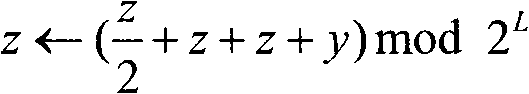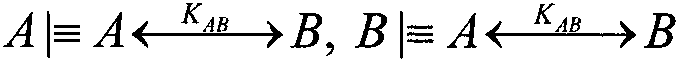Wireless network lightweight class authentication key negotiation protocol based on digital certificate
An authentication key agreement and lightweight authentication technology, which is applied in the field of lightweight authentication key agreement in wireless Internet, can solve the problems of insufficient anti-attack capability, small calculation overhead, and excessive communication calculation overhead, etc., to achieve Satisfy the effect of fewer communication times, less computational overhead, and perfect forward secrecy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] (1) Implementation steps
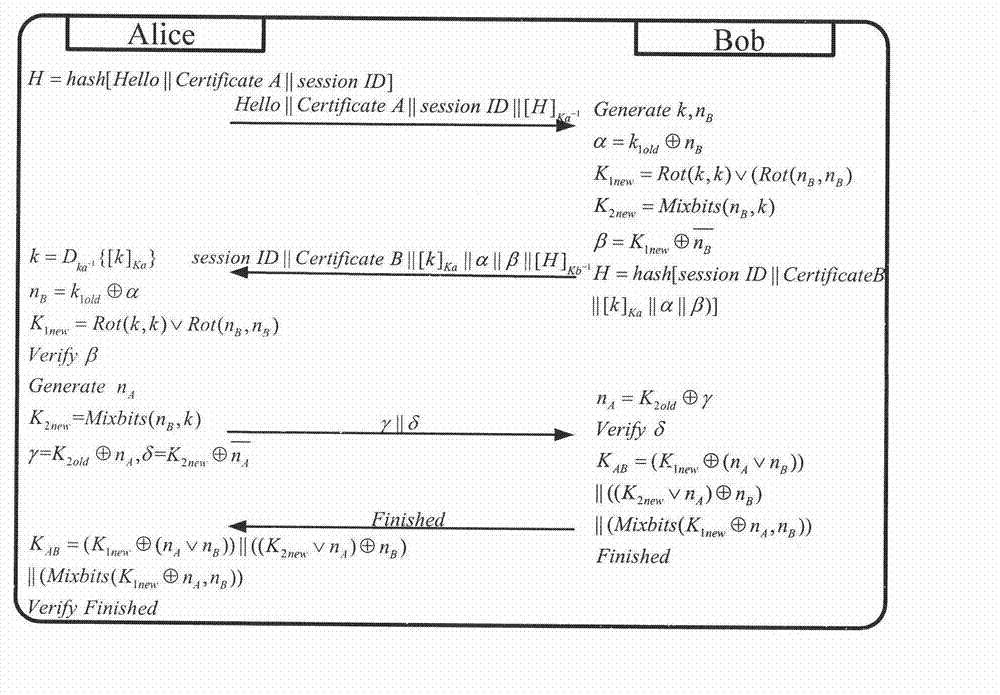
[0020] The protocol includes three stages: identity authentication, key negotiation, and key update. The specific interaction process between users Alice and Bob in the protocol is described as follows:
[0021] 1. Alice sends a Hello message to Bob to initiate a session, and attaches Alice's digital certificate and session ID after the Hello message, calculates the message digest and encrypts it with A's private key to generate a digital signature. Note that when the session ID is non-zero, it means that the user wants to restore the parameters of the previous session, and the saved k of the previous session is used when calculating the new key.
[0022] 2. After receiving A's Hello message, Bob checks the validity of A's digital certificate, performs identity authentication, extracts Alice's public key, verifies A's digital signature, checks the integrity of the message, and proves that A is indeed holding the session for this session. Ther...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com