Two-dimension code electronic key implementation method based on digital signature
An electronic key and digital signature technology, applied in the field of smart locks, can solve the problems of inconvenience to change, easy to lose, not easy to recycle, etc., to achieve the effect of ensuring uniqueness and authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
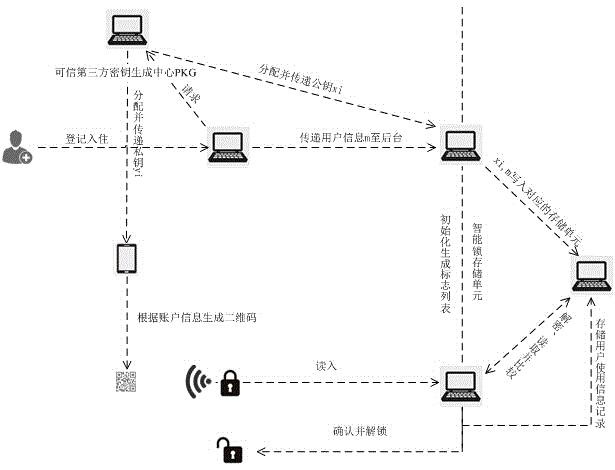
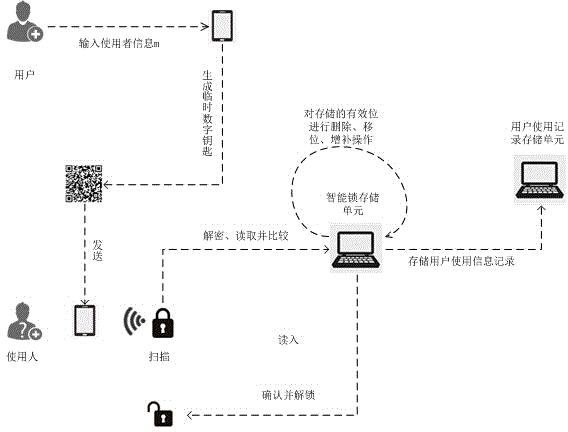
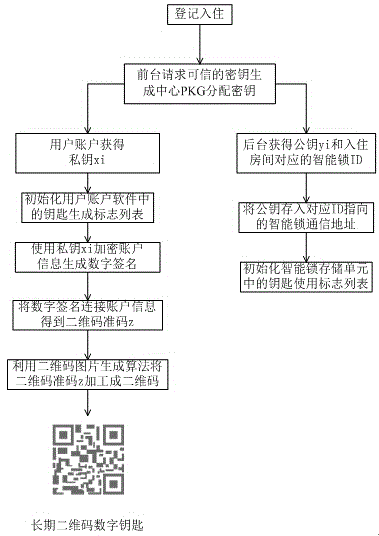
[0018] The generation and identification scheme of the electronic key is described according to the drawings.
[0019] 1. System initialization and user electronic key generation, see figure 1 and image 3 .
[0020] The key pair (x i ,y i ), private key x i Stored in the user account software on the mobile device. When the user makes a reservation through the Internet, checks in at the front desk, transfers the house, or confirms that the user has the right to use the room, he will register through the building management system, store the user identity information in the corresponding smart lock storage unit, and pass the system Find the account's public key y i Stored in the corresponding room smart lock storage unit.
[0021] When the user account software receives the assigned private key, the software automatically initializes the key generation flag list, according to the personal information of the user account, and sets the key type as the user's long-term key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com