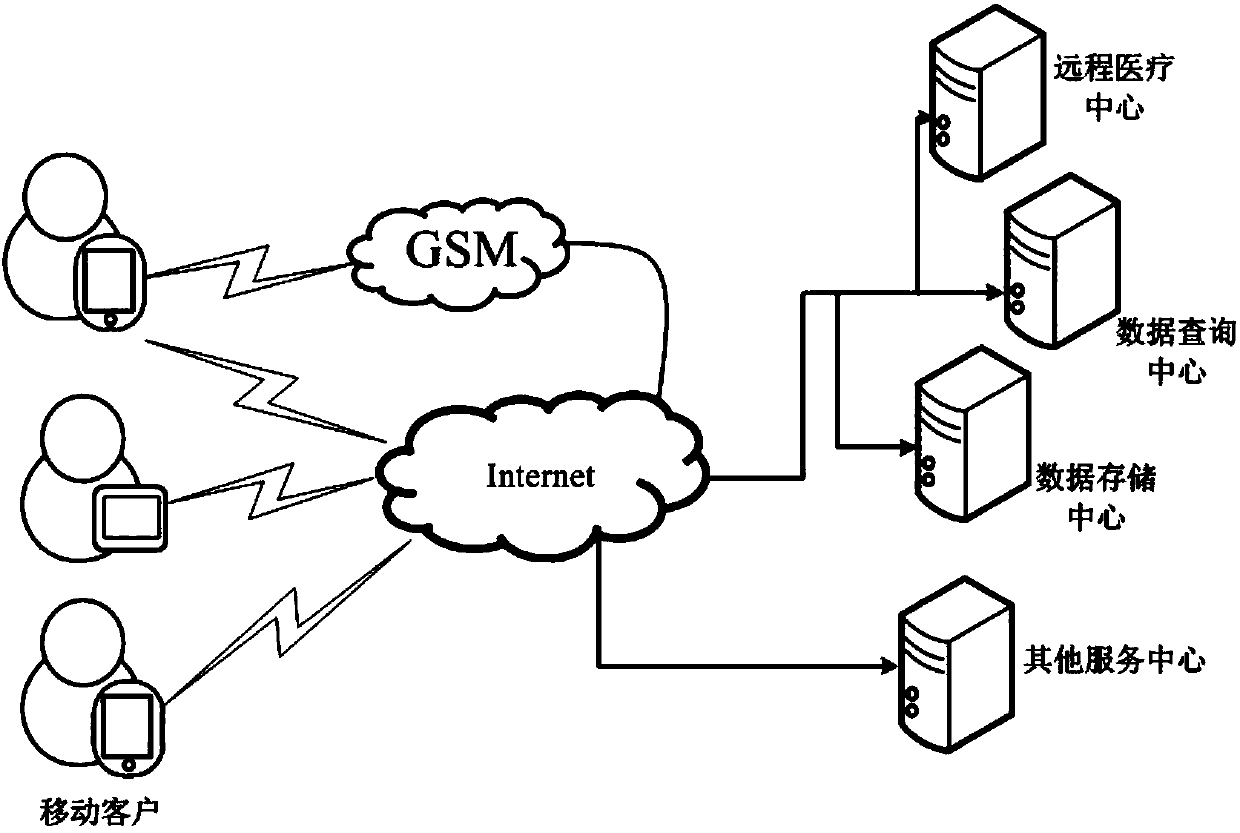
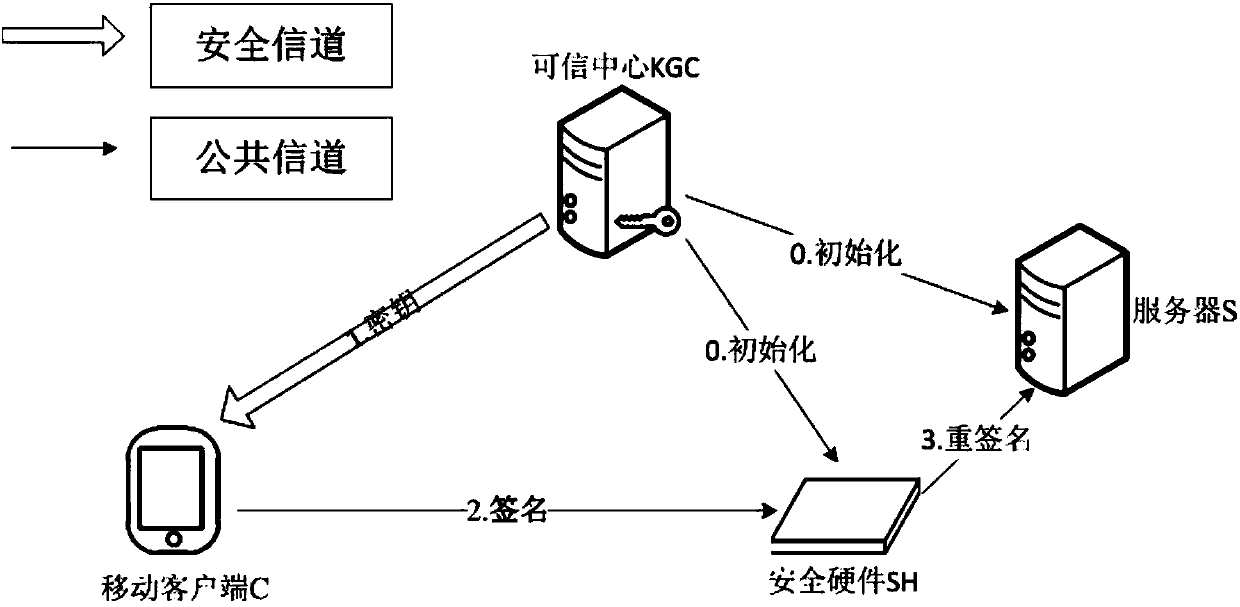
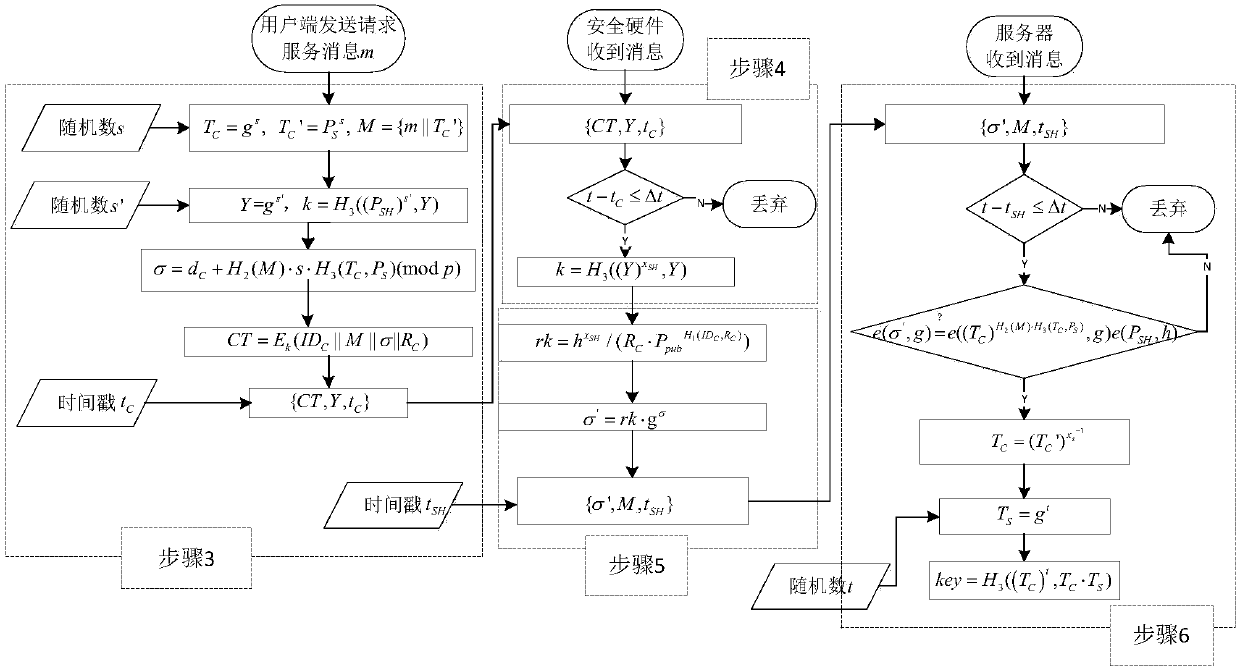
Anonymous authentication method based on security hardware
An anonymous authentication and hardware technology, applied in electrical components, transmission systems, etc., can solve the problems of low authentication efficiency, high storage cost and high computing cost, and achieve the effect of reducing storage cost, computing cost and communication cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0081] Among the existing schemes based on the verification table, such as the scheme of Liu et al. Among the existing schemes based on the pseudonym pool, such as Zhao's scheme. To achieve RSA1024 bit security level, bilinear mapping e:G 1 ×G 1 →G 2 Group G of order q in 1 defined on the elliptic curve y 2 =x 3 On +x(modp), where p is a 512-bit large prime number, and q is a 160-bit Solinas prime number. Some of the main cryptographic operations are defined as follows, T P Indicates the running time of a bilinear pairing operation, T E Indicates the running time of a power operation, T SM Indicates the running time of a pairing-based multiplication operation, T H Indicates the running time of a hash-to-point hash operation. In the Inter(R)PXA270 624MHZ processor and the personal digital device hardware environment of the Linux system, the running time results of each operation obtained by using the MIRACL cryptographic function library are as follows: T P =96.20ms,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com