Fingerprint fuzzy vault method based on (k, w) threshold secret sharing scheme
A fuzzy treasury, threshold secret technology, applied in the field of pattern recognition and cryptography, can solve the hidden dangers of subkey security and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
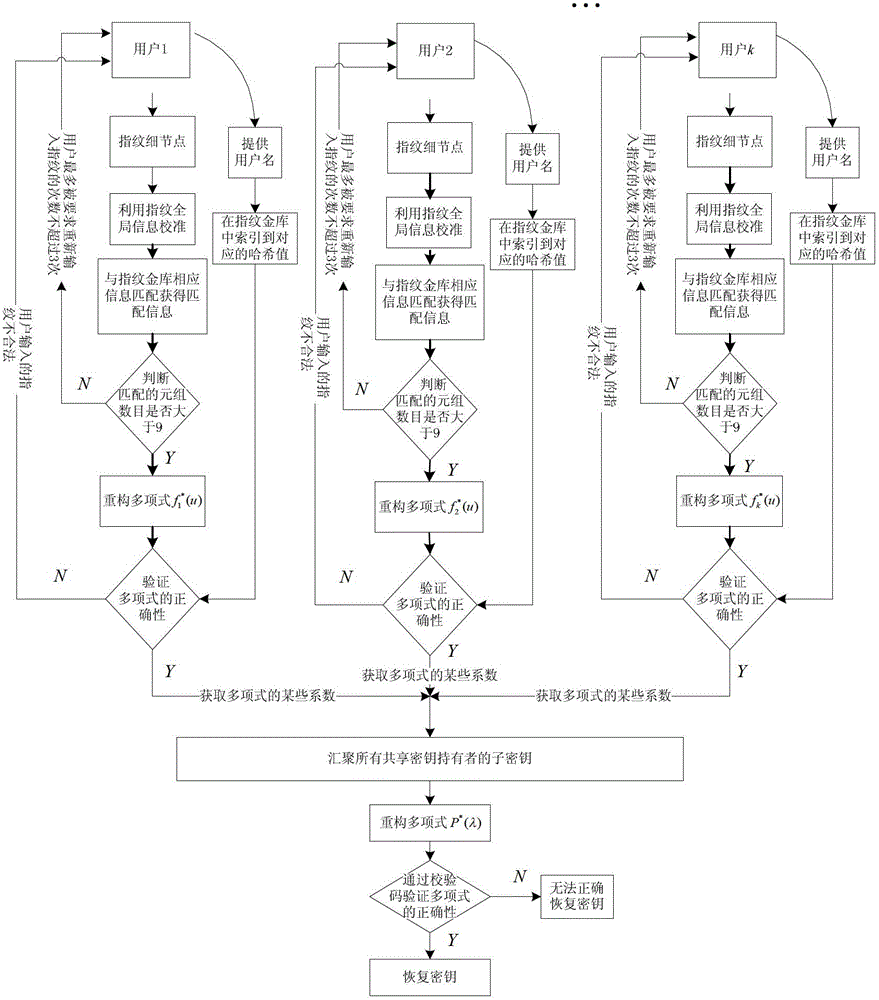
[0045] The present invention will be further described below in conjunction with accompanying drawing.
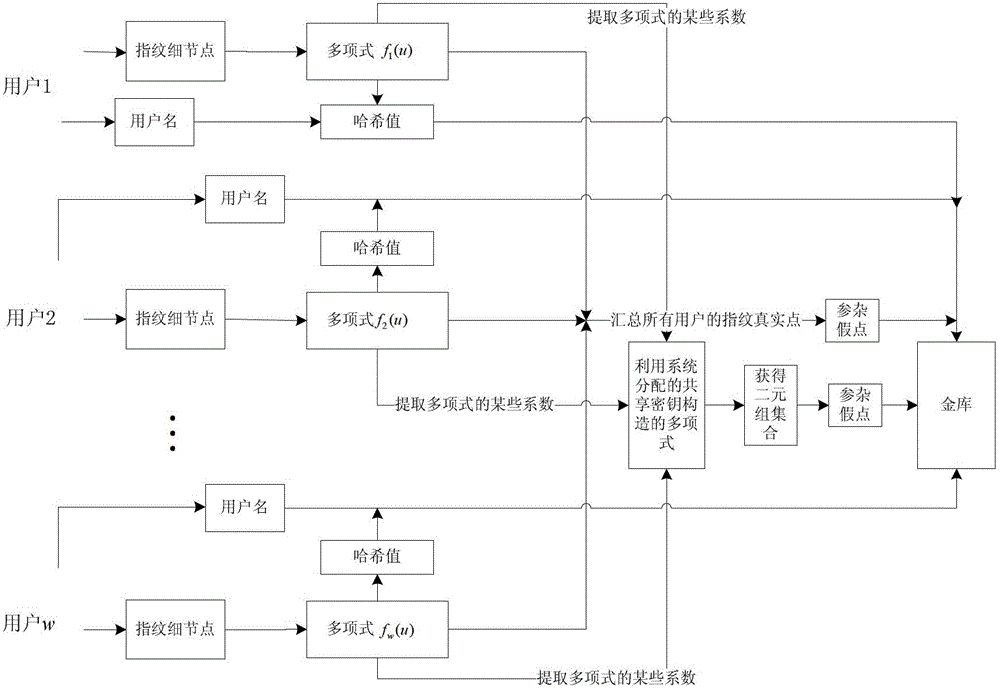
[0046] The details of the shared key distribution stage are as follows (such as figure 1 shown):
[0047] 1. The binding process of fingerprint fuzzy vault and user sub-key
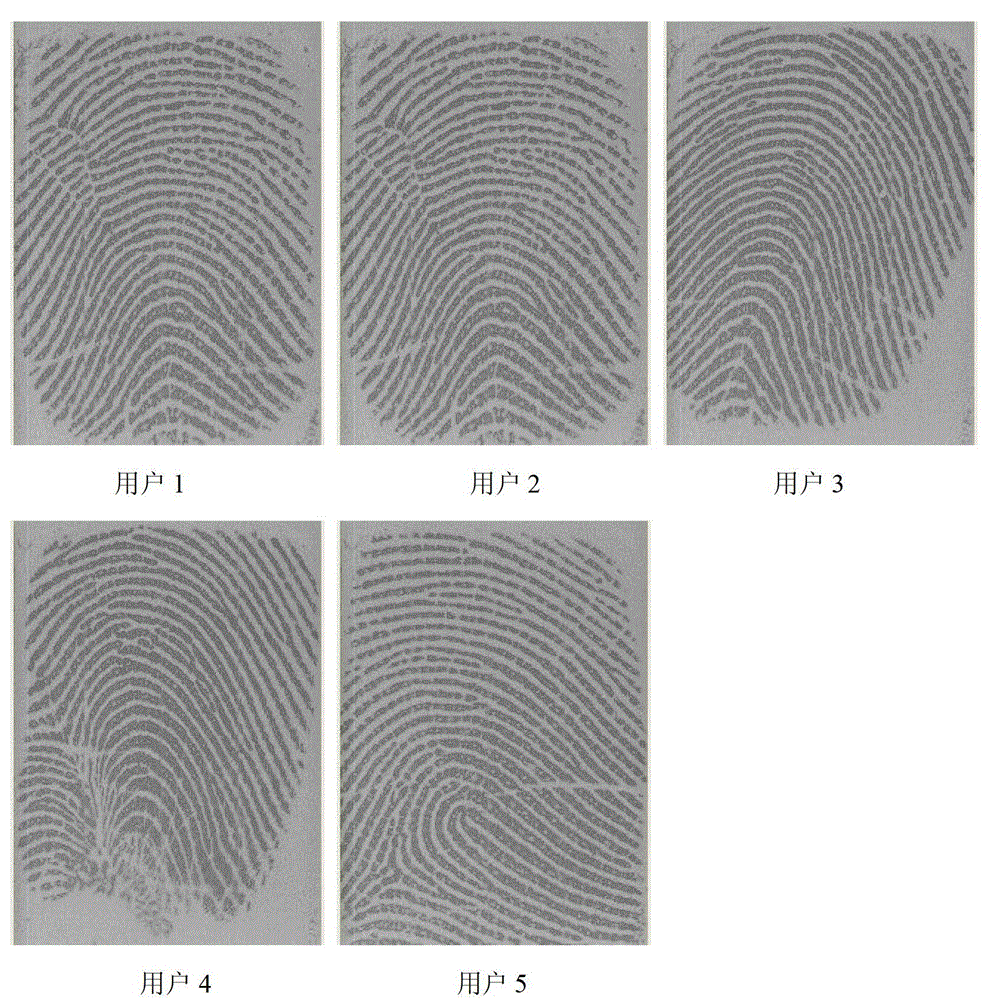
[0048] step 1. Each user enters their personal registered user name and fingerprint respectively. Part of the fingerprint images in the fingerprint database for testing are as follows: image 3 . A series of preprocessing operations such as segmentation, direction field and gradient calculation, equalization, convergence, smoothing, enhancement, binarization, and thinning are performed on the fingerprint image to obtain a clear binary image that maintains fingerprint feature information. Then extract all the feature points in the image, filter and remove the false feature points, and keep the real feature points of the original image, such as Figure 4 shown.
[0049] Step 2. Linearly map the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com