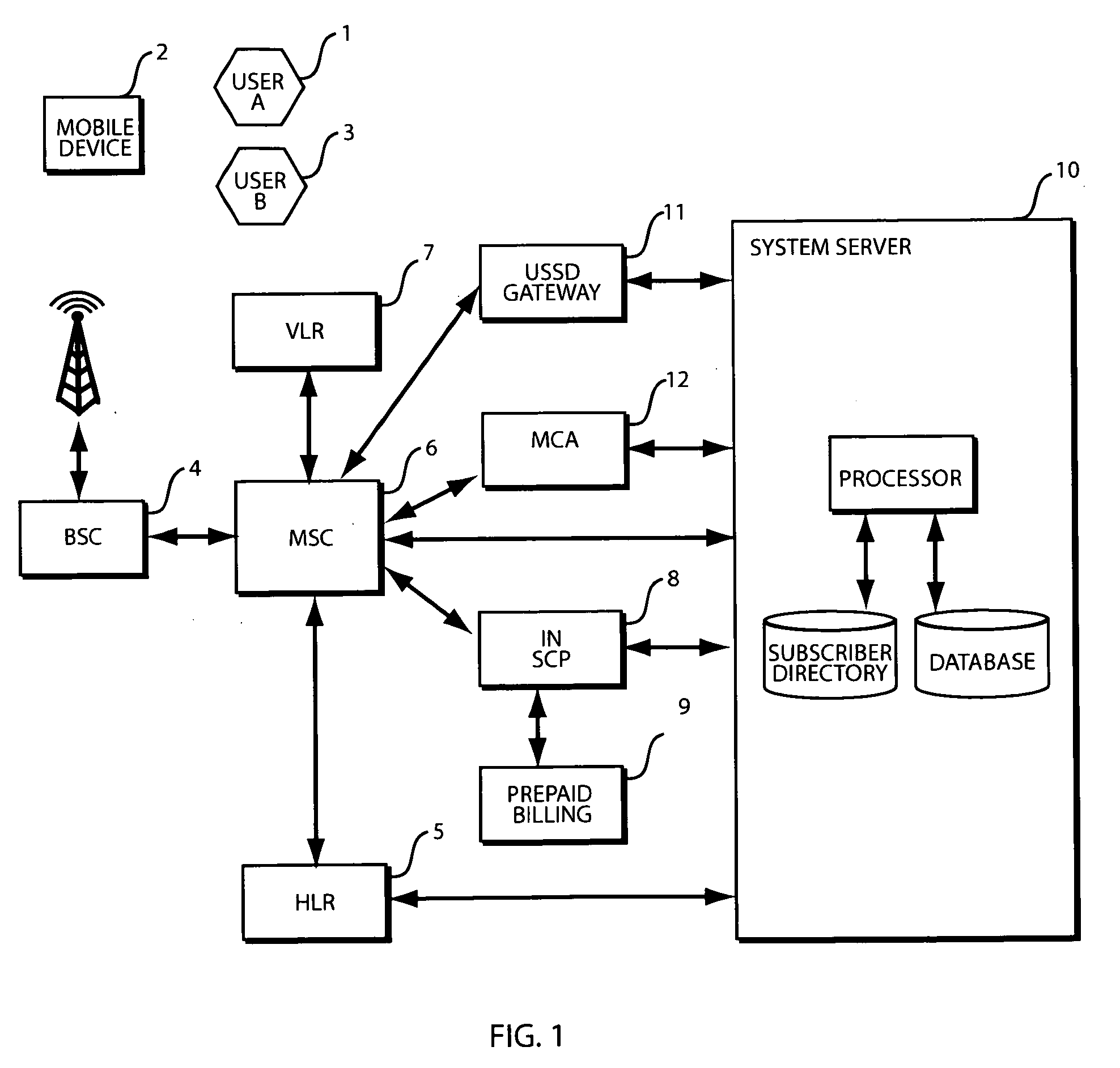
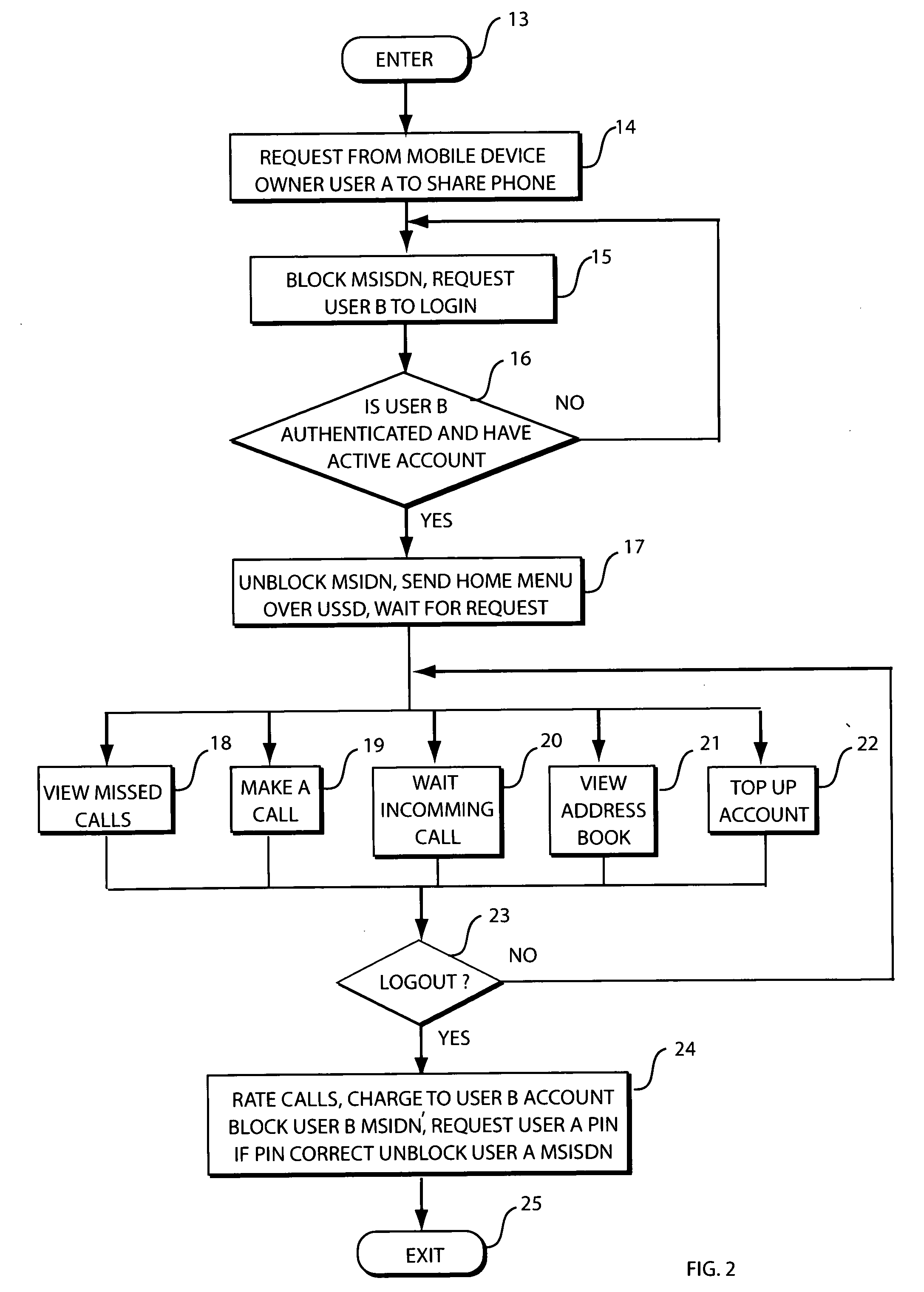
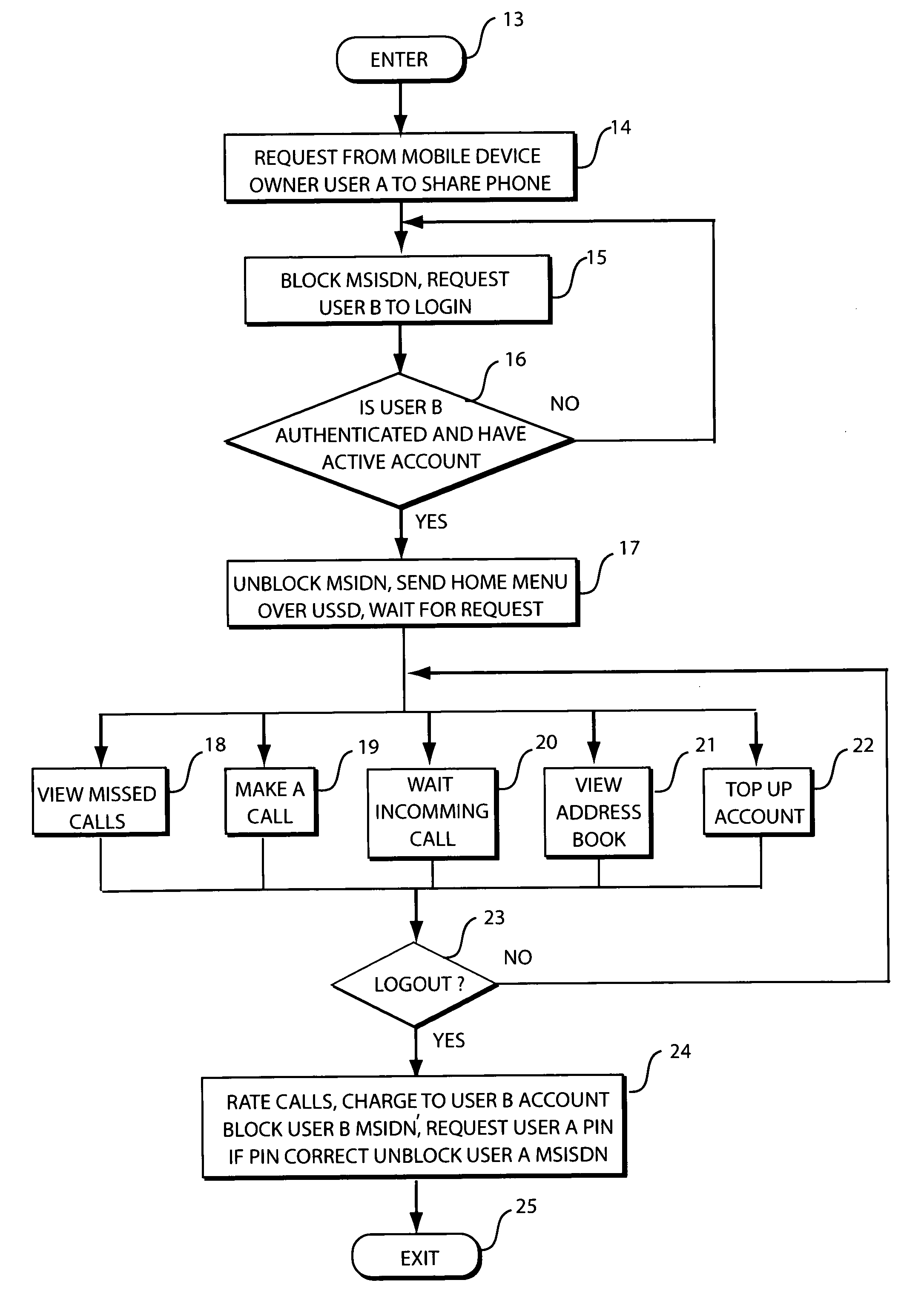
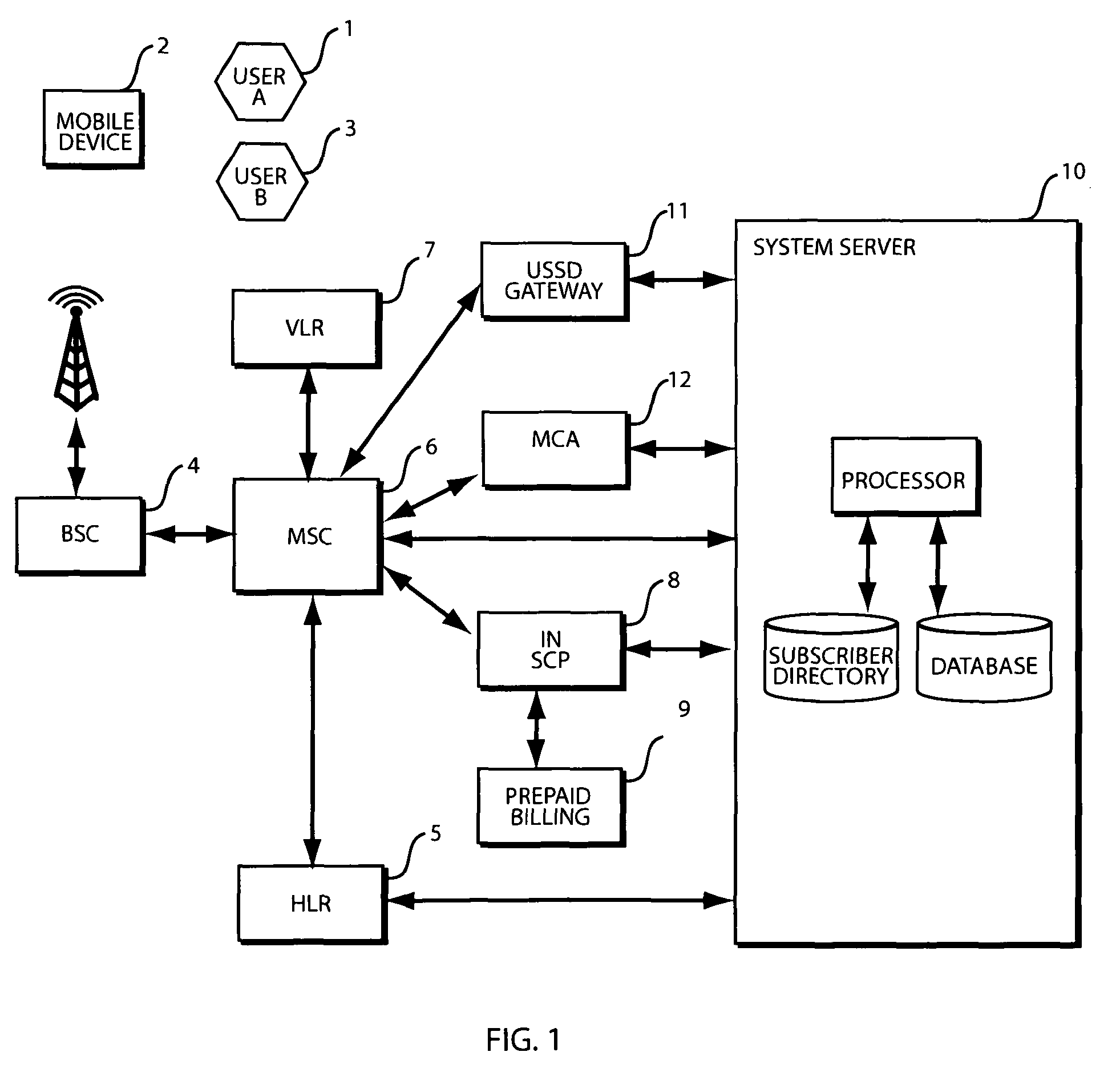
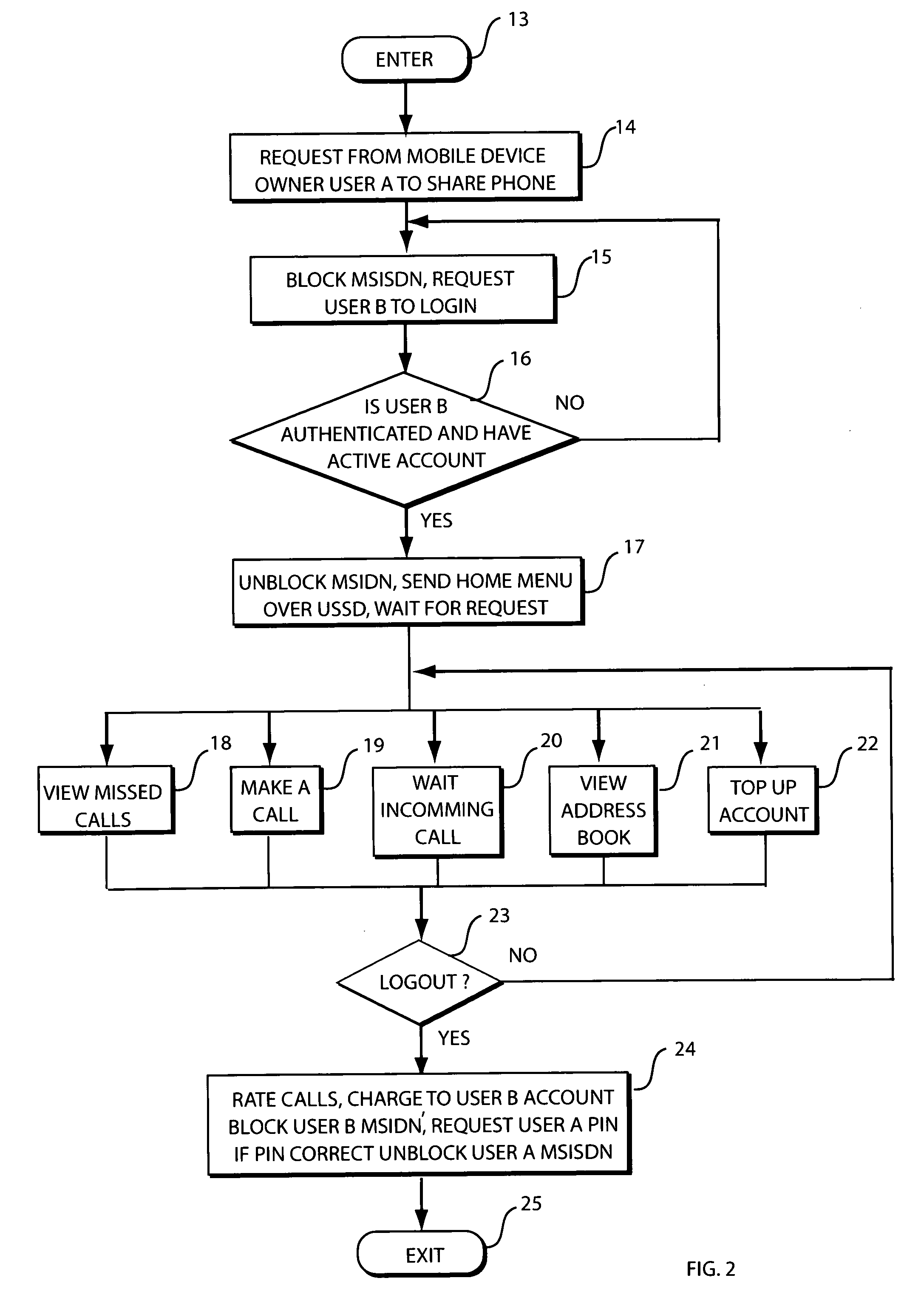
Method and system for enabling personalised shared mobile phone usage
ActiveUS20090227229A1Low costEnsuring privacyMetering/charging/biilling arrangementsAccounting/billing servicesHandsetPersonalization
Disclosed is a system and method for enabling personalised shared mobile phone usage within a wireless telecommunications network, including an illustrative application of the invention as it relates to mobile subscribers who cannot afford a mobile phone handset in the emerging markets. For instance, a prepaid wireless subscriber can be provisioned on a wireless network without the need for a mobile phone handset or SIM but with a personal phone number. The subscriber may access his account and invoke the system by keying in an Unstructured Supplementary Service Data (USSD) short code followed by his account number on a borrowed handset to access a personalised menu sent from the system over the network. Key features of the disclosure are the very low cost of entry and the ability for a subscriber to access the system from any GSM MAP2+ handsets without the need for any modification or downloading of applications.
Owner:BLACKBERRY LTD
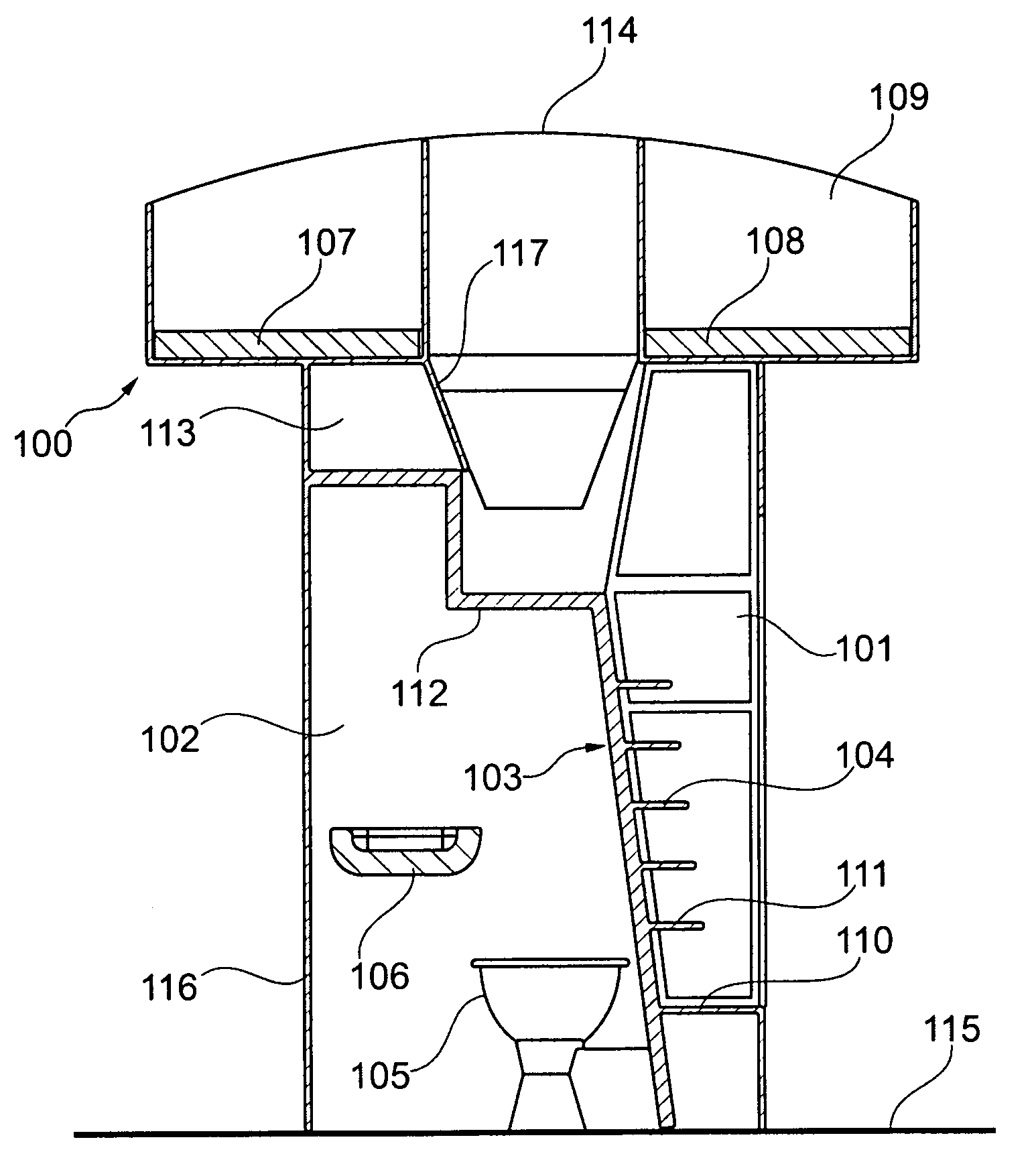
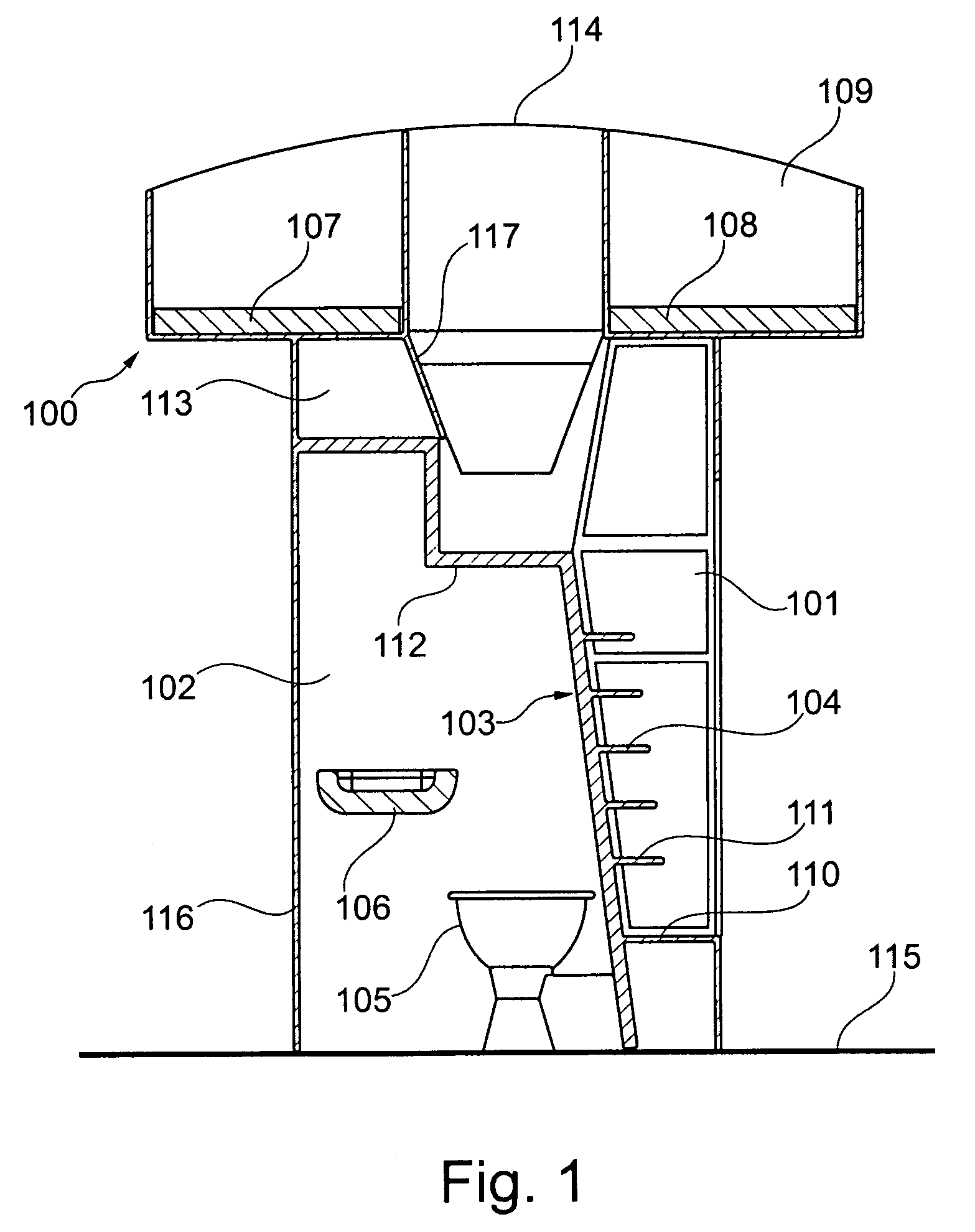
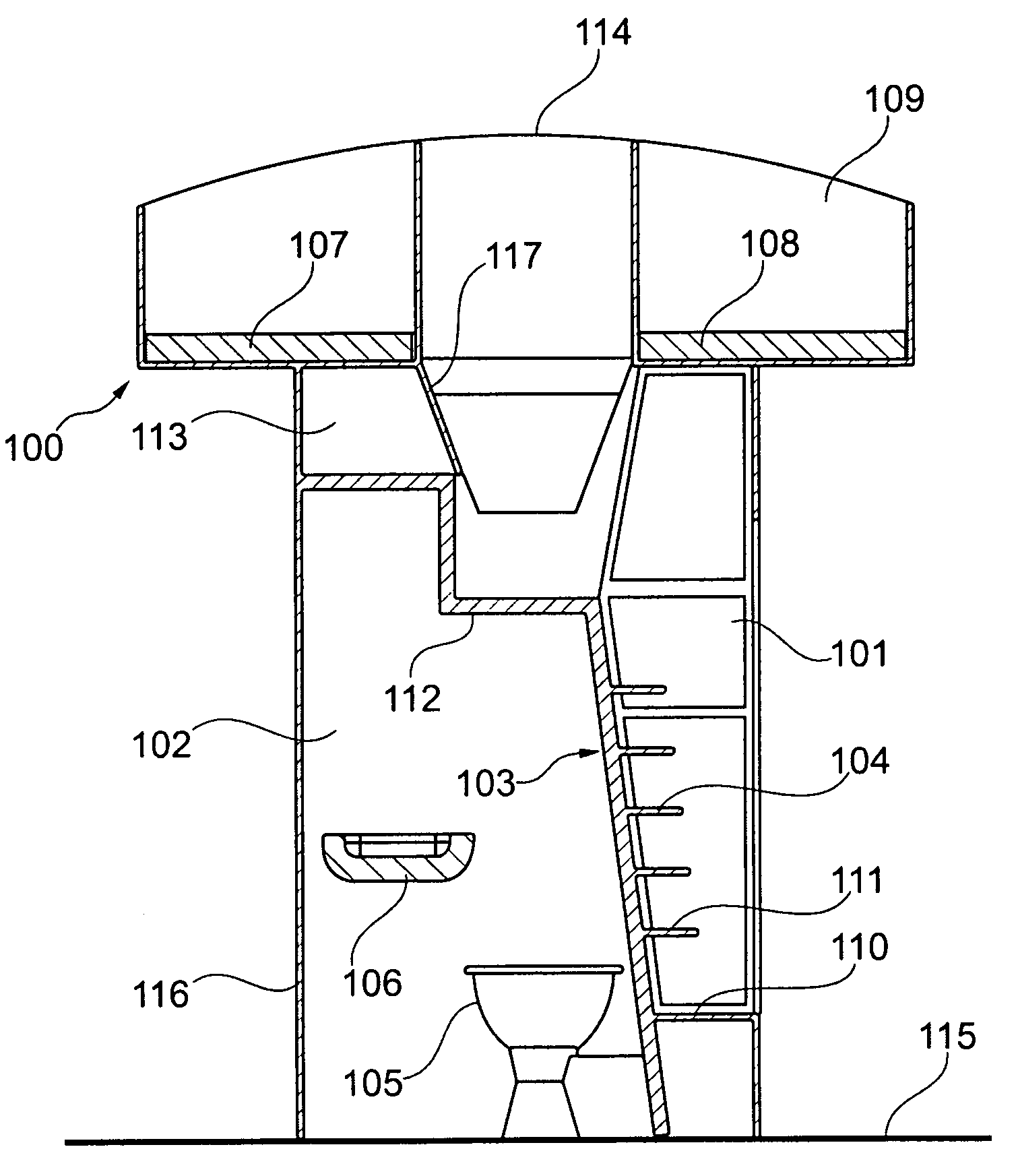
Combined module for an aircraft
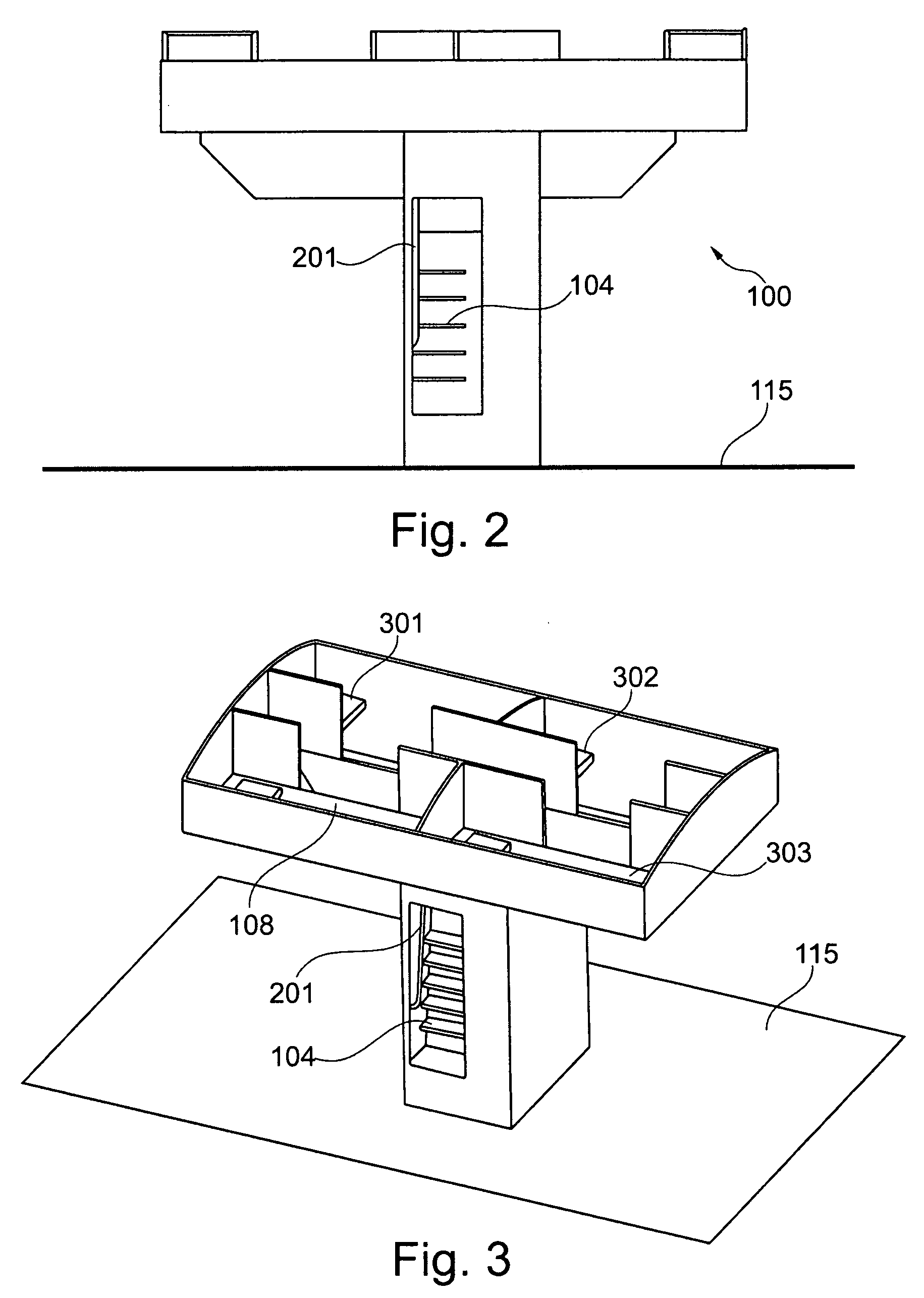
ActiveUS20090050738A1Save spaceAccommodation regionAir-treatment apparatus arrangementsWeight reductionOn boardIn vehicle
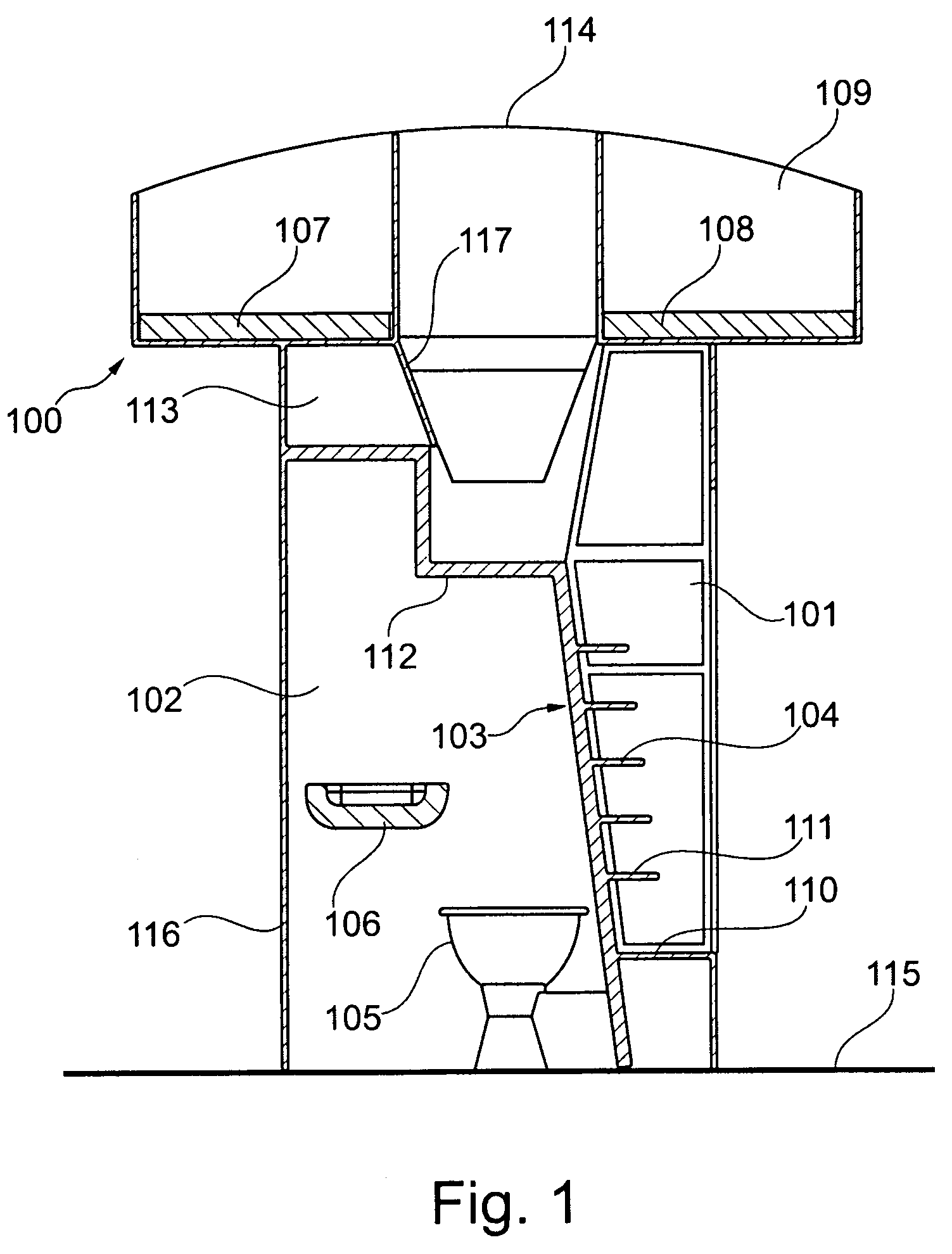
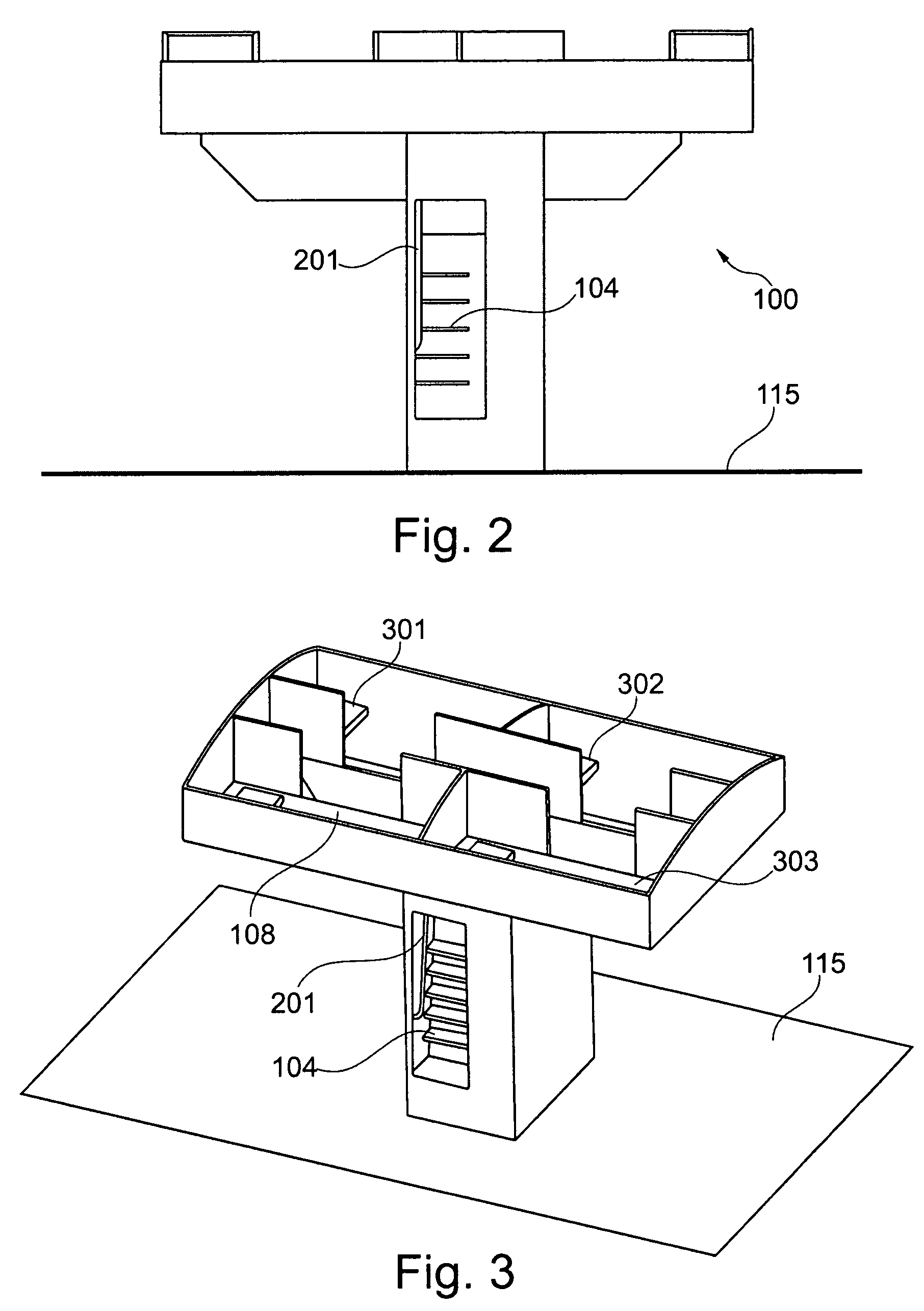
A module for an aircraft for accessing an upper region of the aircraft includes both an ascent region and an accommodation region, with the regions being divided from each other by a divider element. The accommodation region may, for example, be designed as an on-board lavatory. In this way it may be possible to do without the provision of an additional lavatory monument.
Owner:AIRBUS OPERATIONS GMBH
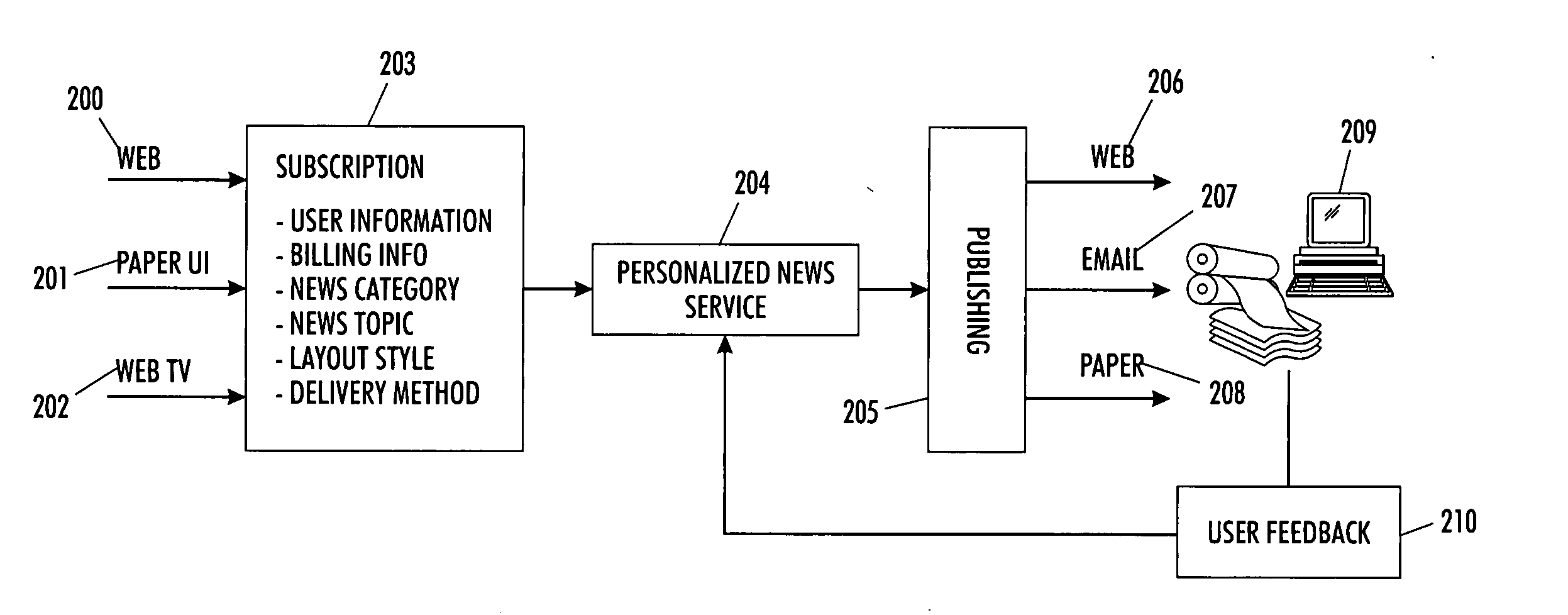
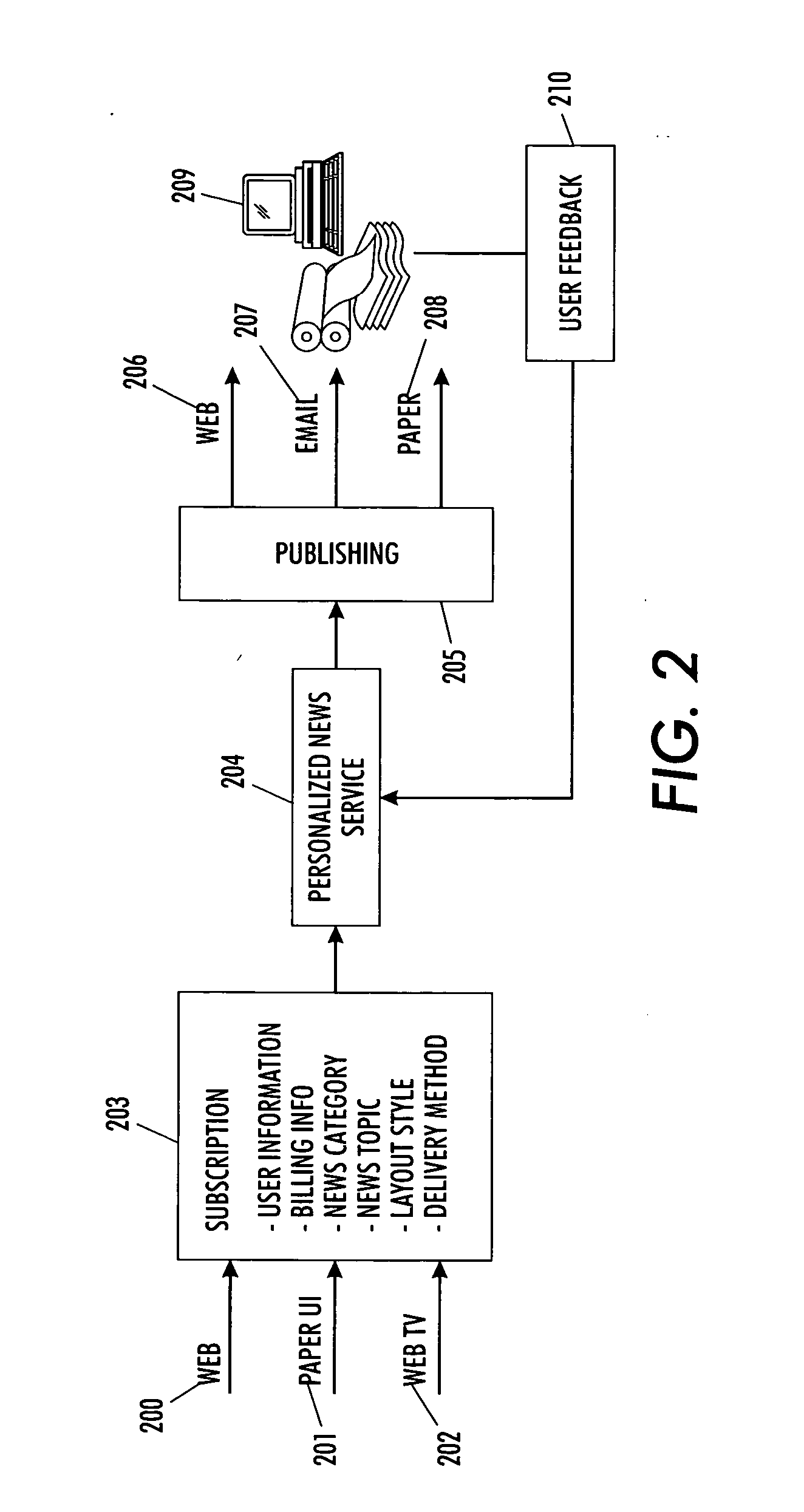
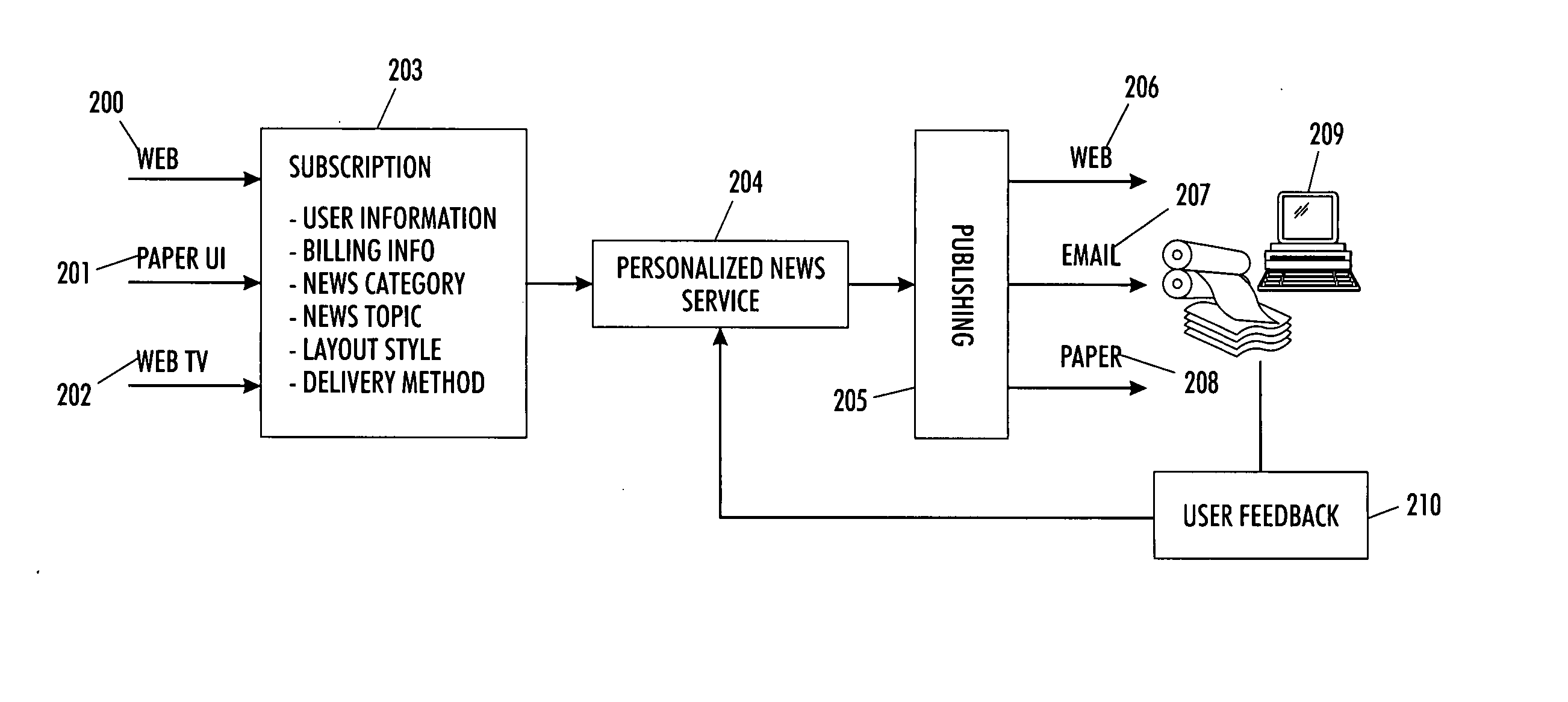
Individually personalized customized report document system
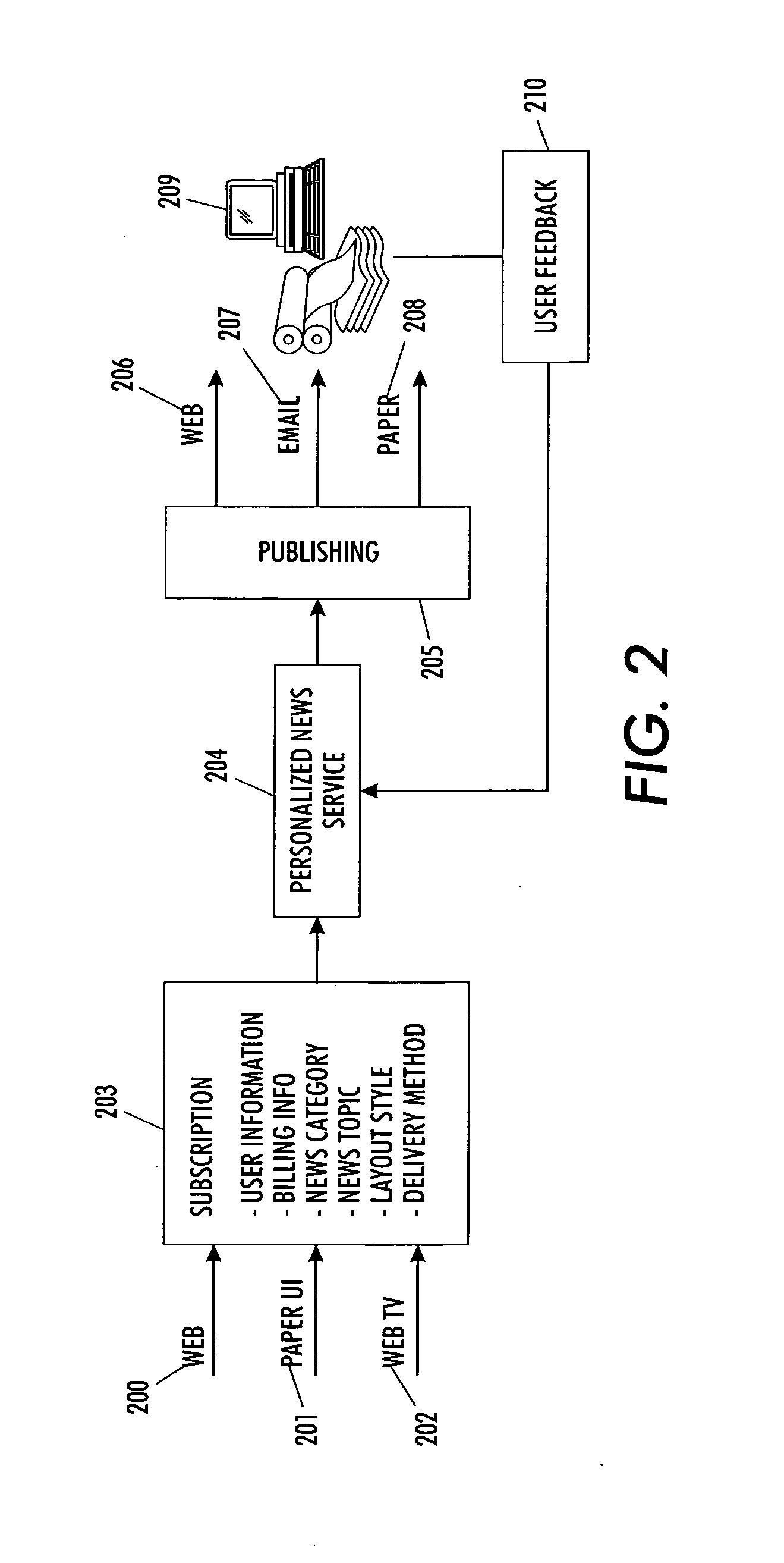
InactiveUS20060048053A1Effective informationEnsuring privacyDigital data information retrievalSpecial data processing applicationsPersonalizationPaper document
A system and methodology is provided herein employing automated search, filtering, and automated document layout technologies conjoined with various delivery options to provide an end-to-end information push service. As such, it enables complete personalized custom report documents to be automatically created, thereby reducing cost in existing personalized document workflows, as well as enabling documents to be created that increase consumer satisfaction and knowledge worker productivity. One example deployment manifestation of the teachings provided yields a personal newspaper embodiment.
Owner:XEROX CORP
System for restricted biometric access for a secure global online and electronic environment
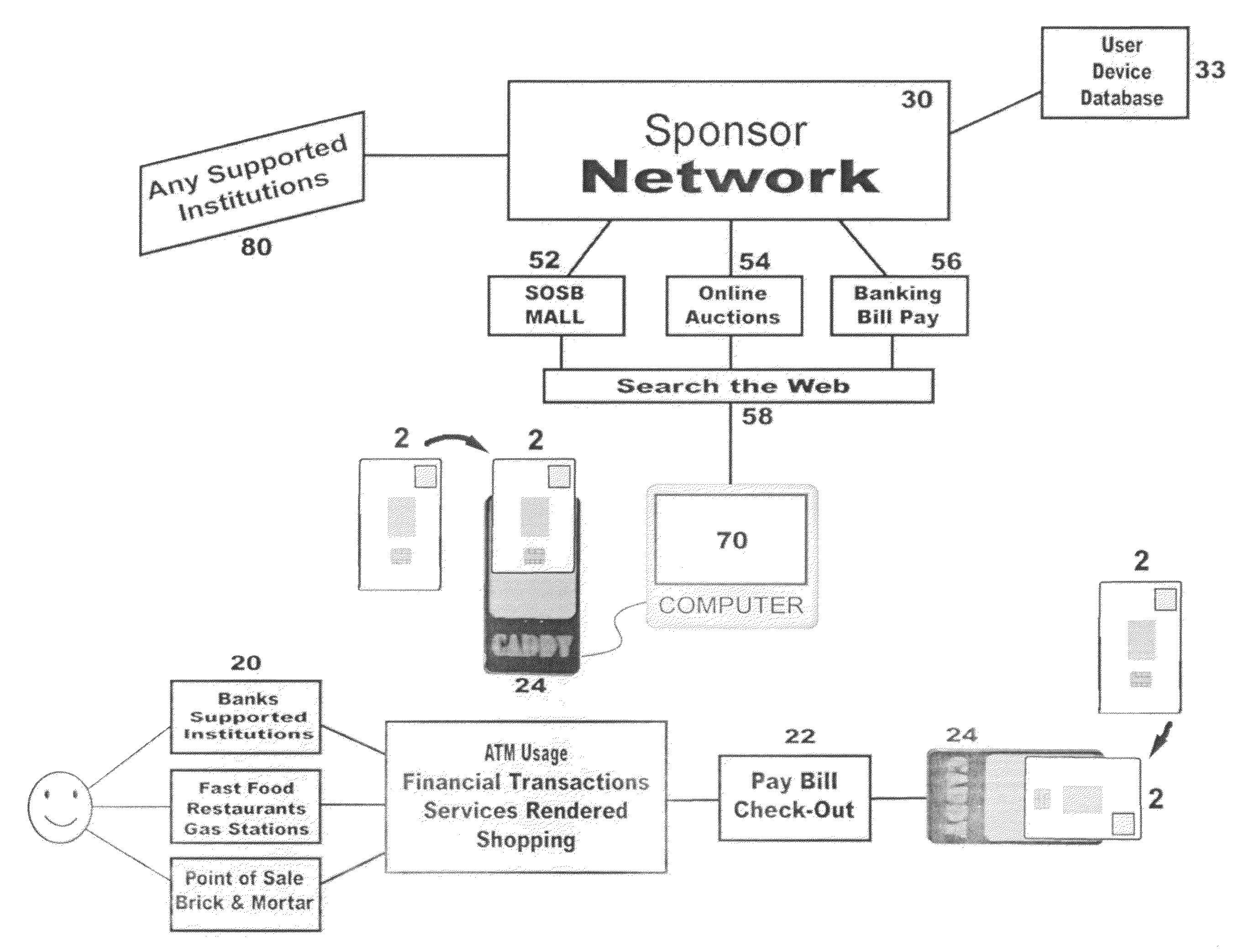
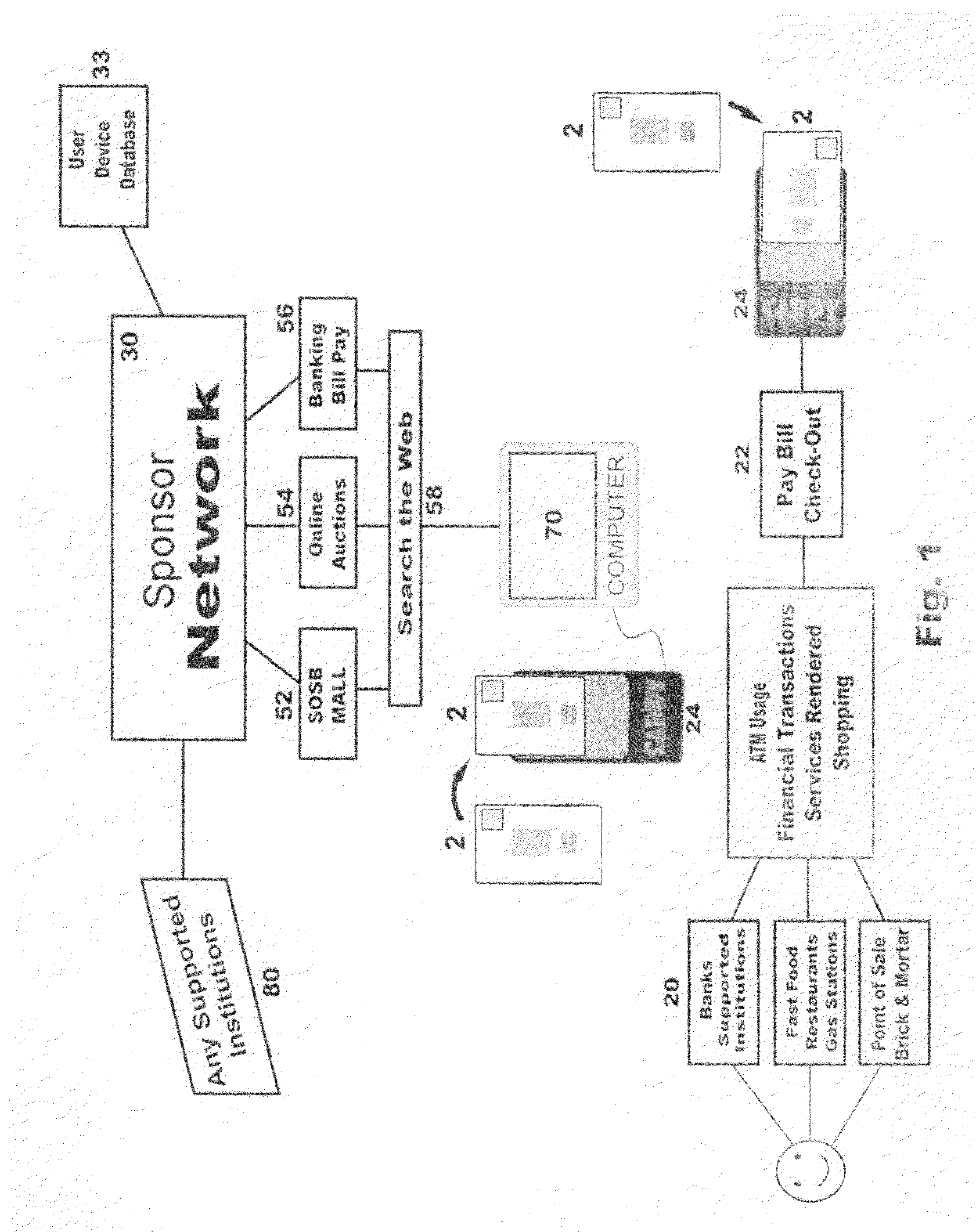
InactiveUS20120032782A1Easy to useFraudulent useElectric signal transmission systemsImage analysisIdentification deviceBiological activation
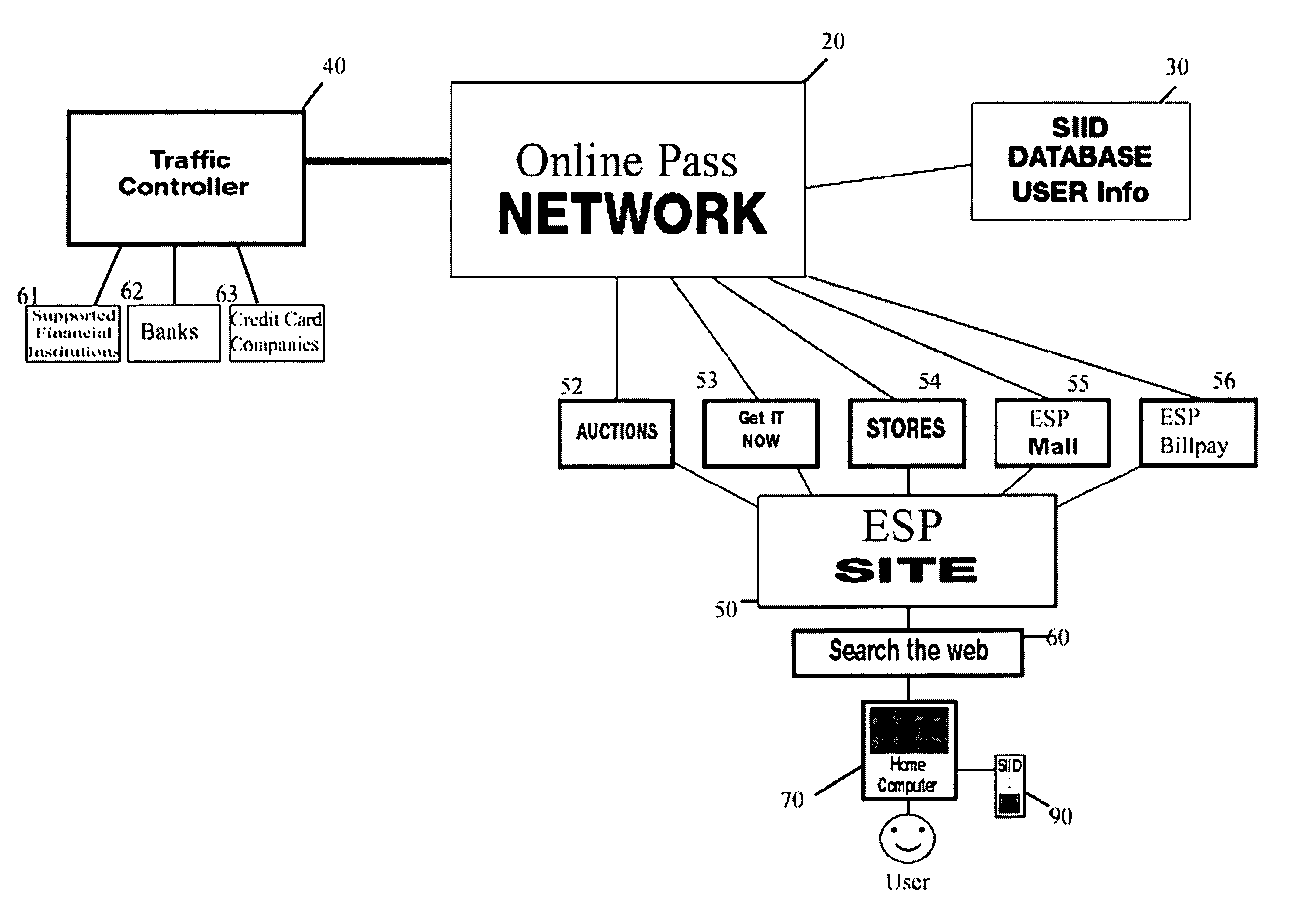
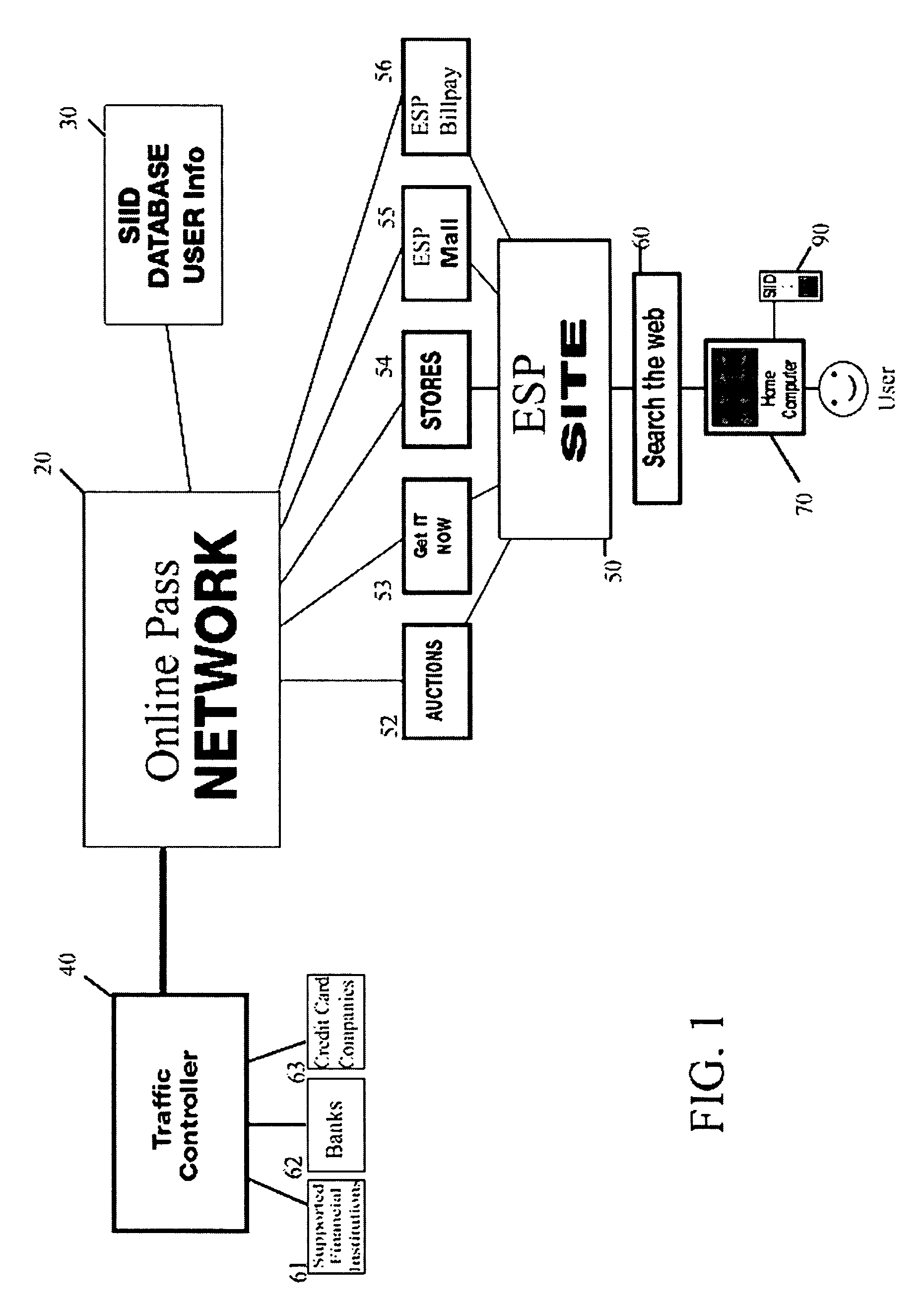
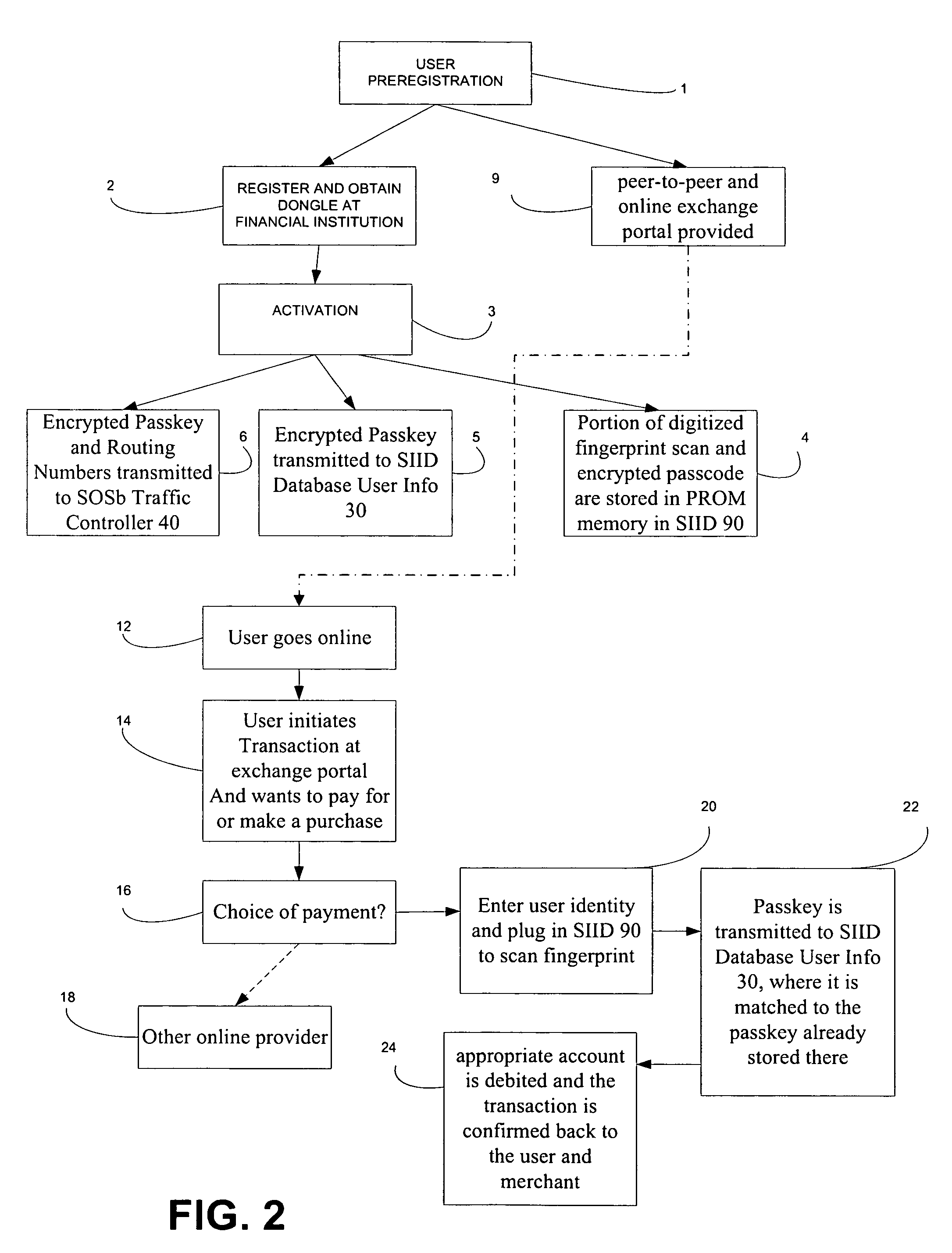
A method and system for biometric-secure settings that also simplifies the checkout process and eliminates fraudulent transactions. The system relies on an exchange service provider (RAGE) that hosts multiple servers: one implementing a web portal for secure online banking, auctions and other exchange opportunities, another being a biometric fingerprint device authenticating database, and yet another being a transaction traffic manager. Participating banks and supporting institutions distribute and activate Secure Individual Identity Devices (SIIDs) to registered users, each SIID being a portable biometric activated identification device that locally stores a fraction of the enrolled users fingerprint (minutia) along with an encrypted code that is used to verify and authenticate the user, eliminating the use of personal or financial information for this purpose. The SiiD becomes the user's own personal key for completing secure online transactions. The user simply plugs their SiiD into any equipped device for activation and scans their own fingerprint for each transaction. The encrypted codes are authenticated in the DSP database and the transaction is processed to the appropriate financial institutions.
Owner:COLELLA BRIAN A
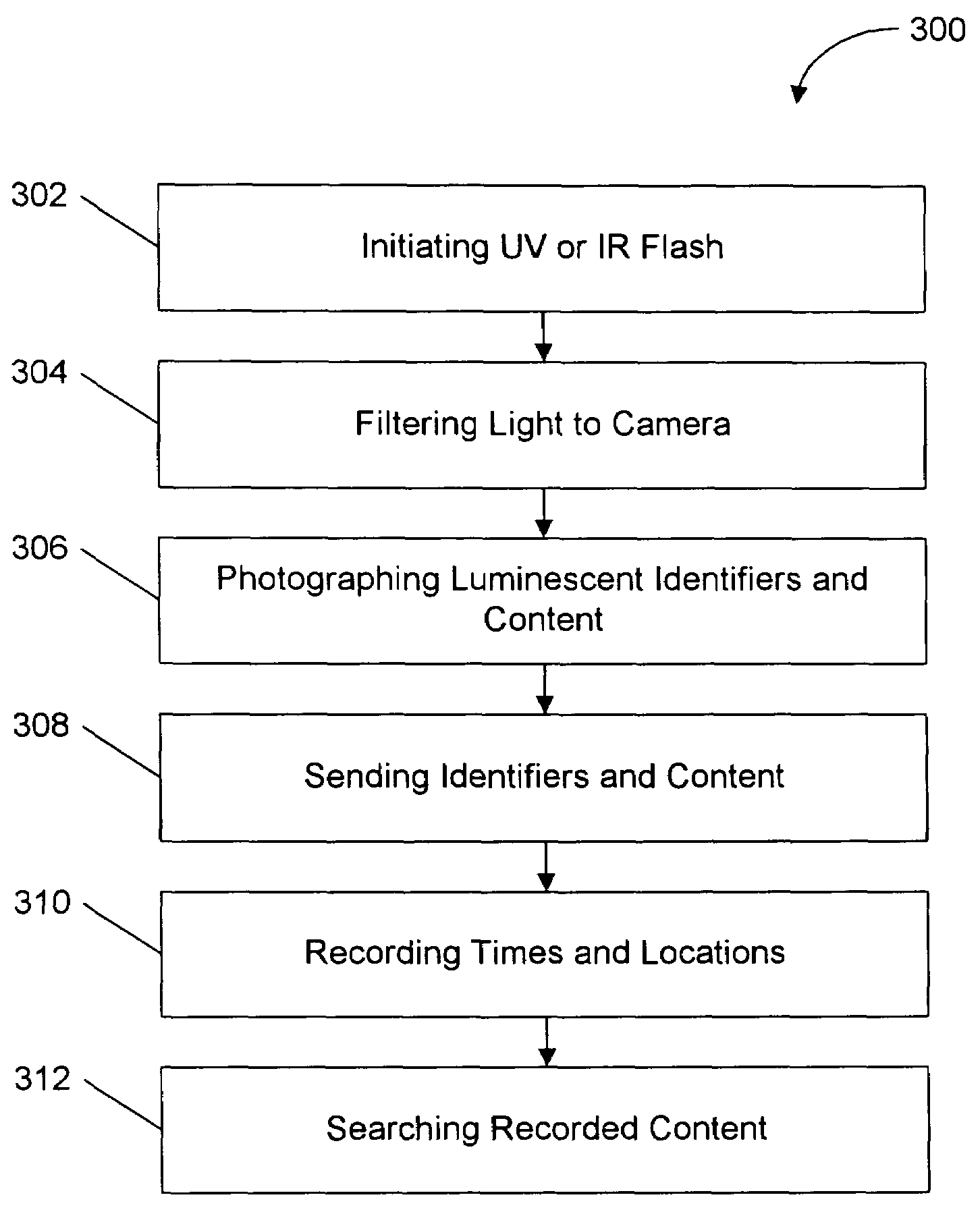
System and method for tracking positions of objects in space, time as well as tracking their textual evolution
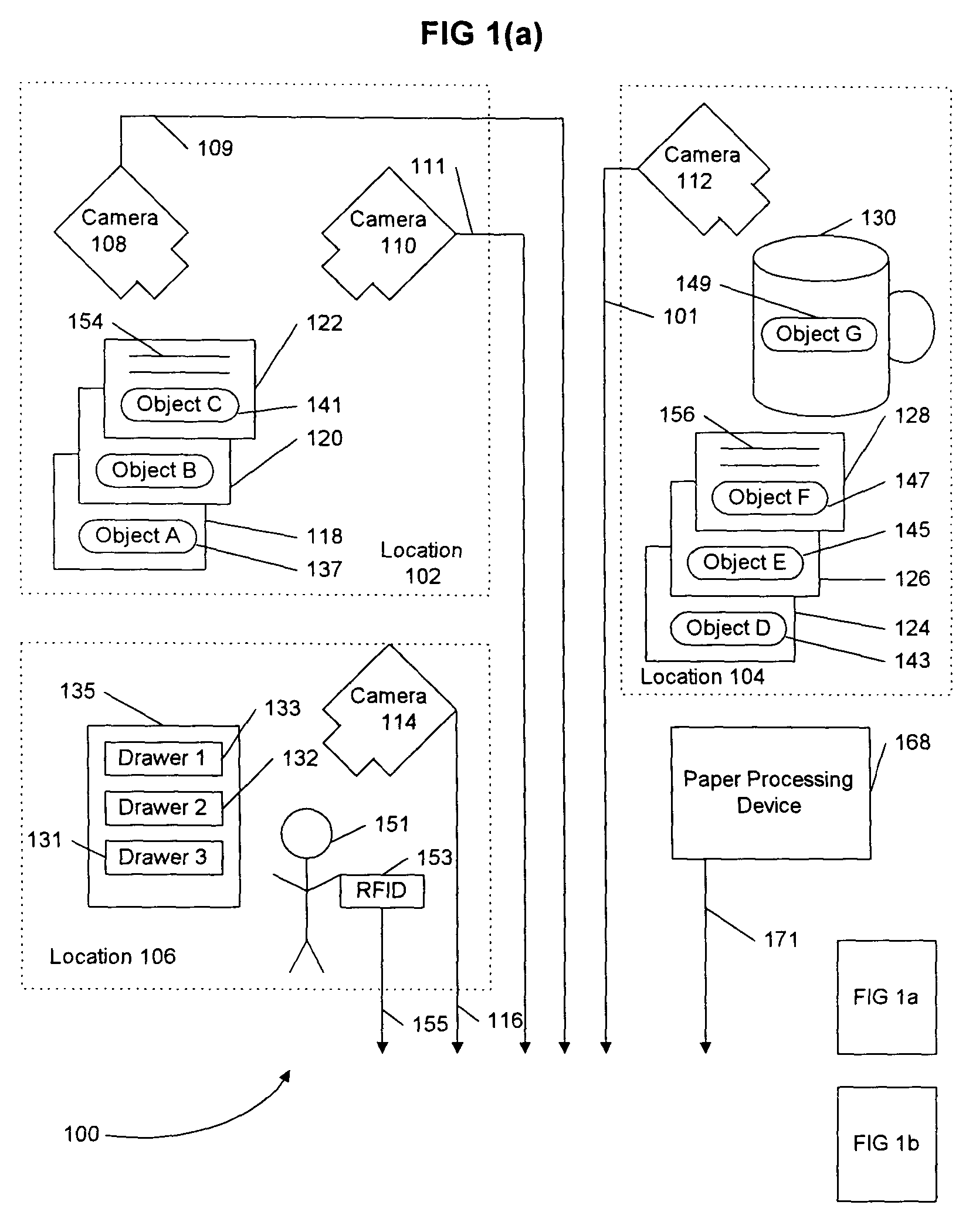
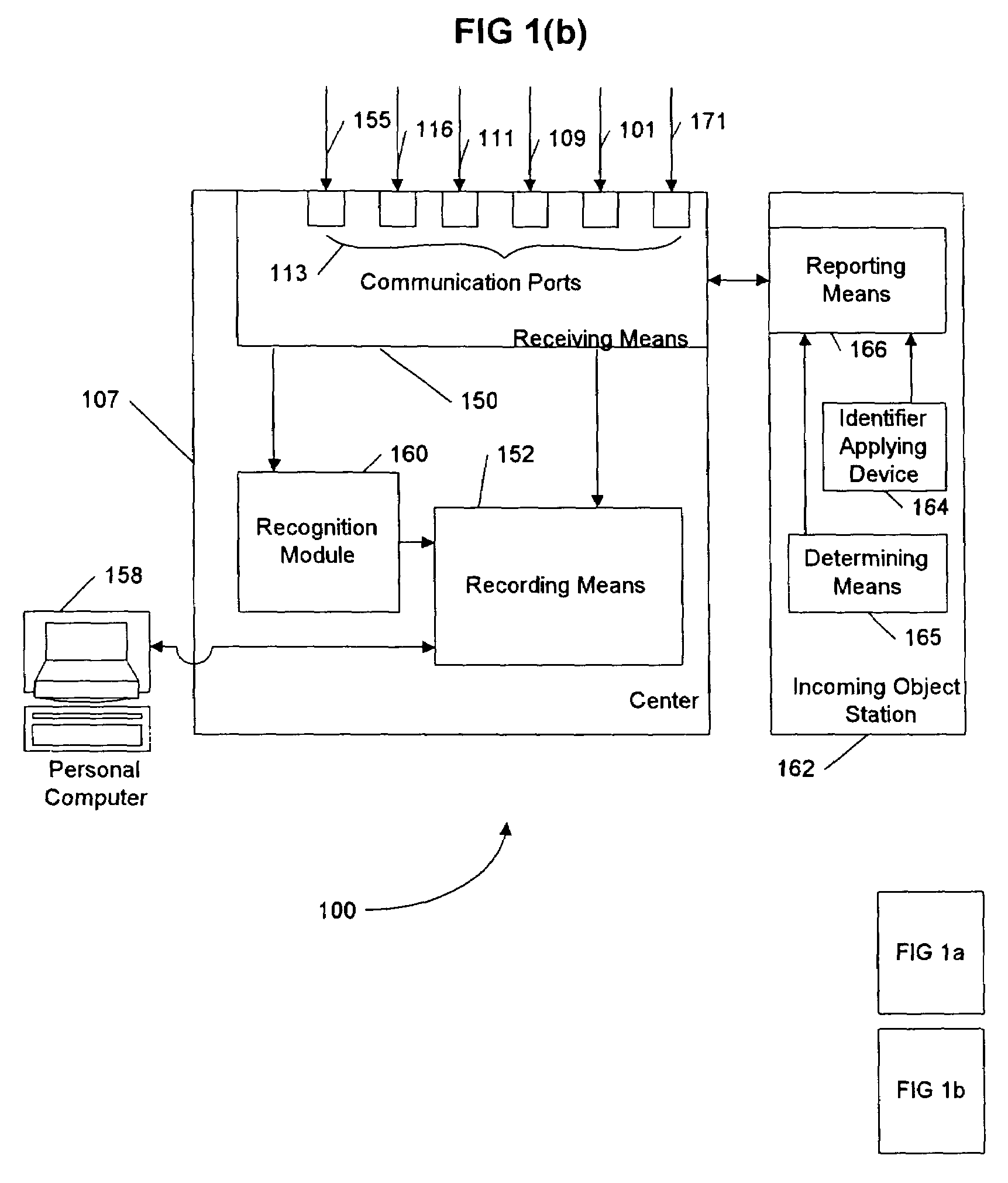
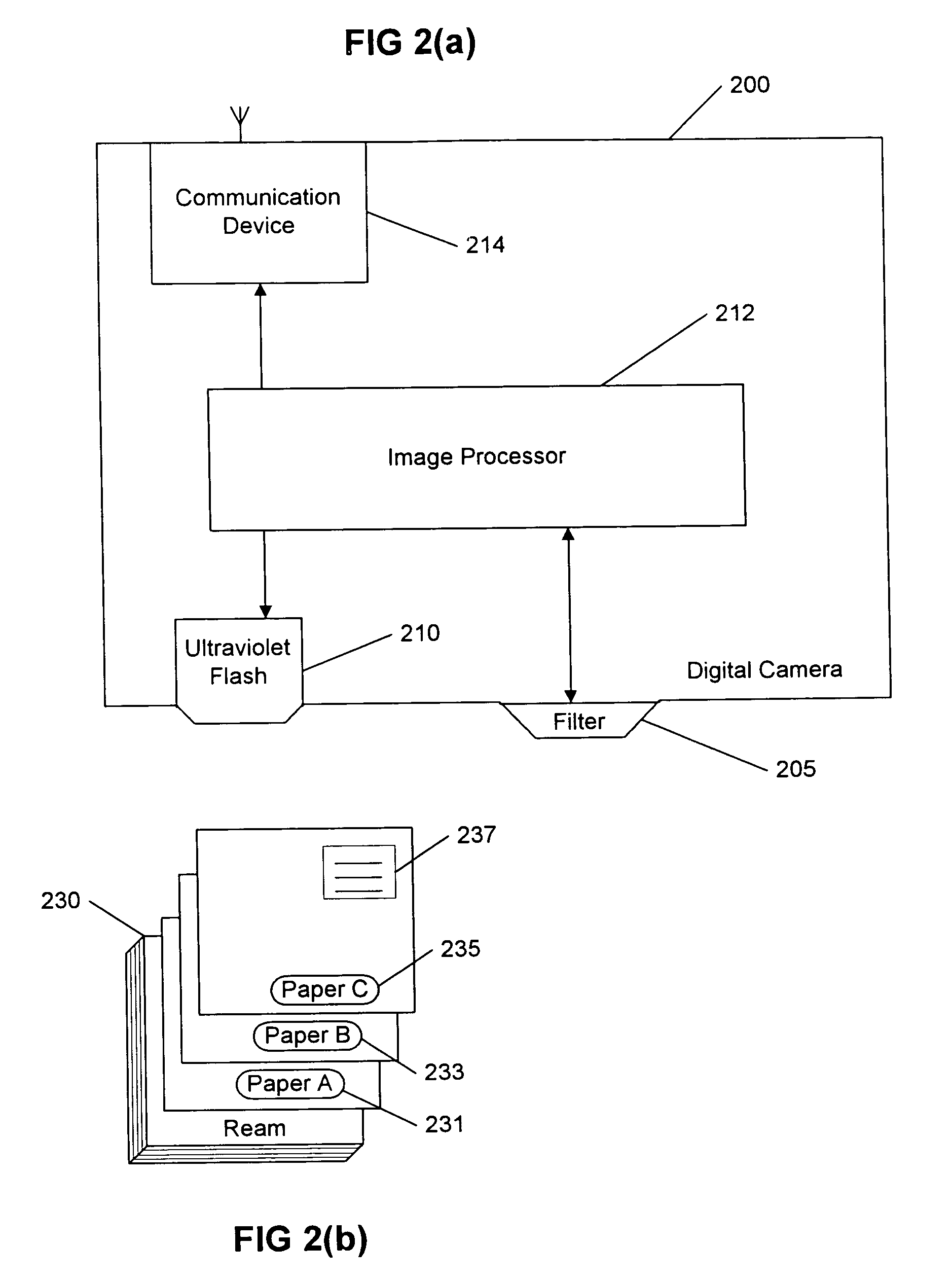
InactiveUS7369681B2Ensuring privacyExact matchTelevision system detailsCharacter and pattern recognitionFluorescenceComputer graphics (images)
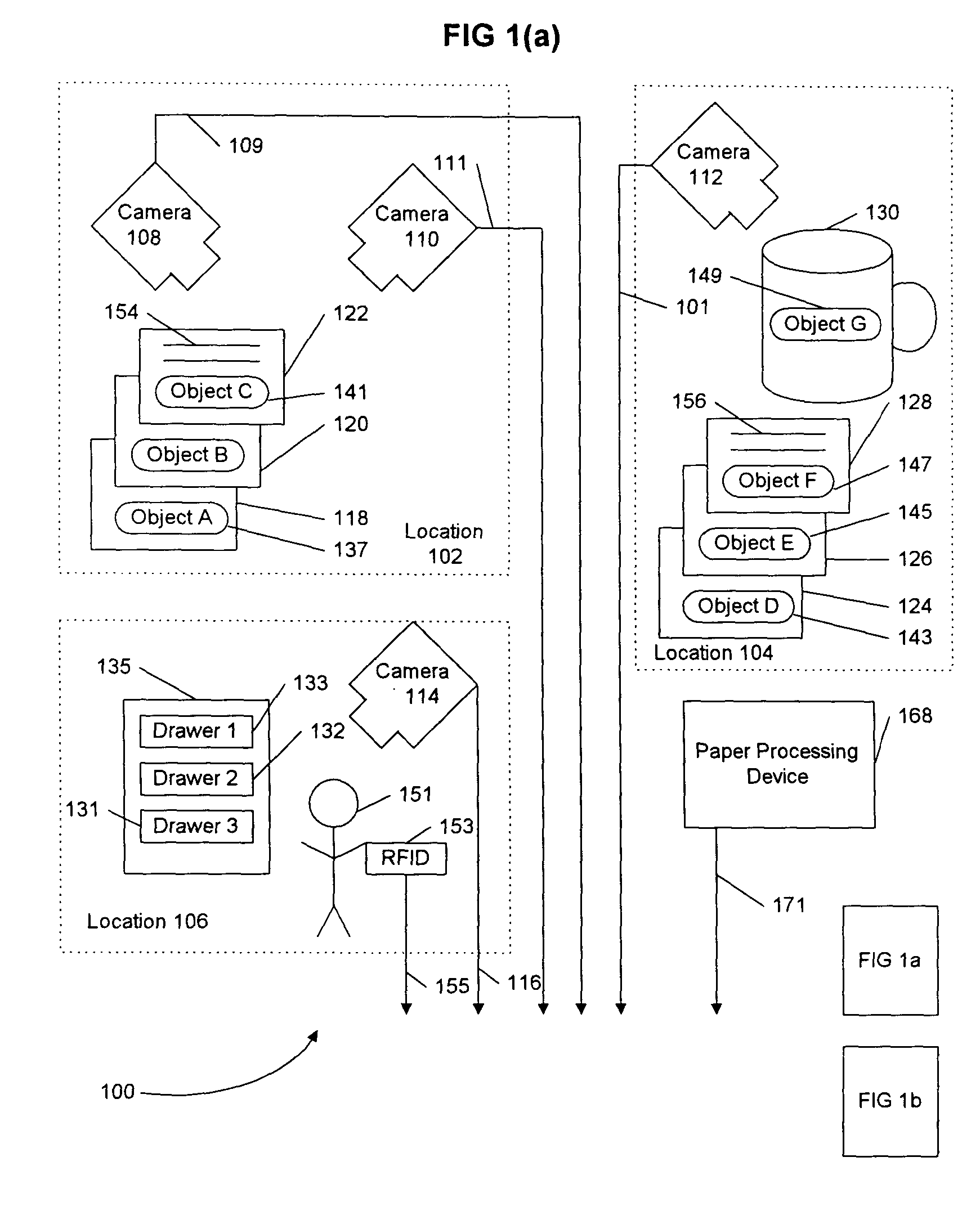
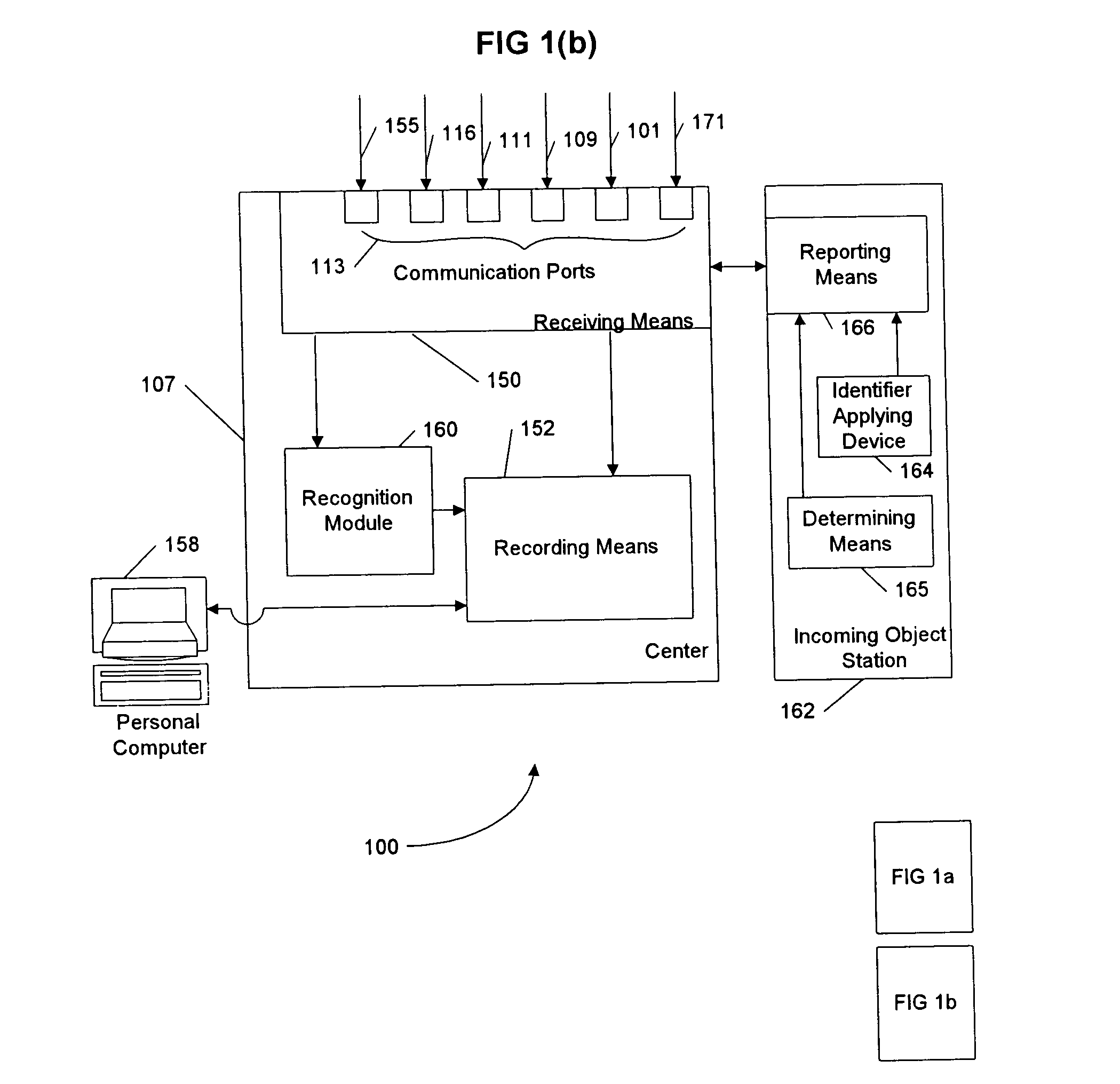
A system and method including cameras for monitoring objects such as documents, at multiple locations, and for recording the objects' movement through space and time. The objects are marked with unique identifiers, and the invention is adaptable for recording and recognizing the objects' development using character recognition. A center receives the information from the cameras, and that information is searchable. Advantageously, the unique identifiers are printed with ink that is invisible unless it fluoresces or phosphoresces, the digital cameras include an ultraviolet flash to cause the identifiers to fluoresce or phosphoresce at a certain wavelength, and the cameras are equipped with filters to filter out wavelengths other than the certain wavelength. Packages or pads of pre-marked blank paper are adaptable for use with the present invention.
Owner:PITNEY BOWES INC
Individually personalized customized report document system with user feedback
InactiveUS20060048042A1Less-costly to produceMinimizing user timeDigital data information retrievalSpecial data processing applicationsPersonalizationPaper document
A system and methodology is provided herein employing automated search, filtering, and automated document layout technologies conjoined with various delivery options to provide an end-to-end information push service. As such, it enables complete personalized custom report documents to be automatically created, thereby reducing cost in existing personalized document workflows, as well as enabling documents to be created that increase consumer satisfaction and knowledge worker productivity. The user satisfaction and productivity is enhanced by tracking the user's actual usage of the report document and feeding that usage back into the user profile. One example deployment manifestation of the teachings provided yields a personal newspaper embodiment which monitors the user usage and provides feedback of that usage to the system methodology thus dynamically altering any subsequently delivered custom report documents.
Owner:XEROX CORP
System for secure payment and authentication
InactiveUS7778935B2Ensuring privacySimple processDebit schemesIndividual entry/exit registersOn boardBiological activation
A system and method for biometric-secure point-of-sale or online transactions and / or authentication and ID verification for restricted access that simplifies the checkout process and eliminates fraudulent transactions. The system employs a credit-card-sized device with integral fingerprint reader, on-board memory with pre-designated card number, infrared coder, power strip, plus at least one magnetic strip (encoded with designated financial account to be used for transactions, including routing number), one magnetic strip for personal medical and identification information and a bar code and photo ID for security. The card scanner is activated by an activation scan in which a subset of “minutia” are stored locally. To consummate a transaction (after registration), the user simply plugs their card scanner into a multi-function reader, and scans their own fingerprint. Upon authentication the card transmits the card / user ID to the reader as authentication of the transaction, the reader reads the encoded account numbers and routing information, offers a choice of account to charge to, verifies the total charge and completes the transaction. The process is fully secure.
Owner:COLELLA BRIAN A
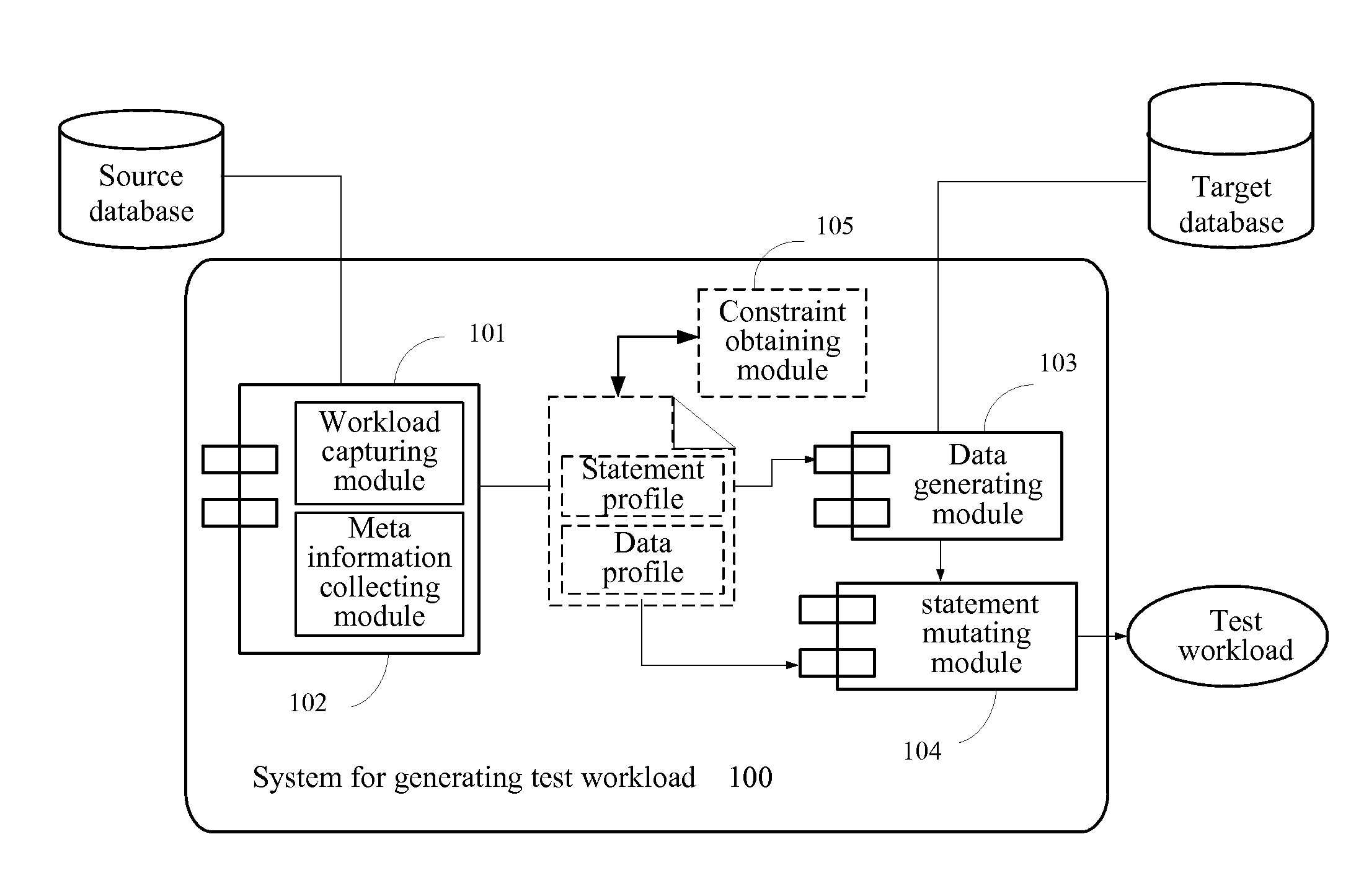
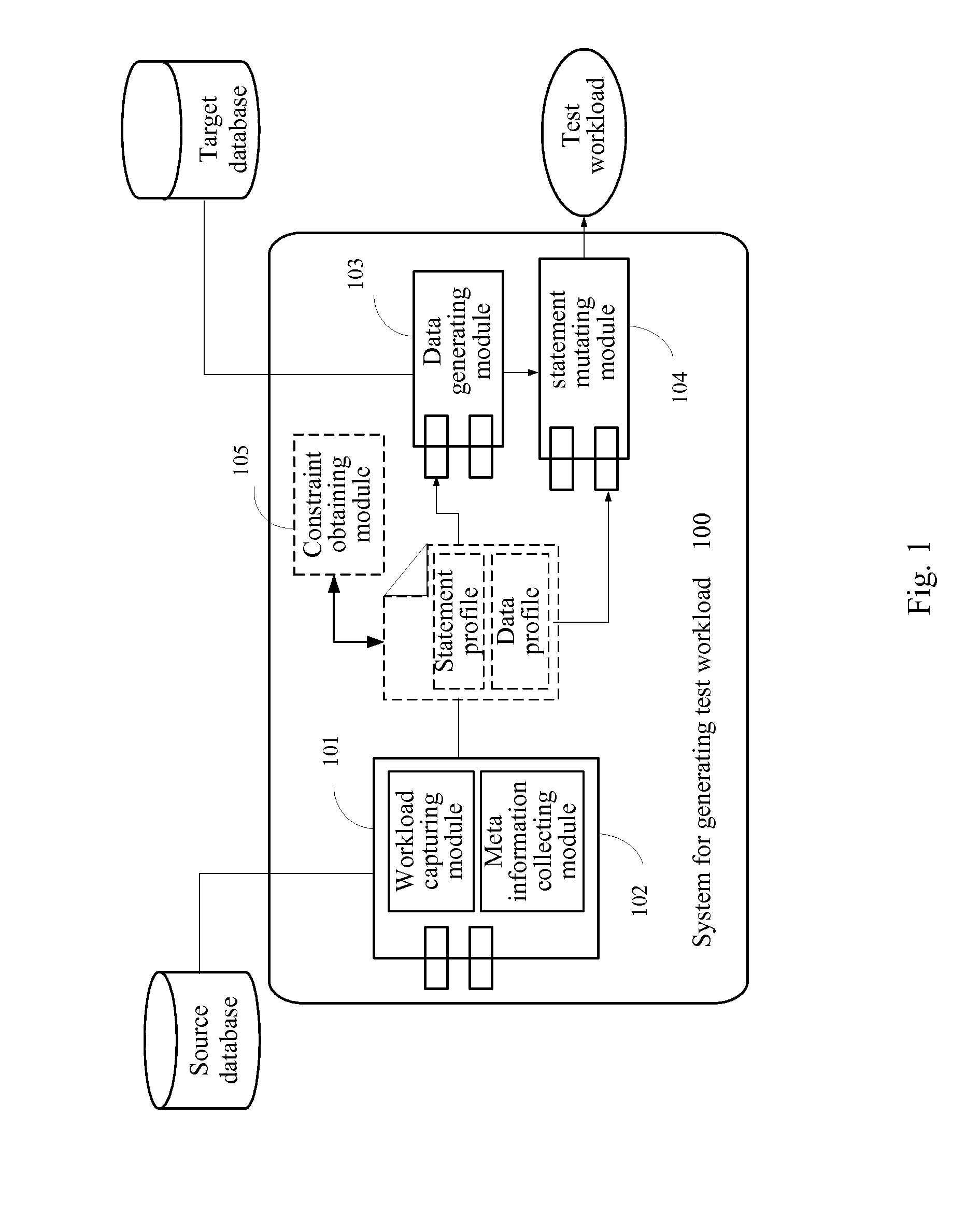
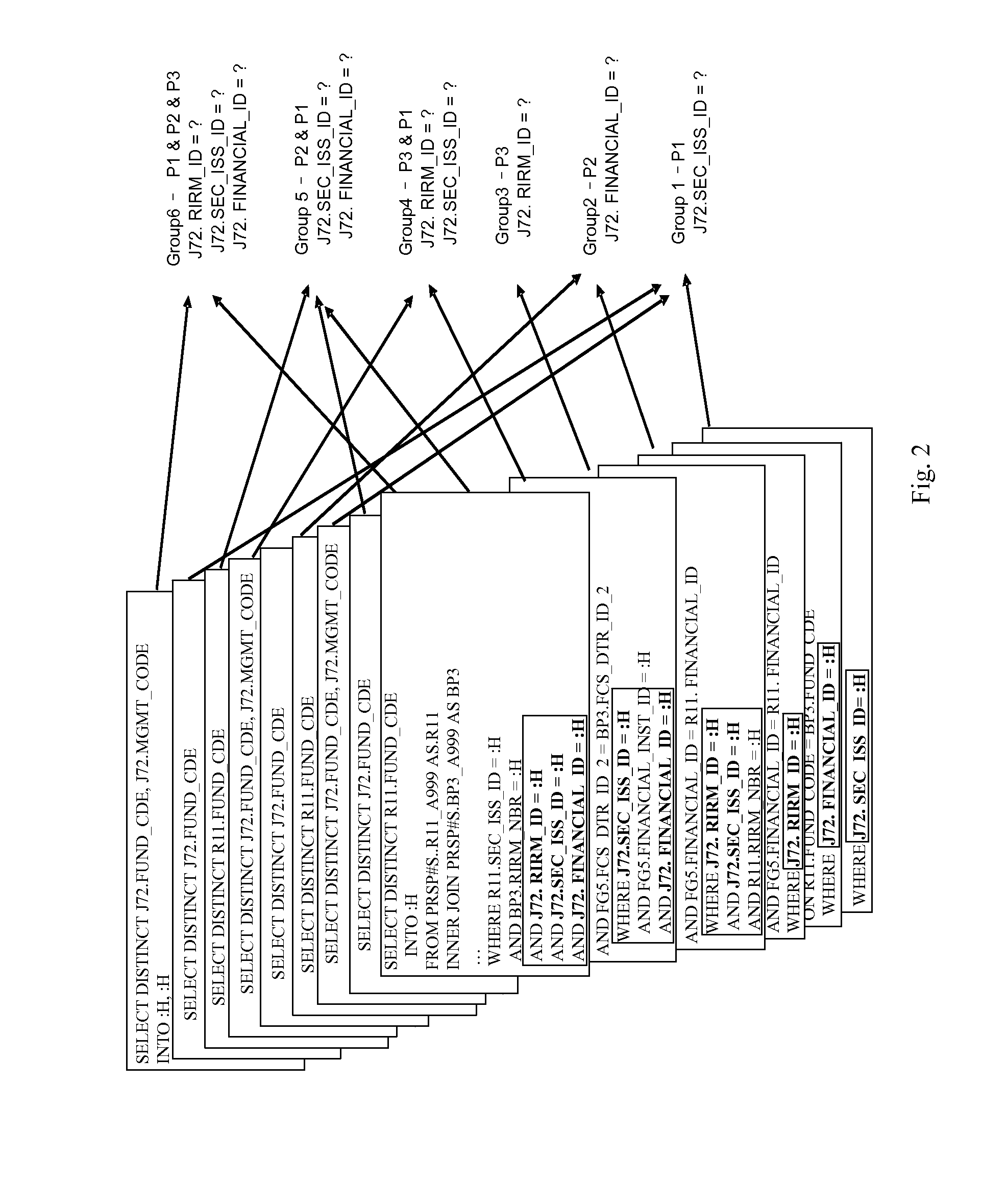
Generating a test workload for a database
InactiveUS20130159353A1Ensuring privacyDigital data processing detailsError detection/correctionWorkloadData treatment
A method of transferring files in a data-processing network using a current node within the network includes reading an outbound content and outbound characteristics of an outbound file. An outbound message is created having outbound strings including a first set of the outbound strings representing the outbound characteristics and a second set of the outbound strings representing the outbound content. The outbound message is sent to a receiver node within the network. An inbound message is received from a sender node within the network. The inbound message has inbound strings including a first set of the inbound strings representing inbound characteristics and a second set of the inbound strings representing inbound content. An inbound file having the inbound content is stored, and the inbound characteristics are applied to the inbound file.
Owner:IBM CORP
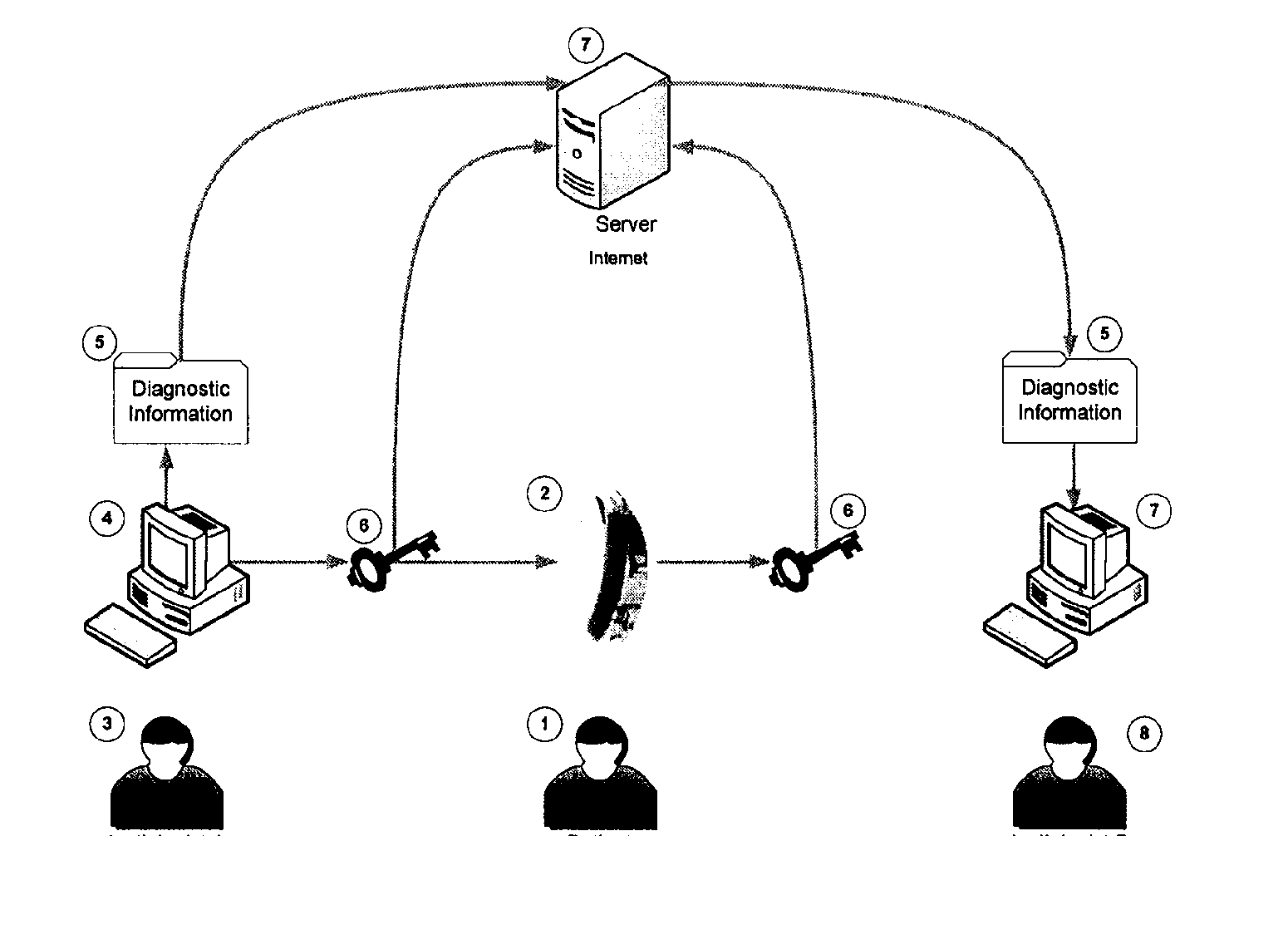
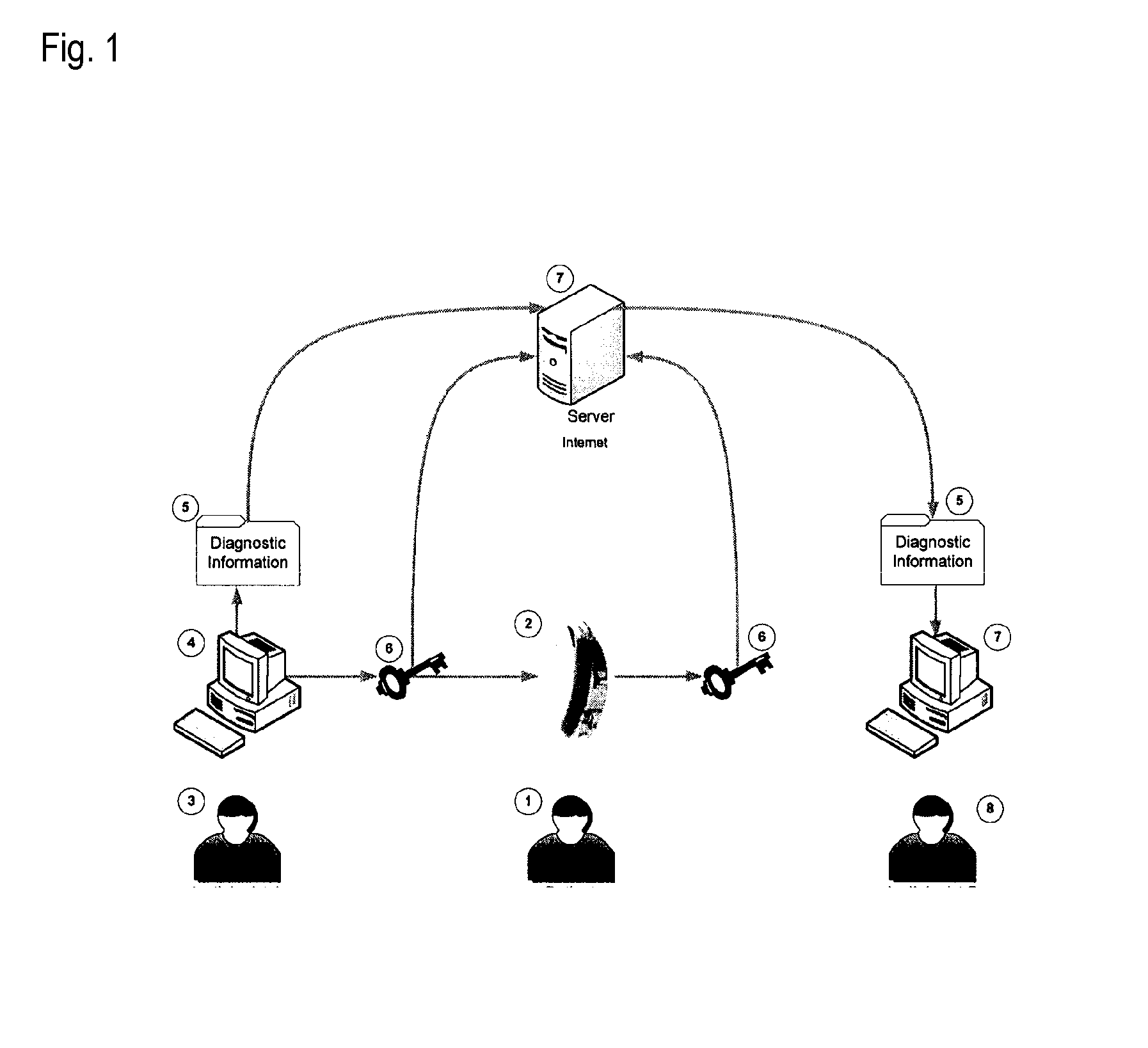
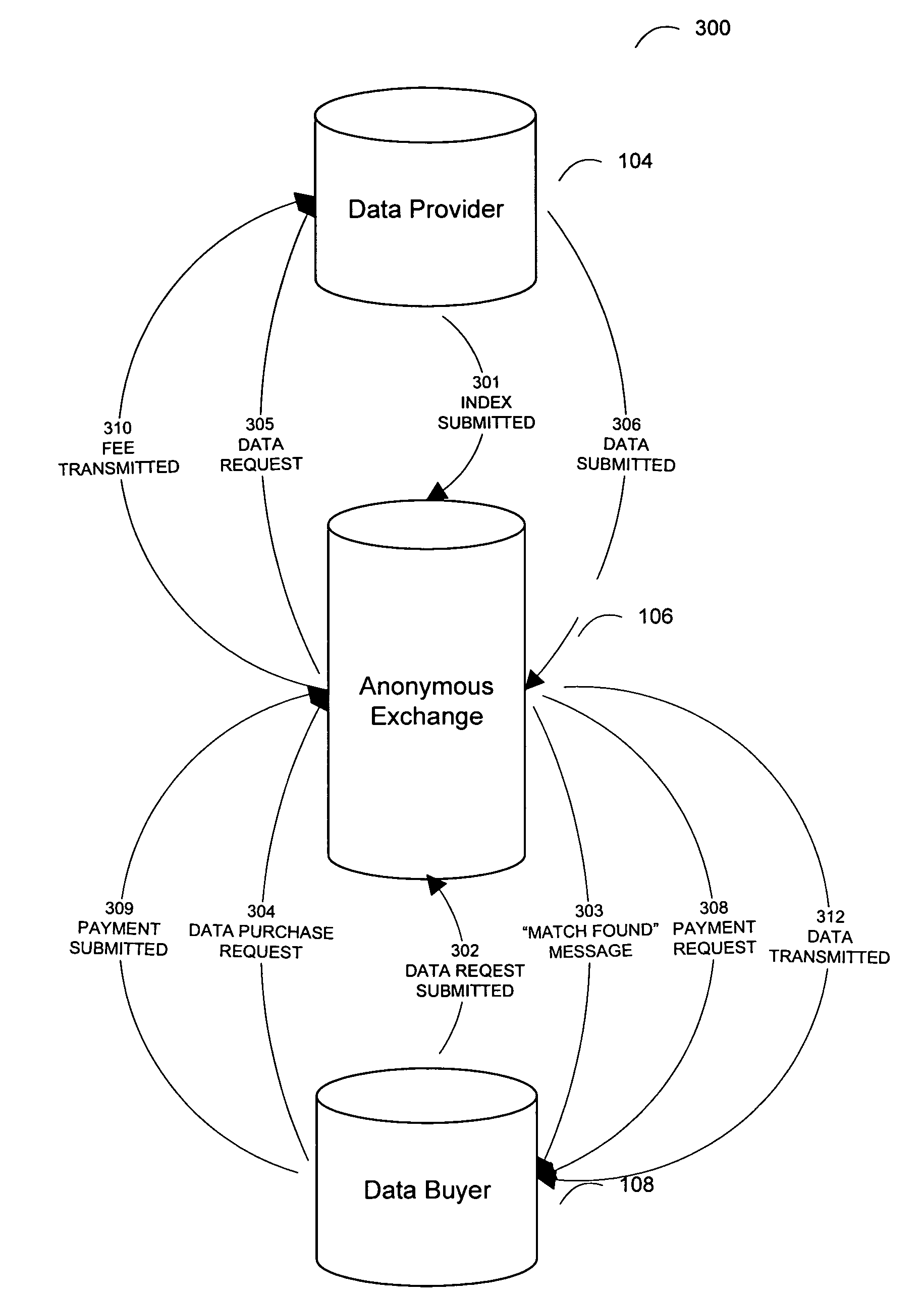
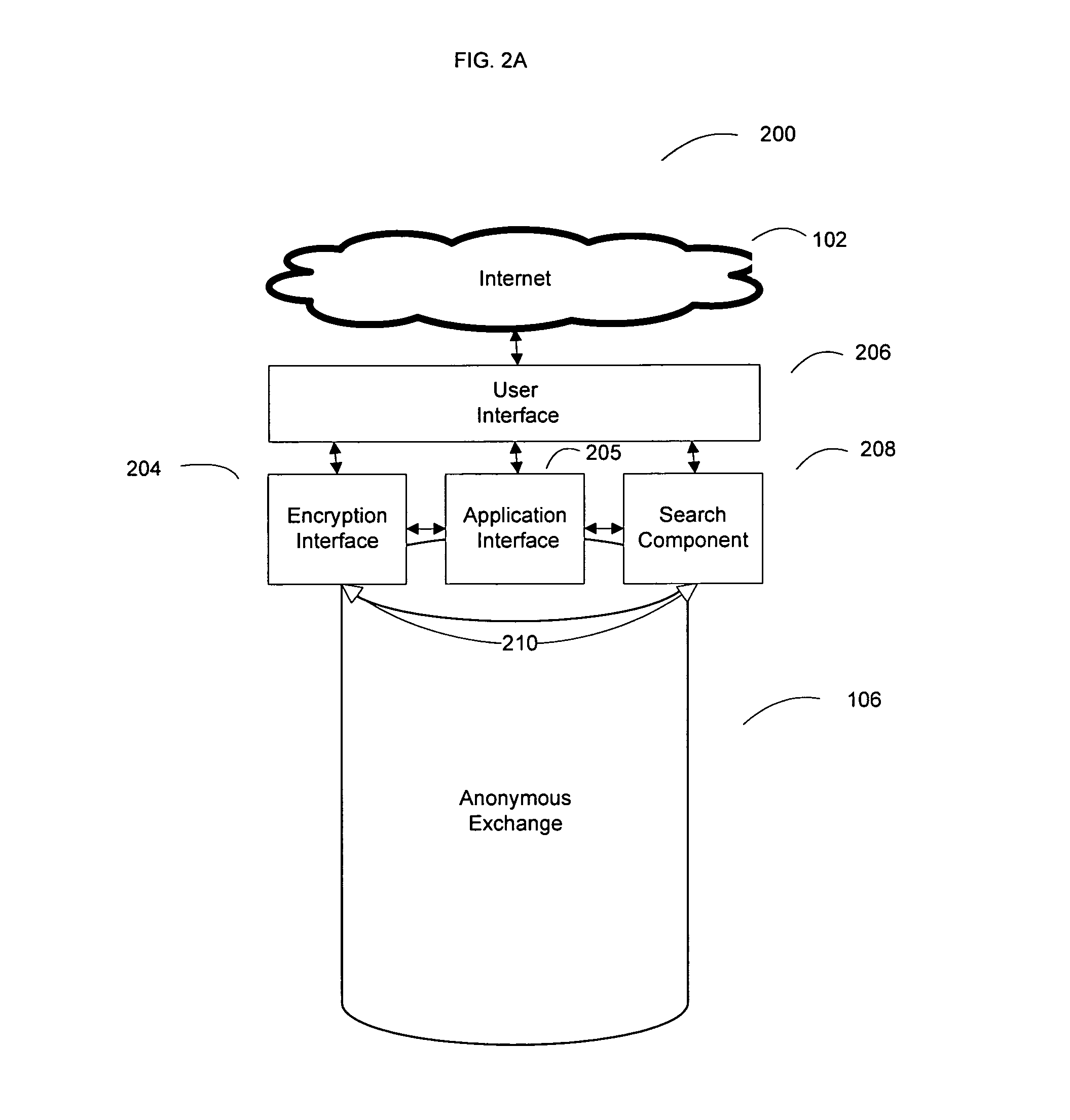
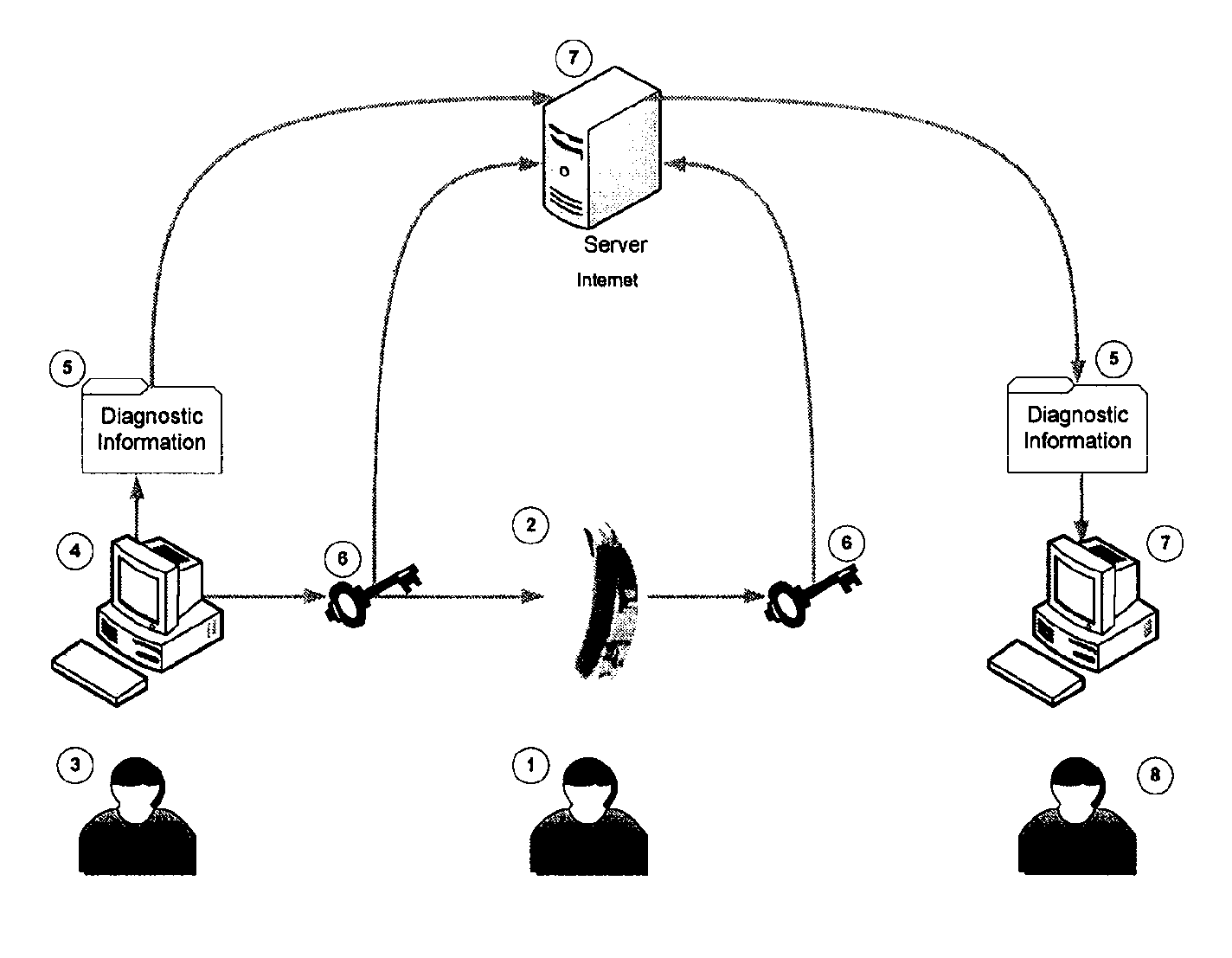
System and method for an anonymous exchange of private data
ActiveUS8560456B2Meet the requirementsEasy accessPublic key for secure communicationComputer security arrangementsPaymentInternet privacy
Facilitating the purchase and sale of private data between anonymous entities based on the use of encryption and a centralized on-line entity to exchange the private data in a secure environment. The seeker of private data, such as consumer information, transmits an encrypted query to the centralized exchange entity. The query submission includes legal representations stating the legally permissible purpose for seeking the information. The centralized exchange entity compares the encrypted query to an encrypted data index collected from at least one data provider, to determine if the query matches any private data held by a data provider. The comparison is conducted within a secure, search component to ensure the privacy of all data and all parties to the transaction. The exchange entity facilitates the anonymous exchange between the data purchaser and the data provider. A payment invoice can be generated and electronically presented by maintainer. The payment may be electronically debited from the designated account of a data purchaser and remitted to a data provider. In addition, a portion of such funds may be retained by the centralized exchange entity.
Owner:CREDIGY TECH
Method and apparatus for managing obfuscated mobile device user identities
InactiveUS20080293411A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionDigital data processing detailsUnique identifierMobile device
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator. The present invention describes a method and apparatus for use in a home network to manage the generation, storage and use of the unique identifiers.
Owner:IBM CORP
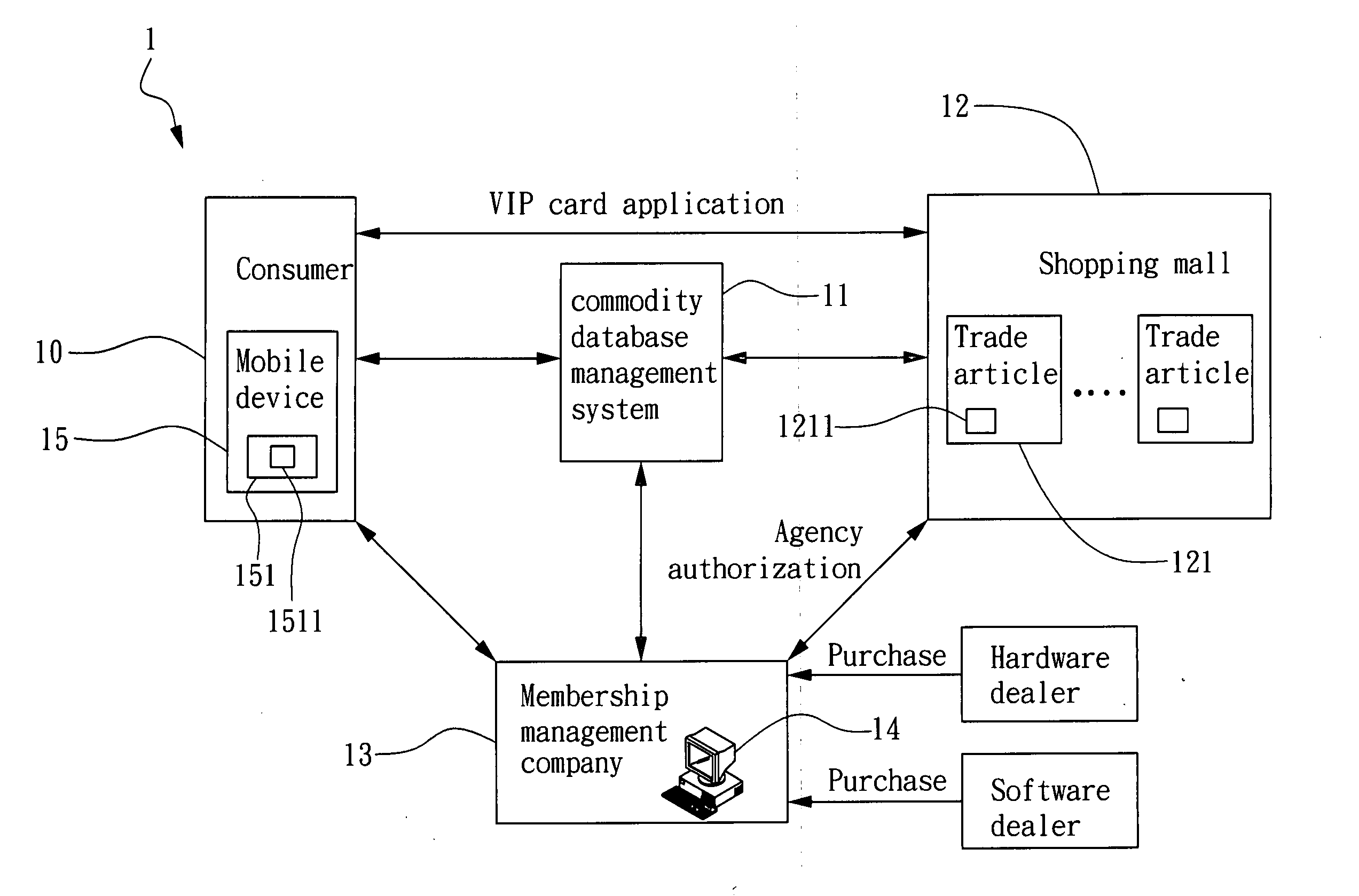
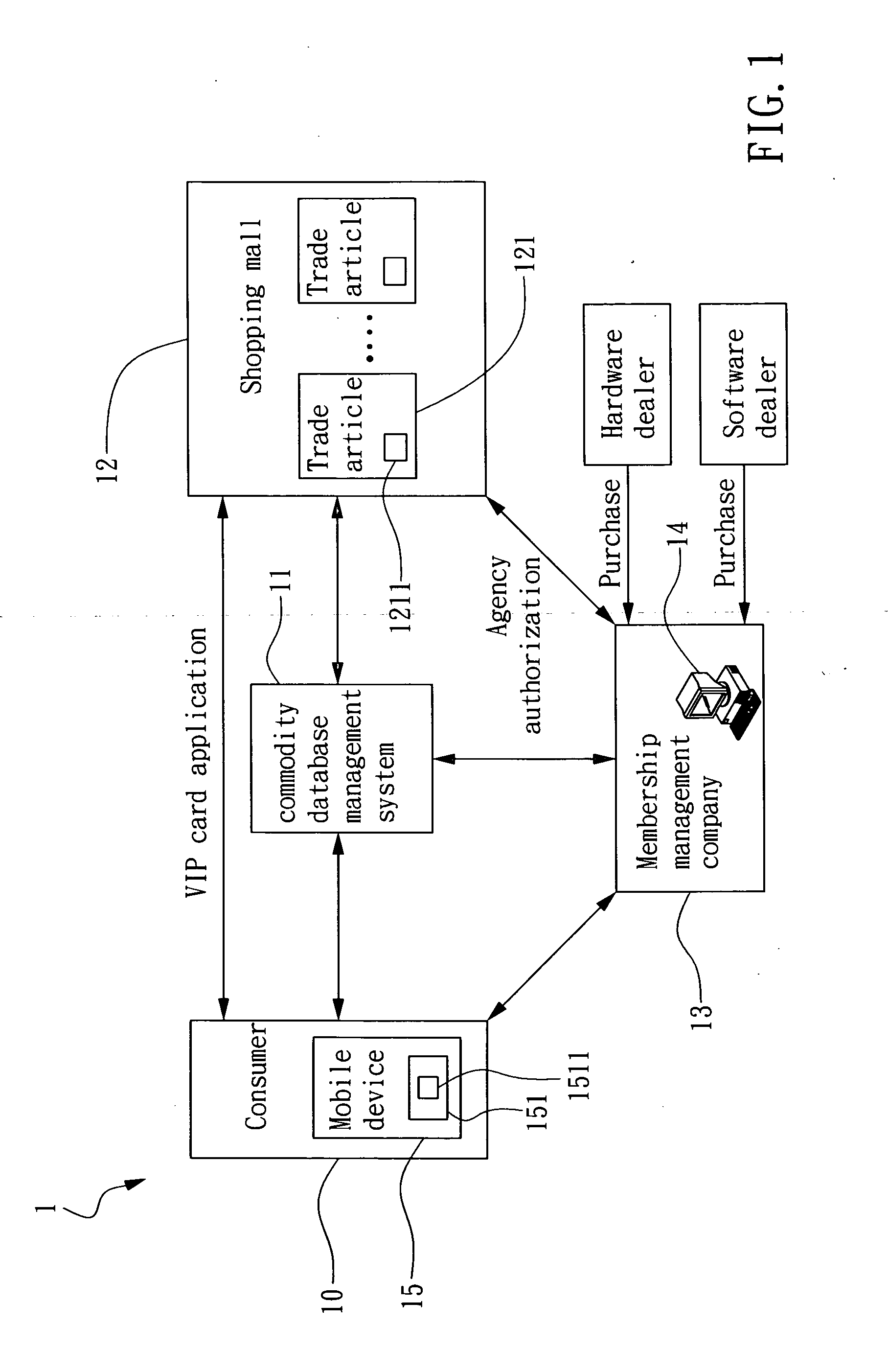
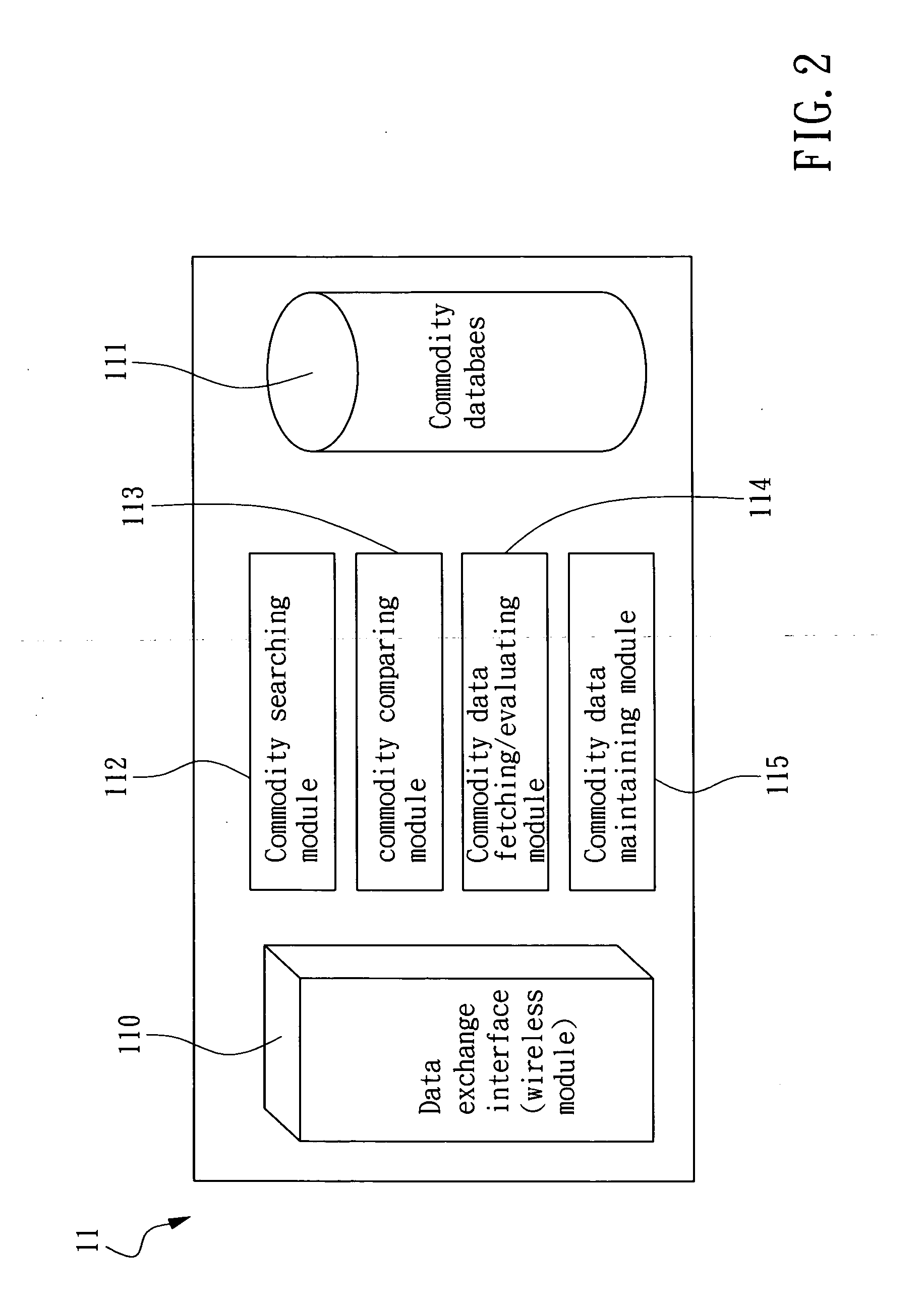
RFID-enabled personal shopping assistant system and method
The present invention relates to a personal shopping assistant system applying radio frequency identification (RFID) technology, i.e. an RFID-enabled personal shopping assistant system. The system of the invention is comprised of a plurality of trade articles, each having an RFID tag attached thereon, at least a mobile device, each having an RIFD reader, and a commodity database, by which a custom service program with real-time personal shopping assistant ability is established. By the RFID-enabled personal shopping assistant system of the invention, a relating method can be established for enabling a service provider to successfully acquire the shopping behavior of its customers so as to proceed with a responsive promotion just in time. Moreover, a consumer can also benefit from the method, that is, a consumer is enabled to rapidly query and obtain his favor goods with respect to his personal preference among a great amount of similar goods. According to the shopping pattern established by the RFID-enabled personal shopping assistant system and method of the invention, not only the time that a consumer wasted in trying to find the goods of his favor can be reduced, but also the correlation between goods and the personal preferences of consumers can be enhanced.
Owner:IND TECH RES INST
Method of individually fitting a hearing device or hearing aid
ActiveUS8166312B2Quick and simple transferEnsure privacy of dataUnauthorized memory use protectionHardware monitoringHearing apparatusHearing aid
The present invention provides a method of providing parameters for the fitting process of individually shaped or customized hearing devices by collecting and storing fitting parameters during a fitting process by a local fitting computer; generating an individual encryption key related to the hearing device; sending the stored fitting parameters encrypted with the encryption key to a remote database; storing the encryption key in the memory of the hearing device; reading out the encryption key from the hearing device; reading out data from the remote database using the encryption. Thus, the privacy of the individual fitting data of a hearing device is secured.
Owner:SONOVA AG
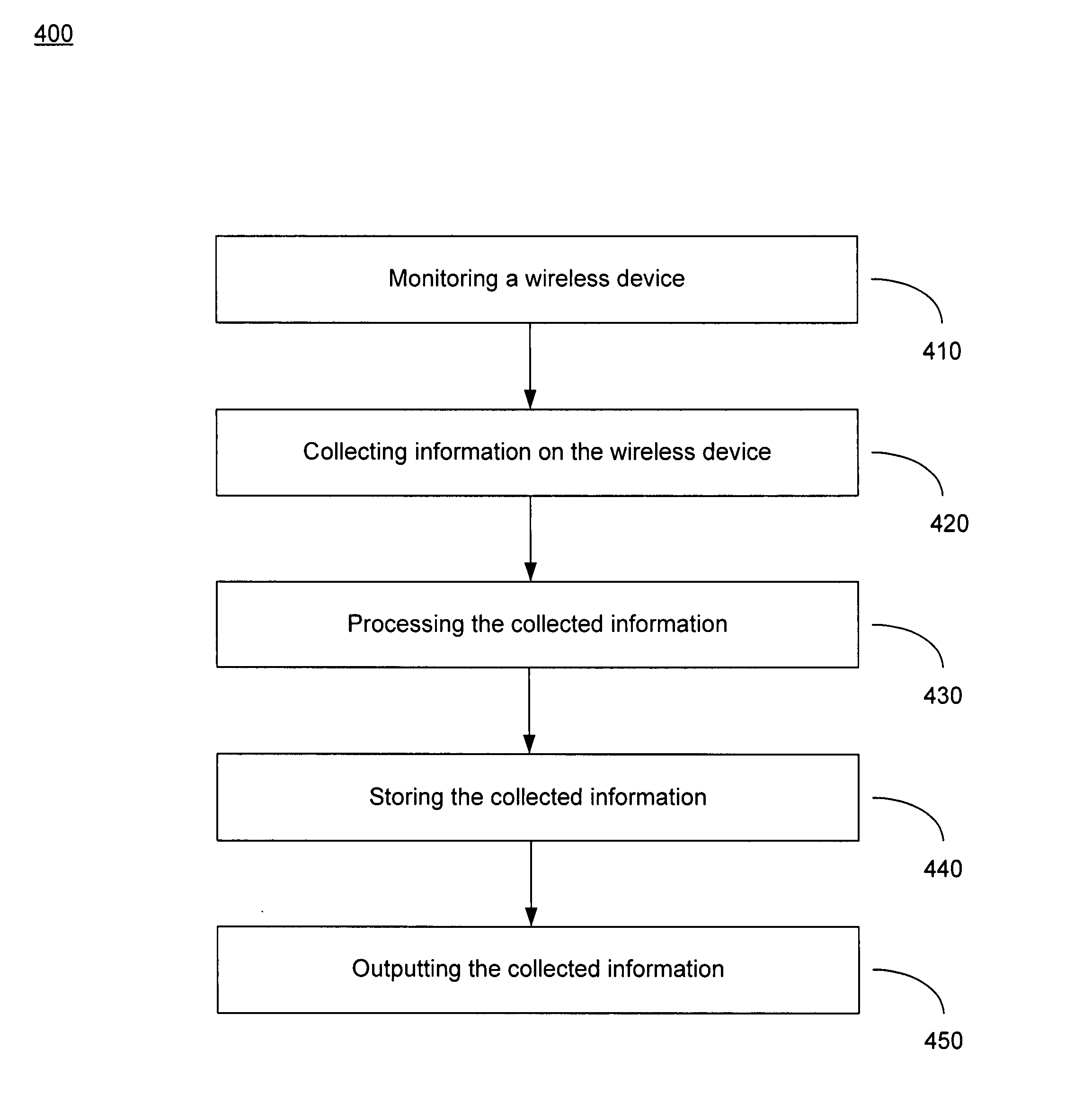
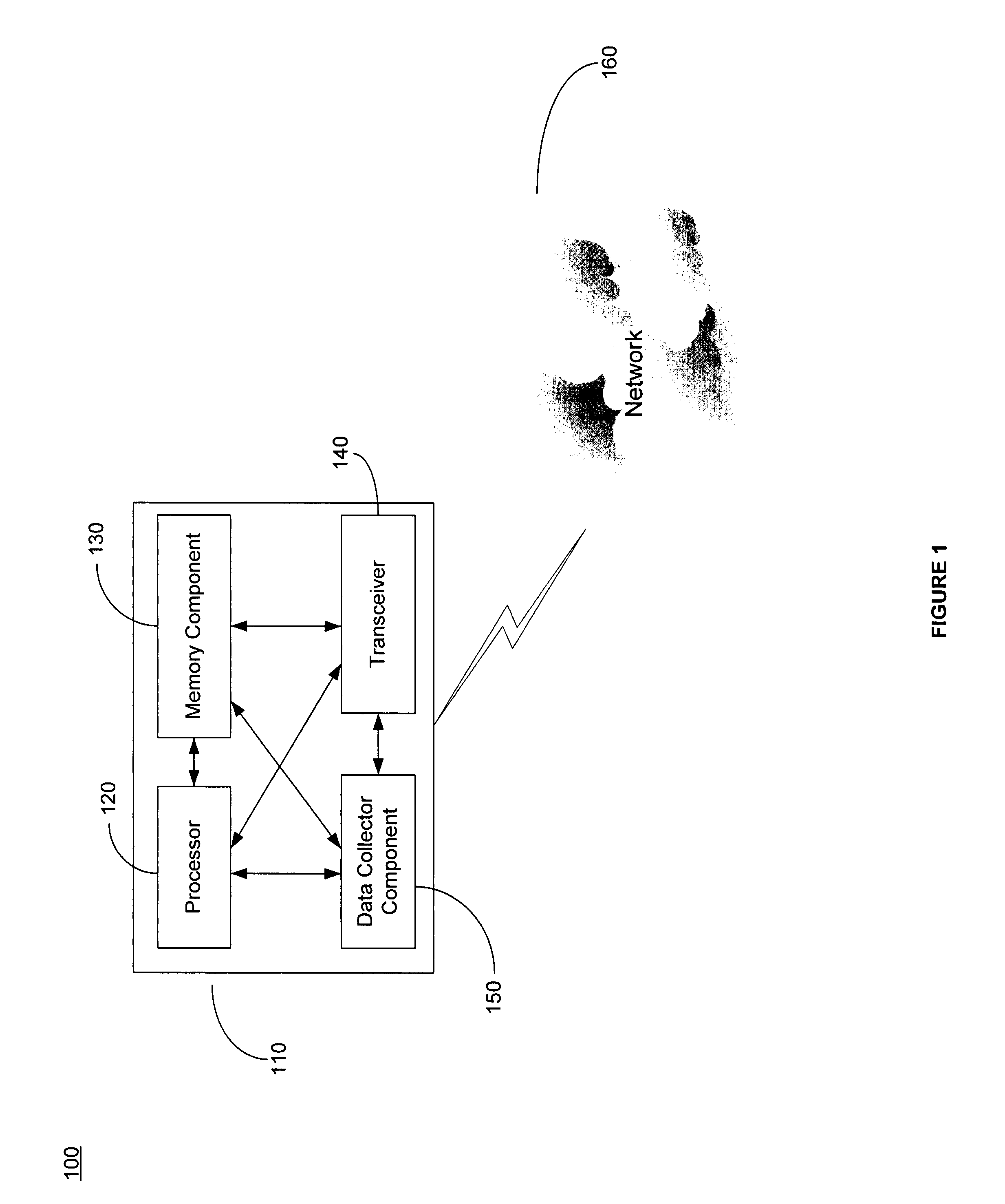
Method and system for collecting wireless information transparently and non-intrusively
ActiveUS8014726B1Minimizing slowdownRisk minimizationError preventionFrequency-division multiplex detailsTransceiverOperational system
A method of collecting information on a wireless device. A wireless device may comprise a processor, a transceiver, a memory and a data collecting component. The data collecting component is operable to monitor the wireless device and collect information (e.g., wireless network information, wireless device information and wireless device usage information). In one embodiment, at least a portion of the data collecting component is installed within and / or below the operating system. For example, at least a portion of the data collecting component may be embedded within the operating system, the kernel, the firmware and / or on top of the firmware, the kernel or any combination thereof. In one embodiment, the collected information may be processed, stored and transmitted. Accordingly, the data collector component operates in a non-intrusive / transparent manner by utilizing less memory space and produces fewer errors without causing a system slowdown while maintaining high level of privacy and security.
Owner:THE NIELSEN CO (US) LLC
System for secure online selling, buying and bill pay in an electronic commerce setting
ActiveUS7949609B2Ensuring privacyAllow large numberBilling/invoicingBuying/selling/leasing transactionsUSBMinutiae
A method and system for biometric-secure online selling, buying and bill paying in electronic commerce and retail point-of-sale settings that also simplifies the checkout process and eliminates fraudulent transactions. The system relies on an exchange service provider (ESP) that hosts multiple servers: one implementing a web portal for secure online banking, auctions and other exchange opportunities, another being a biometric fingerprint device authenticating database, and yet another being a transaction traffic manager. Participating banks and supporting institutions distribute and activate Secure Individual Identity Devices (SIIDs) to registered users, each SIID being a portable biometric activated identification device that locally stores a fraction of the enrolled users fingerprint (minutia) along with an encrypted code that is used to verify and authenticate the user, eliminating the use of personal or financial information for this purpose. The SiiD becomes the user's own personal key for completing secure online transactions. The user simply plugs their SiiD into any USB-equipped device and scans their own fingerprint for each transaction. The encrypted codes are authenticated in the ESP database and the transaction is processed to the appropriate financial institutions.
Owner:COLELLA BRIAN
Method and system for enabling personalized shared mobile phone usage
ActiveUS8311532B2Ensuring privacyLow costMetering/charging/biilling arrangementsAccounting/billing servicesPersonalizationTelecommunications network
Disclosed is a system and method for enabling personalized shared mobile phone usage within a wireless telecommunications network, including an illustrative application of the invention as it relates to mobile subscribers who cannot afford a mobile phone handset in the emerging markets. For instance, a prepaid wireless subscriber can be provisioned on a wireless network without the need for a mobile phone handset or SIM but with a personal phone number. The subscriber may access his account and invoke the system by keying in an Unstructured Supplementary Service Data (USSD) short code followed by his account number on a borrowed handset to access a personalized menu sent from the system over the network. Key features of the disclosure are the very low cost of entry and the ability for a subscriber to access the system from any GSM MAP2+ handsets without the need for any modification or downloading of applications.
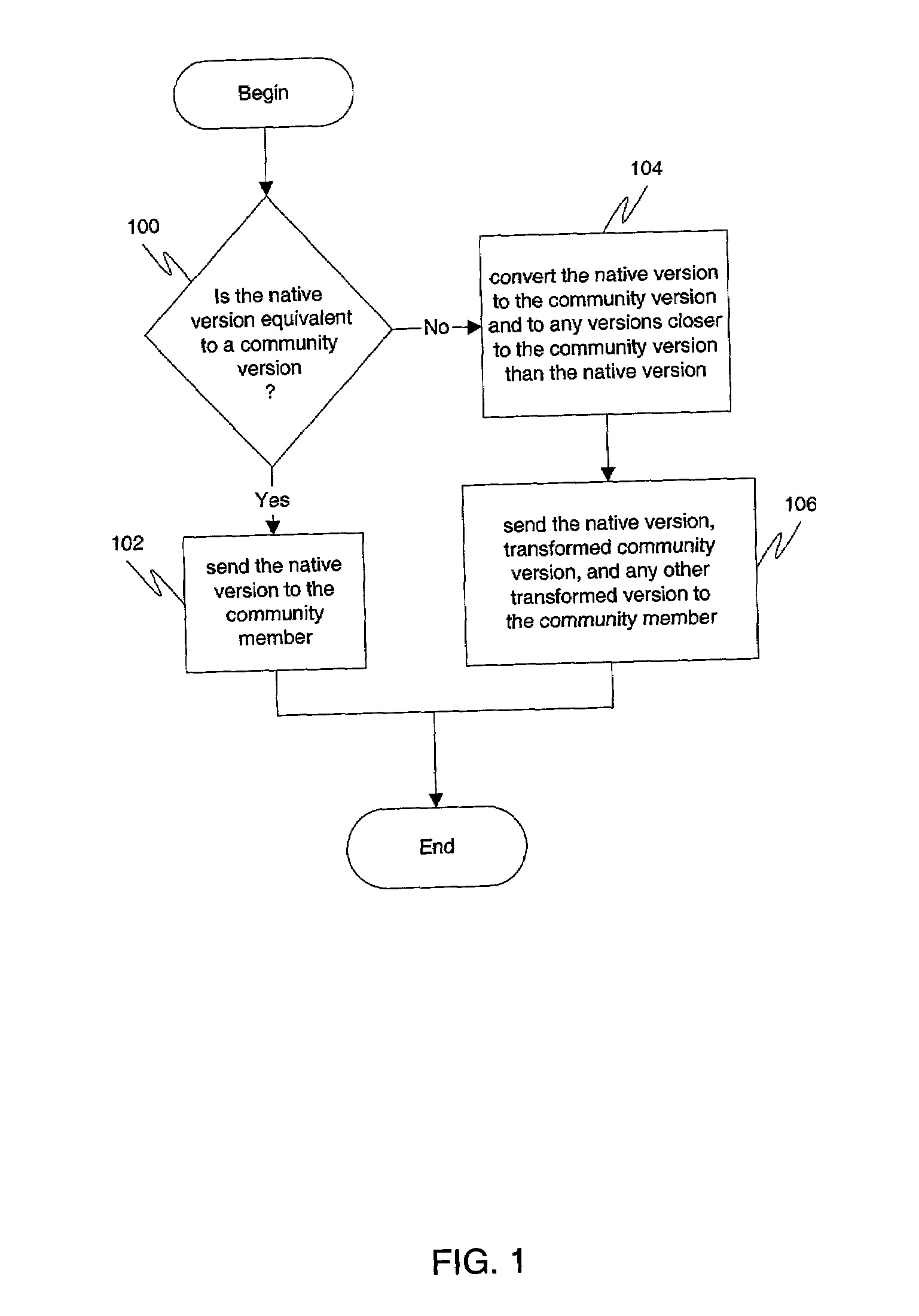
Owner:MALIKIE INNOVATIONS LTD
Combined staircase and lavatory module for an aircraft
ActiveUS8109469B2Save spaceAccommodation regionAir-treatment apparatus arrangementsWeight reductionOn boardAirplane
A module for an aircraft for accessing an upper region of the aircraft includes both an ascent region and an accommodation region, with the regions being divided from each other by a divider element. The accommodation region may, for example, be designed as an on-board lavatory. In this way it may be possible to do without the provision of an additional lavatory monument.
Owner:AIRBUS OPERATIONS GMBH
Biometrically secured identification authentication and card reader device
InactiveUS7953670B2Ensuring privacyConvenient verificationBilling/invoicingBuying/selling/leasing transactionsCredit cardIdentification device
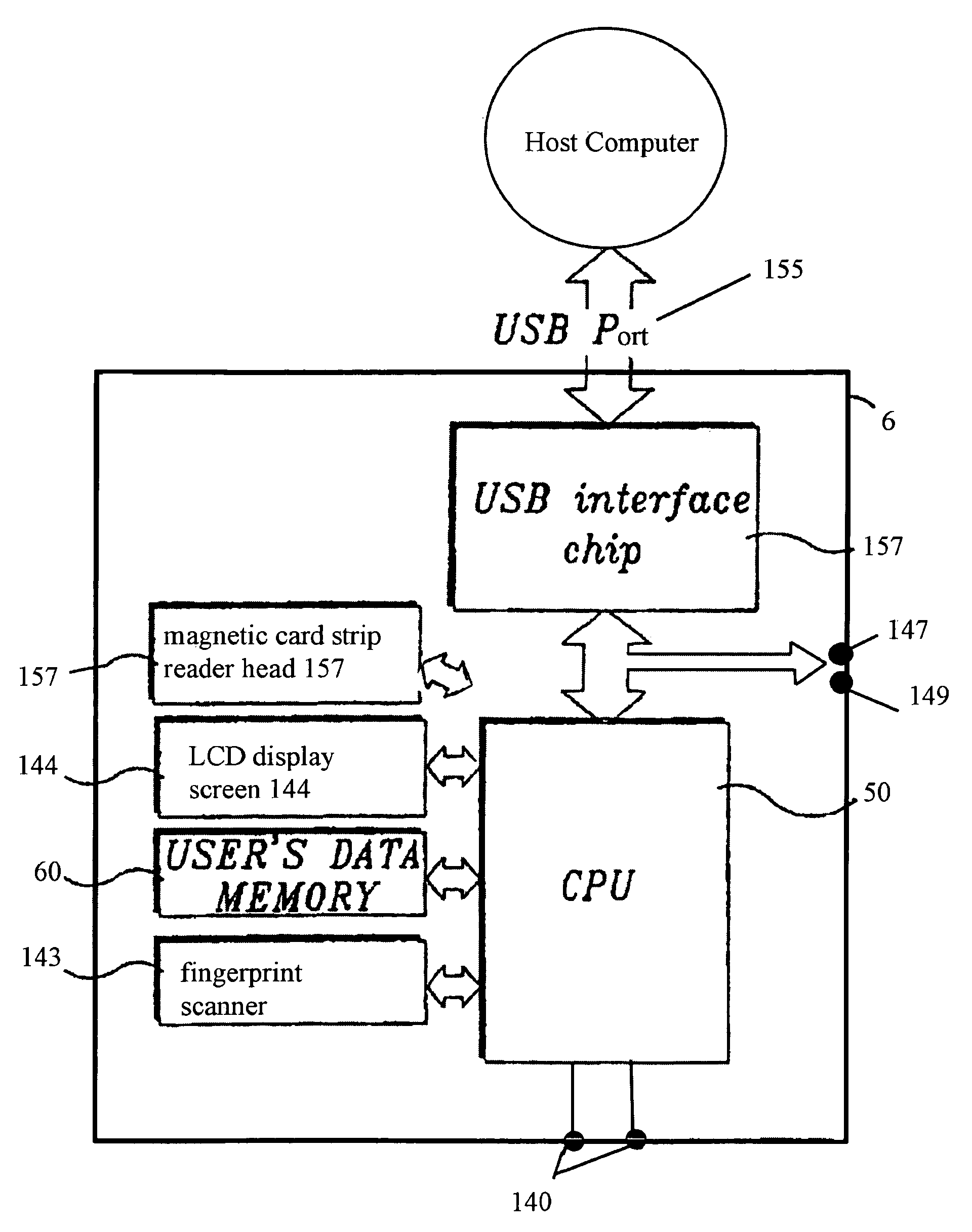
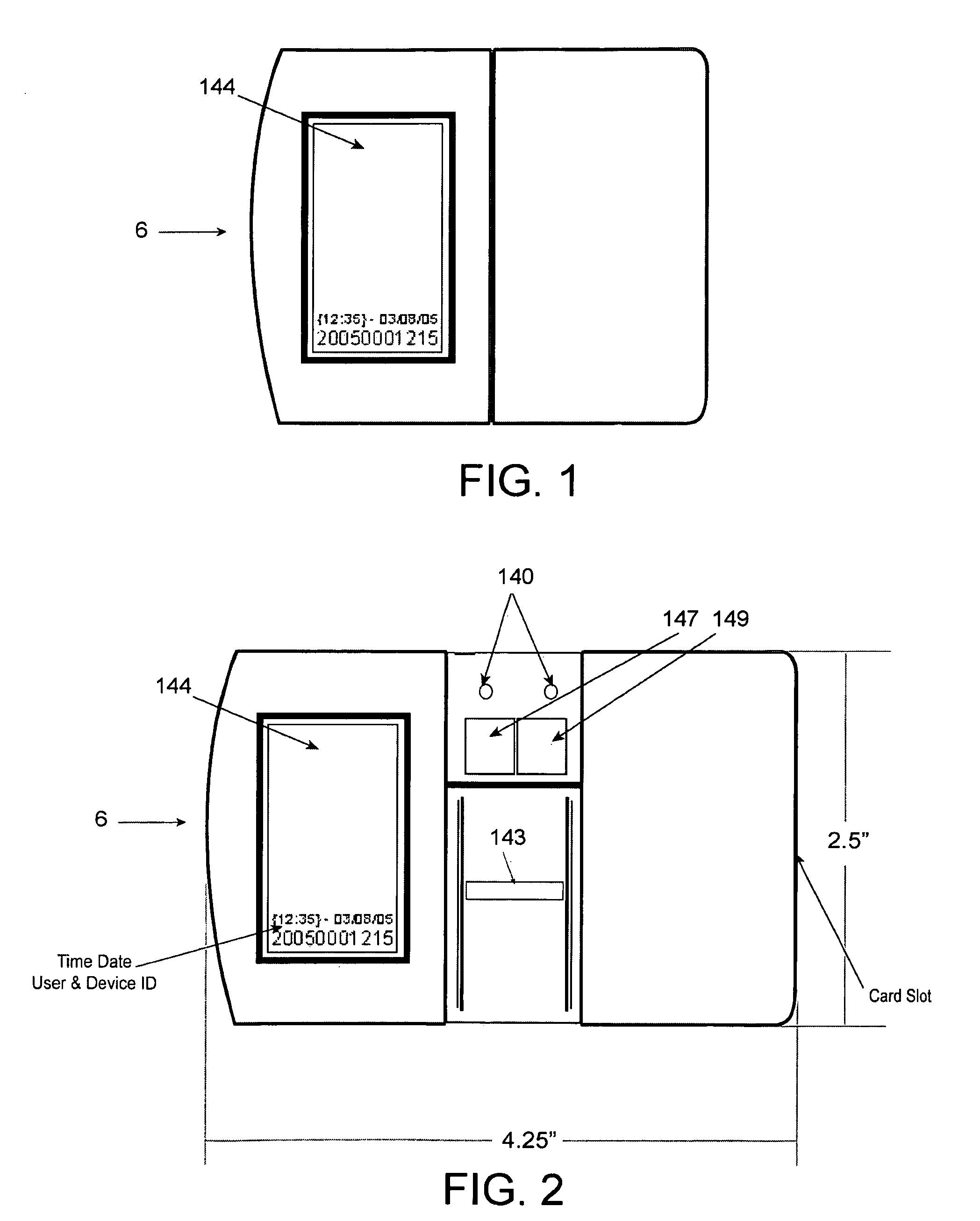
An intelligent Caddy-Pilot for facilitating biometric verification. The device works as a single sign-on device for an internal VPN or network or in conjunction with a central data network and may act as a card reader for various Safe Card and traditional credit cards to perform secure transactions and other objective functions, or as an; instantaneous standalone biometric authentication and identification device. The Caddy-Pilot generally comprises a Credit Card-sized housing defining an end-wise card insertion port, a USB connection port, a magnetic card strip reader head, an internal infrared receiver / transmitter, a fingerprint scanner, LCD display screen, LED indicator lights, and a programmable microprocessor and memory. At issuance, an initial scan of the user's fingerprint is completed and a portion of the digitized fingerprints scan is stored locally on Caddy Pilot along with an image of the user for later authentication. The user may then employ the Caddy-Pilot by connection to any available USB port on a web enabled device to initiate both a local biometric-secure authentication sequence as well as a network biometric authentication single sign-on sequence to fully authenticate the user. Once authenticated the user is permitted access to requested resource or data.
Owner:COLELLA BRIAN A
Hard disk drive medical monitor with GPS
A medical monitor is disclosed for implantation in a human body for monitoring biological activity and states as detected by implanted sensors. The medical monitor includes at least one hard disk drive. An enclosure surrounds the at least one hard disk drive. The medical monitor is in communication with the sensors, by which information on biological activity and states is stored on the at least one hard disk drive. A transmitter and receiver produces and transmits signals, and include a GPS transmitter and a receiver for producing and receiving transmission signals in the radio frequency range, where the GPS sends satellite communication signals via the public GPS frequencies and protocol.
Owner:WESTERN DIGITAL TECH INC
System for secure internet access for children
InactiveUS7853535B2Ensuring privacyDigital data processing detailsMultiple digital computer combinationsDocking stationInternet access
A system and method for secure internet access by children that assigns each child a Safe Card with integral fingerprint scanner, plus an intelligent USB card reader for biometric-secure internet access. Both the Safe Card and card reader / docking station have device ID numbers. At registration each child is assigned a user ID, and a registration record is compiled including user ID, device IDs and photo data. Parents author a parental ruleset for their child which is associated with the registration record. The child activates their Safe Card by an initial fingerprint scan, and can then access the Internet from any web-enabled computer simply by plugging the card reader / docking station into the computer's USB port, inserting their Safe Card, and scanning their fingerprint. This authenticates the child, pre-loads the parental control ruleset and gives the child-user a restricted safe and secure but full internet experience.
Owner:COLELLA BRIAN A
Mobile device with an obfuscated mobile device user identity
ActiveUS20080293378A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyUnique identifier
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator (or an entity authorized thereby). When the mobile device user roams into a foreign network, that network receives the enriched identifier in lieu of an MSISDN. The foreign network uses the first part to identify the mobile device user's home network, e.g., to determine whether to permit the requested access (or to provide some other value-added service). The foreign network, however, cannot decode the second part; thus, the mobile device's identity (as well as the identity of the mobile device user) remains obscured. This ensures that the user's privacy is maintained, while preventing third parties from building a profile of the device based on the requests that include the MSISDN or similar identifier.
Owner:IBM CORP
System and method for tracking positions of objects in space, time as well as tracking their textual evolution
InactiveUS20050062849A1Ensuring privacyExact matchTelevision system detailsCharacter and pattern recognitionFluorescenceUnique identifier
A system and method including cameras for monitoring objects such as documents, at multiple locations, and for recording the objects' movement through space and time. The objects are marked with unique identifiers, and the invention is adaptable for recording and recognizing the objects' development using character recognition. A center receives the information from the cameras, and that information is searchable. Advantageously, the unique identifiers are printed with ink that is invisible unless it fluoresces or phosphoresces, the digital cameras include an ultraviolet flash to cause the identifiers to fluoresce or phosphoresce at a certain wavelength, and the cameras are equipped with filters to filter out wavelengths other than the certain wavelength. Packages or pads of pre-marked blank paper are adaptable for use with the present invention.
Owner:PITNEY BOWES INC
Mobile terminal and method of providing video calls using the same
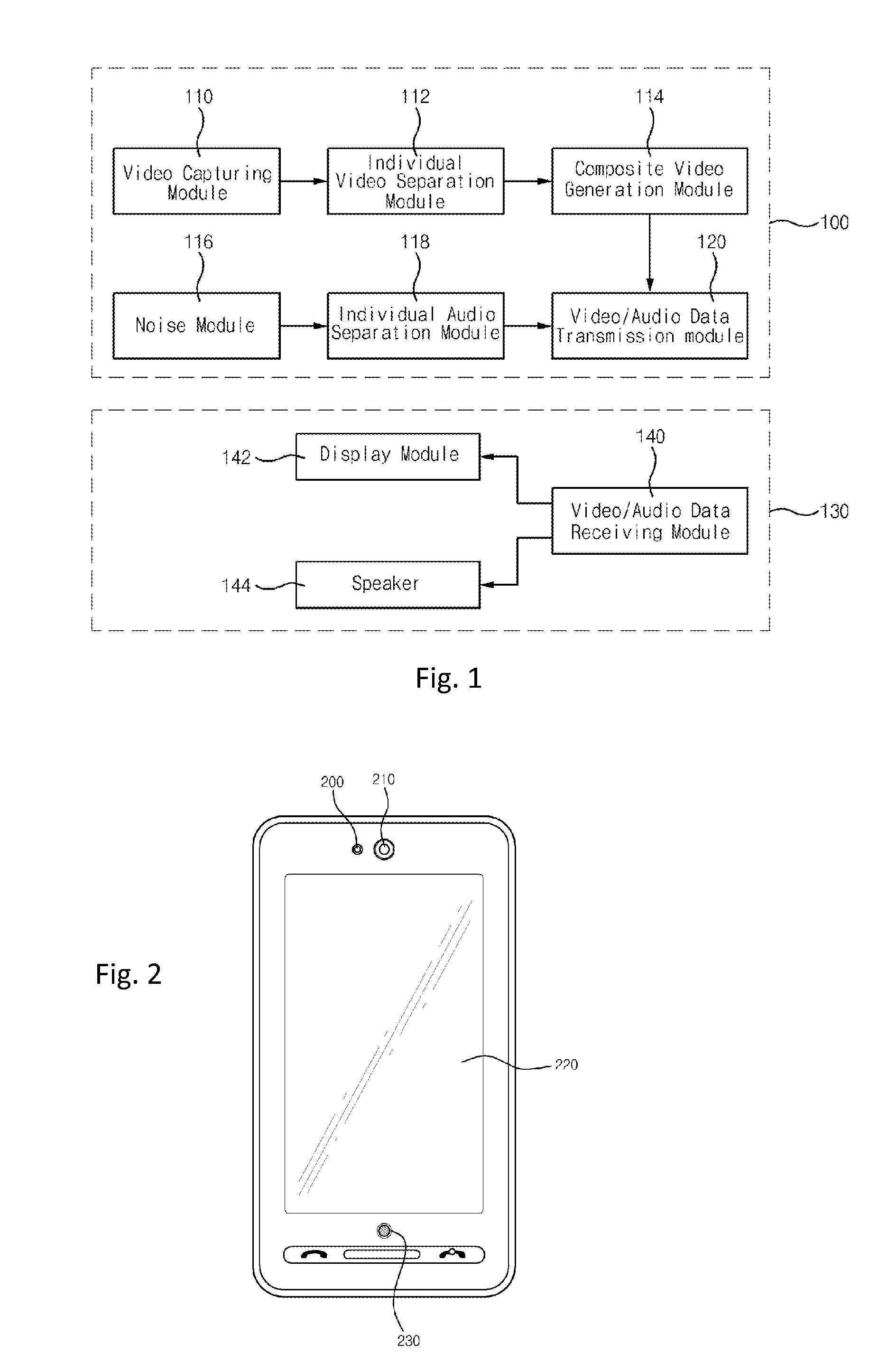
ActiveUS20120140019A1Ensuring privacyGood effect2D-image generationTwo-way working systemsComputer graphics (images)User privacy
A mobile terminal and a method of providing a video call using the same are disclosed. More particularly, a mobile terminal capable of supporting a video call while ensuring user's privacy by mounting a three-dimensional depth camera and a two-dimensional camera in the mobile terminal and a method of providing a video call using the same are disclosed. The mobile terminal of the present invention includes a 2D camera 200 capturing a 2D video and a 3D depth camera 210 capturing a 3D depth video; an individual image separation module 112 extracting boundary information between a user and a background by using depth information regarding a video captured by the 3D depth camera 210; a composite video generation module 114 separating the user video from the video captured by the 2D camera 200 by using the extracted boundary information and composing the separated user video and the set background video.
Owner:KOREA ELECTRONICS TECH INST
Exchanging and converting document versions
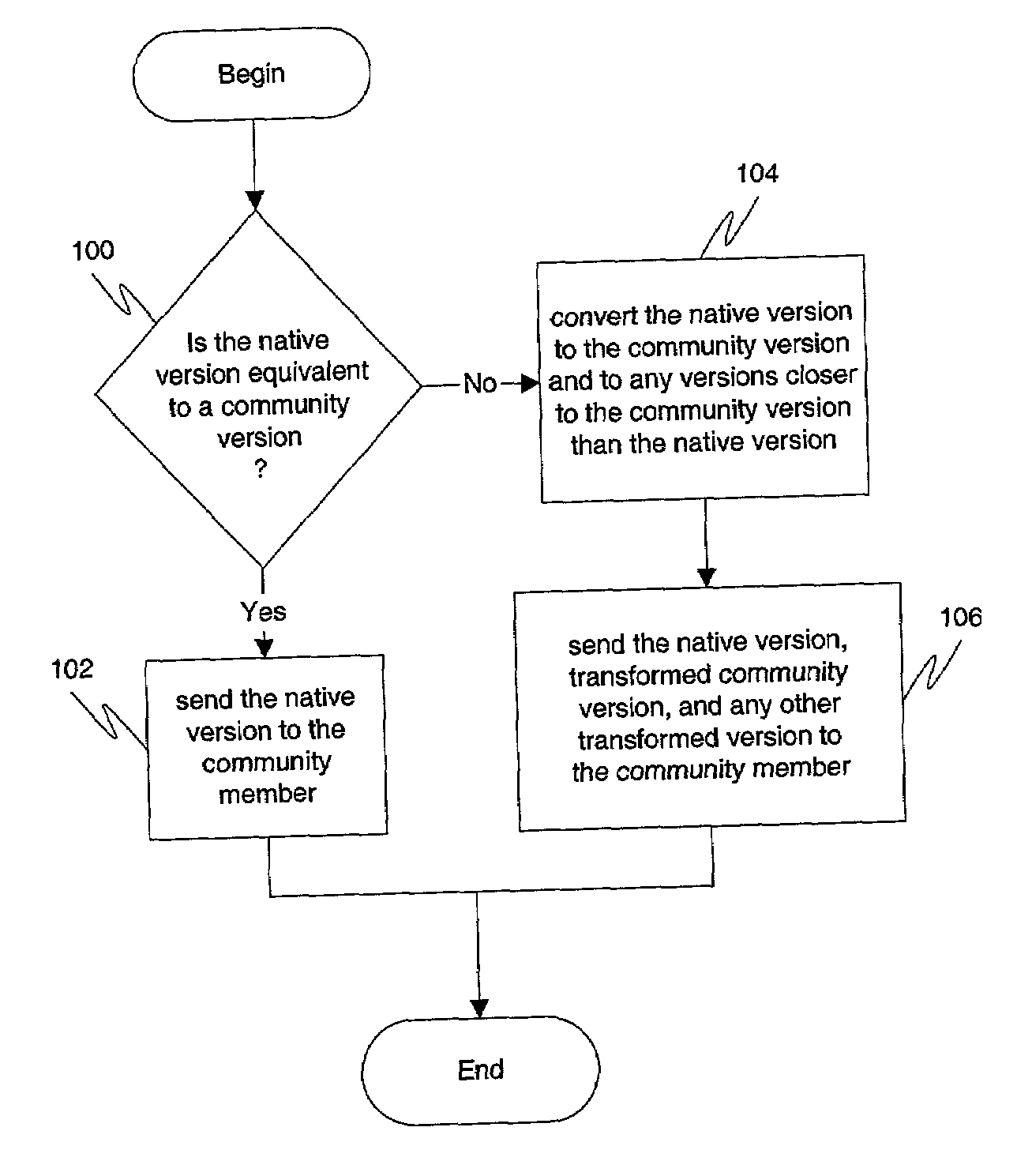
ActiveUS7013426B1Minimal data lossEasy to readDigital data processing detailsNatural language data processingApplication program softwareDocumentation procedure
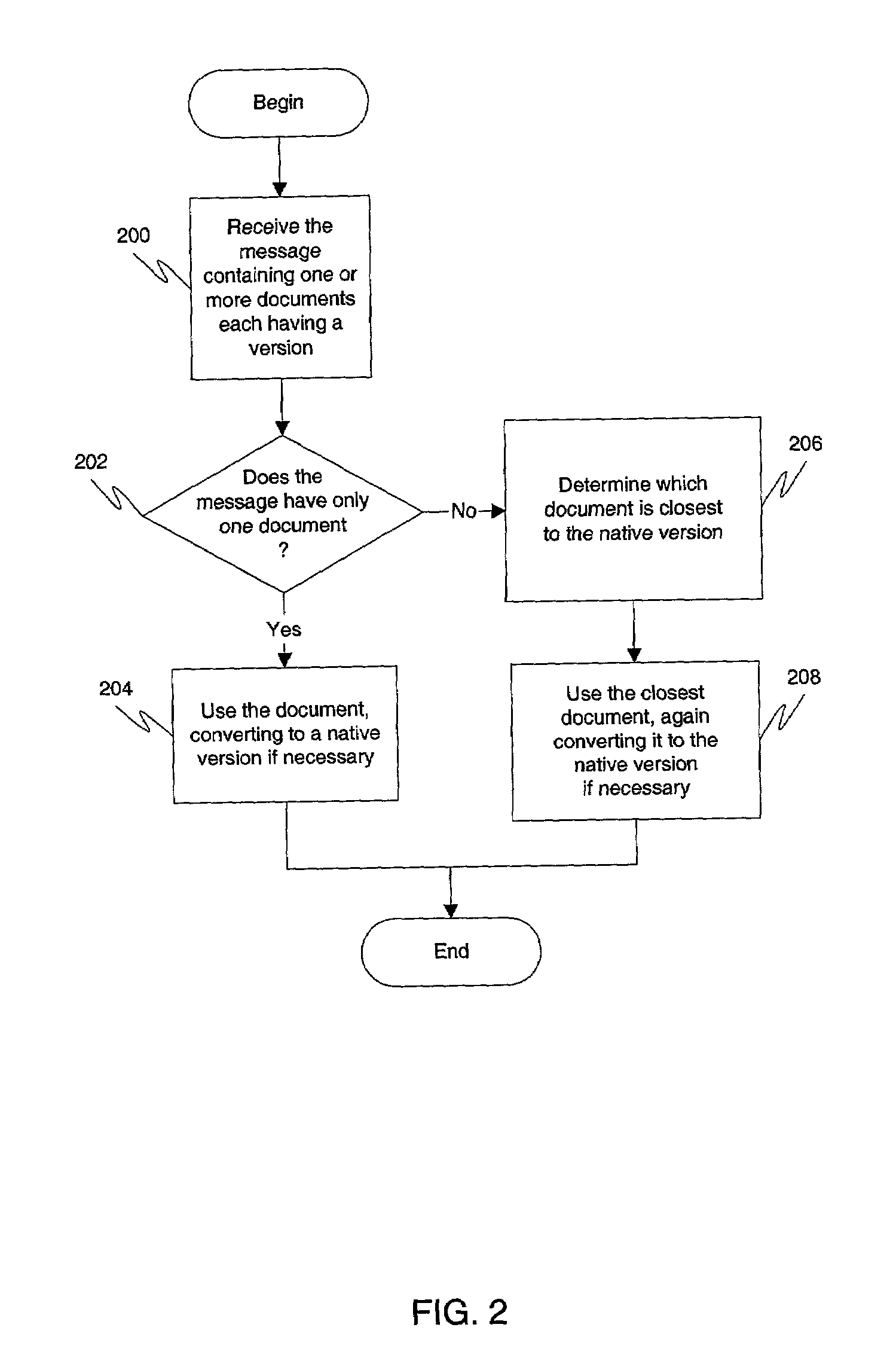
Document version interoperability is provided by allowing members of a community to maintain independent migration by permitting the members to continue to run native application software on their respective systems. A community may define a community version by establishing certain rules for documents. When electronically transmitting a document, a member of the community may provide in the transmitted message containing the document his native version of the document, the community version of the document, as well as any or all versions of the document which are closer to the community version of the document than his native version of the document. This may be accomplished by performing document transformations when creating the message. Upon receipt of the documents, the recipient may choose the document version contained in the message that is most easily read by the recipient's native application program and transform it so that it may be opened by the recipients native application program if necessary. Regardless of what rules are established to define the community version, data loss in any document exchange is minimized. Entities that follow these rules can migrate their native support without requiring coordination with other entities. Members do not have to know the native version supported by other members. This ensures privacy for the members and also lessens the need for direct communications between the members.
Owner:COMMERCE ONE OPERATIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com