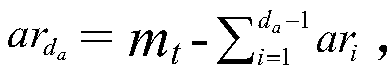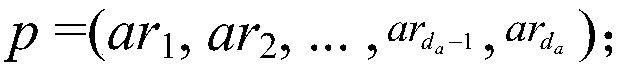A verifiable fully homomorphic encryption method based on matrix operation
A fully homomorphic encryption and matrix operation technology, which is applied to secure communication devices and key distribution, can solve the problems that the security strength cannot reach the level of application, lack of practicability, ciphertext length and computational complexity surge, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] figure 1 It is a schematic diagram of the framework of the method described in the invention, and two entities are involved in the figure, a user (User) and a cloud service provider (CSP). Among them, User is the commissioner of the computing task, and CSP is the actual executor of the computing task. The specific interaction process between them is as follows:
[0042] (1) User uses the encryption algorithm to encrypt the plaintext data m involved in the calculation t Encrypt to get ciphertext C t , and calculate the relevant verification evidence proof in the process, then User saves the proof and C t and the function F(·) that needs to be calculated are sent to the server of the CSP, and the CSP is entrusted to perform the calculation;
[0043] (2) After CSP receives and clarifies User’s outsourced computing tasks, according to the computing function F( ), in the ciphertext C t Carry out corresponding calculations on and return the obtained calculation results R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com