Method, device and system for accessing memory
A memory access and memory technology, applied in the network field, can solve the problems of increased communication delay, large communication delay, and low RDMA operation efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
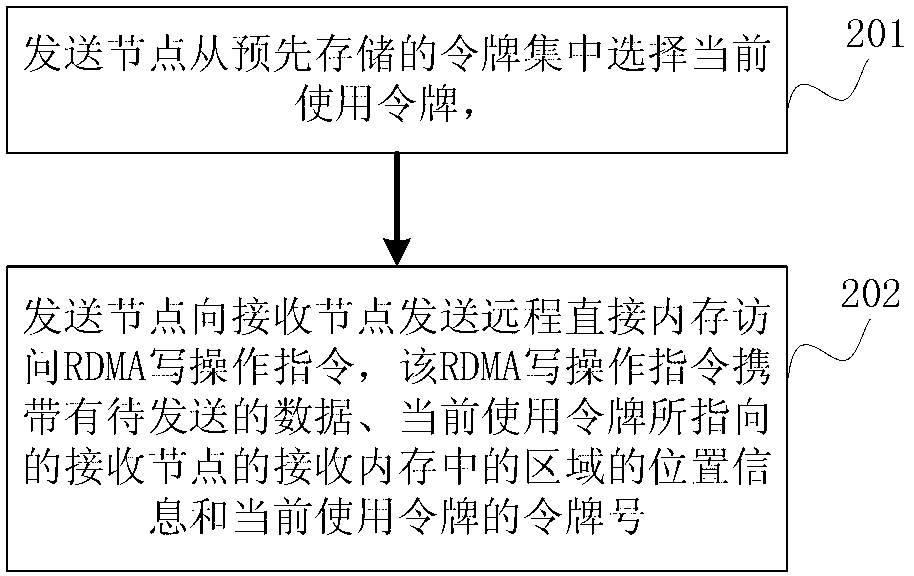
[0114] Please refer to figure 2 , which shows a method flowchart of the memory access method provided by Embodiment 1 of the present invention. In this embodiment, the memory access method is mainly used for figure 1 This is exemplified in the sending node in the implementation environment shown. The memory access methods include:
[0115] Step 201, the sending node selects a currently used token from a pre-stored token set;
[0116] The sending node selects the currently used token from a pre-stored token set, the token set includes at least one token, and each token points to an area in the receiving memory of the receiving node;
[0117] In step 202, the sending node sends a remote direct memory access RDMA write operation instruction to the receiving node, and the RDMA write operation instruction carries the data to be sent, the location information of the area in the receiving memory of the receiving node pointed to by the current usage token, and the current usage. ...
Embodiment 2
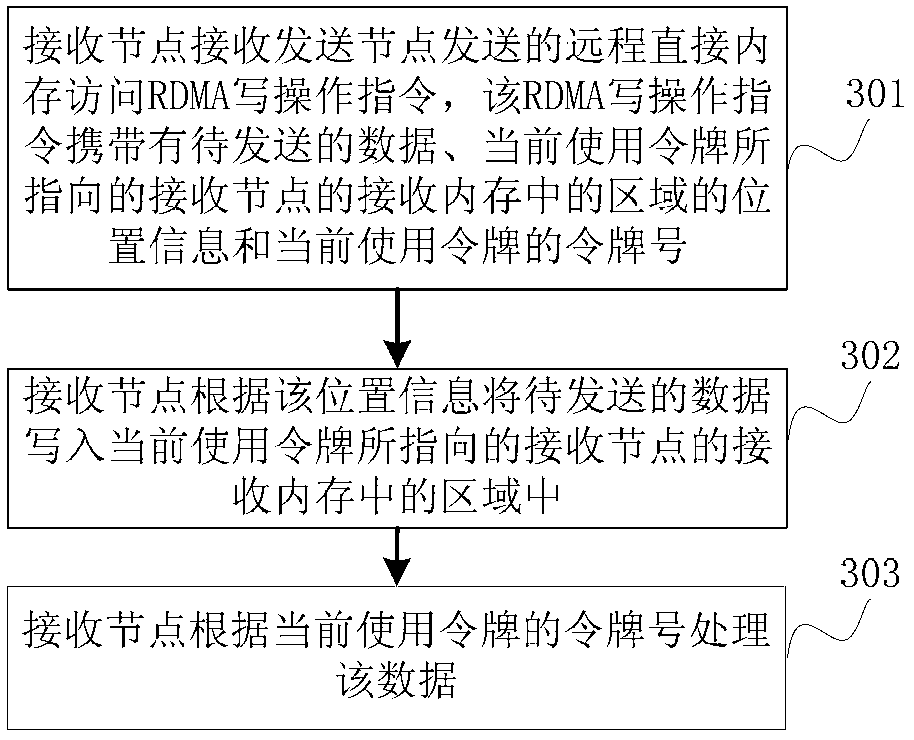
[0121] Please refer to image 3 , which shows a method flowchart of the memory access method provided by the second embodiment of the present invention. In this embodiment, the memory access method is mainly used for figure 1 For example, the receiving node in the illustrated implementation environment. The memory access methods include:
[0122] Step 301, the receiving node receives the remote direct memory access RDMA write operation instruction sent by the sending node, the RDMA write operation instruction carries the data to be sent, the location information of the area in the receiving memory of the receiving node pointed to by the current use token, and the current location information. the token number of the token used;
[0123] The currently used token is selected by the sending node from a pre-stored token set, and each token in the token set points to an area in the receiving memory of the receiving node respectively. The location information may be the starting...
Embodiment 3
[0130] Please refer to Figure 4 , which shows a method flowchart of the memory access method provided by Embodiment 3 of the present invention. In this embodiment, the memory access method is mainly used for figure 1 A memory access system including a sending node and a receiving node is shown as an example. The memory access methods include:
[0131] Step 401, the receiving node creates a receiving memory;
[0132] The receiving node divides a memory area in the local memory as the receiving memory required during the RDMA operation, and the receiving memory is used to store the data written by the sending node. For example, the receiving node divides a memory space with a size of 100KB in the local memory as the receiving memory, which is used to store the data written by the sending node.
[0133] Step 402, the receiving node creates a token, and allocates a receiving memory area for each token;
[0134] The receiving node creates tokens and allocates receiving memory f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com