Safety detection method and device for cipher chip
A cryptographic chip and security detection technology, applied in the field of cryptographic chip security detection methods and devices, can solve the problems of lack of internal structure observation of cryptographic chips, lack of precise control of laser energy, lack of laser injection time and space coordinated control, etc. The effect of efficient laser scanning injection and ciphertext data screening, strong scalability and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
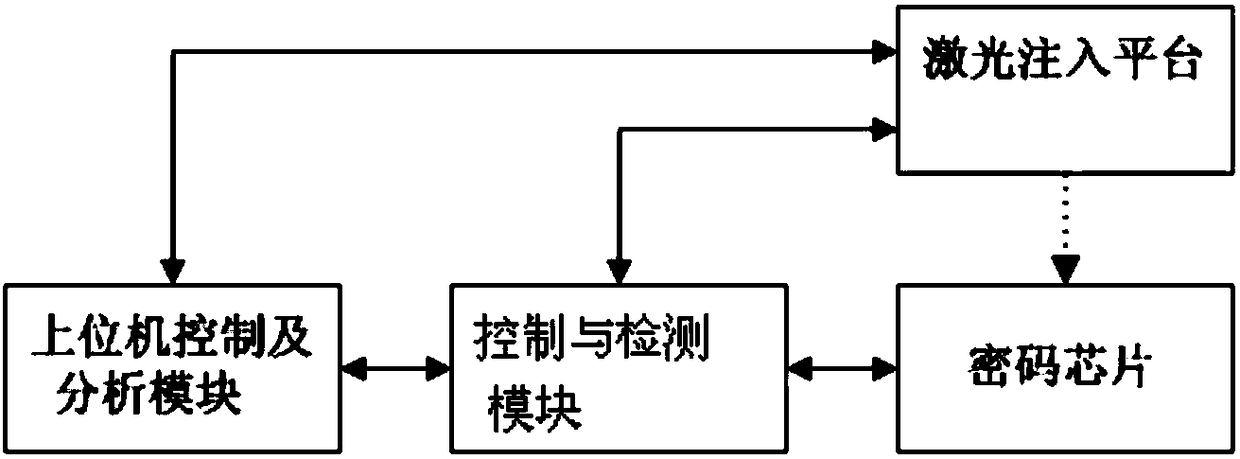
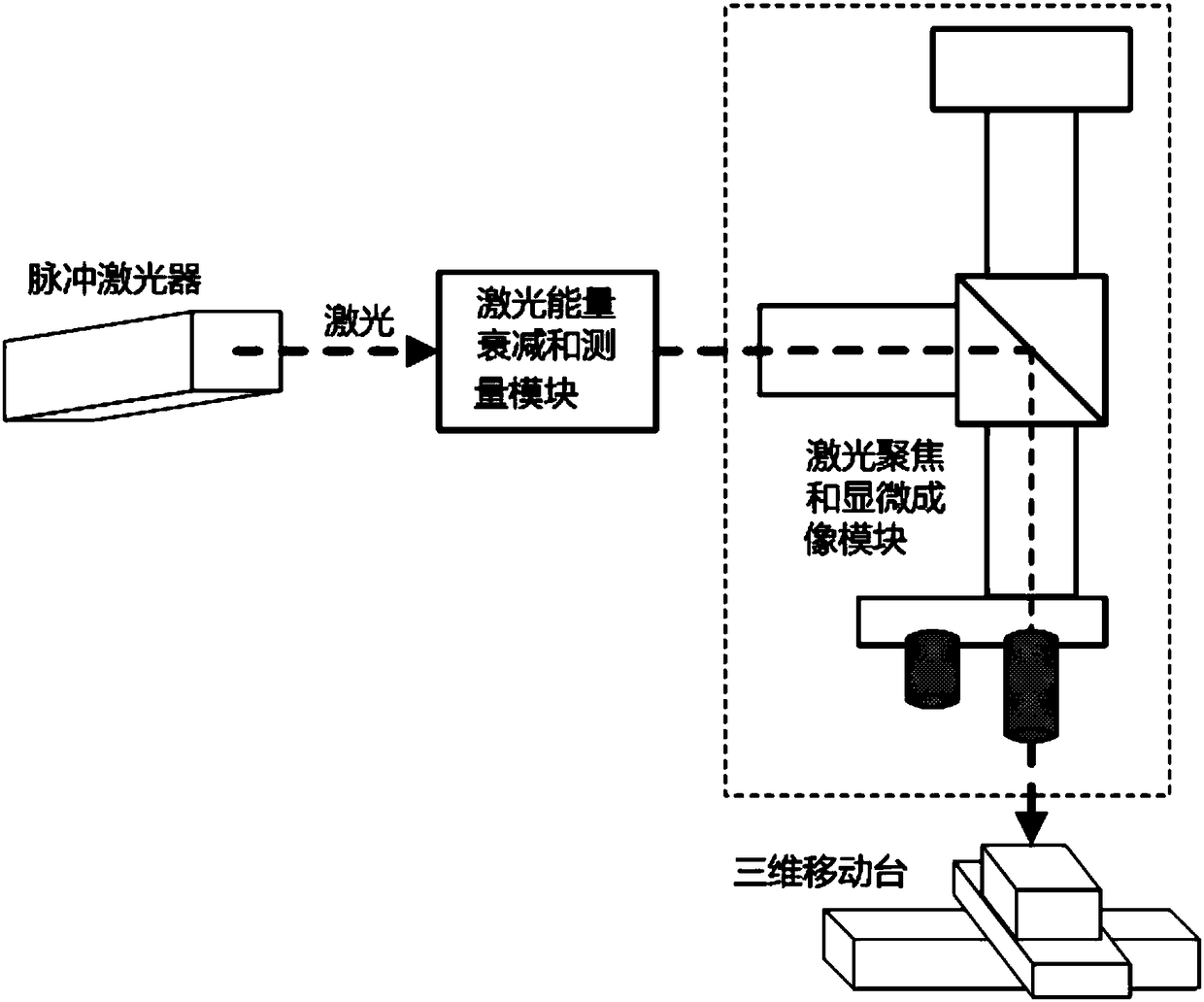
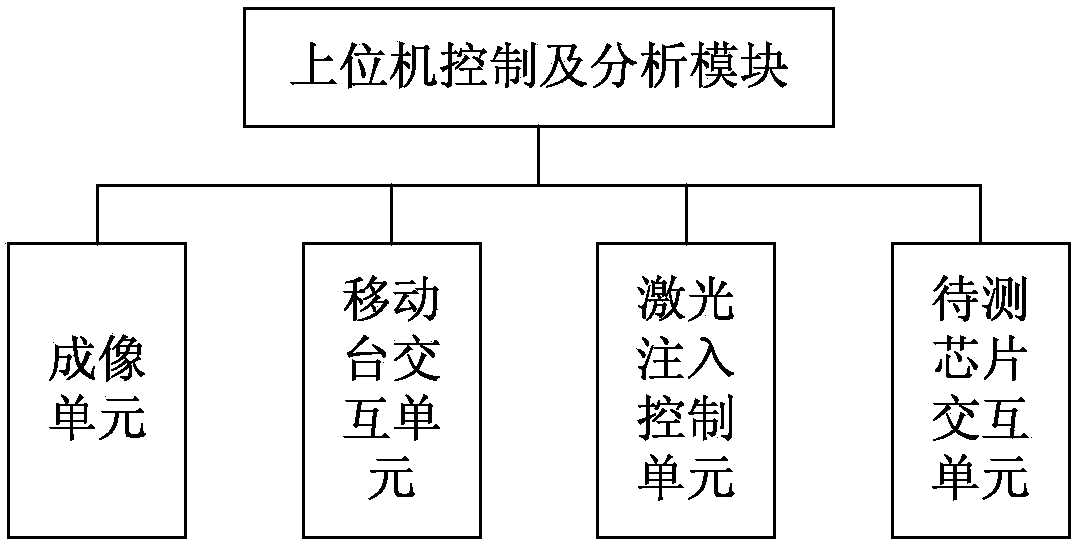
[0099]The present invention provides a specific embodiment, using a detection device for injecting laser into a cryptographic chip of the present invention to detect a cryptographic chip under test using the DES algorithm, and intends to adopt the 16th round of attack strategy, such as Figure 6 As shown, the laser is injected into the DES logic operation area of the cryptographic chip under test at different times to obtain several sets of correct-wrong ciphertext data, screen the ciphertext samples that meet the attack strategy, and judge whether it can be recovered through the corresponding differential fault analysis method. A key or part of a key. Its specific steps include:
[0100] Step 1) Determine the attack strategy to be adopted according to the specific cryptographic system and implementation method of the cryptographic chip under test. This embodiment adopts the sixteenth round of attack strategy for the DES algorithm. It is hoped that the sixteenth round of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com