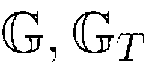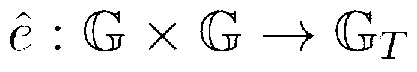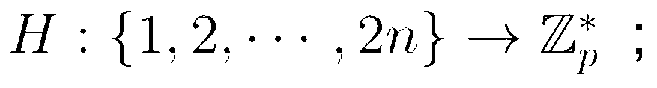Attribute-based encryption supporting flexible and direct-revocatory ciphertext policy
A technology of ciphertext strategy and attribute key, which is applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below.
[0027] It should be noted that, in order to better understand the present invention, first make the following description:
[0028] 1. Attributes and access structures
[0029] Suppose there are n attributes in the attribute space, namely u={ω 1 , ω 2 ,...,ω n}, where n is a definite natural number. Each attribute ω i There are three cases: positive burden "It doesn't matter", Indicates that the user has the attribute ω i , Indicates that the user has no attribute ω i or ω i is not a correct attribute of the user. Considering that the access structure W consists of a single AND gate of positive and negative attributes, namely in is the index into the set of attributes specified in W, yes or An attribute is "don't care" if it does not appear in the AND gate. have to be aware of is, if and only if ω i ∈S when hour, when when, where
[0030] 2. Auxiliary functions
[0031] We i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com