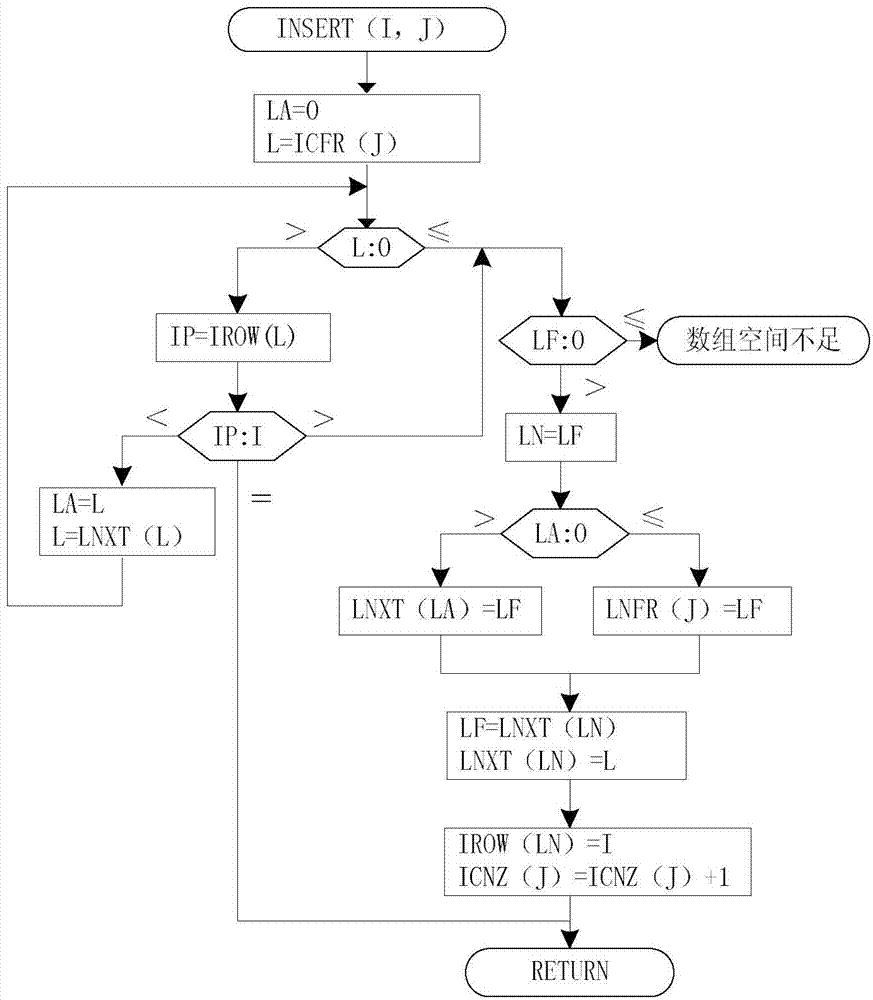
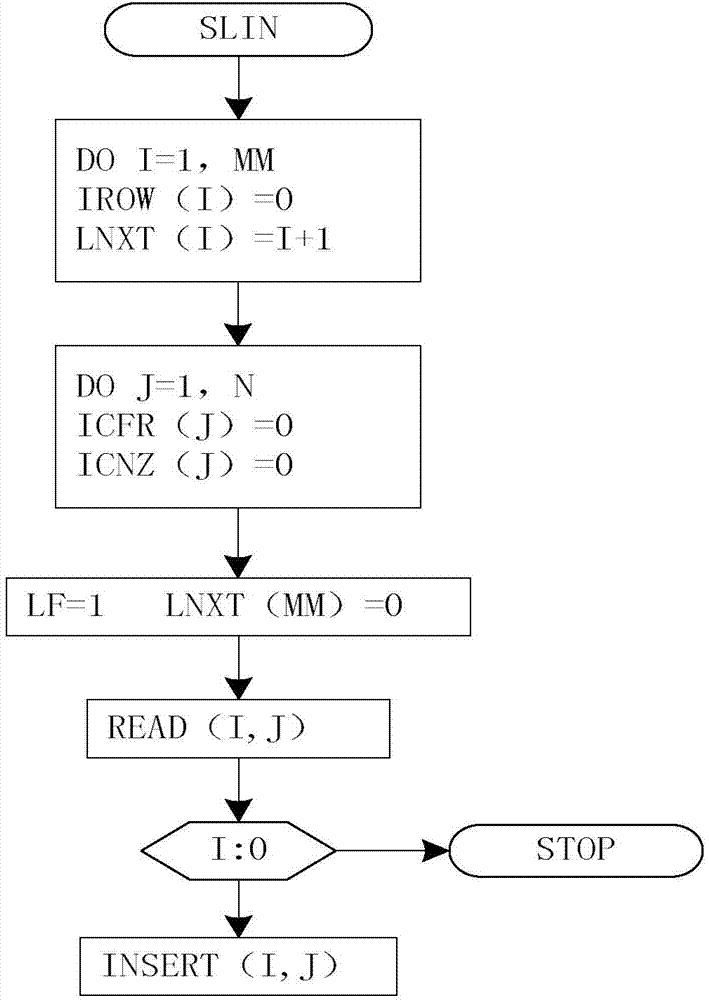
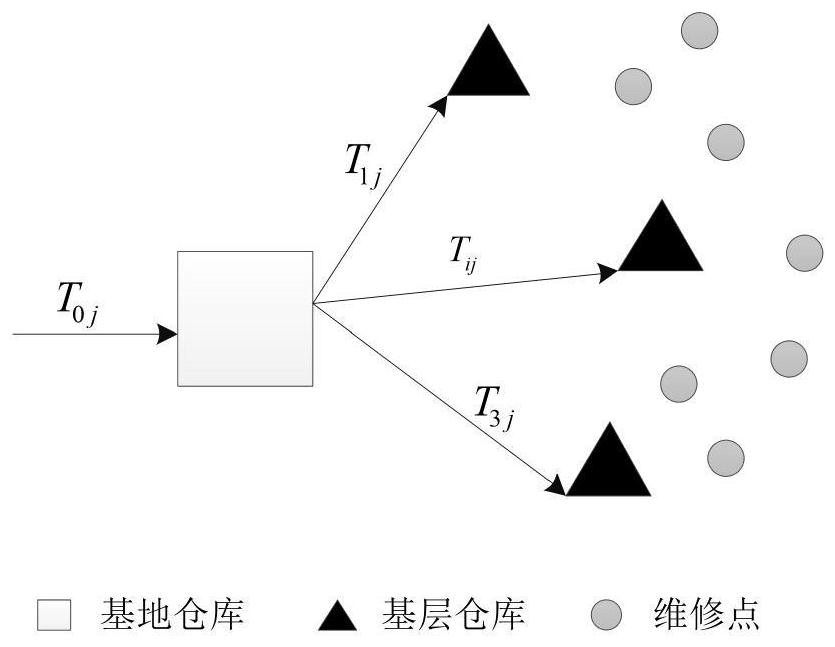
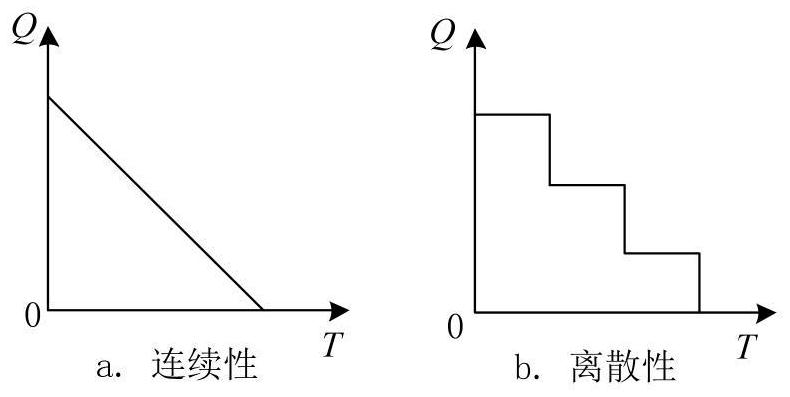
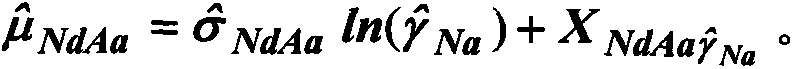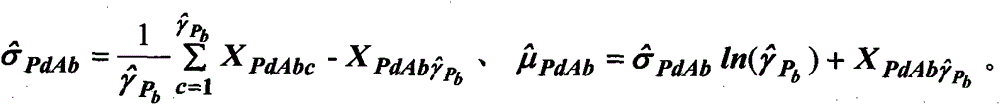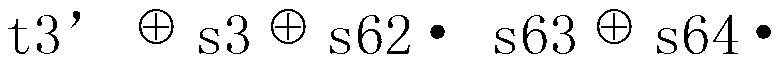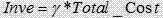Patents
Literature
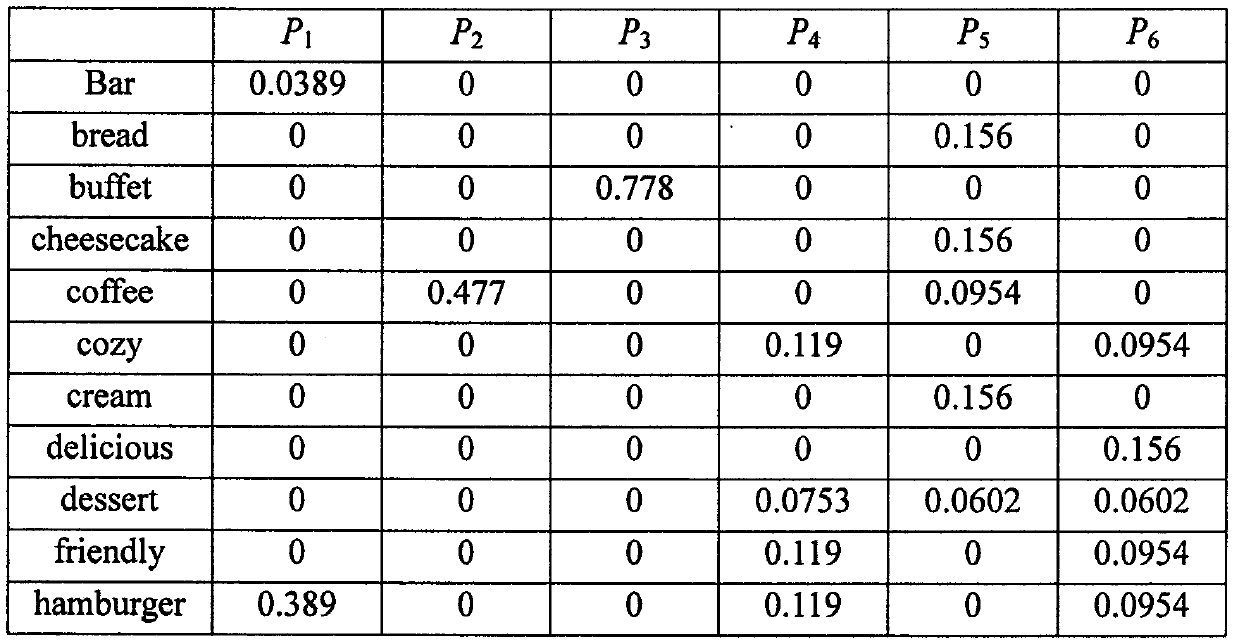
58results about How to "Low storage cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
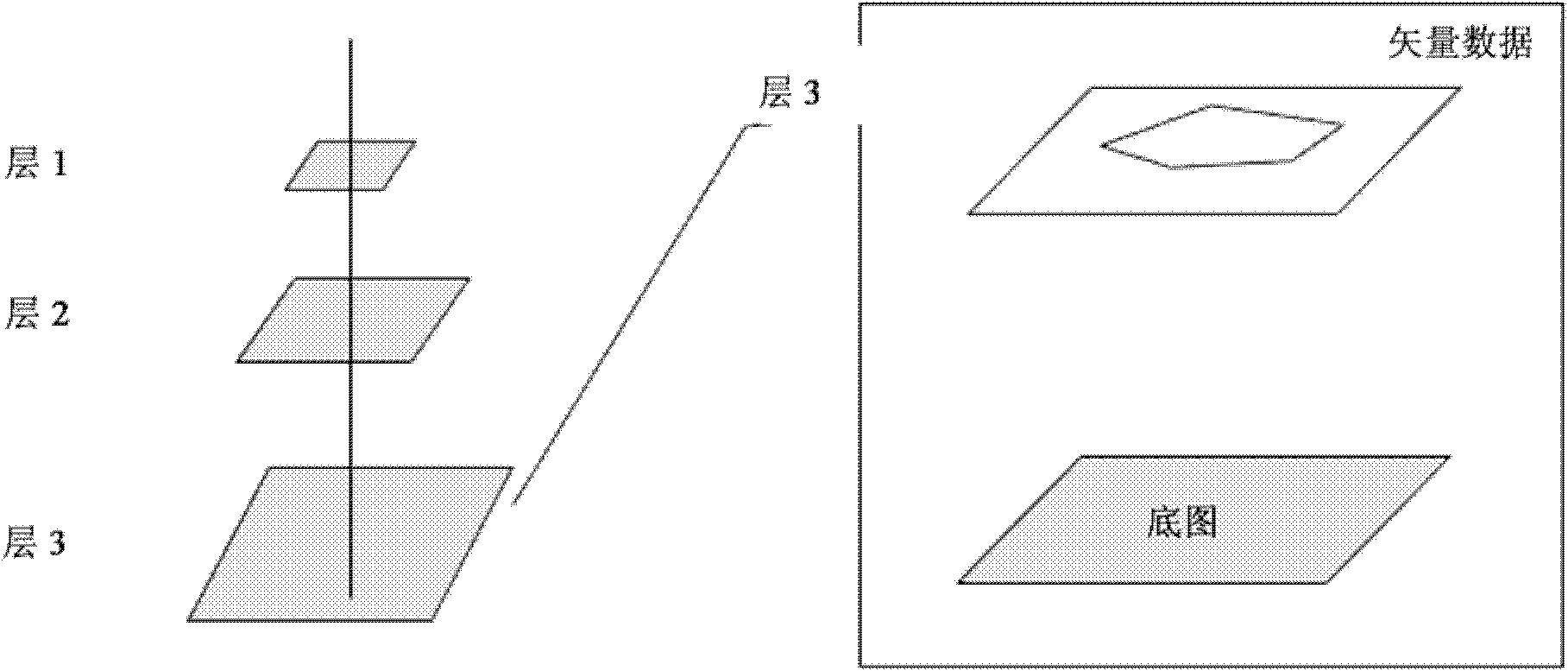
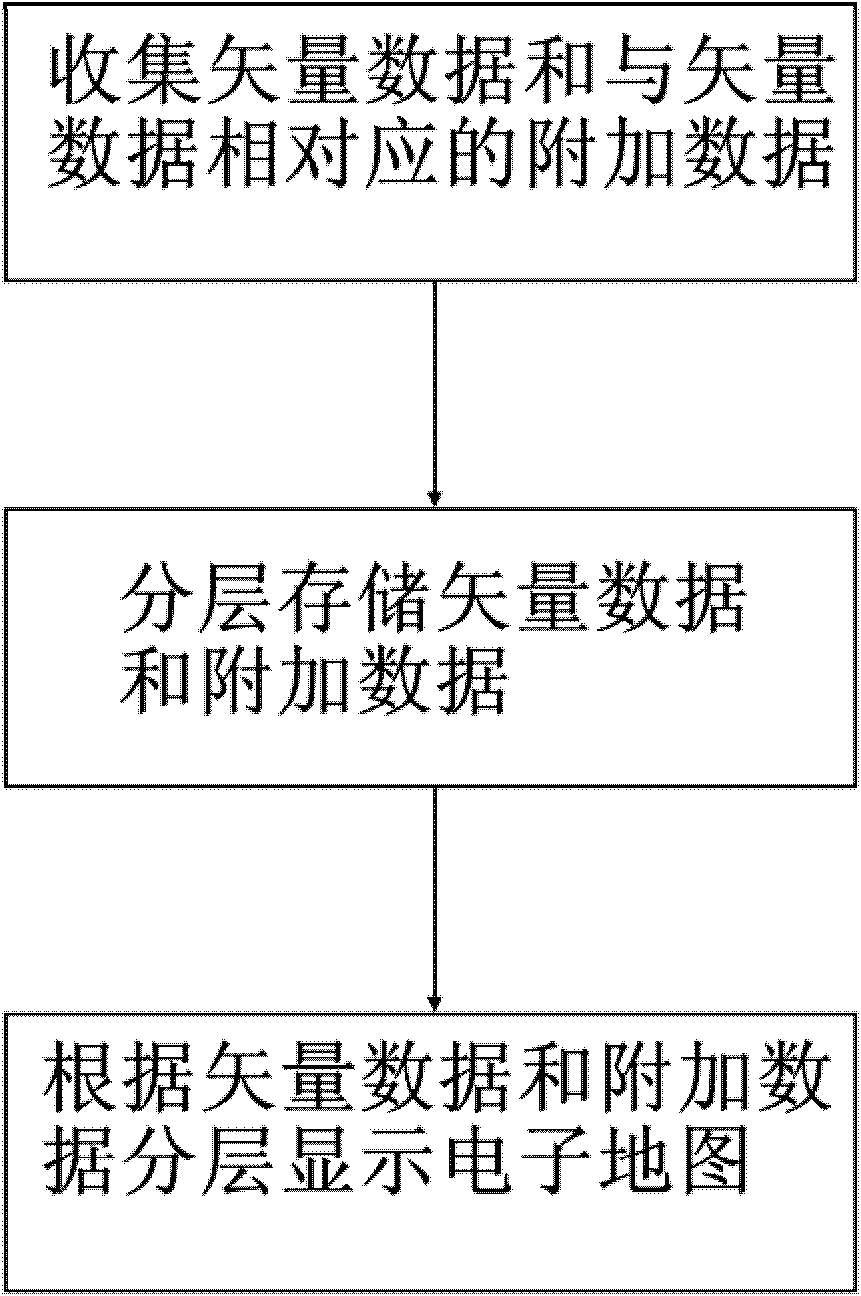
Method for generating electronic map
InactiveCN103187002AShortcut displayClear logicMaps/plans/chartsGeographical information databasesElectronic mapCollections data
The invention provides a method for generating an electronic map. The method includes a data collecting procedure, a data storage procedure and an electronic map displaying procedure, wherein the data collecting procedure includes a step of collecting vector data and additional data corresponding to the vector data; the data storage procedure includes the steps of storing the collected vector data and the collected additional data in a server database, enabling the vector data corresponding to different types of main body elements to be stored in a plurality of layers, and enabling the vector data of each type of main body elements to be stored in one layer; the electronic map displaying procedure includes the steps that an electronic map displaying end obtains the vector data and the additional data from a server, draws vector diagrams corresponding to each layer of vector data layer by layer according to the vector data in each layer, and adds the additional data related to main body element identification data (ID) in the layer of vector data, and consequently the electronic map is generated in a displaying device.
Owner:北京点道互联科技有限公司
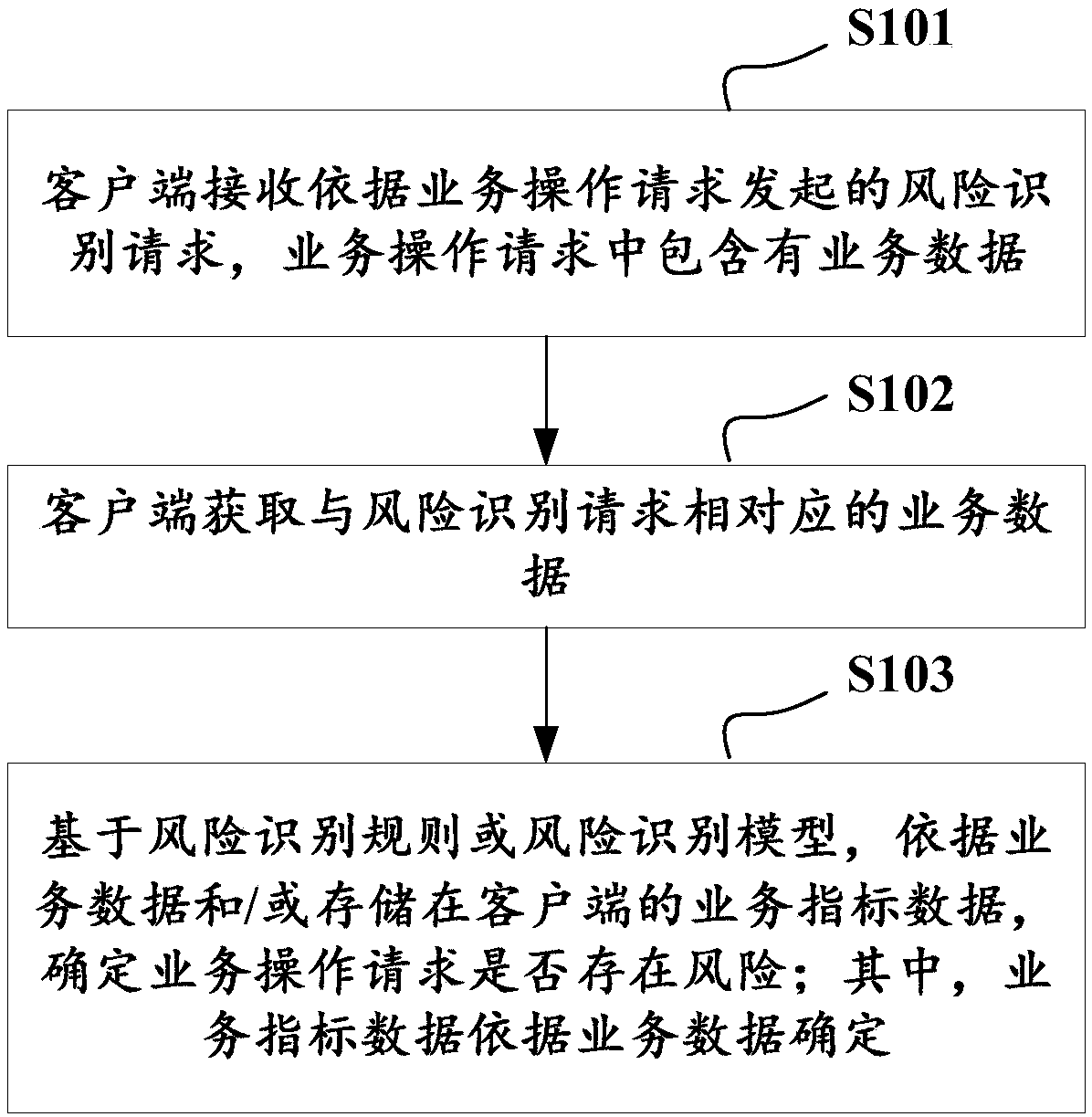
Risk identification method, client device and risk identification system
InactiveCN107644340AReduce storage costsLow storage costTransmissionCommerceRisk identificationClient-side
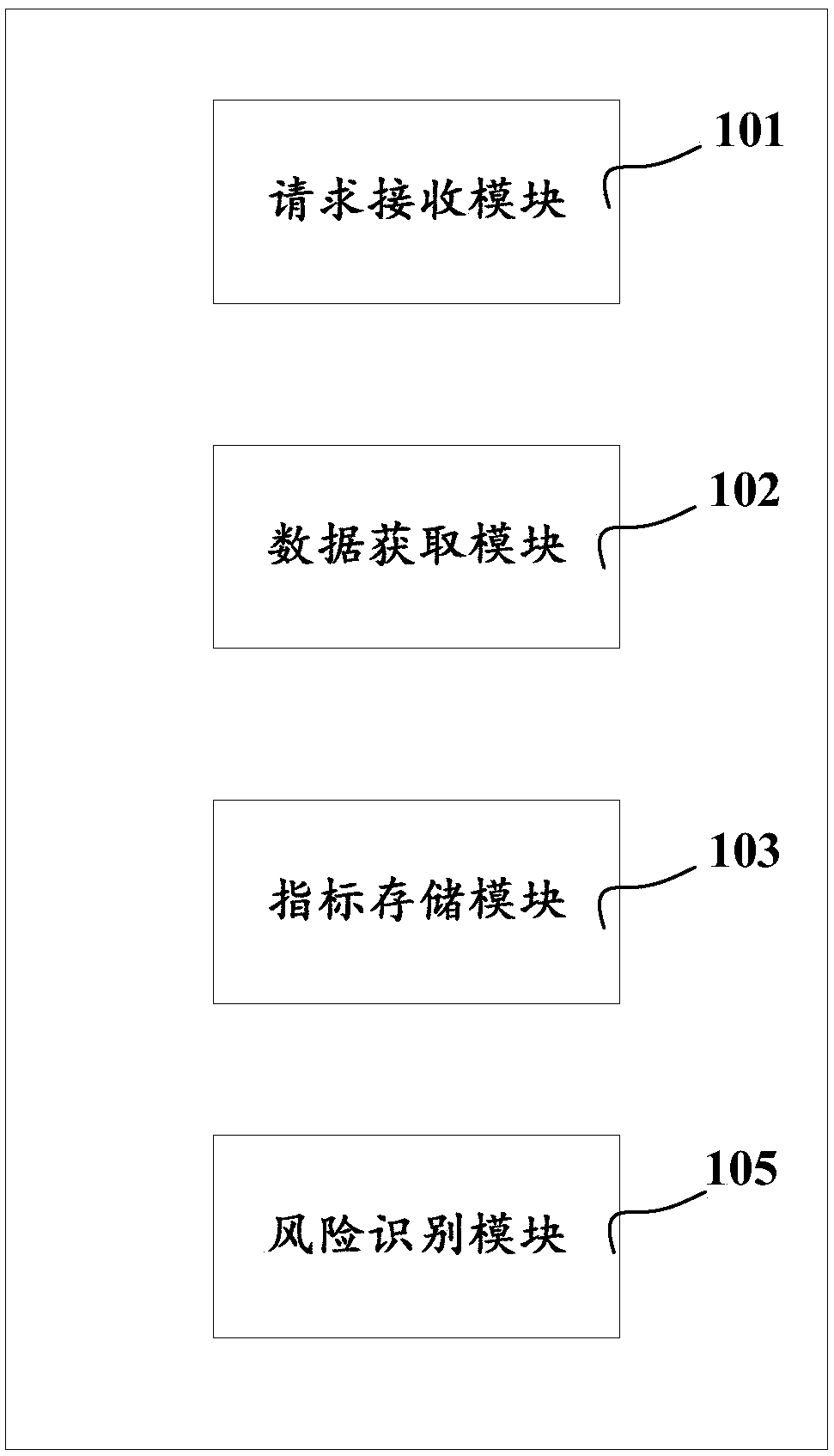
The present invention discloses a risk identification method. The method comprises: receiving a risk identification request initiated according to a service operation request through a client, whereinthe service operation request comprises service data; obtaining service data corresponding to the risk identification request by the client; and based on a risk identification rule or a risk identification model, determining whether the service operation request has risks or not according to the service data and / or service index data stored in the client, wherein the service index data is determined according to the service data. The present invention further discloses a risk identification device. The risk identification device comprises a data obtaining module, an index storage module and arisk identification module. The present invention further discloses a risk identification system. The system comprises a client device and a server device, or a client device, a server device and a cloud risk identification device. The problem is solved that the cost of a server is too high in the prior art, consumption for the server is reduced, and storage cost of risk identification and control is reduced.
Owner:ADVANCED NEW TECH CO LTD
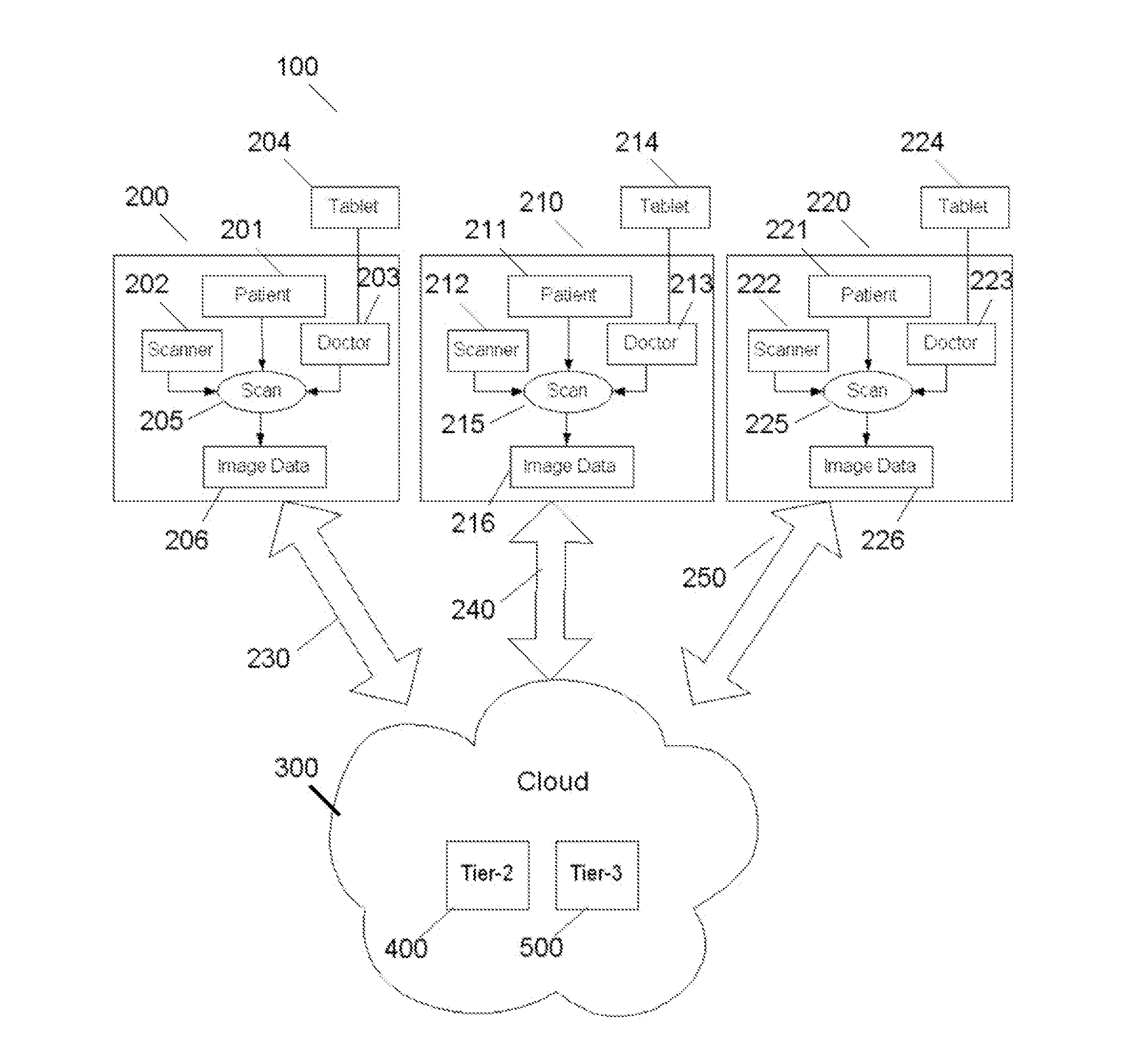
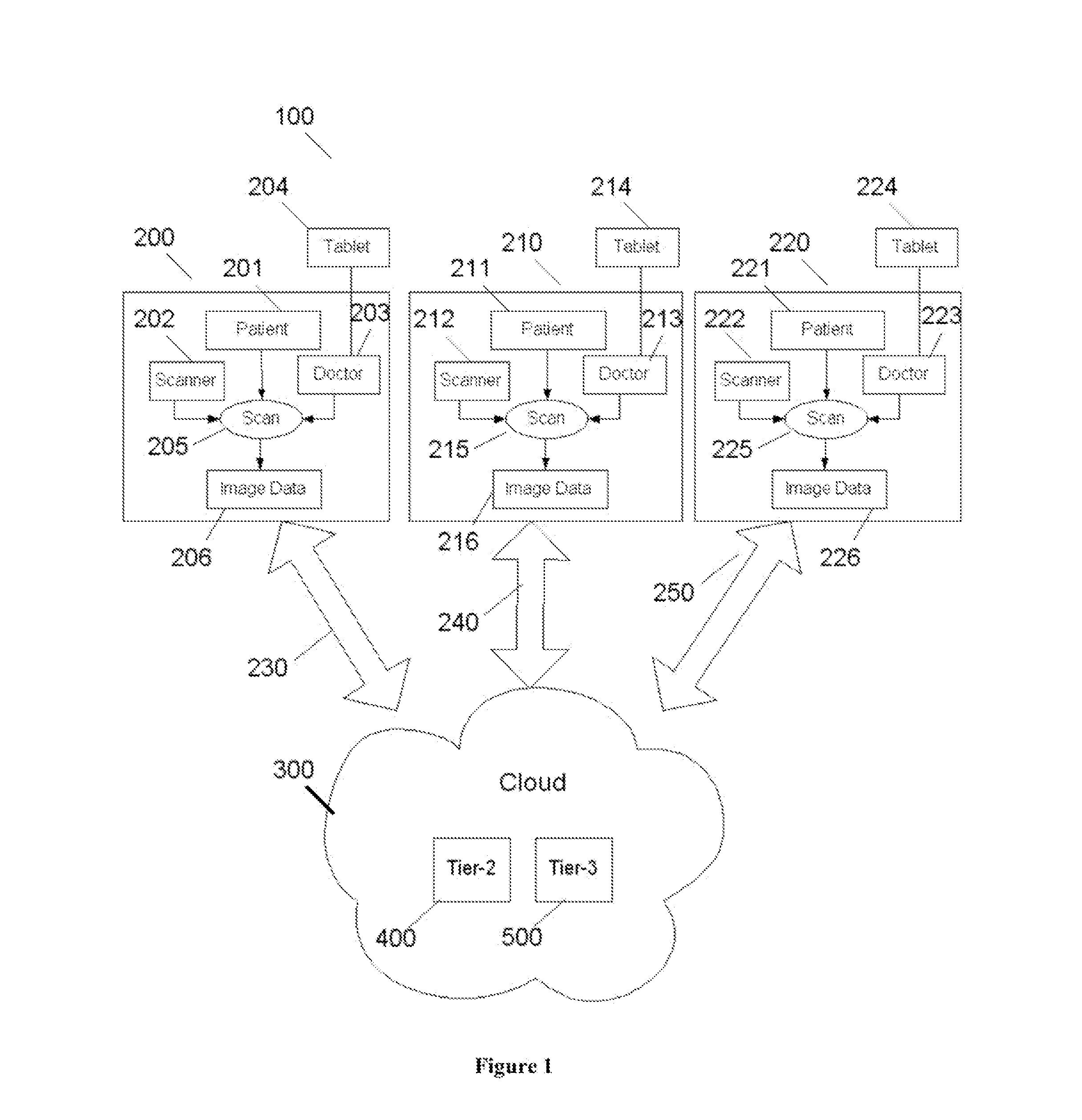
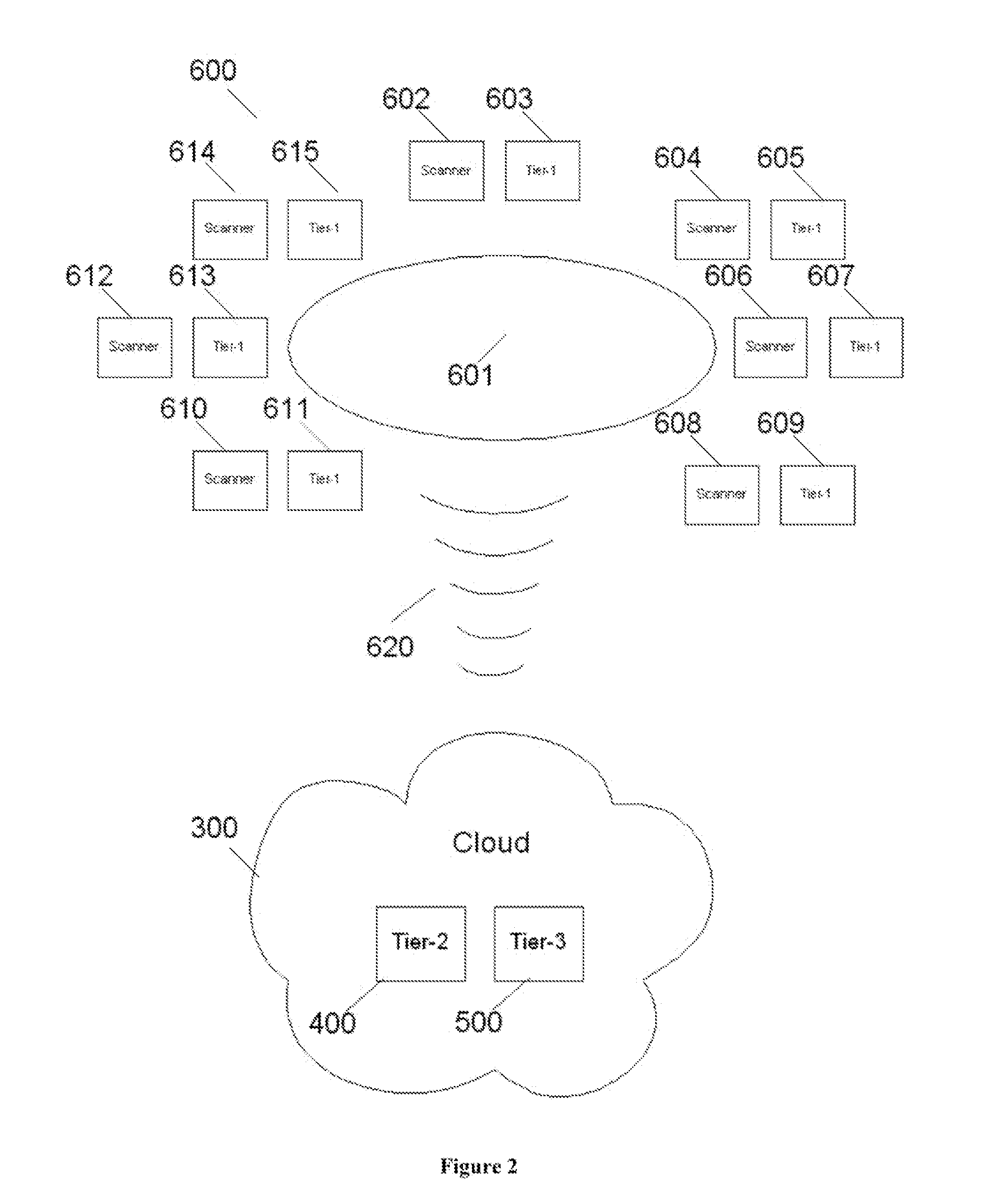
Mobile Architecture Using Cloud for Hashimoto's Thyroiditis Disease Classification
InactiveUS20120220875A1Low storage costStorage cost can be freeUltrasonic/sonic/infrasonic diagnosticsDiagnostic recording/measuringImage basedMobile architecture
Hashimoto's Thyroiditis (HT) is the most common type of inflammation of the thyroid gland and accurate diagnosis of HT would be advantageous in predicting thyroid failure. The application presents three tier architecture for image-based diagnosis and monitoring application using Cloud is described. The presentation layer is run on the tablet (mobile device), while the business and persistence layer runs on a single cloud or distributed on different Clouds in a multi-tenancy and multi-user application. Such architecture is used for automated data mining application for diagnosis of Hashimoto's Thyroiditis (HT) Disease using ultrasound.
Owner:SURI JASJIT S
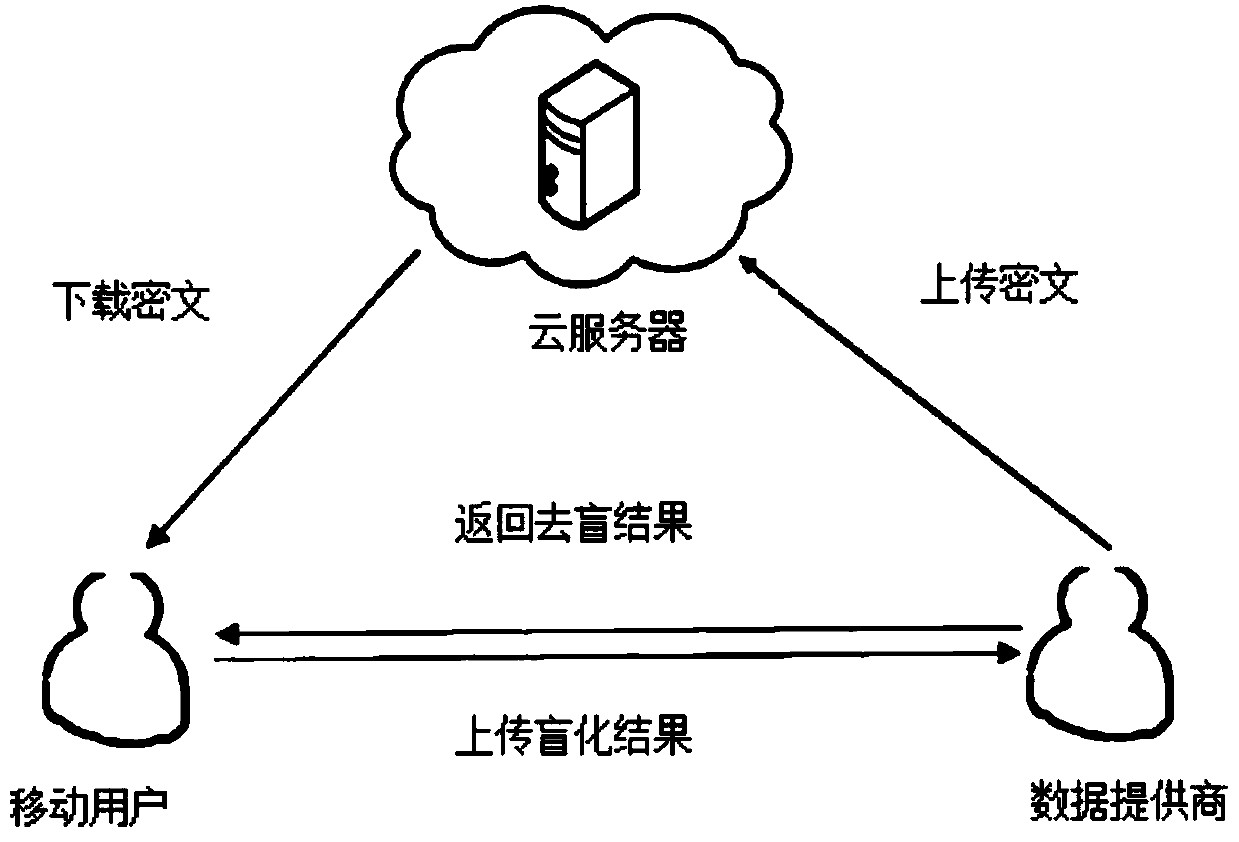
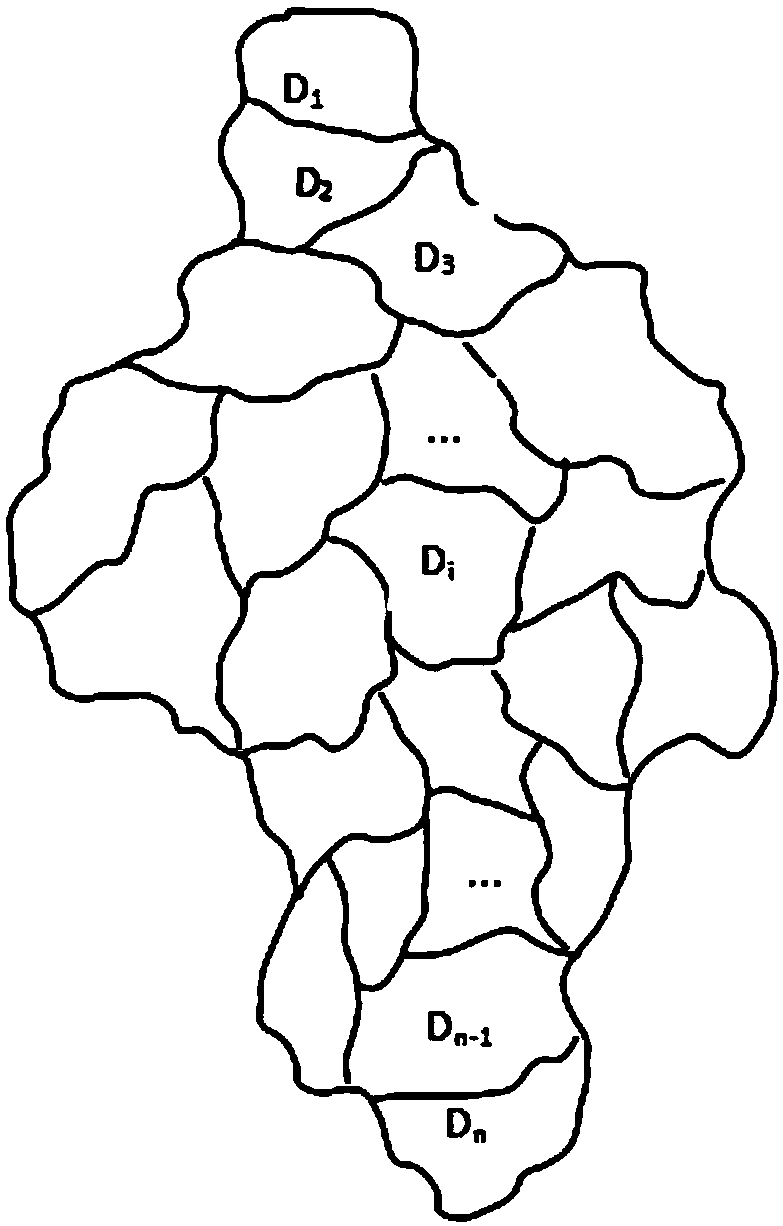
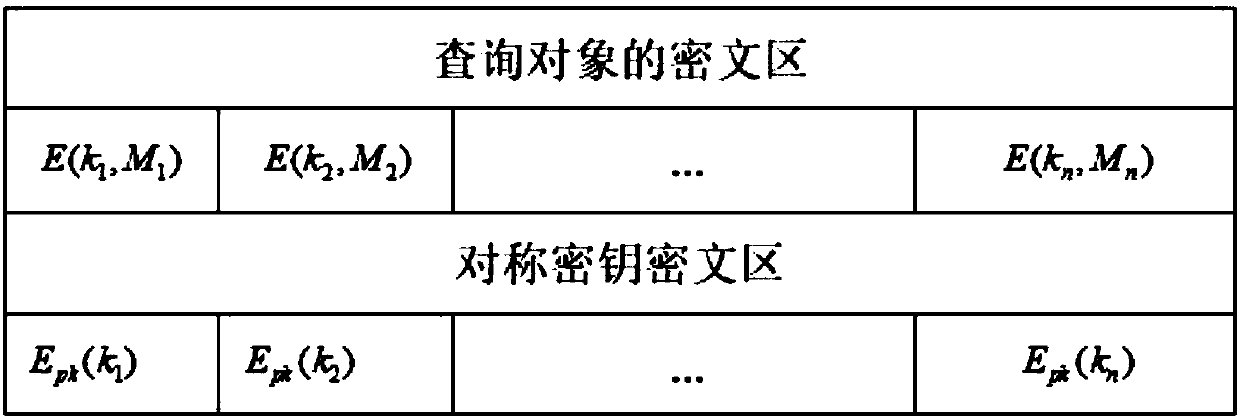
Homomorphic encryption-based position privacy querying method
ActiveCN107749865AGuaranteed privacyFast encryptionKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextCiphertext
A homomorphic encryption-based position privacy querying method disclosed by the present invention comprises a cloud server, a data service provider and a plurality of mobile users. The data service provider SP partitions the areas in a map according to the intensity of the querying objects, then encrypts the querying objects in the partitions via a symmetric encryption algorithm, and encrypts thesymmetric secret keys via a homomorphic encryption algorithm, and finally stores all ciphertexts in the cloud server, thereby secretly saving the private keys of the homomorphic encryption. Users download the ciphertexts of the querying objects and the corresponding symmetric secret key ciphertexts from the cloud server according to the own positions, and further carry out the blind processing onthe symmetric secret key ciphertexts and transmit to the data service provider, and the data service provider transmits the decrypted blind plaintexts to the users, and finally, users decrypt the corresponding querying objects to obtain the final query results. According to the present invention, the position information of the users is not leaked during the whole process, thereby protecting theposition privacy.
Owner:安徽迪科数金科技有限公司
Double-cold-source and multi-working-condition water cold storage system
InactiveCN106152341AOvercoming the single problem of cold storage and cold sourceOvercome singleLighting and heating apparatusAir conditioning systemsCooling towerFree cooling
The invention discloses a double-cold-source and multi-working-condition water cold storage system. According to the double-cold-source and multi-working-condition water cold storage system, a cooling tower, a refrigeration host and a cold storage tank arranged are arranged with an end load to form a circulation loop for supplying cold to the end load; the cooling tower and the refrigeration host are arranged with the cold storage tank to form a circulation loop; a cold source is stored in the cold storage tank, cold is supplied to the end load through the cold storage tank; the refrigeration host, the end load and the cold storage tank are arranged in a parallel manner, thus multi-mode cold supply and cold storage are realized as a whole; the cold storage can be carried out through the refrigeration host or natural cooling, thus the problem of a single cold source of cold storage of a traditional water cold storage system is overcome; and moreover, the cold storage is carried out through the natural cold source, thus the cold storage cost is low. The double-cold-source and multi-working-condition water cold storage system disclosed by the invention is suitable for the field of cold supply and cold storage air-conditioning systems.
Owner:GUANGZHOU TOPSUN POWER TECH
Hybrid spatial indexing mechanism for processing geographic text Skyline query
ActiveCN108052514ALow storage costImprove update efficiencySpecial data processing applicationsData setInformation data
The invention provides a hybrid spatial indexing mechanism for processing geographic text Skyline query, wherein geographic text Skyline query refers to performing Skyline query on a geographic text information dataset. Data points in the geographic text dataset include geographic position information and keyword text information. The Inverted-Merged R*-Tree (IMR*-T) integrates the R*tree and theInverted File thought, and the invention belongs to the query indexing field in computer science. The invention focuses on solution of the problem of storing the geographic text dataset and performingSkyline query on the geographic text dataset, can improve the Skyline query efficiency on the premise of ensuring reasonable storage. The invention constructs a multi-branch tree according to data point spatial position distribution by means of an R* tree construction strategy, and can construct an Inverted File for leaf nodes of the tree. To improve the clipping efficiency of the dataset, tree nodes store boundary frame information. The invention is widely suitable for relevant application scenarios of geographic text Skyline query.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
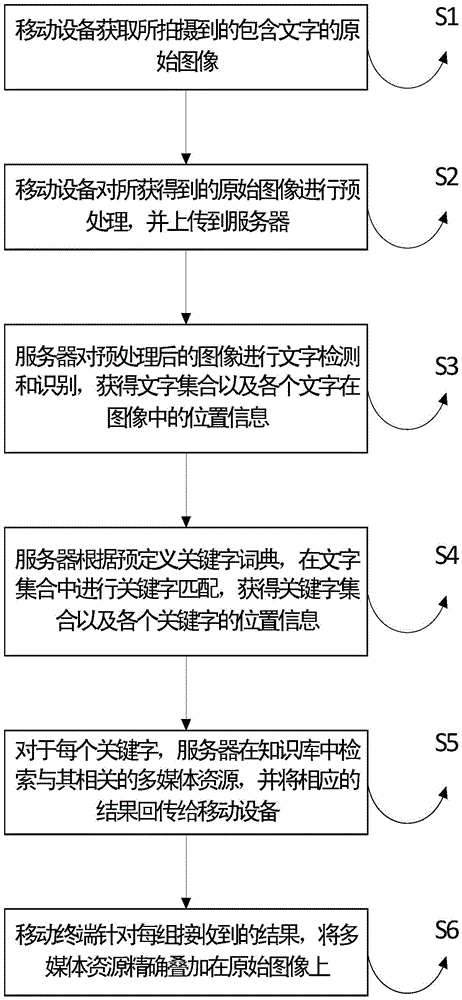
Character recognition based mobile augmented reality reading method and reading system thereof
InactiveCN105631051ARich reading materialMake up for the shortcomings of less information and poor interactivityWeb data indexingSemantic analysisThe InternetComputer terminal
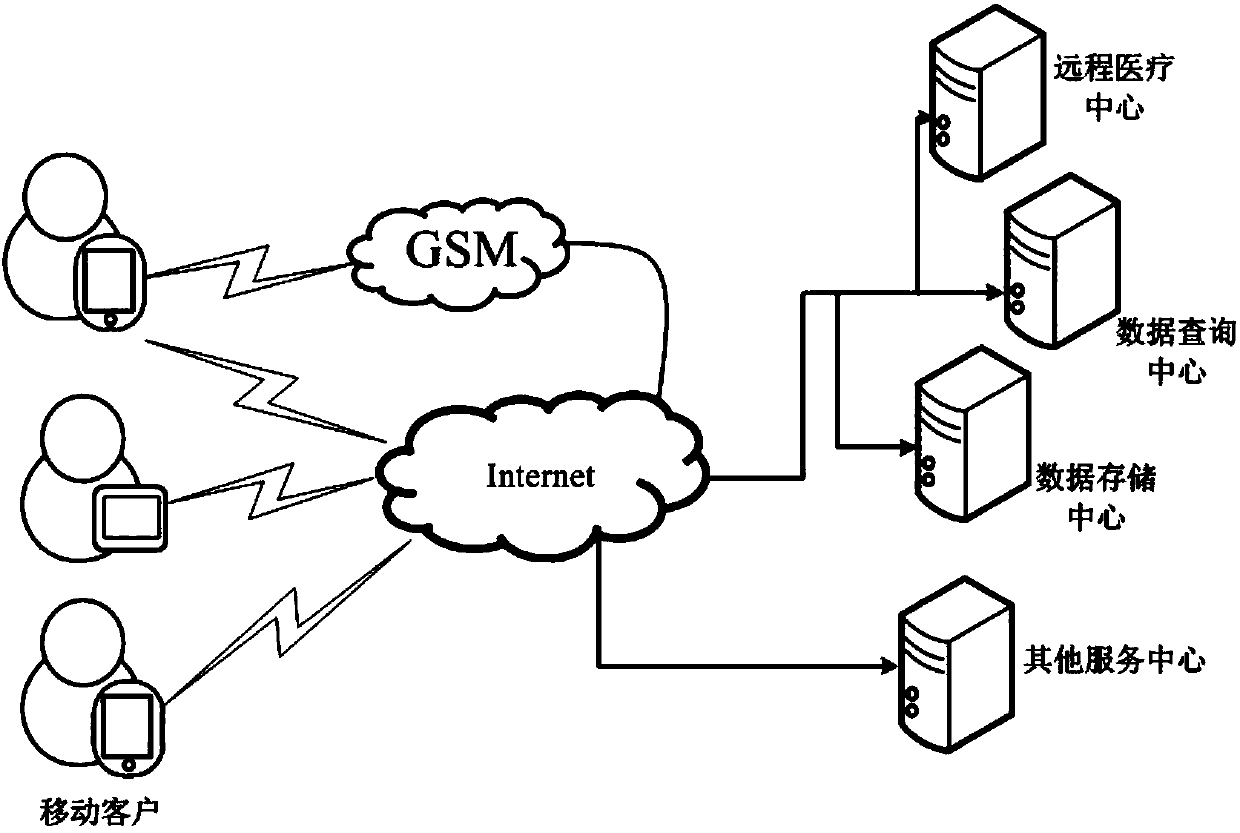
The invention discloses a character recognition based mobile augmented reality reading method.The method includes steps: 1, a mobile device acquires a shot original image containing characters; 2, the mobile device preprocesses the acquired original image and uploads to a server; 3, the server acquires a character set and position information of each character in the image; 4, the server acquires a keyword set and position information of each keyword; 5, the server searches multimedia resources related to each keyword and returns corresponding results to the mobile device; 6, aiming at each group of received results, the mobile terminal precisely overlays the multimedia resources onto the original image.The invention further discloses a reading system for implementation of the character recognition based mobile augmented reality reading method.The reading system comprises a mobile phone terminal and a server terminal, and the mobile phone terminal and the server terminal are in communication through the internet.The character recognition based mobile augmented reality reading method and the reading system have the advantages of low storage cost of the server and the like.
Owner:SOUTH CHINA UNIV OF TECH
Attribute-based encryption supporting flexible and direct-revocatory ciphertext policy
ActiveCN103297227AReduce the burden onReduce computational complexityKey distribution for secure communicationComputation complexityAttribute-based encryption
The invention discloses attribute-based encryption supporting flexible and direct-revocatory ciphertext policy. The encryption is characterized in that the encryption includes: (1) generating system public keys and main secret keys; (2) generating attributive secret keys; (3) encrypting to generate ciphertext; (4) generating and publishing public parameters by an attribute center; generating ciphertext updating secret keys and transmitting the ciphertext updating secret keys to cloud service providers through secure channels; (5) ciphertext updating procedure; (6) user decrypting procedure. The Attribute-based encryption supporting flexible and direct-revocatory ciphertext policy has the advantages that the size of ciphertext is constant, communication traffic is small, users do not need to update attribute, computation complexity and storage cost are low, users do not need to update secret keys every time, load of authority centers is greatly relieved and the like.
Owner:XIDIAN UNIV
Building outer surface wind pressure measurement method
ActiveCN104535254AIncreased safety marginTake full account of uncertaintyFluid pressure measurementRigid modelEngineering
The invention provides a building outer surface wind pressure measurement method. The method includes the steps that a rigid model is manufactured and pressure measurement points are set; a wind tunnel test is conducted on the rigid model in a single round, so that a point wind pressure coefficient independent peak value reserving sequence and a face average wind pressure coefficient independent peak value reserving sequence are acquired; maximum likelihood estimation is conducted on point scale parameters and point position parameters of the point wind pressure coefficient independent peak value reserving sequence and face scale parameters and face position parameters of the face average wind pressure coefficient independent peak value reserving sequence, so that the maximum design value and the minimum design value of point wind pressure coefficients and the maximum design value and the minimum design value of face average wind pressure coefficients are determined, wherein the point scale parameters, the point position parameters, the face scale parameters and the face position parameters submit to extreme value distribution; the most disadvantageous maximum design value and the most disadvantageous minimum design value of the point wind pressure coefficients and the most disadvantageous maximum design value and the most disadvantageous minimum design value of the face average wind pressure coefficients are determined; the wind pressure of the outer surface of a building is determined. The method has the advantages of being low in cost, high in safety and capable of being widely applied to the field of buildings.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Safety verification method, device and system based on non-interactive zero-knowledge
ActiveCN104717067AEnhanced anonymityAchieve traceabilityKey distribution for secure communicationUser identity/authority verificationNon-interactive zero-knowledge proofCentral node
The invention discloses a safety verification method, device and system based on non-interactive zero-knowledge, and relates to the field of electronic safety verification. The method includes the steps of public secret keys and private secret keys of a central node device and other local node devices; sending the identity (ID) and the identity commitment value of any local node device I to the central node device after the local node device I obtains the identity commitment value with the ID of the local node device I as the commitment object; sending certificate information to the local node device I through the central node device according to the private secret key of the central node device, the ID of the local node device I and the identity commitment value of the local node device I; establishing the non-interactive zero-knowledge proof based on the certificate commitment value after the local node device I obtains the certificate commitment value with the certificate information as the commitment object, and conducting signing on key information on service according to the non-interactive zero-knowledge proof, the public secret key of the local node device I and the private secret key of the local node device I; sending the key information on the signed service to a verification device through the local node device I.
Owner:LIAONING MOBILE COMM
Novel on-lattice MA-ABE (Multi-Authority Attribute Based Encryption) method based on LWE
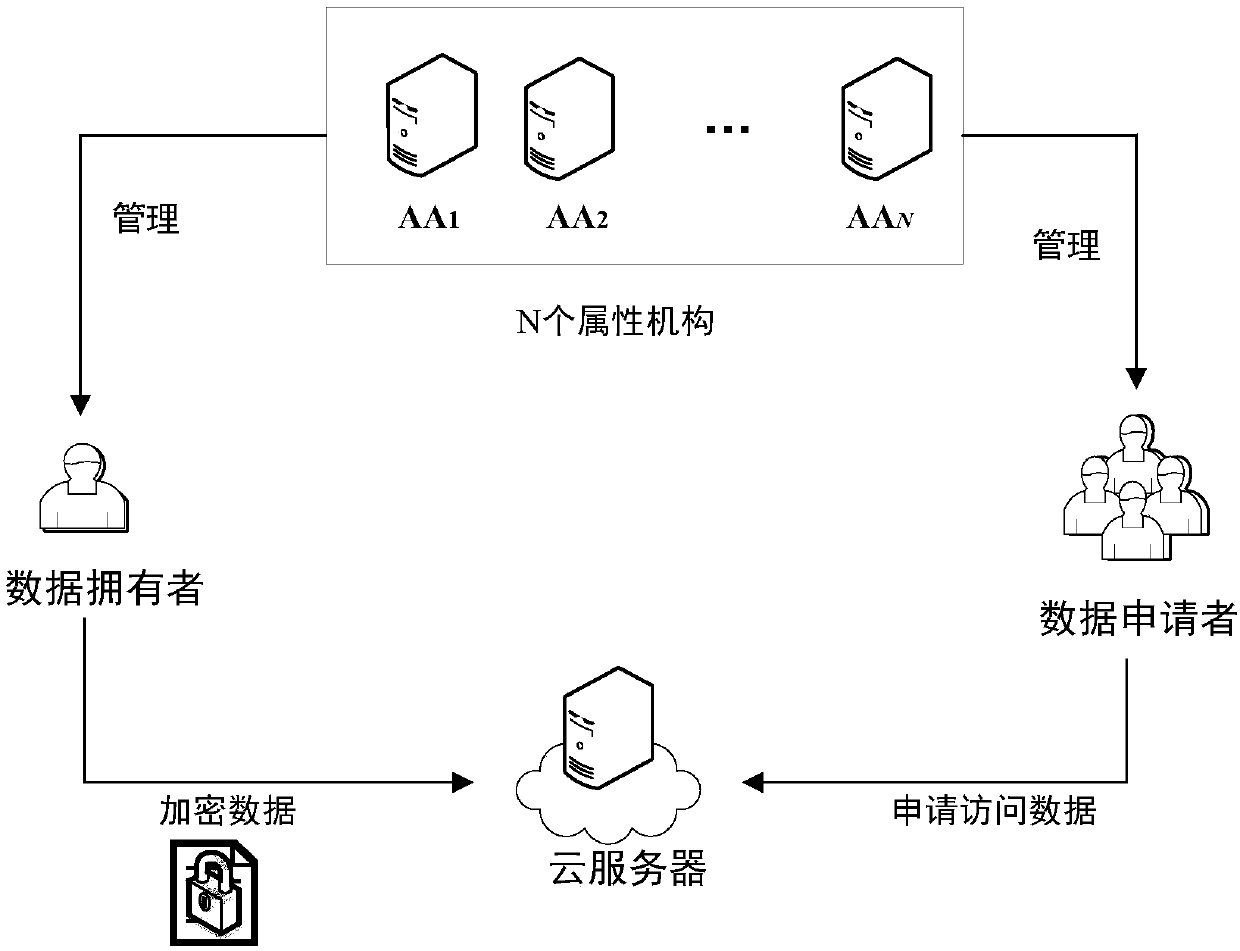
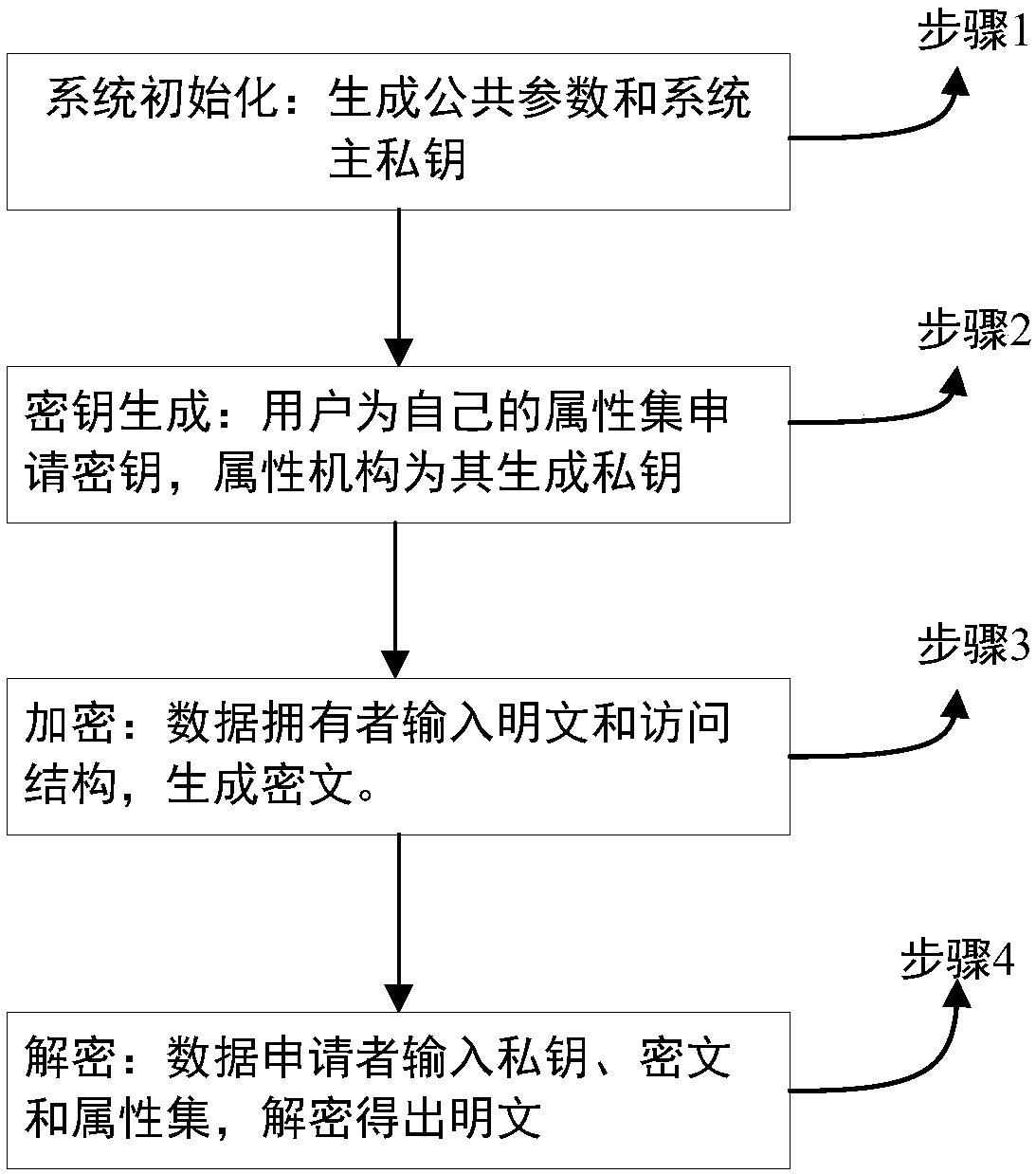
InactiveCN107682157AIncrease flexibilityLow storage costPublic key for secure communicationCryptographic attack countermeasuresLattice basisAttribute-based encryption
The invention discloses a novel on-lattice MA-ABE (Multi-Authority Attribute Based Encryption) method based on LWE, which comprises four steps of system initialization, secret key generation, encryption and decryption. According to the invention, a plurality of attribute mechanisms manage different attribute sets and respectively distribute secret keys to users in permissions of the attribute mechanisms so as to improve integral efficiency of a system when ensuring security; and meanwhile, a Shamir threshold secret sharing technology is applied, three operations of an access strategy, i.e., anAND operation, an OR operation and a threshold operation, are implemented by adopting an access tree structure, and flexibility is high. Moreover, according to the invention, bilinear pairing is replaced with a lattice principle, a lattice basis delegation algorithm without dimension growth is introduced, encryption and decryption speeds are improved, and storage cost of private keys and ciphertexts of users is reduced. The novel on-lattice MA-ABE method disclosed by the invention is comprehensive in consideration, perfect in function, optimal in system performance and can be better applied to a cloud storage environment.
Owner:HENAN POLYTECHNIC UNIV
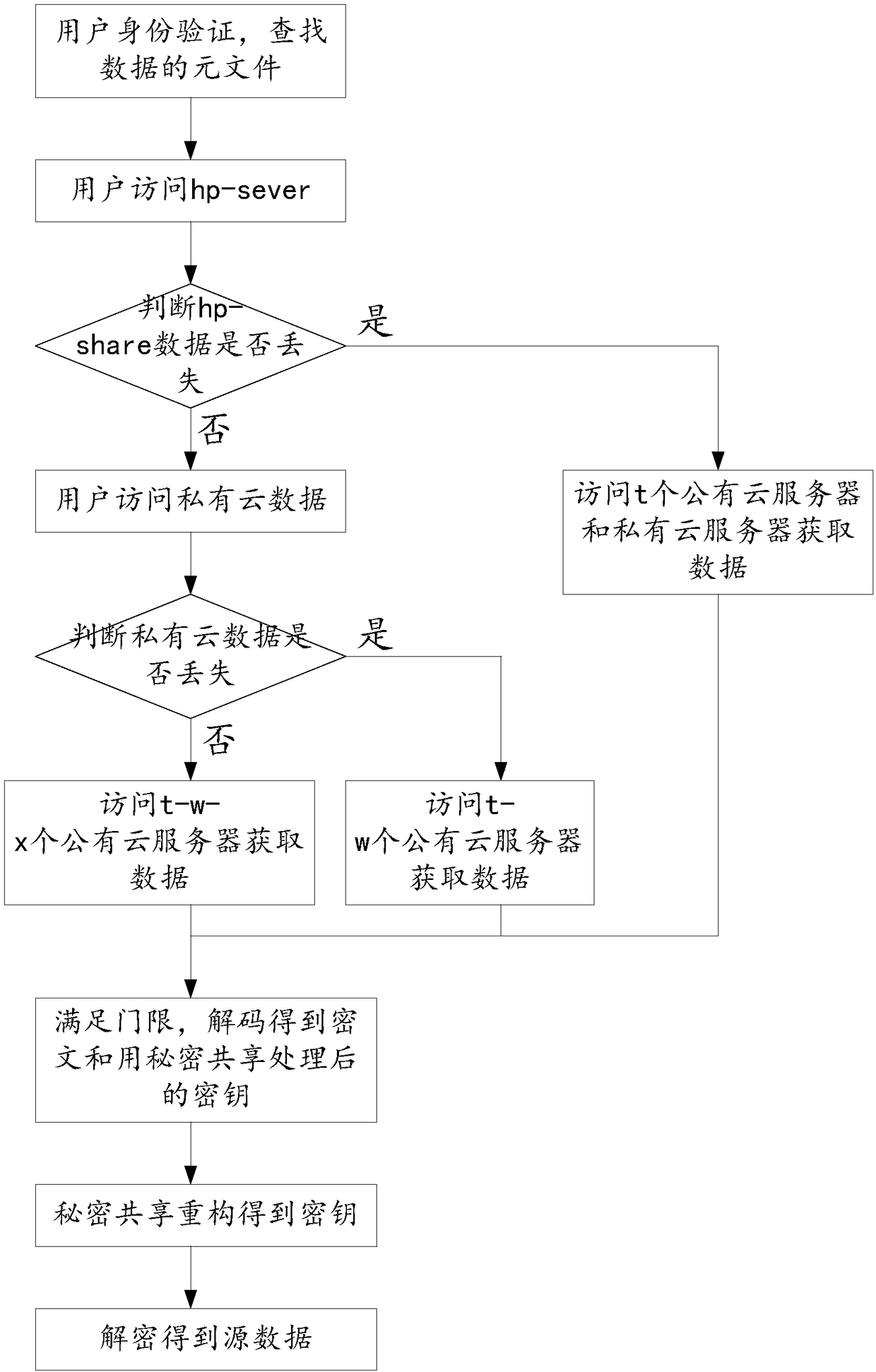
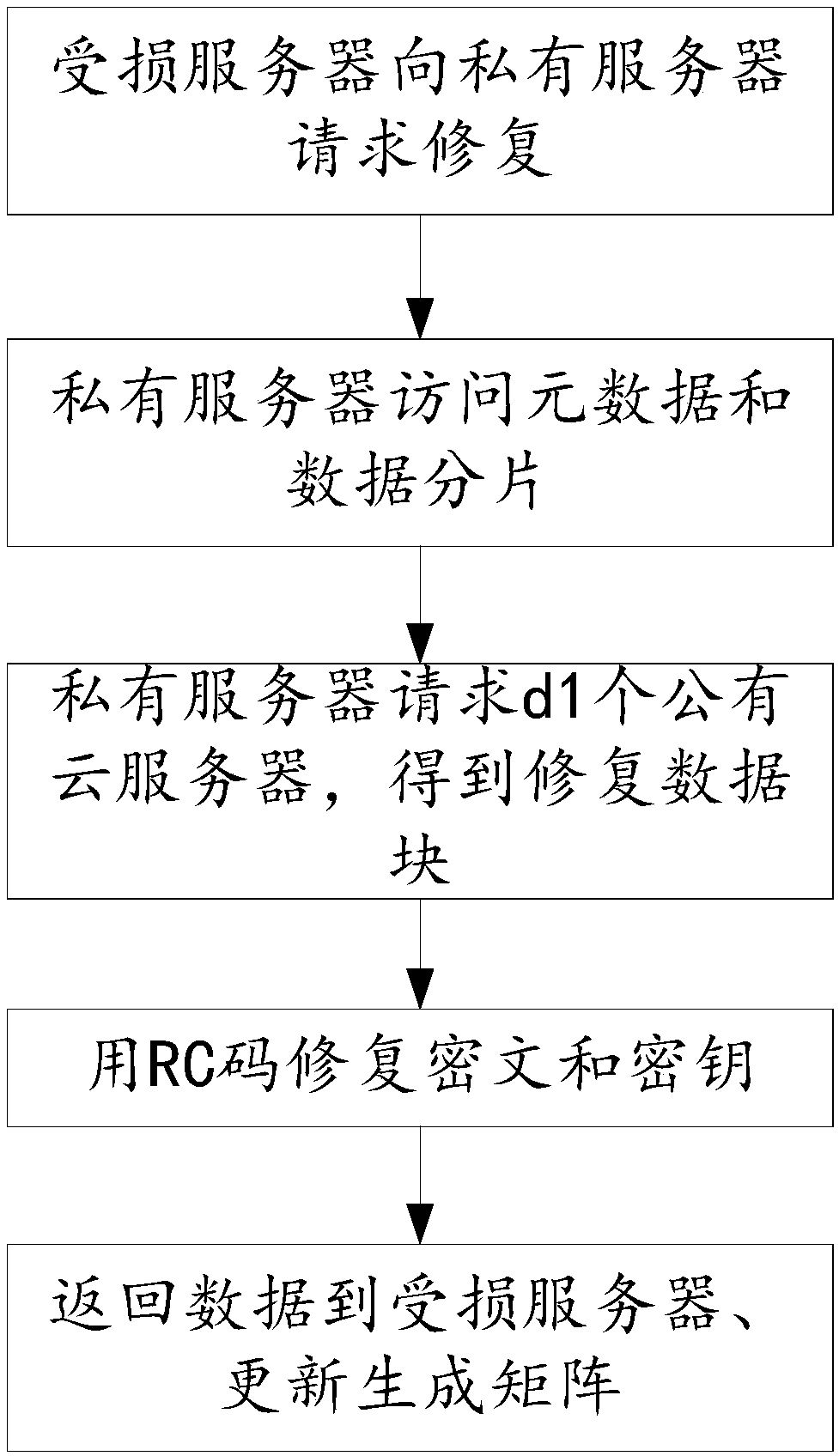
Method and system for safely distributing and repairing data in multi-cloud storage environment, and medium
ActiveCN108810063ASupport damage repairLow storage costTransmissionRedundant operation error correctionOriginal dataConfidentiality
The invention provides a method and system for safely distributing and repairing data in a multi-cloud storage environment, and a medium. The method comprises the following steps: a data distributionstep: distributing data information into a multi-cloud storage system; a data recovery step: when user data need to be accessed, adopting a data recovery technology to recover user original data according to obtained data fragments; and a data repair step: when certain public cloud data are damaged or inaccessible, using a data repair process to repair node data. The method for safely distributingand repairing the data in the multi-cloud storage environment provided by the invention has storage confidentiality, reliable redundancy, low storage cost, high repair security and low repair cost, and supports single-node damaged repair.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
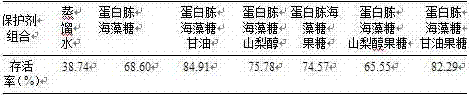
Preparation method capable of realizing aspergillus niger spore multiplication through carrier adsorption and producing xerospore powder of aspergillus niger
PendingCN107058209APromote proliferationGrow fastMicroorganism based processesOn/in organic carrierSporeAmylase
The invention discloses a preparation method capable of realizing aspergillus niger spore multiplication through carrier adsorption and producing xerospore powder of aspergillus niger. The preparation method comprises steps as follows: corn and bran are mixed in the ratio of 7:3, the corn and bran mixture and water are mixed in the ratio of the total weight of solids to the volume of water being 1:5, then, high-temperature-resistant amylase is added, the mixture is boiled at 100 DEG C for 30 min and filtered, and a culture solution of aspergillus niger spores is obtained. Crushed corncobs in the volume of 1 cm<3> is mixed with the culture solution of aspergillus niger in the weight-to-volume ratio being 1:3.5, and the mixture is put in a solid-state fermentation tank, sterilized at 121 DEG C for 20 min, cooled to 37 DEG C and inoculated with 104-105 CFU / mL aspergillus niger spores on the basis of the volume of the culture solution of aspergillus niger. The solid-state fermentation tank is kept at the temperature of 37 DEG C, the mixture is cultured for 120 h, a compound protectant is added after the aspergillus niger spores are diluted, the volume ratio of a spore suspension to the compound protectant is 2:3, the balancing time lasts for 40 min, vacuum drying is performed, and xerospore powder of aspergillus niger is collected. By means of the preparation method, the survival rate of aspergillus niger spore powder is increased, and the storage period of strains is prolonged. Meanwhile, a compound dryer adding method consumes little energy, and the preparation method adopts a simple process and is low in cost and more suitable for large-scale production.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
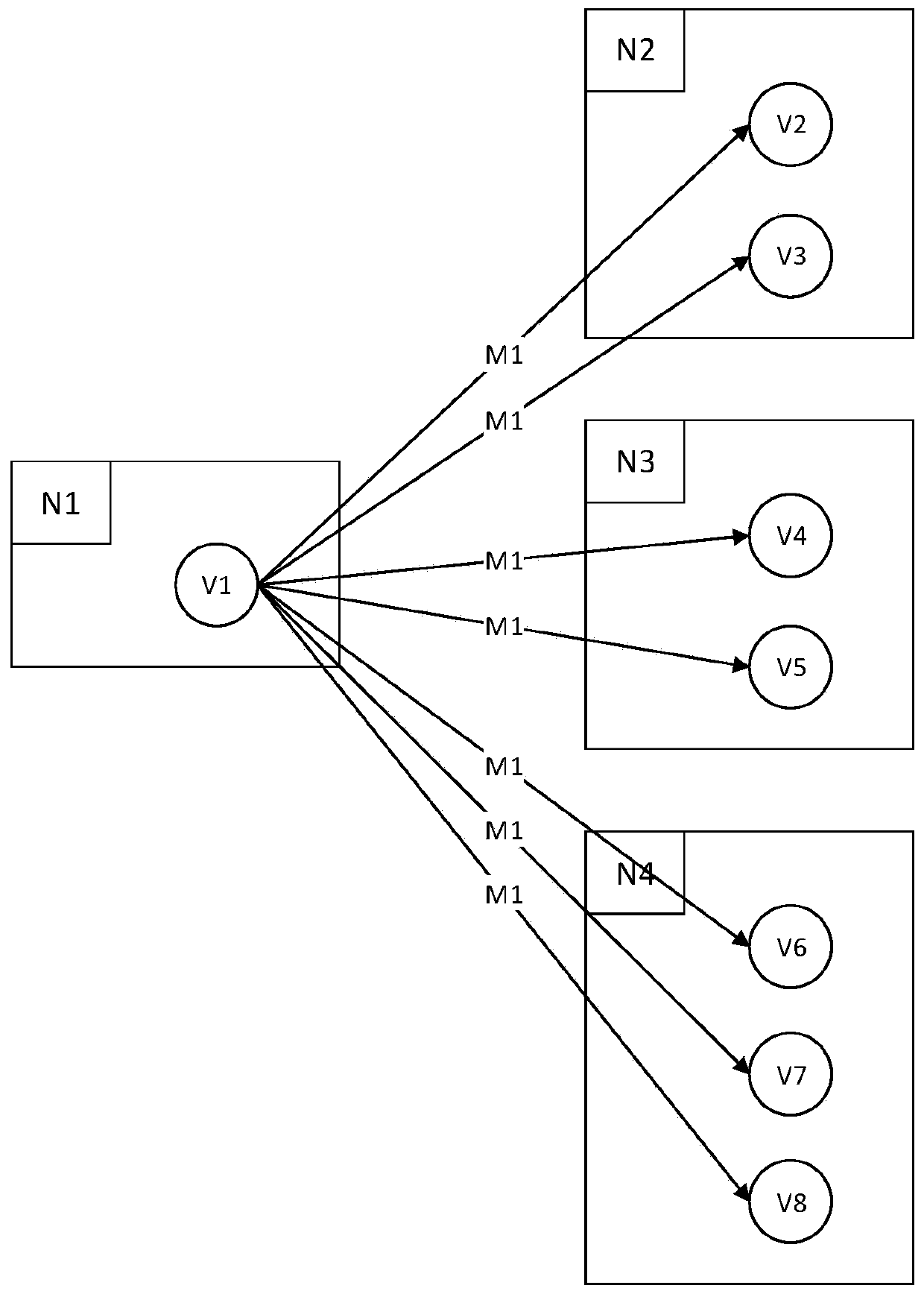
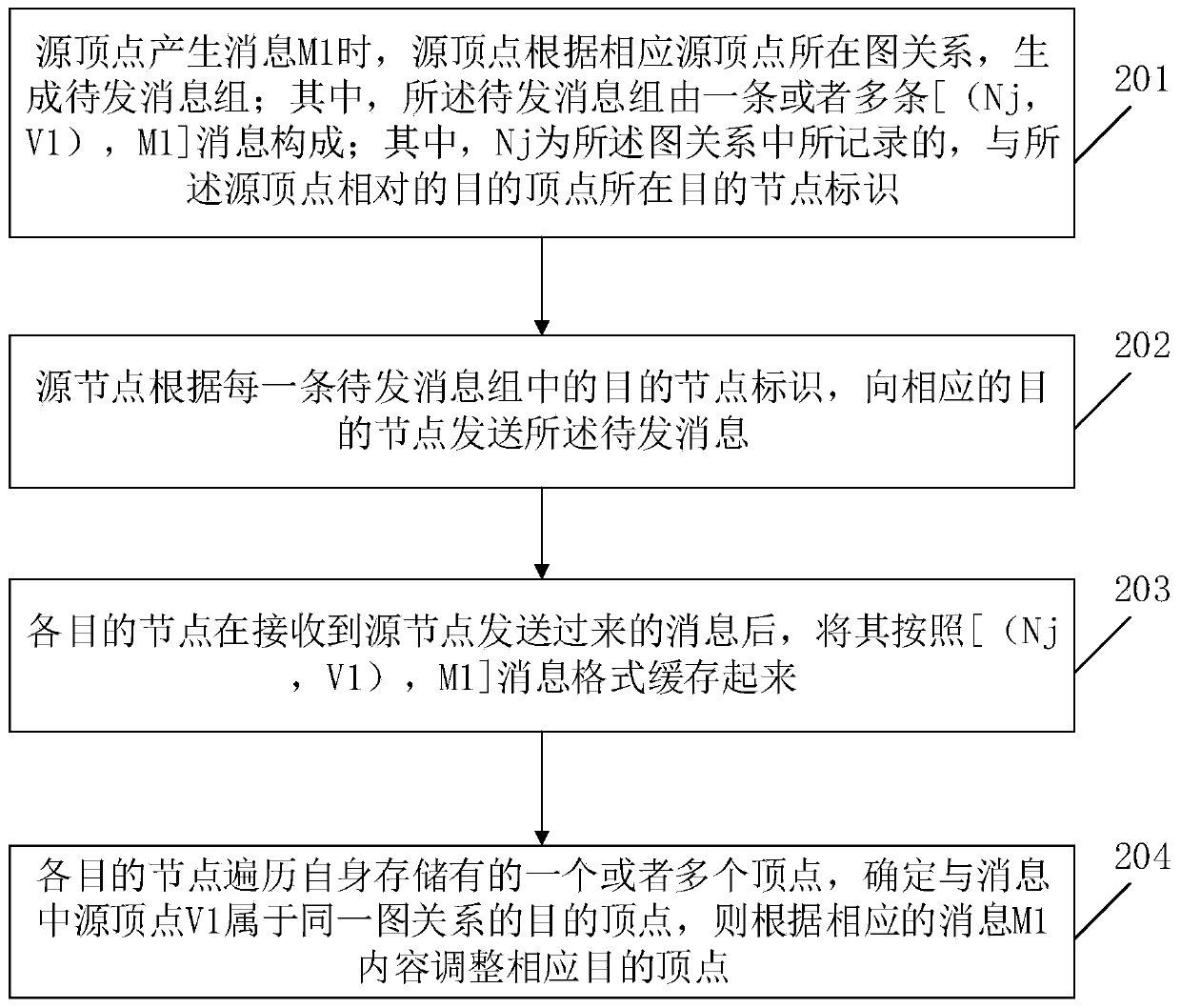
Message passing method and device in distributed graph calculation process
ActiveCN111177486AReduce communication costLow storage costInterprogram communicationOther databases indexingMessage deliveryEngineering
The invention relates to the technical field of distributed graph calculation, and provides a message transmission method and device in a distributed graph calculation process. The method comprises the steps that when a source vertex generates a message M1, the source vertex generates a to-be-sent message group according to a graph relationship where the corresponding source vertex is located; thesource node sends the to-be-sent message to a corresponding destination node according to the destination node identifier in each to-be-sent message group; after receiving the message sent by the source node, each destination node caches the message according to a message format; and each destination node traverses one or more vertexes stored in the destination node, determines the destination vertex belonging to the same graph relationship with the source vertex V1 in the message, and adjusts the corresponding destination vertex according to the content of the corresponding message M1. According to the invention, the number of messages which need to be transmitted across nodes and stored is irrelevant to the number of destination vertexes and is only positively relevant to the number ofdestination nodes, so that the communication cost of message transmission and the storage cost of message caching are greatly reduced.
Owner:四川蜀天梦图数据科技有限公司 +1
IP fast rerouting method for improving inter-domain routing OSPF algorithm
ActiveCN101695053AEnsure correct forwardingReduce the number of addressingData switching networksRouting tableNetwork packet
An IP fast rerouting method for improving inter-domain routing OSPF algorithm includes following steps: (a) utilizing an OSPF algorithm to calculate normal routing and guide a normal routing table, (b) utilizing an ED-NotVia algorithm to find an NotVia address and generating an NotVia transfer table according to the NotVia address, (c) packing a raw packet via the NotVia address by a failure upstream node when fault is caused and does not complete convergence, and redirecting to a next hop of a fault point, (d), matching with a protection source to realize transfer of an NotVia packet when another router receives the NotVia packet, and (e), unpacking the NotVia packet when the NotVia packet achieves the next hop of the fault point, recovering the NotVia packet into a raw packet, and then transferring the raw packet into an original destination address through normal routing. ED-NotVia proposes to combine 'removing useless NotVia addresses' with 'unpacking in advance' for the first time. The method has the advantages of simple implementation, low cost, optimum protection path without unpacking bottle-neck and the like, and is adaptable to improving properties of inter-domain routing of a large-scale autonomous system in failure.
Owner:TSINGHUA UNIV
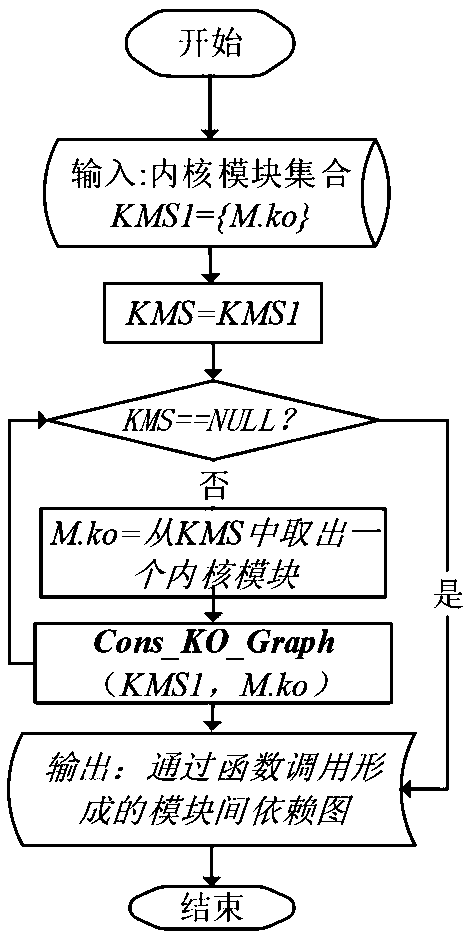
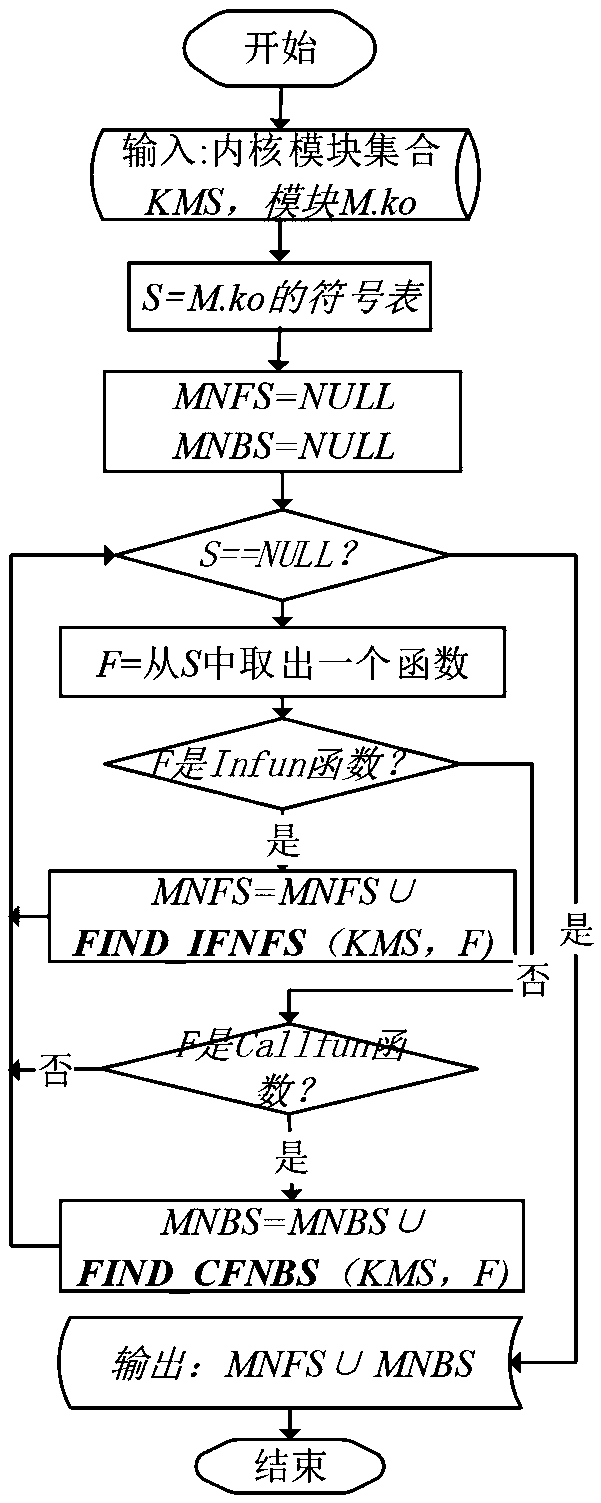
Kernel module compatibility influence domain analysis method and system based on function dependence graph, and medium
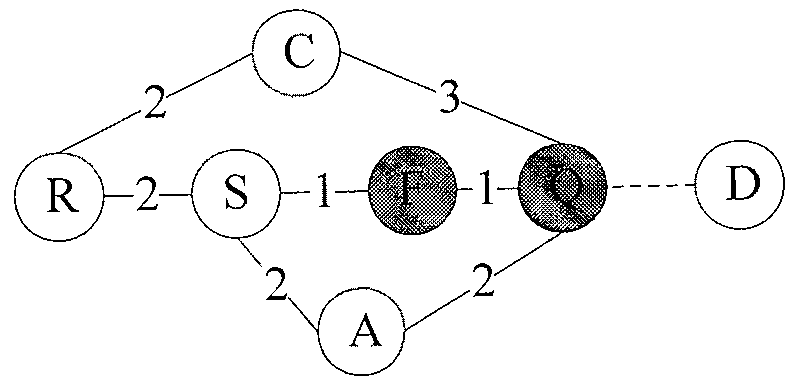
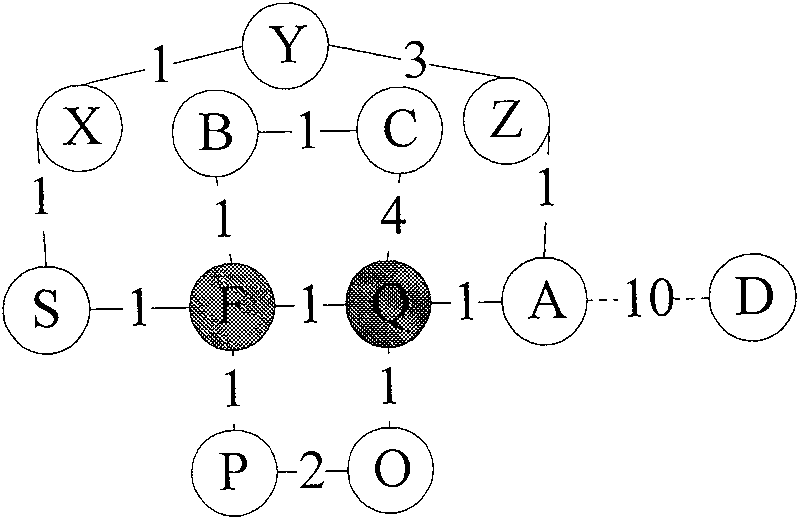
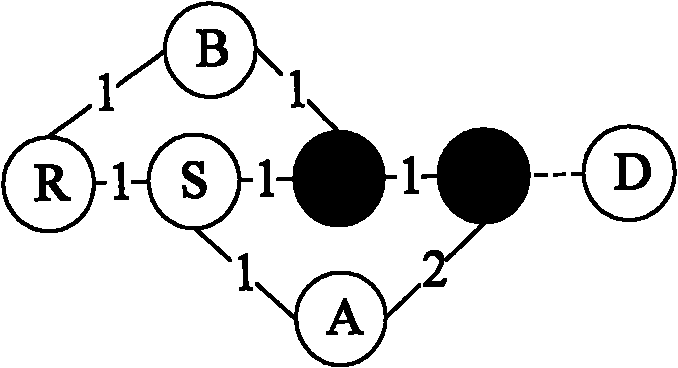
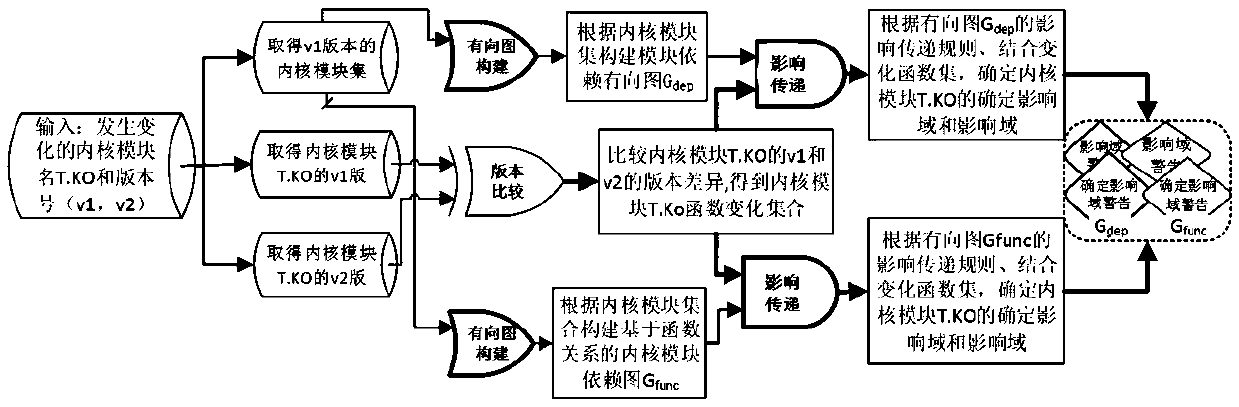
ActiveCN111008152AGuaranteed CompatibilityLow storage costReverse engineeringSoftware testing/debuggingDirected graphAlgorithm
The invention discloses a kernel module compatibility influence domain analysis method and system based on a function dependency graph, and a medium. The method comprises the steps of constructing a kernel module dependency directed graph according to a function call relationship between a kernel and a kernel module; after a certain kernel module version is upgraded, comparing function differencesbetween versions before and after kernel upgrading, and determining a changed kernel module interface function set; and radiating kernel interface function changes to a kernel module set related to the kernel interface function changes in the directed graph along the kernel module depending on the directed graph so as to determine a kernel module compatibility influence domain, and sending out acompatibility early warning according to the difficulty degree solved by the compatibility problem. According to the method and the system, version compatibility detection can be realized for the determined influence domains and influence domains among different versions of the kernel modules, and the method and the system can be used for ensuring self-consistency and compatibility early warning among the kernel modules, and have the advantages of low calculation and storage cost and high detection accuracy.
Owner:NAT UNIV OF DEFENSE TECH
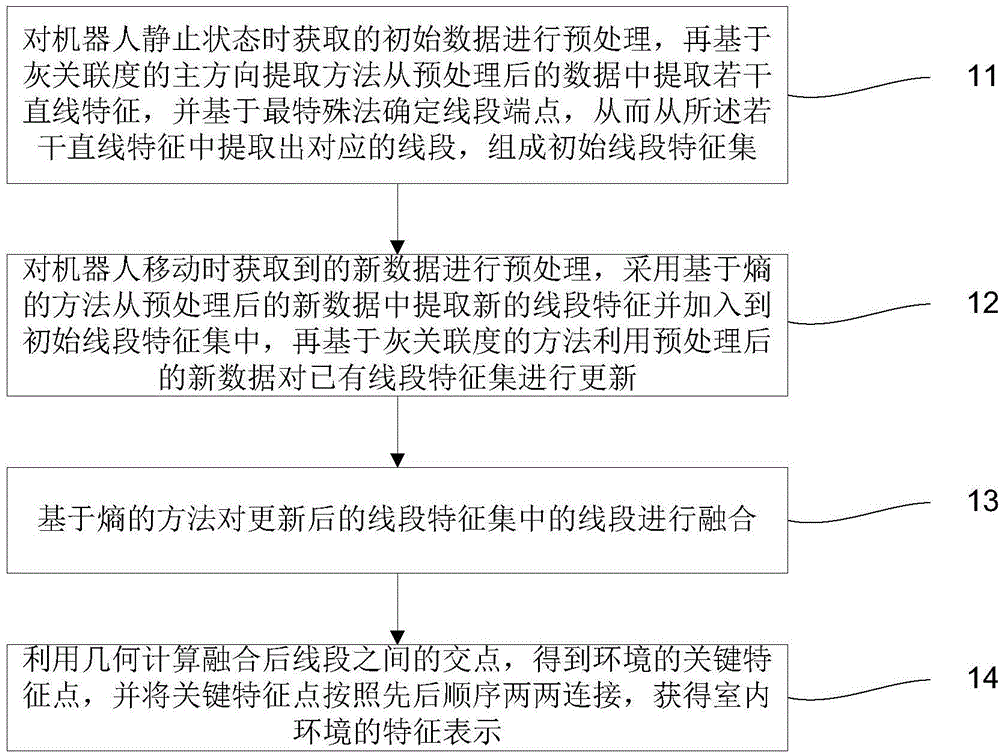
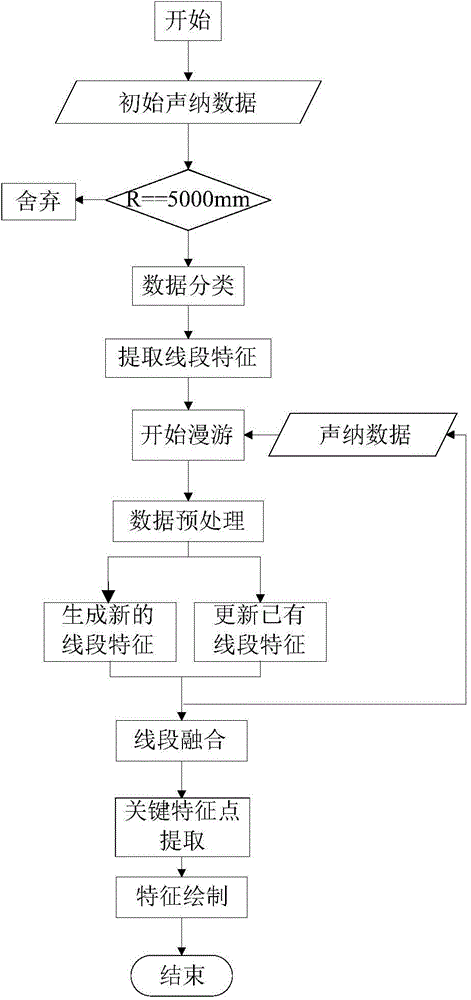
Indoor environment feature extraction method based on entropy and gray correlation degree
ActiveCN104793492ALow storage costImprove real-time performanceAdaptive controlFeature extractionCognition
The invention discloses an indoor environment feature extraction method based on entropy and gray correlation degree. The indoor environment feature extraction method includes that related technology in an information theory is utilized to complete gradual cognition of environment through a knowledge processing method simulating human processing environment information; environment feature extraction is realized by utilizing entropy and gray correlation degree, calculation and information storage cost is reduced to greatest extend, and data processing robustness is improved; environment features are updated through entropy when a robot wanders, so that instantaneity and accuracy of sonar data processing are improved; indoor environment feature extraction based on entropy and gray correlation degree can be effectively used in moving robot positioning, map building and path planning, so that accuracy and robustness of robot navigation tasks are improved.
Owner:UNIV OF SCI & TECH OF CHINA
Circuit for parallelly encoding quasi-cyclic low-density parity check code
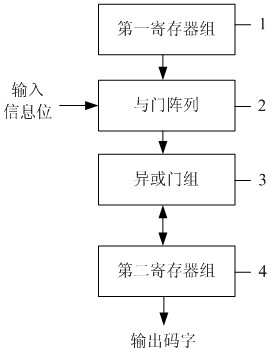
InactiveCN102130694AUnrestricted rank and dimensionHigh speedError correction/detection using multiple parity bitsProcessor registerParallel encoding
The invention discloses a circuit for parallelly encoding a quasi-cyclic low-density parity check code. The circuit comprises one or more encoding circuit units; each of the encoding circuit units comprises a first register group 1, an AND-gate array 2, an exclusive or (XOR) gate group 3 and a second register group 4; both the first register group and the second register group consist of L registers according to a dimension L of a cyclic permutation matrix; the XOR gate group consists of L XOR gates according to the dimension L of the cyclic permutation matrix; the output end of the first register group is connected with the input end of the AND-gate array; the output end of the AND-gate array is connected with the input end of the XOR gate group; the output end of the XOR gate group is connected with the input end of the second register group; and the output end of the second register group is connected with the input end of the XOR gate group. By the circuit for parallelly encoding the quasi-cyclic low-density parity check code, the parallel encoding of the quasi-cyclic low-density parity check code is realized; the encoding complexity is low and the encoding speed is high; the sequence and the dimension of the cyclic permutation matrix cannot be restrained, so a parallel factor is not restrained; therefore, the circuit has the advantages of high flexibility and small area.
Owner:ZHEJIANG UNIV
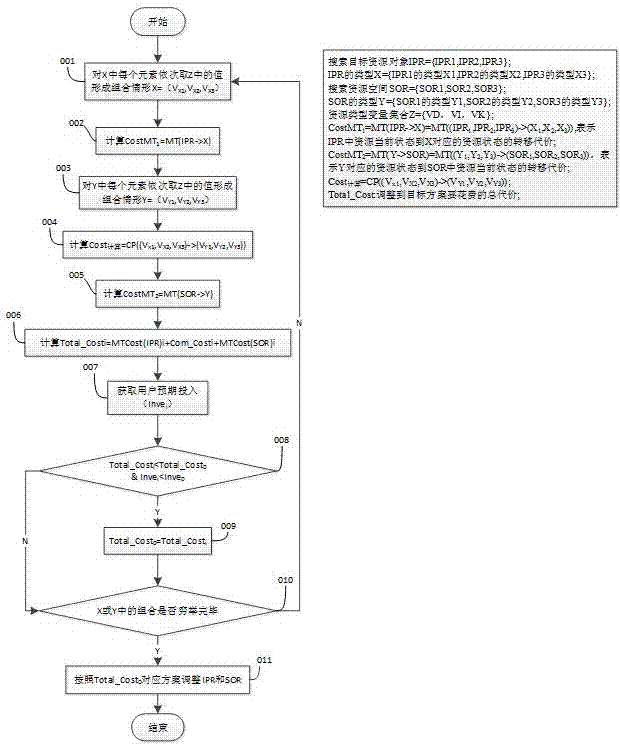
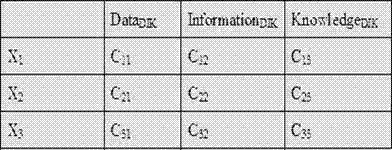
Transaction processing optimization method of input-driven storage and computing integration for typed resources
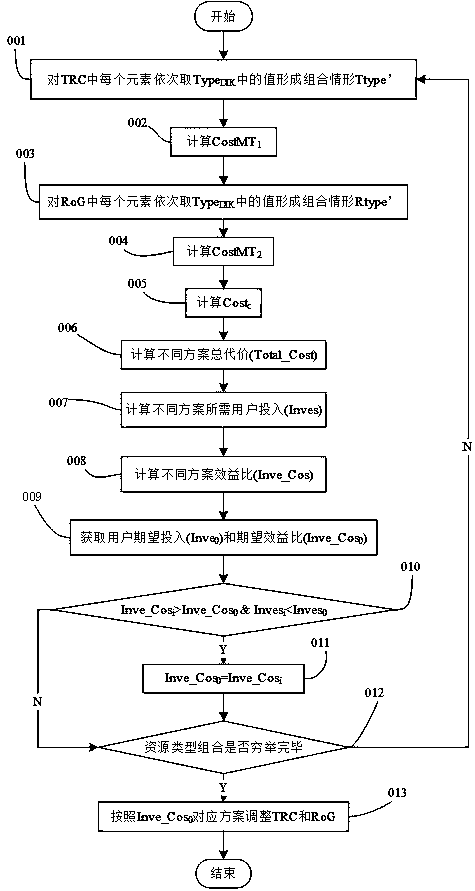
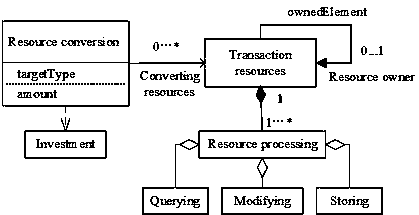
InactiveCN107330129AExpress interactionExpress collaborationSpecial data processing applicationsUser inputDistributed computing
The invention discloses a transaction processing optimization method of input-driven storage and computing integration for typed resources, gives out resource sources including explanation of data, information, knowledge and the like and concept representation of data mapping, information mapping and knowledge mapping and belongs to the field of intersection of distributed computing and software engineering technology. The storage lies in that a scheme is collaboratively adjusted by computing, storage is determined by computing, storage serves search, the scheme finding out resource type transfer cost and computing cost with the most reasonable cost according to user input, a resource object processing mechanism and a resource space organization scheme are determined reasonably, and spatial and temporal efficiency in transaction resource processing is optimized.
Owner:HAINAN UNIVERSITY
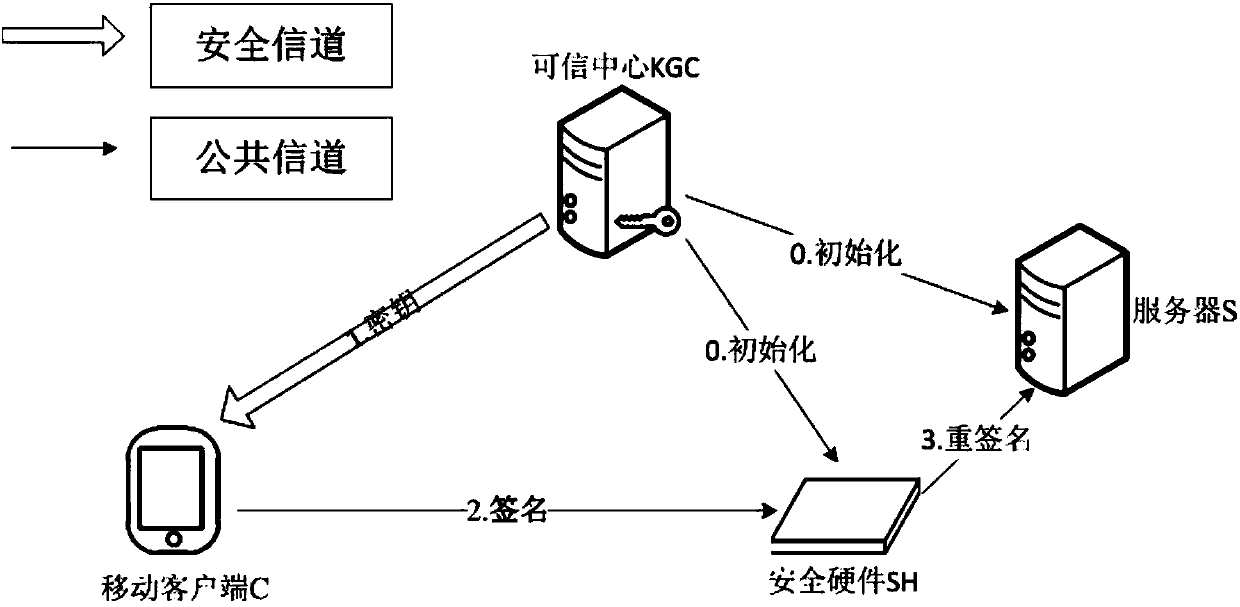
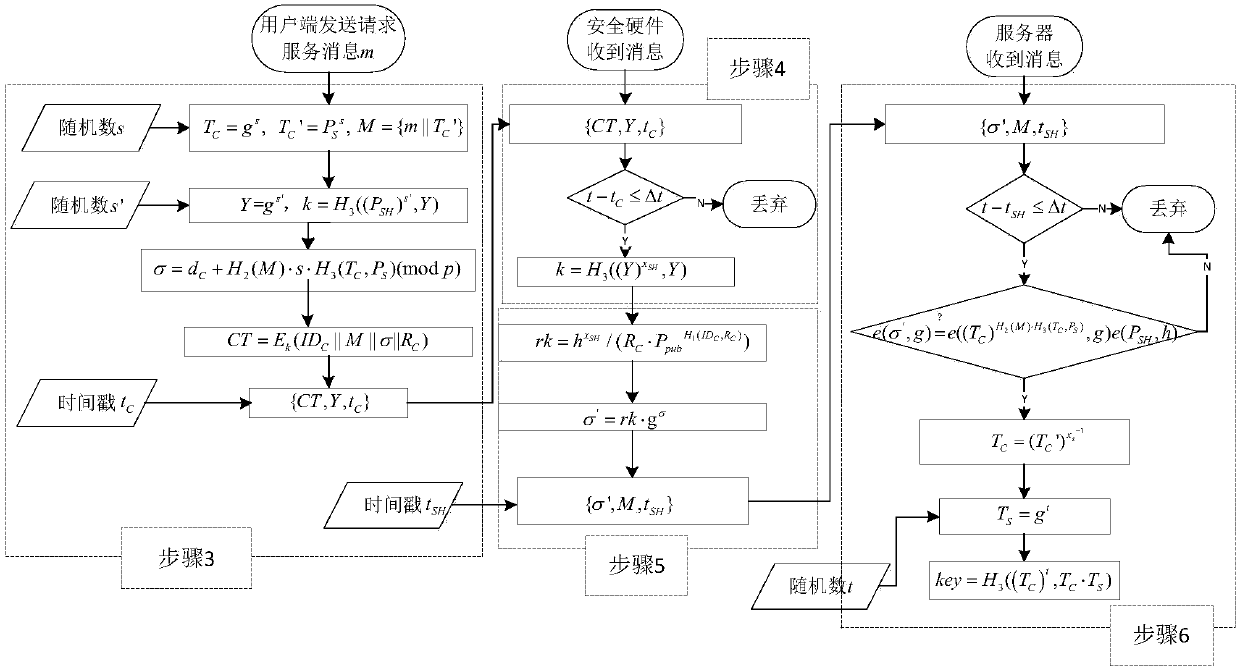
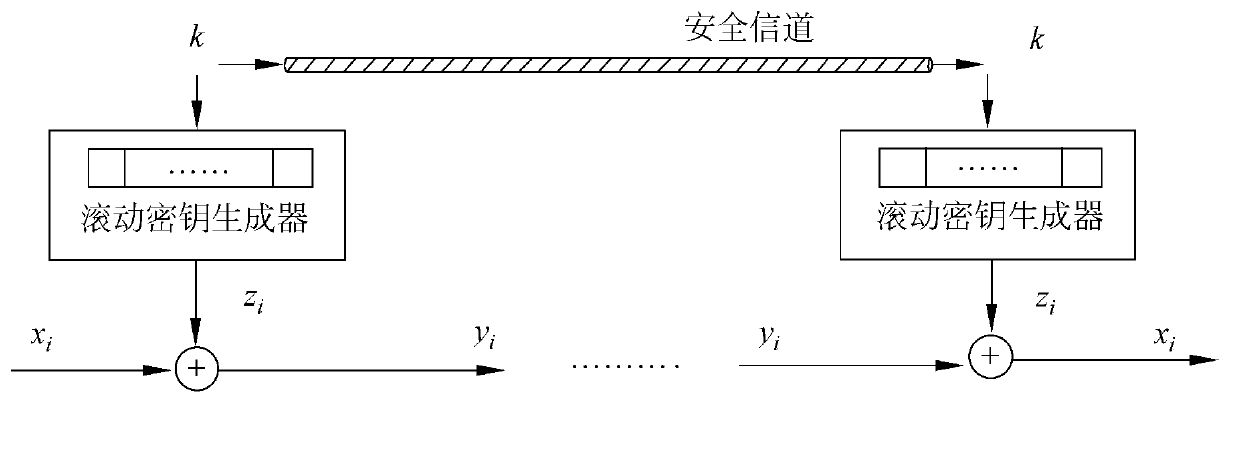
Anonymous authentication method based on security hardware
The invention discloses an anonymous authentication method based on security hardware. The method is characterized in that the method is applied to an internet environment that consists of a trusted center, a plurality of mobile clients and a plurality of application servers. The method comprises the following steps: 1, the trusted center generates system parameters as well as private keys and public keys of all participants; 2, any of the mobile clients generates a signature; 3, the mobile clients generate keys and ciphertexts; 4, the security hardware decrypts with the keys and resigns the signatures; 5, the application servers authenticate the re-signatures, generate authentication codes, and send the authentication codes to the mobile clients; and 6, the mobile clients authenticate the authentication codes and obtain subsequent services from the application servers. By adopting the anonymous authentication method disclosed by the invention, the problem of high storage cost and calculation cost and low authentication efficiency in an anonymous authentication process of the clients in an existing mobile network can be effectively solved, and meanwhile, the privacy of the clients and the security of the application servers can be increased.
Owner:ANHUI UNIVERSITY
Method for encrypting four non-linear driven light-weight stream ciphers
ActiveCN103166753AEasy to implement internal operationAchieve scrambling effectKey distribution for secure communicationDiffusionComputer hardware
The invention discloses a method for encrypting four non-linear driven light-weight stream ciphers. Bit oriented exclusive OR and AND operation is adopted for operation, and internal operation is easy to realize; initialized internal vectors are subjected to multiple loops of bit mixing scrambling operation by using the multi-loop iterative algorithm of block ciphers, so that a scrambling effect can be quickly achieved; the effects of mixing and diffusing seed key bits can be quickly achieved by newly introducing partitioning alternative diffusion and multi-layer mixing technologies; four selected non-linear driven components have the stable cryptographic properties to resist multiple kinds of attacks; a biquadratic item is newly introduced at the key generation stage for non-linear scrambling, so that the conventional internal state recovery attack can be effectively resisted; a seed key has the length of 88 bits to ensure high safety intensity; the algorithm is simple, software and hardware can be easily implemented in parallel, and the method is particularly suitable to be used under the environment that resources are limited, such as a wireless sensor network; and the storage cost for implementation is low.
Owner:GUILIN UNIV OF ELECTRONIC TECH
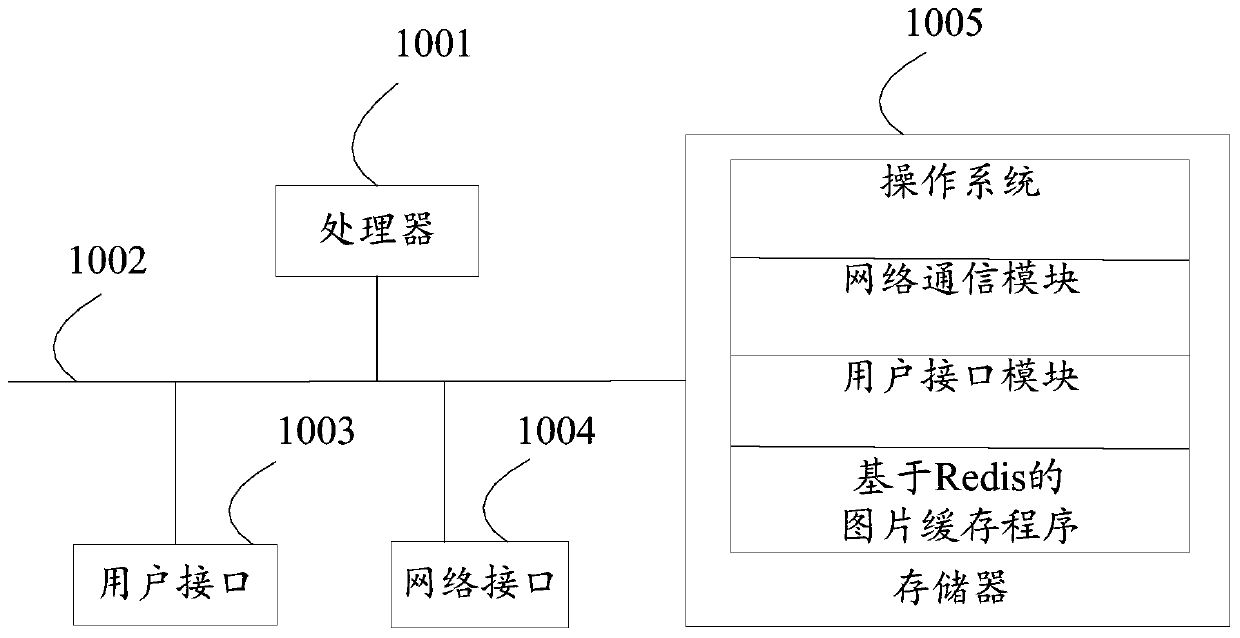
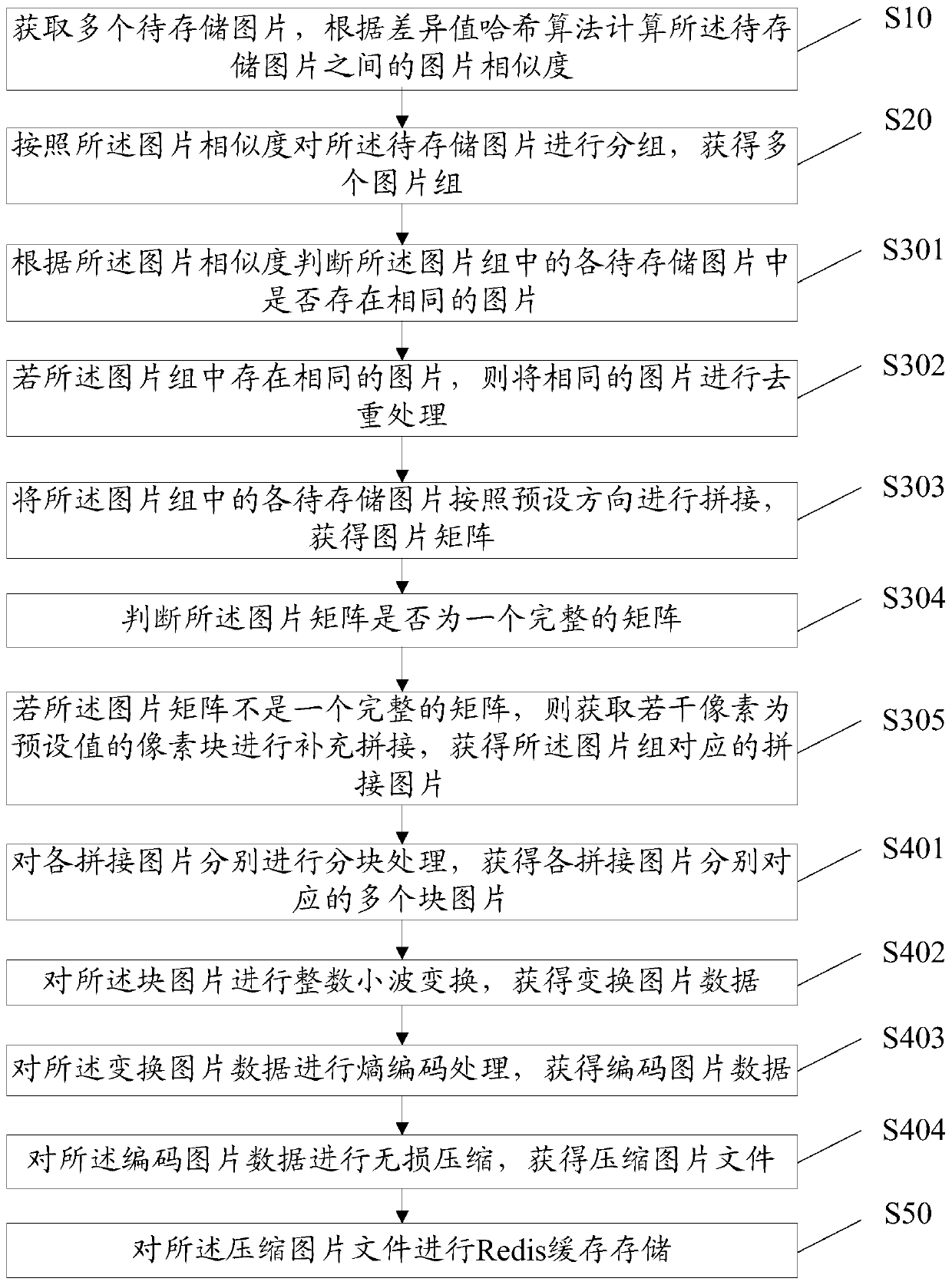
Redis-based picture caching method, device, storage medium and equipment
InactiveCN110399511AReduce duplicate compressed storageReduce compression costsImage enhancementImage analysisLossless compressionComputer graphics (images)
The invention discloses a Redis-based picture caching method, a Redis-based picture caching device, a storage medium and equipment. The method comprises the steps: obtaining a plurality of to-be-stored pictures, and calculating the picture similarity among the to-be-stored pictures according to a difference value hash algorithm; grouping the pictures to be stored according to the picture similarity to obtain a plurality of picture groups; splicing the pictures to be stored in the picture group to obtain spliced pictures corresponding to the picture group; performing lossless compression on each spliced picture to obtain a compressed picture file; and performing Redis cache storage on the compressed picture file. According to the method, grouping processing is carried out on the pictures according to the picture similarity. The lossless compression is carried out on the pictures. Therefore, the repeated expression of pixel blocks is reduced, and the storage cost is reduced.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
Query result size estimation method
ActiveCN104731889AImprove estimation accuracyTakes up little storage spaceSpecial data processing applicationsDatabase design/maintainanceTruth valueOriginal data
The invention discloses a query result size estimation method, and belongs to the technical field of database management. The method includes the steps of firstly, establishing the one-to-one mapping relation between data object identification and a Boolean matrix element; secondly, establishing the structure of a data record model used for object query counting, and an algorithm of the data record model structure, wherein when a certain object exists, a matrix element, corresponding to a Boolean matrix represented by the data record model, of the object identification is marked as 1, and otherwise the matrix element is marked as 0; thirdly, reading in original data and inserting corresponding records into the data record model, and meanwhile renewing the total number of counted truth-value elements in each line in the data record data; fourthly, converting the range of the queried data identification into the line range of the Boolean matrix, accumulating the total truth-value elements of the matrix lines within the query range, and obtaining the estimated value of the query result size.
Owner:HOHAI UNIV
Maintenance equipment site selection and inventory method and system under multistage supply chain and inventory warehouse
ActiveCN112288138ASite selection cost is smallLow costForecastingArtificial lifeLocal optimumApproximation algorithm
The invention belongs to the technical field of maintenance equipment inventory data processing, and discloses a maintenance equipment site selection and inventory method under a multi-stage supply chain and an inventory warehouse, and the method comprises the steps of carrying out the optimization and updating of a constructed warehouse site selection and inventory collaborative optimization system of maintenance equipment under the multi-stage supply chain through employing a hybrid fruit fly optimization algorithm; and determining the opening position of the base warehouse, assigning a maintenance point to the base warehouse, and making an inventory control decision, so that the sum of the base warehouse site selection cost, the ordering cost and the storage cost is minimum. According to the invention, the opening position of the base warehouse can be determined, and the sum of the site selection cost, the ordering cost and the storage cost is minimized through the assignment from the maintenance point to the base warehouse and the inventory control decision. According to the invention, the JRD model structure based on the RAND approximation algorithm is derived and arranged again, so that the HFOA algorithm is designed to be very suitable for solving the model, the algorithm is not prone to falling into local optimum and is stable in convergence, and the invention has higher solving efficiency for the large-scale site selection inventory problem.
Owner:XIDIAN UNIV
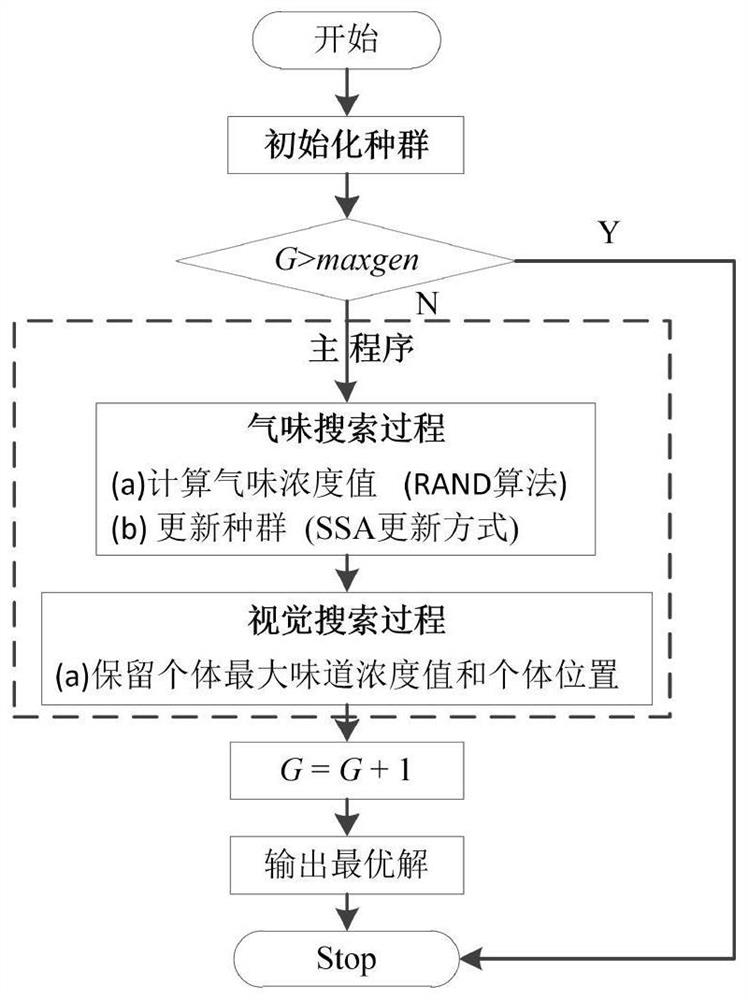
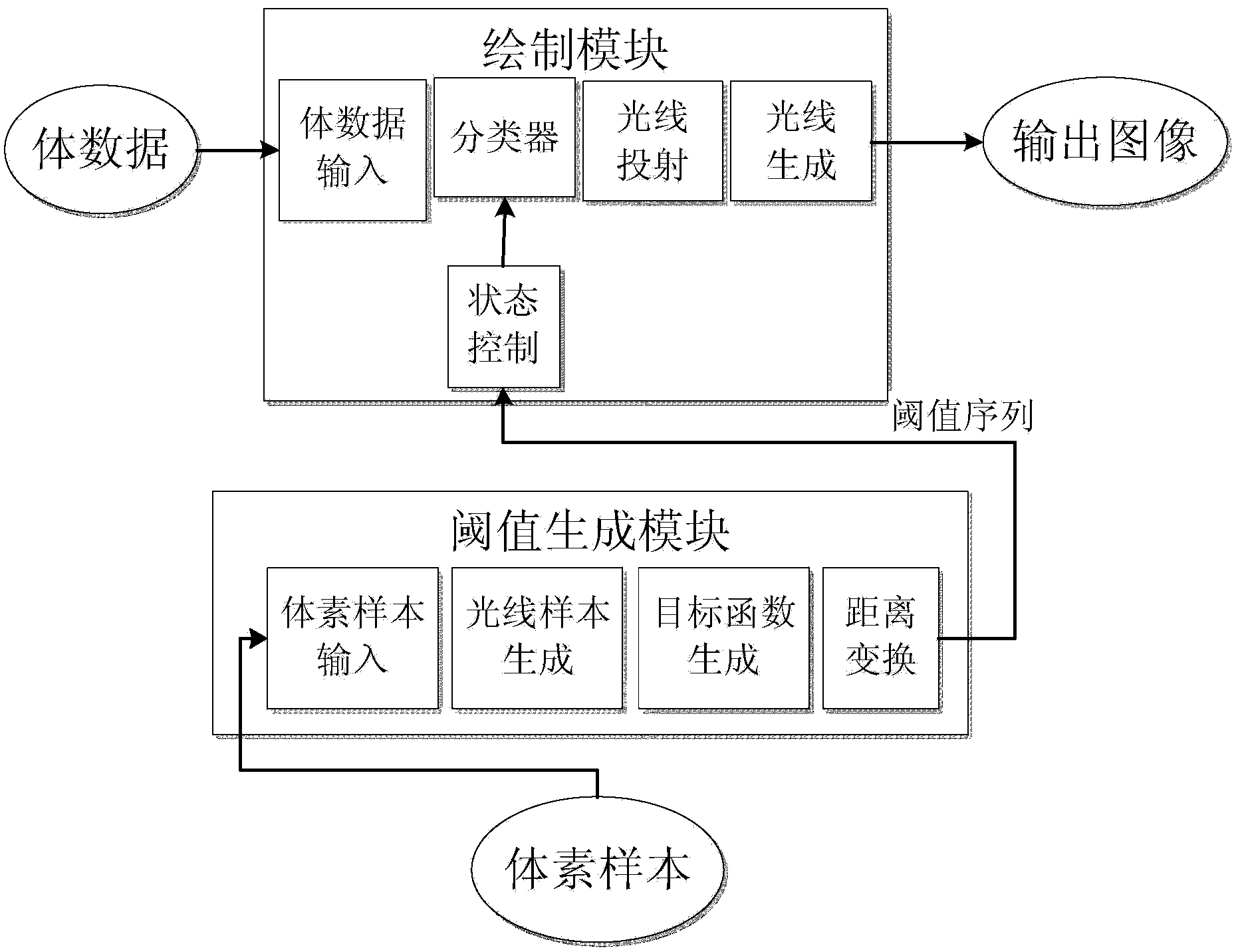
Automatic multi-threshold-based multilayer coloring body drawing method
The invention discloses an automatic multi-threshold-based multilayer coloring body drawing system. The system comprises a threshold generation module and a drawing module, wherein the threshold generation module generates a threshold sequence according to the input voxel sample; and the drawing module performs multilayer coloring according to the threshold sequence relative to volume data and generates a colored output image. The invention also provides an automatic multi-threshold-based multilayer coloring body drawing method. Compared with the prior art, the automatic multi-threshold-based multilayer coloring body drawing system has the advantages that the discrimination effect of the multilayer structure is obvious, the volume data can be subjected to layered coloring, the data do not need to be segmented in advance, the memory and computing cost in the drawing process are low, and the efficiency is high. The system has important application values in the fields of visualization in scientific computing and visualization in medical images.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Track compression method based on moving behavior characteristics
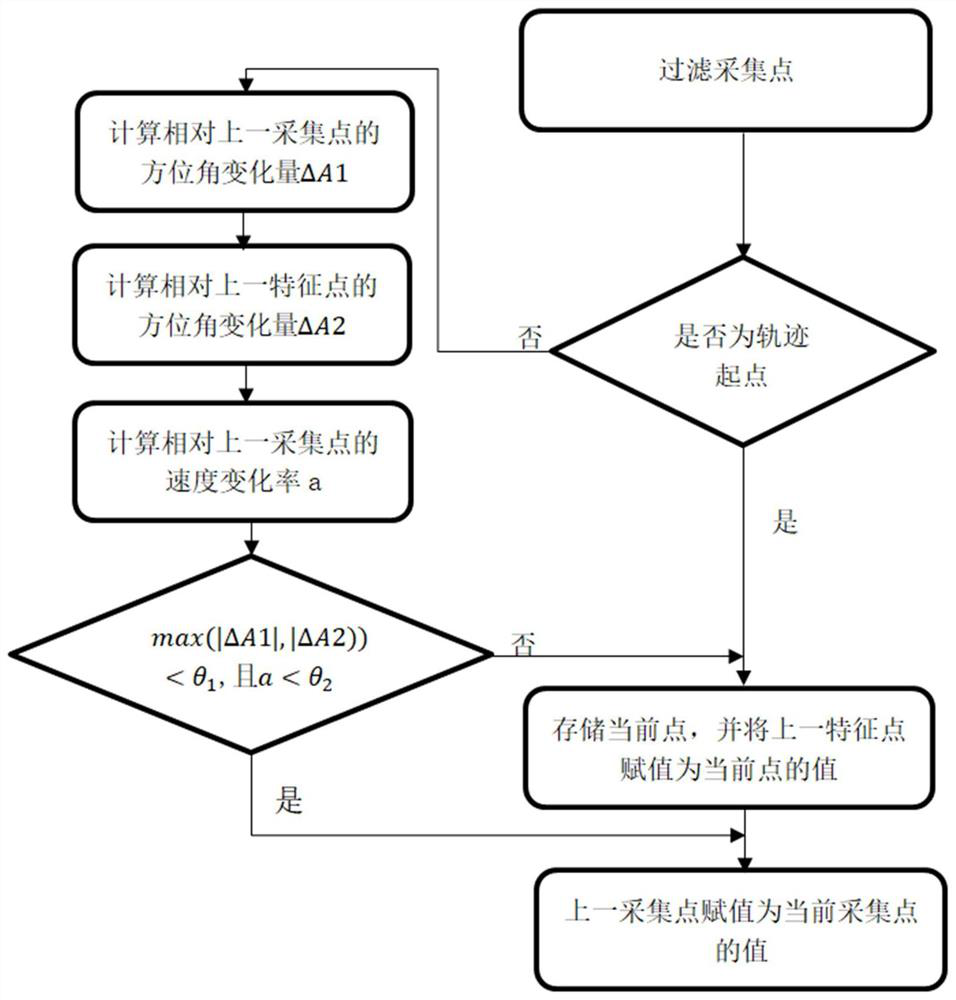
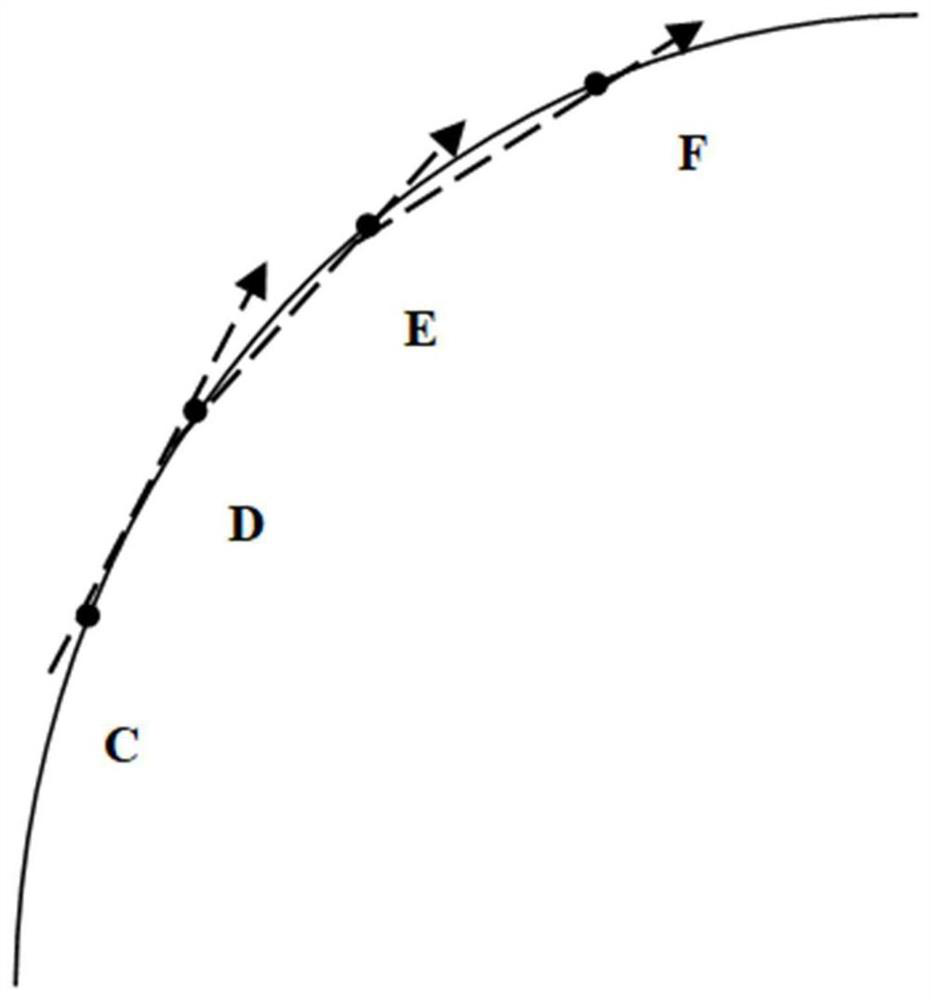
PendingCN112762941AHas linear time complexitySecondary cache lessNavigational calculation instrumentsSimulationComputational physics
The invention provides a track compression method based on moving behavior characteristics. The track compression method comprises the following steps: acquiring an acquisition point of a track; if the current acquisition point is a starting point, regarding the current acquisition point as a feature point and stored, and meanwhile, assigning the previous feature point as the value of the current acquisition point; otherwise, calculating the azimuth angle variation of the current acquisition point relative to the previous acquisition point and the previous characteristic point, and calculating the speed change rate of the current acquisition point; if the larger value of the azimuth angle variable quantity and the speed change rate are both smaller than the corresponding preset threshold values, processing is not carried out; otherwise, regarding the characteristic points as characteristic points and storing the characteristic points, and meanwhile, assigning the previous characteristic point as the value of the current acquisition point; and finally, assigning the previous acquisition point as the value of the current acquisition point, and continuing to execute the above steps on the next acquisition point of the current acquisition point. Compared with the prior art, the method has the advantages that the characteristic points are captured more accurately, and the driving state information under the situations of rapid acceleration, rapid deceleration, rapid steering and the like can be stored.
Owner:JINLING INST OF TECH
Distributed temporal graph reachability query processing method based on Blogel
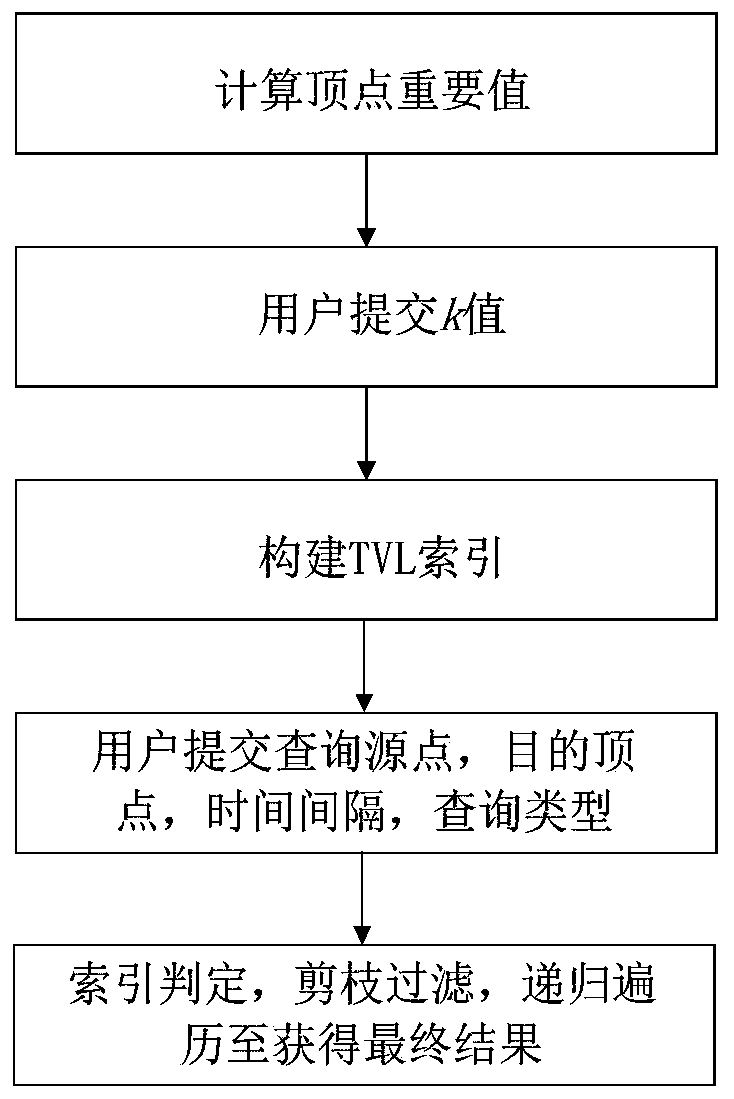
InactiveCN110377795ANarrow down the search spaceImprove build efficiencyOther databases indexingOther databases queryingReachabilityArrival time
The invention discloses a distributed temporal graph reachability query processing method based on a Block. According to the method, three tense graph accessibility queries are provided, 1. querying common tense graph accessibility; 2, querying at the shortest time interval; and 3, querying the earliest arrival time. According to the method, based on a Blogel distributed computing framework, tenseinformation and a graph topological structure of a tense graph are effectively organized by utilizing a tense vertex label index TVL; the batch and parallel technologies are utilized to improve the construction efficiency of the TVL index; and an index judgment method and a pruning technology are utilized to reduce the graph search space and improve the query efficiency. The method comprises thefollowing steps of calculating a reachable standard vertex label set Lout and a reachable standard vertex label set Lin for each vertex in a TVL index construction stage; then, in the query stage, thepruning technology is used for effectively reducing the query search space, and the query result is quickly returned according to the index judgment method. According to the method, the accessibilityquery processing efficiency is greatly improved, and the optimal performance is provided.
Owner:ZHEJIANG UNIV +1
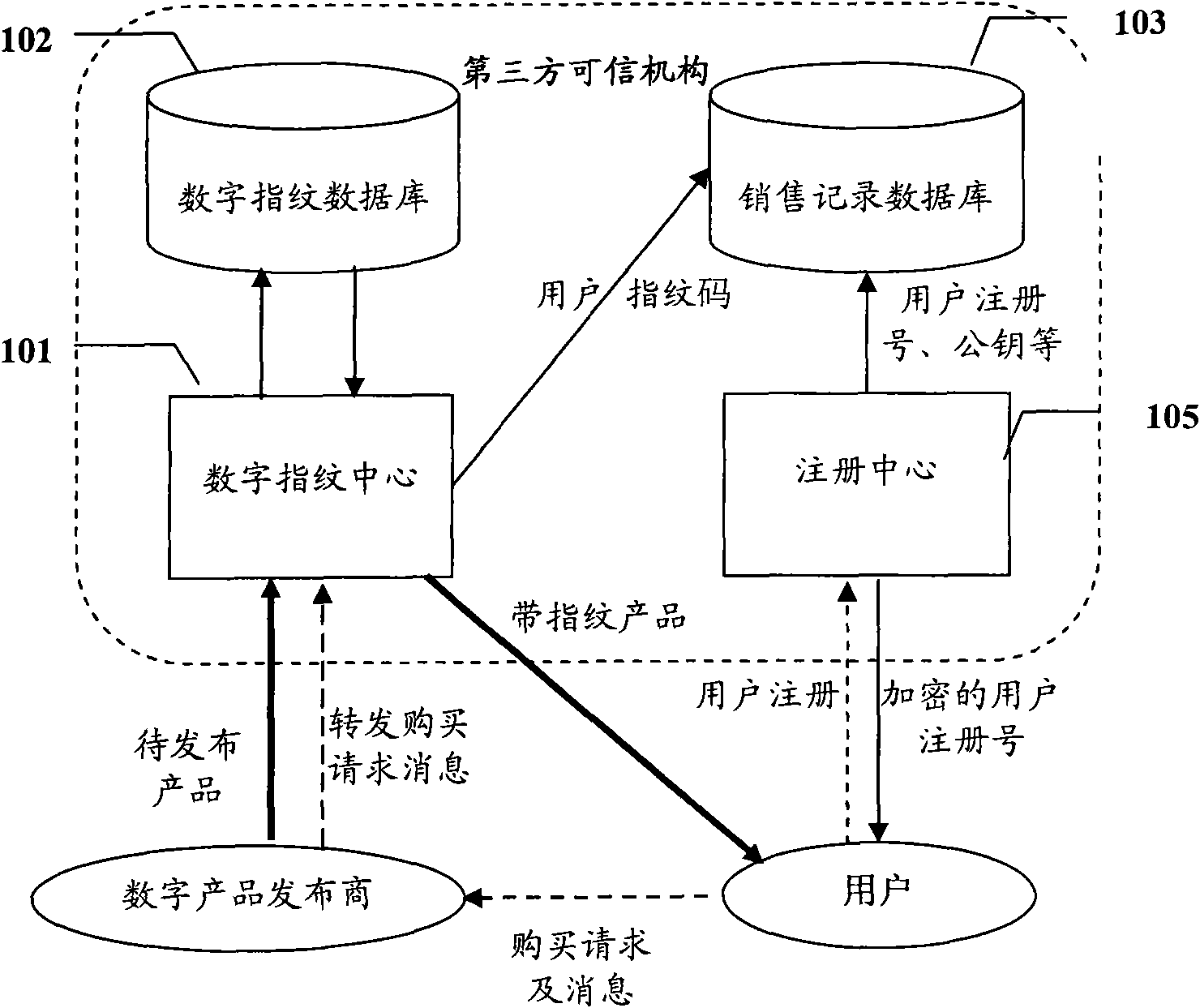
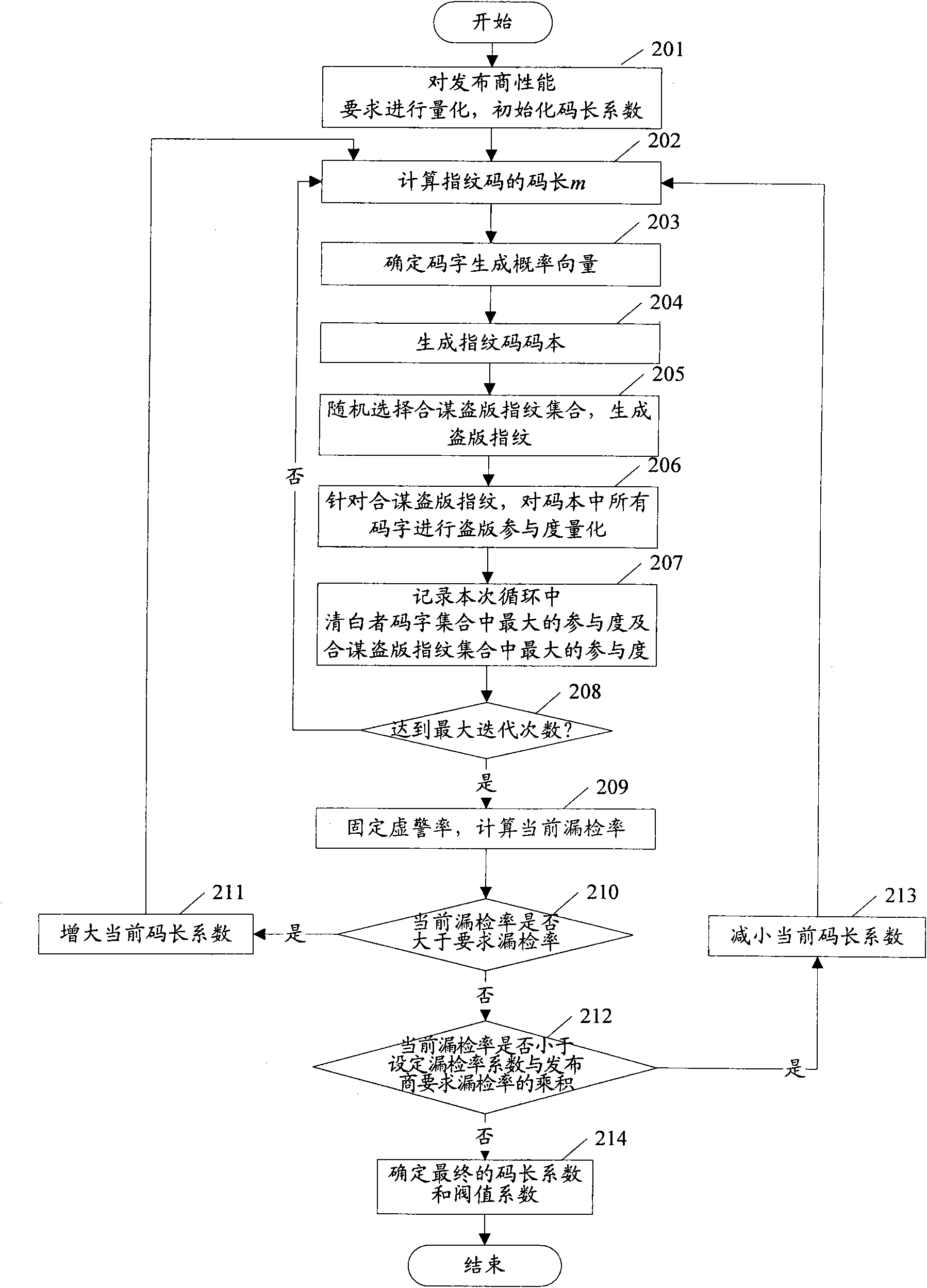
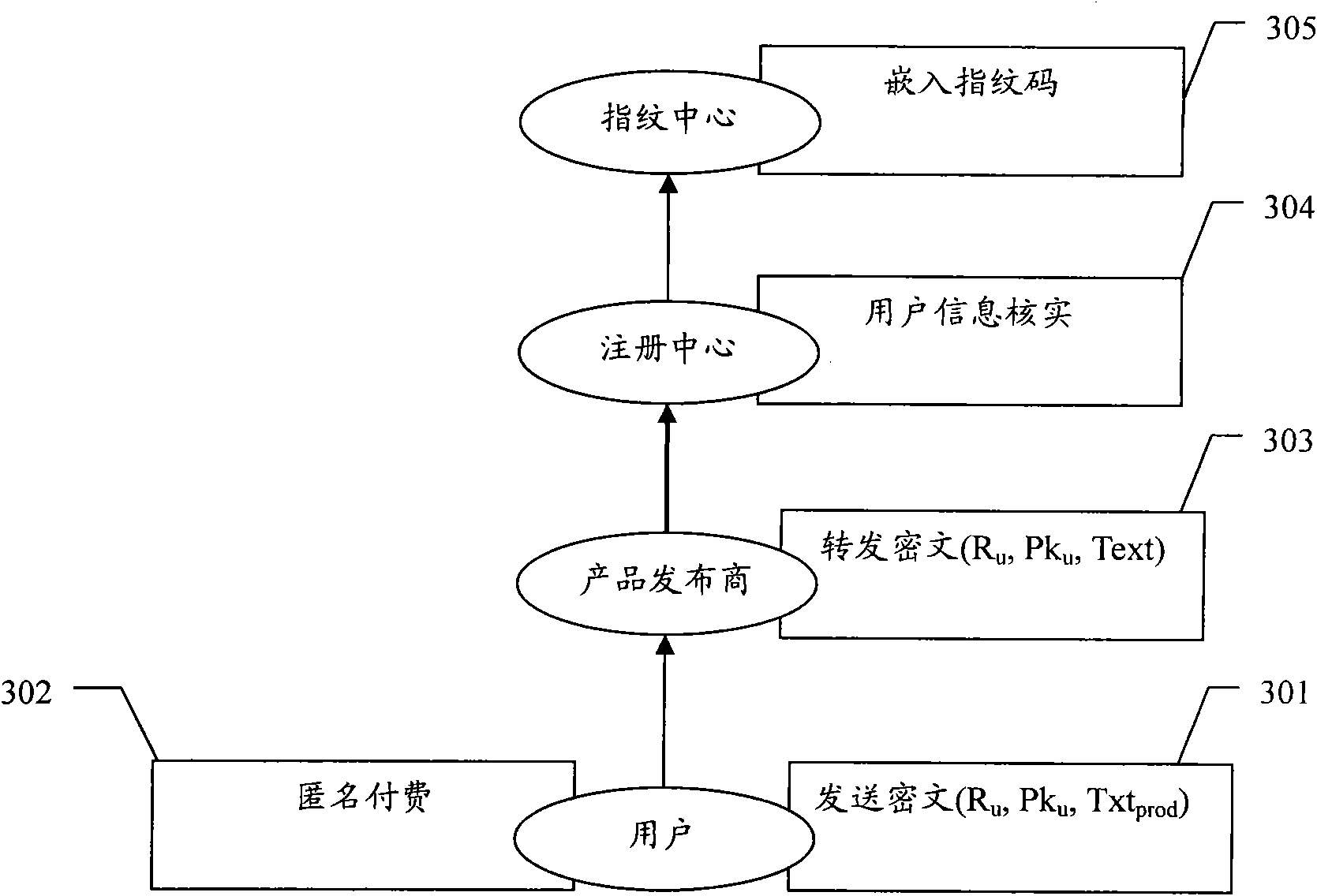
Method for protecting digital product based on asymmetric digital fingerprint and system thereof
InactiveCN101556675ACode length shorteningCode length factor shortenedTransmissionCommerceThird partyProduct base
The invention discloses an asymmetric digital fingerprint generation method and a method for protecting a digital product based on the method and a system thereof. The method comprises the following steps: a digital fingerprint center of a third-party credible authority generates a codebook of digital fingerprint codes according to performance requirements of a product releaser; a user provides an authenticated public key to a registration center and applies a registration number for buying digital products and the registration center uses the public key to encrypt the registration number and then sends the encrypted registration number to the user; the user buys the products from the releasers; and the digital fingerprint center inserts digital fingerprint to the products to be released and then releases the digital products to the user; and the digital fingerprint center tracks pirates for the pirated products and the credible authority feeds back the tracked results to the releasers. The invention optimizes code length coefficients of fingerprint codes, reduces the influence to the digital products under the condition of meeting the requirements of the product releasers and reduces storage expenditure of the fingerprint center. The user information is not public to the releasers, thus reducing the possibility for misjudging the pirates.
Owner:北京汉邦欣洲信息科技有限公司
Input-driven transaction-oriented time-space efficiency optimization method for storage and calculation-integrated coordinated adjustment
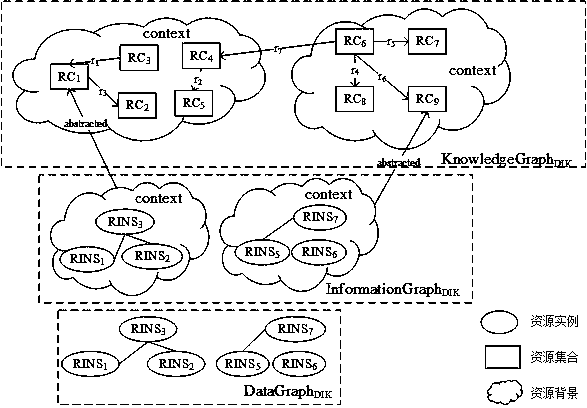
InactiveCN107133371AExcellent search efficiencyEasy to find linksWeb data indexingSpecial data processing applicationsUser inputSpacetime
The invention discloses an input-driven transaction-oriented time-space efficiency optimization method for storage and calculation-integrated coordinated adjustment, provides interpretation of resource forms, including data, information and knowledge, and concept representation of a data map, an information map and a knowledge map, and belongs to the field of crossover of distributed calculation and a software engineering technology. Storage is determined by calculation and search is served by storage, and which layer resources should be stored on cannot be judged just from the resource type. The resource type transfer cost and calculation cost scheme with the most reasonable cost is found out according to user input, a resource object search mechanism and a resource space organization scheme are reasonably determined, and improvement of the resource search efficiency is facilitated.
Owner:HAINAN UNIVERSITY
Attribute-based encryption under a flexible and direct revocation ciphertext policy
ActiveCN103297227BReduce the burden onReduce computational complexityKey distribution for secure communicationComputation complexityCiphertext
The invention discloses attribute-based encryption supporting flexible and direct-revocatory ciphertext policy. The encryption is characterized in that the encryption includes: (1) generating system public keys and main secret keys; (2) generating attributive secret keys; (3) encrypting to generate ciphertext; (4) generating and publishing public parameters by an attribute center; generating ciphertext updating secret keys and transmitting the ciphertext updating secret keys to cloud service providers through secure channels; (5) ciphertext updating procedure; (6) user decrypting procedure. The Attribute-based encryption supporting flexible and direct-revocatory ciphertext policy has the advantages that the size of ciphertext is constant, communication traffic is small, users do not need to update attribute, computation complexity and storage cost are low, users do not need to update secret keys every time, load of authority centers is greatly relieved and the like.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com