Safety verification method, device and system based on non-interactive zero-knowledge
A non-interactive, verification device technology, applied in the field of security verification based on non-interactive zero-knowledge, can solve problems such as poor security and inability to check duplicate transactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] This embodiment provides a non-interactive zero-knowledge-based security verification method, such as figure 1 As shown, the method mainly includes:
[0031] Step 101: Generate the public key and private key of the central node device and the public key and private key (may be referred to as public key and private key) of each local node device respectively according to the input security parameters.
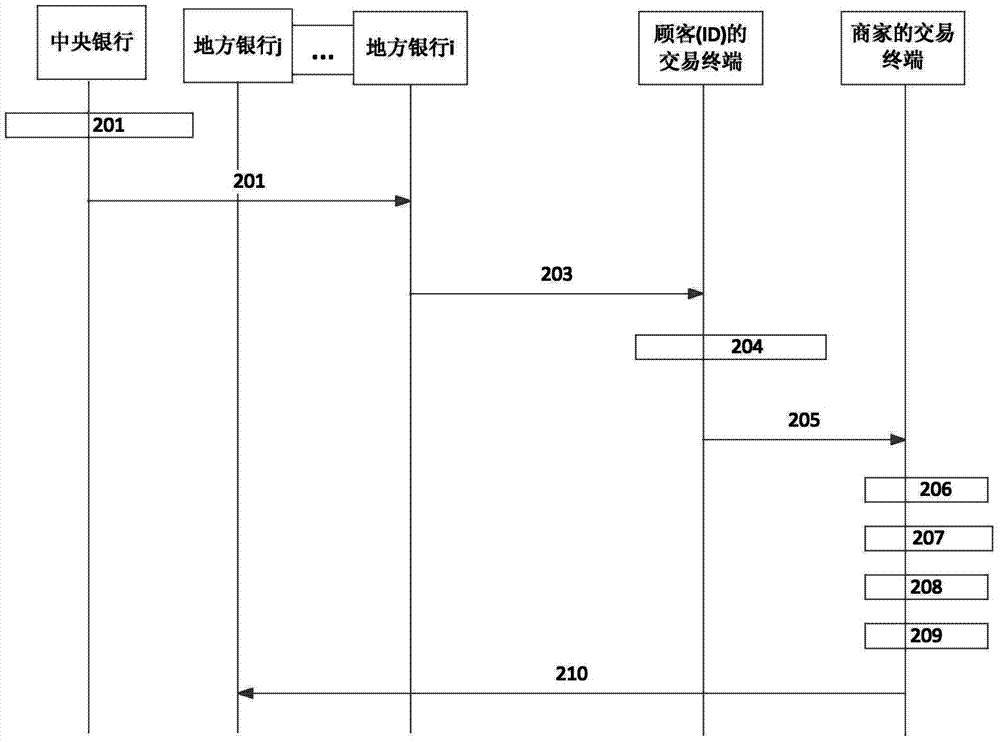
[0032] This step 101 can be regarded as a process of system initialization. For a specific execution method, reference may be made to step 201 in Embodiment 2.
[0033] Step 102, any local node device I (I is any natural number, here the local node device I represents any local node device) in each local node device obtains the identity commitment value with its identity ID as the commitment object, and then uses its identity ID as the commitment object to obtain the identity commitment value. And the identity commitment value is sent to the central node device; the cen...
Embodiment 2
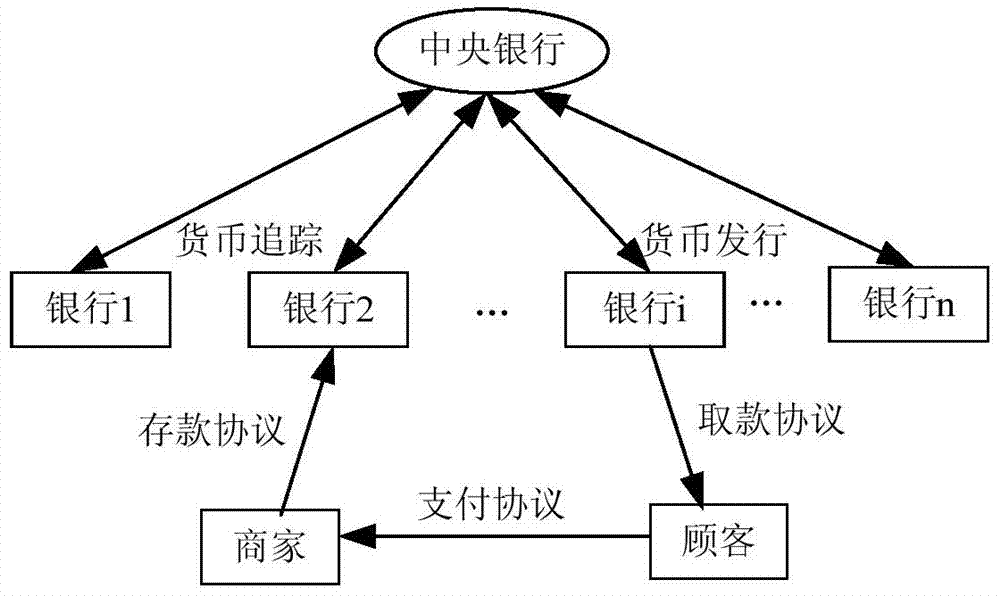
[0057] This embodiment combines figure 2 The multi-bank electronic cash system model shown provides a non-interactive zero-knowledge based security verification method. In this method, the central bank is equivalent to the central node device; each local bank is equivalent to each local node device, such as local bank i is equivalent to local node device I; the customer's transaction terminal is equivalent to the verification device; the merchant's transaction terminal is equivalent to the first Three-party platform; electronic cash in transactions is equivalent to key business information.
[0058] like figure 2 As shown, in the construction of an anonymous and untraceable electronic cash system, there are multiple local banks participating, and each bank can safely issue electronic money, which is equivalent to several group members; these banks form a group subject to the Central Bank Controlling the group, the central bank is equivalent to the group manager. These ban...
Embodiment 3
[0112] In order to facilitate the implementation of the method in Embodiment 1 or 2, this embodiment provides a local node device, such as Figure 4 As shown, it includes: an acquisition unit 21 , a commitment unit 22 , and a certification unit 23 .
[0113] The acquiring unit 21 is used to acquire the public key and the private key of the local node device generated by the central node device; the commitment unit 22 is used to obtain the identity commitment value with its identity ID as the commitment object, and then its identity ID and identity commitment The value is sent to the central node device; the certification unit 23 is used to receive the certificate information issued by the central receiving device, and after obtaining the certificate commitment value with the certificate information as the commitment object, construct a non-interactive zero-knowledge proof based on the certificate commitment value, and according to the non-interactive zero-knowledge proof. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com