Malicious code detection method and system
A malicious code detection and malicious code technology, applied in the field of software security detection, can solve problems such as inability to accurately identify malicious software, and achieve the effect of improving training and detection efficiency and high detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
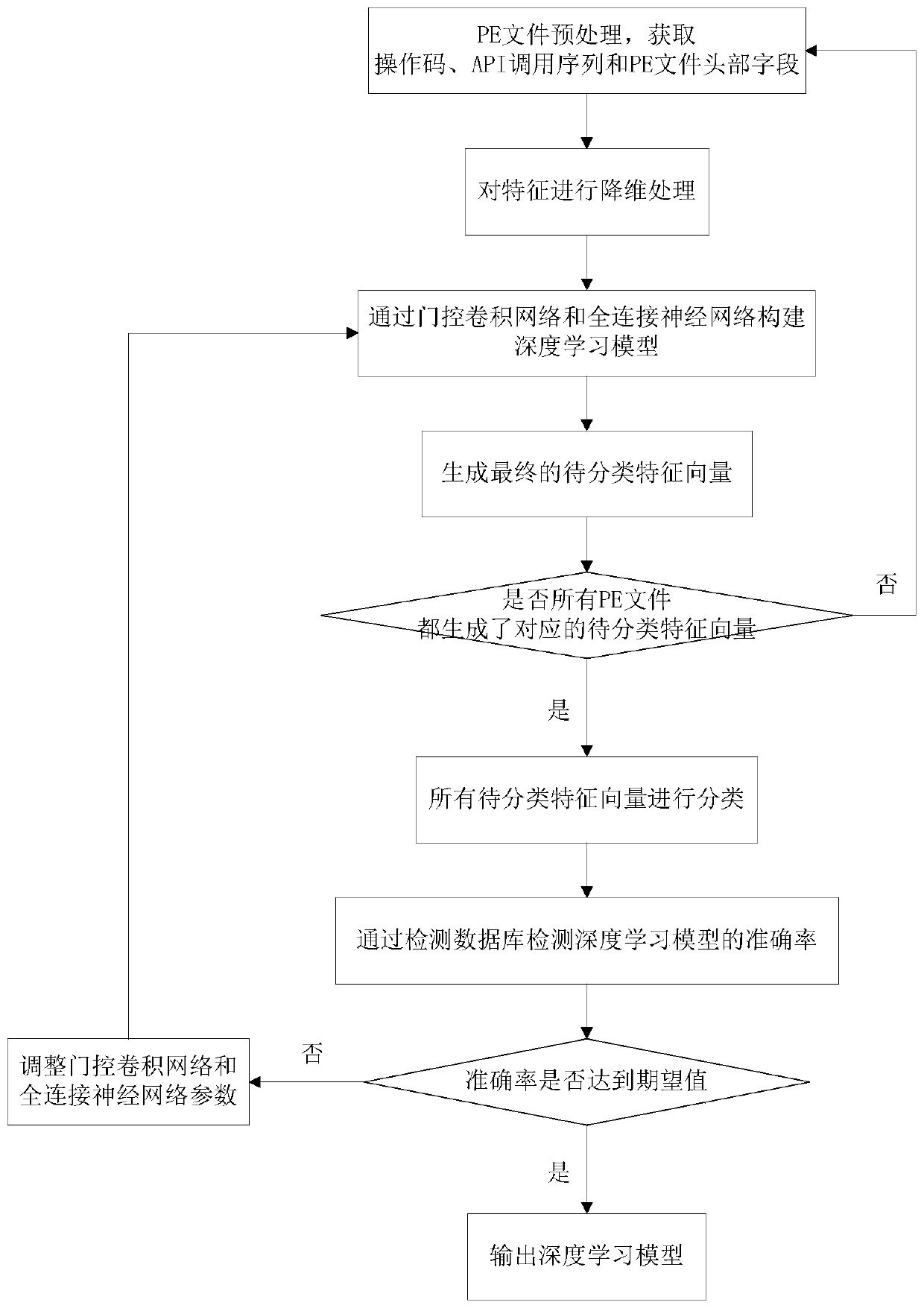
[0032] Because part of the sample data set involved is a malicious program, which may cause harm to the terminal computer, the construction of the entire system and the execution of the method are executed under a virtual machine. In this embodiment, VMware Workstations software is selected, which can easily and conveniently build the environment required by this embodiment.
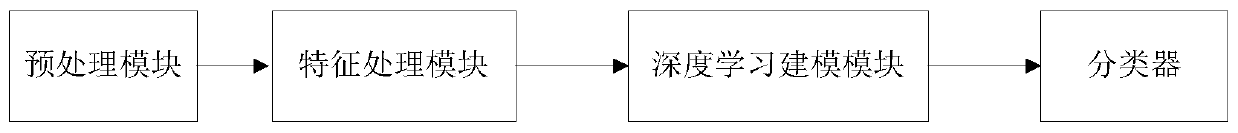
[0033] Such as figure 1 Shown the present invention to malicious code detection system, comprises:
[0034] Preprocessing module: used to obtain the characteristics of PE files, including opcodes, API call sequences and PE file header fields;
[0035] Feature processing module: used to receive the output of the preprocessing module, and perform dimensionality reduction processing on the feature through a stacked noise reduction autoencoder to obtain a feature vector after dimensionality reduction;
[0036] Deep learning modeling module: According to the features of the binary data of the PE file and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com