Network abnormal behavior intelligent detection and response method and device and electronic equipment
A technology for intelligent detection and network anomalies, applied in the field of computer networks, can solve problems such as network single point failure, honeypot quantity and management inconvenience, and increase the delay of normal network access, so as to improve response speed, convenience and accuracy, The effect of delaying the attack process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
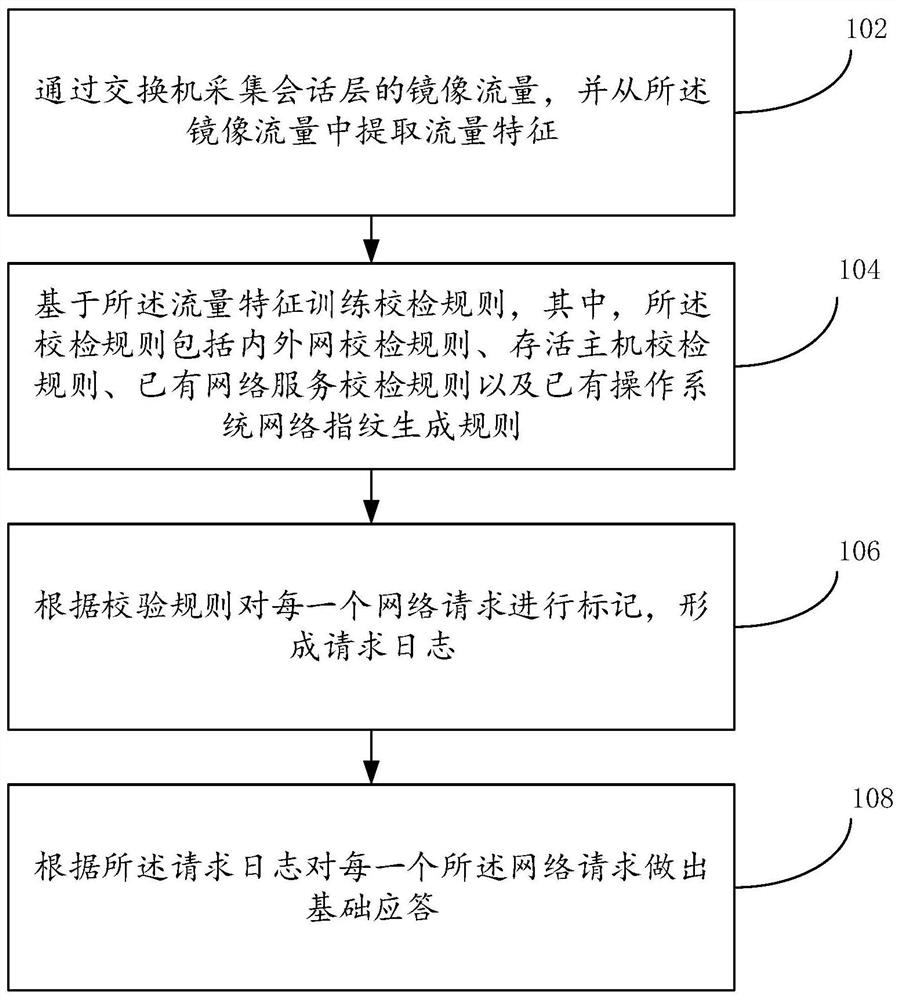
[0059] see figure 1 , the present disclosure provides an intelligent detection and response method for abnormal network behavior, specifically including the following method steps:
[0060] Step S102: collecting mirrored traffic at the session layer through the switch, and extracting traffic characteristics from the mirrored traffic.
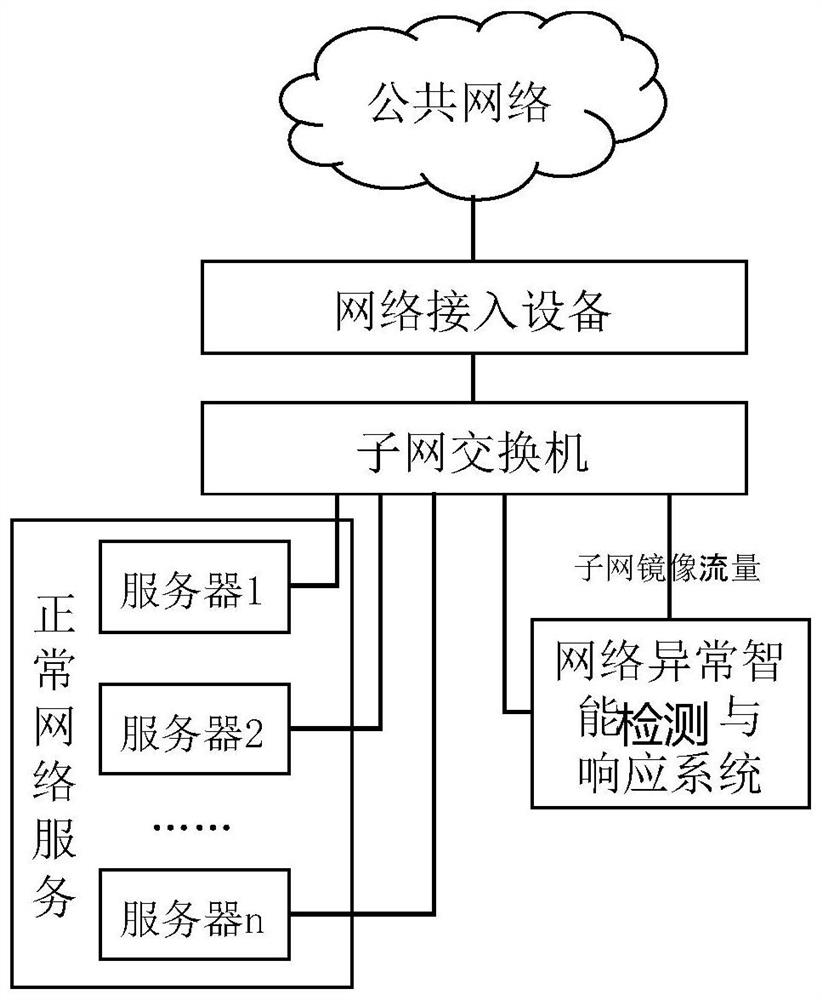
[0061] Such as figure 2 As shown in the figure, the network abnormal behavior intelligent detection and response system is connected to the mirror traffic interface of the target network, and the mirror traffic data of the key session layer communicating with the local network is collected through the subnet switch, and the mirror traffic data is received by each server in the normal network service. The mirrored traffic data is exactly the same. On the one hand, the mirrored traffic data is used to generate subsequent detection rules, and on the other hand, it is used for anomaly detection.
[0062] Among them, the traffic characteristics in...
Embodiment 2
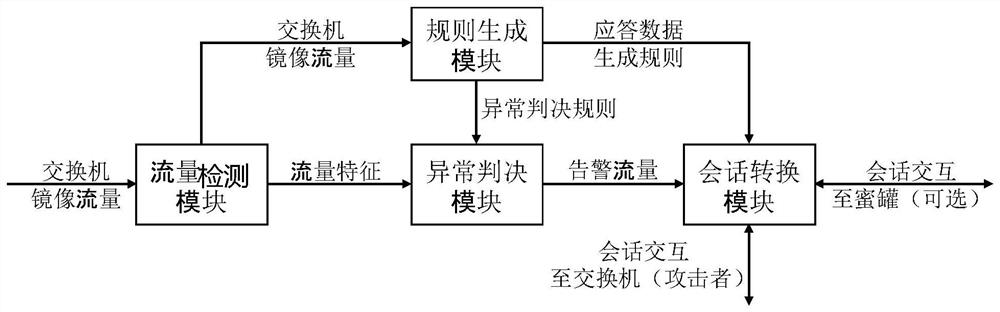
[0101] see Figure 7 , the present disclosure provides an intelligent detection and response system for abnormal network behavior, the detection and response system is embedded in the entire network interaction system in the form of hardware or software modules, such as figure 2 As shown, the network access device obtains network data from the public network, forwards the network data to the server through the subnet switch, and distributes the data to the network abnormal behavior intelligent detection and response system. The internal modules of the network abnormal behavior intelligent detection and response system pass the software Or hardware implementation, the same functional modules have the same technical effect as in Embodiment 1, and will not be repeated here. The network abnormal behavior intelligent detection and response system specifically includes:
[0102] The extraction unit 702 is configured to collect mirrored traffic at the session layer through the switc...
Embodiment 3
[0129] The present disclosure provides an electronic device, including a processor and a memory, the memory stores computer program instructions that can be executed by the processor, and when the processor executes the computer program instructions, any one of the first aspects can be realized. The method steps described above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com