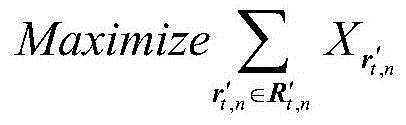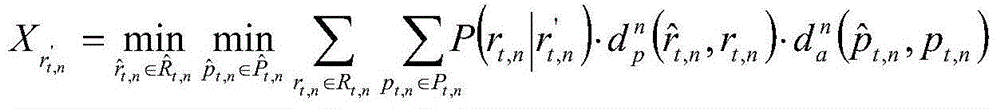Privacy protection quantitative analysis method in location-based service
A privacy protection and location-based service technology, applied in the field of privacy protection quantitative analysis in location-based services, can solve the problems of lack of strong attacker background knowledge, relatively few evaluations of location privacy protection effect, and no consideration of attacker background knowledge.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
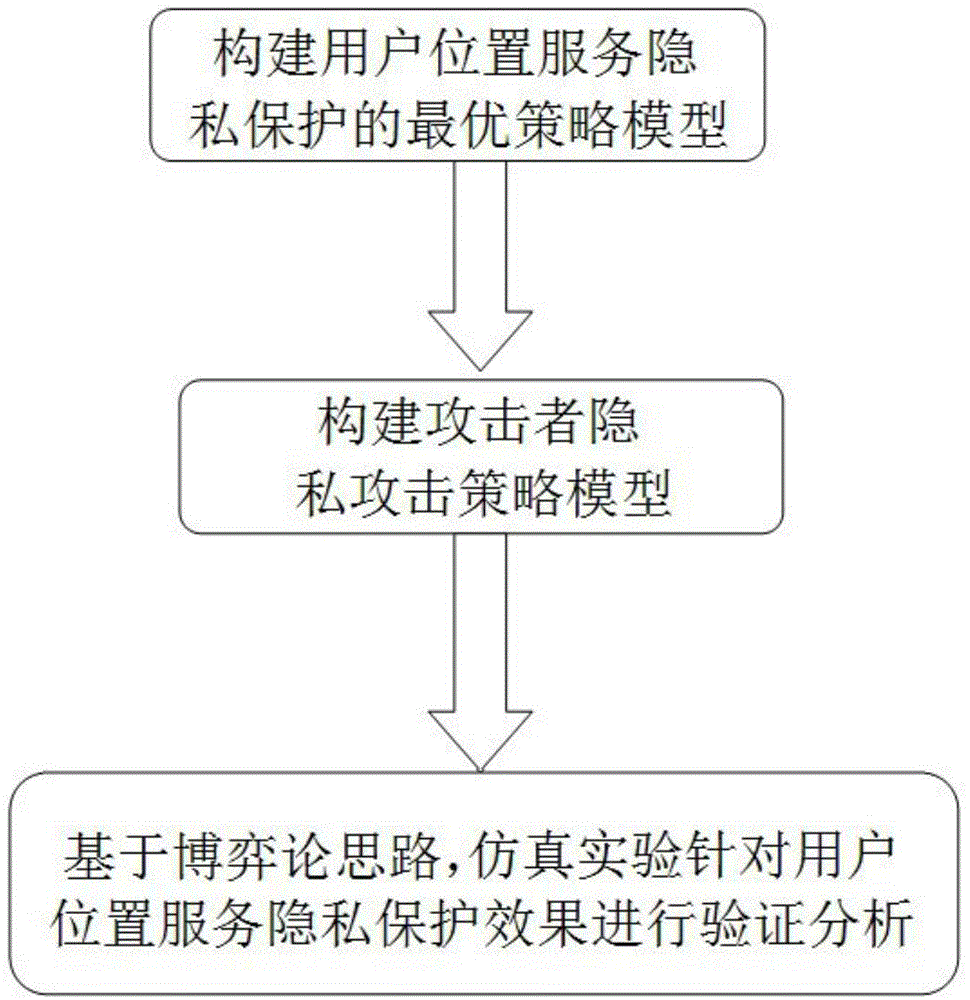
[0045] Such as figure 1 As shown, the privacy protection quantitative analysis method in the location service designed by the present invention is based on the analysis and research on the user's location privacy protection effect at a certain moment, fully considering the attacker's ability to attack the user's location and behavior, and proposes to use the attacker's The background knowledge is integrated into the user privacy protection effect evaluation model. After formalizing the problem through game theory, the optimal strategy of the user and the attacker is solved. In the actual application process, the scenario we consider is: a user can be in a Move in the spatial region Ω, divide Ω into a grid, and each cell in the grid represents a position r ∈ Ω with the smallest granularity. For some location-based applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com