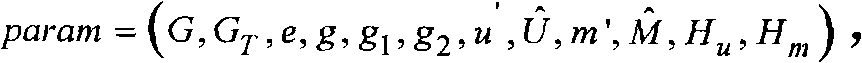Identity-based threshold ring signature method
A threshold ring and identity technology, which is applied in the field of identity-based threshold ring signatures, can solve problems such as the difficulty of trapdoor one-way functions in public key cryptography
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
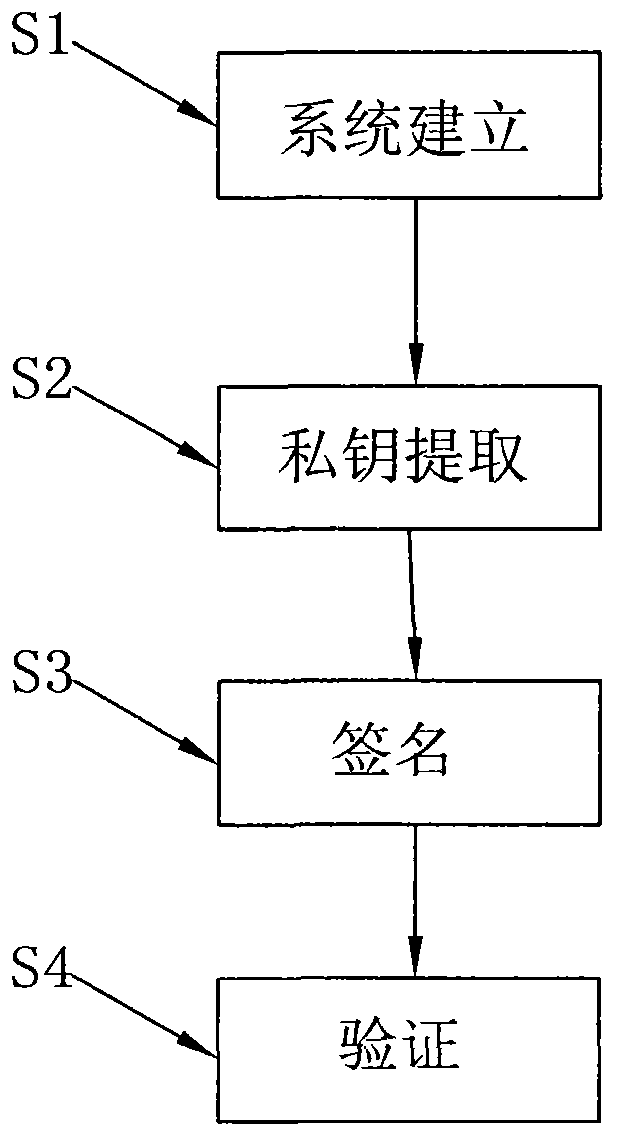
[0030] Such as figure 1 As shown, the present invention is an identity-based threshold ring signature method, comprising the following steps:
[0031] An identity-based threshold ring signature method, comprising the following steps:
[0032] S1. System establishment: randomly select parameters, generate system parameters and corresponding master keys, where system parameters are public parameters, and the specific steps are:
[0033] Let G, G T is a cyclic group whose order is a prime number p, e: G×G→G T is a bilinear map, two collision-free hash functions and Output the identity ID and message m of any length with a length of n u and n m the bit string;
[0034] The trusted third party randomly selects the parameter α∈Z p , generating element g∈G, computing g 1 =g a . Randomly choose the parameter g 2 , u′,m′∈G,n u dimension vector no m dimension vector where u i , m i ∈ R G, then the system parameters are param = ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com