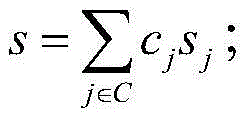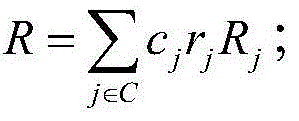Cloud-storage data lightweight-level public auditing method with privacy protection
A privacy-protecting, lightweight technology that is applied in the field of communications and can solve problems such as poor confidentiality and the inability to guarantee the integrity and correctness of user data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0073] The symbols used in the implementation are described in the table below:
[0074]
[0075]
[0076] The specific steps are:
[0077] (1) System initialization: define a P The elliptic curve E on , where p is a large prime number, set P to be a point where the upper order of E is a prime number q, and P is a cyclic group generator of , and The discrete logarithm problem on is intractable;
[0078] 1) From Z q Randomly select a value x, and calculate Q=xP, generate an elliptic curve-based signature algorithm public key K={(p,q,E,P,x,Q):Q=xP}, private key x;
[0079] 2) The system generates a lightweight symmetric encryption algorithm f, the symmetric key is τ, and τ is shared by the user and TPA;
[0080] 3) The system then randomly generates a public-private key pair (spk, ssk) of a lightweight signature algorithm, and sets a secure hash function h: → Z q ;
[0081] (2) Signature steps:
[0082] The user first sets the data file F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com