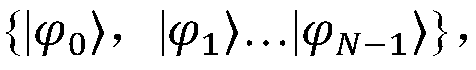Patents
Literature
71results about How to "Eliminate loopholes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
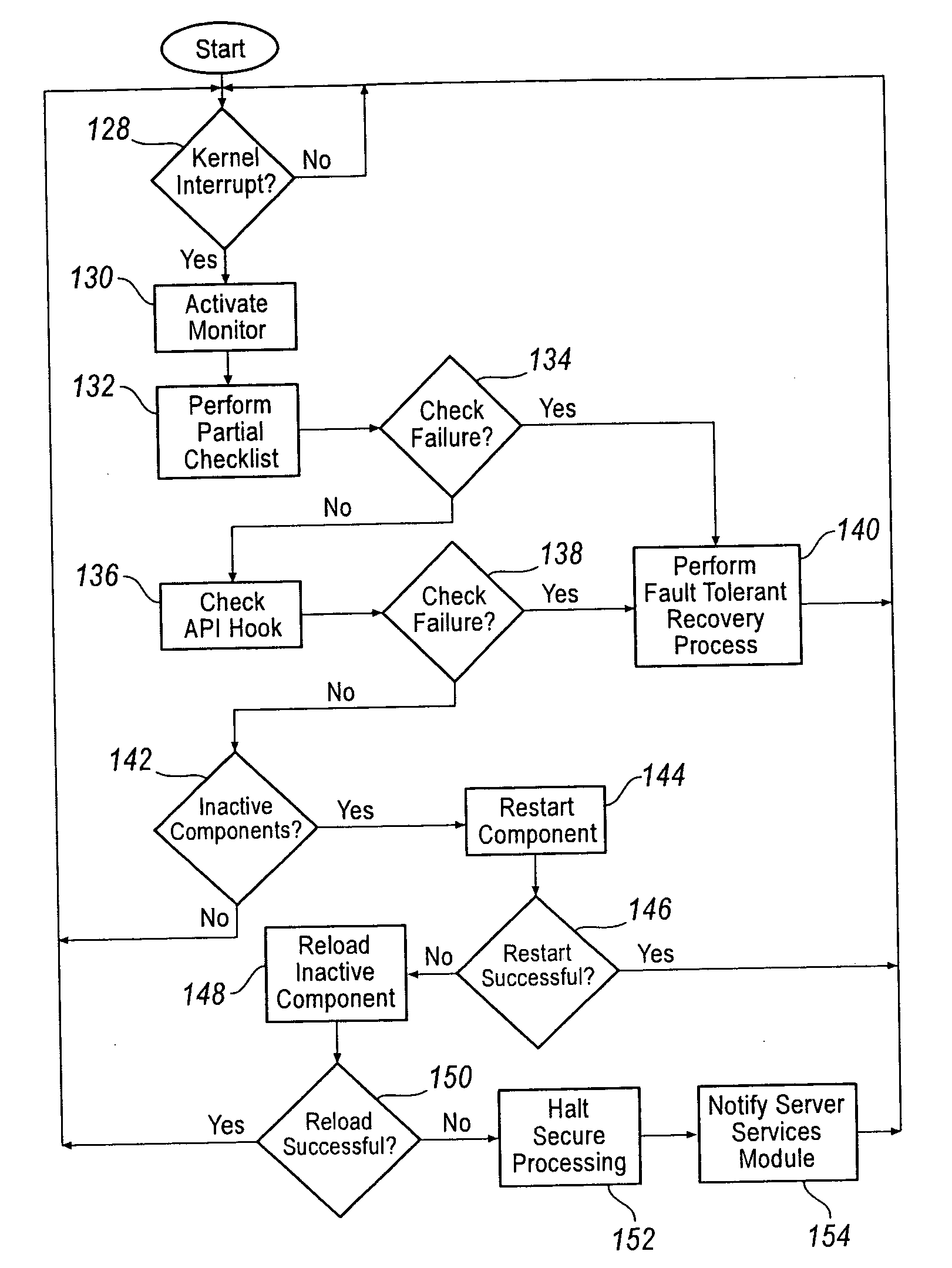
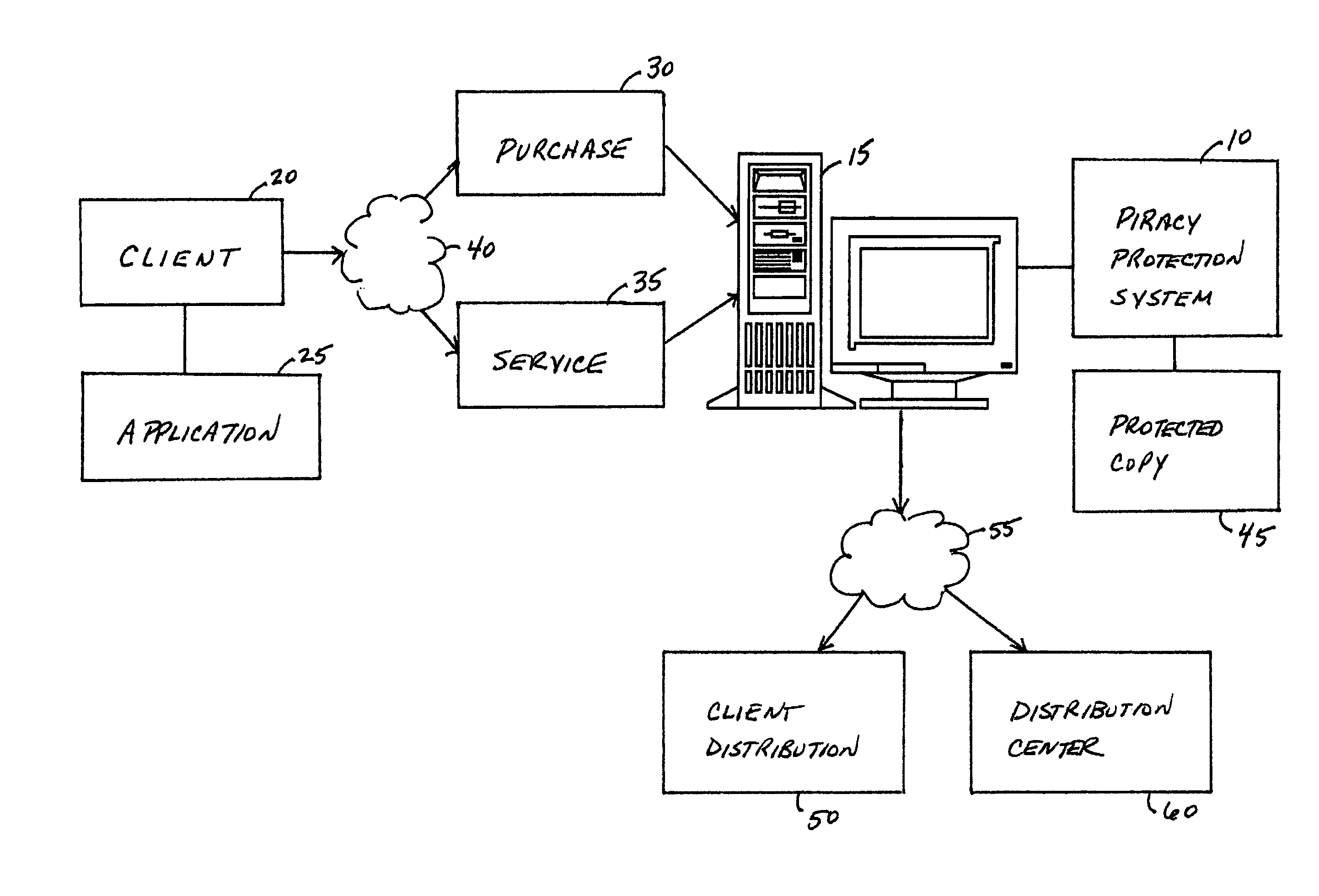
Secure flow control for a data flow in a computer and data flow in a computer network
InactiveUS20070006294A1System stabilityEliminate loopholesComputer security arrangementsMultiple digital computer combinationsData streamComputer security
Systems and methods of the present invention manage data flow of a computer and computer network in a secure domain. The system includes an administration module and a management module. The administration module assigns a security label to data within the secure domain, and establishes a set of schema based on the security labels associated with the data. The management module regulates data flow within the secure domain based on the set of schema.
Owner:HUNTER G KENNETH
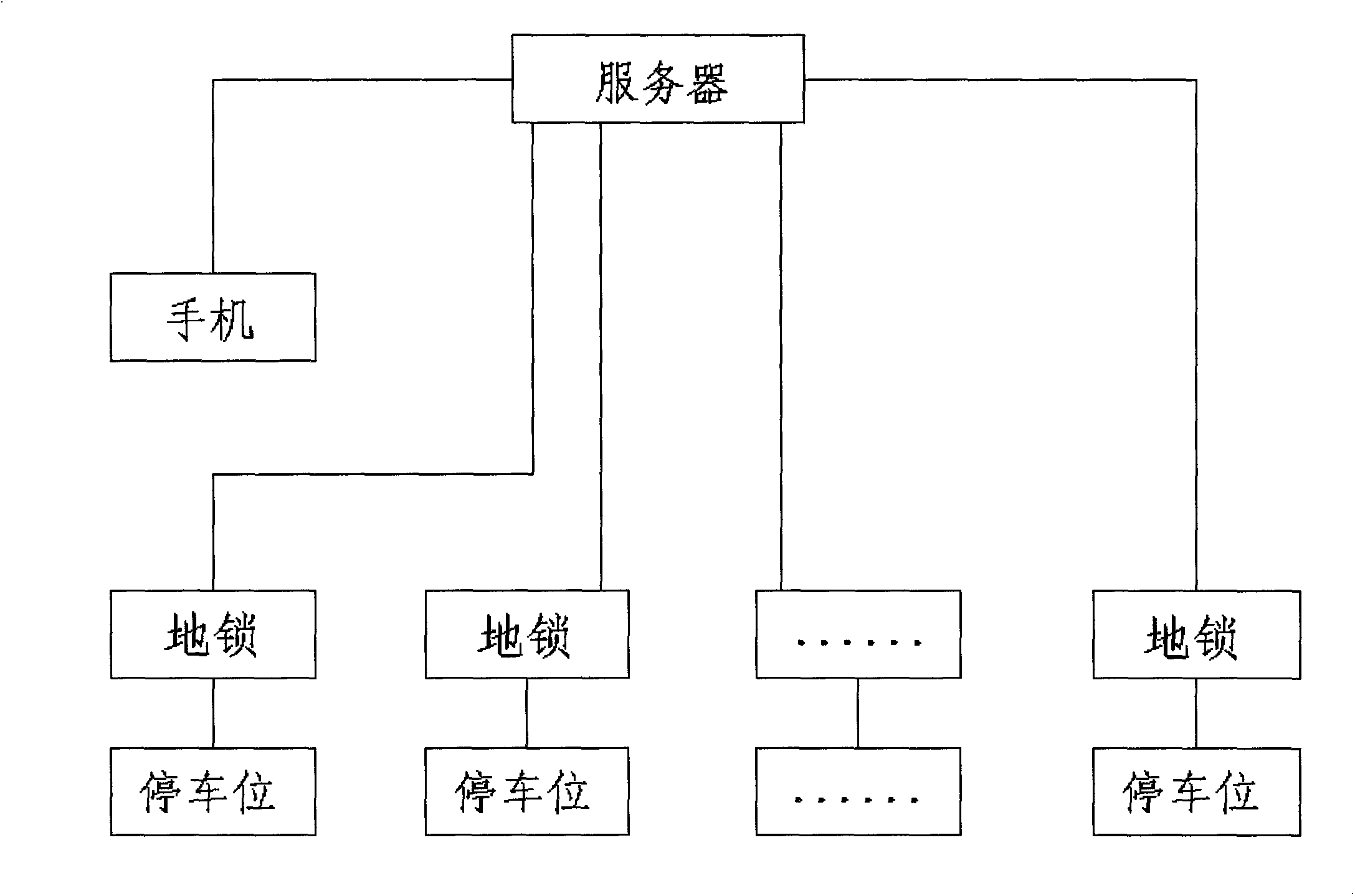
Car parking place management method and system thereof
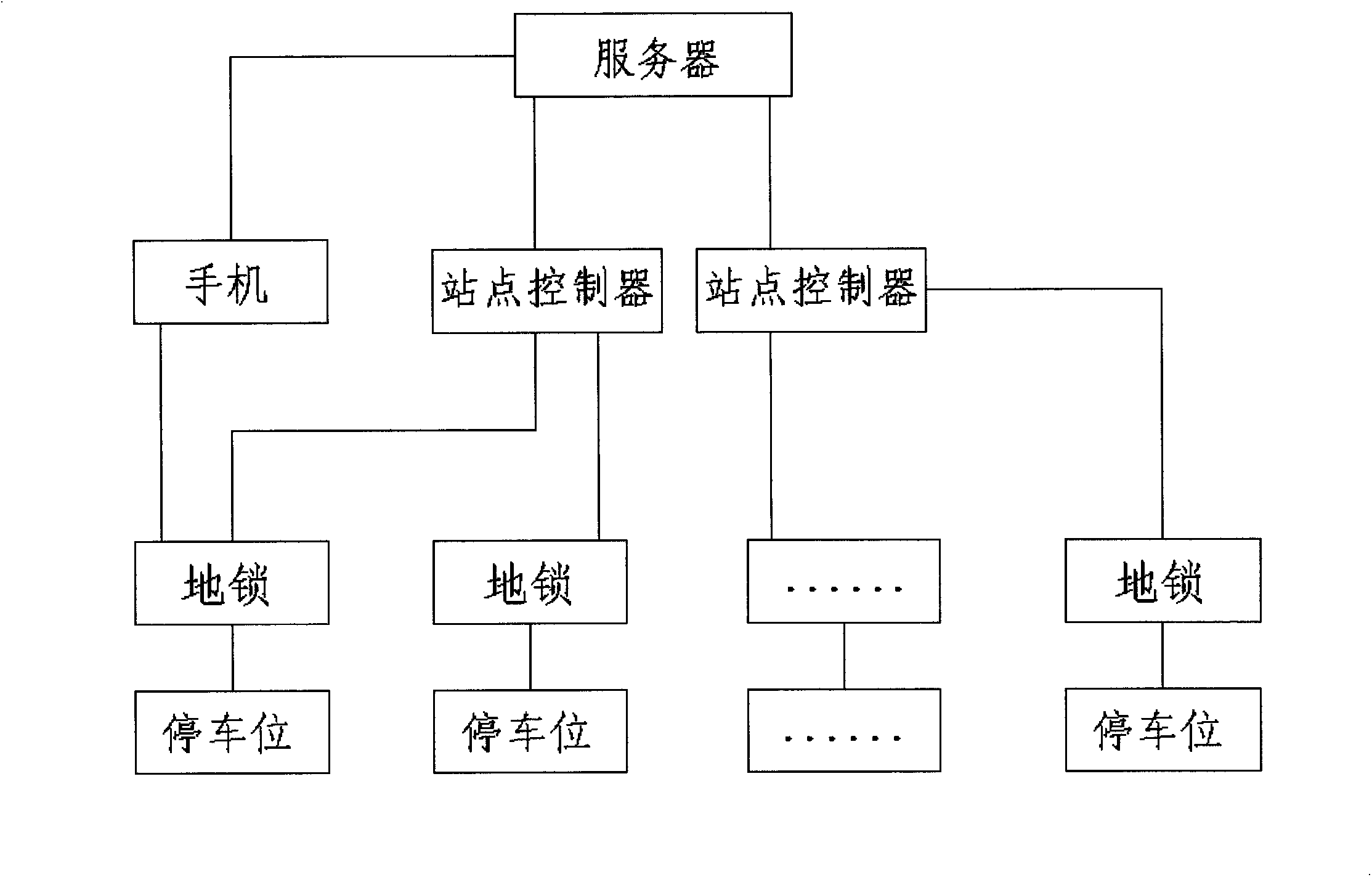
InactiveCN103646568AInquire at any timeEliminate loopholesTicket-issuing apparatusIndication of parksing free spacesRemote controlParking space
The invention discloses a car parking place management method based on a mobile phone APP and a system thereof. Through the mobile phone APP, available parking places for rent can be subjected to management such as query, reservation, renting, recovery and the like, and the parking places are locked and unlocked through remote control. The system comprises a server and a parking place ground lock. The server is connected with the parking place ground lock through a site controller. The parking place ground lock is provided with a two-dimensional code for scanning. The system also comprises a mobile phone which is provided with a positioner. The server is provided with an APP service platform. The mobile phone is in wireless connection with the server. The car parking place management method and system have the advantages of simple use process, high use safety, the query of parking place information at any time and the elimination of a parking fee collection link loophole.
Owner:杭州行我行网络有限公司
Robotic system for assisting in minimally-invasive surgery, which can position a surgical instrument in response to orders from a surgeon, is not attached to the operating table and does not require pre-calibration of the insertion point
InactiveUS20090326324A1Easily and rapidly removedEasy system integrationEndoscopesSurgical robotsEngineeringActuator
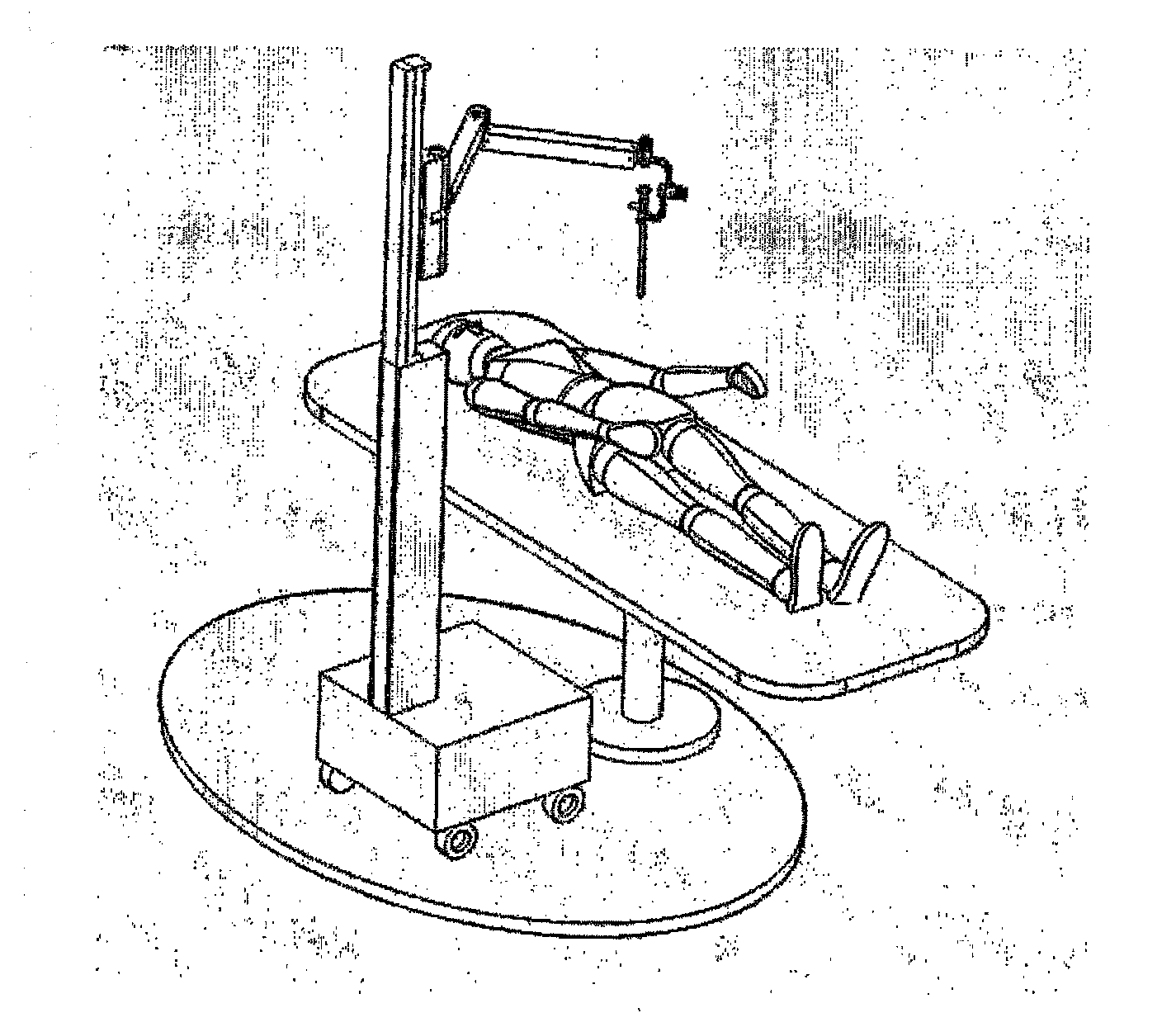
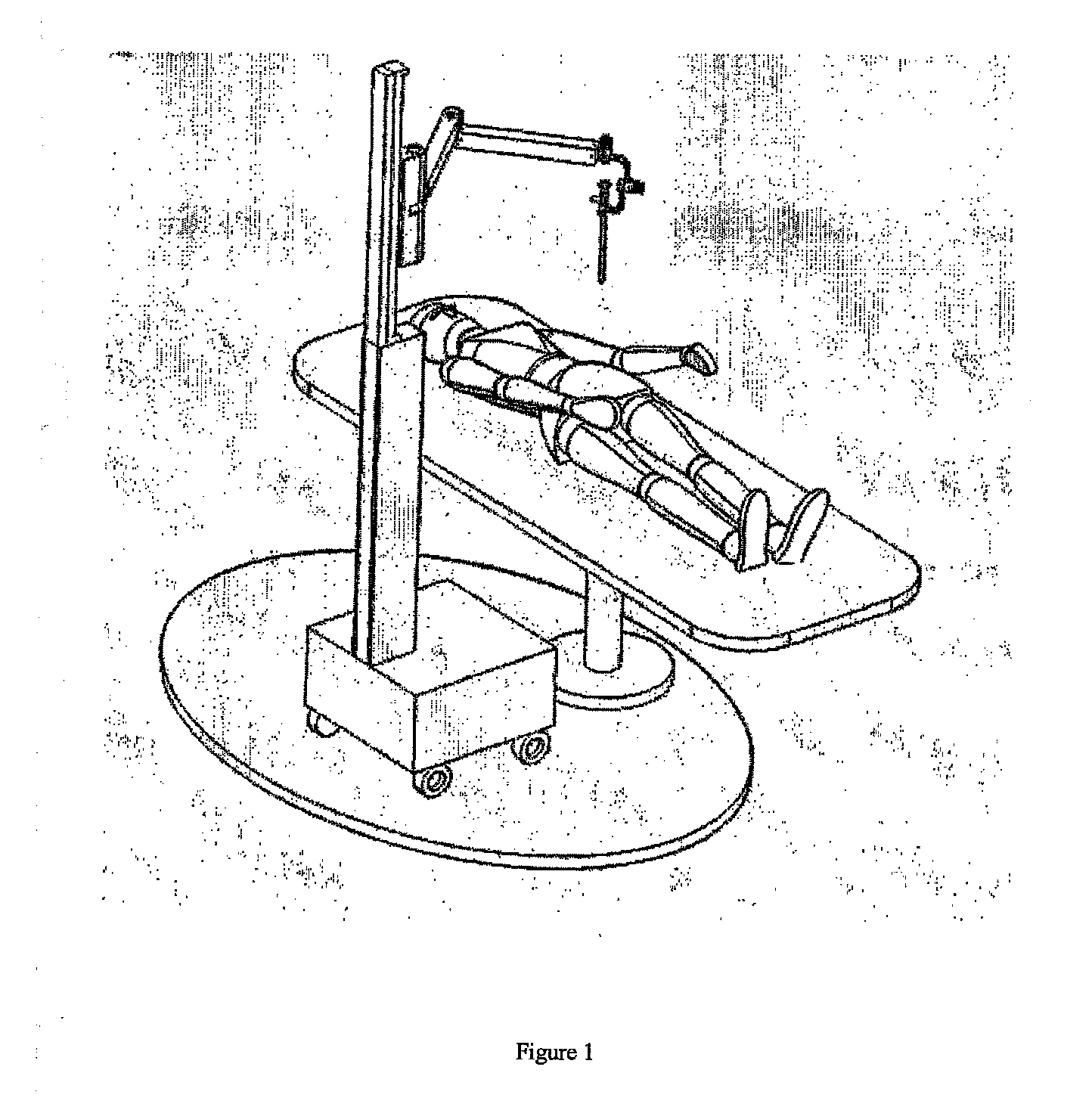
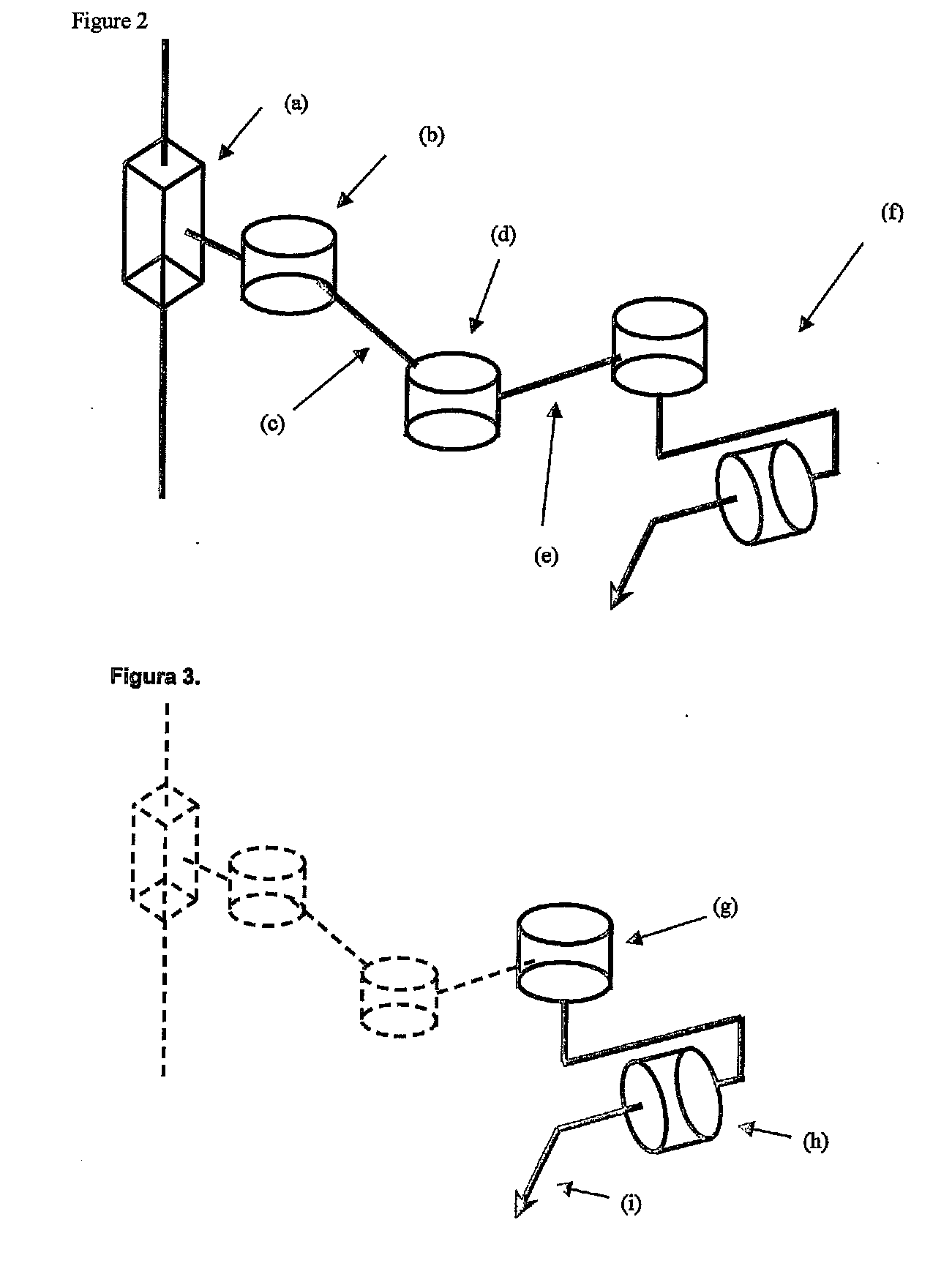
Robotic system for assisting in minimally-invasive surgery, which can position a surgical instrument in response to orders from a surgeon, is not attached to the operating table and does not require pre-calibration of the insertion point. The system includes: a manipulator robot having three active degrees of freedom, which is provided with an end actuator having two passive degrees of freedom, said actuator being used to attach a surgical instrument; a robot controller built into the structure thereof, which can perform a method for calculating the movement to be imparted to the carried surgical instrument so that it reaches the desired location without requiring pre-calibration and without the assembly having to be attached to the operating table; and an interface system for ordering the system to perform the desired actions. The assembly comprising the robot, the controller and the interface system is battery operated.
Owner:UNIV DE MALAGA
Systems and methods for securing an automotive controller network
InactiveUS20190281052A1Eliminates and reduces disadvantageEliminates and reduces and problemAutonomous decision making processMultiple keys/algorithms usageEngineeringSecurity policy
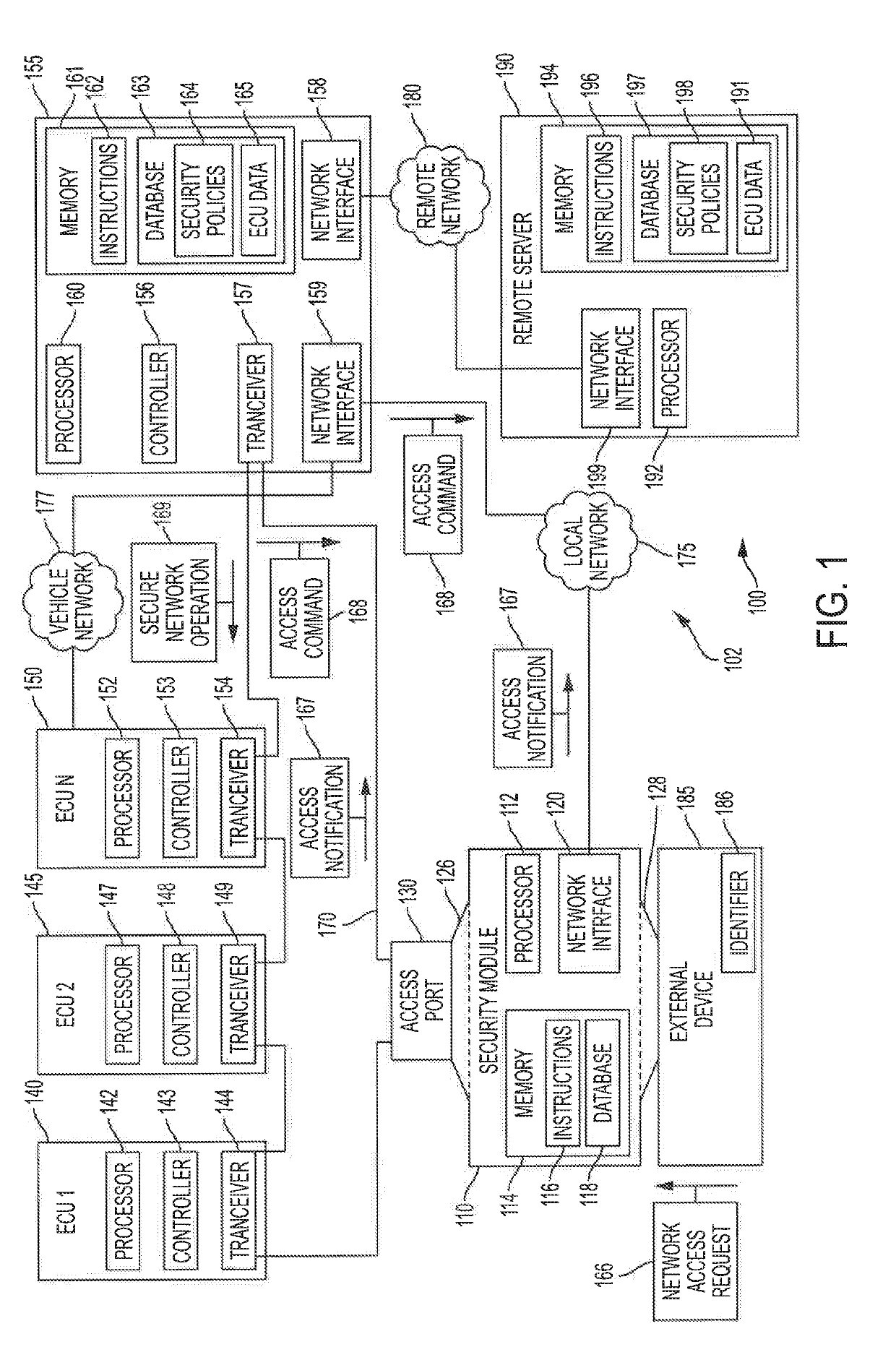
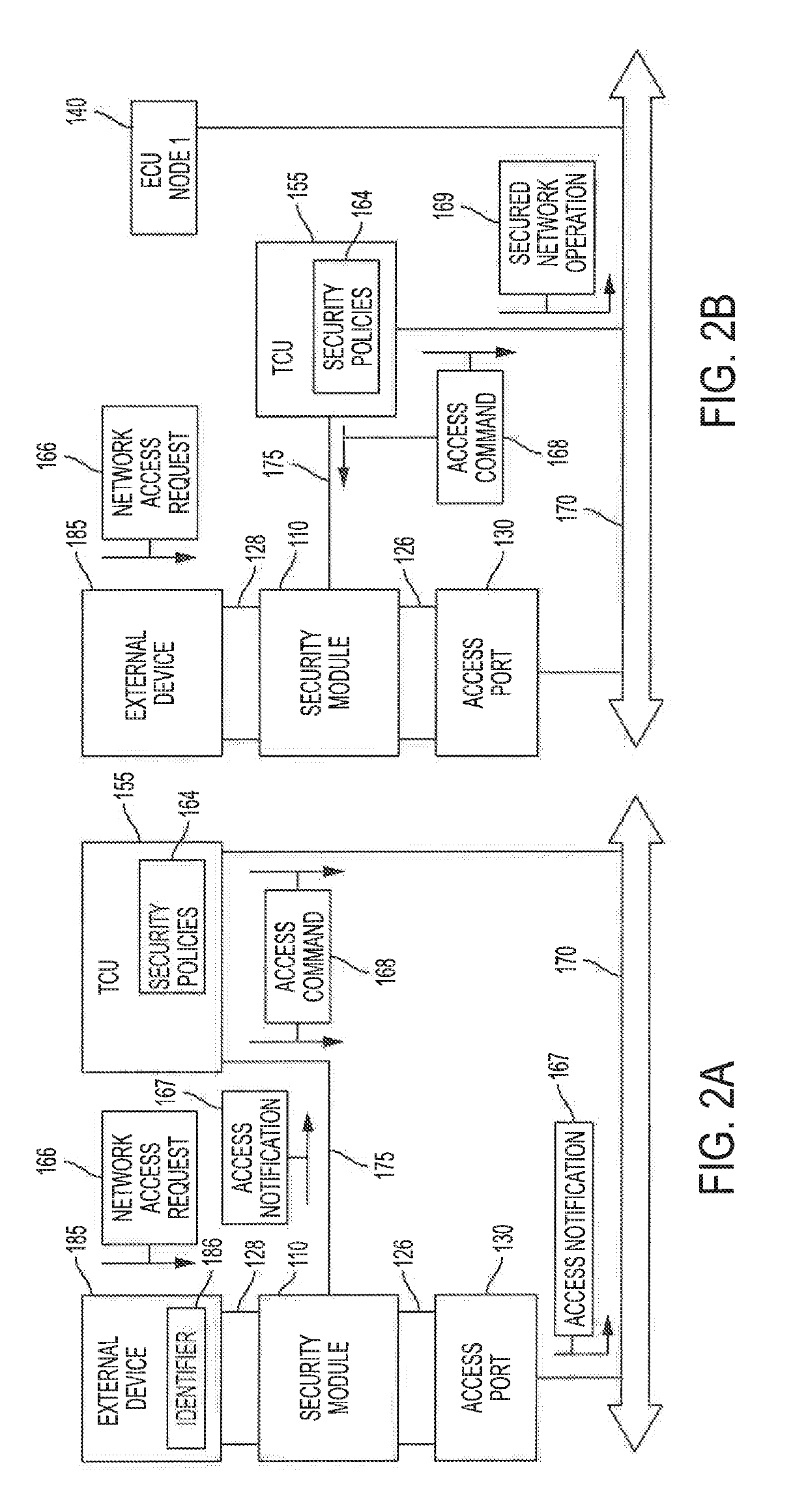
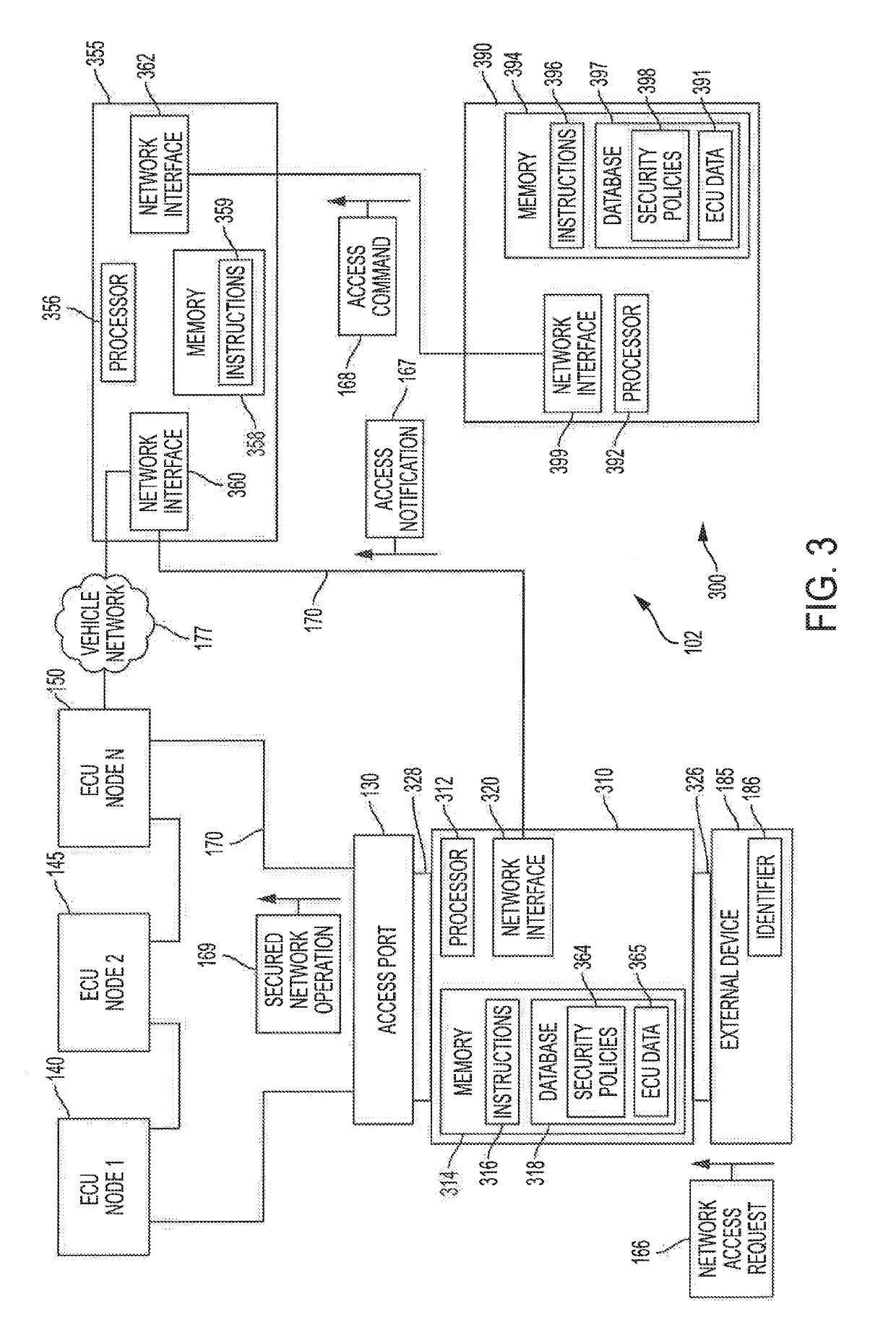
Systems and methods for securing a select vehicle's automotive controller network are described. Embodiments introduce a pass-through security module with a first interface physically coupled to an unsecured access port to the automotive controller network and configured to communicatively couple or decouple with the access port based on a determination of whether network access requests received by a second interface of the security module from an external device are authorized to interact the automotive controller network. Authorization determinations may be made by the security module in conjunction with a telematics control unit and / or a remote server in accordance with one or more security policies. The security module may further use the one or more security policies to impose an encryption infrastructure on the automotive controller network to facilitate sender identification and data frame authenticity.
Owner:AUTON INC
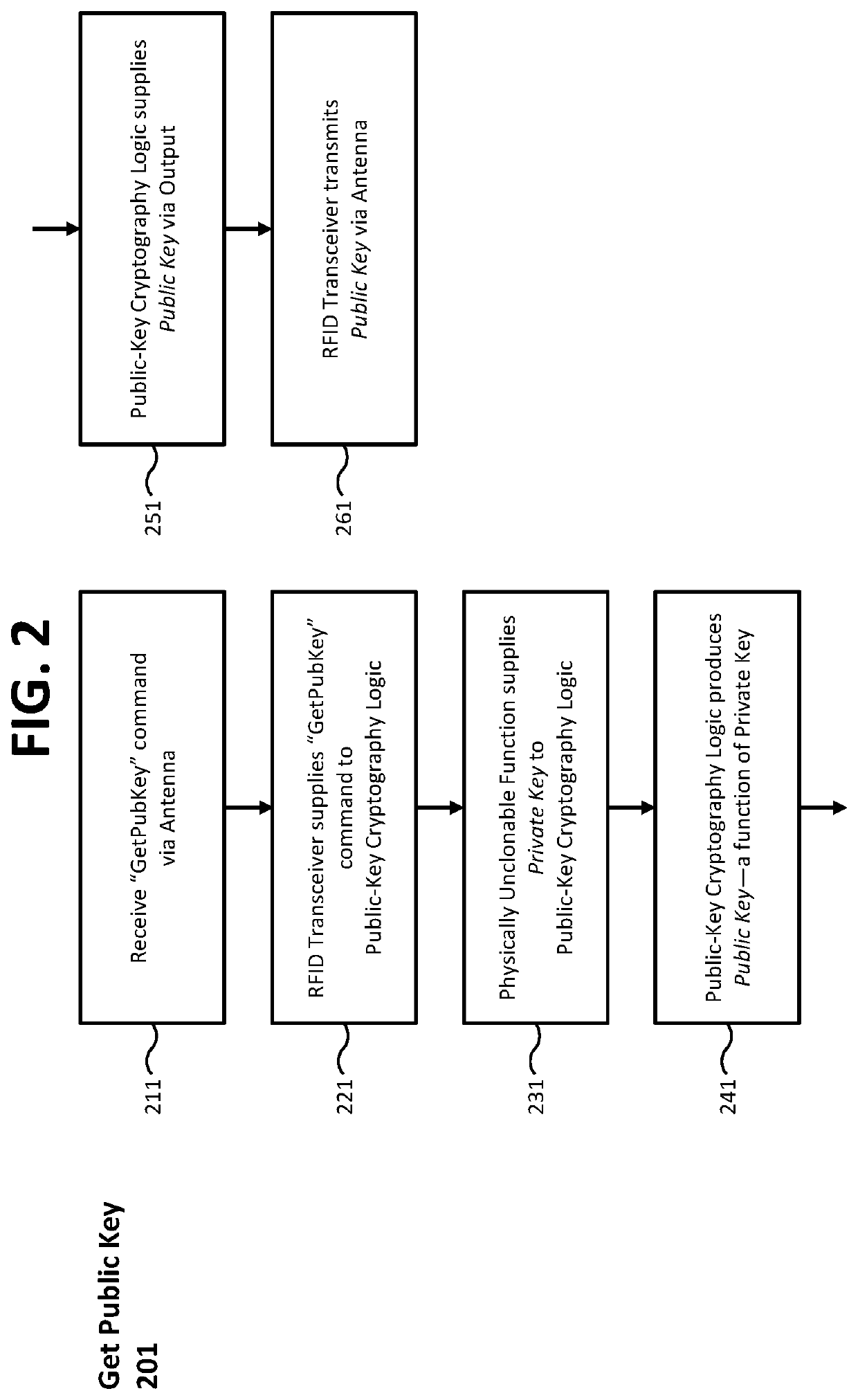
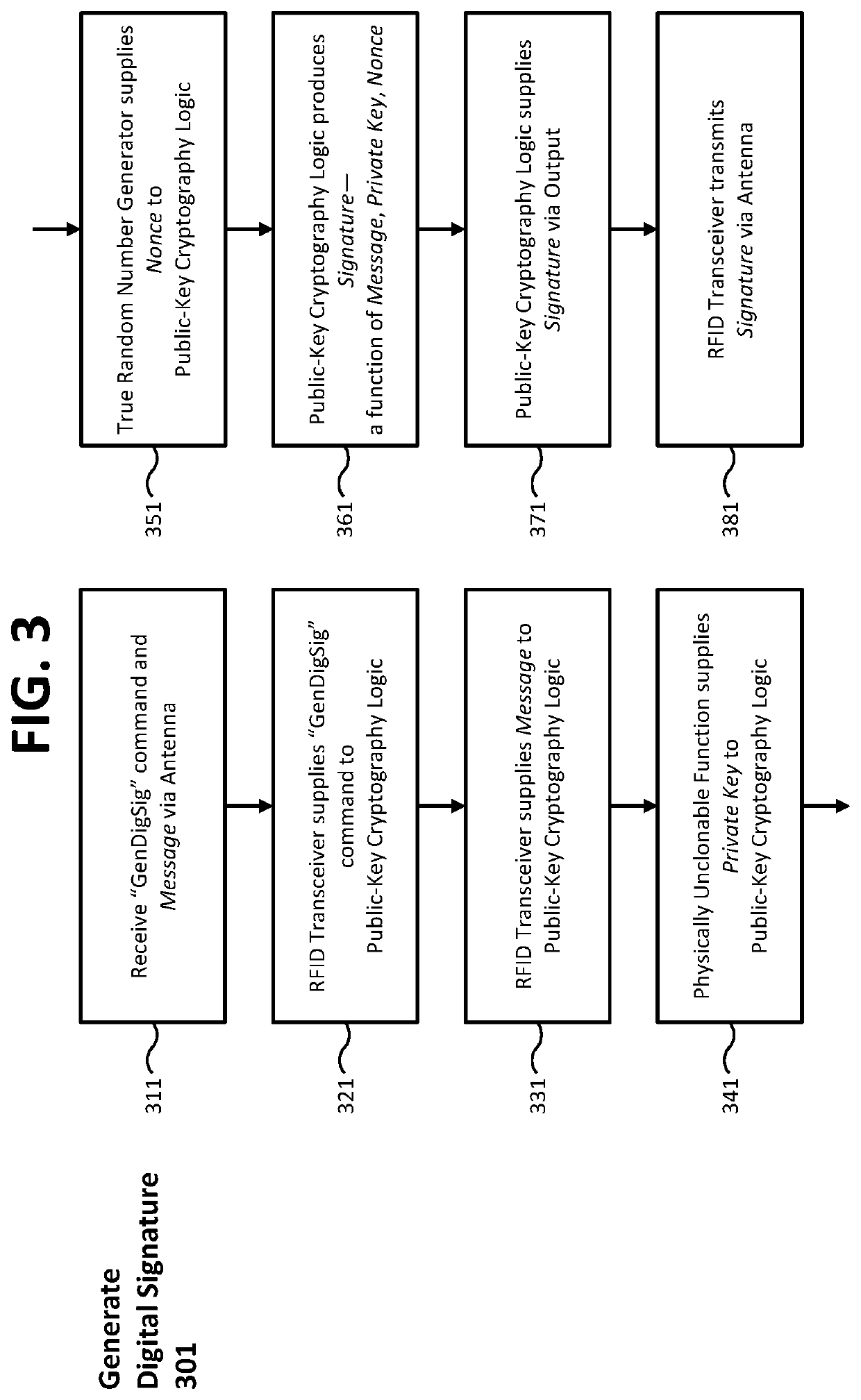
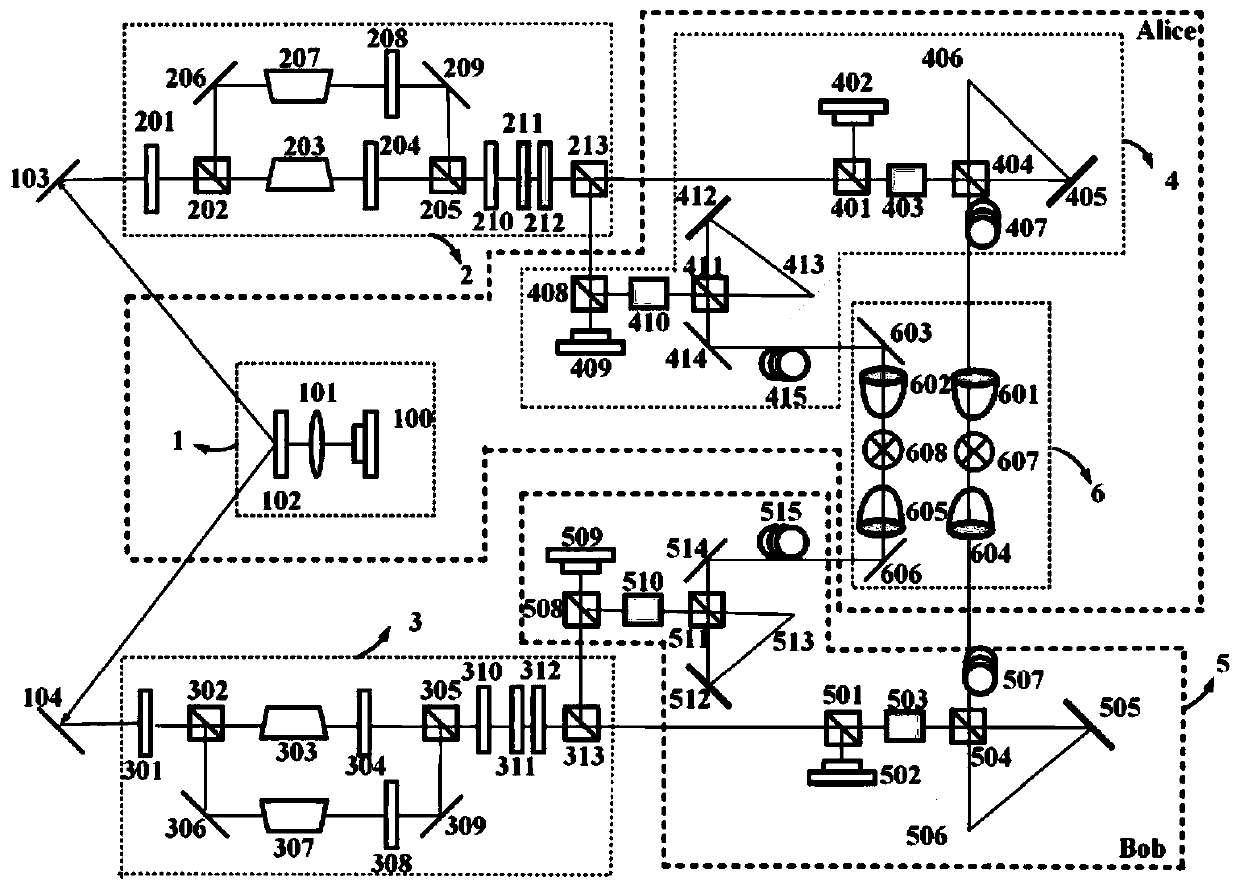
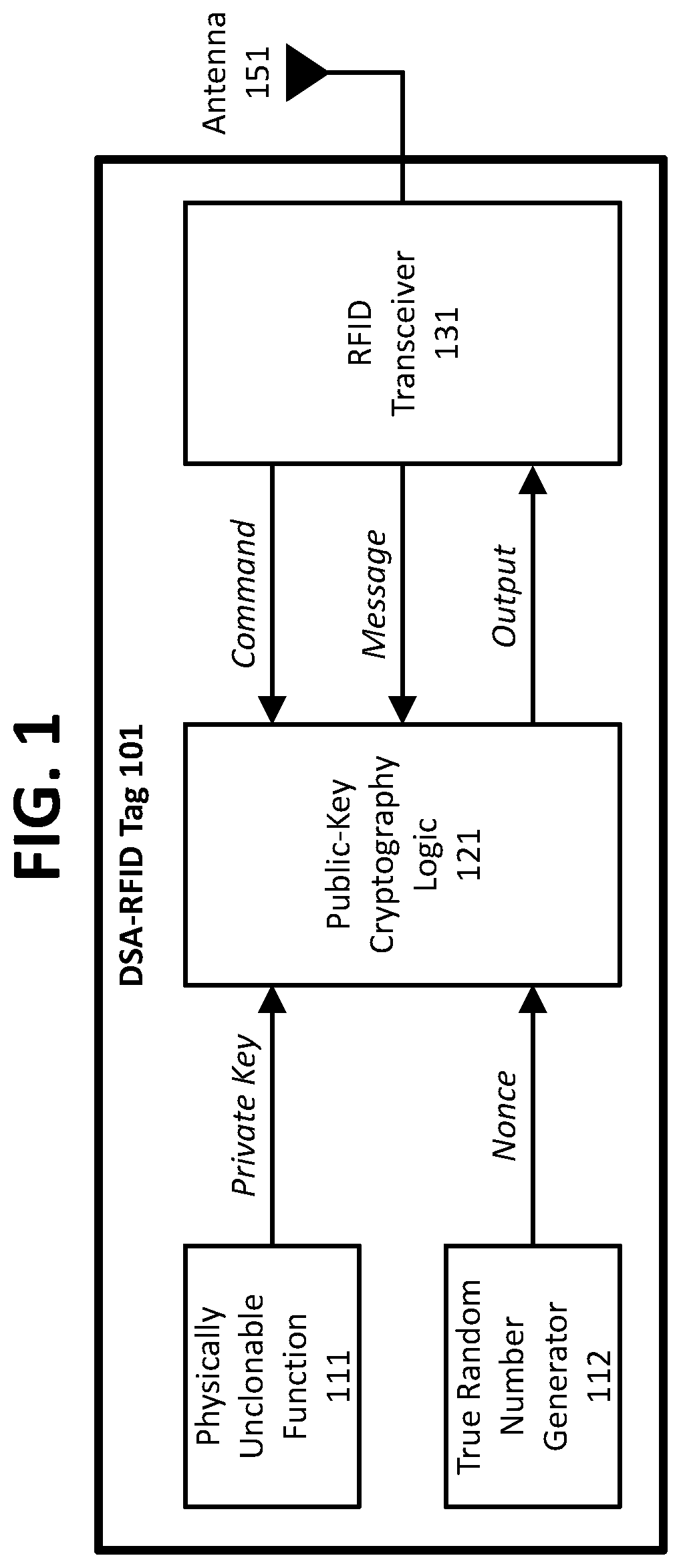
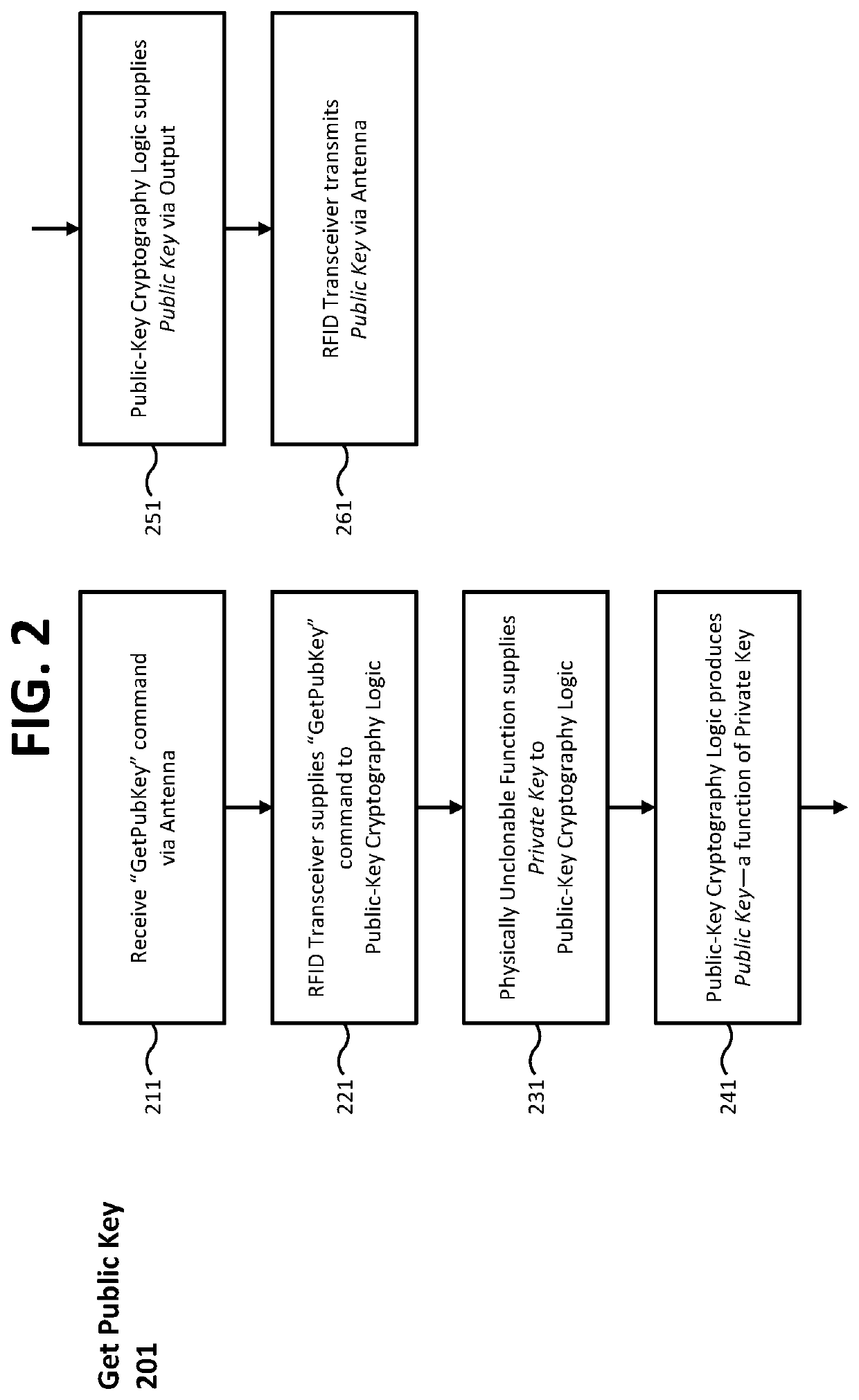
Devices, methods, and systems for cryptographic authentication and provenance of physical assets
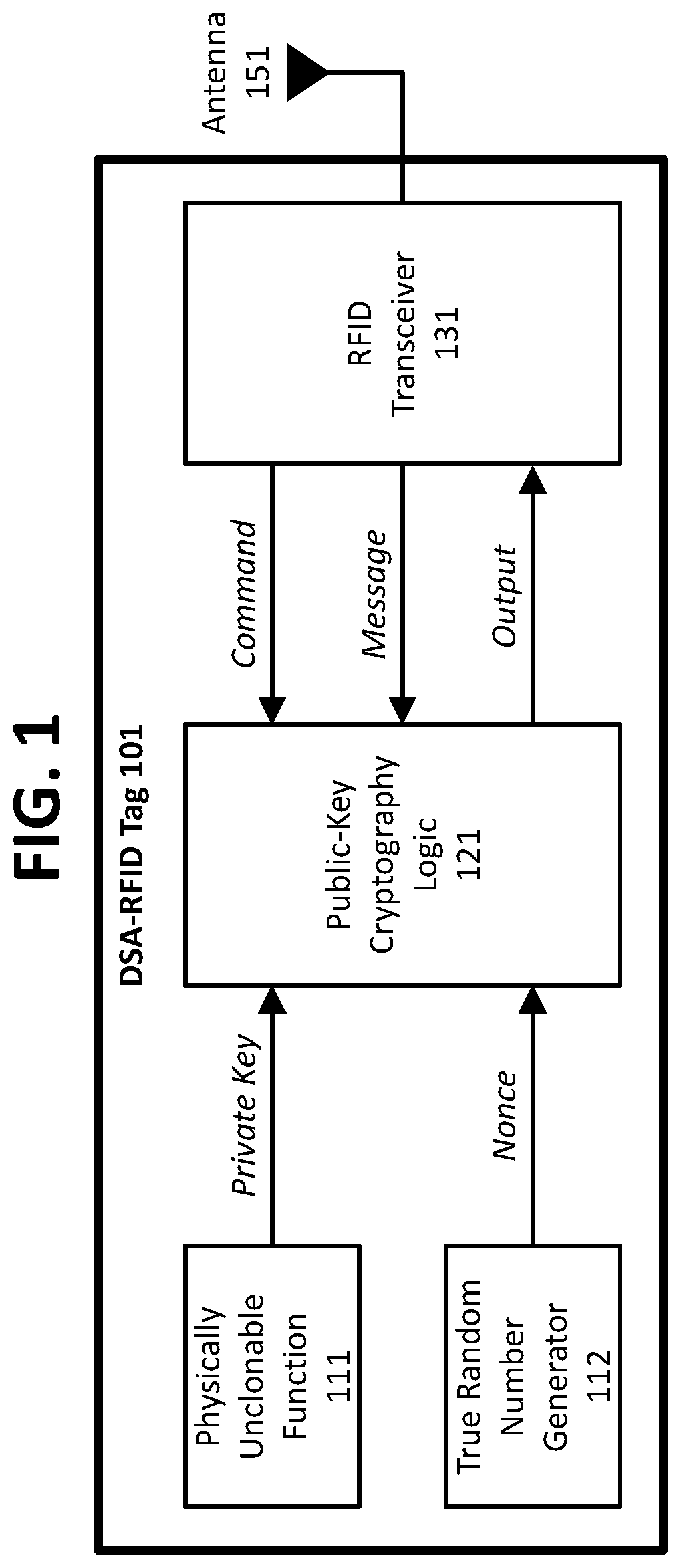
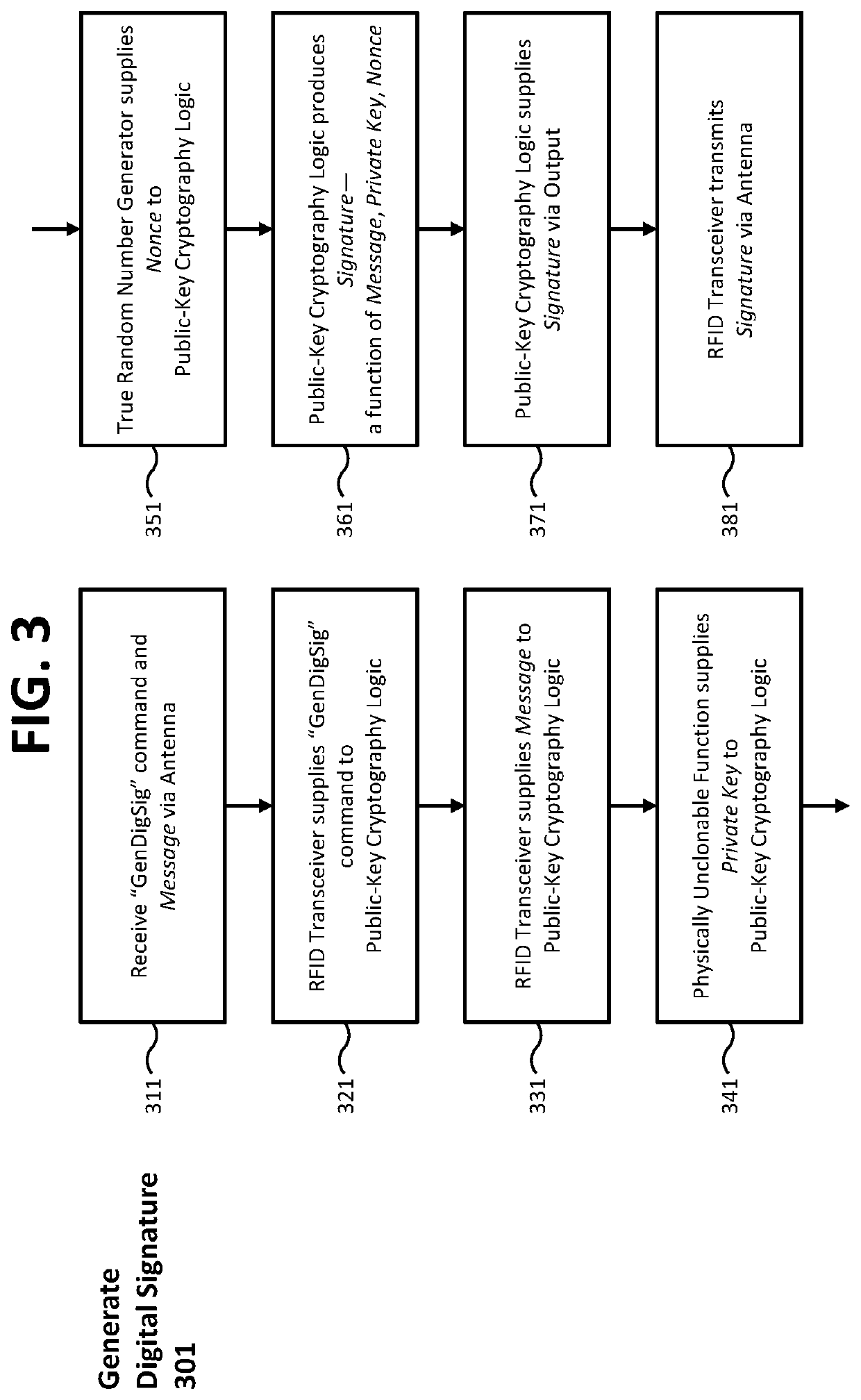
ActiveUS10523443B1Eliminate loopholesKey distribution for secure communicationRandom number generatorsDigital Signature AlgorithmAuthentication
Authentication and provenance of physical assets may be achieved by attaching a cryptographically strong RFID tag including a physically unclonable function and public-key cryptography logic which implements a digital signature algorithm. The cryptographically strong RFID tag directly participates in a novel implementation of blockchain technology, constructing an indelible and cryptographically provable record of authenticity and provenance with a new level of trustworthiness to protect physical assets.
Owner:KLEINMAN BRUCE
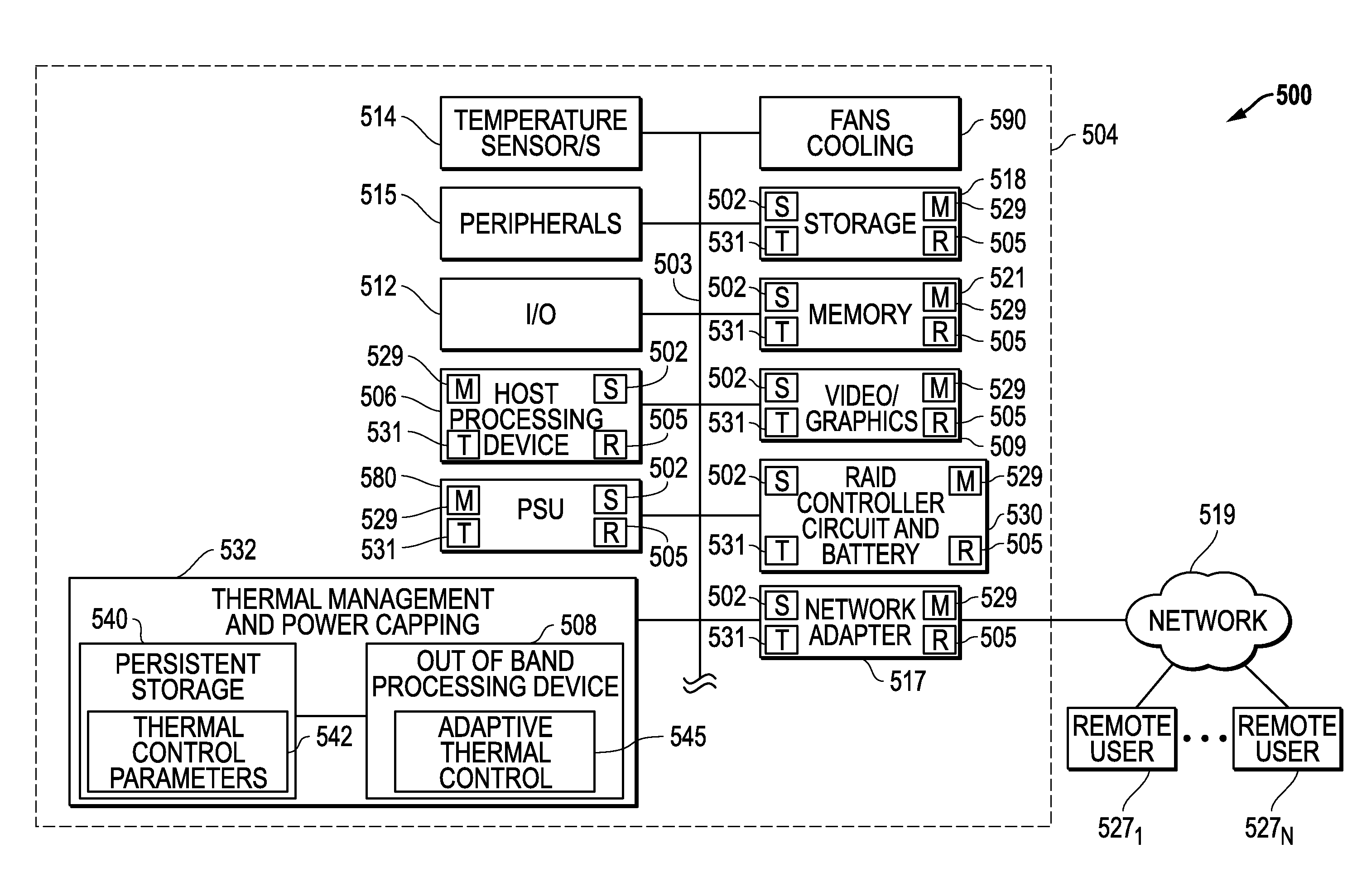
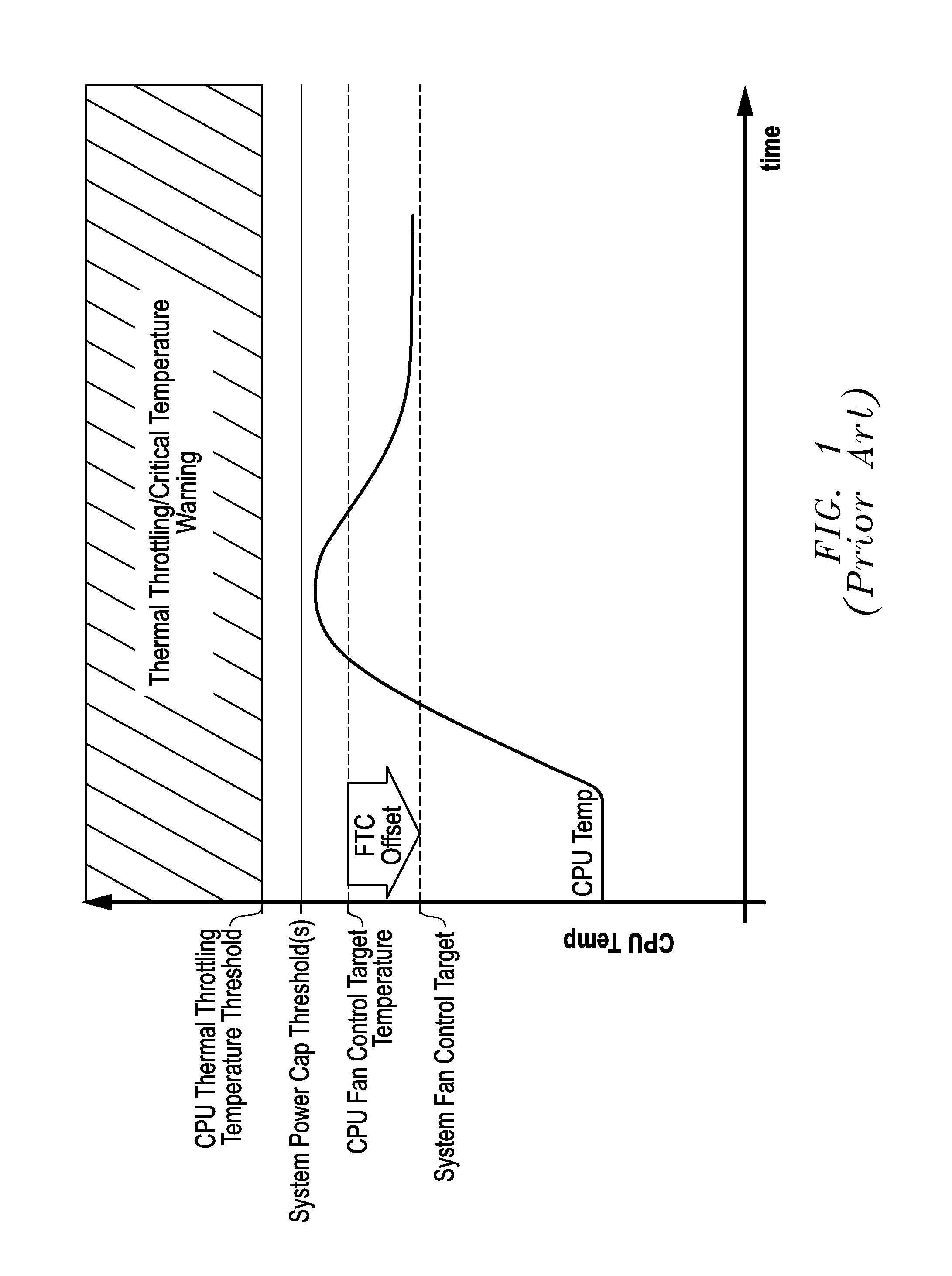
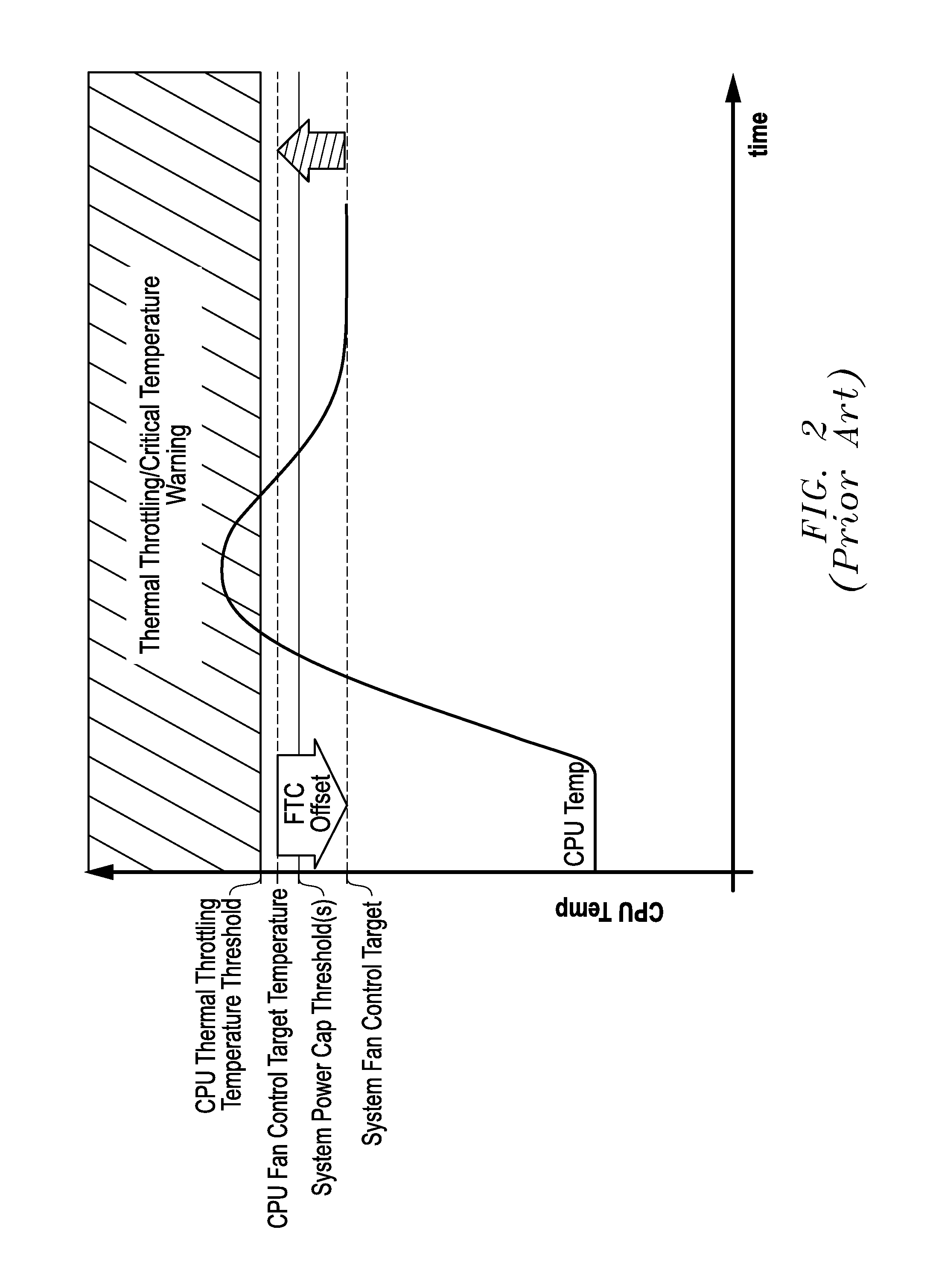
Systems And Methods Of Adaptive Thermal Control For Information Handling Systems
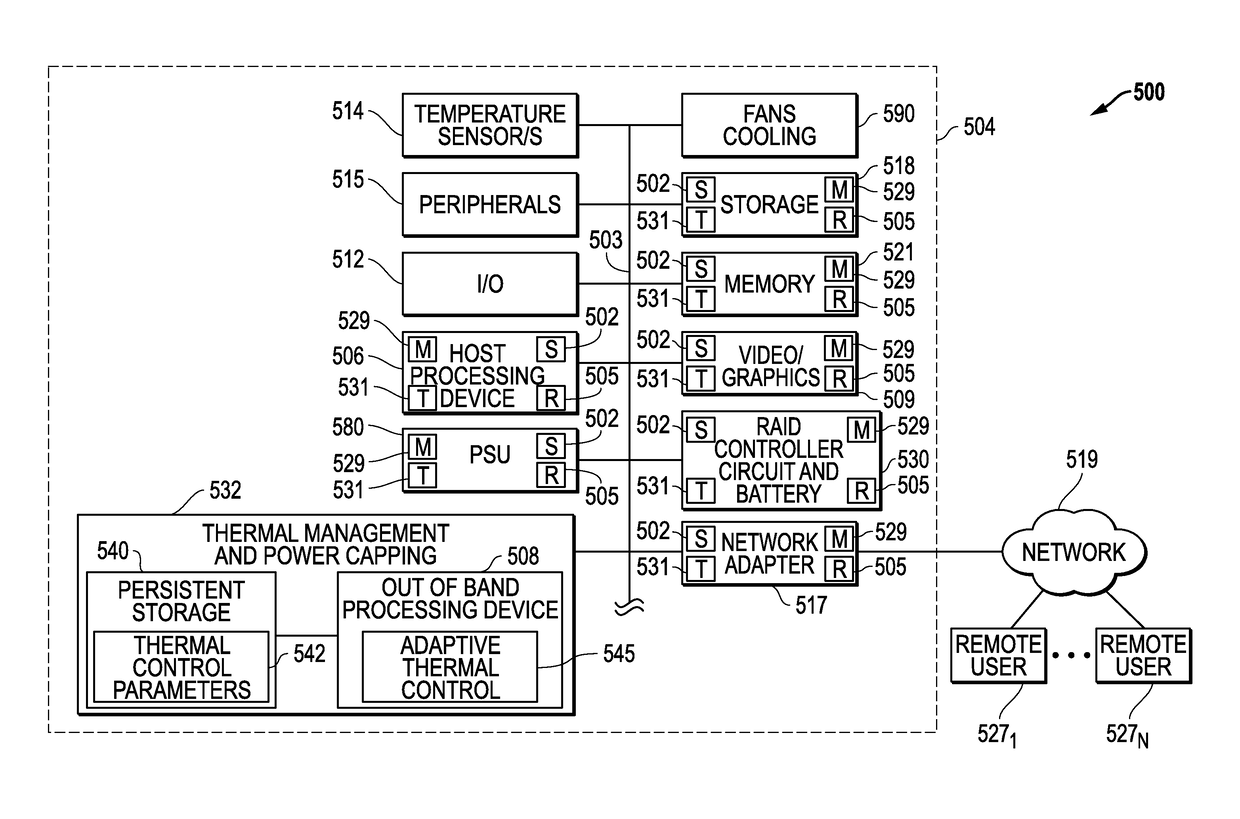
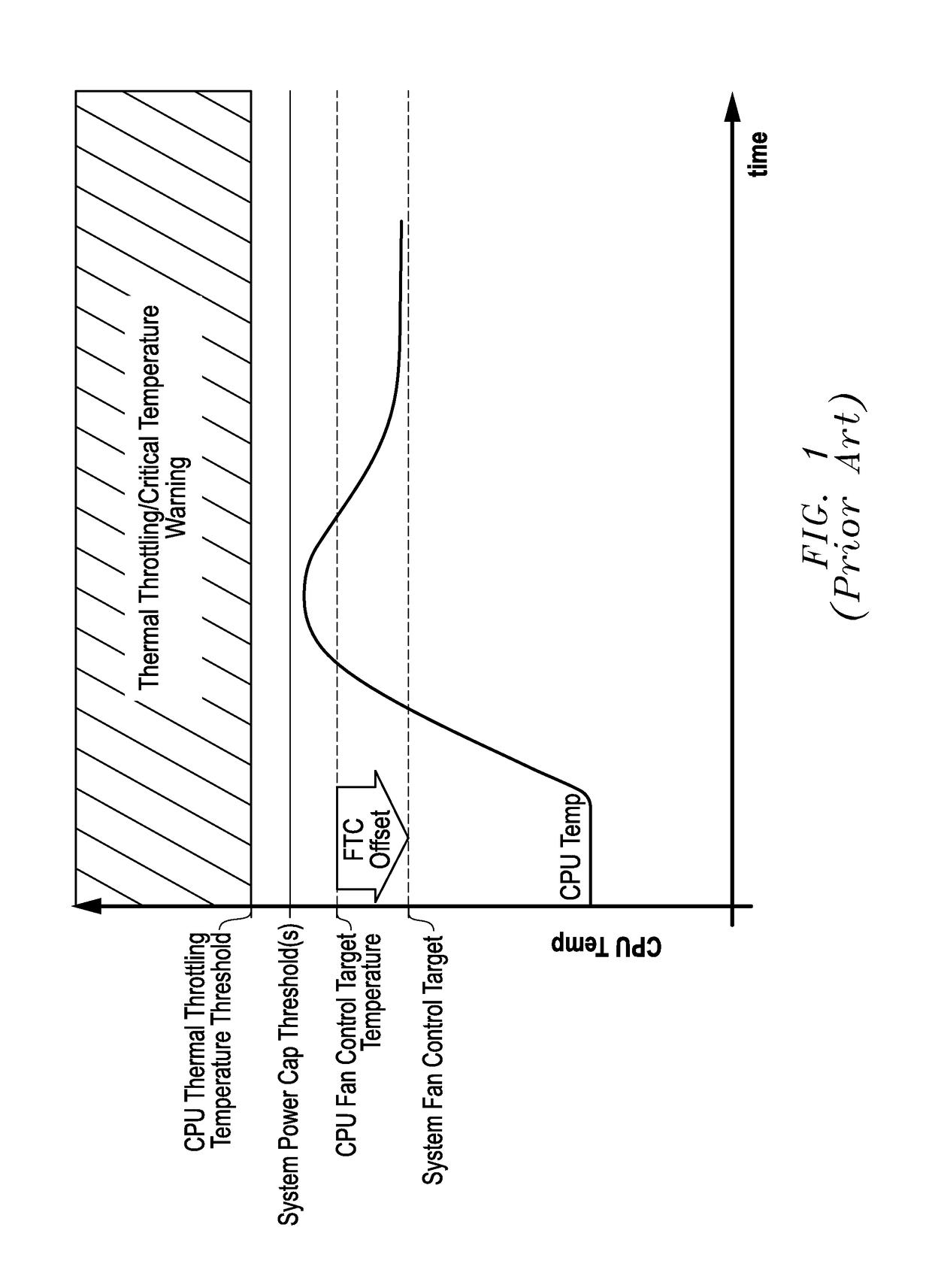
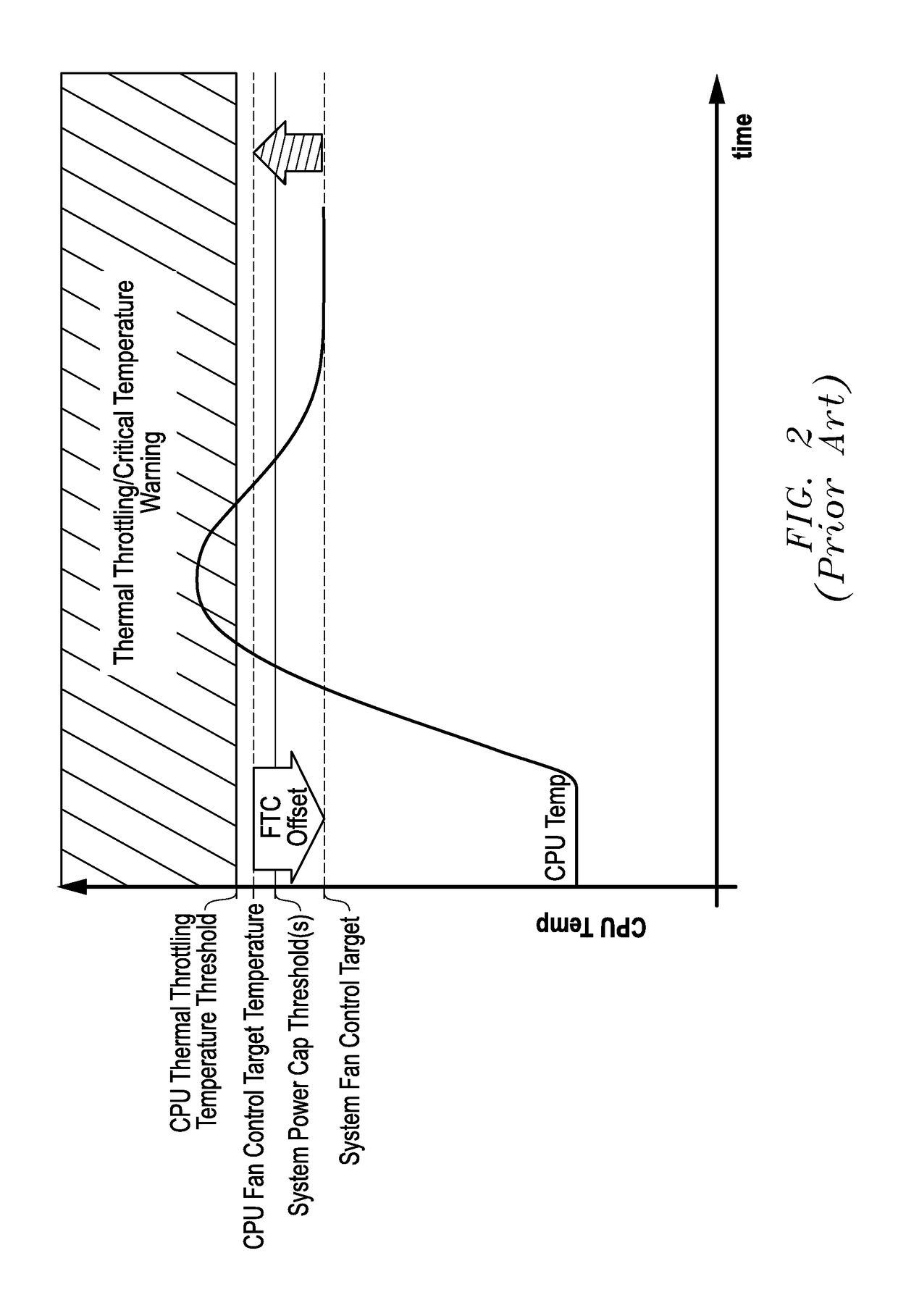
ActiveUS20160274629A1Eliminate vulnerabilityEliminate loopholesProgramme controlDigital data processing detailsSelf adaptiveEngineering
Systems and methods of adaptive thermal control are provided for information handling system platforms that may be implemented to automate and scale fan control settings by making the fan control settings relative to a reported component thermal control parameter value from a component of an information handling system platform, such as a CPU or other heat generating component. In one example, bounds for system use of vendor or component manufacturer-reported thermal control parameter values may be set for system cooling so as to confine use of these values within information handling system platform limits characterized by a manufacturer of an information handling system platform.
Owner:DELL PROD LP
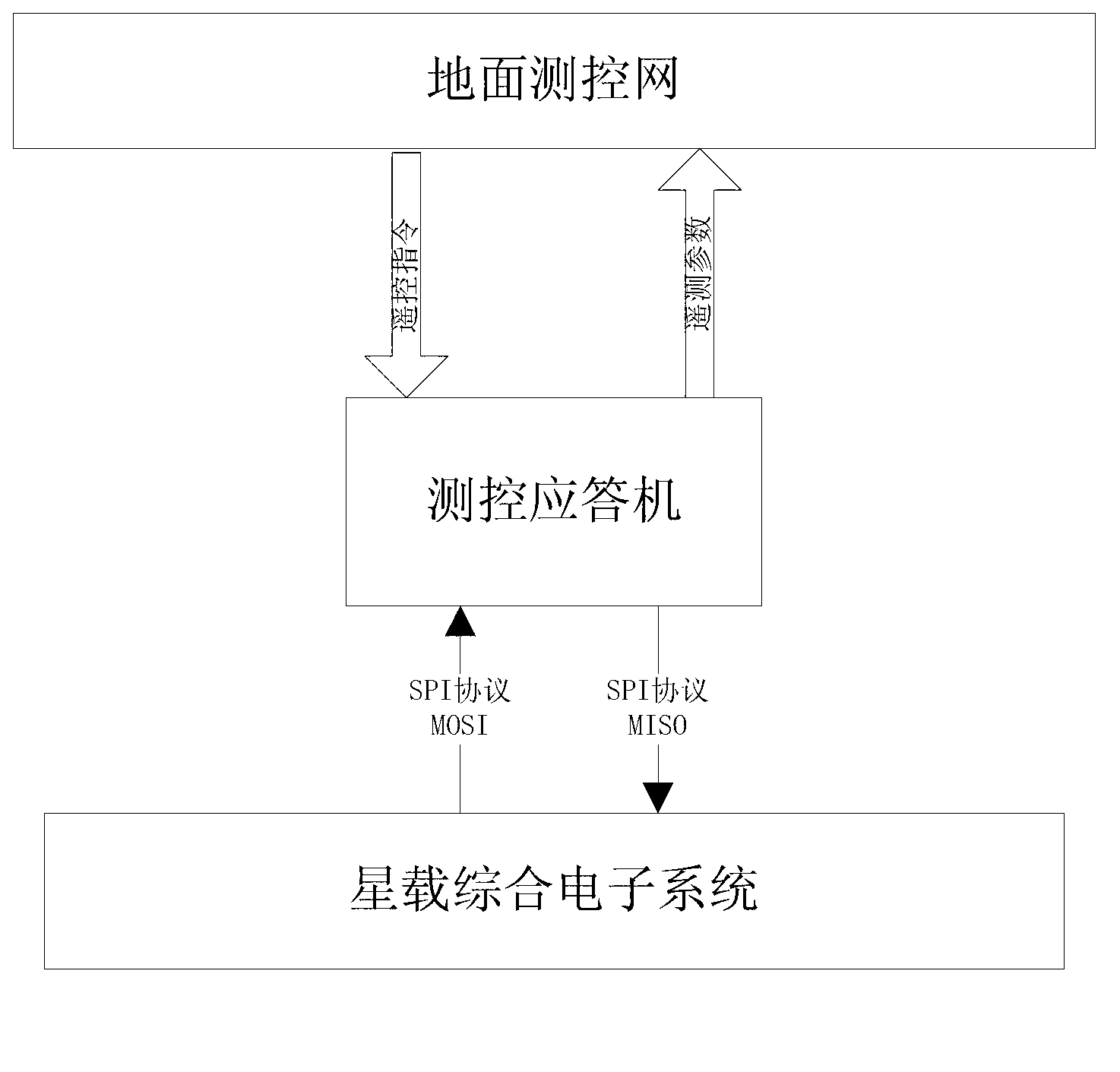
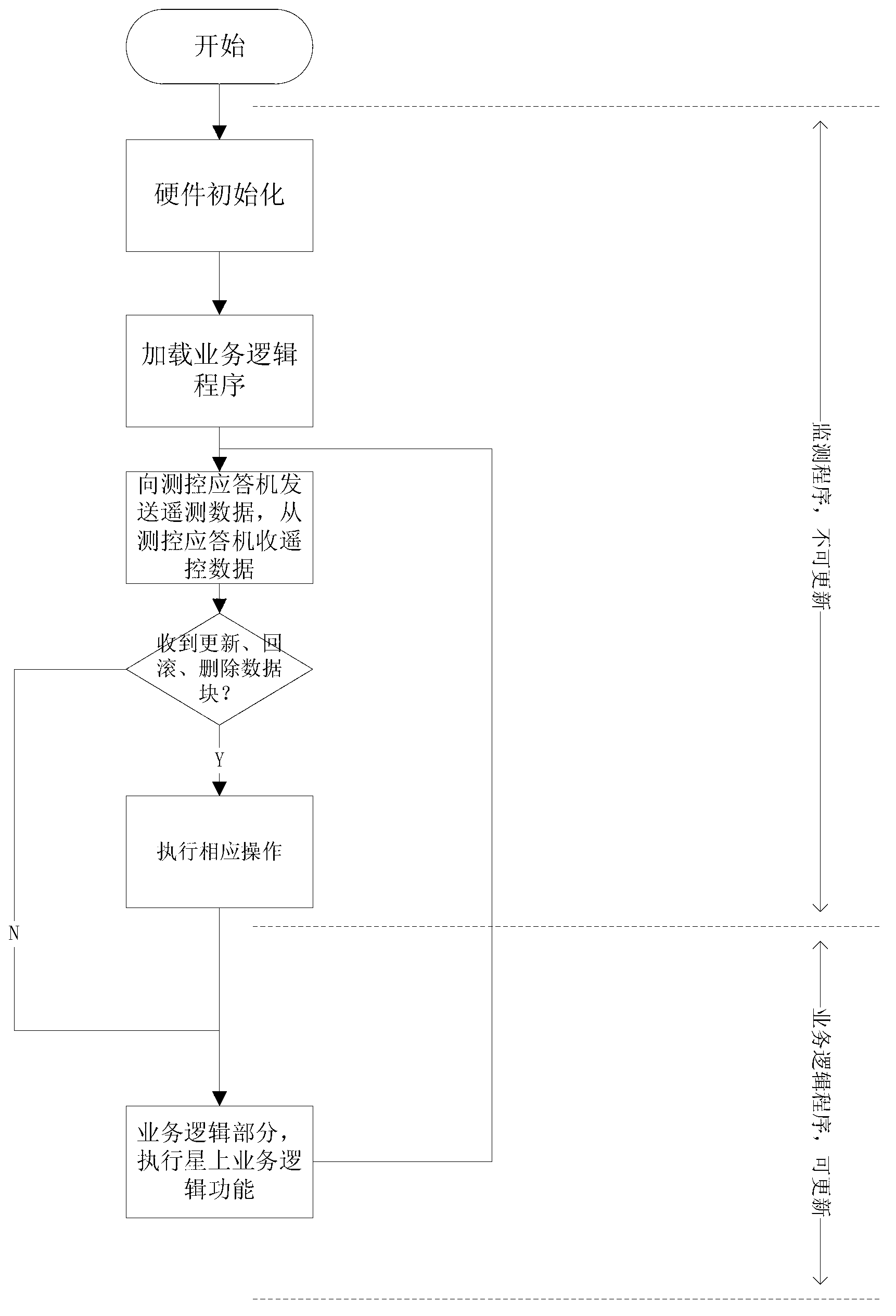
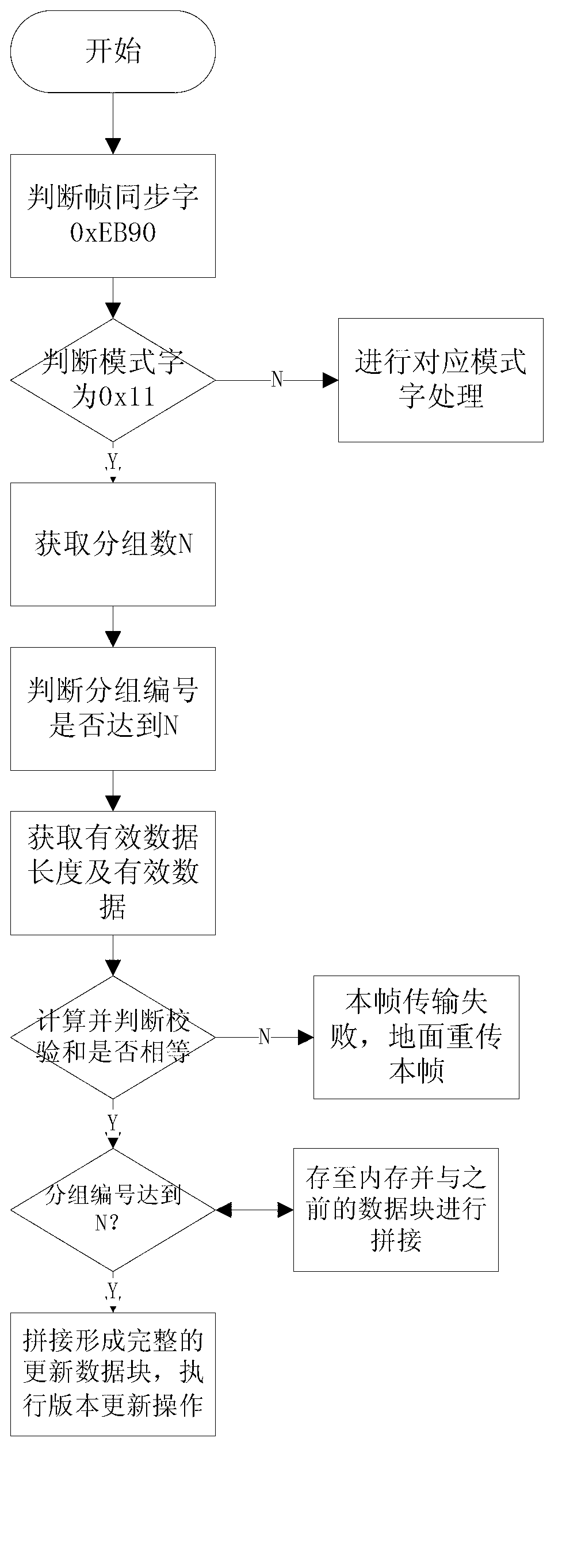
On-orbit update method for satellite-borne integrated electronic system program
InactiveCN103226484AImprove general performanceSimple configurationProgram loading/initiatingElectronic systemsGranularity
The invention discloses an on-orbit update method for a satellite-borne integrated electronic system program. The on-orbit update method comprises the steps as follows: dividing the satellite-borne integrated electronic system program into a monitoring program and a service logic program, receiving an update data block of a target program block in the service logic program to be updated from the ground through the monitoring program, detecting if the target program block runs, updating after the target program block is executed if the target program block runs, and otherwise, updating immediately; and when updating, obtaining a program execution right from the service logic program to be updated through the monitoring program, storing the current version and the version number of the target program block to an external memory, importing a new-version program block carried by the update data block into a memory, giving the program execution right to the service logic program to be updated, and updating the original version number of the target program block into a new version number through the service logic program to be updated. Compared with the prior art, the on-orbit update method is strong in commonality, updates the granularity into a function, and can execute the rollback and delete operations.
Owner:ZHEJIANG UNIV
Power controller
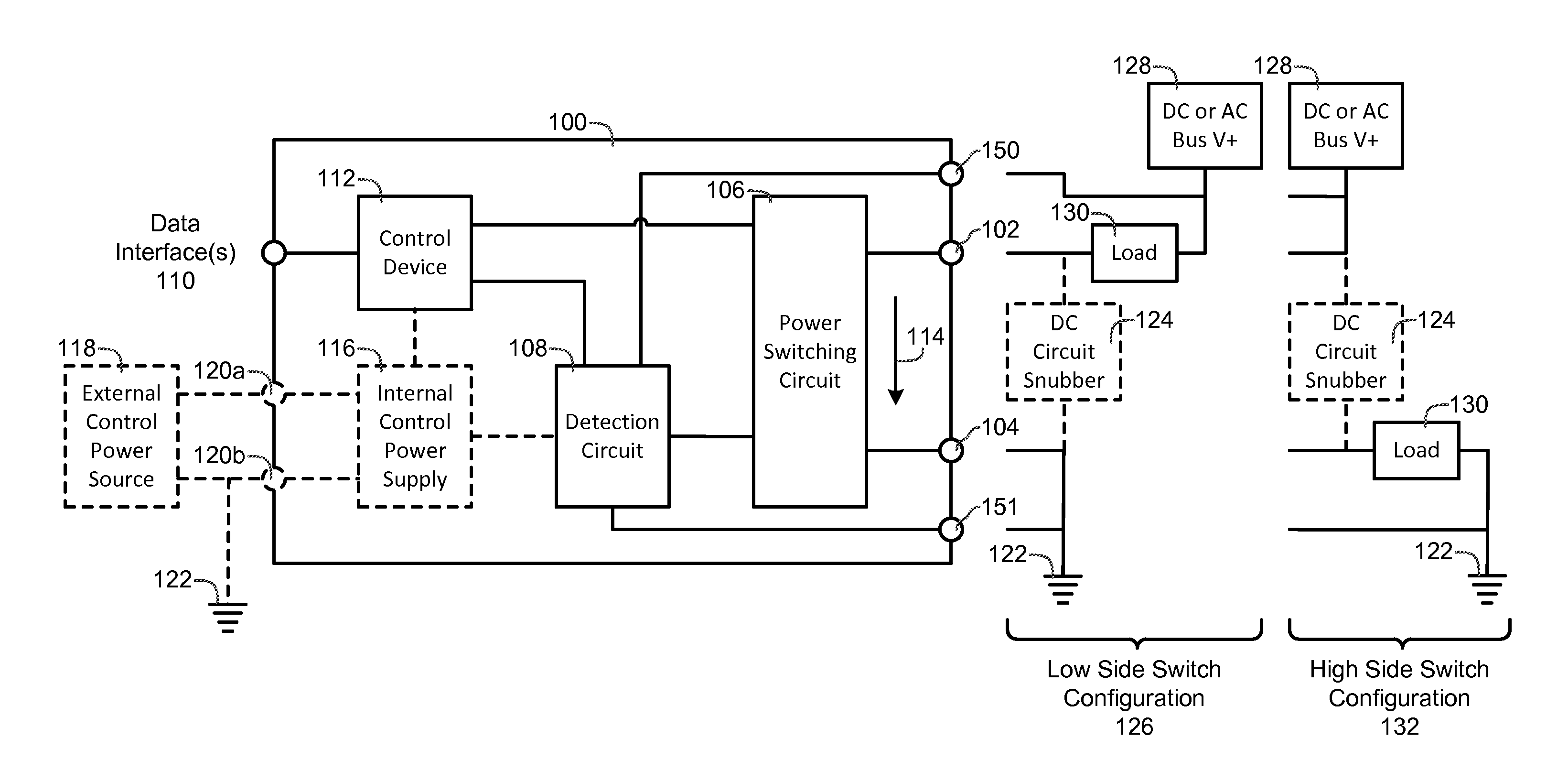
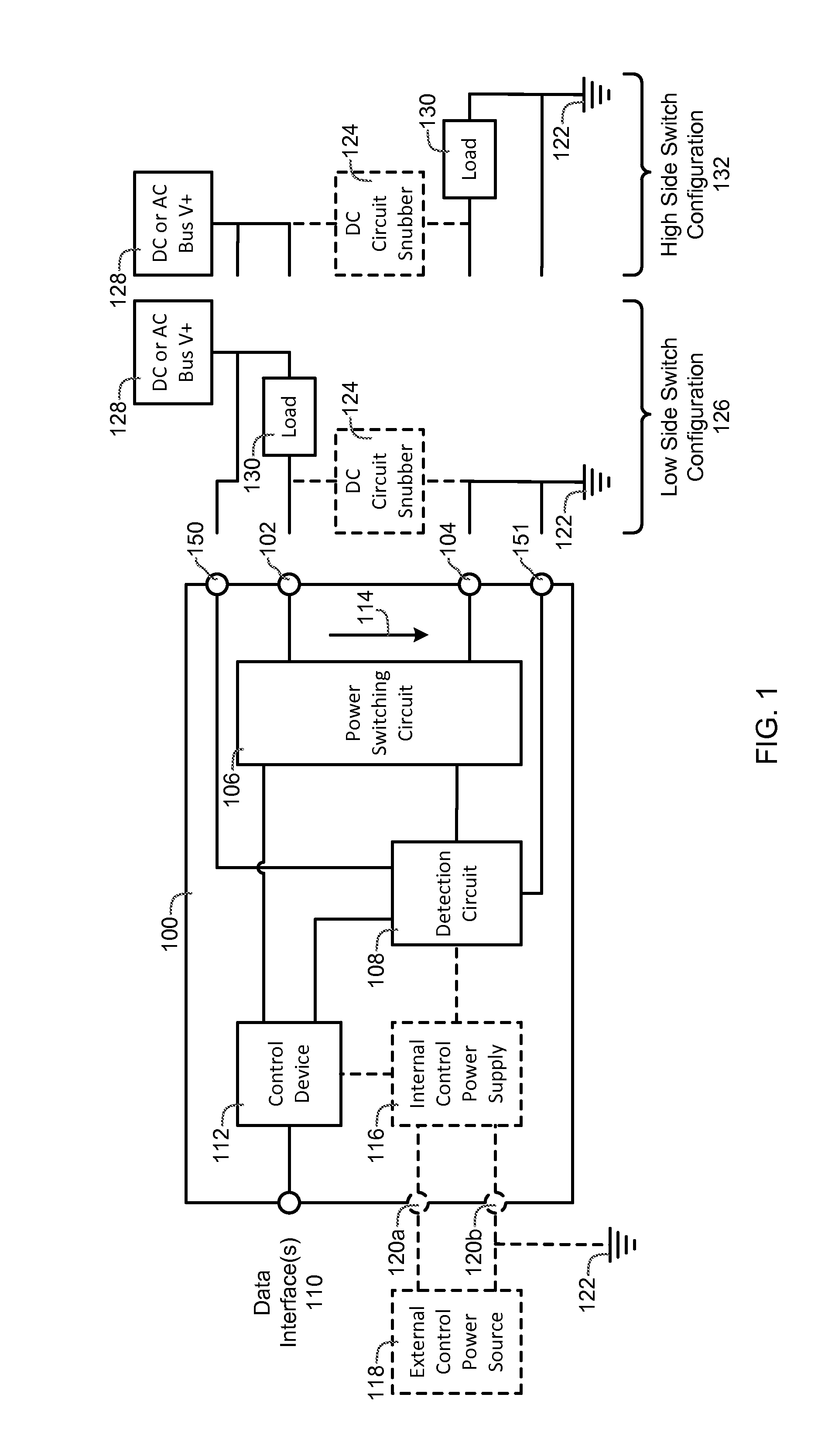
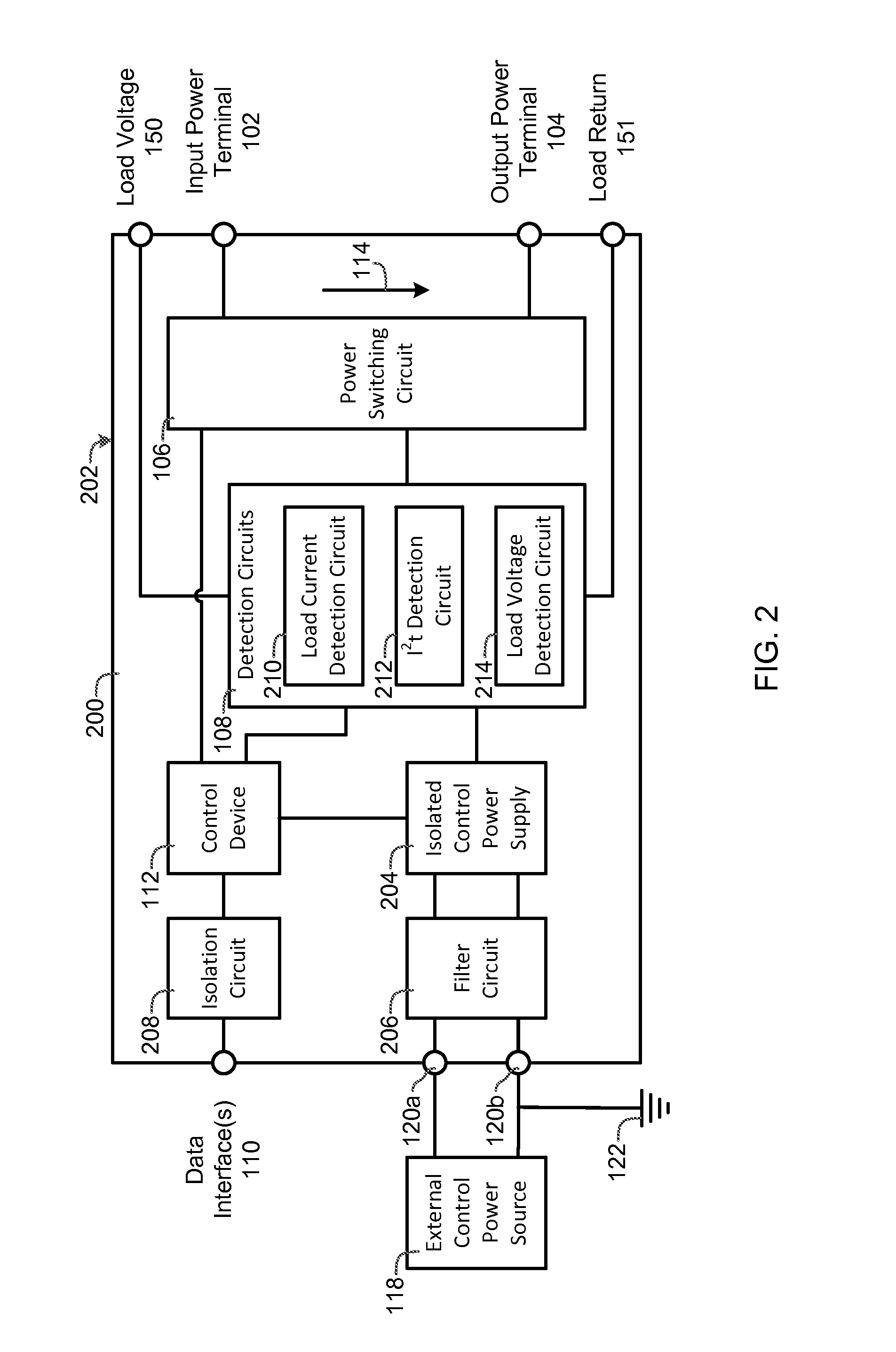
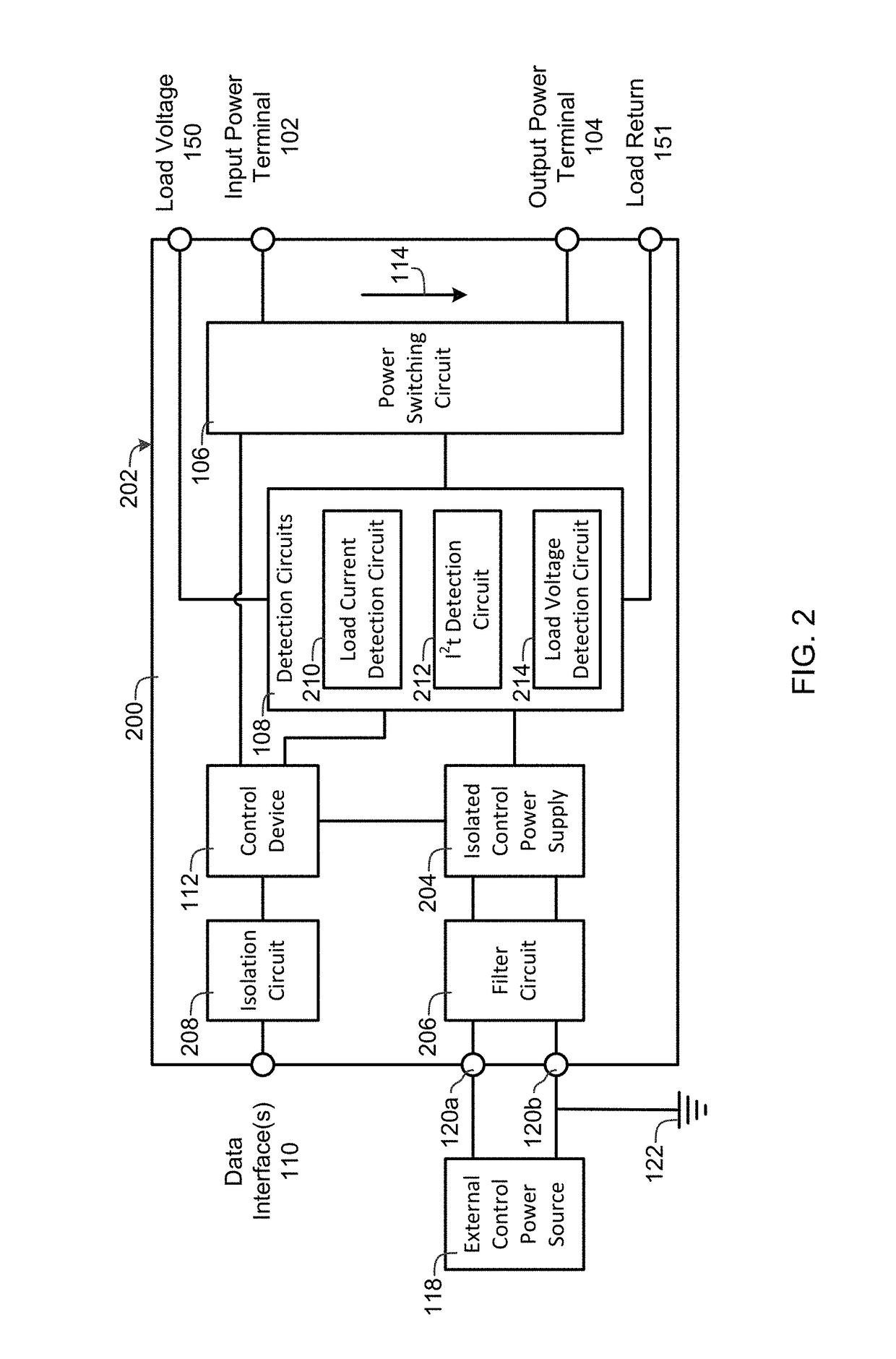
ActiveUS20150057822A1Prevents catastrophicAvoid destructive failureTransistorMechanical power/torque controlPower controllerPower switching
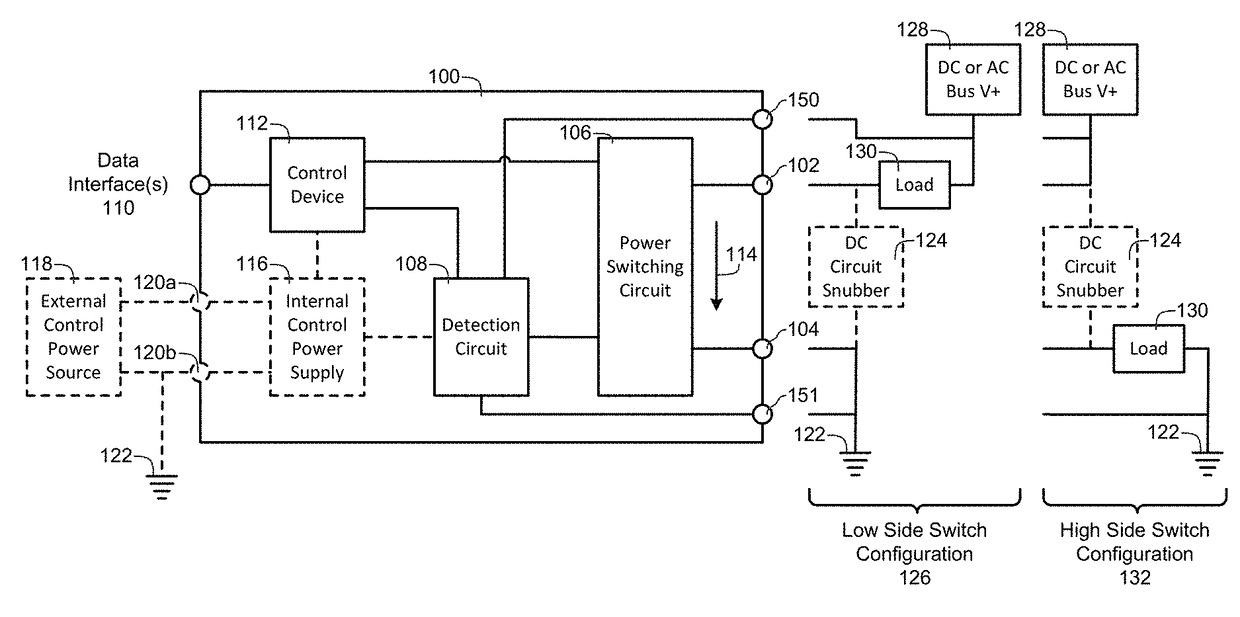
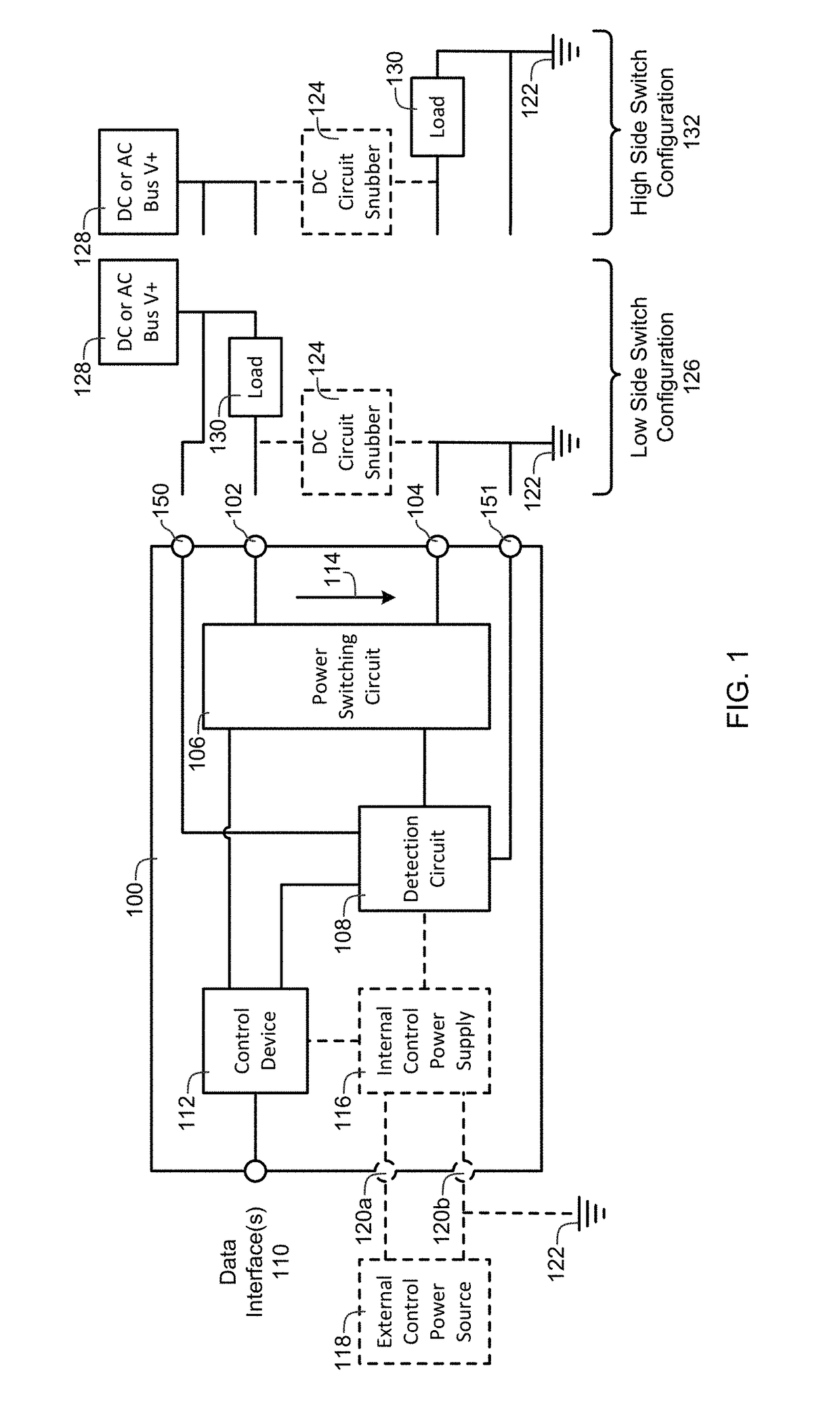
A power controller includes an input power terminal, an output power terminal, a power switching circuit connected between the input power terminal and the output power terminal, a detection circuit connected to the power switching circuit, one or more data interfaces, and a control device connected to the detection circuit and the one or more data interfaces. The detection circuit measures a load current and a current squared time (I2t) value between the input power terminal and the output power terminal. The control device automatically turns the power switching circuit “OFF” whenever the load current exceeds a first value or the current squared time value exceeds a second value or an “OFF” signal is received from the one or more data interfaces, and automatically turns the power switching circuit “ON” whenever an “ON” signal is received from the one or more data interfaces.
Owner:MICROPAC IND
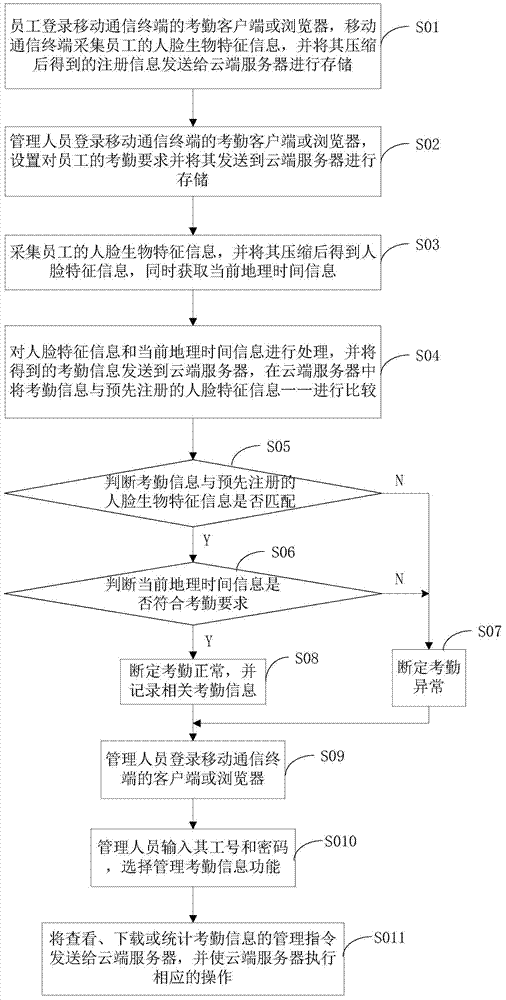
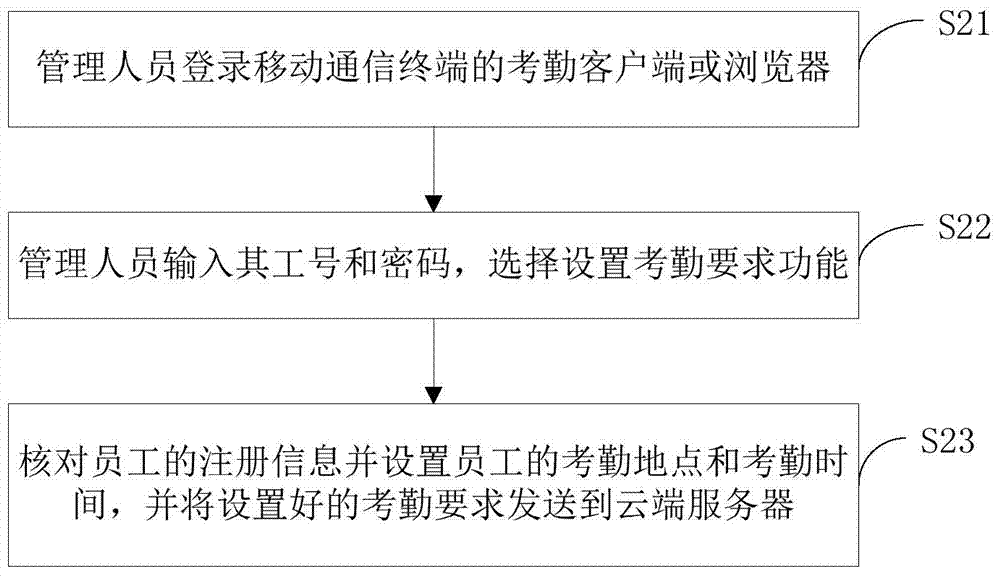
Attendance checking method based on mobile communication terminal and device
InactiveCN103903310AReduce data volumeFast recognitionRegistering/indicating time of eventsTime informationComputer terminal
The invention provides an attendance checking method based on a mobile communication terminal. The attendance checking method comprises the following steps: registering staff; setting attendance checking requirements by administrative staff and sending the attendance checking requirements to a cloud server; compressing collected human face biological characteristic information to human face characteristic information; meanwhile, obtaining current geographical time information; processing the human face characteristic information and the current geographical time information; sending obtained attendance checking information to the cloud server; comparing the attendance checking information with registering information; judging whether the attendance checking information is matched with the registering information or not; if so, carrying out the next step; otherwise, judging the attendance check to be abnormal; judging whether the current geographical time information meets the attendance checking requirements or not; if so, judging the attendance check to be normal and recording the attendance checking information; otherwise, judging the attendance check to be abnormal. The invention further relates to a device for realizing the method. The attendance checking method based on the mobile communication terminal and the device, provided by the invention, are implemented and have the beneficial effects that the transmission is rapid, the recognition efficiency is high, the recognition is rapid and the flaws existing in attendance checking management can be eliminated.
Owner:SHENZHEN WAVE MULTIMEDIA
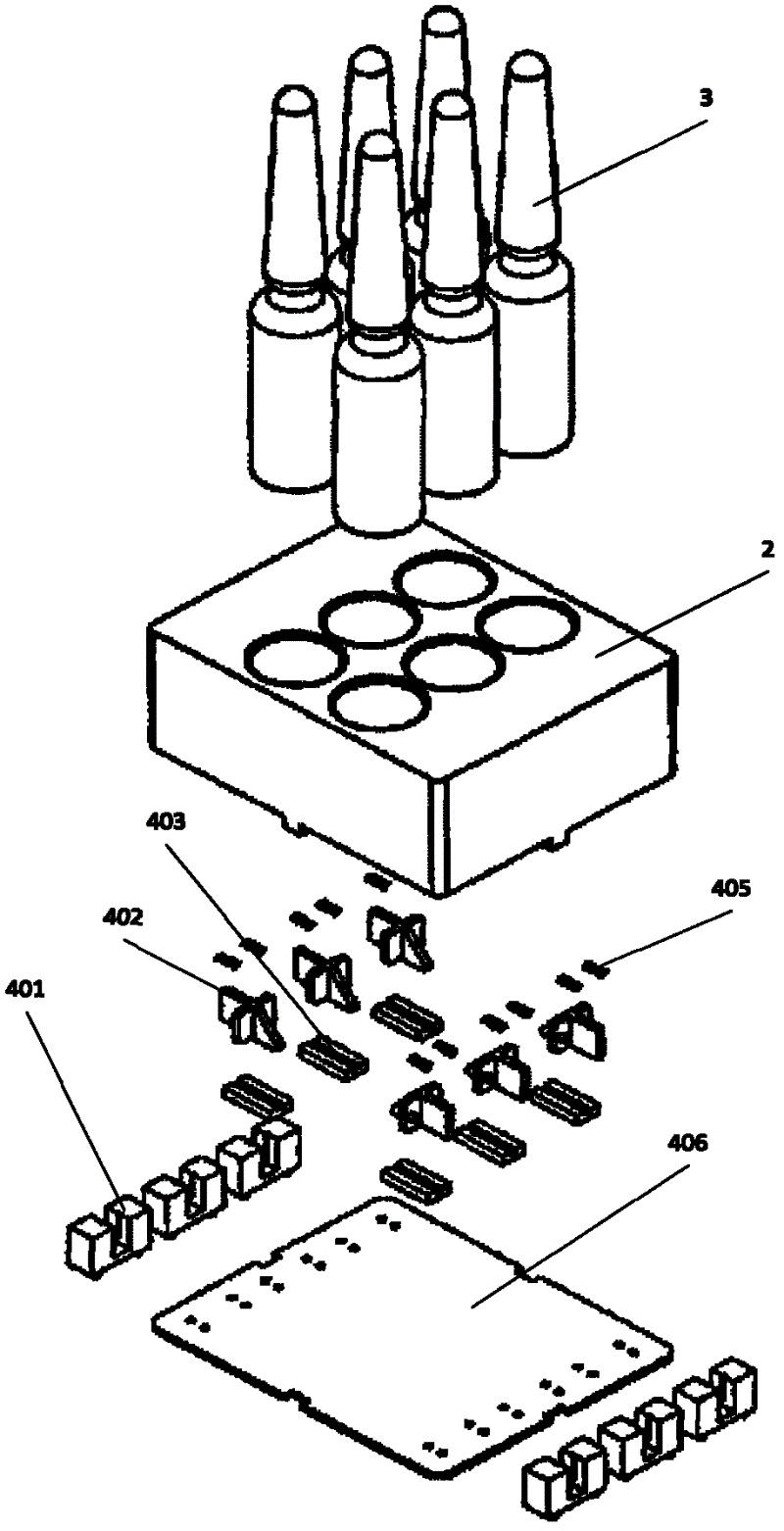
Counting medicine box
ActiveCN102774590ASimple structureFunction increaseCounting mechanisms/objectsStorage devicesElastic componentMedicine
The invention relates to a medicine box, and especially relates to a medicine box with an automatic counting function, which belongs to the field of medical and health devices. The medicine box disclosed by the invention comprises a main body and a medicine shelf, wherein the medicine shelf comprises a counting mechanism with a counting function. The counting mechanism realizes the recording of medicine numbers through an optical control principle, and the counting mechanism disclosed by the invention comprises a photoelectric switch, an elastic sheet, a base and an elastic component; the elastic sheet is a rectangular plate, and one end (away from the photoelectric switch) of the elastic sheet is provided with a bulge; the bulge end of the elastic sheet is arranged in the base, the other end of the elastic sheet extends out of the base through an open slot, and the elastic sheet can slide upwards and downwards along the open slot; the elastic component is arranged in the base, and the elastic sheet is pressed on the elastic component; and the counting function of the medicine box is realized through that the elastic sheet moves upwards and downwards in the middle of the photoelectric switch. The medicine box disclosed by the invention has the advantages of simple structure, and accuracy and reliability in counting, greatly improves the security and convenience of medicine storage, eliminates vulnerabilities and management risks existing in manual operations, and saves the labor cost and the management cost, therefore, the medicine box is suitable to be used in large and medium-sized hospitals, pharmacies and the like.
Owner:北京华兴长泰物联网技术研究院有限责任公司
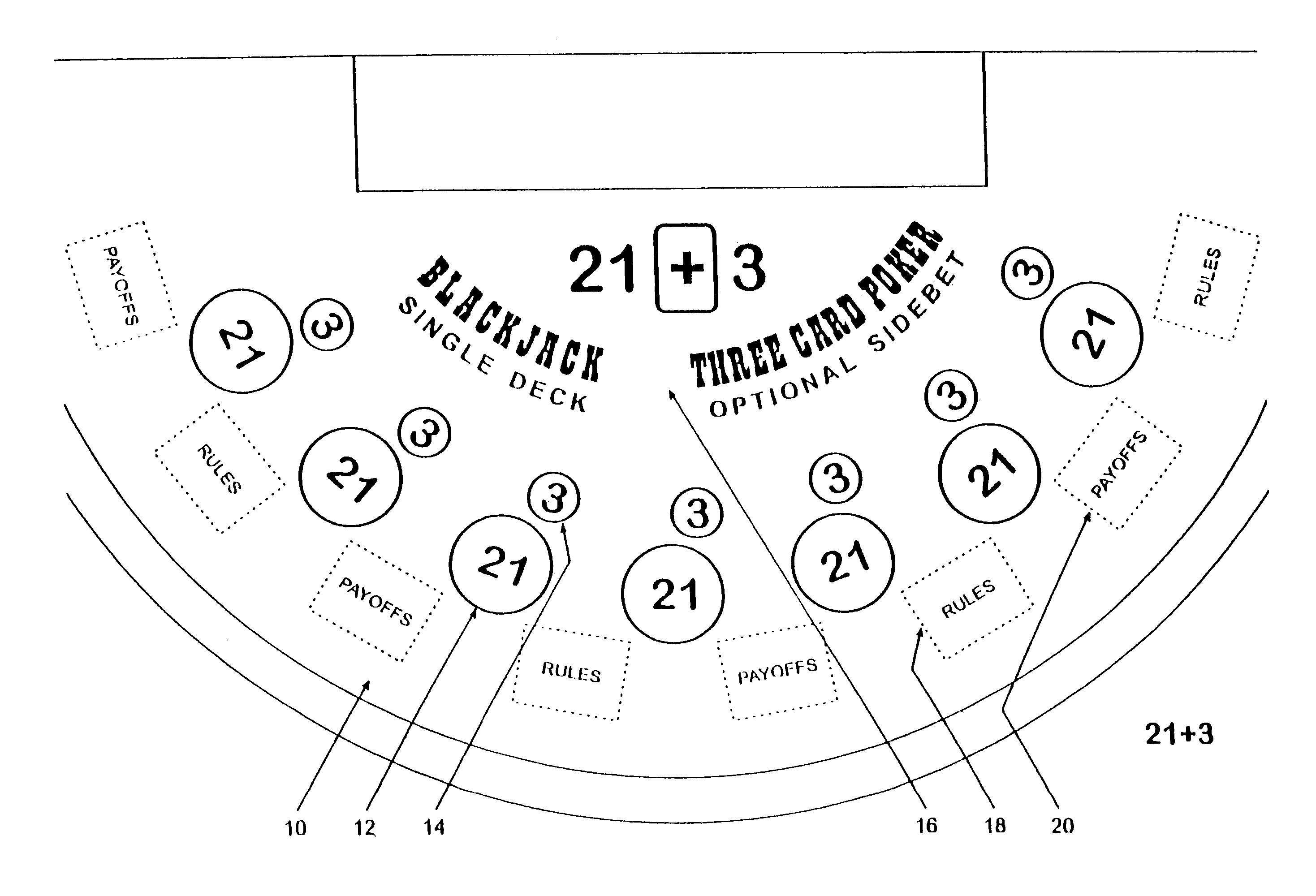
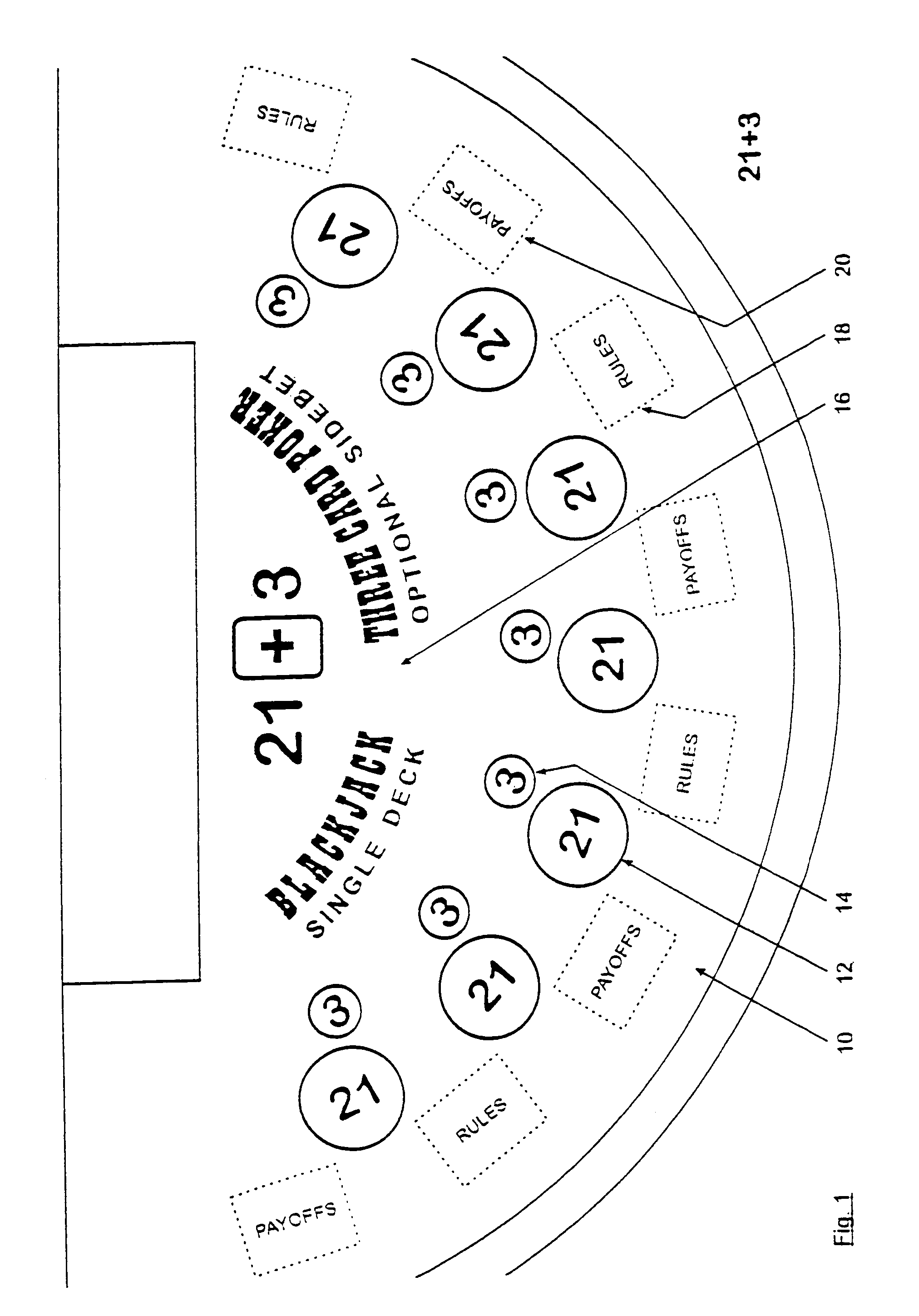
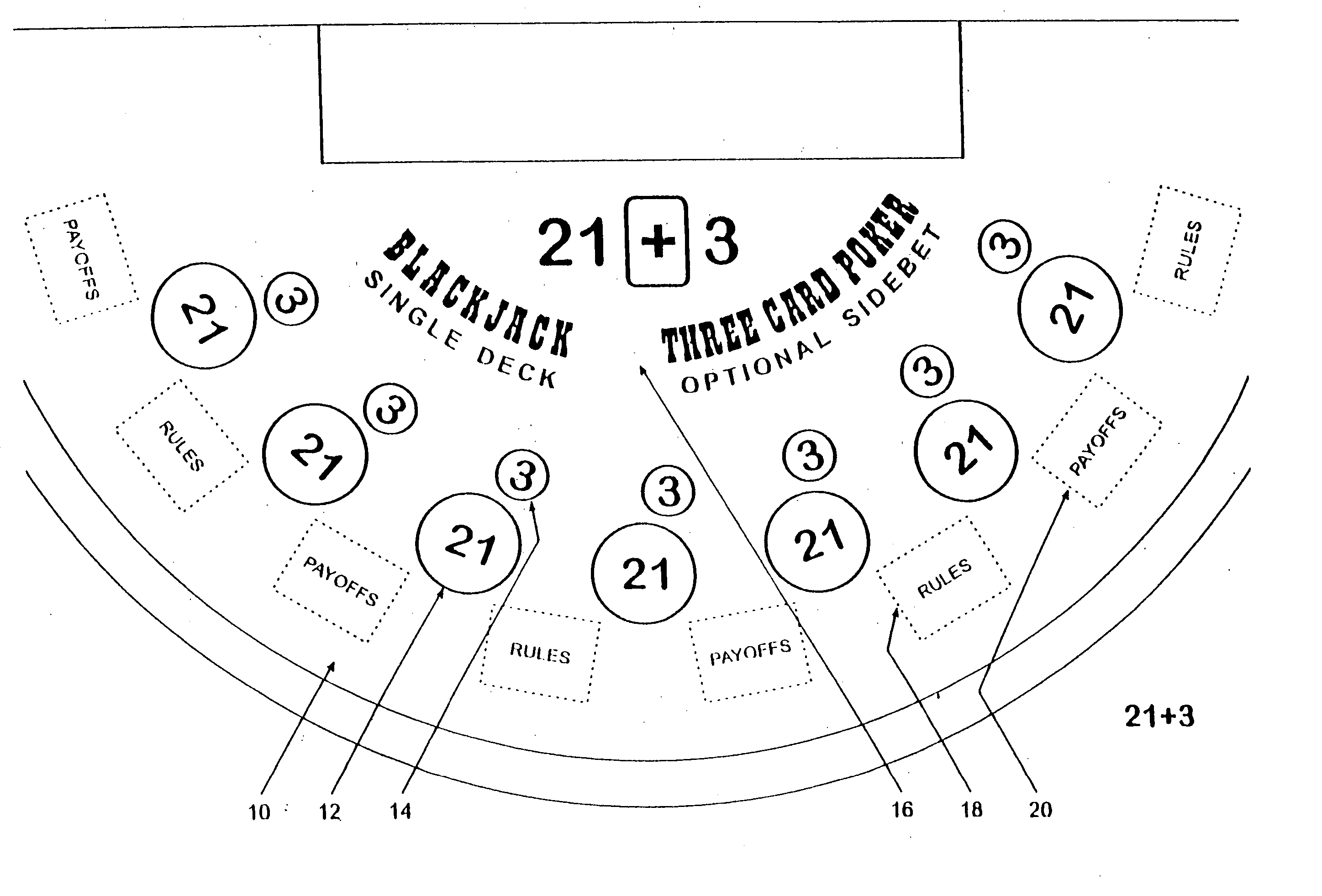
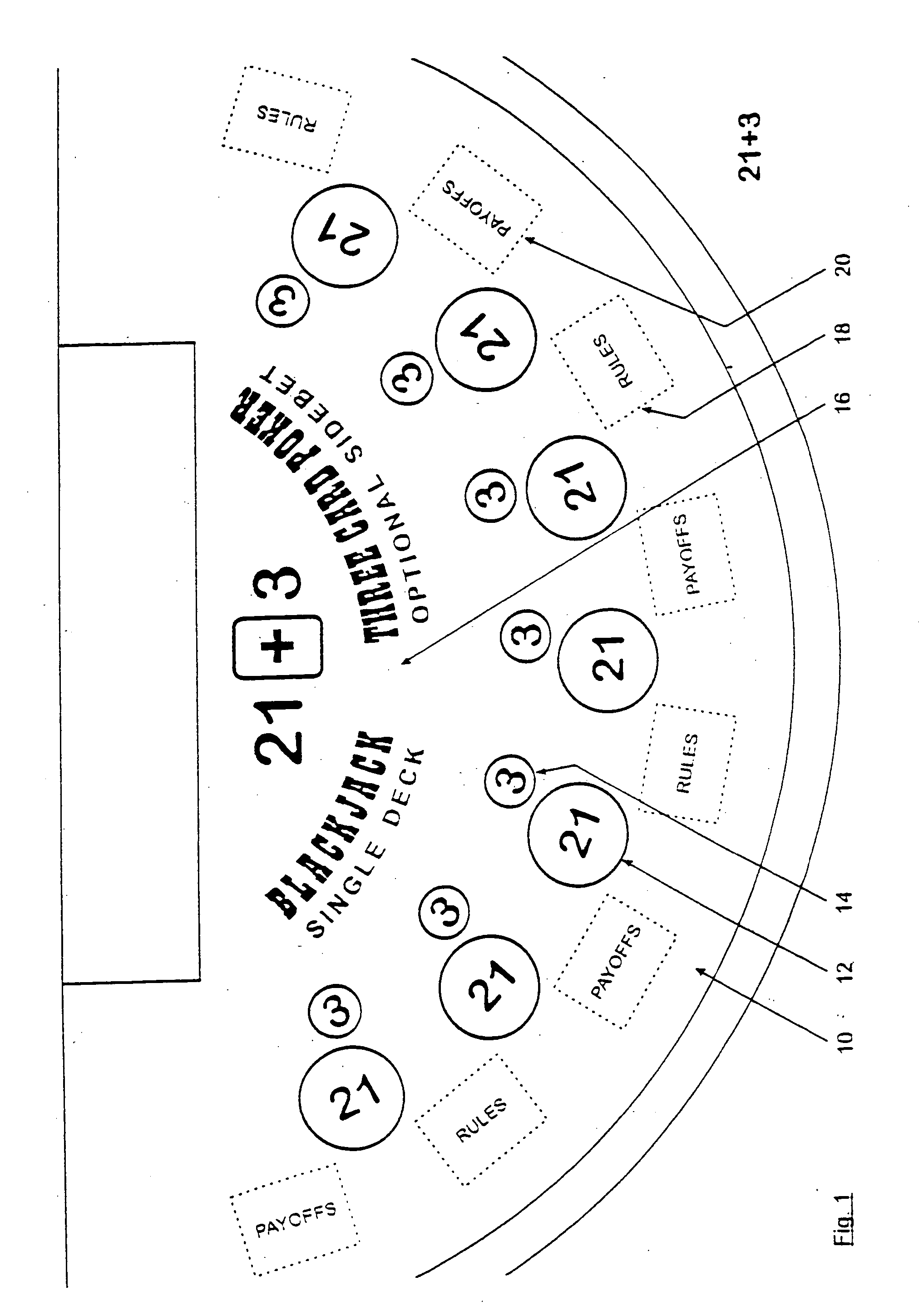
Method for playing Blackjack with a three card poker wager ("21+3")
Card games that combine the play of Blackjack (“21”) with a 3-card Poker wager or side bet (“21+3”). Each player places a basic Blackjack wager and an optional 3-card Poker wager before the cards are dealt. Each player is then dealt a card with the dealer receiving a face-up card. Each player is dealt a second card. At this point, the outcome of each 3-card Poker hand is determined, where a 3-card Poker hand consists of the 2-card hand dealt to that player and the dealer's face-up card. After settling the Poker wagers, the game of Blackjack continues in a typical fashion. The invention advantageously retains all the features and advantages of Blackjack as well as provides the dynamics of 3-card Poker, without interfering with the card sequence, for enhanced player anticipation and enjoyment.
Owner:GALAXY GAMING
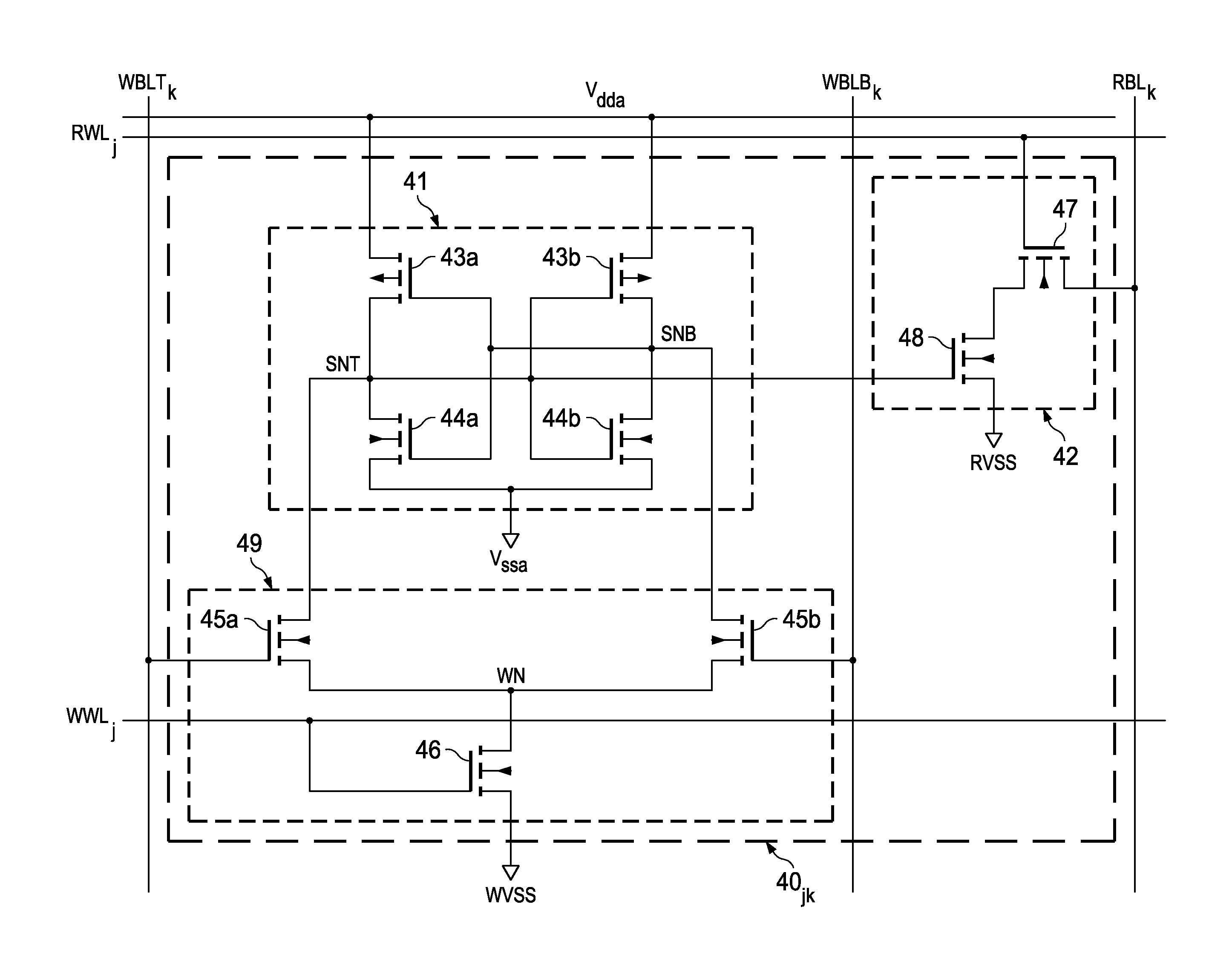
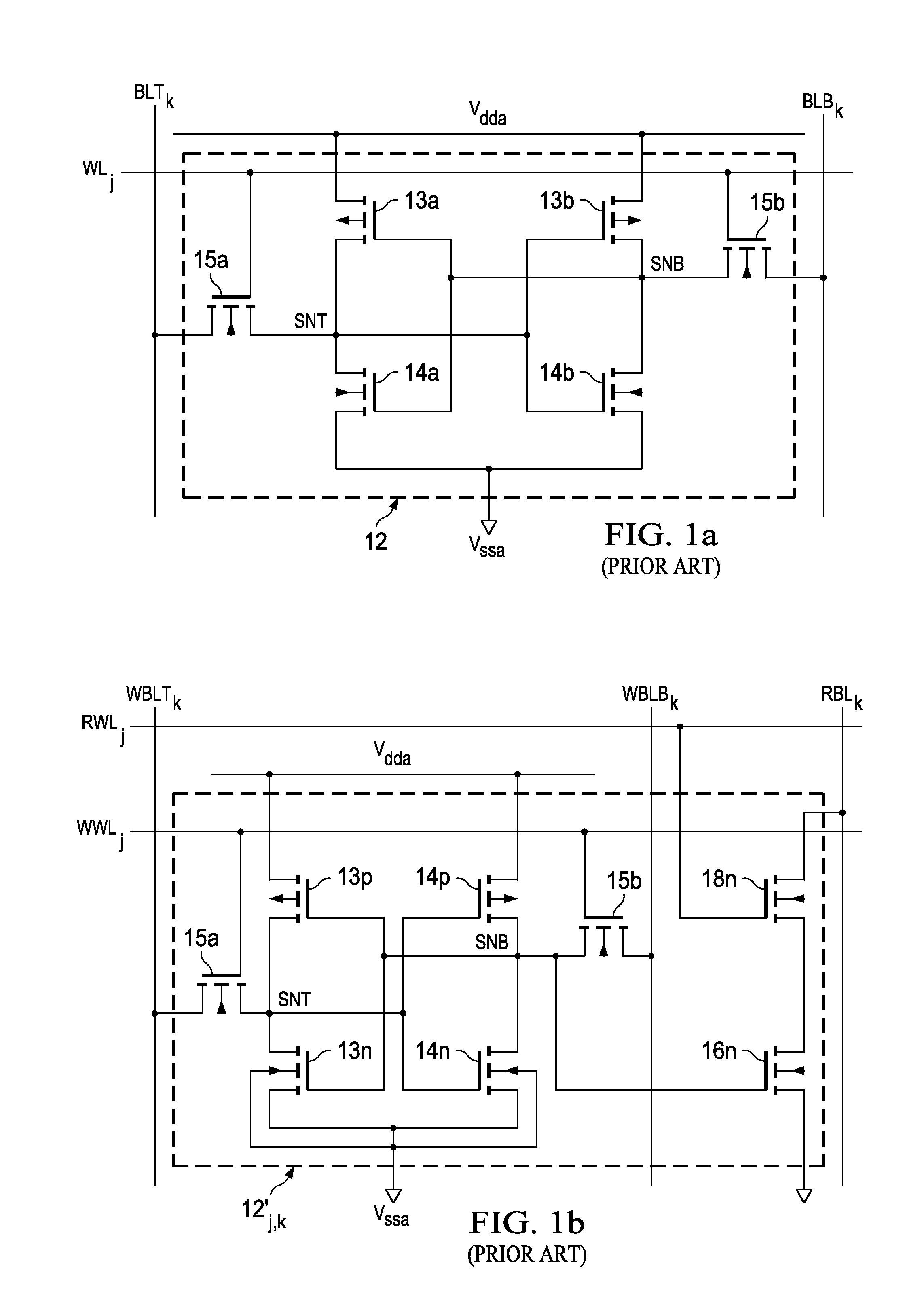
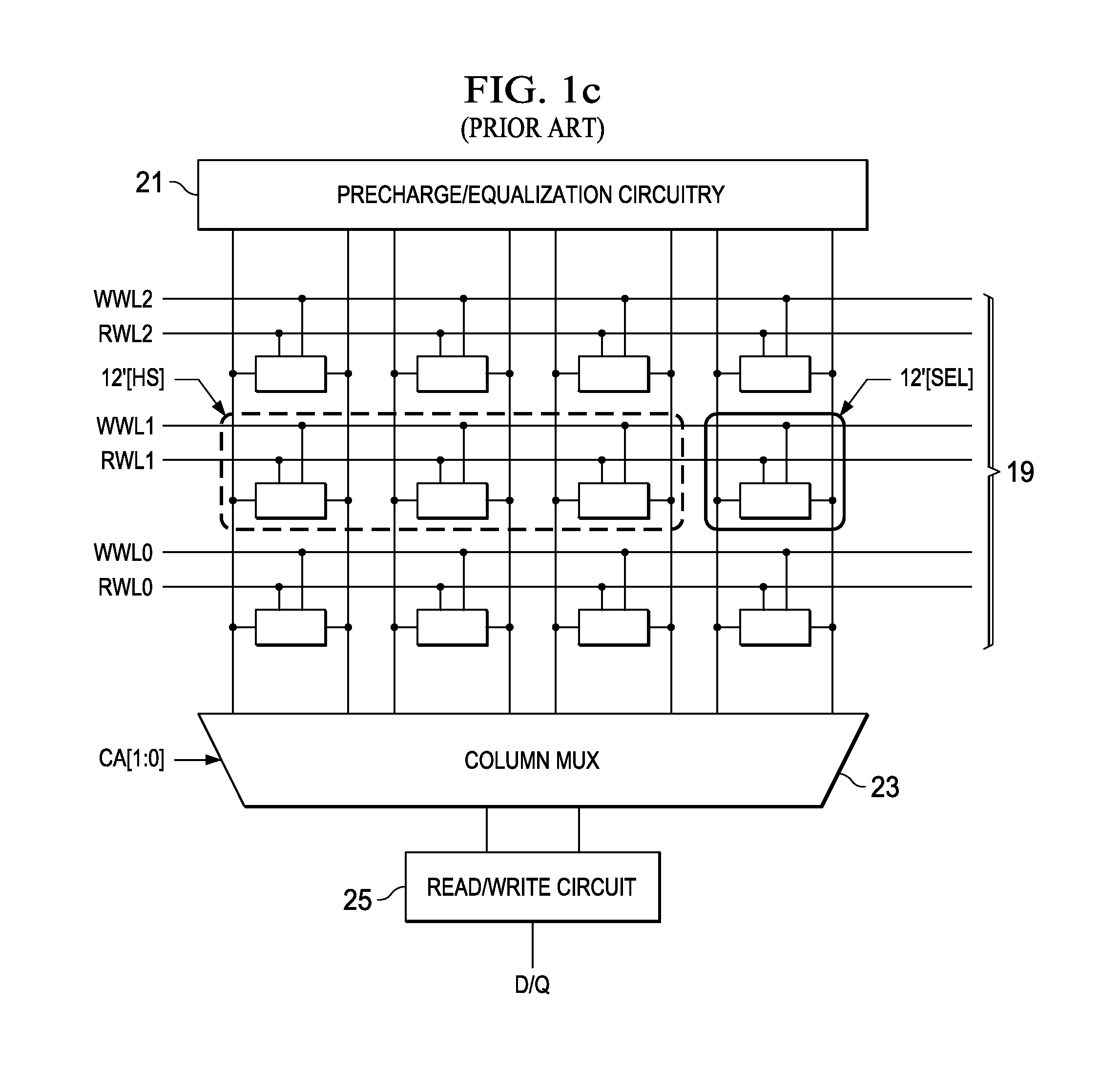
Disturb-Free Static Random Access Memory Cell
ActiveUS20120014173A1Improve stabilityEliminate VulnerabilitiesDigital storageData bufferStorage cell
A solid-state memory in which each memory cell includes a cross-point addressable write element. Each memory cell includes a storage element, such as a pair of cross-coupled inverters, and a read buffer for coupling one of the storage nodes to a read bit line for the column containing the cell. The write element of each memory cell includes one or a pair of write select transistors controlled by a write word line for the row containing the cell, and write pass transistors connected to corresponding storage nodes and connected in series with a write select transistor. The write pass transistors are gated by a write bit line for the column containing the cell. In operation, a write reference is coupled to one of the storage nodes of a memory cell in the selected column and the selected row, depending on the data state carried by the complementary write bit lines for that column.
Owner:TEXAS INSTR INC
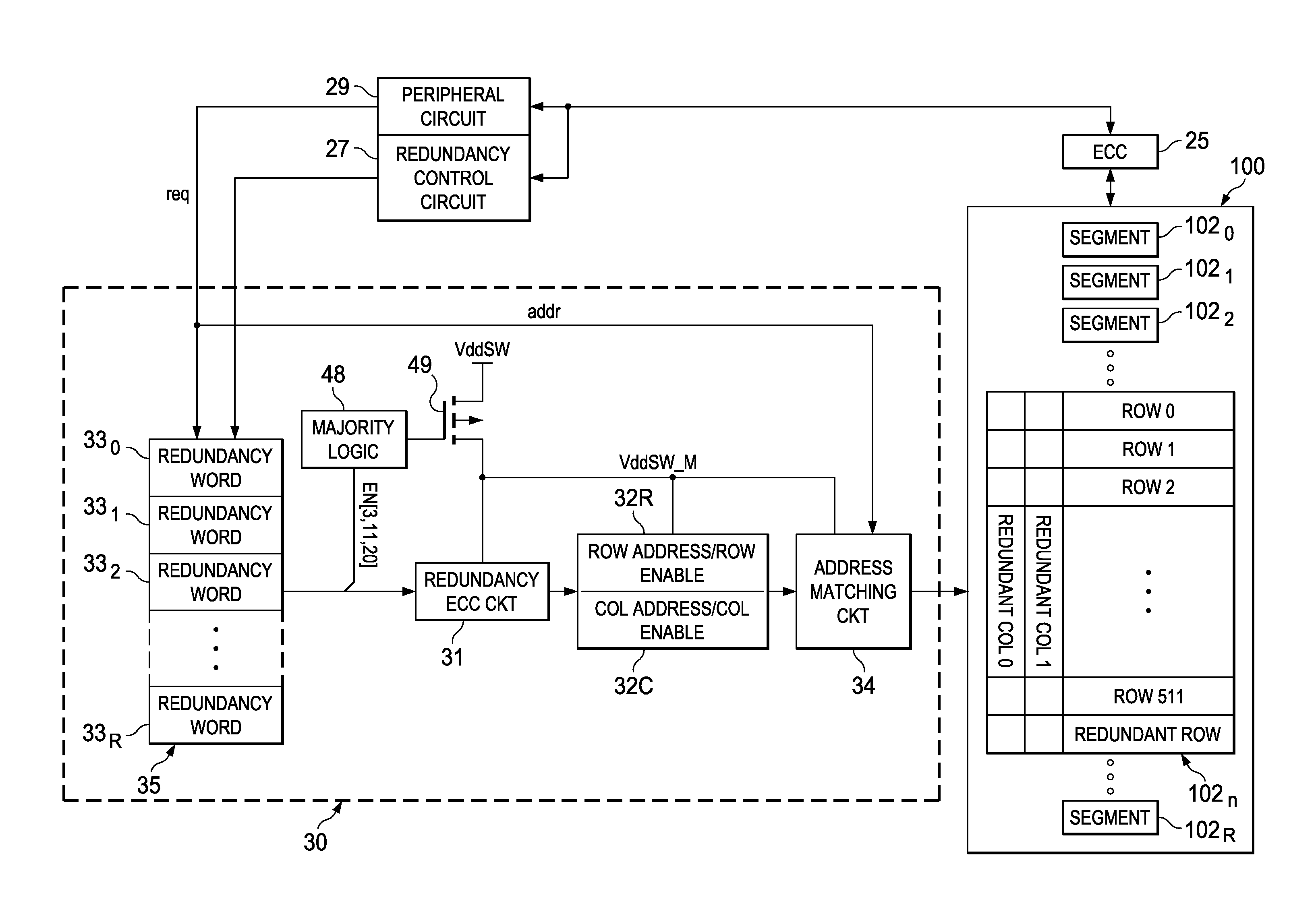
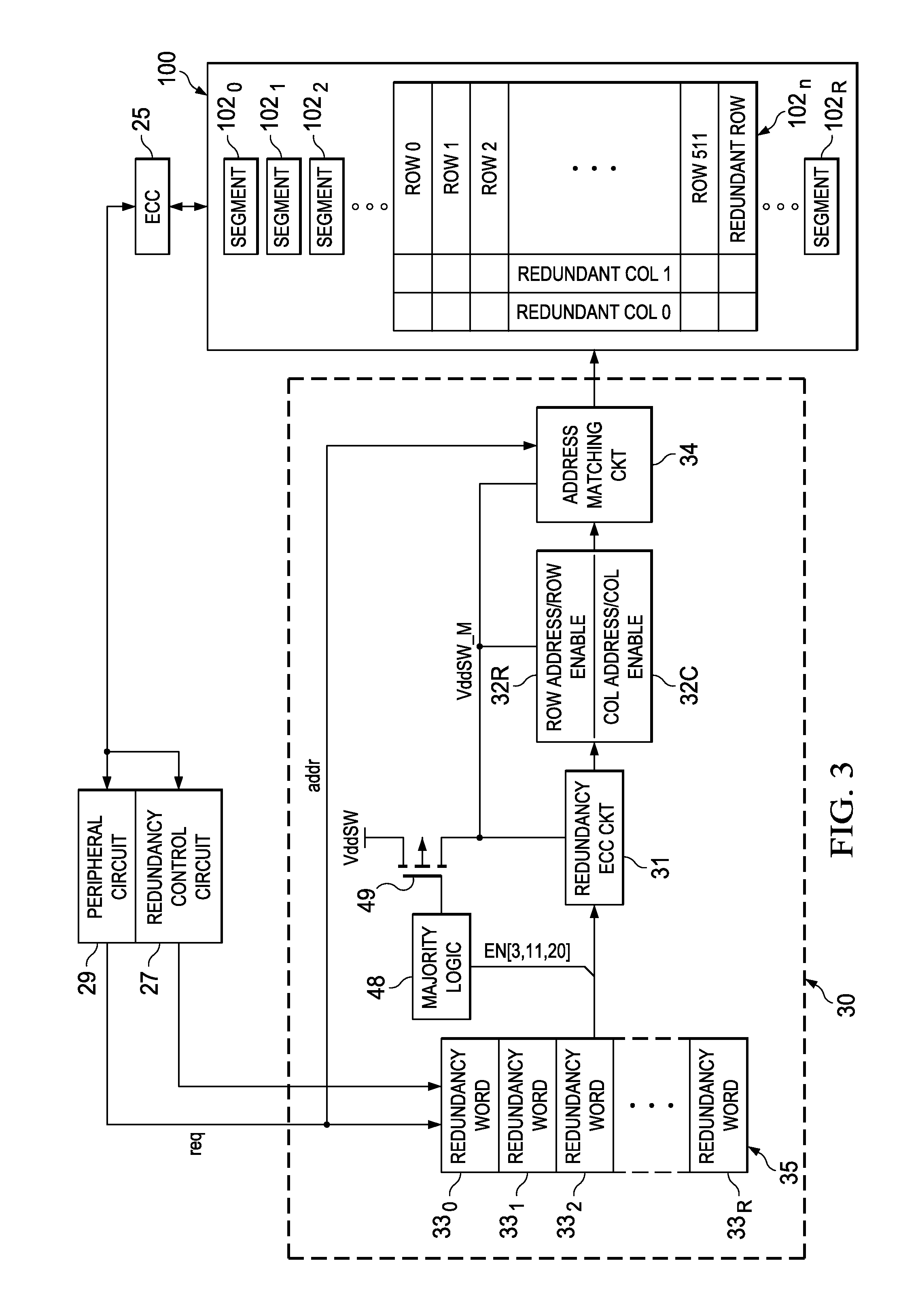
Low-Power Redundancy for Non-Volatile Memory
ActiveUS20110231736A1Reduce the required powerReduced Power RequirementsError correction/detection using block codesDigital storageData bitsFerroelectric RAM
A static RAM redundancy memory for use in combination with a non-volatile memory array, such as ferroelectric RAM (FRAM), in which the power consumption of the SRAM redundancy memory is reduced. Each word of the redundancy memory includes data bit cells for storing addresses of memory cells in the FRAM array to be replaced by redundant elements, and also enable bits indicating whether redundancy is enabled for those addresses. A logical combination of the enable bits in a given word determines whether the data bit cells in that word are powered-up. As a result, the power consumption of the redundancy memory is reduced to the extent that redundancy is not enabled for segments of the FRAM array.
Owner:TEXAS INSTR INC
Method for playing Blackjack with a three card poker wager ("21+3")
InactiveUS20050121854A1Improve expectationsIncrease revenue generationBoard gamesCard gamesMultimedia
Owner:GALAXY GAMING
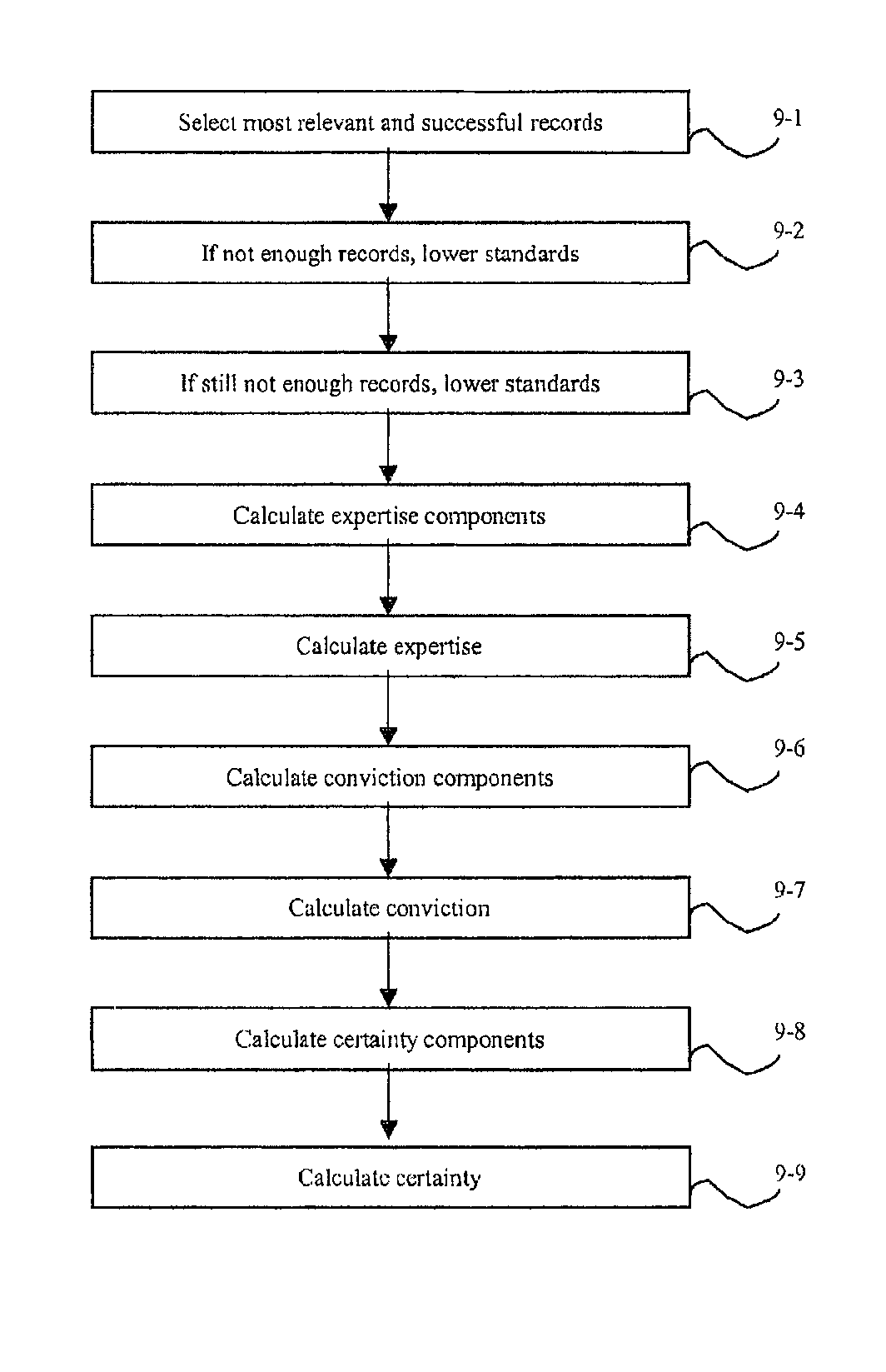
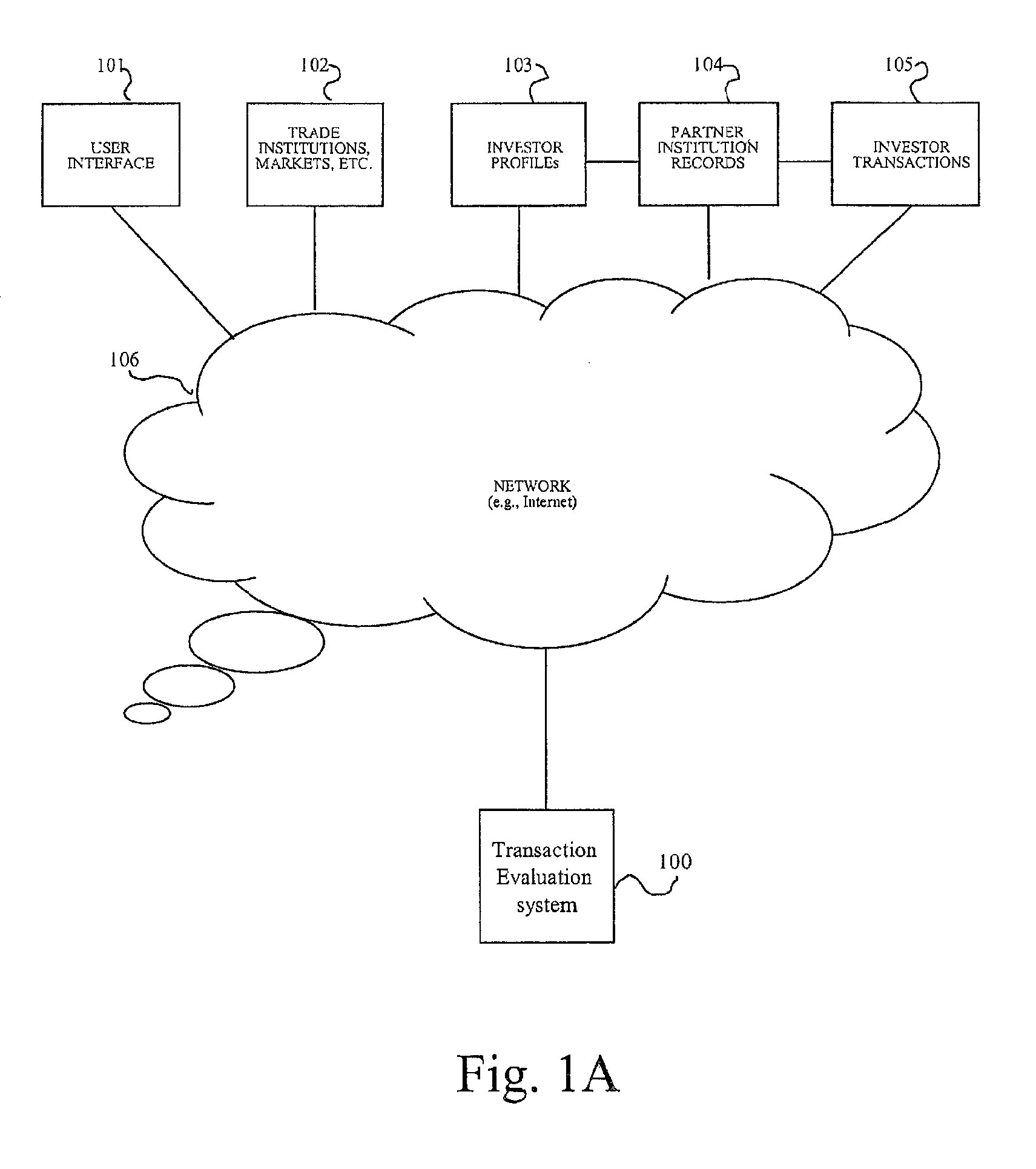
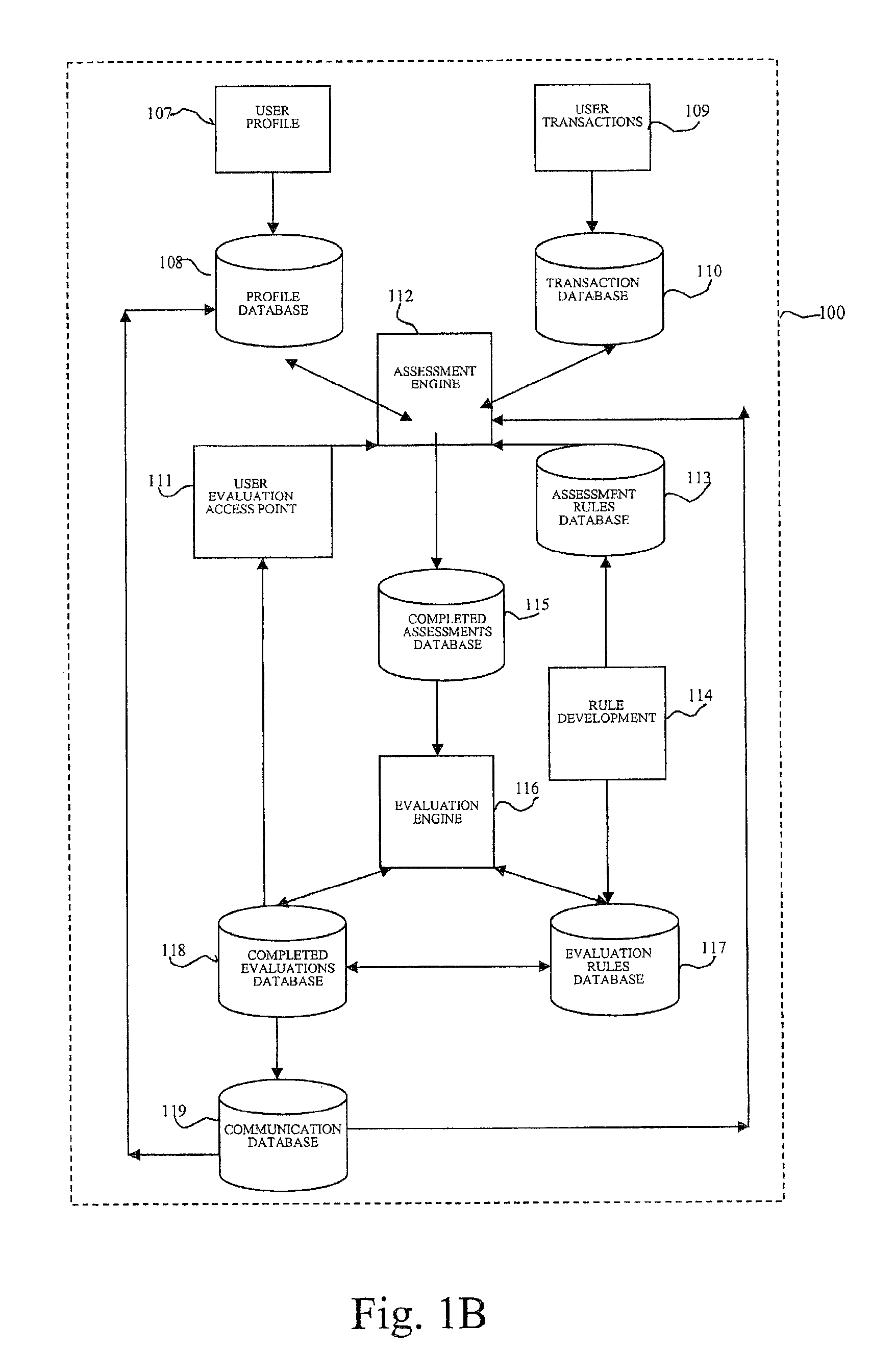
System and method for generating transaction based recommendations
InactiveUS8494946B2Eliminate loopholesAvoid excessive volatilityFinanceVideo gamesTransaction dataAssessment data
A system for generating recommendation data includes an assessment unit and an evaluation unit. The assessment unit is configured to receive transaction data for a plurality of transactions and to assess each transaction and generate assessment data based thereon. The evaluation unit is coupled with the assessment unit and configured to receive an evaluation request including a proposed transaction, and generate recommendation data including a certainty indicator which indicates a level of certainty that the proposed transaction will be successful according to predetermined criteria.
Owner:LORTSCHER JR FR DUANE
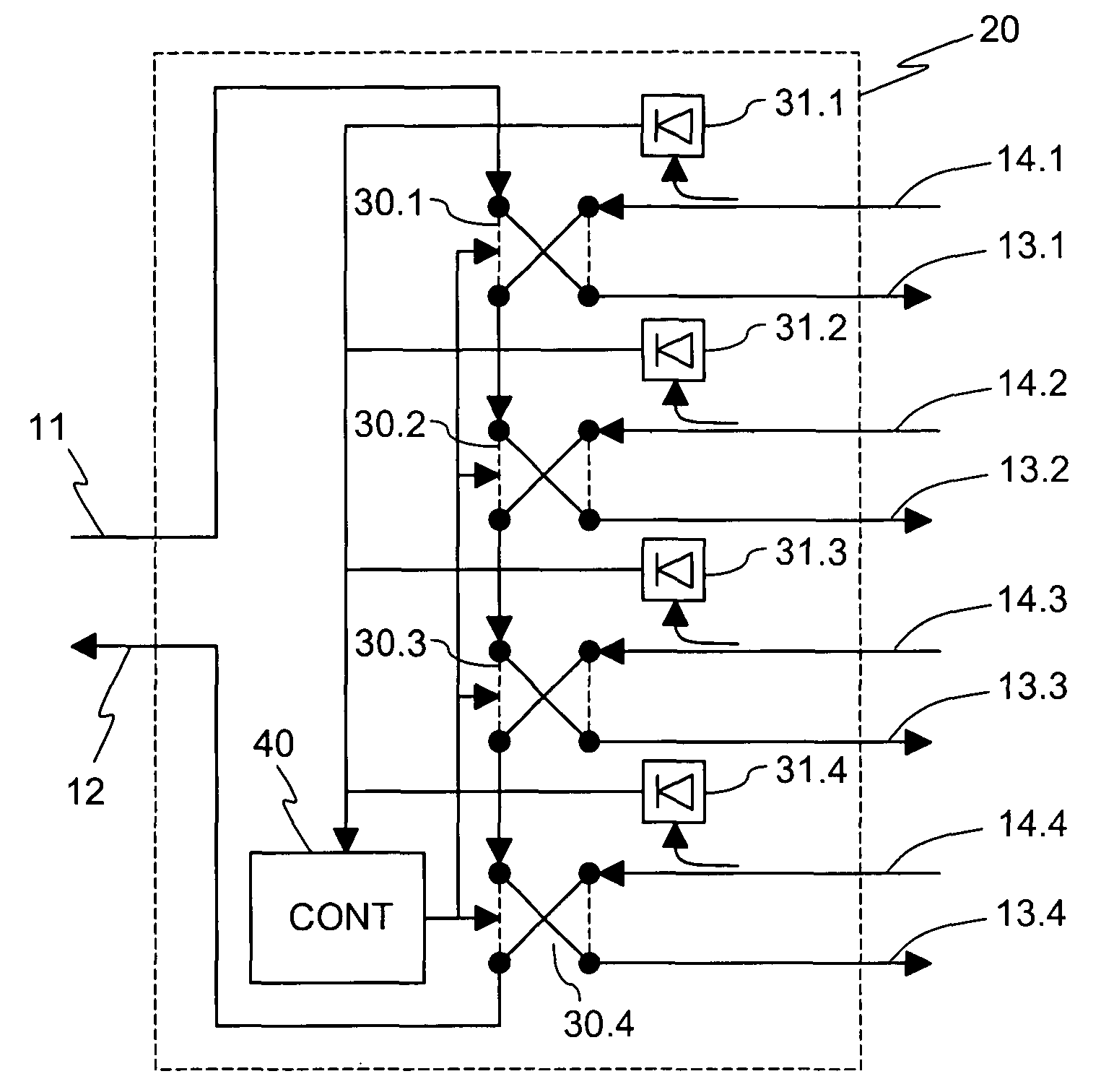
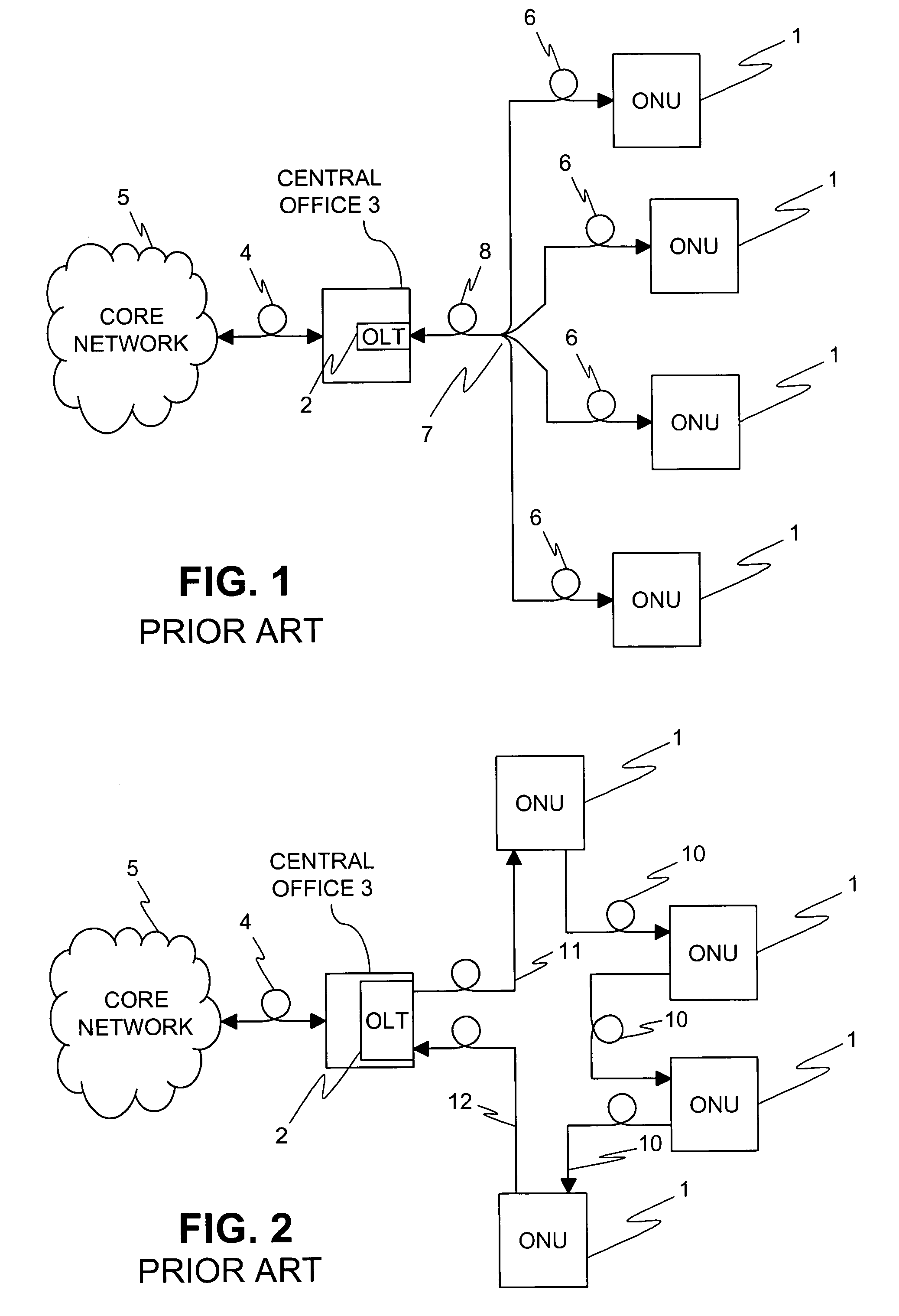
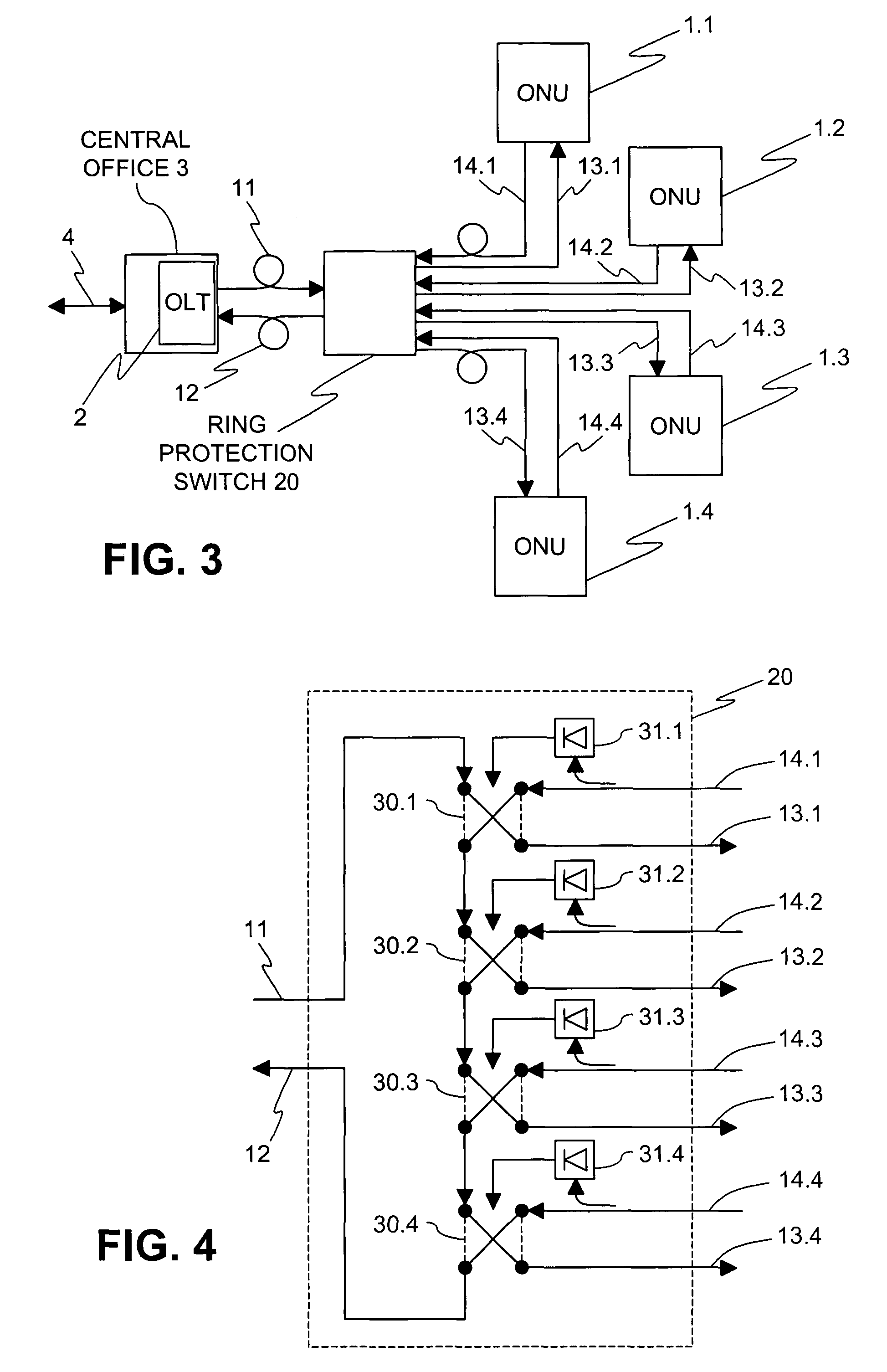
System and method for a protected optical access ring network
InactiveUS7409154B2Eliminate loopholesSimple and robust constructionMultiplex system selection arrangementsLaser detailsAccess networkRing network
An optical access network employs a ring topology in which connections between the network units and between the network units and the optical line terminal are via a protection switch. The protection switch monitors connections from the optical network units to detect a loss of signal and, on detecting a loss of signal from an optical network unit, switches the respective optical network unit out of the ring, thus maintaining continuity of the ring topology.
Owner:LUCENT TECH INC
System, method, and service for detecting improper manipulation of an application
InactiveUS8056138B2More robustnessEliminate loopholesDigital data processing detailsUser identity/authority verificationObfuscationNew Executable
Owner:INT BUSINESS MASCH CORP
Method for control of synchronous electrical motors
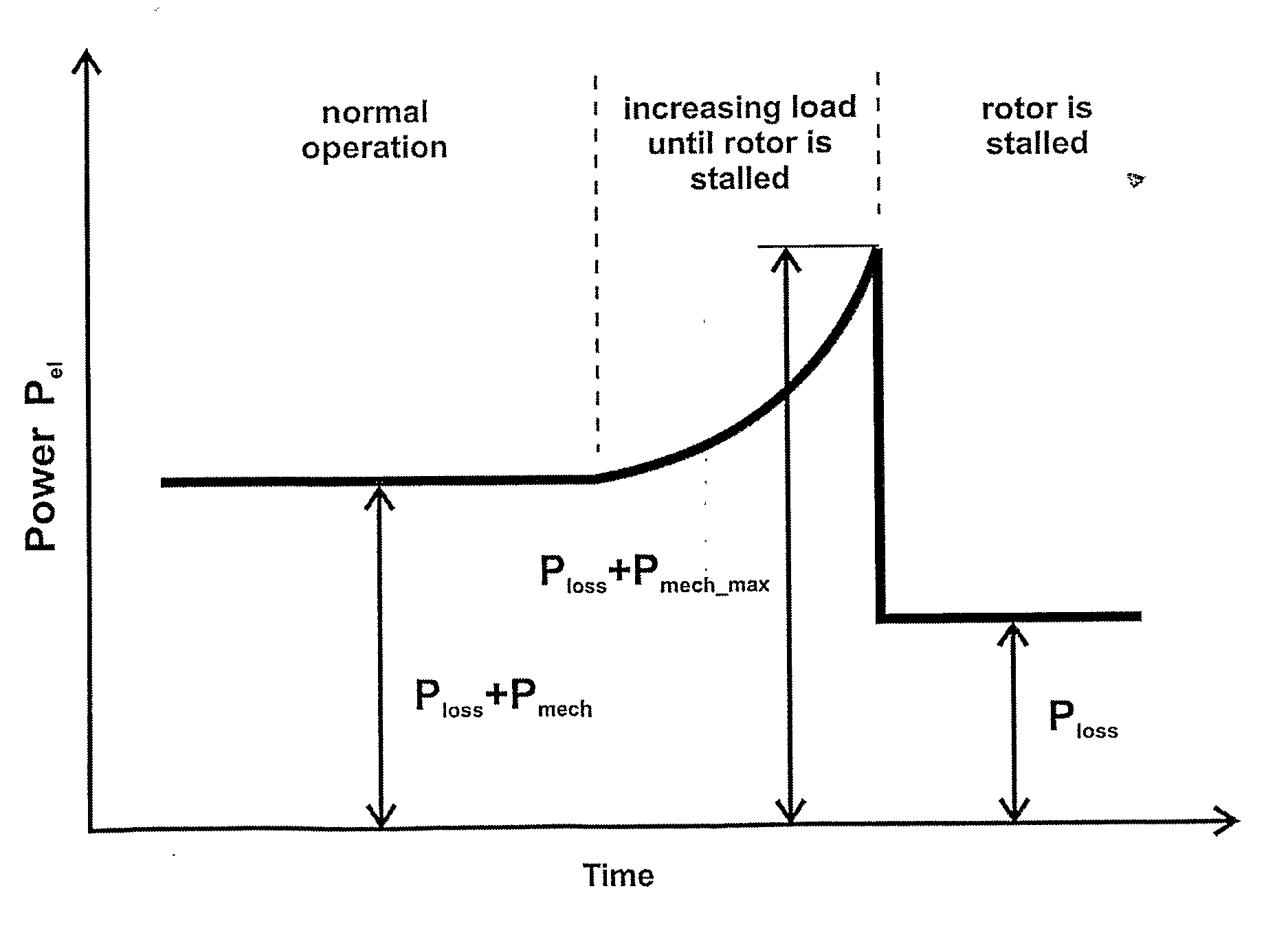
ActiveUS20120098473A1Avoid loopholesAutomatically calibratingMotor/generator/converter stoppersCommutation monitoringSynchronous motorOperating speed
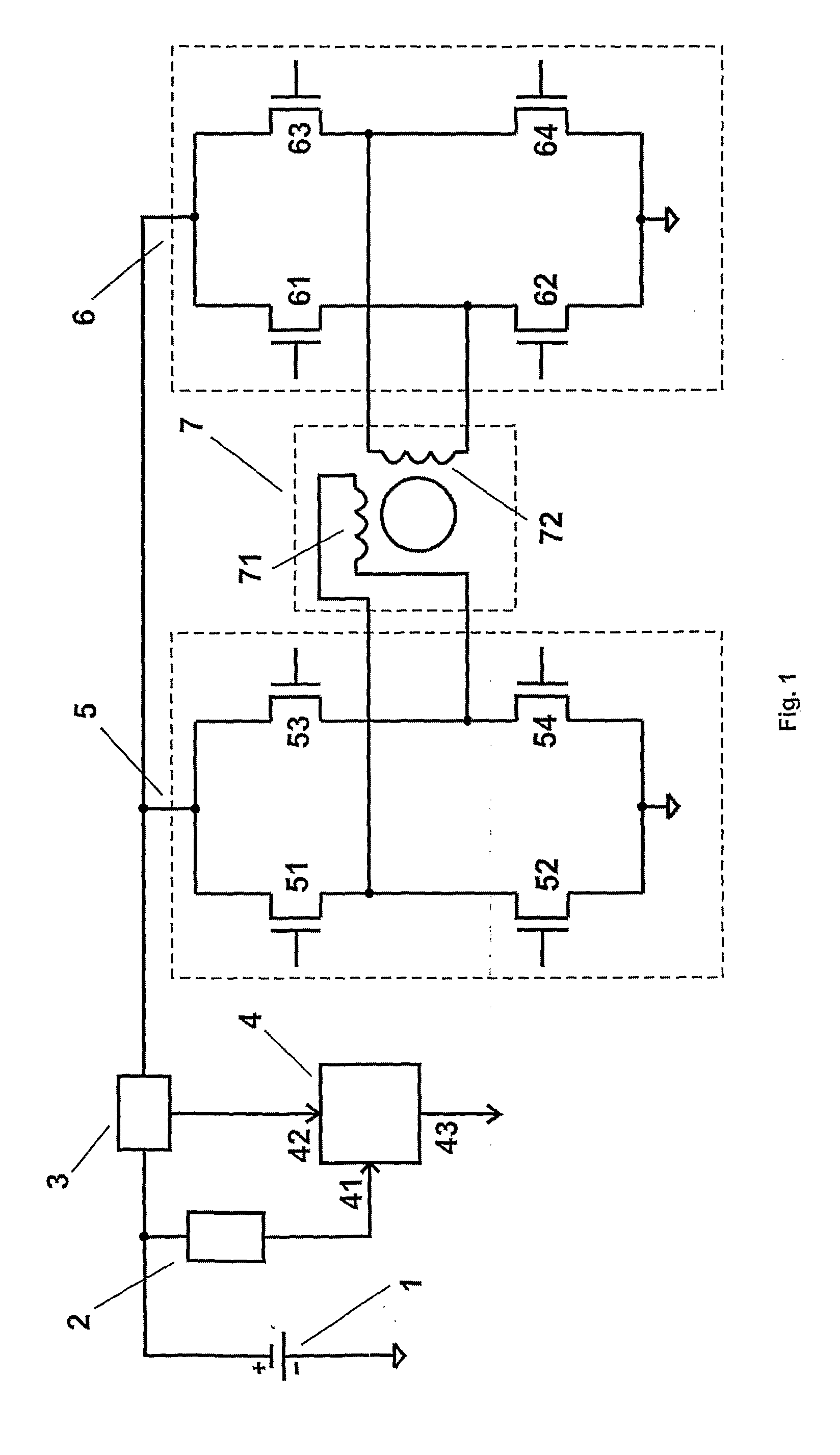
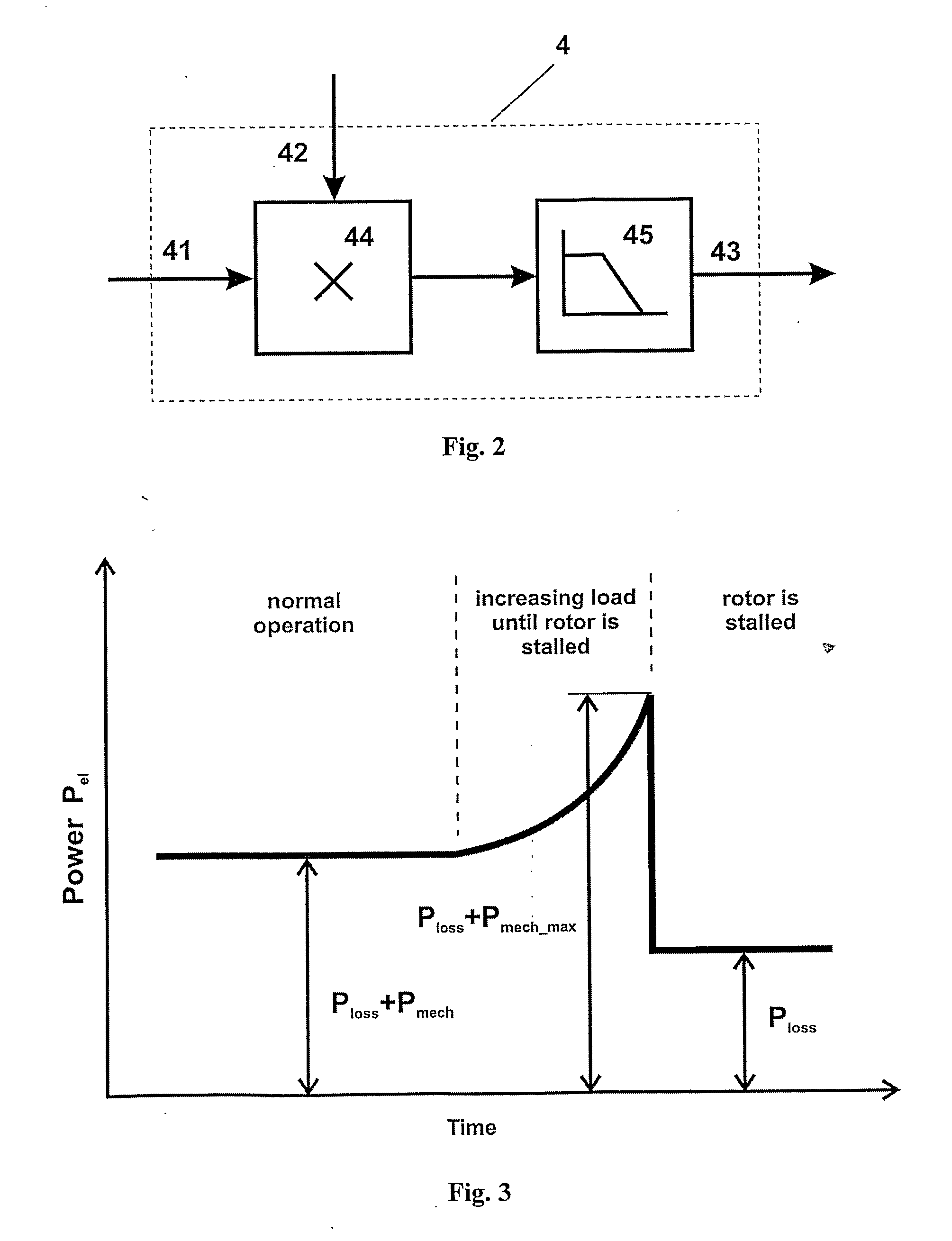
Method for control of synchronous electrical motors with application for stepper and Brush-Less Direct Current motors for which there is an explicit relation between the active electrical power supplied to the motor and the mechanical power that the motor delivers to the load. The active electrical power Pel consumed by the motor is measured and according to FIG. 3 the mechanical power Pmech and the maximum available mechanical power Pmech max are determined. The ratio between Pmech and Pmech max is calculated and is compared to the set value of the same ratio. If it is greater than the set one either the operating currents are increased either the operating speed is decreased or both operations are executed. But if it is smaller—either the operating currents are decreased either the operating speed is increased or both operations are executed.
Owner:NACHEV RADEK GEORGIEV +1
Medicine box
ActiveCN102616432AAvoid delayRecord in timeDrawer-and-shell containersExternal fittingsElastic componentMedicine
The invention relates to a medicine box, in particular to a medicine box with an automatic counting function, which belongs to the field of medical and health instruments and comprises a main body and a medicine frame, wherein the medicine frame comprises a counting mechanism with the counting function. A technical mechanism achieves medicine quantity recording through an optical control principle, a medicine mechanism comprises a switch, a sliding block, a base and an elastic component, one end of the sliding block is a rectangular plate, the other end of the sliding block is a slanted plate, the rectangular plate end of the sliding block is close to an optoelectronic switch, the slanted plate end of the sliding block is far away from the optoelectronic switch, and two sides of the sliding block extend respectively to form flank baffles which are intersected with the rectangular plate in a cross-shaped mode. The elastic component is arranged between the optoelectronic switch and the flank baffles of the sliding block, and the counting function is achieved by means of the fact that the sliding block slides in the middle of the optoelectronic switch when a sliding block slanted plane feels medicine weight. The medicine box has the advantages of being simple in structure and accurate and reliable in counting, greatly improves safety and convenience of medicine storage, avoids loopholes and management risks caused by manual operation, saves labor cost and management cost, and is applied to medium and large hospitals, drugstores and the like.
Owner:北京华兴长泰物联网技术研究院有限责任公司
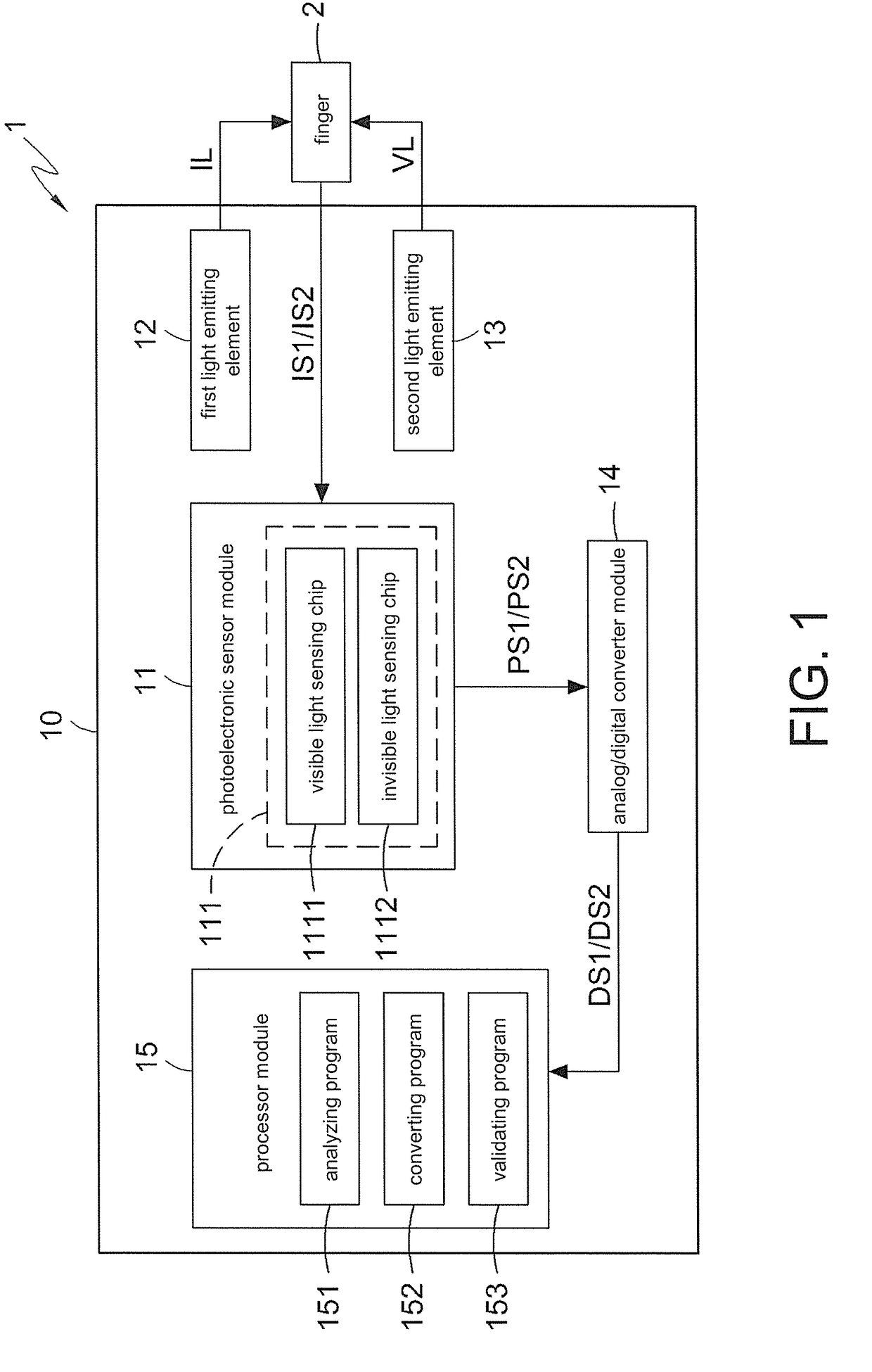
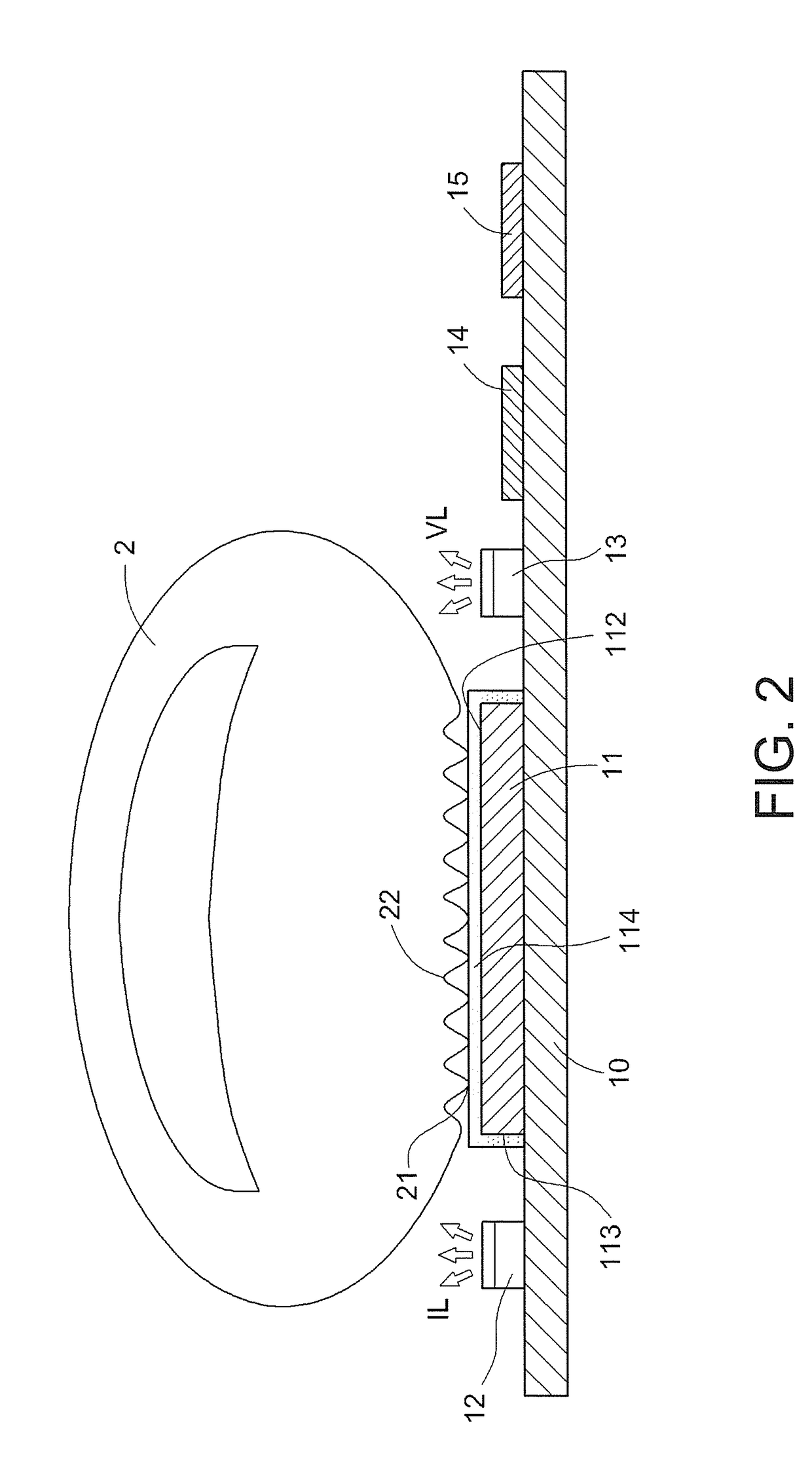
Fingerprint identification method and device thereof
ActiveUS20170323139A1Easy procedureEasy passPrint image acquisitionMatching and classificationLight beamIdentification device
A fingerprint identification method is provided. The method includes steps as follows: having a finger press on a photoelectronic sensor module; respectively emitting an invisible light beam reflected to a photoelectronic sensor module after passing through the finger and a visible light beam reflected to the photoelectronic sensor module via a surface of the finger; generating, by the photoelectronic sensor module, photocurrent signals based on the visible light beam and the invisible light beam; respectively generating, by an analog / digital converter module, a first digital signal and a second digital signal based on the photocurrent signals; and outputting, by a processor module, the first digital signal as a gray-scale fingerprint image and a second digital signal as a colored fingerprint image. The invention also provides a fingerprint identification device performing the fingerprint identification method.
Owner:GINGY TECH
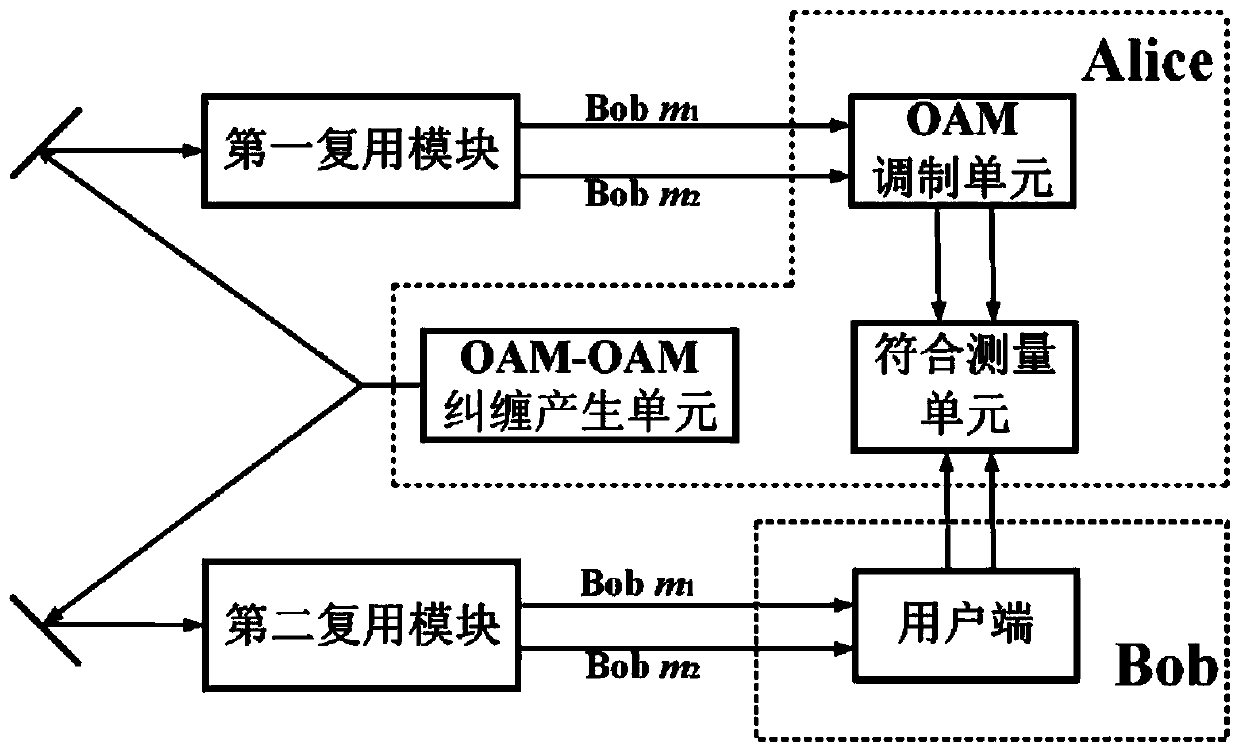
OAM entanglement modulation key distribution network system and method with real-time tracking compensation
PendingCN111130779AImprove securityIncrease key rateKey distribution for secure communicationPhotonic quantum communicationMultiplexingPhase distortion
The invention provides an OAM entanglement modulation key distribution network system with real-time tracking compensation. The OAM entanglement modulation key distribution network system comprises anOAM-OAM entanglement generation unit, a first multiplexing module, a second multiplexing module, an OAM modulation unit, a Bob client and a coincidence measurement unit, wherein the OAM-OAM entanglement generation unit is used for generating an orbital angular momentum and an orbital angular momentum mixed entanglement quantum state; the first multiplexing module and the second multiplexing module are used for separating any OAM state; the OAM modulation unit is used for carrying out phase deflection modulation on the orbital angular momentum and loading coding information; and the coincidence measurement unit is used for performing coincidence measurement on signal light and idle light to decode the quantum bit information. According to the invention, the security of the quantum key distribution system is improved; an adaptive optical system is introduced, phase distortion caused by atmospheric turbulence is reduced, and the mode consistency during OAM light interference is guaranteed; an M-Z interferometer is used for separating any OAM, the quantum coding capacity is expanded, and an efficiently coded quantum key distribution system is obtained; and the engineering applicationrange is wide, the structure is simple, and the expandability is high.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
Devices, methods, and systems for cryptographic authentication and provenance of physical assets
ActiveUS11038694B1Eliminate loopholesKey distribution for secure communicationRandom number generatorsKey (cryptography)Internet privacy
Owner:KLEINMAN BRUCE
Systems and methods of adaptive thermal control for information handling systems
ActiveUS9785208B2Eliminate loopholesEliminate needProgramme controlPower supply for data processingEngineeringHandling system
Systems and methods of adaptive thermal control are provided for information handling system platforms that may be implemented to automate and scale fan control settings by making the fan control settings relative to a reported component thermal control parameter value from a component of an information handling system platform, such as a CPU or other heat generating component. In one example, bounds for system use of vendor or component manufacturer-reported thermal control parameter values may be set for system cooling so as to confine use of these values within information handling system platform limits characterized by a manufacturer of an information handling system platform.
Owner:DELL PROD LP
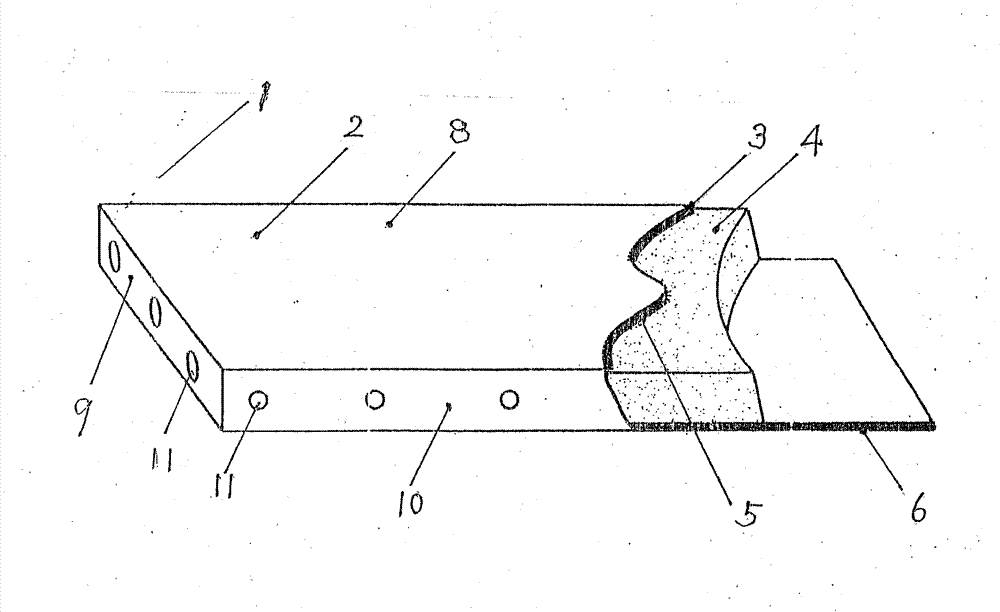
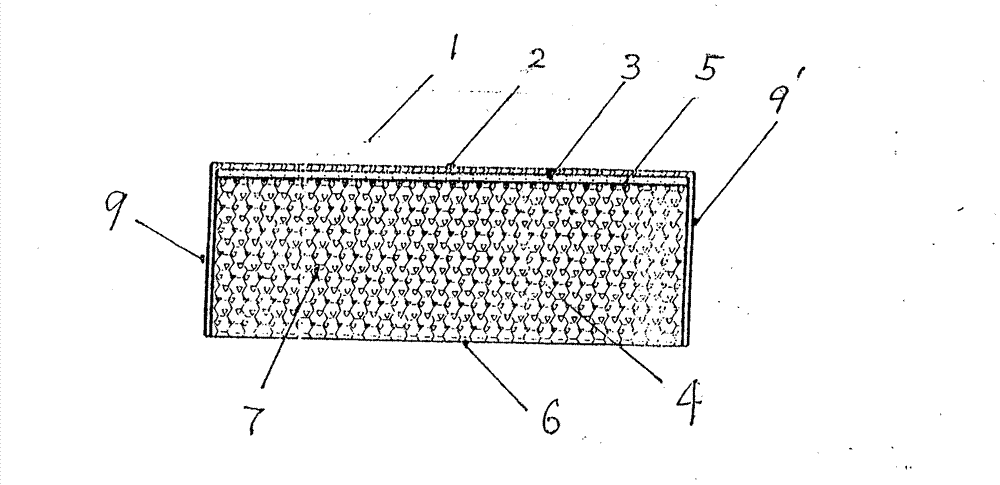
High-strength, high-toughness and rain-resistant infrared cement heat-preserving decorative board
InactiveCN103362265AImprove rain resistanceImproved rain resistanceCovering/liningsWater-setting substance layered productSodium phosphatesFlexural strength
The invention belongs to the technical field of constructing material cement decorative boards, and discloses a high-strength, high-toughness and rain-resistant infrared cement heat-preserving decorative board which is good in mechanical strength, toughness, rain resistance, fire resistance, heat insulation performance, sound absorption performance, moisture resistant characteristic and far-infrared radiation capacity. In comparison with an existing cement decorative board, the bending strength of the decorative board can be improved by 1.5-3 times, the compression strength can be improved by more than 2 times, the fire resistance is improved by 10-20 times, and the rain resistance characteristic is improved by 2-5 times. A core board layer of the decorative board is composed of Portland cement, high-alumina cement, gypsum, inorganic far-infrared powder, fine aggregate, inorganic retarding agent, organic retarding agent, water reducing agent and moisture repellent, and the upper surface and the lower surface of the decorative board are respectively provided with vinylon non-woven fabric. Coal ash, black iron ore powder, sodium phosphate capable of forming ionic bonds are preferably selected as key raw material, and the moisture repellent technology is applied to filler aggregate and the surface of a hardened body. In order to improve affinity, the width-length ratio of the non-woven fabric is 0.5-0.62, the diameter of the fiber is 15-45 microns, and the surface of the decorative board is treated in an activating mode.
Owner:丁召志
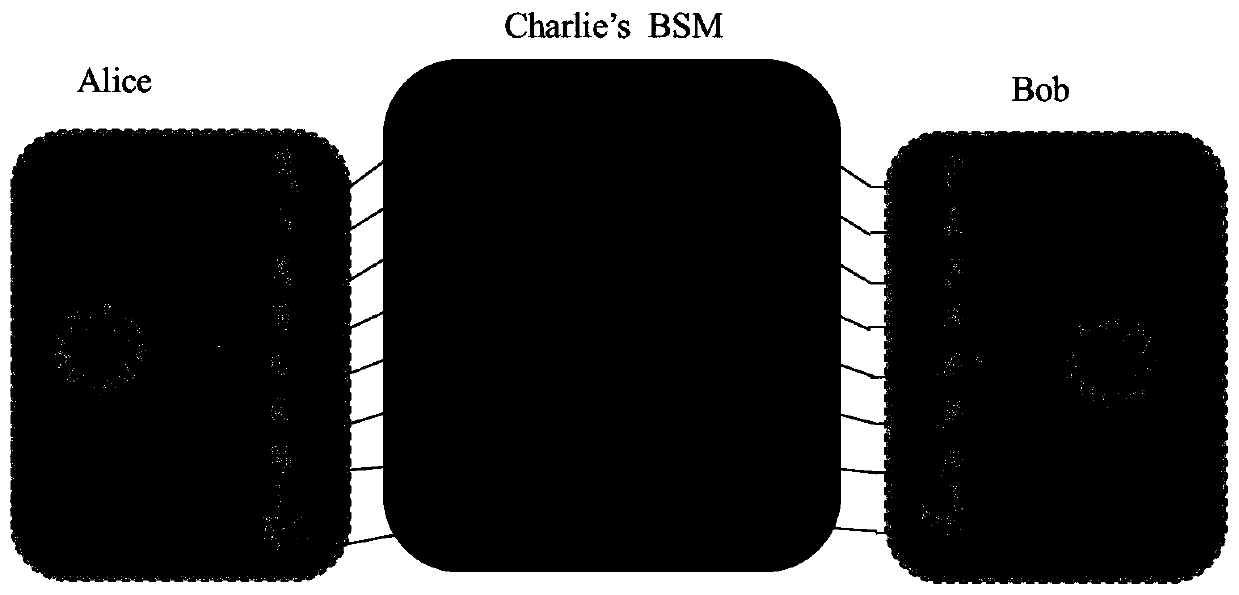
Quantum secure direct communication method irrelevant to measurement equipment in high-dimensional subspace
ActiveCN110401494AIncrease channel capacityEliminate loopholesKey distribution for secure communicationPhotonic quantum communicationChannel capacityThird party
The invention provides a quantum secure direct communication method irrelevant to measurement equipment in a high-dimensional subspace. A sender Alice and a receiver Bob perform Bell state measurementthrough an untrusted third-party Charlie, and then according to a measurement result, the Alice executes a space unitary operation to encode a message for transmission. According to the method, whenBell state measurement is carried out, Alice randomly prepares N EPR pairs under a Z base or an X base, a particle is taken out from each EPR pair to form a sequence PA, Bob also prepares a sequence PB, and the state of the sequence PB is one of quantum states on the Z base or the X base under an N-dimensional space; particles in PA and PB are simultaneously generated to Charlie, and Bell state measurement is carried out. According to the invention, the loopholes of all measuring ends are thoroughly eliminated, and the channel capacity and the information transmission security are improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Registration method of third party payment platform, device, and system
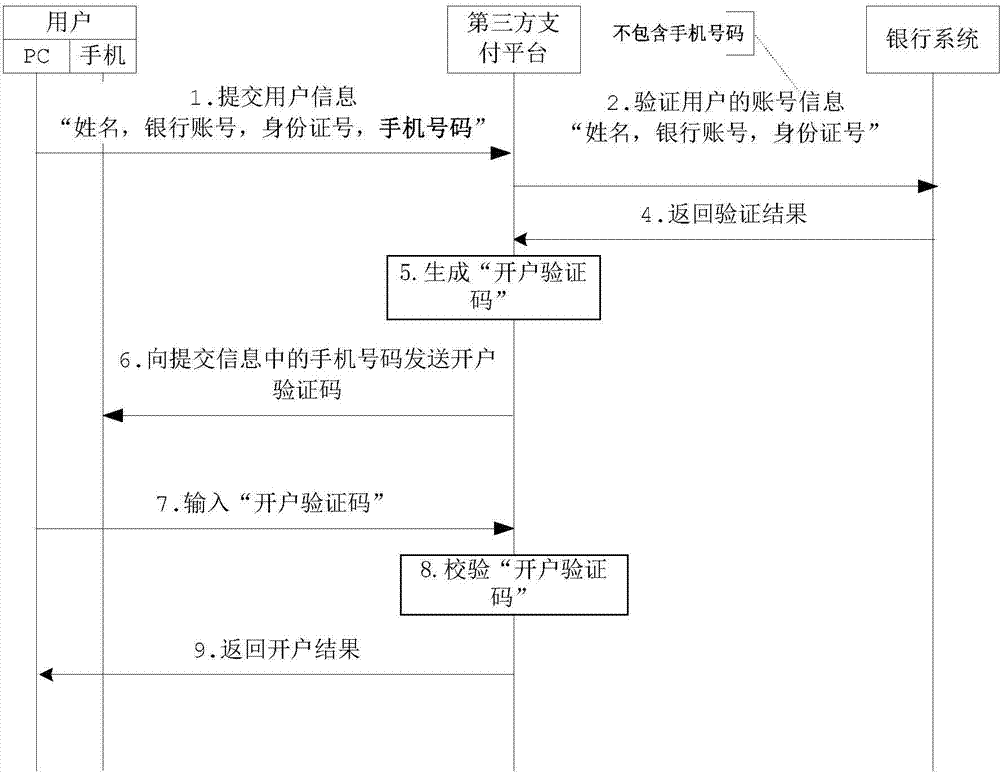
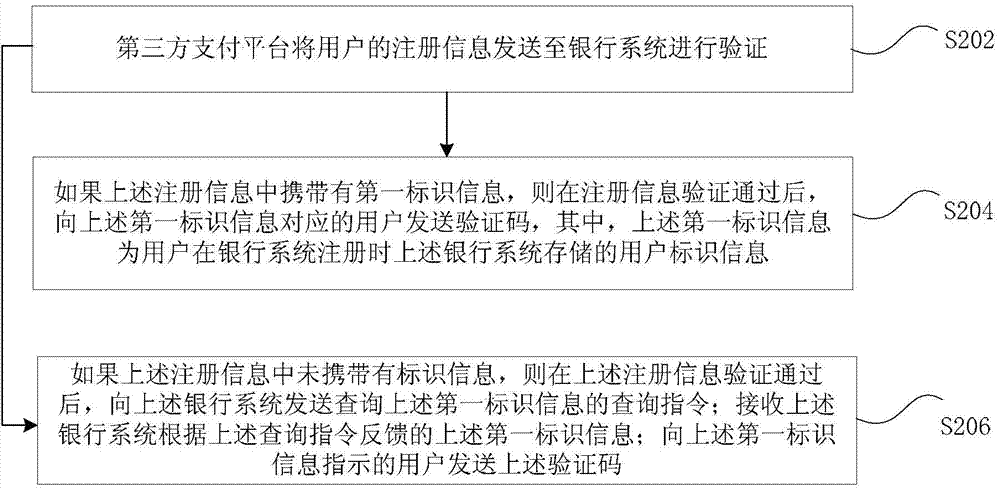
InactiveCN104852884AEnsure safetyEliminate technical issues of potential safety issuesFinanceTransmissionThird partyThird-Party Payments
Provided are a registration method, device and system for a third-party payment platform. The method comprises: sending, by a third-party payment platform, registration information about a user to a banking system for verification; if the registration information carries first identification information, after the verification of the registration information has been passed, sending a verification code to a user corresponding to the first identification information, wherein the first identification information is user identification information stored by the banking system when the user registers in the banking system; if the registration information does not carry the first identification information, after the verification of the registration information has been passed, sending a query instruction for querying the first identification information to the banking system; receiving the first identification information fed back by the banking system according to the query instruction; and sending the verification code to the user indicated by the first identification information. By means of the technical solution provided in the present invention, the technical problem in the related art that there is not yet an effective technical solution for eliminating potential security issues in the process of quick payment is solved.
Owner:ZTE CORP
Wireless Perimeter Security Device and Network Using Same
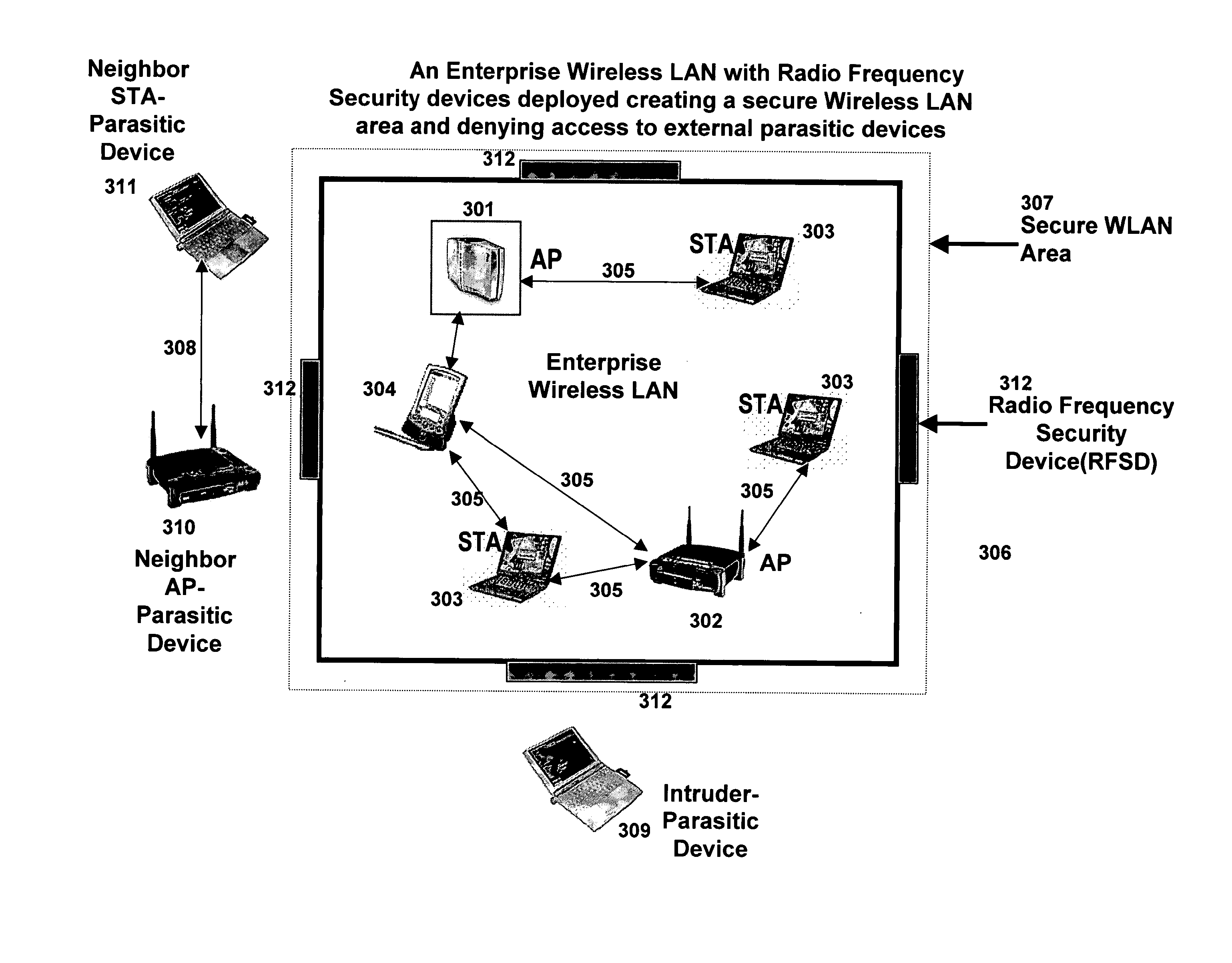
ActiveUS20080046566A1Eliminate loopholesEliminates data and interceptionNetwork topologiesData switching by path configurationWireless lanEngineering
A Radio Frequency based security system for providing security for wireless Local Area Networks (WLAN) that allows the creation and maintenance of arbitrarily shaped secure wireless access areas with boundaries around said wireless Local Area Network and prevents access to the said wireless LAN from outside the perimeter of the secure area. The system includes a plurality of perimeter Radio Frequency Sentry Devices (RFSDs) that are employed to establish the boundaries of said secure area around said wireless LAN. The wireless LAN being secured may be an industry standard IEEE 802.11a, 801.11b or 802.11g based wireless LAN or any other wireless LAN that uses packet based communication protocols. The said RFSDs may be stand-alone devices or they may be connected to a wired or wireless Local Area Network.
Owner:CALLAHAN CELLULAR L L C
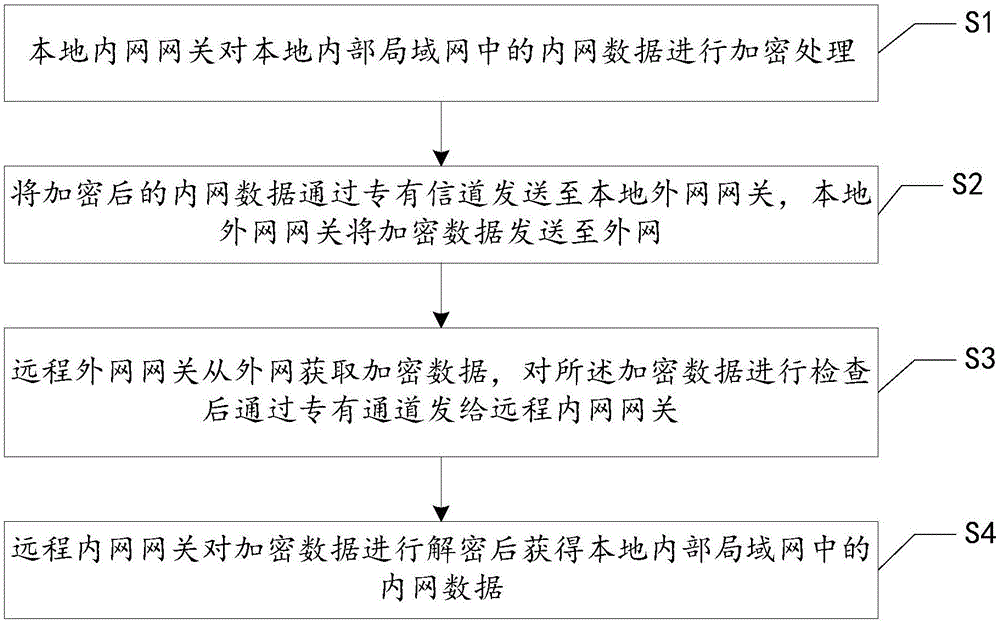
Anti-attack intranet data transmission method and system
InactiveCN106506540AImprove securityImprove resistance to attackTransmissionInformation transmissionPrivate network
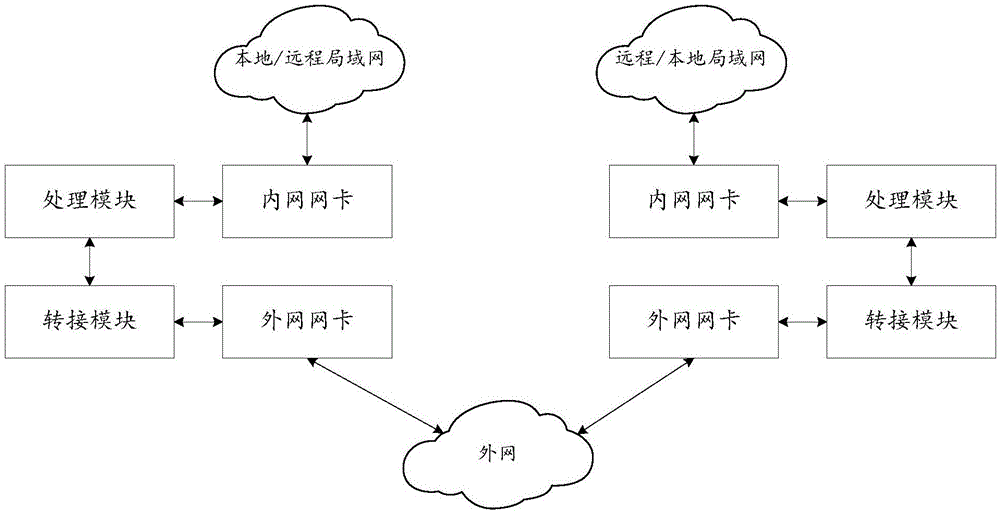
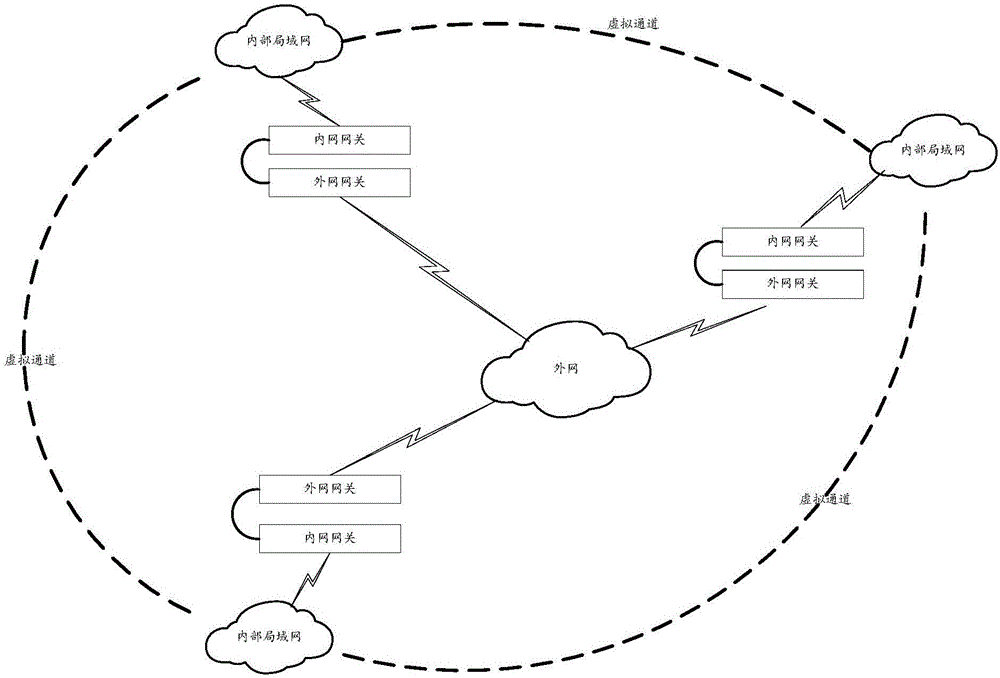
The invention relates to the field of information communication, in particular to an anti-attack intranet data transmission method and system, which solves the problems of low security and practicality during the conventional information transmission process. The method comprises the following steps: a local intranet gateway carries out encryption processing of intranet data in a local internal local area network (LAN); the encrypted intranet data is sent to a local extranet gateway through a special channel, and the local extranet gateway sends the encrypted data to an extranet; a remote extranet gateway acquires the encrypted data from the extranet, examines the encrypted data, and sends the examined data to a remote intranet gateway through a special channel; and the remote intranet gateway decrypts the encrypted data to obtain the intranet data in the local internal LAN. The method and system provided by the invention has the advantages that the data is transmitted between the internal LANs in different areas through extranet switching, and transmitted information is encrypted, so that the information security is improved, benefits from the extranet are utilized, and the anti-attack capability is greatly higher than that of the traditional virtual private network (VPN) system.
Owner:BEIJING SANSEC TECH DEV
Power controller
ActiveUS9702910B2Prevents catastrophic and destructive failureImprove reliabilityTransistorCircuit-breaking switches for excess currentsPower controllerPower switching
A power controller includes an input power terminal, an output power terminal, a power switching circuit connected between the input power terminal and the output power terminal, a detection circuit connected to the power switching circuit, one or more data interfaces, and a control device connected to the detection circuit and the one or more data interfaces. The detection circuit measures a load current and a current squared time (I2t) value between the input power terminal and the output power terminal. The control device automatically turns the power switching circuit “OFF” whenever the load current exceeds a first value or the current squared time value exceeds a second value or an “OFF” signal is received from the one or more data interfaces, and automatically turns the power switching circuit “ON” whenever an “ON” signal is received from the one or more data interfaces.
Owner:MICROPAC IND
Electronic check-in inspection method special for freeway collecting tolling
ActiveCN104574542AEliminate loopholesAvoid the influence of human factorsTicket-issuing apparatusSpecial data processing applicationsThree levelMonitoring system
The invention relates to an electronic check-in inspection method special for freeway collecting tolling. The electronic check-in inspection method includes the steps that (1) a station level check-in unit obtains normalized check-in recoding information; (2) a station level inspection unit conducts first-time inspection on the check-in recoding information; (3) a highway section center inspection unit conducts second-time inspection on the check-in recoding information. The electronic check-in inspection method is based on an electronic check-in inspection system, a three-level normalized system including station level checking-in, station level inspection and highway section center inspection is built, traceable normalized check-in data are obtained through a station level check-in device, traceable normalized first-time inspection is completed through the traceable normalized check-in data, normalized second-time inspection on the check-in data and first-time inspection is achieved through section center inspection, a rigorous monitoring system is accordingly formed, loopholes are eliminated, and influences of human factors are thoroughly avoided.
Owner:江苏高速公路联网营运管理有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com