MIPv6 based security multicast method and steps
A technology of secure multicast and multicast source, applied in the field of secure multicast based on MIPv6
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
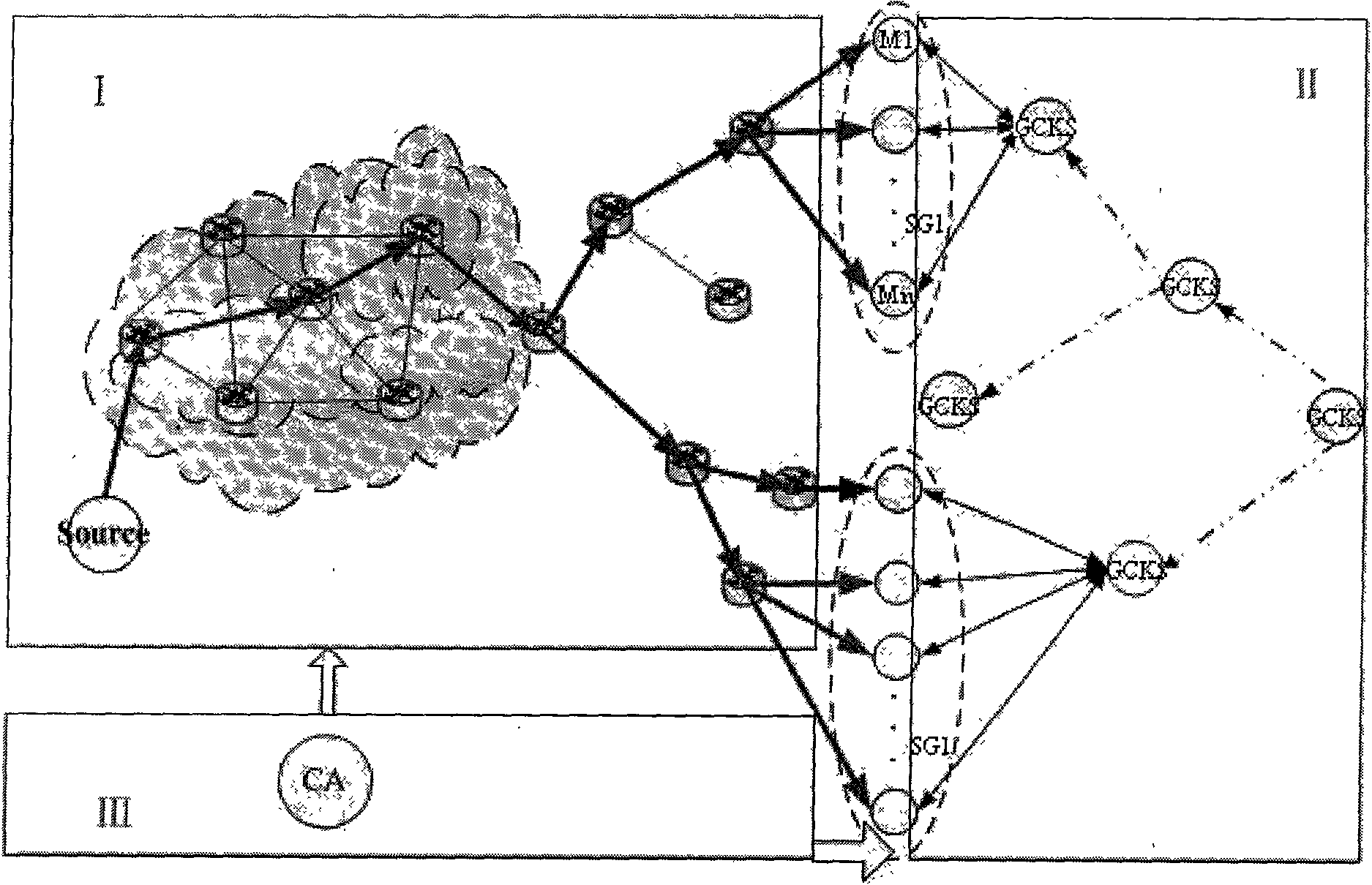
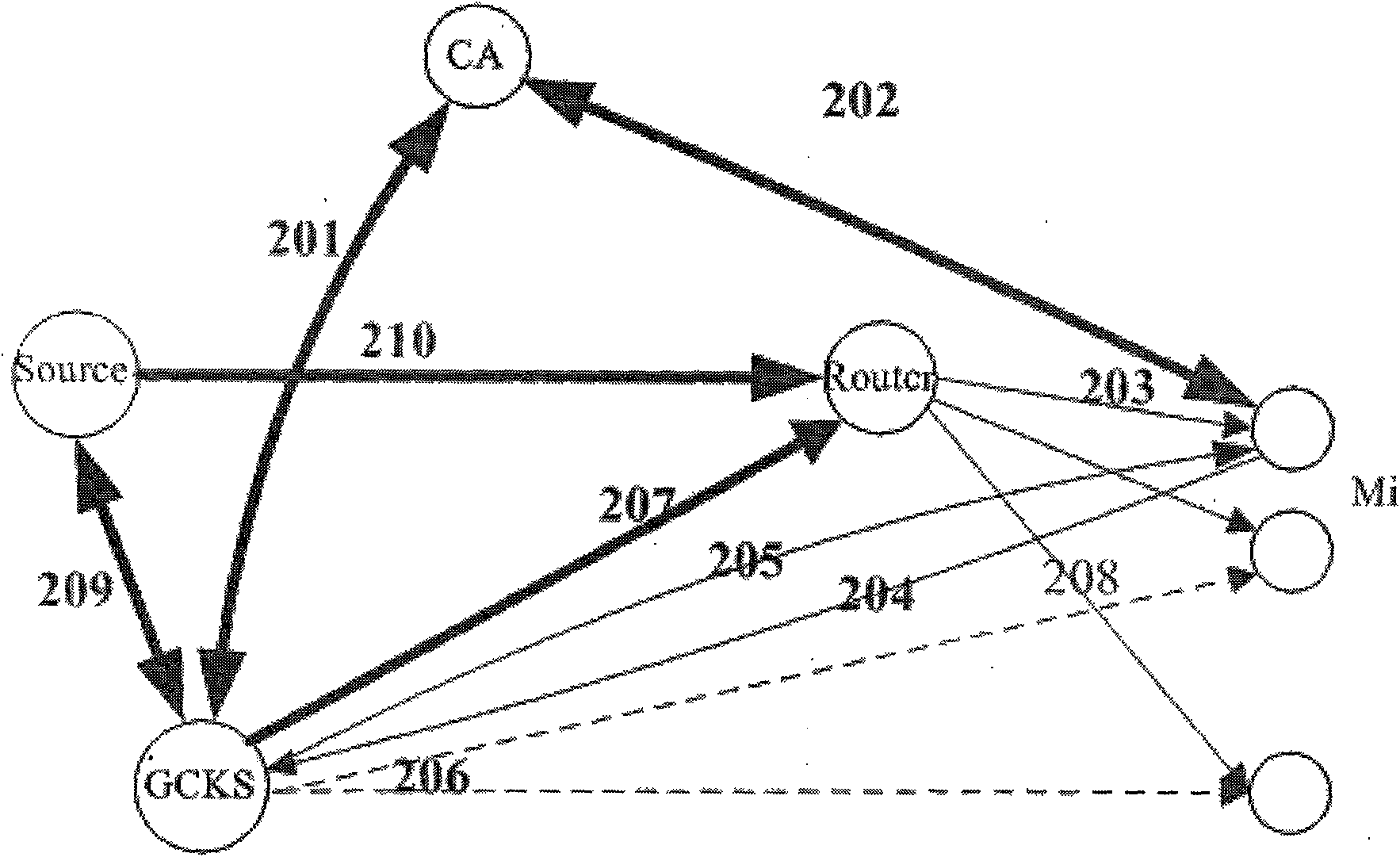
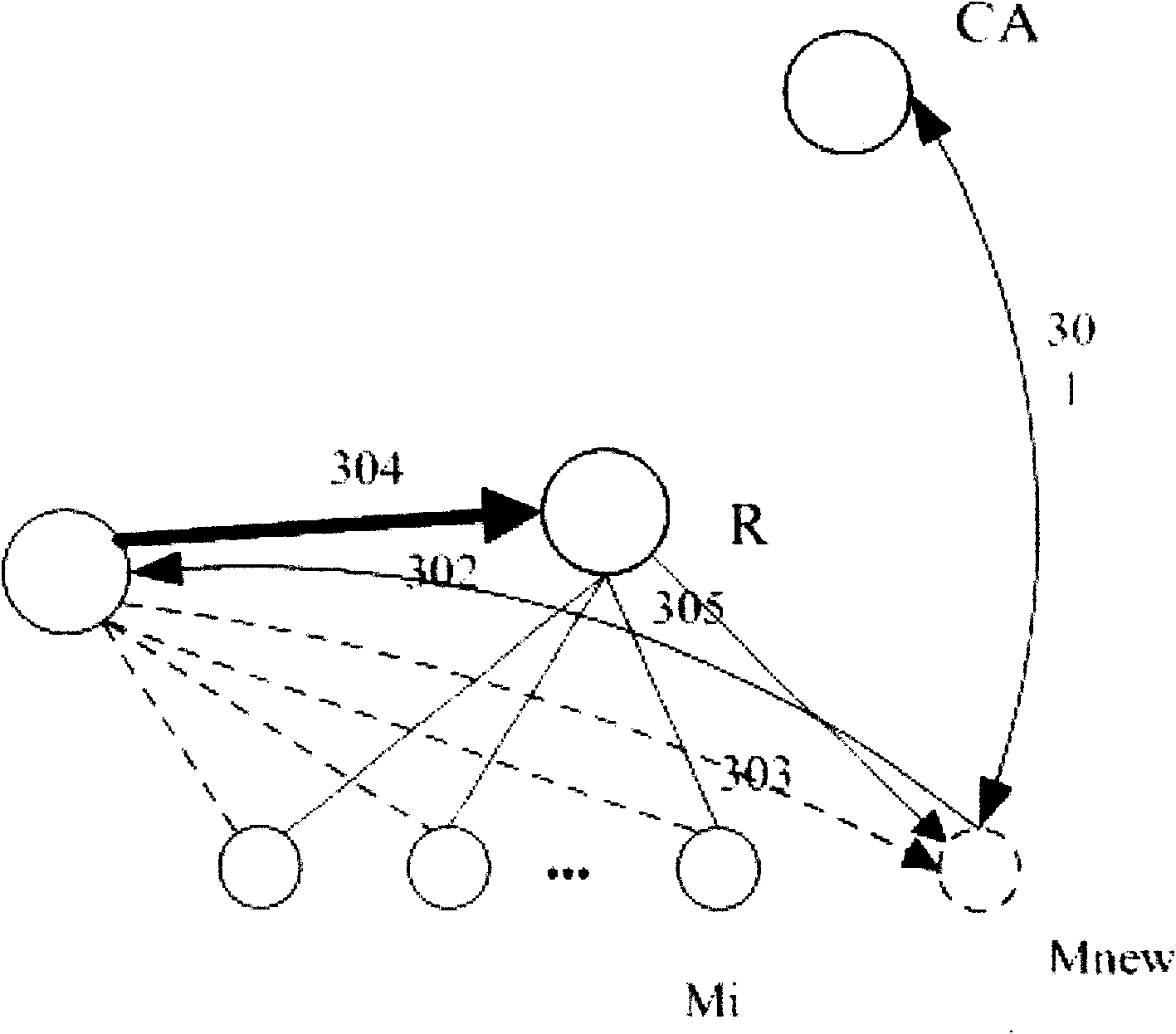
[0073] refer to figure 1 , the present invention includes 4 parts, namely CA center 1, GCKS 4 (group controller / key server), group member (multicast group) 2 and multicast source 3. Among them, CA (Certification Center) 1 is used for authenticating and distributing certificates to group members, multicast sources and GCKS; The router forwards the information list of group member 2; it is used for SA (Security Association) negotiation with the multicast source; it is used for GCKS negotiation to build a group key; the multicast source 3 is used to send multicast data to group member 2 through the intermediate router packet; group member 2 is used to obtain multicast packets.
[0074] From figure 1 It can be seen from the figure that the CA center authenticates the multicast source, GCKS and group members and distributes certificates using the CA deployment method of the PKI public key infrastructure. The format of the certificate is based on the general X.509 format. The pub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com