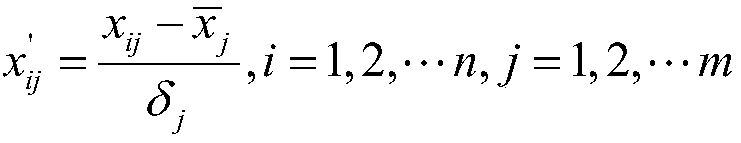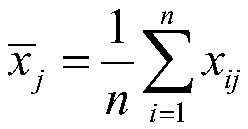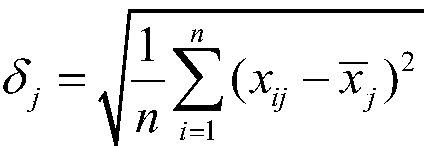Embedded system firmware security analysis method and system
An embedded system and security analysis technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as difficulty in security analysis, difficulty in repeating embedded devices, and unsafe hidden dangers in embedded devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] An embedded system firmware security analysis method and system, the evaluation steps of which are: determining factor set A, determining comment set B, determining the weight C of each factor, calculating the relative size D of weights between evaluation indicators and comprehensive evaluation E, determining The factor set A is the evaluation index system set U={u 1 ,u 2 ,...,u n}. (For example, the firmware is analyzed by using the TROMMEL tool here, and 13 major vulnerability threats U={u are listed in the firmware analysis report 1 ,u 2 ,...,u 13}), to determine that the comment set B often forms different grades due to the different evaluation values of each index. For example, the evaluation of safety level includes ultra-high risk, high risk, medium risk, low risk, safe and so on. A collection of different decisions is called a collection of comments. Write it here as:
[0033] V = {super high risk v 1 , high risk v 2 , medium risk v 3 , low risk v ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com