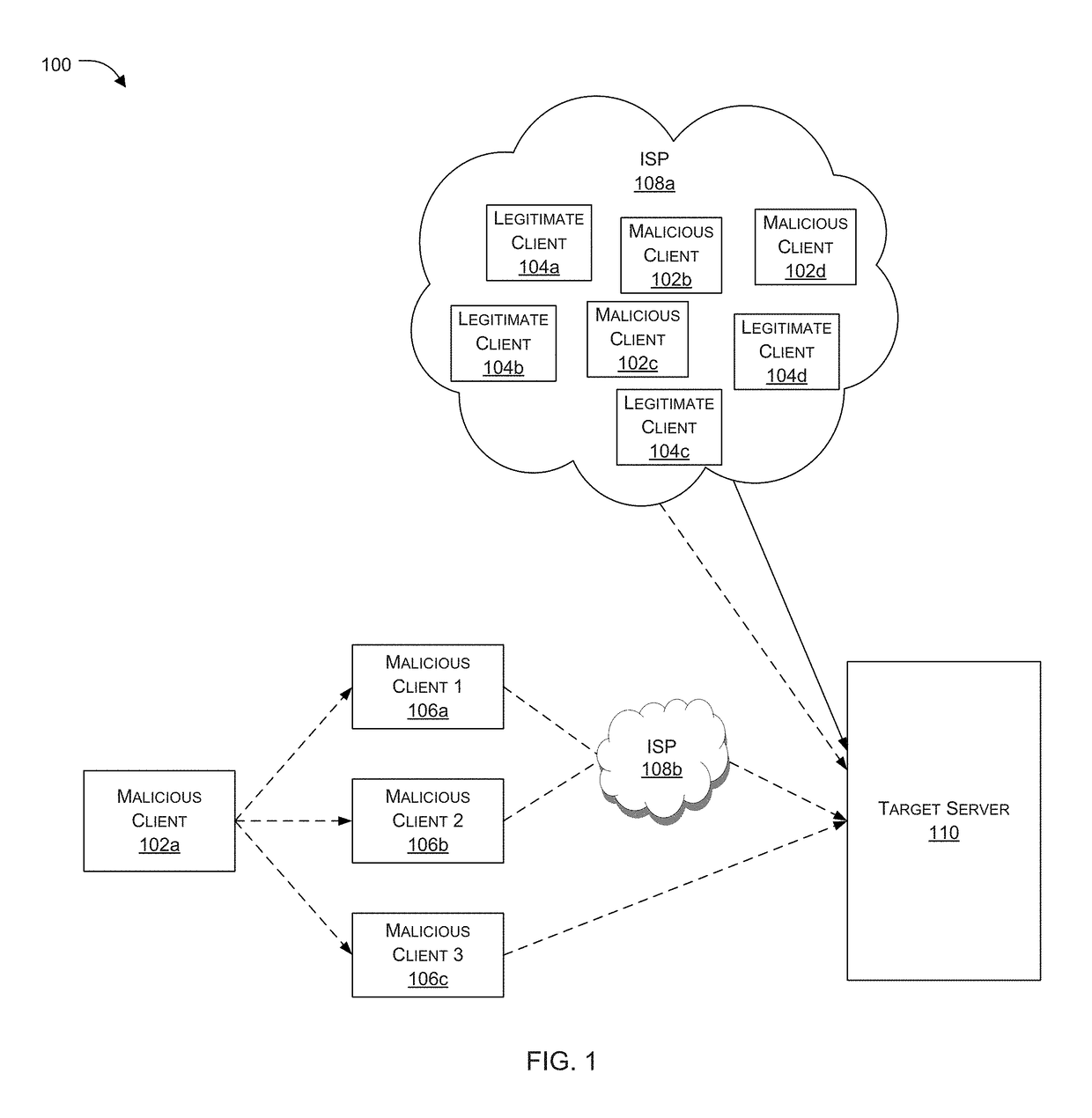
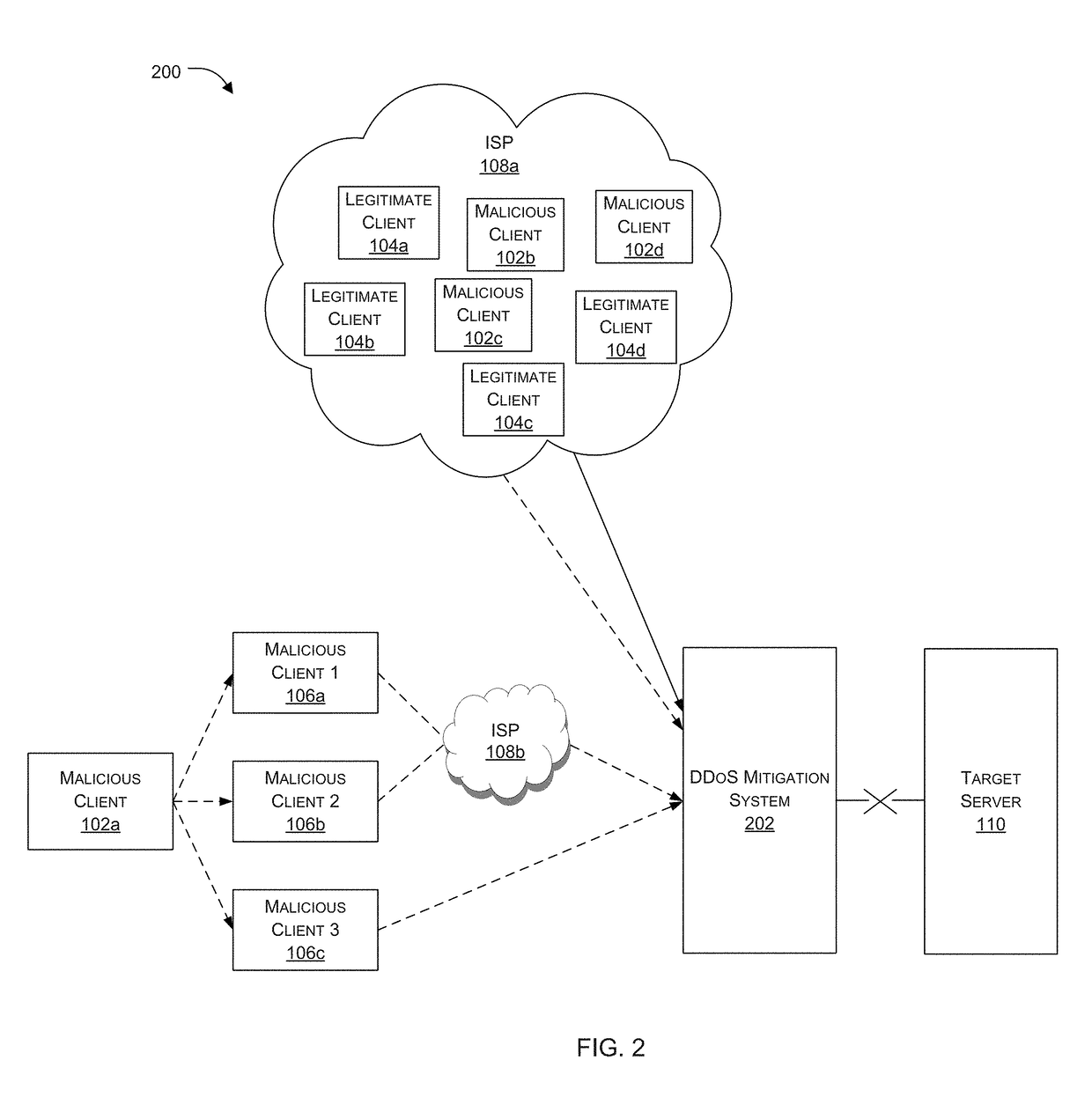
Patents
Literature
157 results about "Mitigation methods" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A bycatch mitigation technique (MT) is a method that fishers or fishery managers can use to reduce catch of non-target species.
Communication systems
ActiveUS20090190541A1Reduce distractionsNetwork traffic/resource managementRadio transmissionFrequency spectrumTransceiver
An interference mitigation method in a wireless network in which a plurality of nodes share an available frequency spectrum by performing wireless communication on sub-channels defined within the available spectrum. The nodes are grouped into clusters, each cluster having a leader of the cluster. Preferably, every node in the cluster is a transceiver equipped to act as leader and this leader role is rotated around the cluster.
Owner:FUJITSU LTD
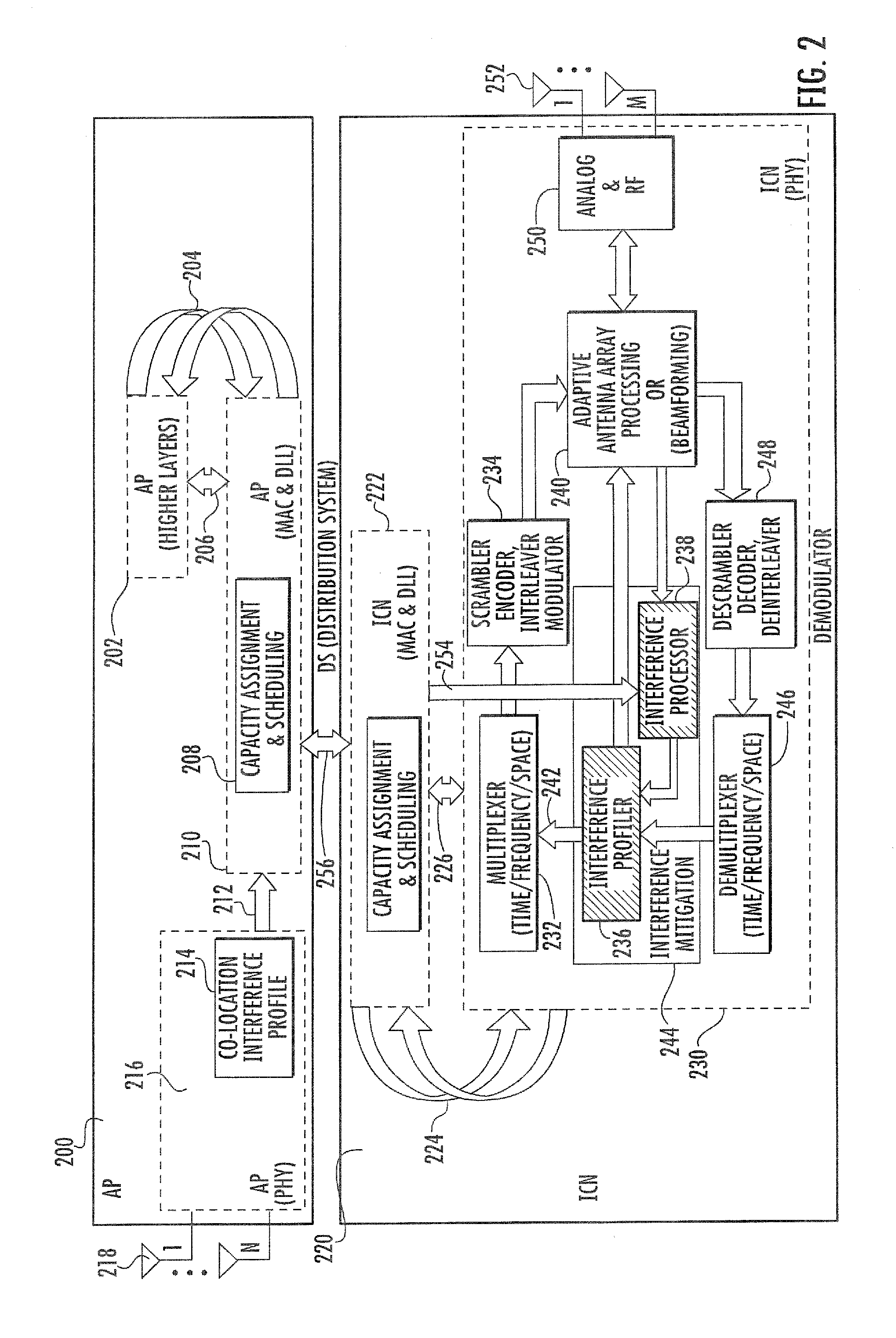
Methods and apparatus for centralized and coordinated interference mitigation in a WLAN network
InactiveUS20110090885A1Facilitate communicationEasy to interferePower managementNetwork topologiesBroadcast channelsPrecoding
Method and apparatus for interference mitigation in wireless local area networks (such as WLANs). In one embodiment, a centralized interference measurement and mitigation method is disclosed. The method may involve spectral sensing, beamforming, MIMO, power control, MAC scheduling using a cross-layer approach, and / or broadcast channel precoding, employed towards performance enhancement of WLAN networks in presence of interference. In one variant, different actions at interference mitigation are selected based on the source of the interference (e.g., inter-network or intra-network).
Owner:SAFAVI SAEID
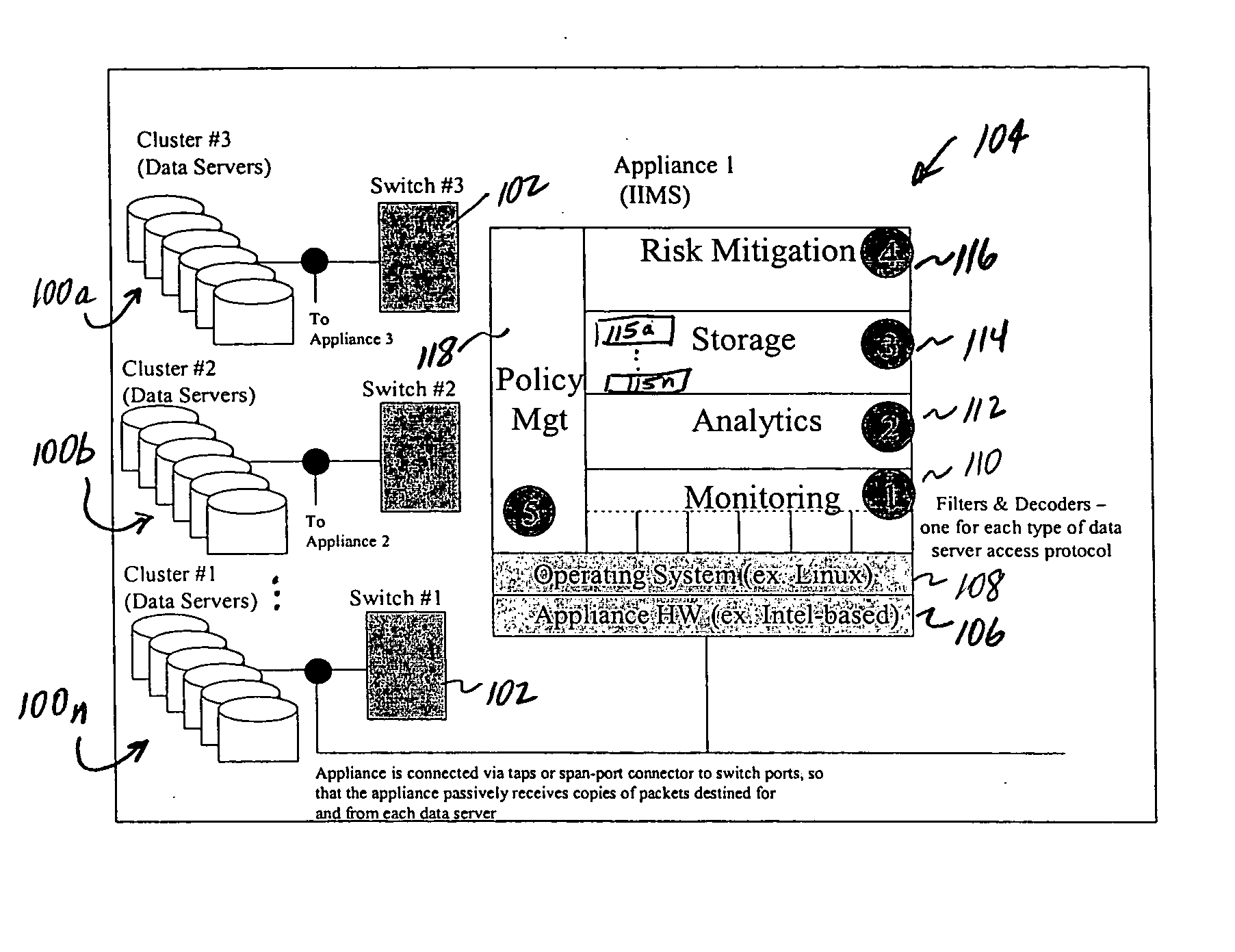
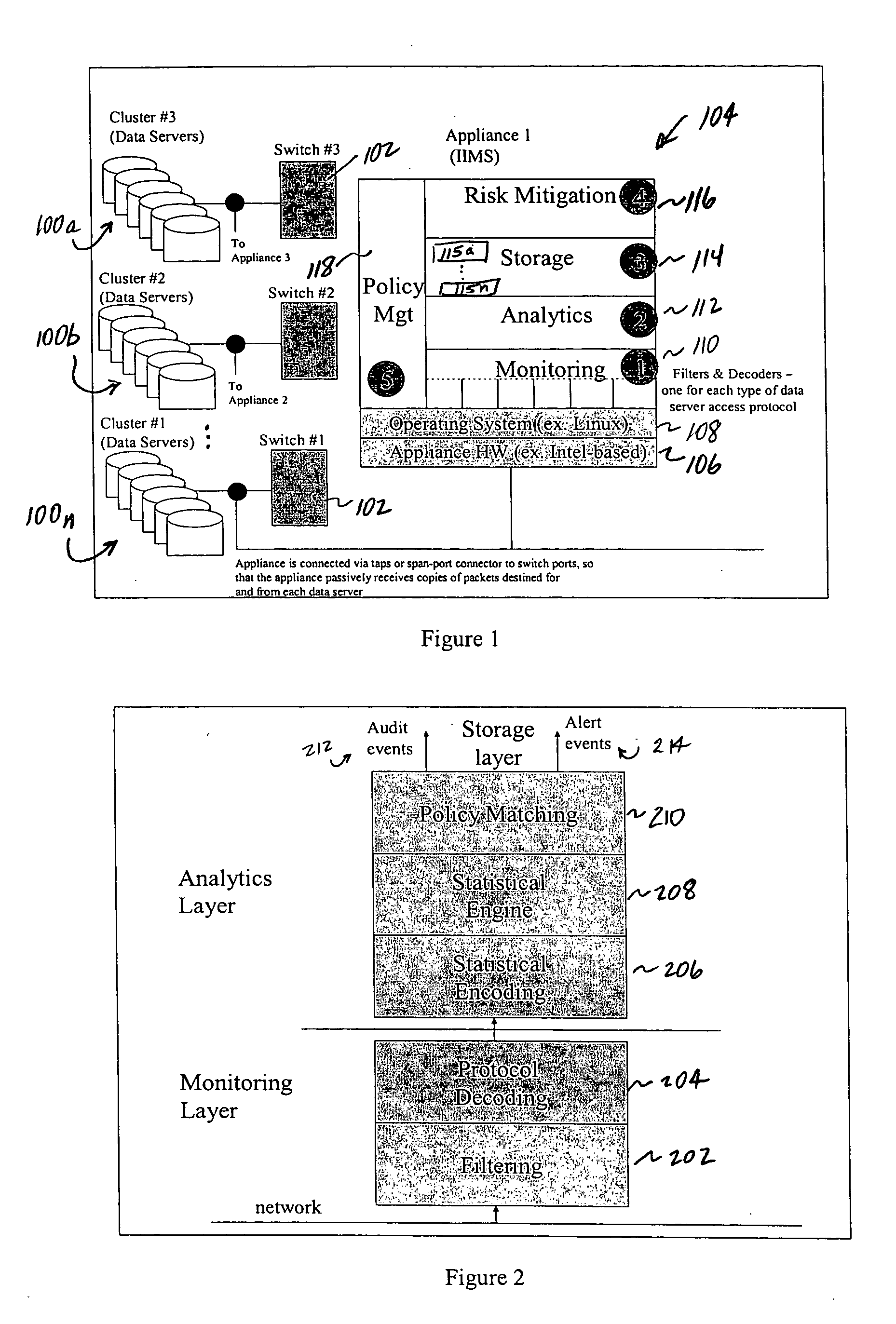
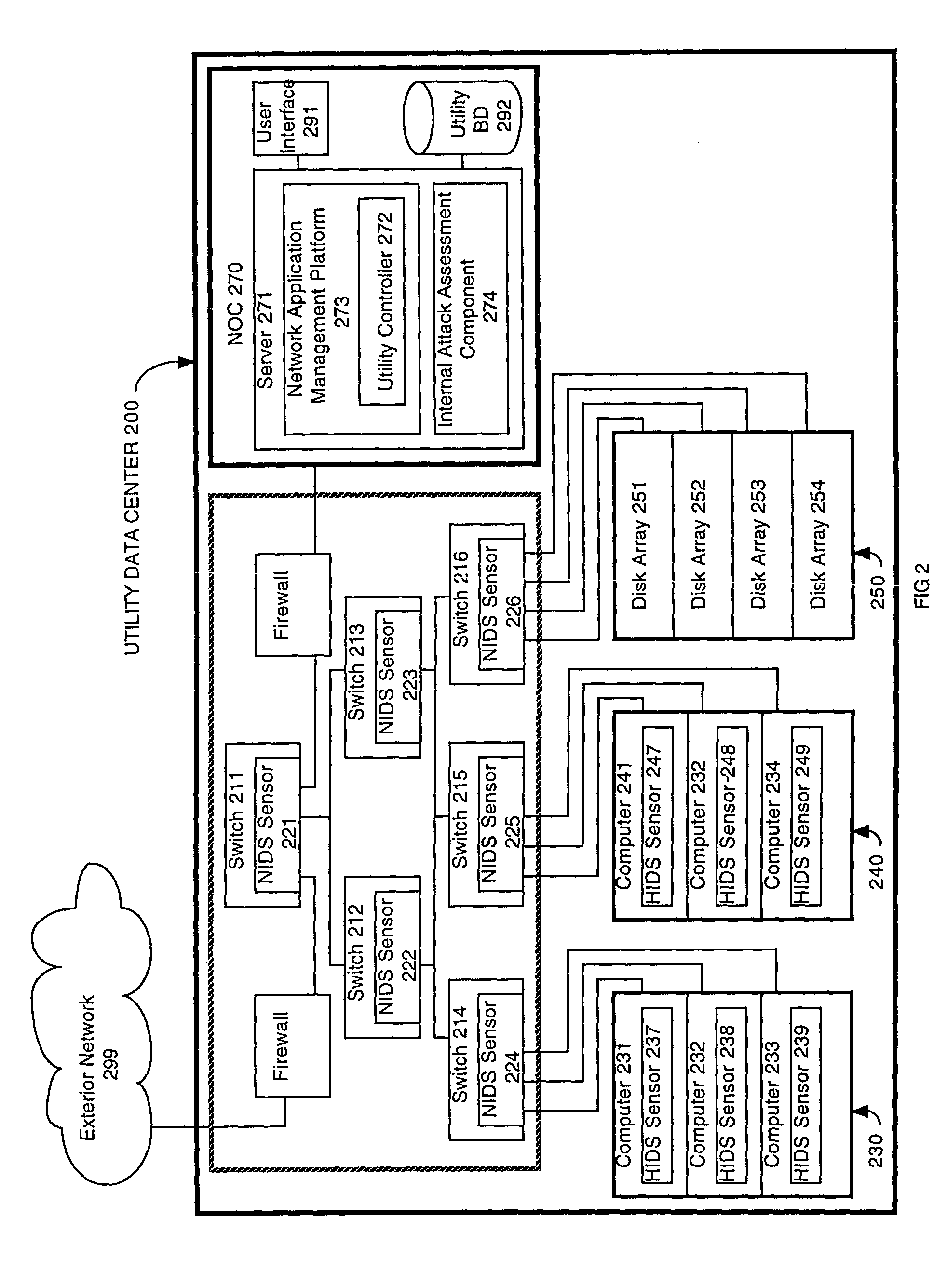
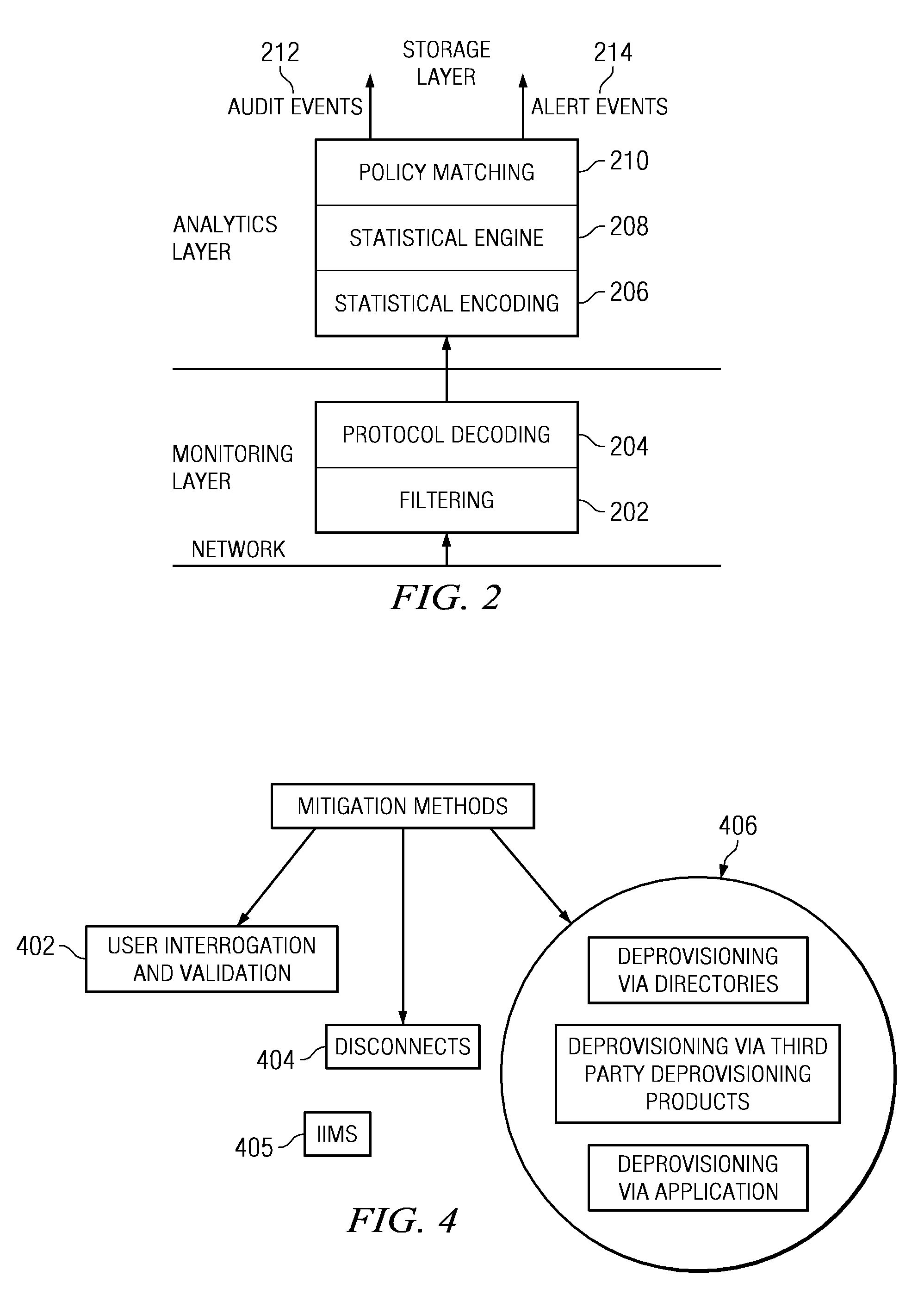
Method of and system for enterprise information asset protection through insider attack specification, monitoring and mitigation
ActiveUS20050071643A1Reduce harmComputer security arrangementsSecret communicationData accessAttack strategy
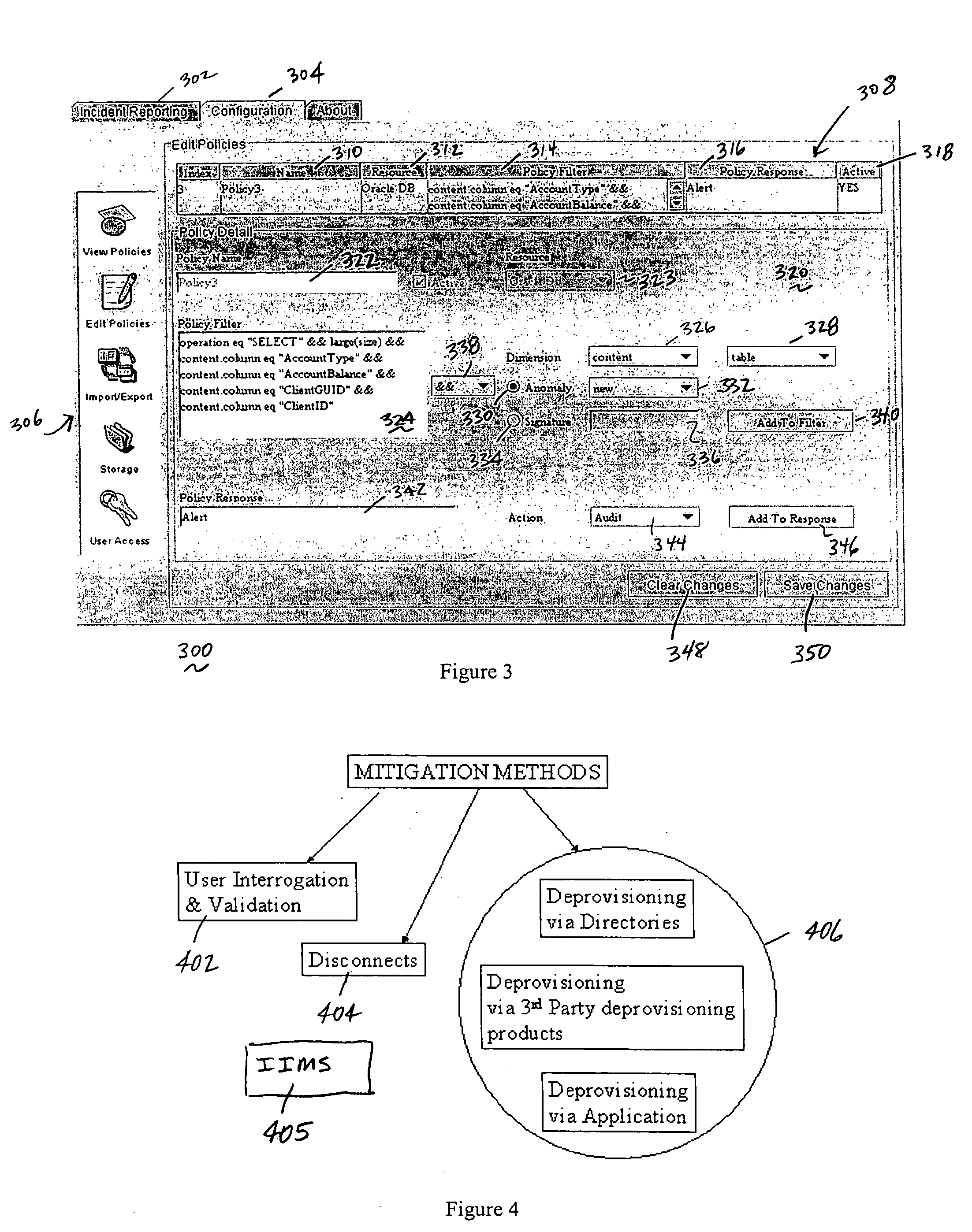
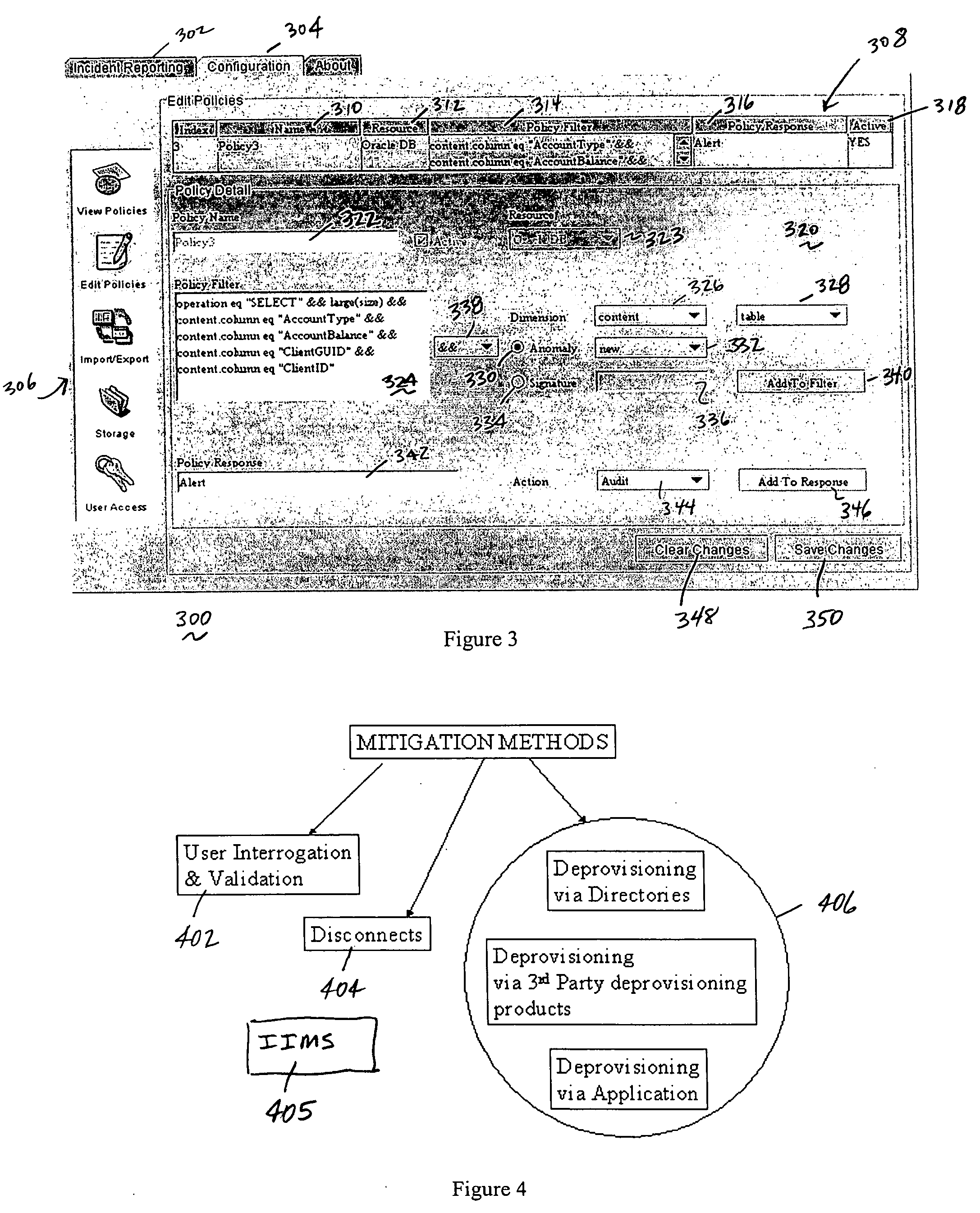
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of“anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
Real-time mitigation of data access insider intrusions
ActiveUS20050071642A1Reduce harmDigital data processing detailsComputer security arrangementsData accessInsider attack
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, network re-routing, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
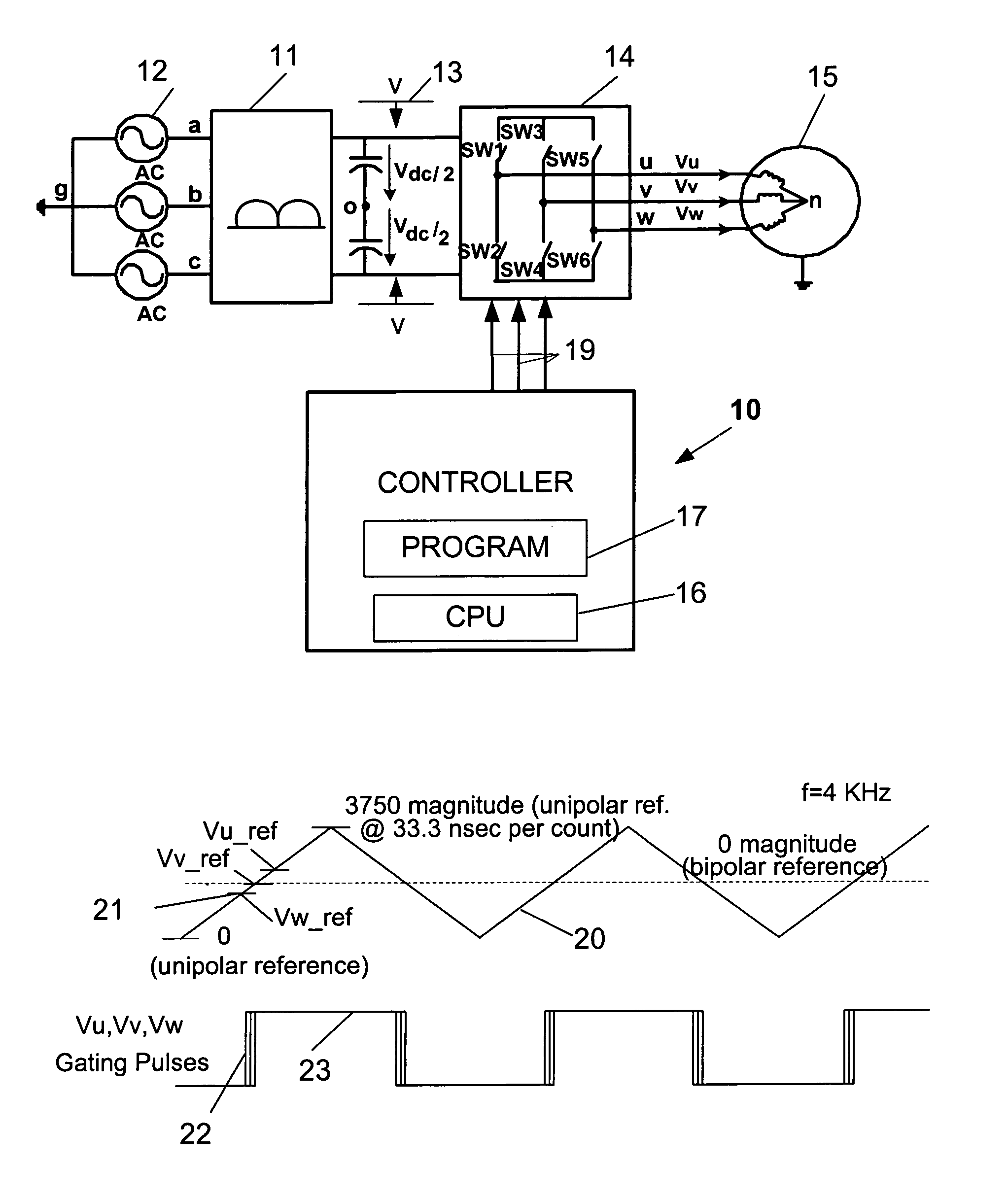
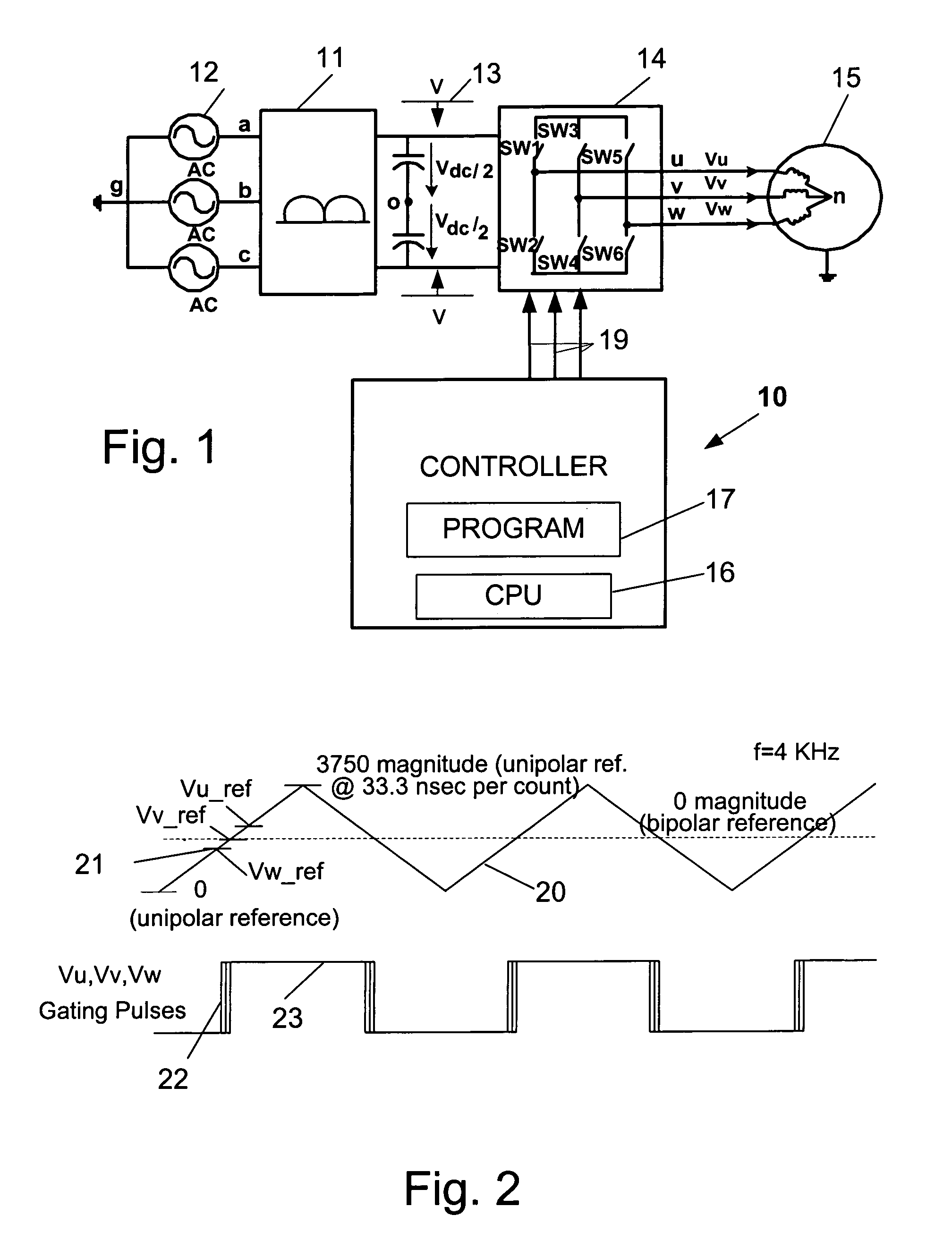
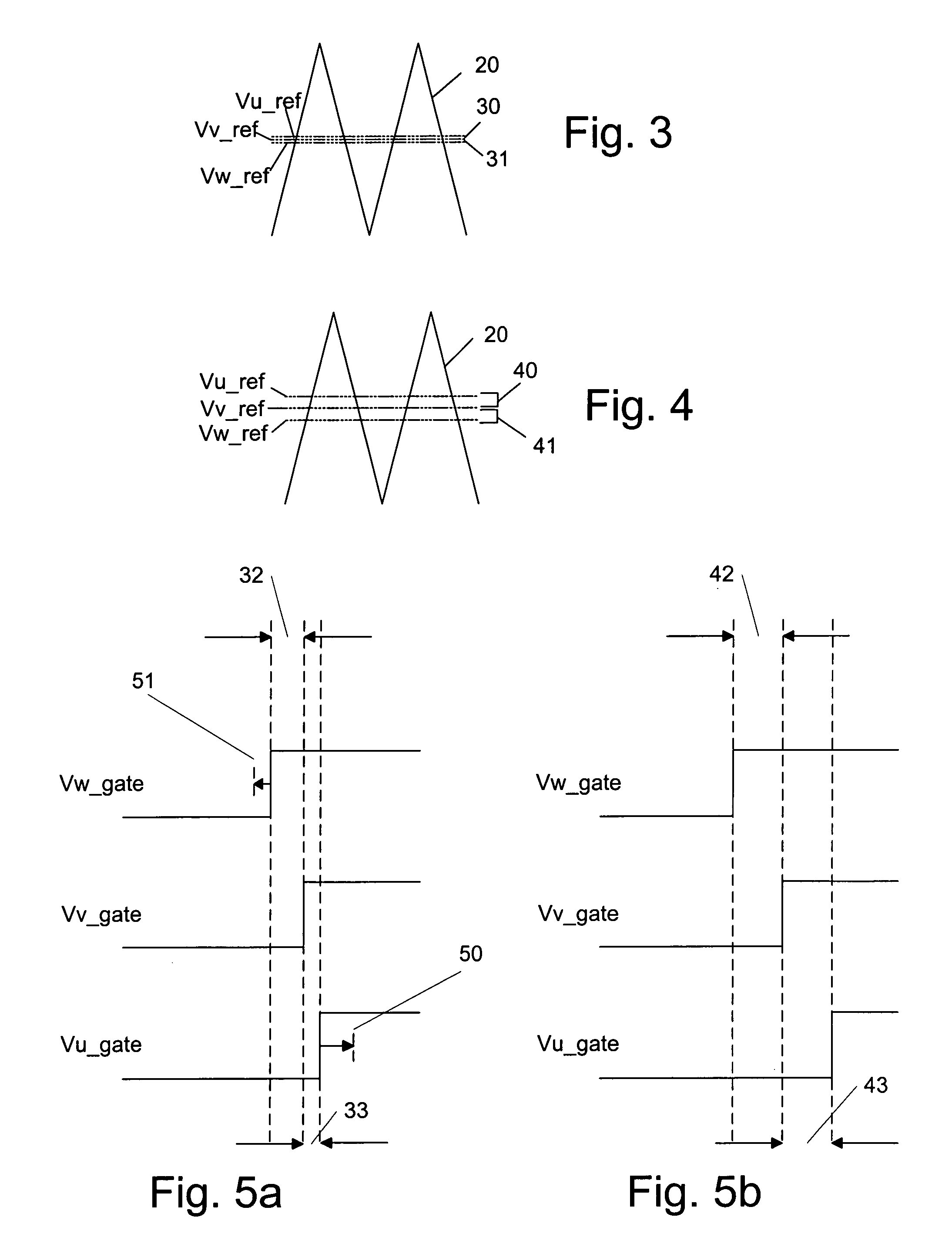
Adjusting gate pulse time intervals for reflected wave mitigation
ActiveUS7034501B1Reduce the impactReduce impactMotor/generator/converter stoppersAC motor controlOvervoltageMinimum time
Methods and apparatus for controlling switching in a DC-to-AC inverter to prevent overvoltages applied to an AC motor by determining the switching order of the phase voltage signals, providing gating signals at switching intervals by modulating a carrier wave with the phase voltage signals, comparing the switching intervals to a predetermined minimum time interval sufficient for reflected wave transients to dissipate, and adjusting the switching intervals to be at least equal to the predetermined minimum time interval.
Owner:ROCKWELL AUTOMATION TECH
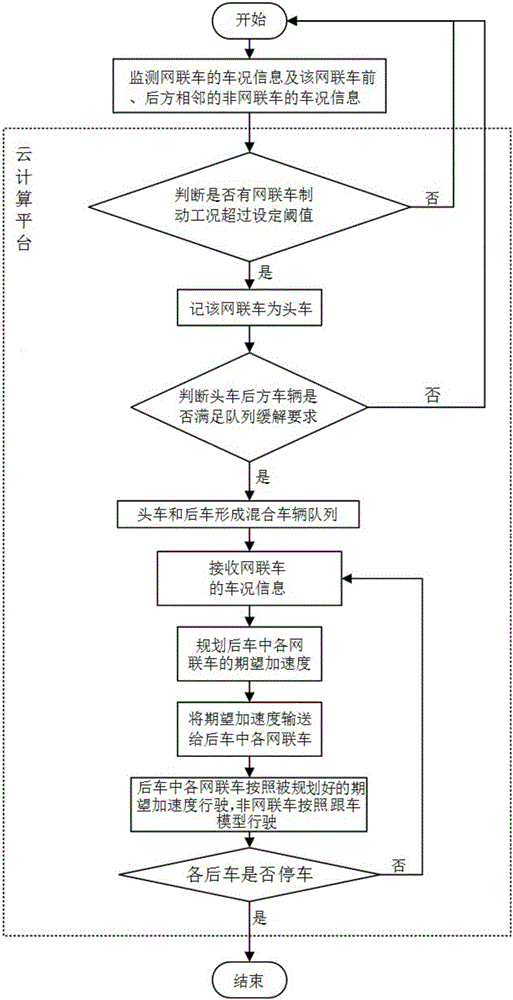
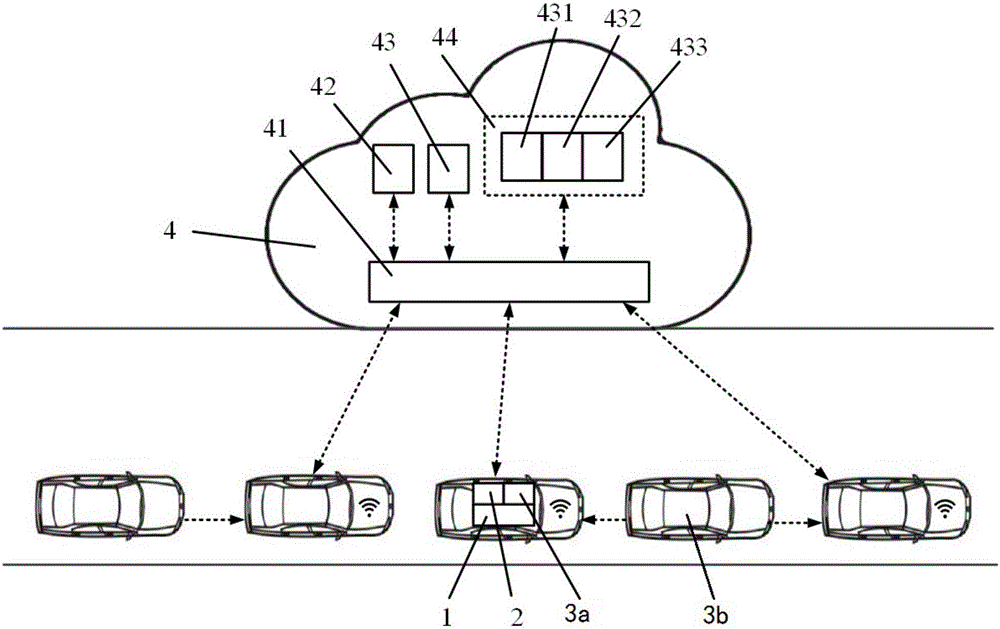
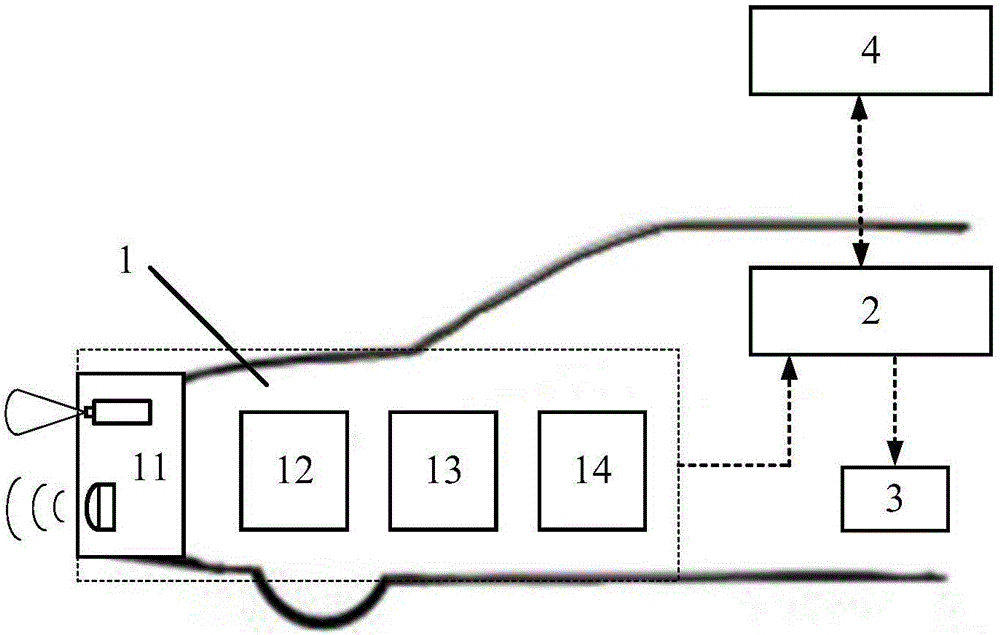
Collision relieving method and device between vehicles in hybrid vehicle queue
ActiveCN105774800AImprove access delayHigh communication rateTransmissionNetwork connectionHybrid vehicle
The invention discloses a collision relieving method and device between vehicles in a hybrid vehicle queue. The collision relieving method between the vehicles in the hybrid vehicle queue includes the following steps that firstly, vehicle condition information of the network-connection vehicles and vehicle condition information of the non-network-connection vehicles in front of and behind the network-connection vehicles are acquired; secondly, the head vehicle and the rear vehicles in the hybrid vehicle queue are sequentially judged, if the corresponding network-connection vehicle is the head vehicle or the rear vehicles, the third step is executed, and if the corresponding network-connection vehicle is neither the head vehicle nor the rear vehicles, the first step is executed again, wherein the head vehicle is the network-connection vehicle with the braking working condition exceeding a set threshold value, and the rear vehicles are vehicles meeting the queue collision relieving requirement behind the head vehicle; thirdly, the vehicle condition information of the network-connection vehicles is received; fourthly, the expected acceleration of each network-connection vehicle in the rear vehicles is planned; fifthly, each network-connection vehicle in the rear vehicles travels according to the planned expected acceleration, and the each network-connection vehicle in the rear vehicles travels according to a vehicle following mode; and sixthly, whether each of the rear vehicles is parked or not is judged, if certain rear vehicles are parked, control is stopped, and if no rear vehicles are parked, the third step is executed again. By the adoption of the method and device, the braking space between the vehicles in the hybrid vehicle queue can be used for control.
Owner:TSINGHUA UNIV
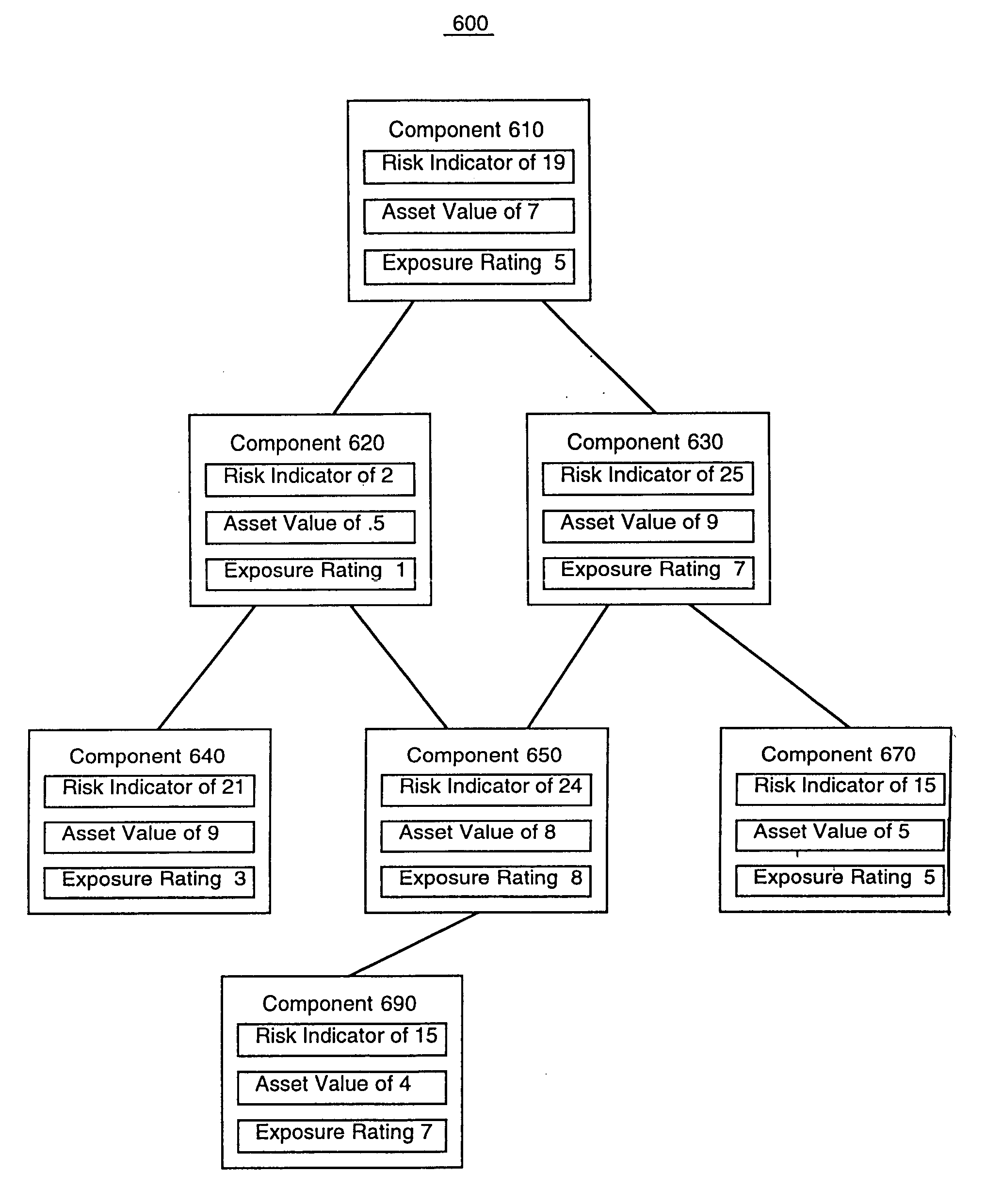
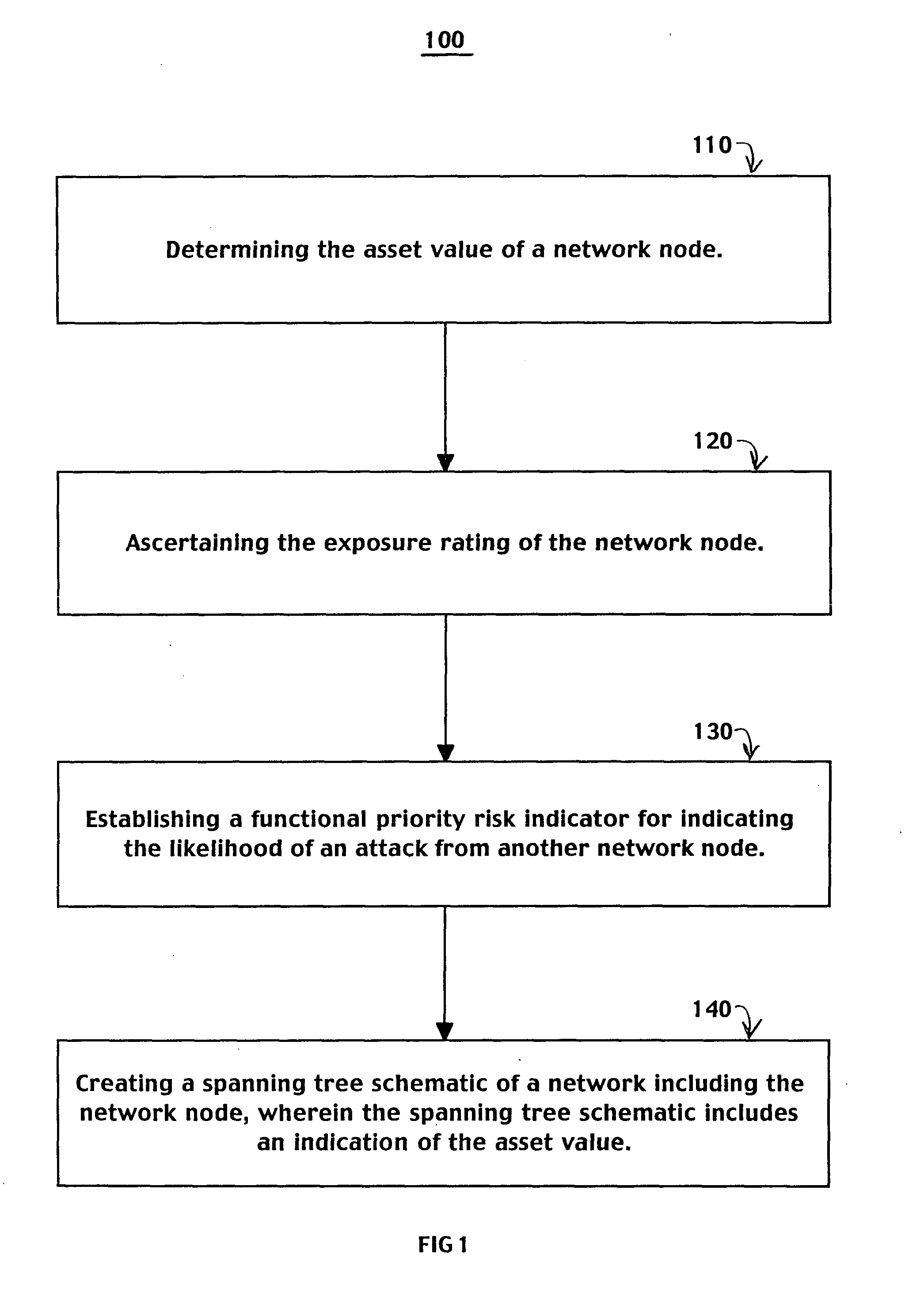
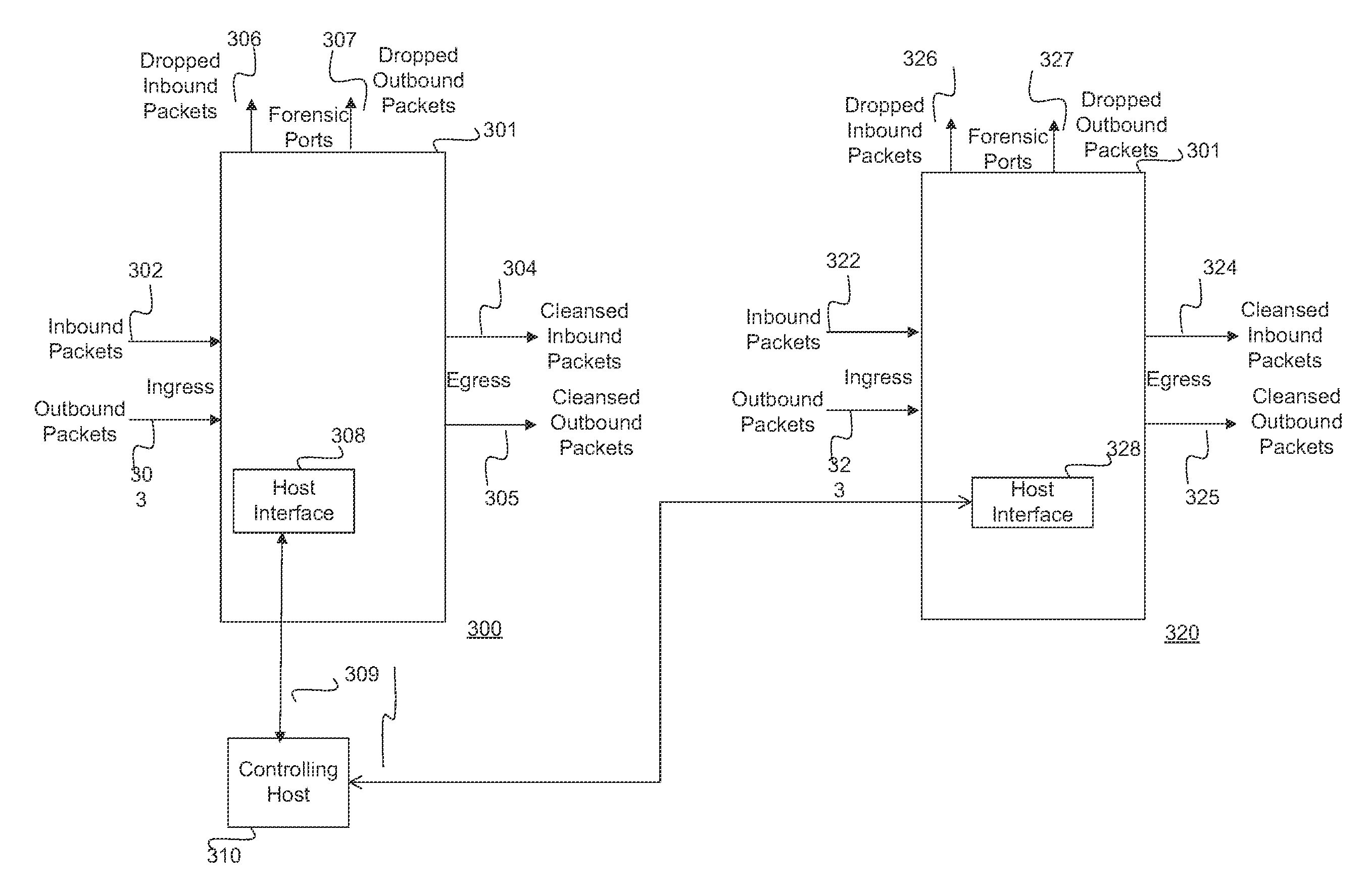
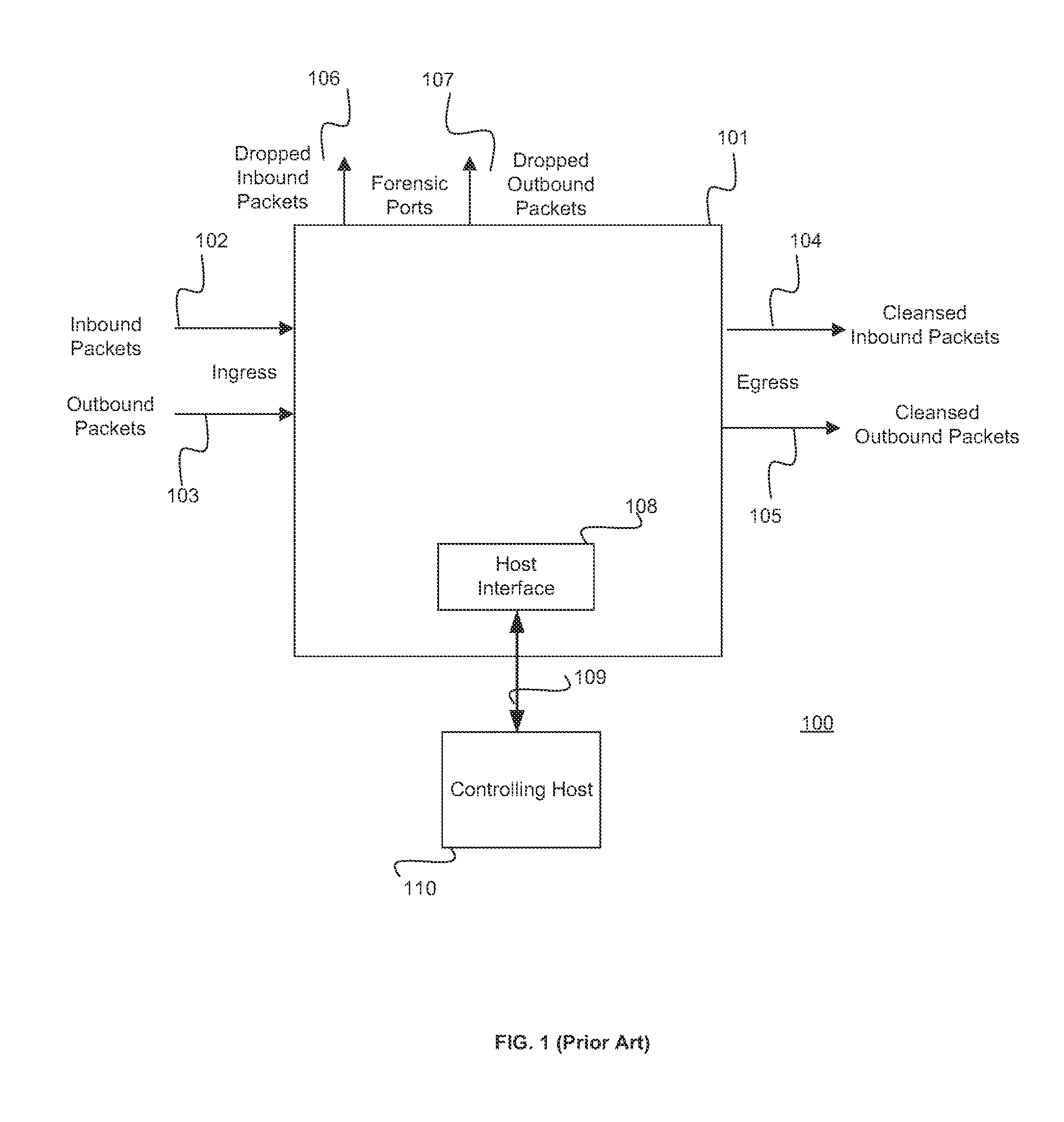
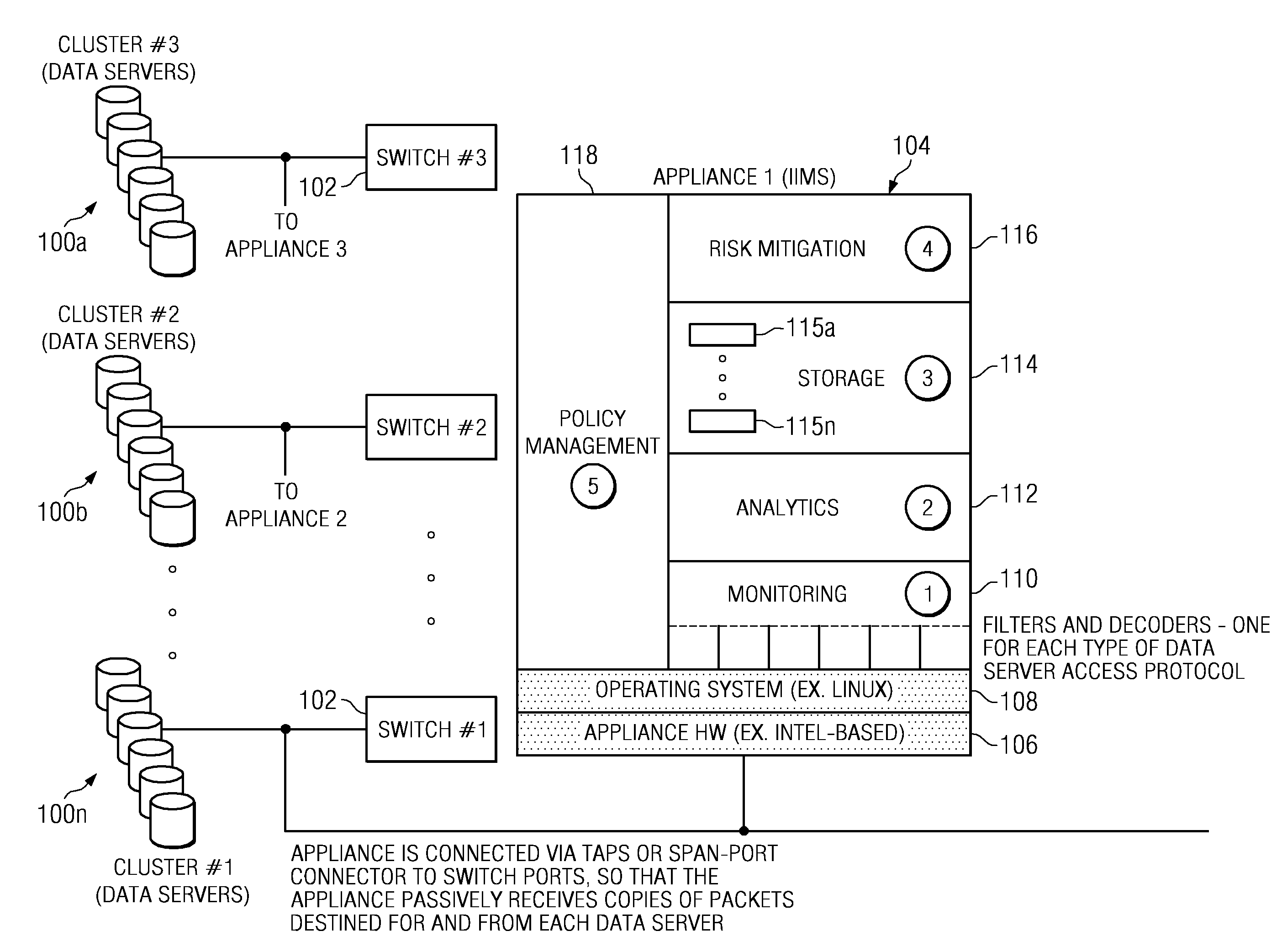
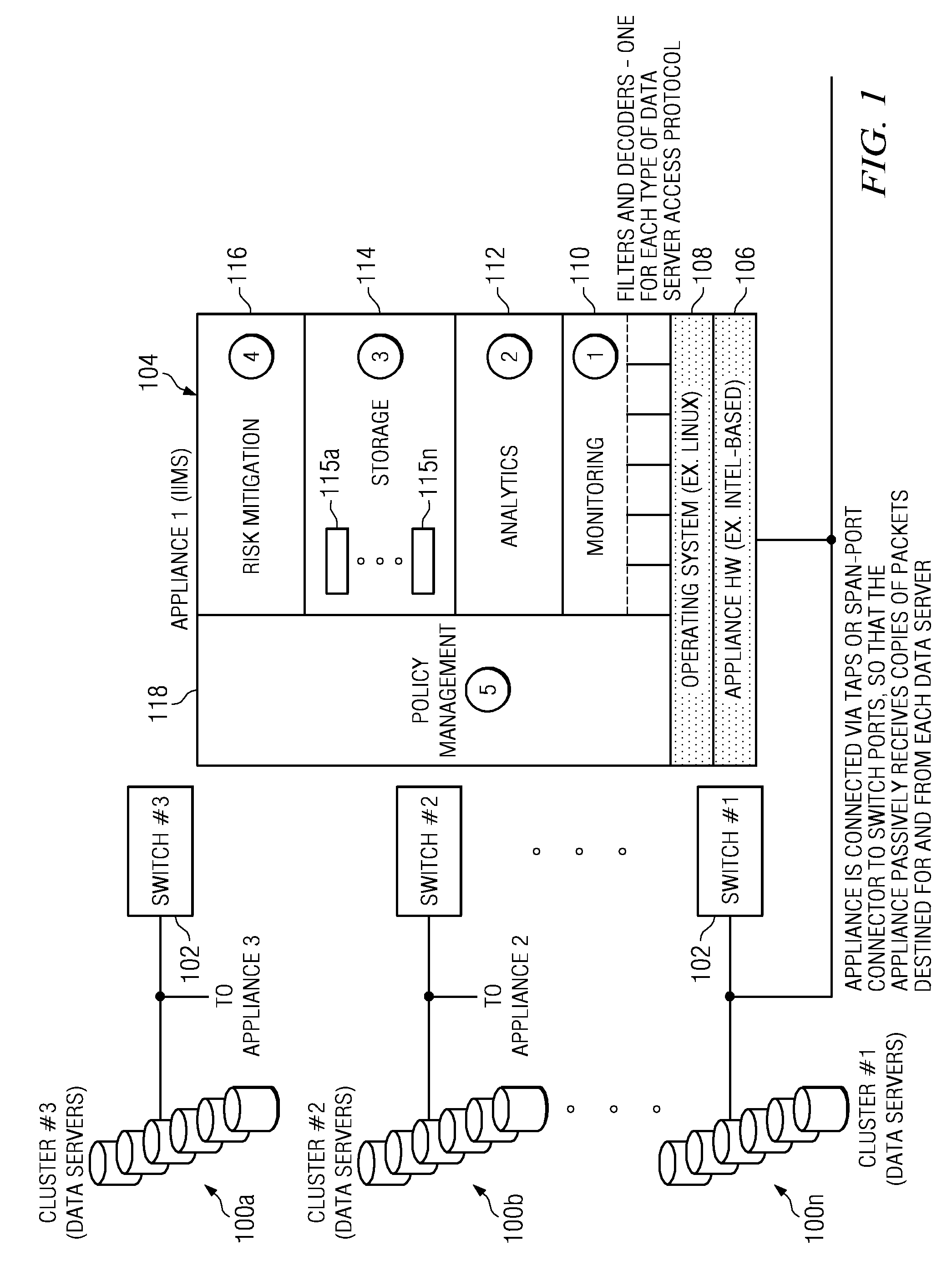
Security intrusion mitigation system and method
ActiveUS20050050351A1Reduce attackReduce diffuseMemory loss protectionDigital data processing detailsDiffusionComputer network
A security intrusion mitigation system and method are presented. In one embodiment a security intrusion mitigation method includes utilizing network spanning tree configuration information to determine an action for mitigating diffusion of intrusive attacks. The spanning tree information can include an indication of an internal diffusion risks. An action for mitigating diffusion of intrusive attacks is automatically performed. The action for mitigating diffusion of the intrusive attacks includes compensation for functional support of prioritized applications.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
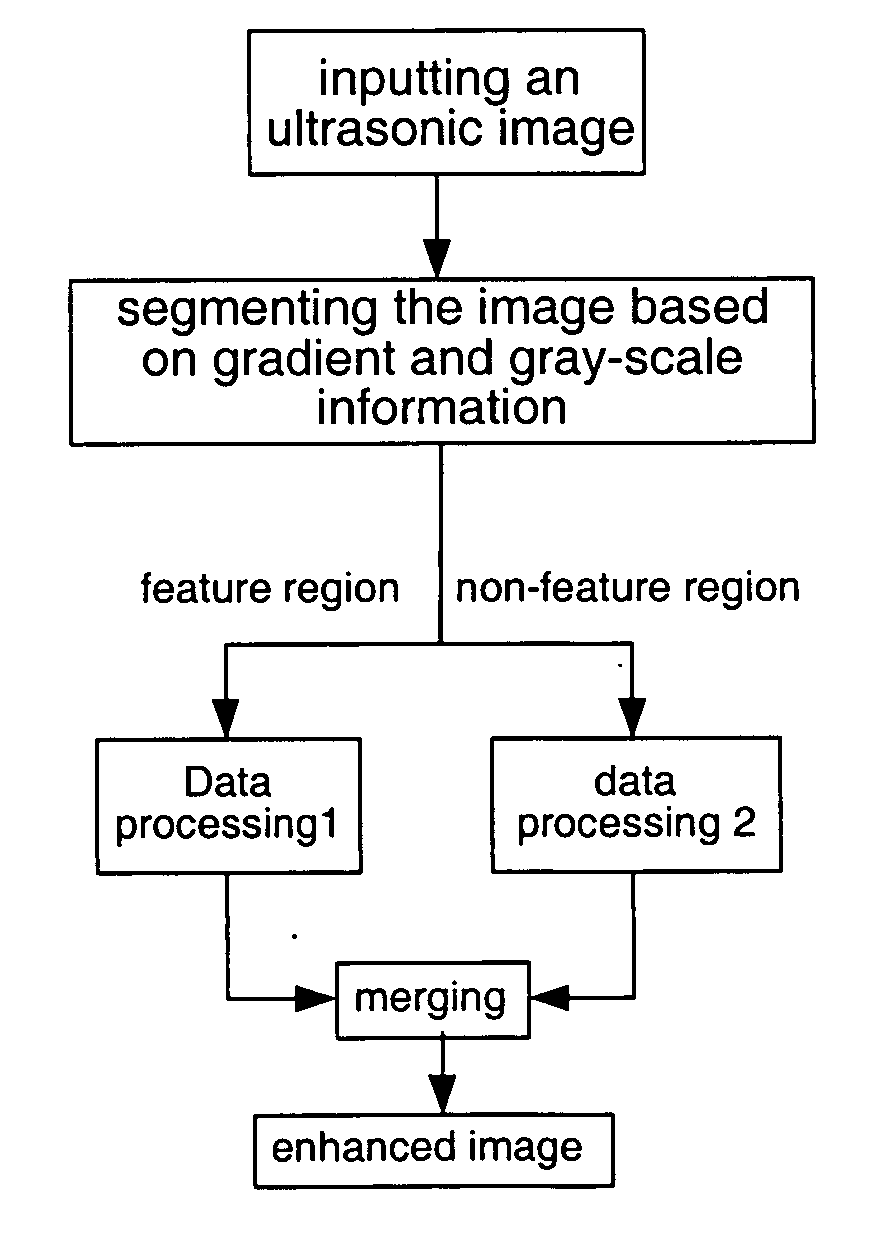
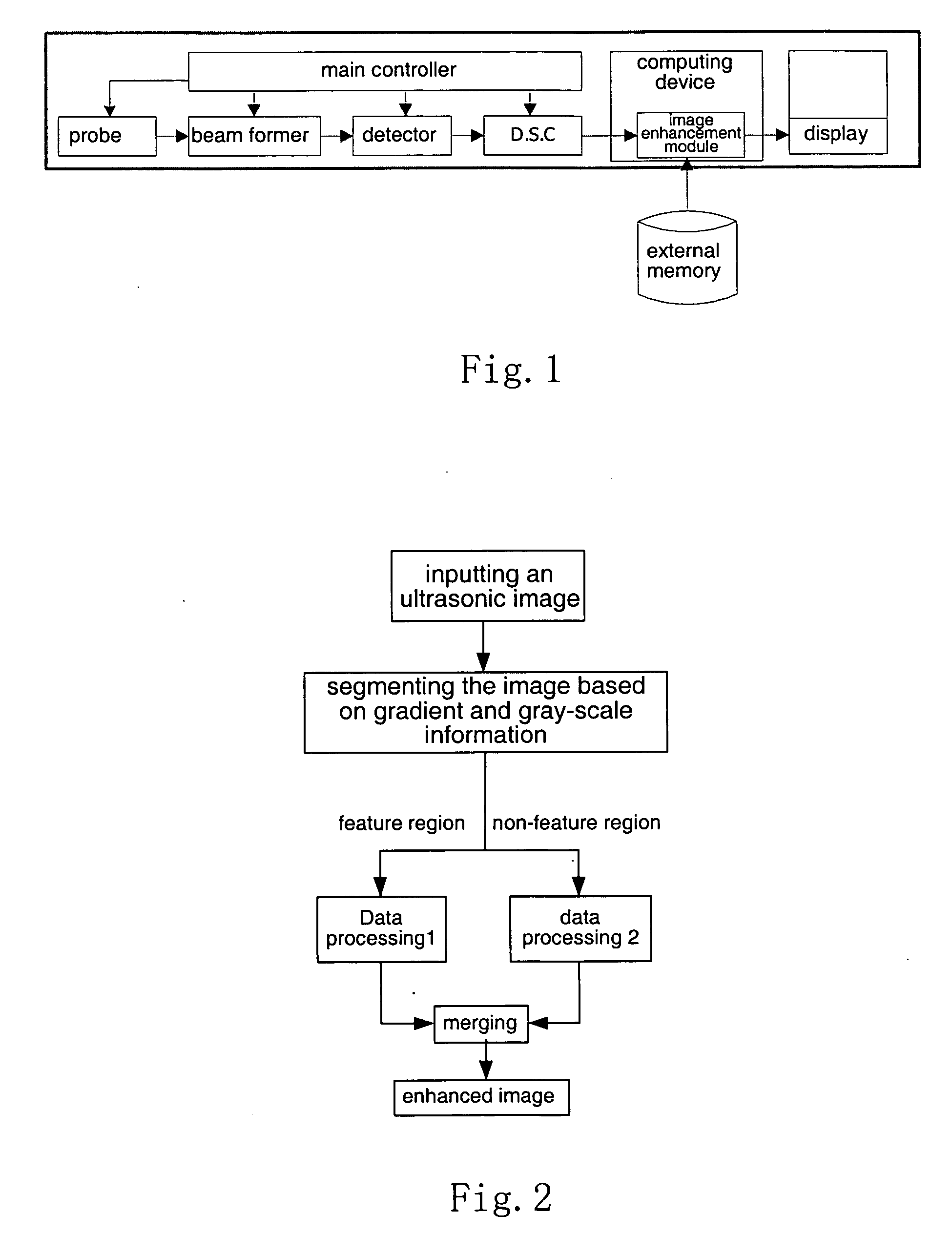
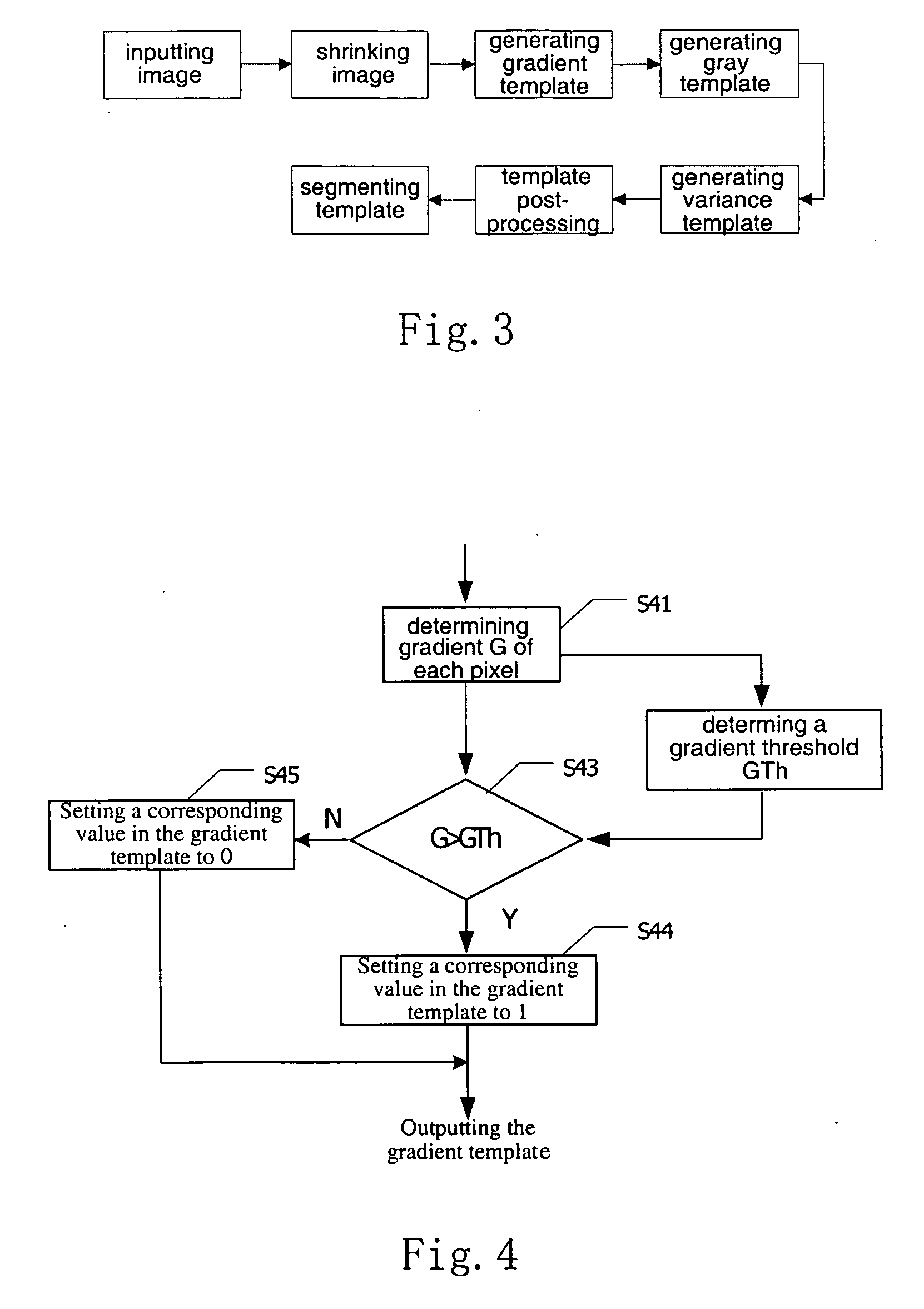
Ultrasound image enhancement and speckle mitigation method
ActiveUS20070065009A1Enhanced Ultrasound ImagingTake advantage ofUltrasonic/sonic/infrasonic diagnosticsImage enhancementSonificationImage segmentation
A method for enhancing an ultrasound image is provided, wherein the ultrasound image is segmented into a feature region and a non-feature region, while sufficiently utilizing features contained in the ultrasound image, in particular including some inconspicuous features. The enhanced image according to present invention is not susceptive of the image segmentation and avoid dependence of the enhancement effect on the segmentation template, so as not to produce an evident artificial boundary between the feature region and the non-feature region but to highlight some special information in the image and to remove or mitigate invalid information. Thus the enhanced ultrasound image is particularly suitable for the visual system of the human beings.
Owner:SHENZHEN MINDRAY BIO MEDICAL ELECTRONICS CO LTD
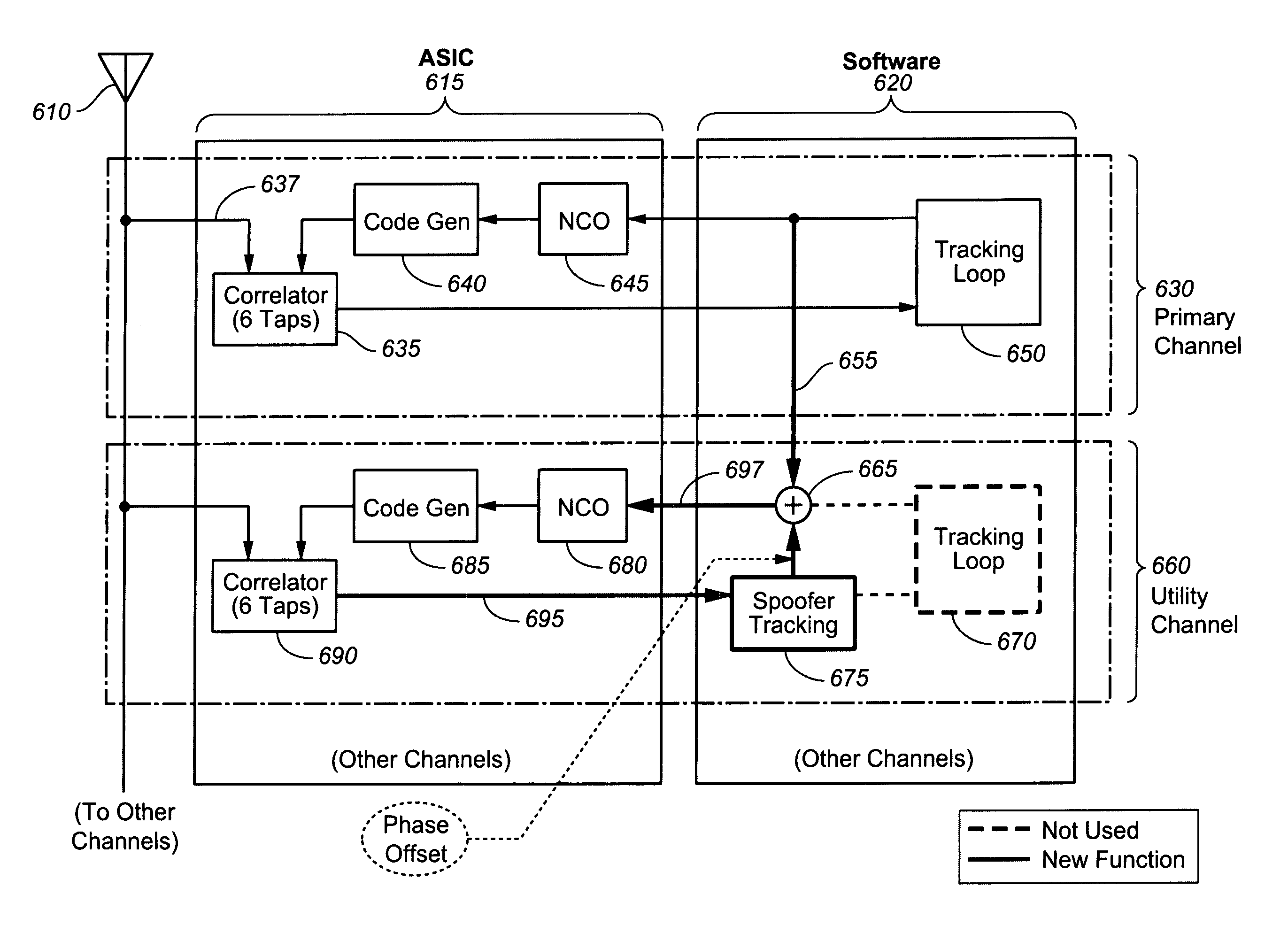
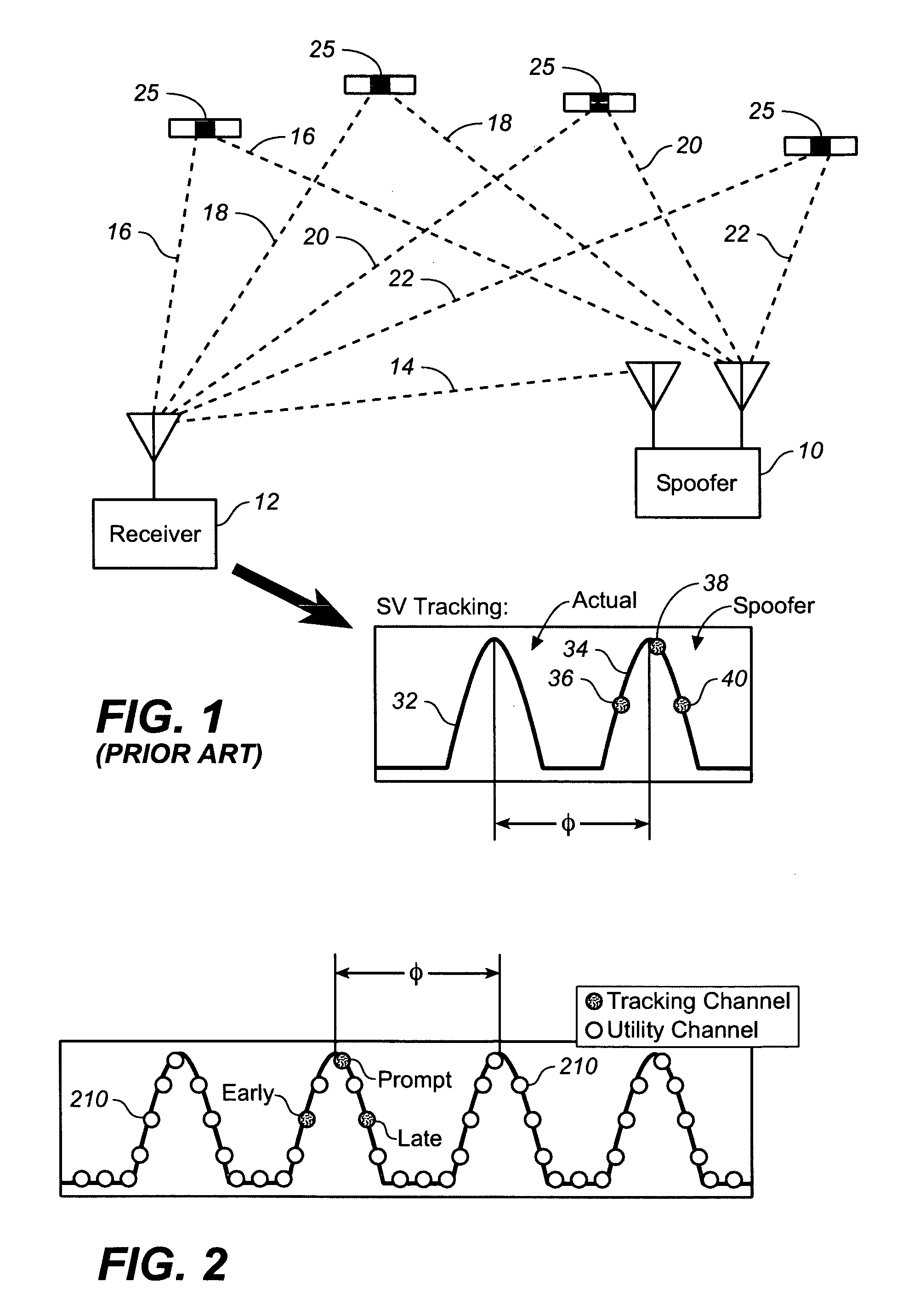
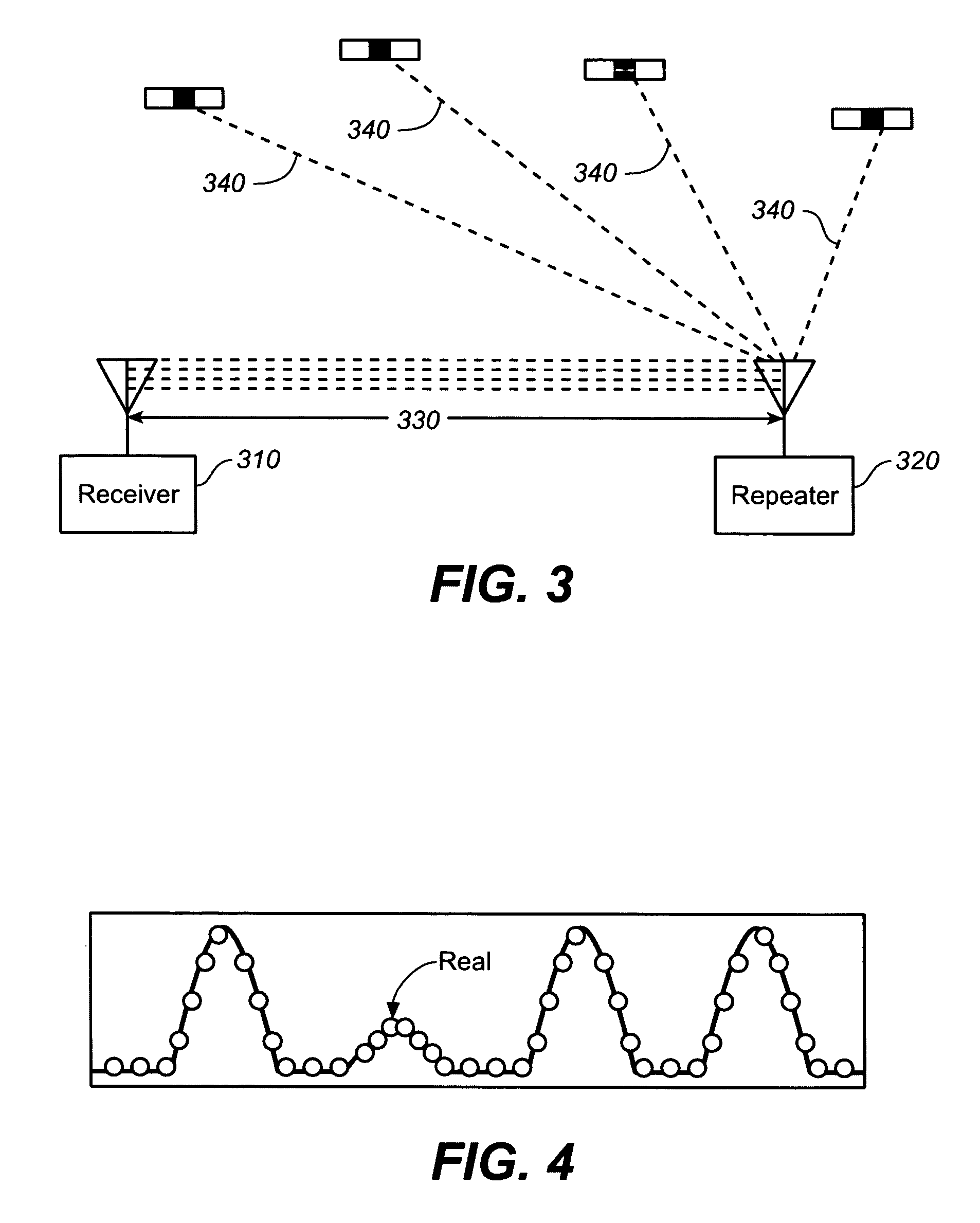
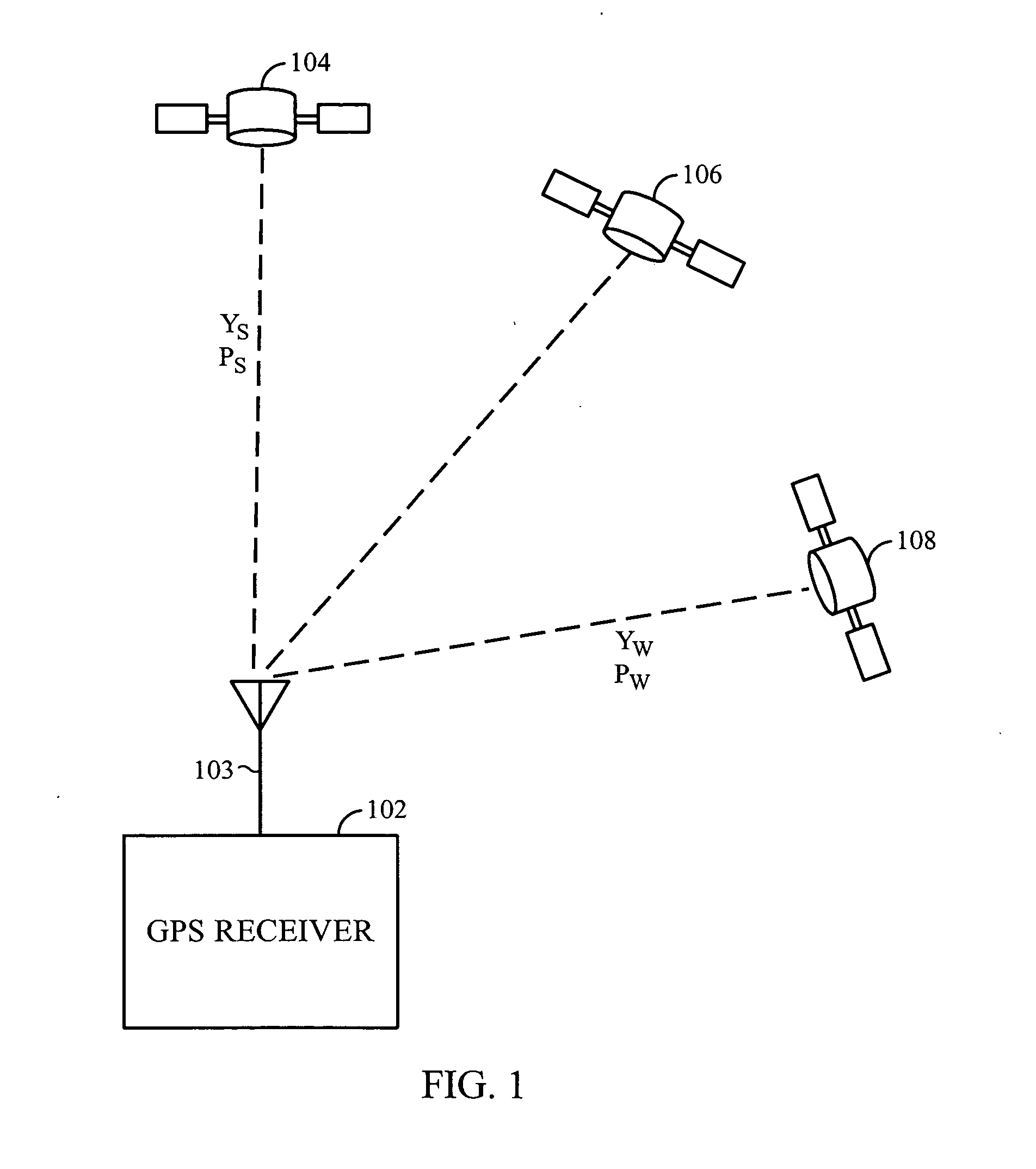
Advanced spoofer mitigation and geolocation through spoofer tracking
ActiveUS7764224B1Mitigating spoofingRadio wave direction/deviation determination systemsPosition fixationGps receiverNuller
A GPS receiver employing advanced spoofer mitigation, geolocation and tracking capabilities through the use of a utility channel coupled in parallel to a tracking channel. The tracking channel tracks the direct signal while the utility channel tracks one or more spoofer signals. A signal from the primary channel is used by the utility channel to locate spoofer signals, with the primary channel operating independently of the utility channel. Three complementary spoofer mitigation methods are disclosed for identifying advanced repeaters and security-compromised spoofers, which may also be used for geolocation of such spoofers: (1) the consistency routine; (2) the nuller routine; and (3) the multiple antennas routine. An improved architecture is disclosed to allow easy upgrading and retrofitting of an existing GPS receiver.
Owner:ROCKWELL COLLINS INC
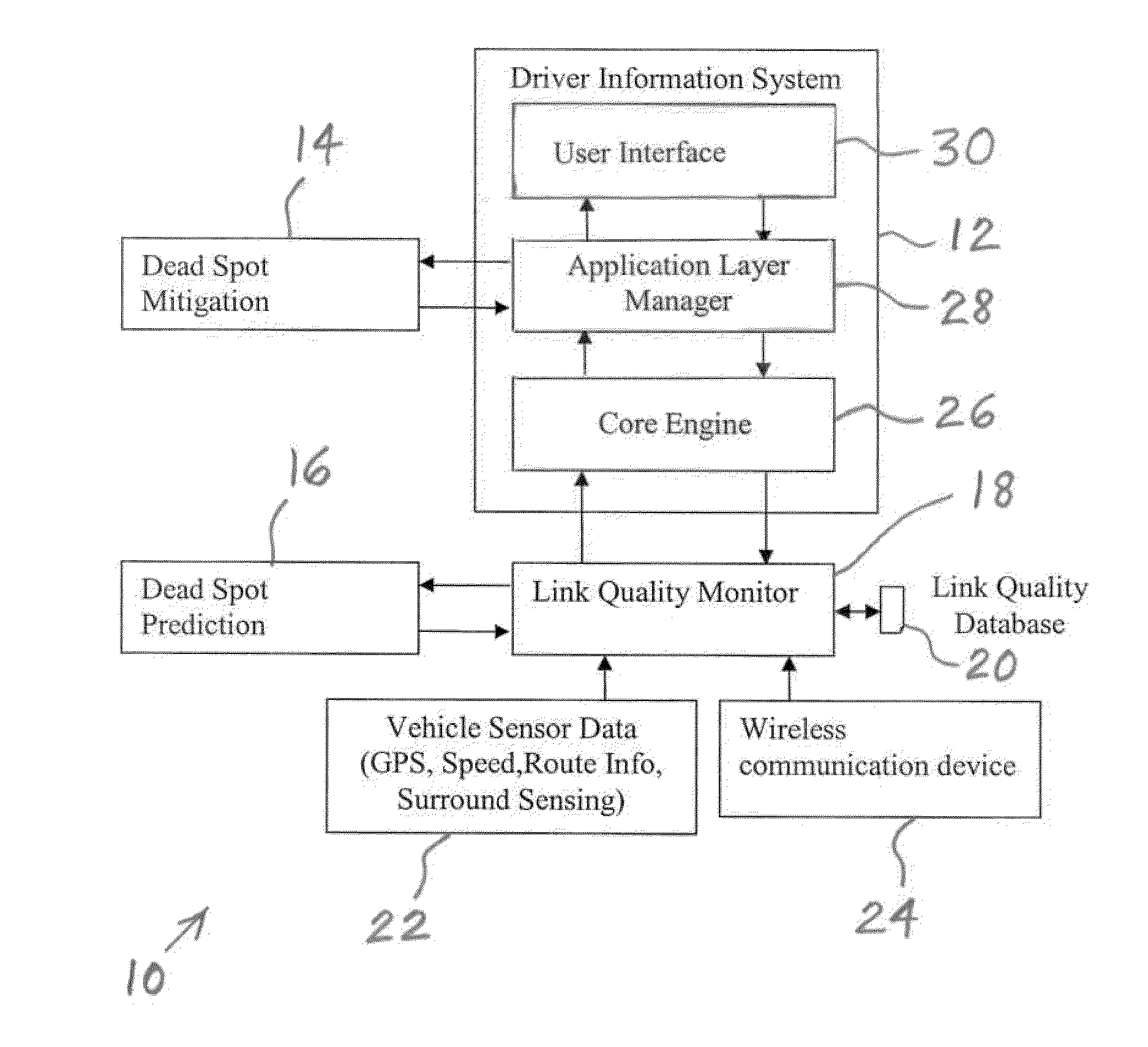
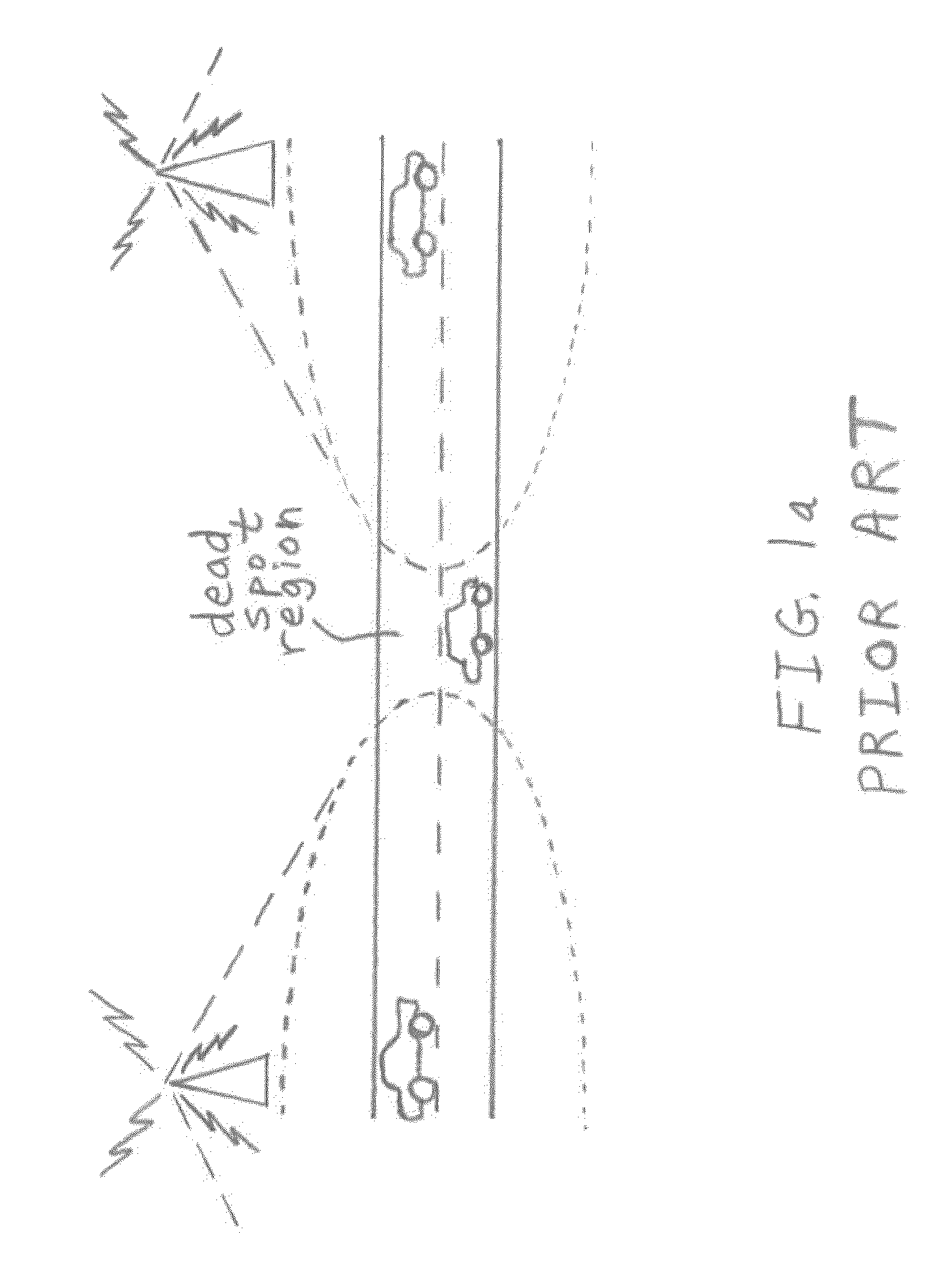
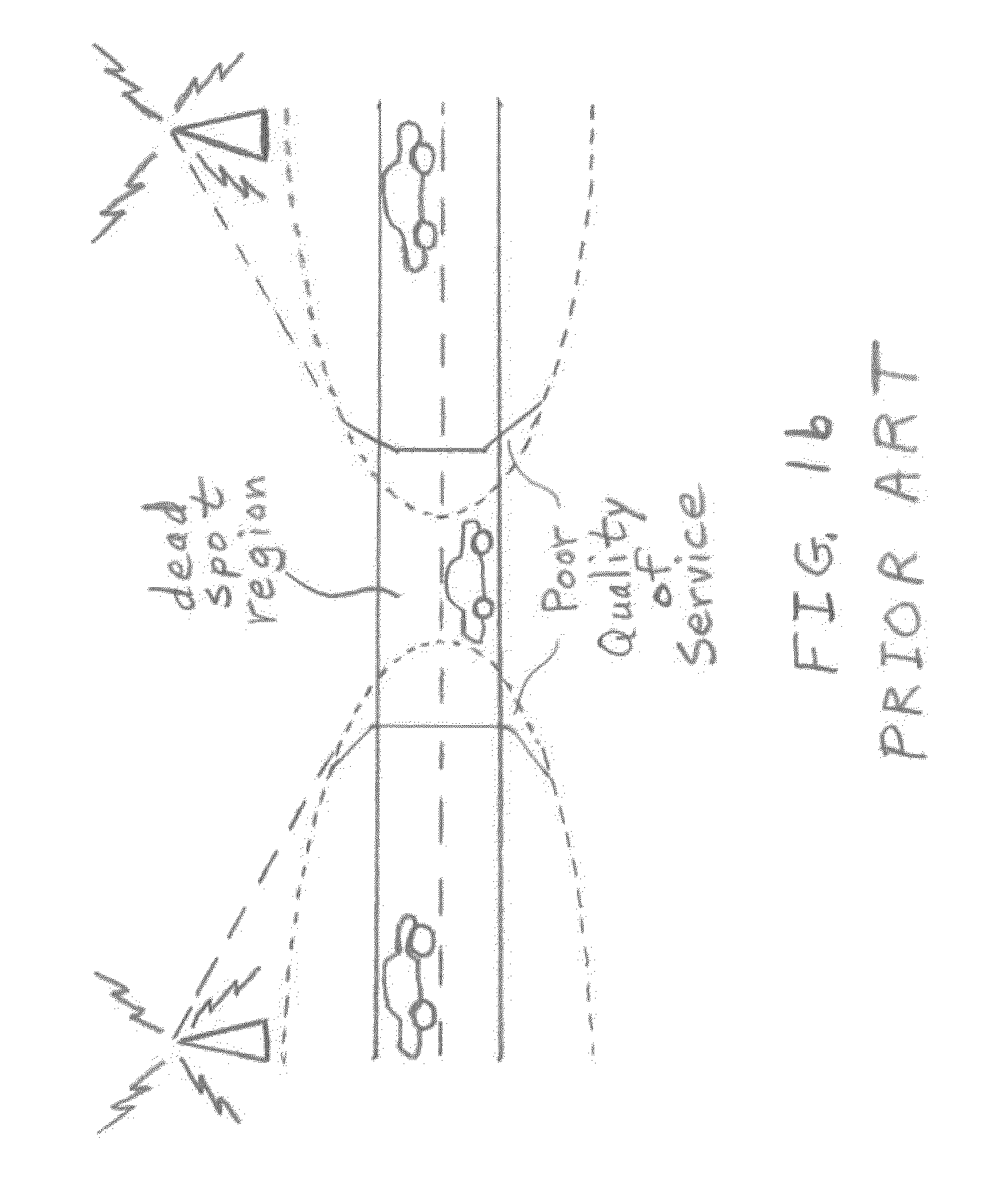
Dead spot mitigation methods for media applications in vehicular environments
ActiveUS20110167128A1Easy to moveImprove performanceInstruments for road network navigationMultiple digital computer combinationsWireless connectivityReal-time computing
A wireless communication method has computer-implemented steps including identifying a location of a dead spot region within an expected route of a vehicle. The vehicle has a loss of wireless connectivity within the dead spot region. Lengths of time before the vehicle will arrive at the dead spot region and before the vehicle will exit the dead spot region are estimated. Audio content and / or video content are accessed from at least one source inside the vehicle and / or at least one source outside the vehicle such that playing of the content is uninterrupted while the vehicle is within the dead spot region, the accessing being dependent upon the estimated lengths of time.
Owner:ROBERT BOSCH GMBH
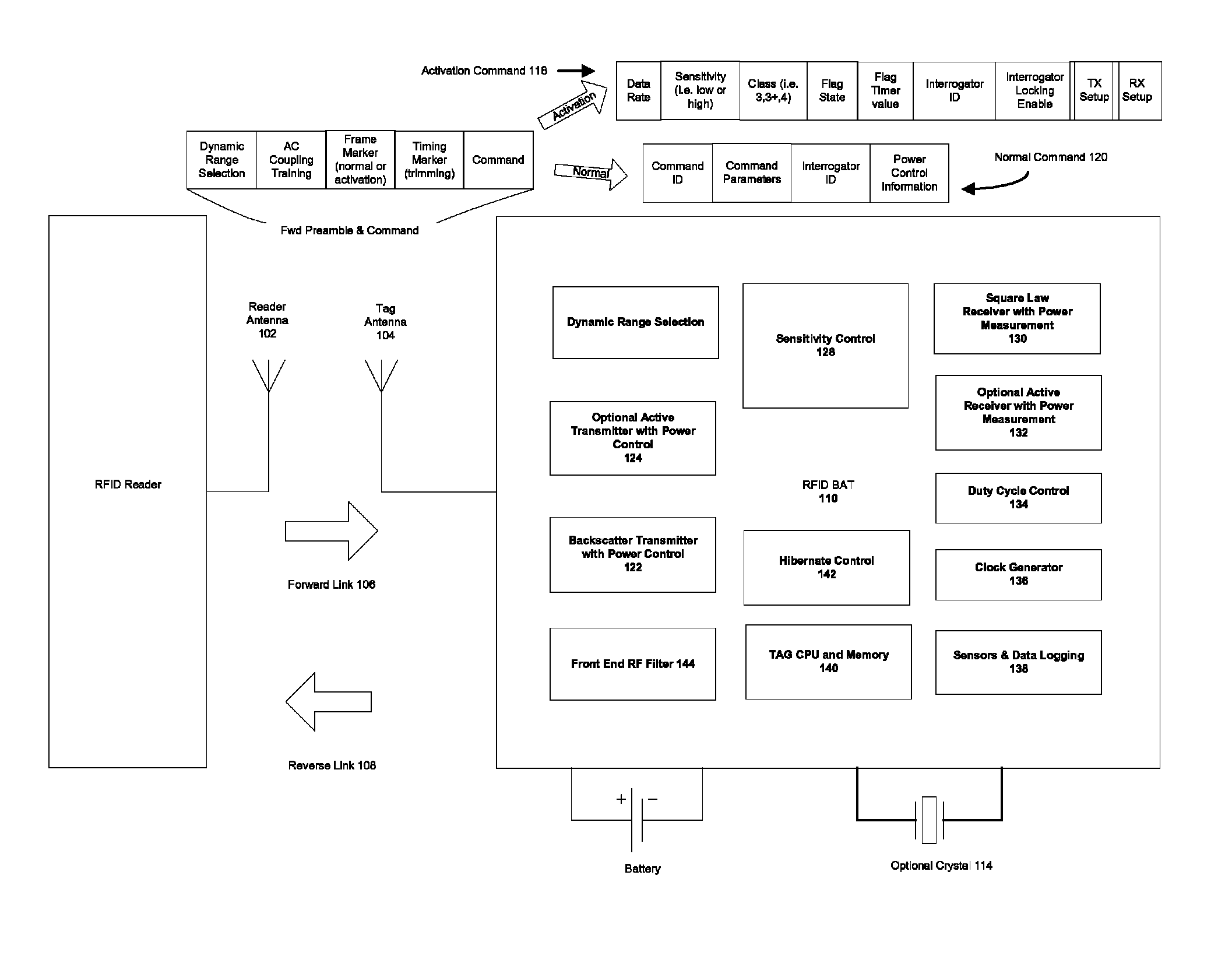
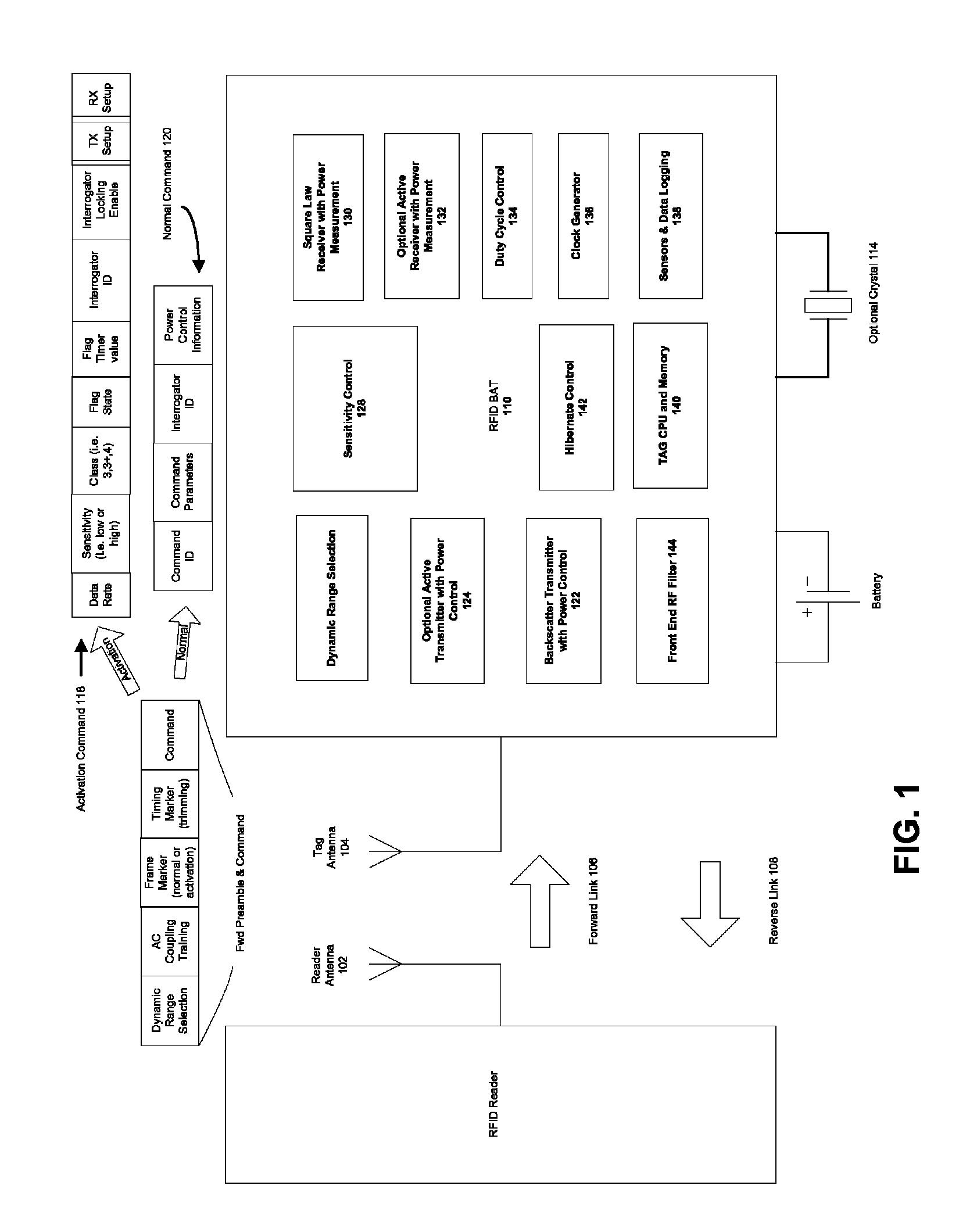
Battery assisted RFID system RF power control and interference mitigation methods
ActiveUS8410906B1Easy to operateIntermediate level of performanceMultiplex system selection arrangementsRadio transmissionTransmitted powerBiological activation
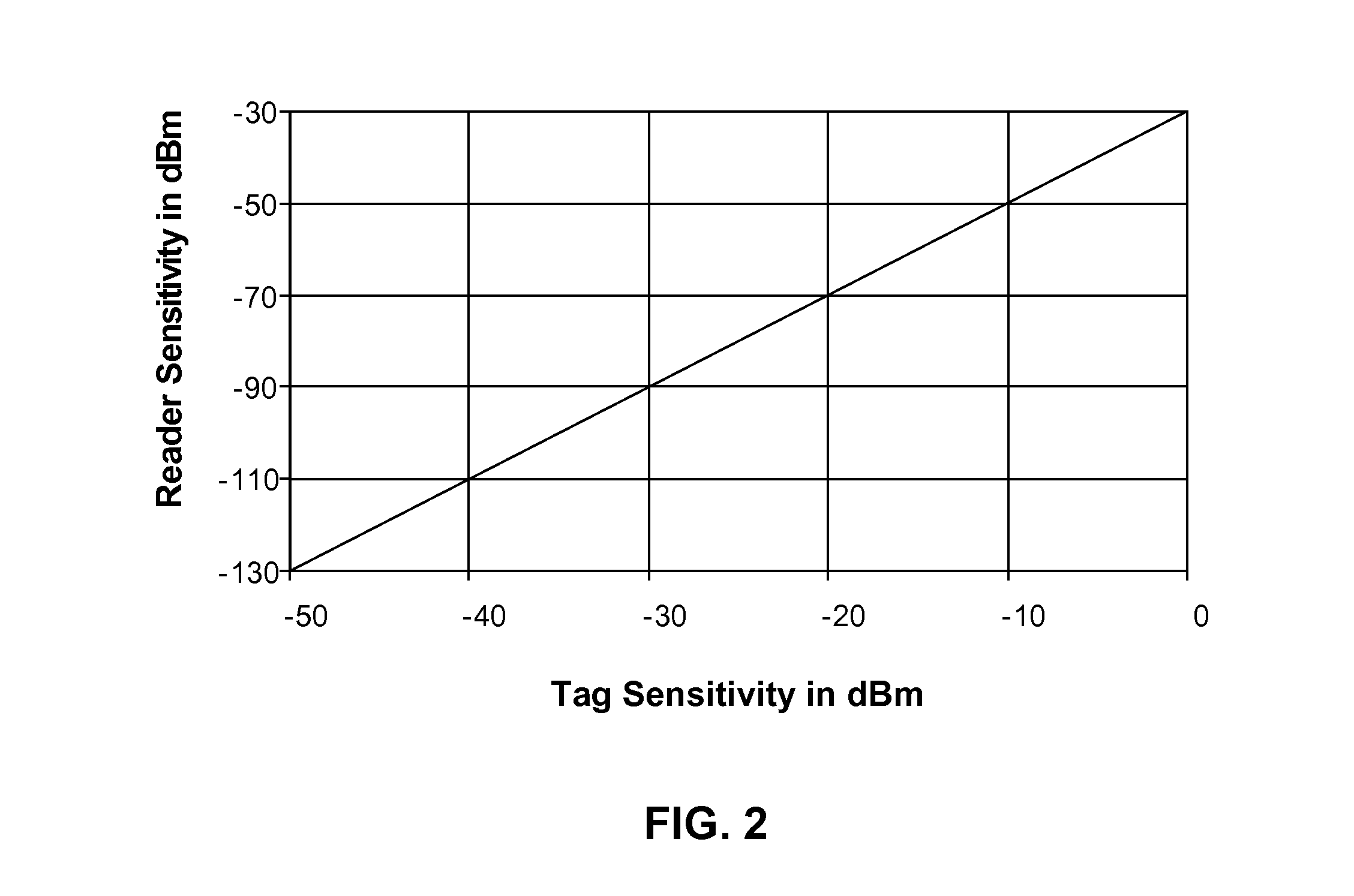
The present invention discloses battery assisted RFID system RF power leveling methods that optimize the amount of transmitted power and interference from a reader in relation to the sensitivity of the RFID tags, their ranges from the reader, and the unique physics of the backscatter RFID radio link. These methods enhance system reliability when employing battery assisted RFID tags that operate with sensitive transistor based square law tag receivers and highly sensitive RFID readers intended to take advantage of outstanding tag sensitivity. Further enhancement is achieved via design of system command sets and tag state machine behavior that optimally support the power level operations, power level operations that span across tag hibernation and normal modes, and that otherwise control system interference. Embodiments of the present invention are also enhanced with receiver training and synchronizing methods suited to the high tag sensitivity and need for dynamic range state switching. These enhancements may employ pseudo-random sequence based receiver training, activation signaling, and frame synchronizing.
Owner:ZEST LABS INC
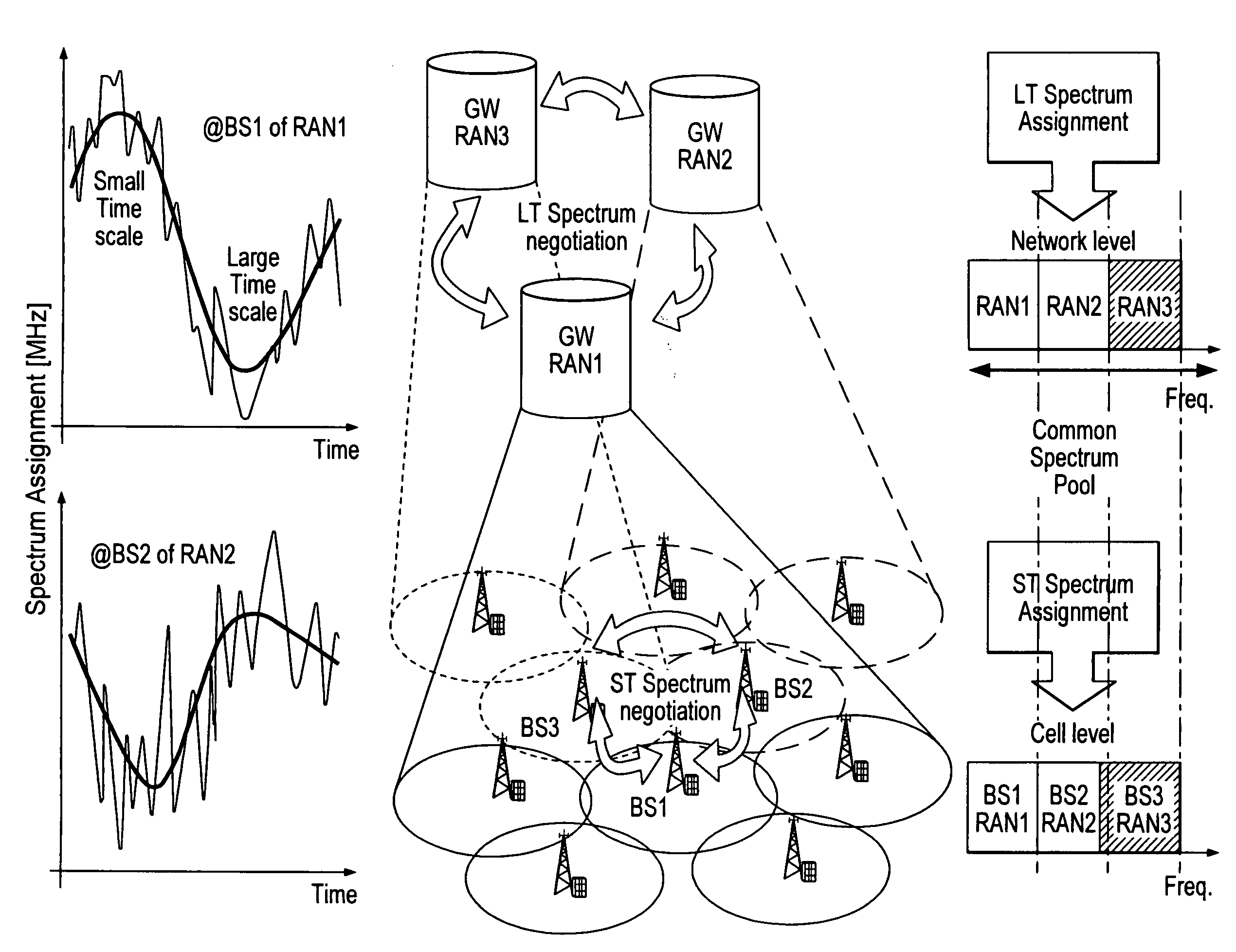
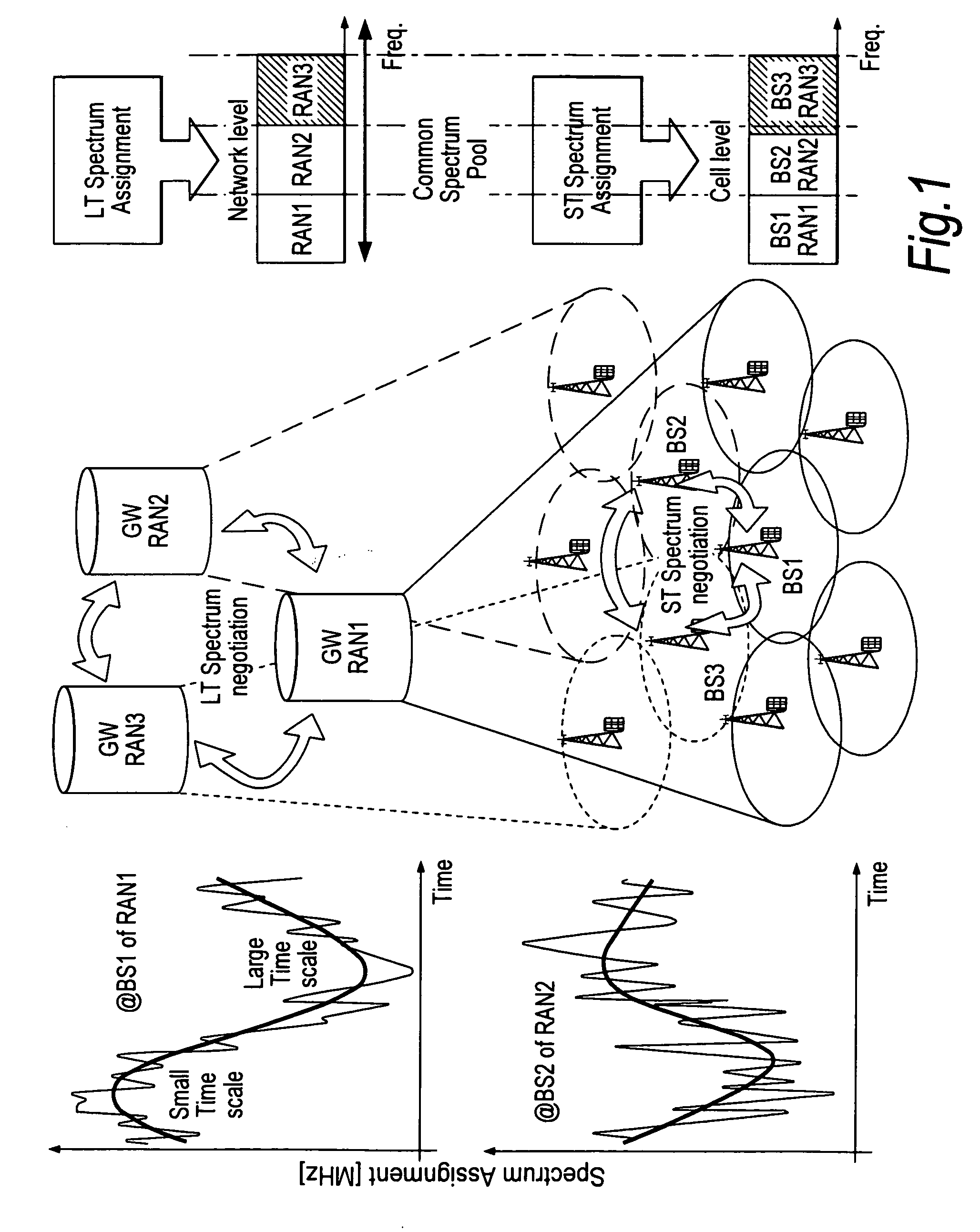
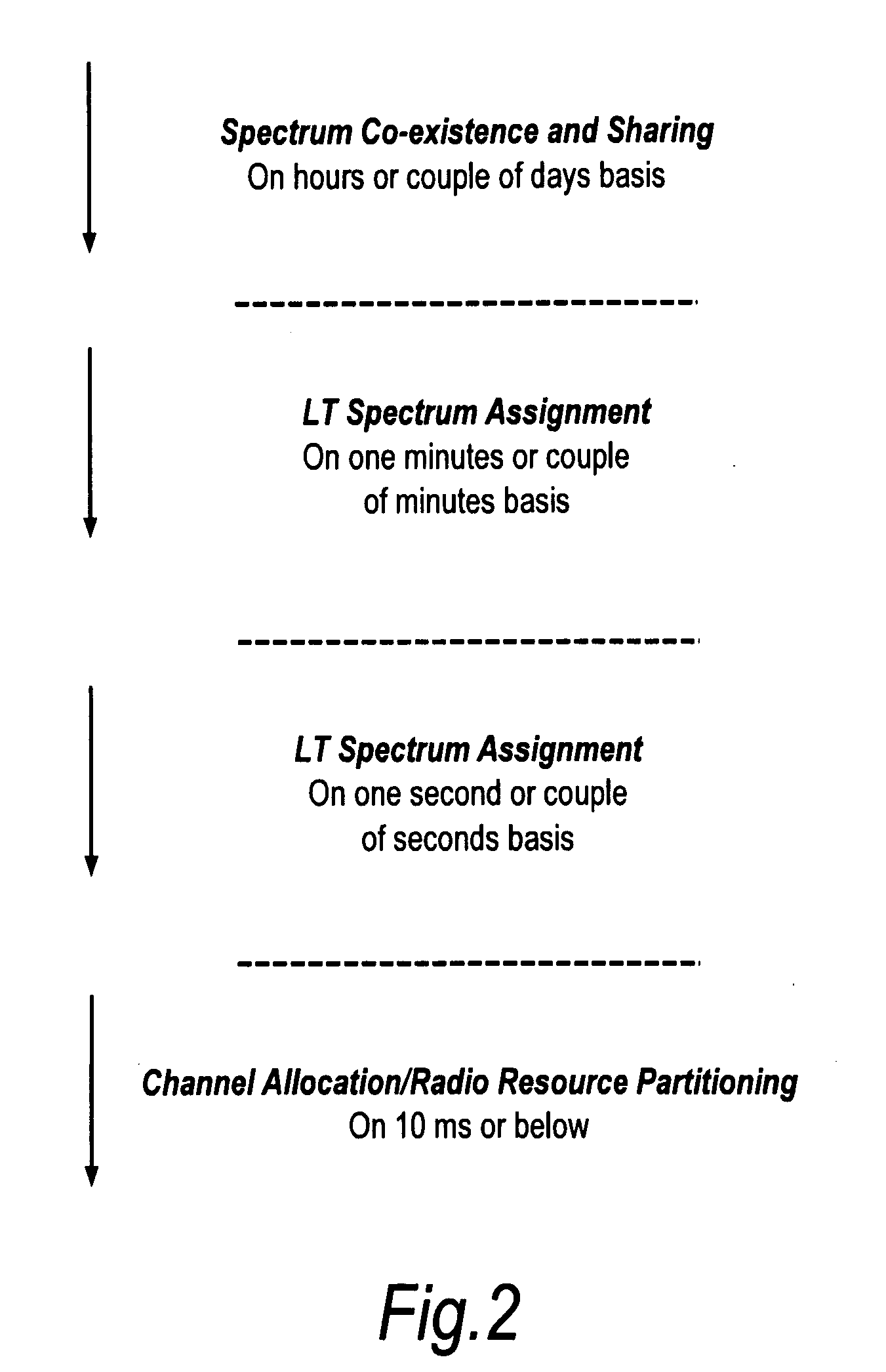
Interference mitigation method in cellular system based on orthogonal frequency division multiple access
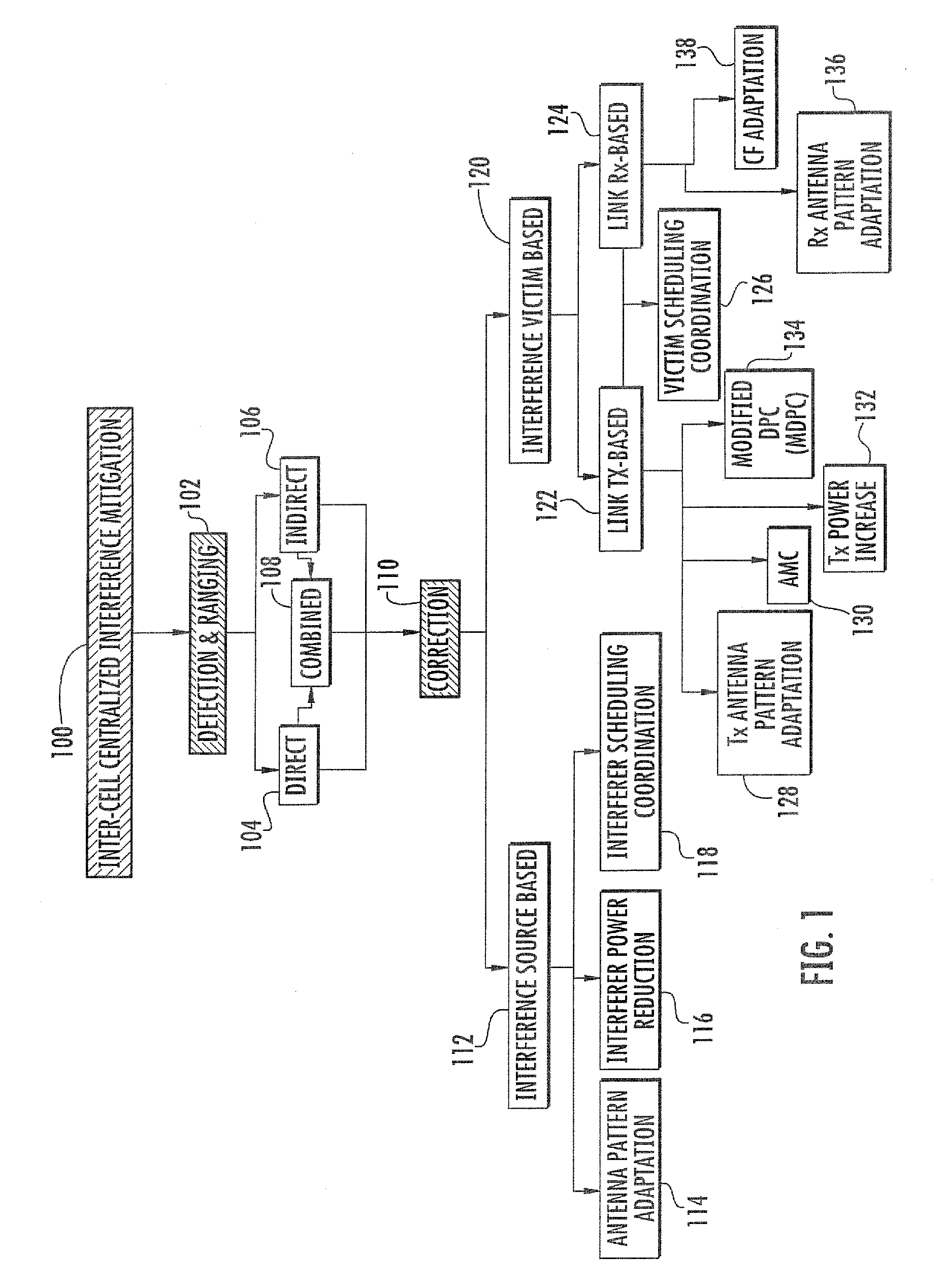
InactiveUS20100322109A1Improve user efficiencyPower managementSpatial transmit diversityTelecommunicationsMitigation methods
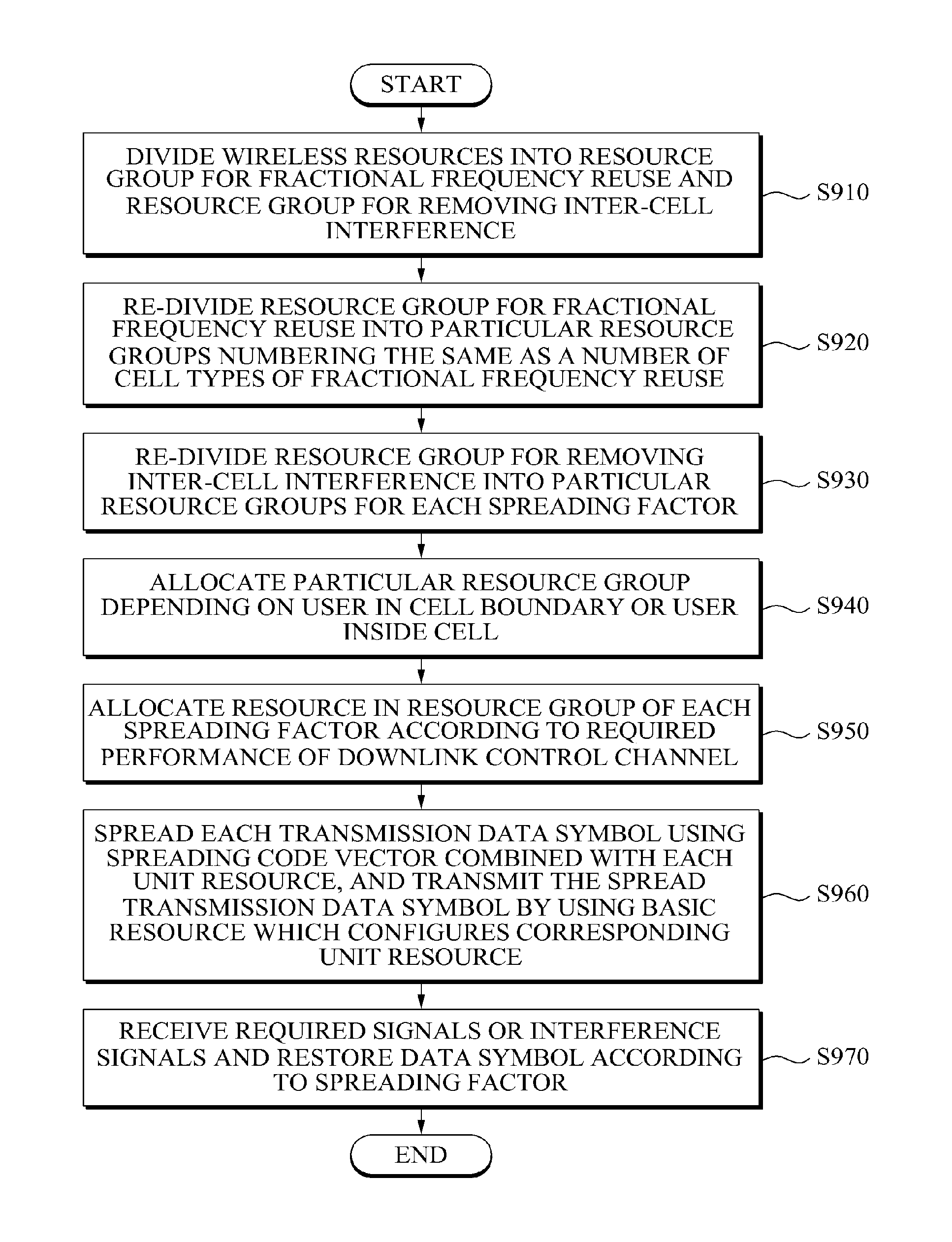
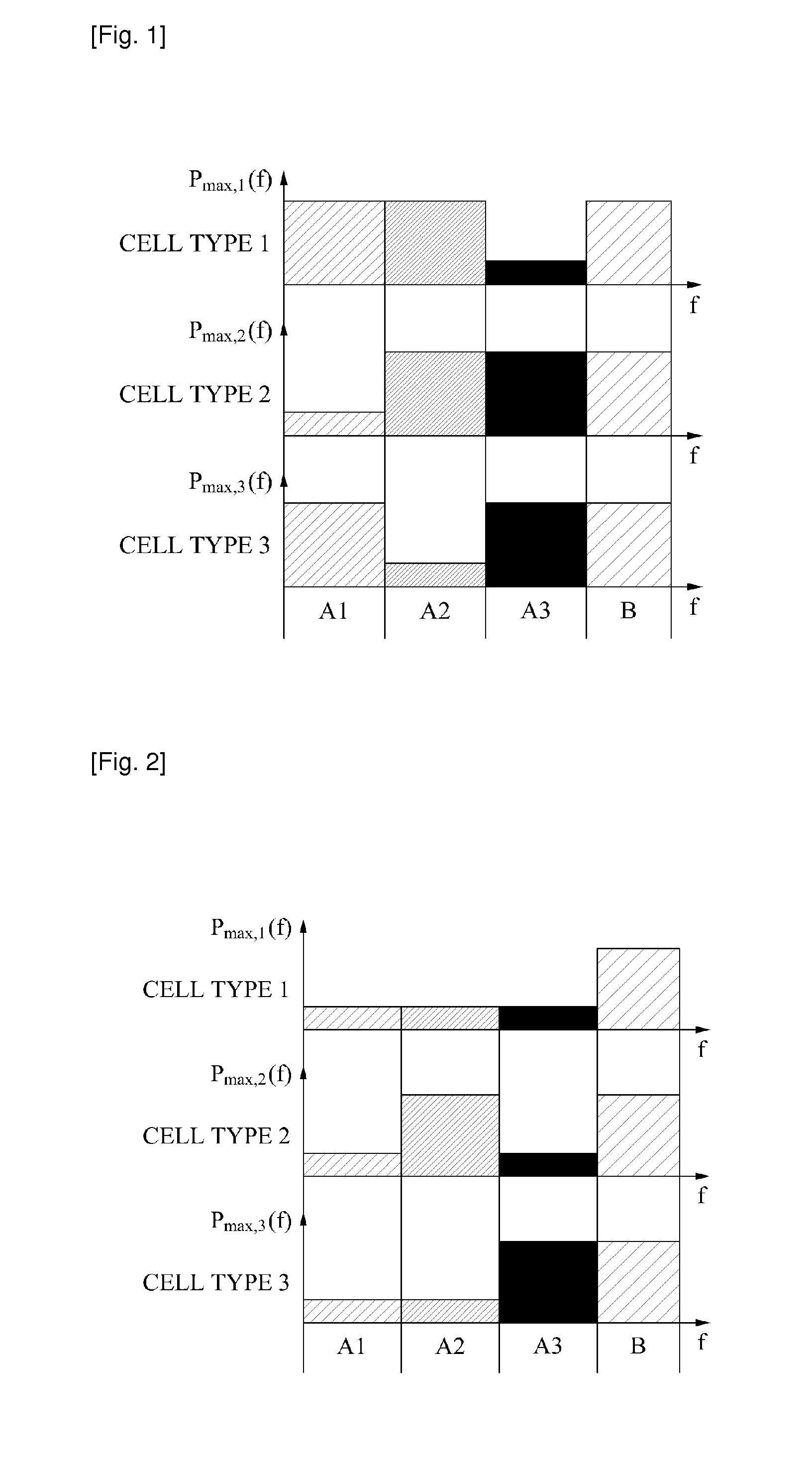
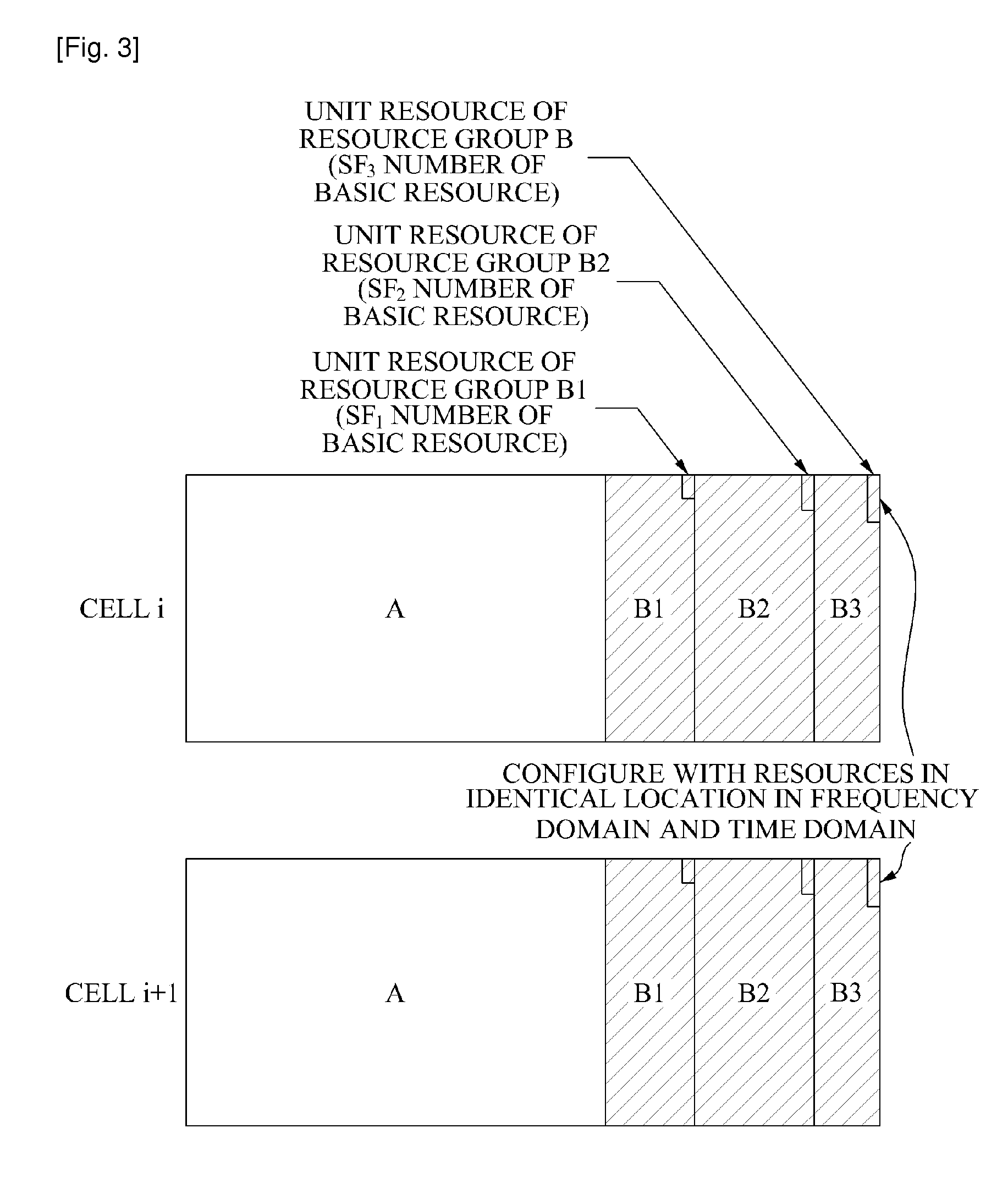
An inter-cell interference mitigation method in an orthogonal frequency division multiple access (OFDM)-based cellular system includes: dividing wireless resources into a resource group for fractional frequency reuse and a resource group for removing inter-cell interference; and re-dividing the resource group for fractional frequency reuse into particular resource groups numbering the same as a number of cell types of fractional frequency reuse, and applying a maximum transmission power to a particular resource group according to a cell type for fractional frequency reuse.
Owner:ELECTRONICS & TELECOMM RES INST
In-device interference mitigation
Methods and apparatus for mitigating in-device interference are described. The methods may include an in-device interference event (e.g. an interference situation), and the processing of events may depend on the priority of the technologies. A handover to another frequency or radio access technology (RAT) may occur in case a co-existing technology may be activated. The network may signal to the device a list of frequencies or RATs that it may be allowed to measure and handoff to. A network may provide a scaling value that the device may use to speed up reaction to the interference. The device may apply a scaling factor to an "out of synch' counter and / or the radio link failure (RLF) timer used for the RLF procedure. The device may apply different scaling factors for the measurements and time to trigger events. The device may trigger a report to the network requesting gaps for an alternate RAT.
Owner:INTERDIGITAL PATENT HLDG INC
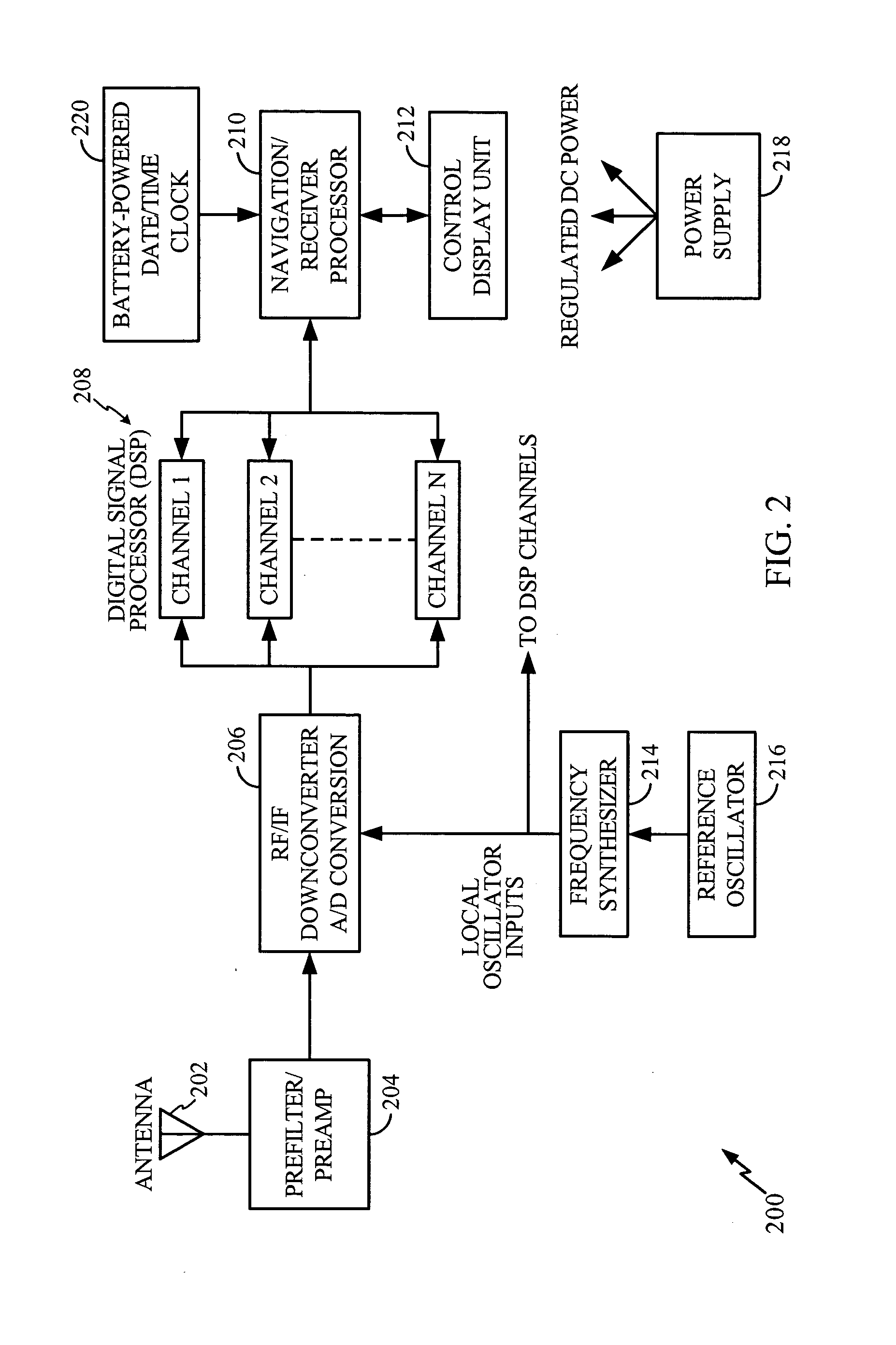
Cross-correlation mitigation method and apparatus for use in a global positioning system receiver
A method and apparatus mitigating the effects of cross-correlation signals on received satellite signals in a Global Positioning System (GPS) receiver is described. MS-Assisted and MS-Based cross-correlation detection and mitigation methods and apparatus are described. A GPS search mode architecture is used to detect SV signals and identify potential cross-correlations. The GPS search modes have different coherent integration lengths and different degrees of sensitivity. After detection, measurements are logged into a database for further processing. Several cross-correlation tests are described. For example, a “Mainlobe” cross-correlation test is described that identifies the most significant cross-correlations that occur when the Doppler difference between the interfering SV signal and the target SV signal is nonzero and a multiple of 1 kHz. Appropriate C / No and Doppler thresholds, or masks, are selected and used to identify the mainlobe cross-correlations. A wide Doppler mask is used to account for the effects on cross-correlations caused by BPSK data bit modulation. Appropriate MS-Assisted and MS-Based cross-correlation masks are described. Other cross-correlation tests include “variable C / No”, “strong”, “wide Doppler” and “pre-emptive” cross-correlation detection tests.
Owner:QUALCOMM INC
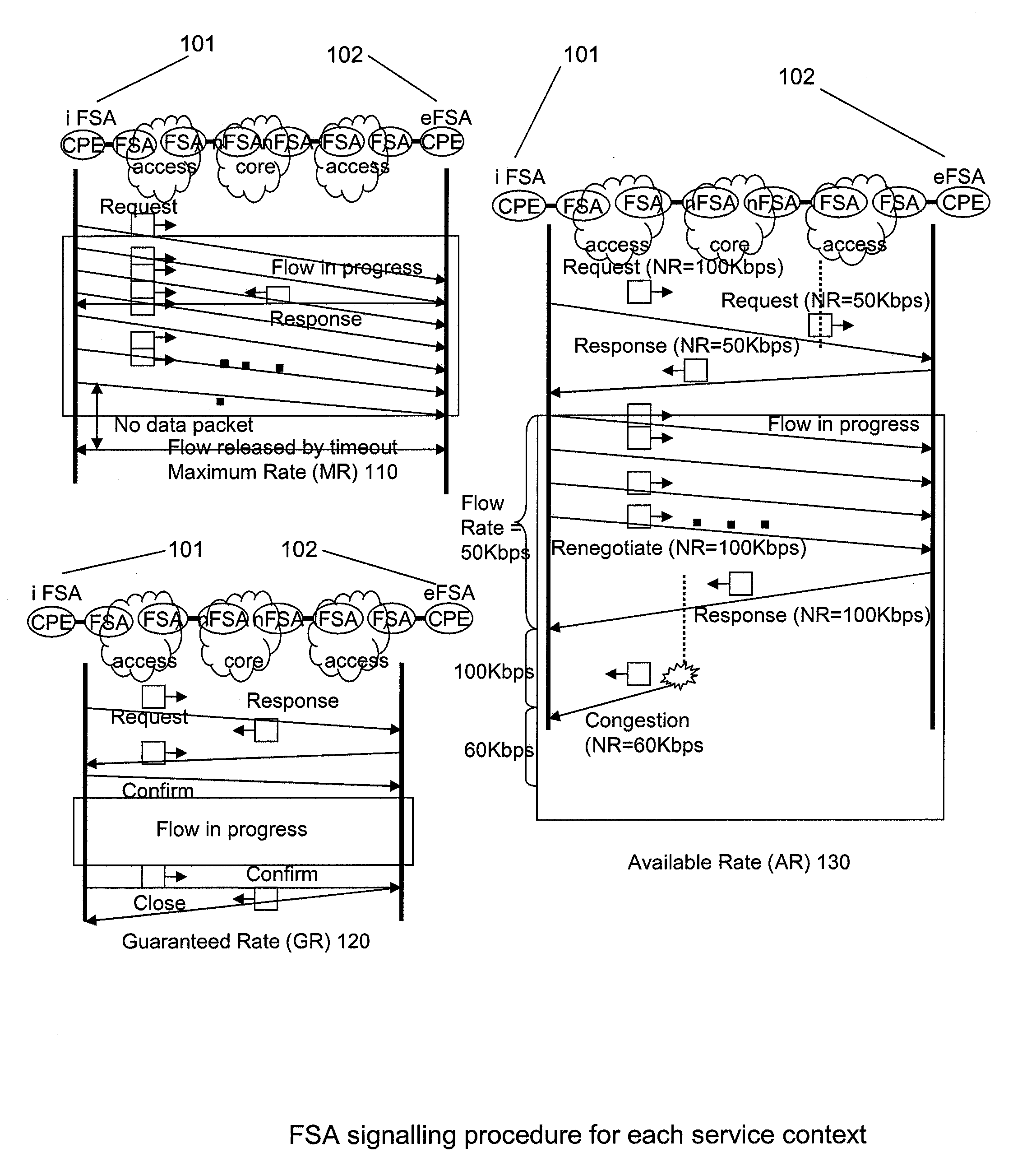
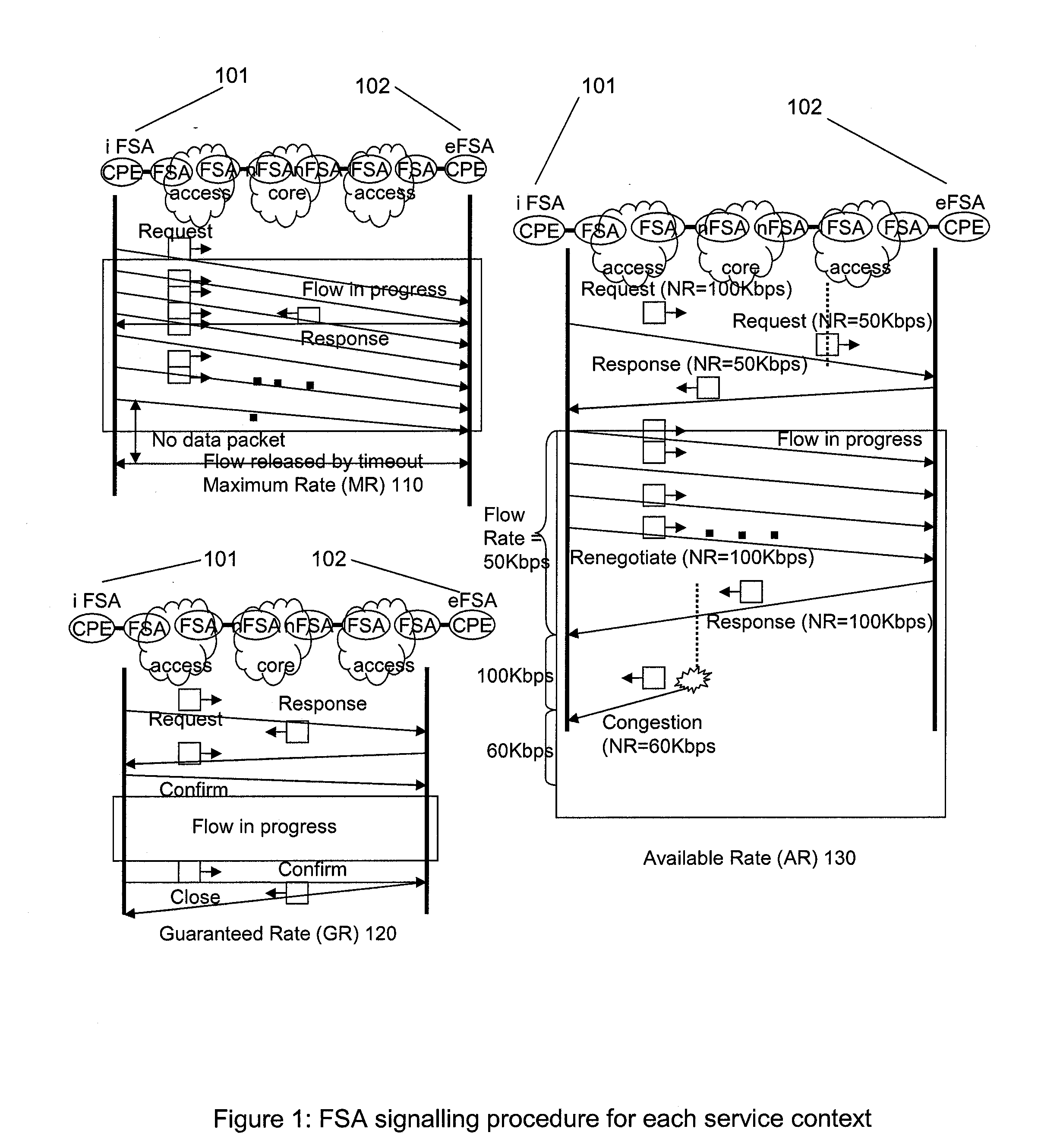
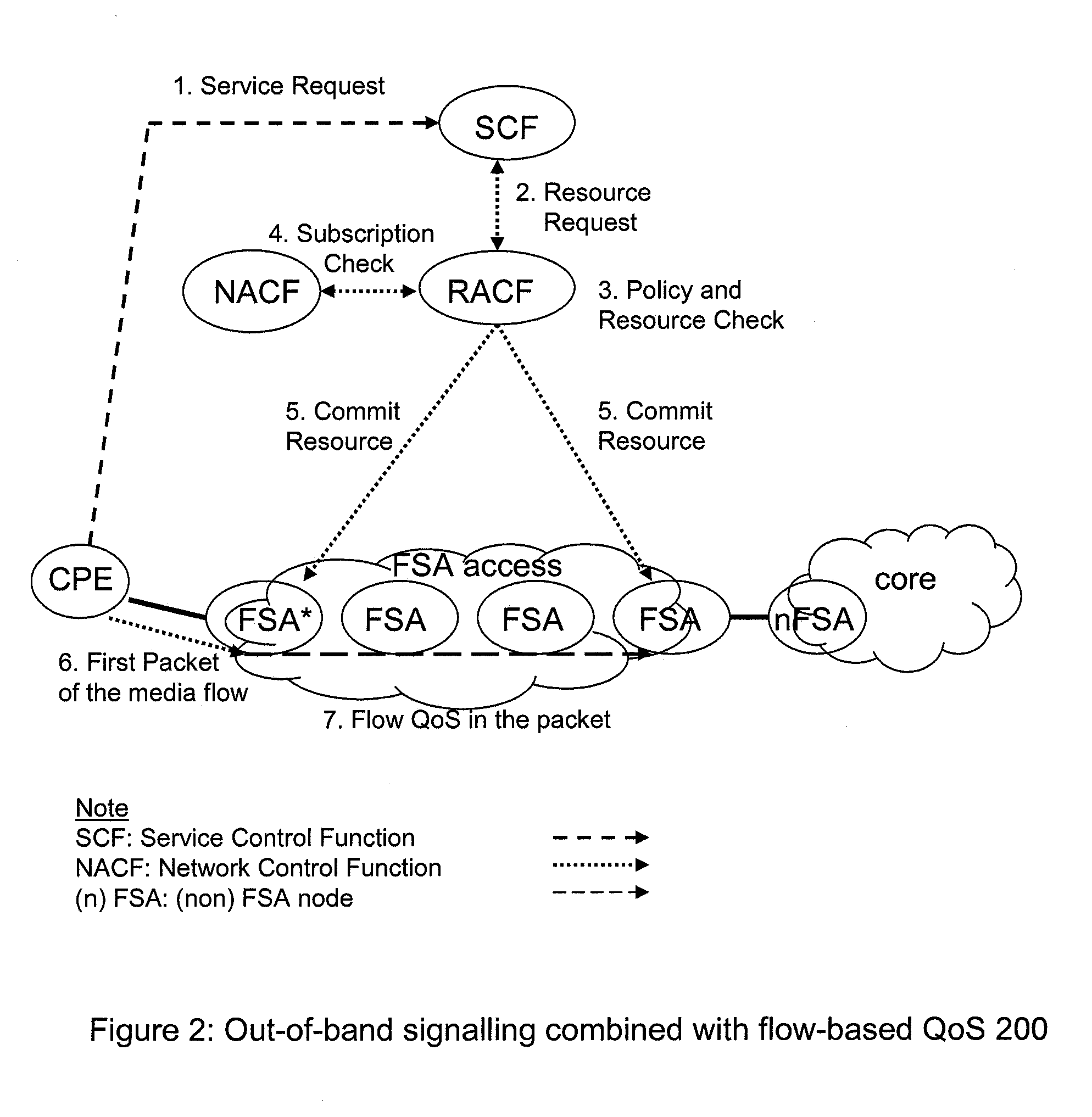
Flow State Aware QoS Management Without User Signalling
InactiveUS20100135158A1Improve service qualityFacilitate communicationEnergy efficient ICTError preventionTraffic capacityQos management
Conventional packet network nodes react to congestion in the packet network by dropping packets in a manner which is perceived by users to be indiscriminate. In embodiments of the present invention, indiscriminate packet discards are prevented by causing packets to be discarded according to bandwidth allocations that intelligently track flow sending rates. Flows are allocated bandwidth based on policy information. Where such policy information indicates that the flow should be treated as delay-sensitive, the present invention includes means to allocate an initial minimum rate that will be guaranteed and such flows will also have the use of an additional capacity that varies depending on the number of such flows that currently share an available pool of capacity. This provides a congestion alleviation method which is less annoying to users since communications that have been in existence for longer are less susceptible to component packets being deleted.
Owner:RAZOOM
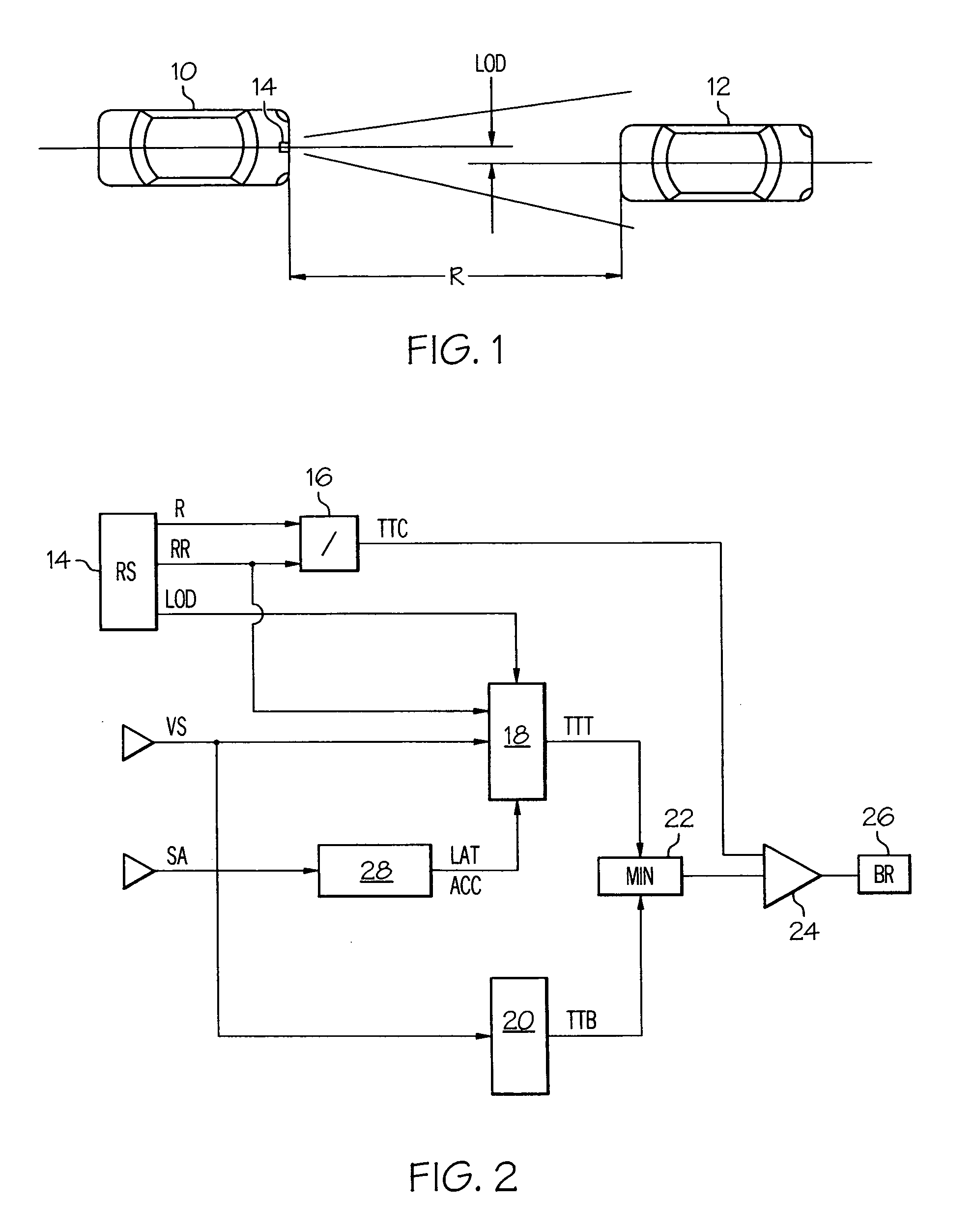
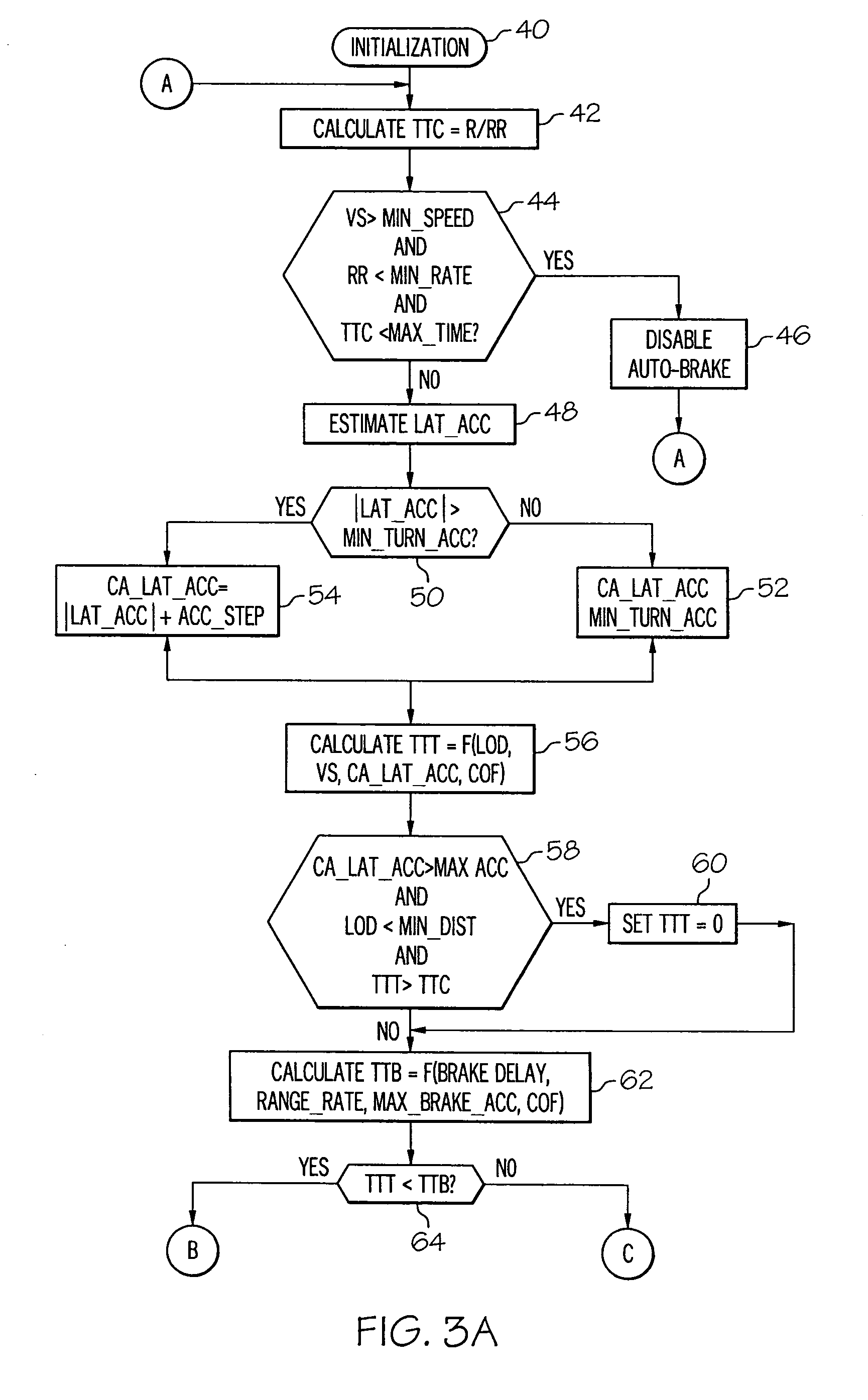
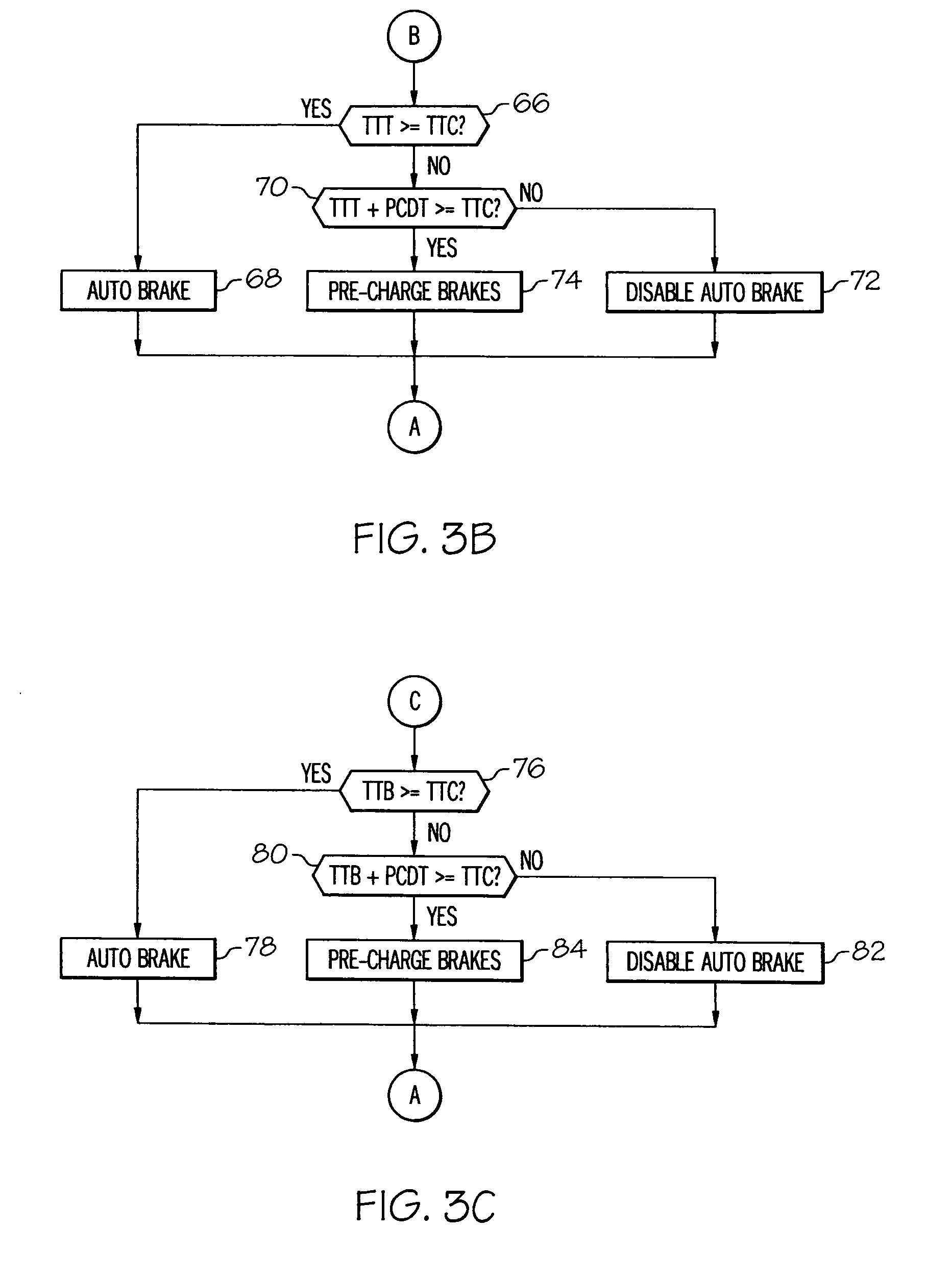
Collision prediction and mitigation method for a vehicle
A potential collision is predicted by comparing estimates of the time-to-brake (TTB) and the time-to-turn (TTT) of a host vehicle with a computed time-to-collision (TTC). The collision is deemed to be unavoidable when the smaller of TTB and TTT is greater than TTC. The TTT estimate is based in part on the lateral acceleration capability of the vehicle, and the lateral acceleration is initialized to a low value corresponding to its instantaneous capability, and is set incrementally higher than the actual lateral acceleration when the driver initiates evasive turning. The TTT and TTB estimates are increased by the time required to pre-charge the vehicle brakes so that brake pre-charging can be automatically initiated when required to optimize collision mitigation due to braking.
Owner:DELPHI TECH INC
Real-time mitigation of data access insider intrusions
ActiveUS7673147B2Reduce harmDigital data processing detailsComputer security arrangementsData accessInsider attack
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, network re-routing, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
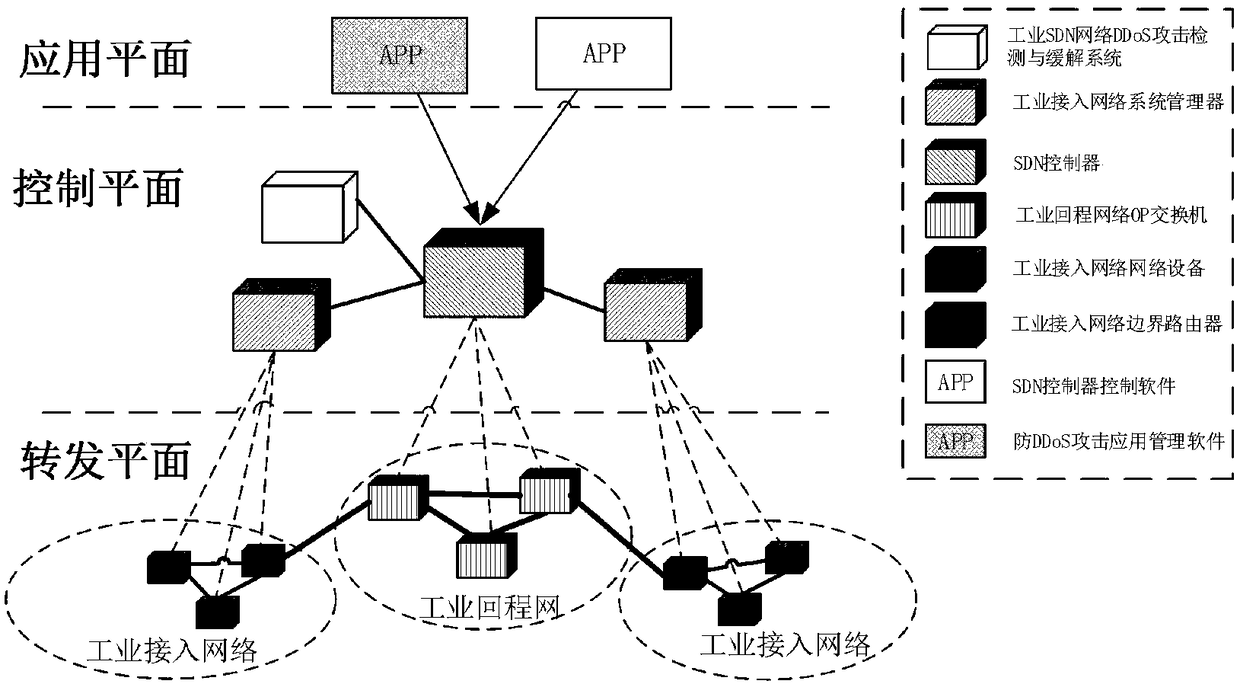
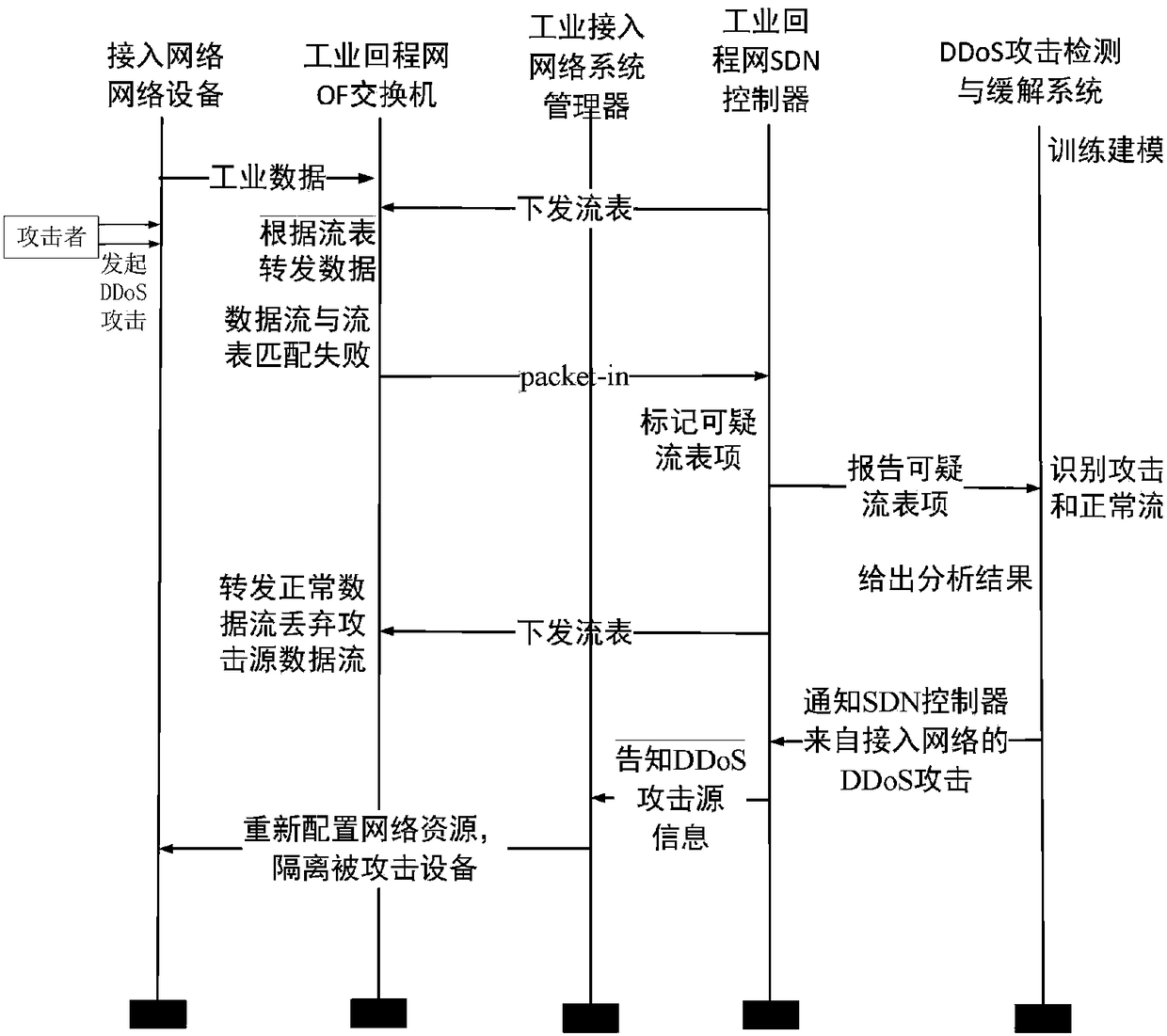
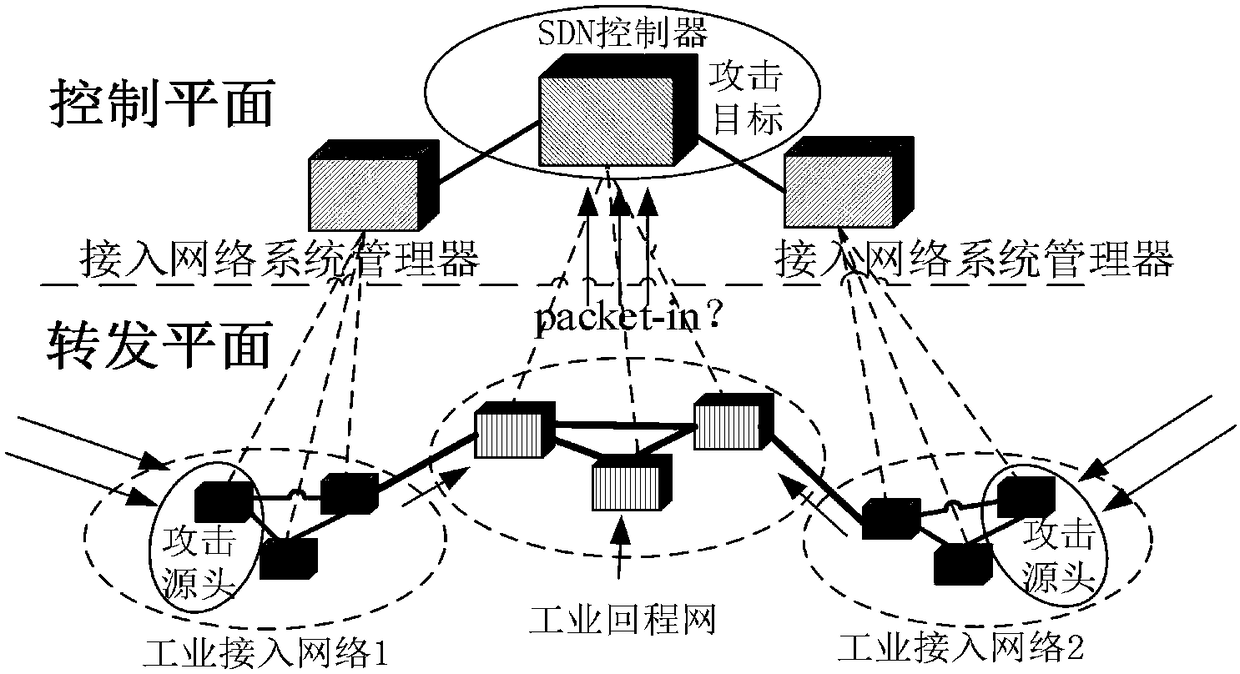
Method for detecting and alleviating DDoS attack of industrial SDN network
ActiveCN108289104AHighly Reliable Data TransmissionGuaranteed real-timeNetwork topologiesData switching networksAccess networkData stream
The invention relates to a method for detecting and alleviating DDoS attack of an industrial SDN network, wherein the method belongs to the field of network safety. According to the method of the invention, by means of cooperative function between an east-and-west direction interface of an SDN controller in an industrial backhaul network and a system manager of an industrial access network, according to the characteristics of the industrial backhaul network and an industrial access network data packet, an OpenFlow switch flow item matching domain is expanded, and a flow table 0 is set to an elevate DDoS attack specialized flow table for resisting an attack data flow in time. the SDN controller and the DDoS attack detecting and alleviating system of the industrial backhaul network are utilized, thereby identifying an attacking data flow and finding out a DDoS attack source, and applying a DDoS attack alleviating strategy through scheduling an industrial access network system manager. The method ensures normal flow of the industrial backhaul network and the industrial access network and overcomes threat of DDoS attack to safety of the industrial network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
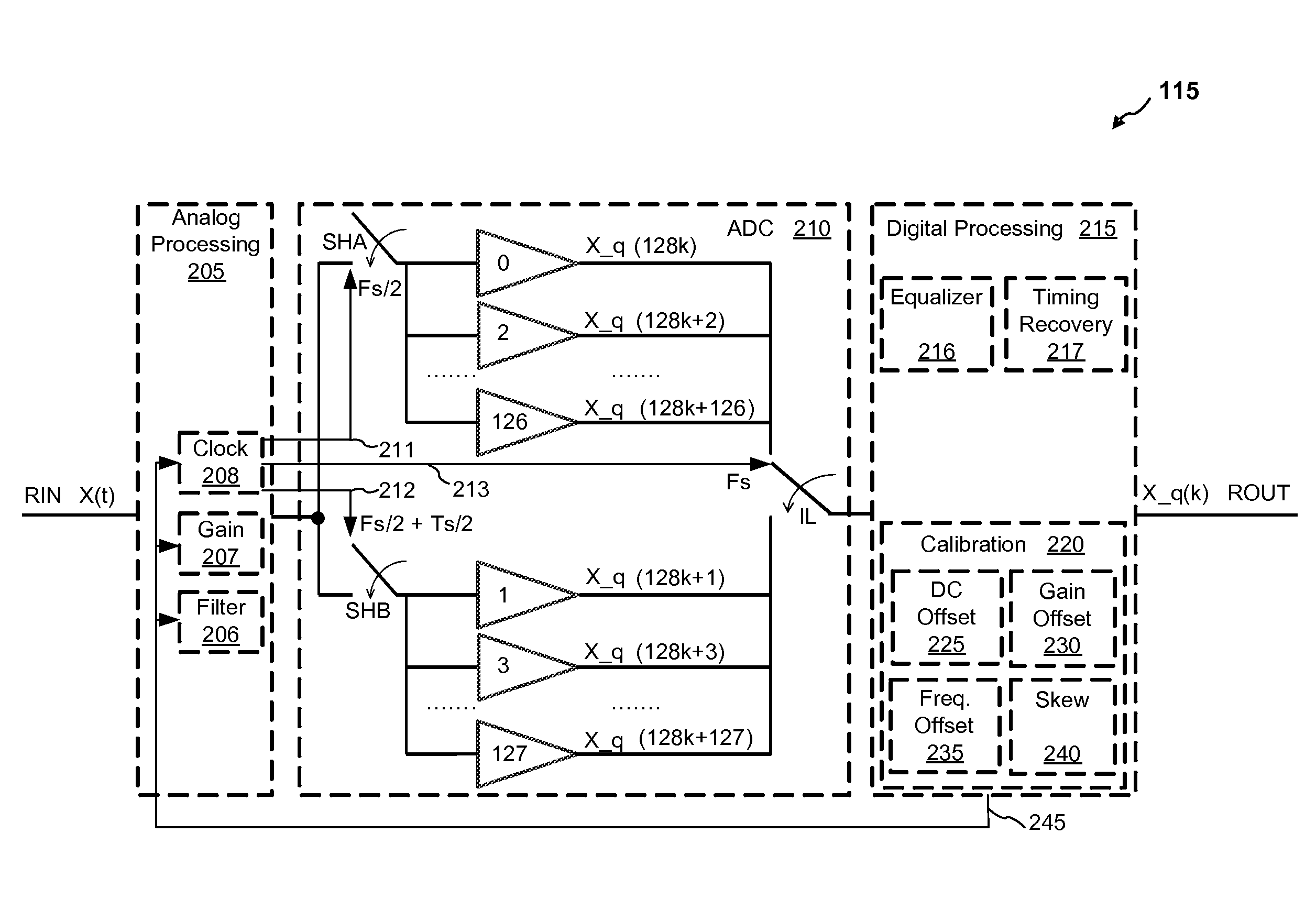
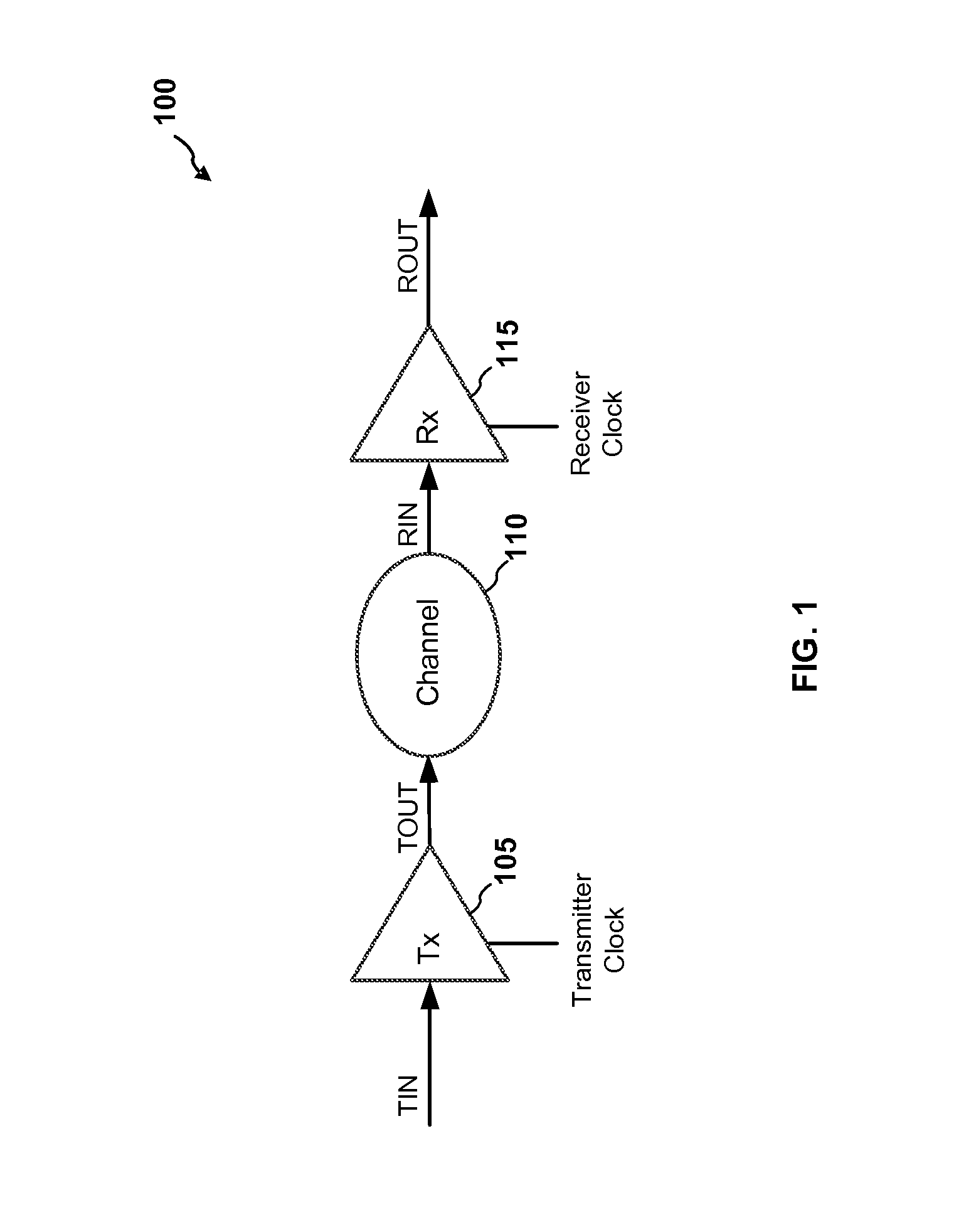
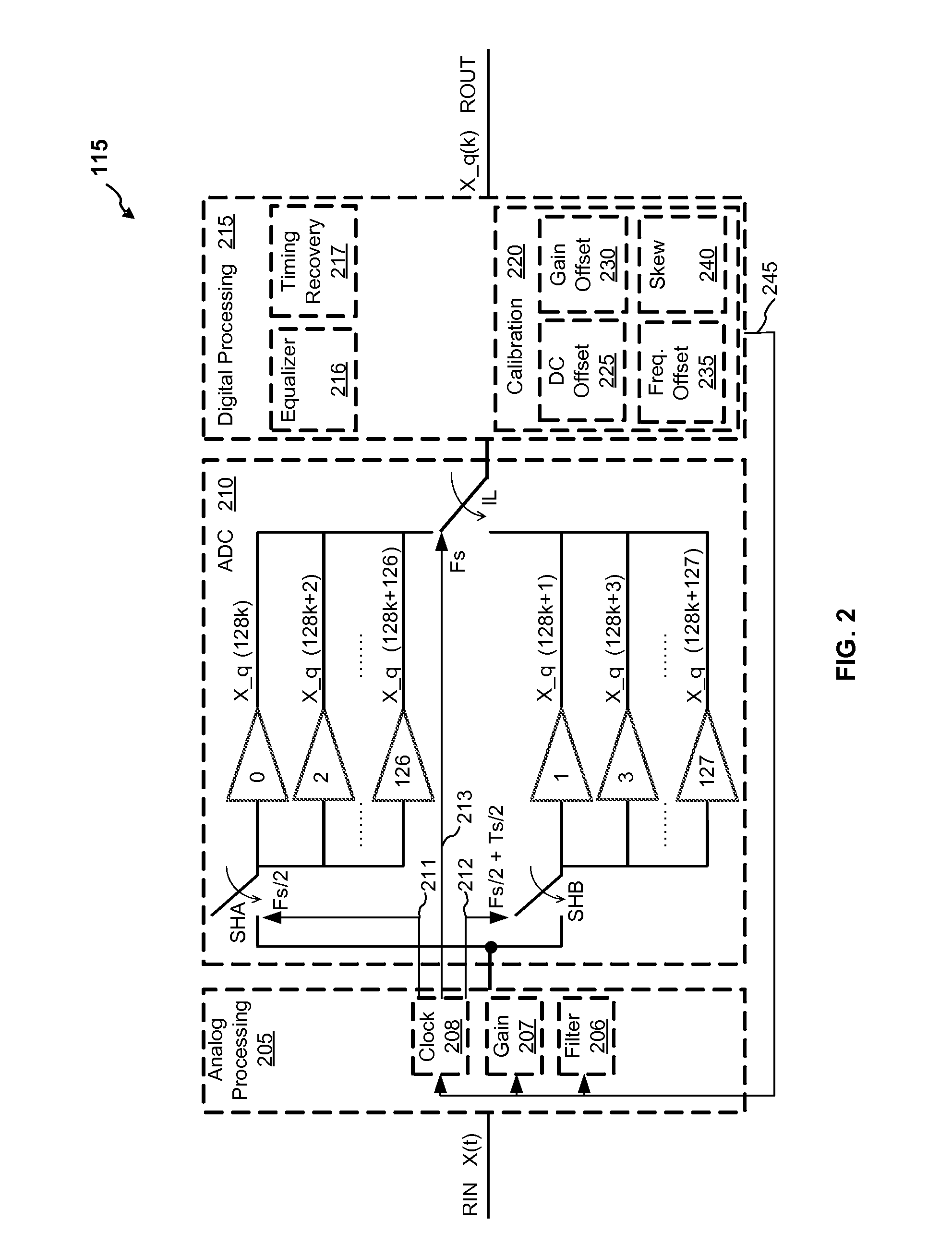
High speed time-interleaved ADC gain offset and skew mitigation
InactiveUS9270291B1Receiver initialisationReceivers monitoringCorrelation functionLatency (engineering)
Methods and apparatuses are described for timing skew mitigation in time-interleaved ADCs (TI-ADCs) that may be performed for any receive signal without any special signals during blind initialization, which may be followed by background calibration. The same gain / skew calibration metrics may be applied to baud sampled and oversampled systems, including wideband receivers and regardless of any modulation, by applying a timing or frequency offset to non-stationary sampled signals during initial training. Skew mitigation is low latency, low power, low area, noise tolerant and scalable. Digital estimation may be implemented with accumulators and multipliers while analog calibration may be implemented with adjustable delays. DC and gain offsets may be calibrated before skew calibration. The slope of the correlation function between adjacent samples may be used to move a timing skew estimate stochastically at a low adaptive rate until the skew algorithm converges.
Owner:AVAGO TECH INT SALES PTE LTD
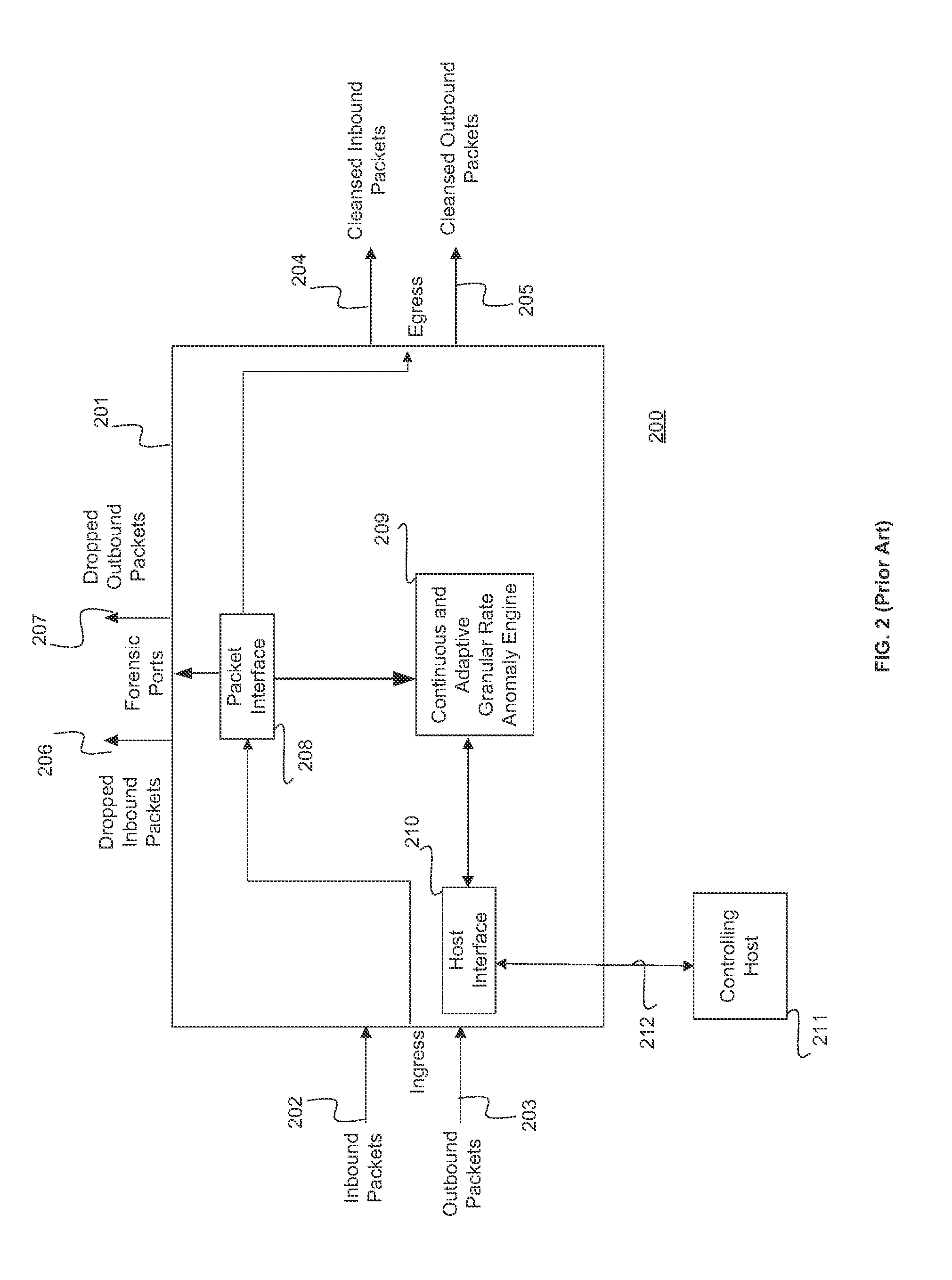
Scalable inline behavioral ddos attack mitigation
ActiveUS20150026800A1Improve throughputMemory loss protectionError detection/correctionAdaptive learningCommunications system
Methods and systems for a scalable solution to behavioral Distributed Denial of Service (DDoS) attacks targeting a network are provided. According to one embodiment, a method to determine the scaling treatment is provided for various granular layer parameters of the Open System Interconnection (OSI) model for communication systems. A hardware-based apparatus helps identify packet rates and determine packet rate thresholds through continuous and adaptive learning with multiple DDoS attack mitigation components. The system can be scaled up by stacking multiple DDoS attack mitigation components to provide protection against large scale DDoS attacks by distributing load across these stacked components.
Owner:FORTINET
Intra-cell and inter-cell interference mitigation methods for orthogonal frequency-division multiple access cellular networks
InactiveUS20130114451A1Error preventionFrequency-division multiplex detailsOrthogonal frequency-division multiple accessComputer science
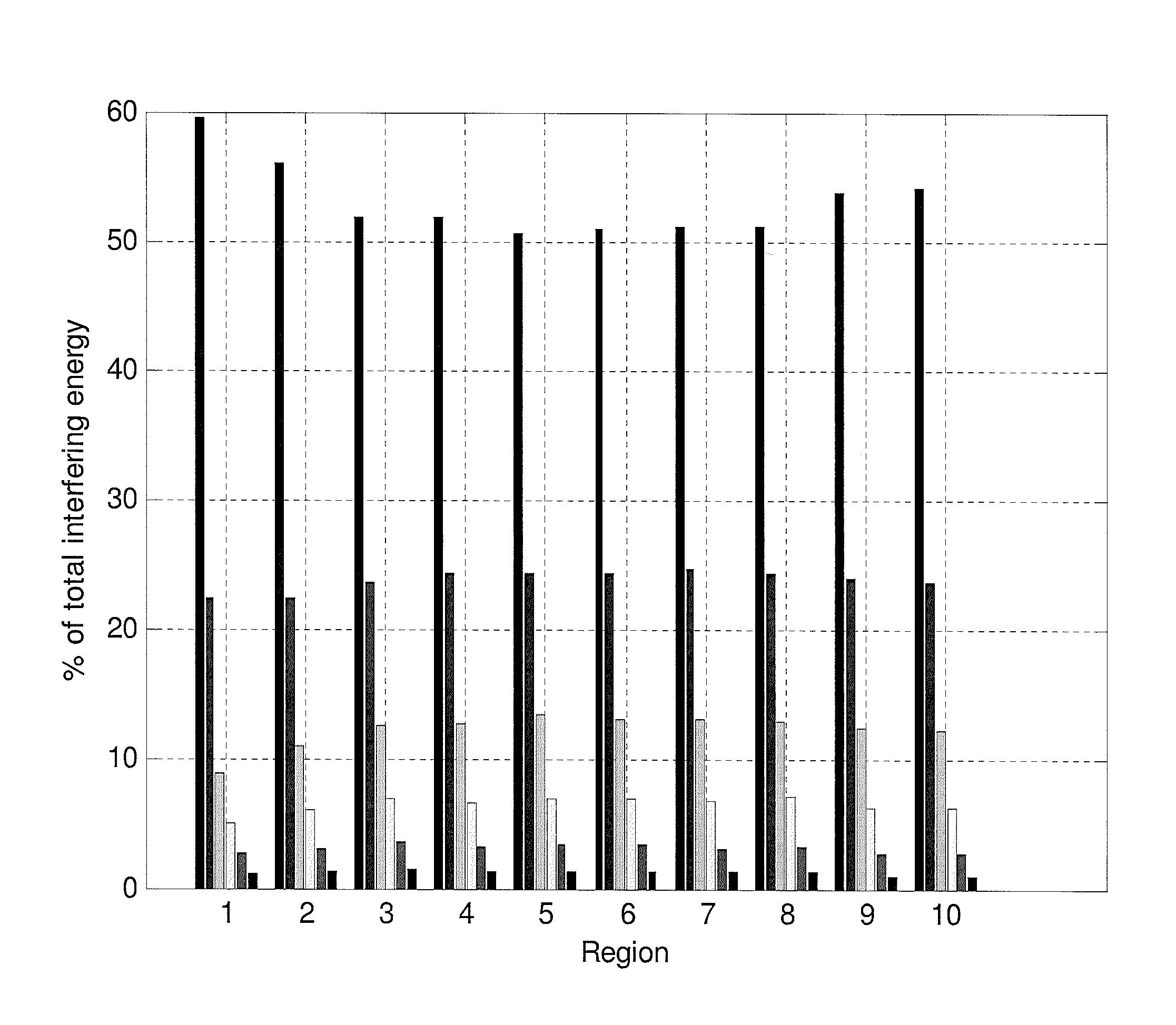
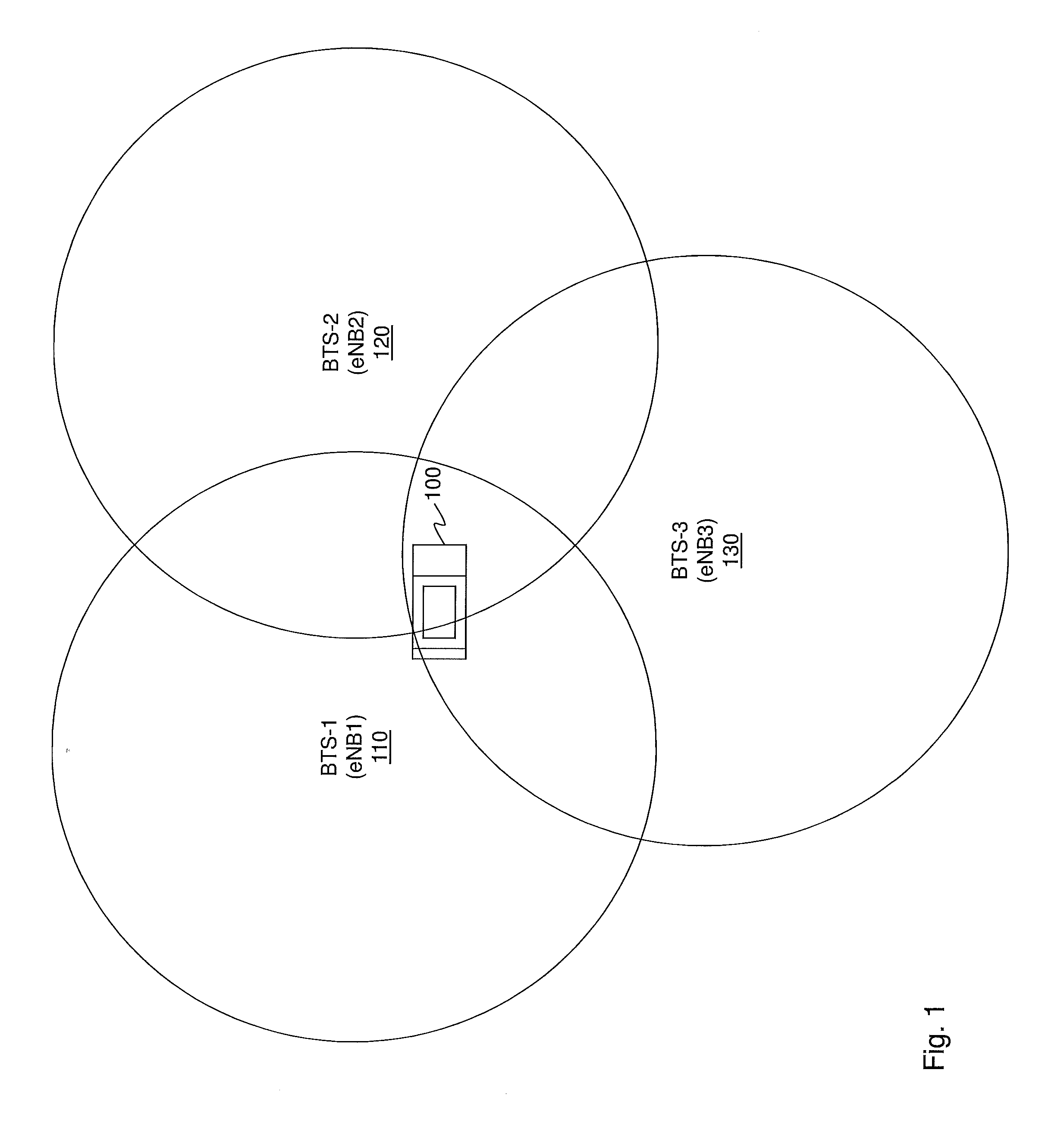
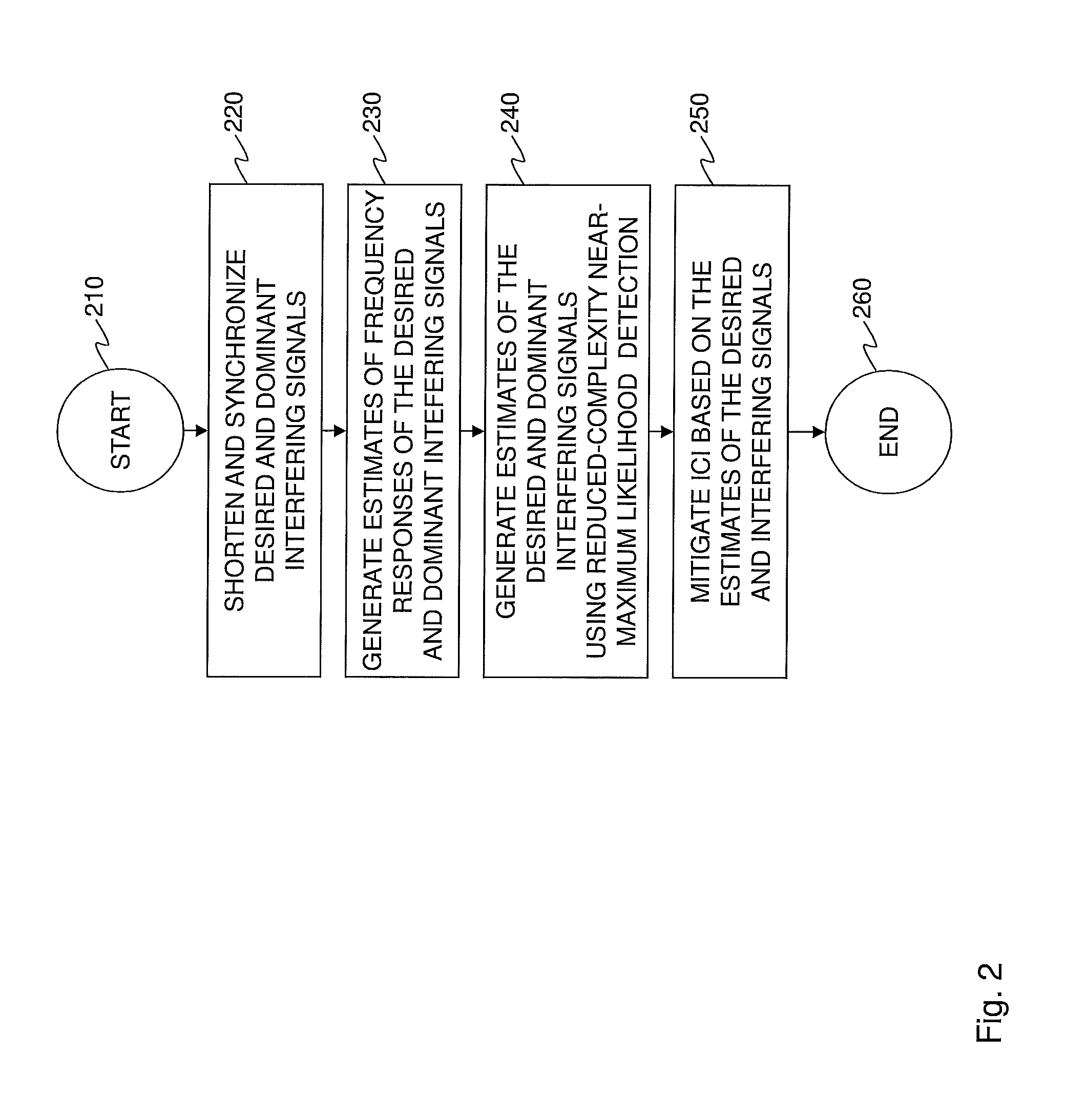
Various embodiments of a method of mitigating interference in an OFDMA cellular network and a user terminal incorporating various of the embodiments. In one embodiment, the method includes: (1) selecting at least one dominant interfering signal, (2) generating estimates of a desired signal and the at least one dominant interfering signal, (3) jointly deciding based on the estimates such that an energy of a residual error is reduced and (4) mitigating interference based on the estimates.
Owner:GRINDSTONE CAPITAL
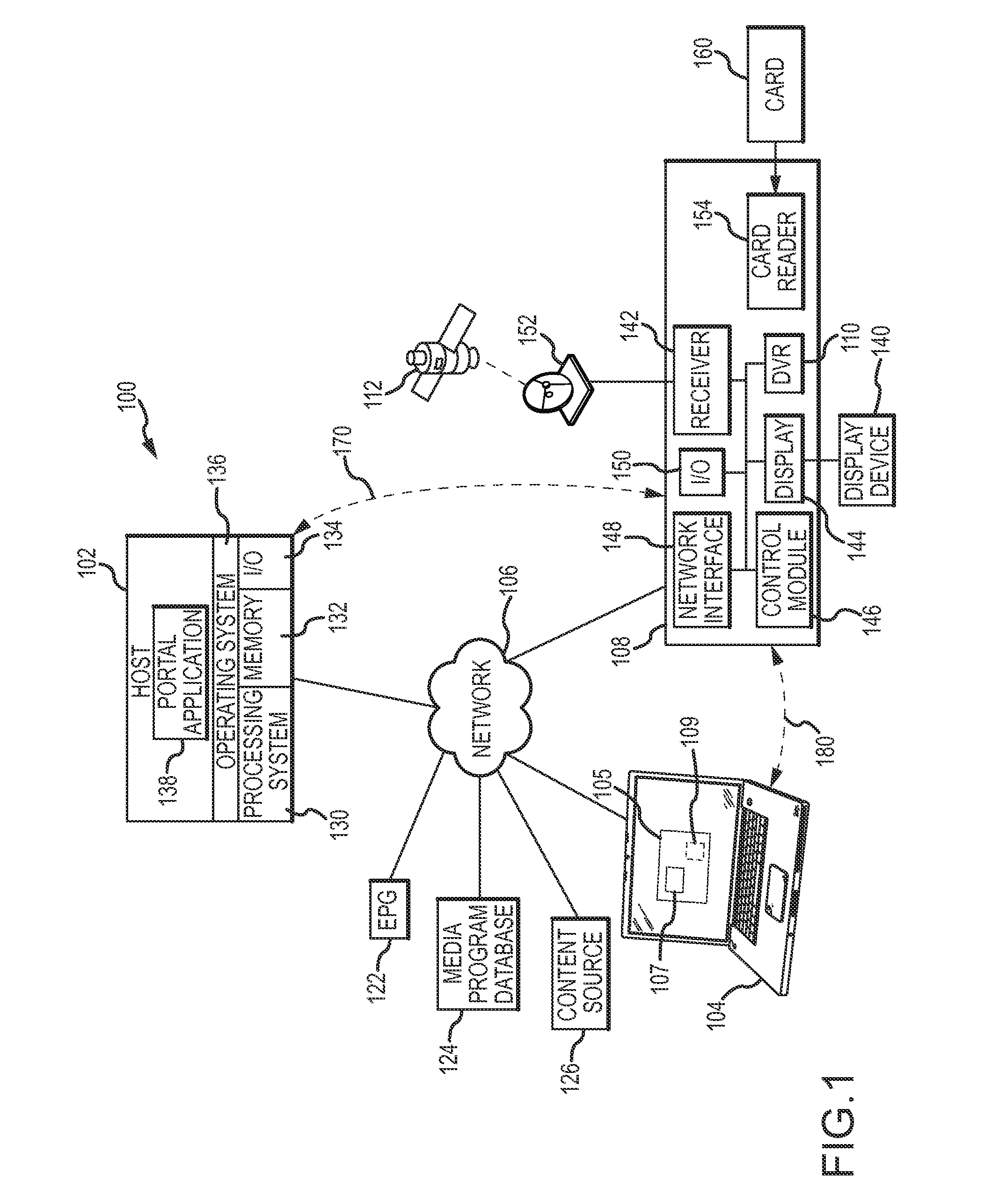
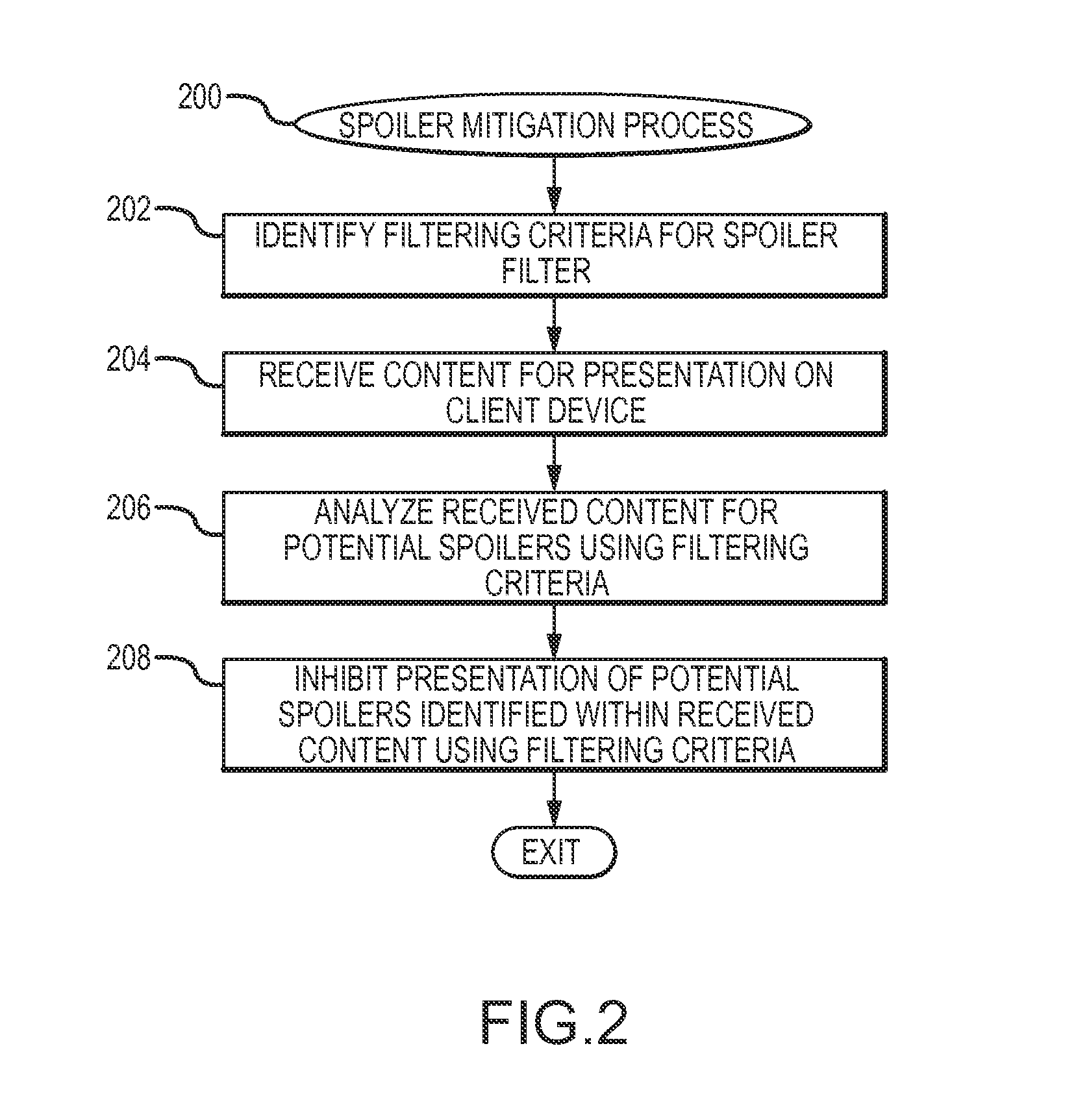
Spoiler mitigation methods and systems
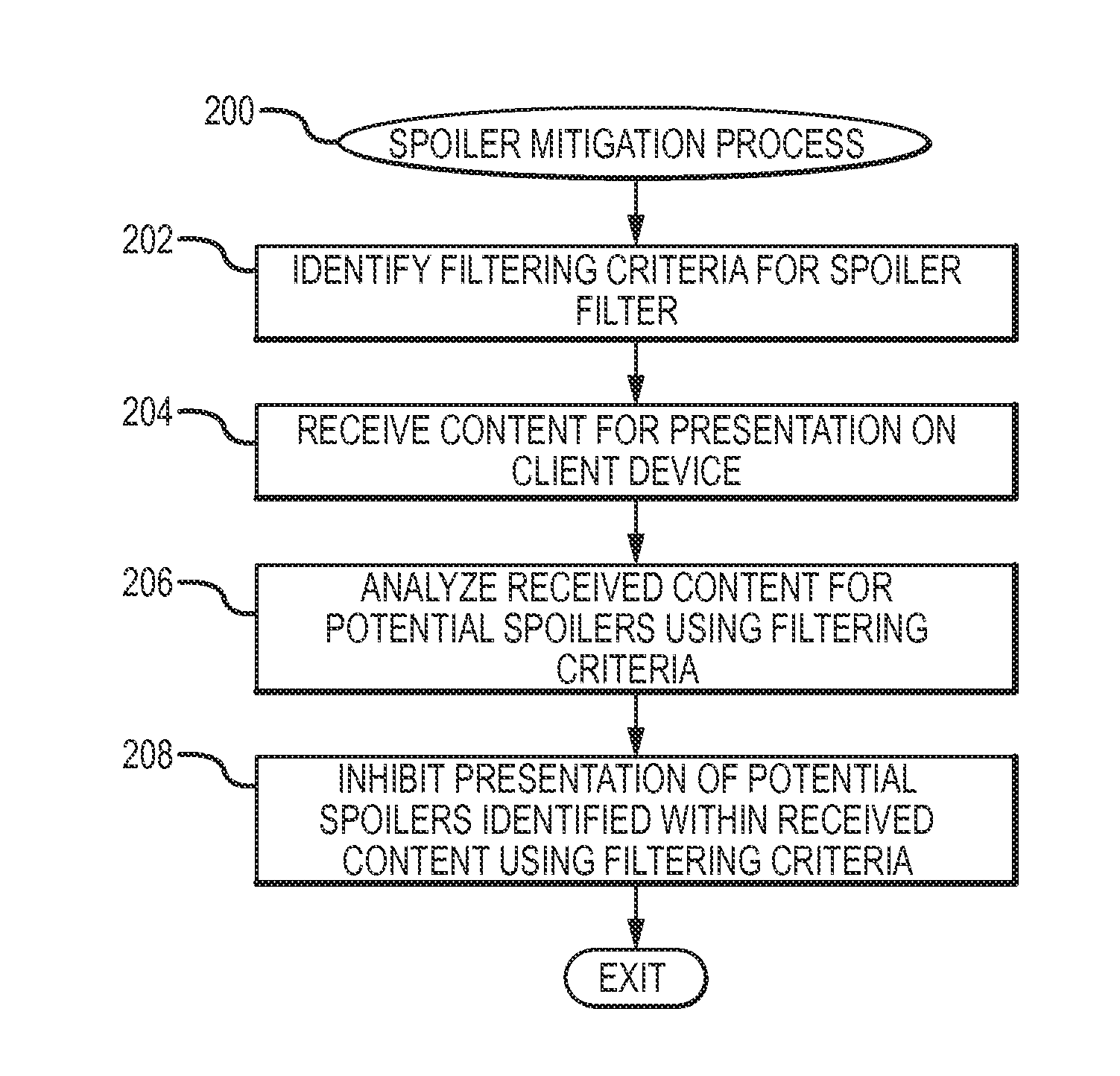
InactiveUS20150382061A1Analogue secracy/subscription systemsCoding/ciphering apparatusWorld Wide WebMitigation methods
Methods and systems are provided for mitigating spoilers when placeshifting content. One exemplary method involves identifying a filtering criterion based on a media program available for viewing on a client device via a network, obtaining, via the network, content for presentation on the client device, identifying a portion of the content corresponding to the media program using the filtering criterion, and inhibiting presentation of the identified portion of the content on the client device.
Owner:SLING MEDIA LLC
Policy specification framework for insider intrusions
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, deprovision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
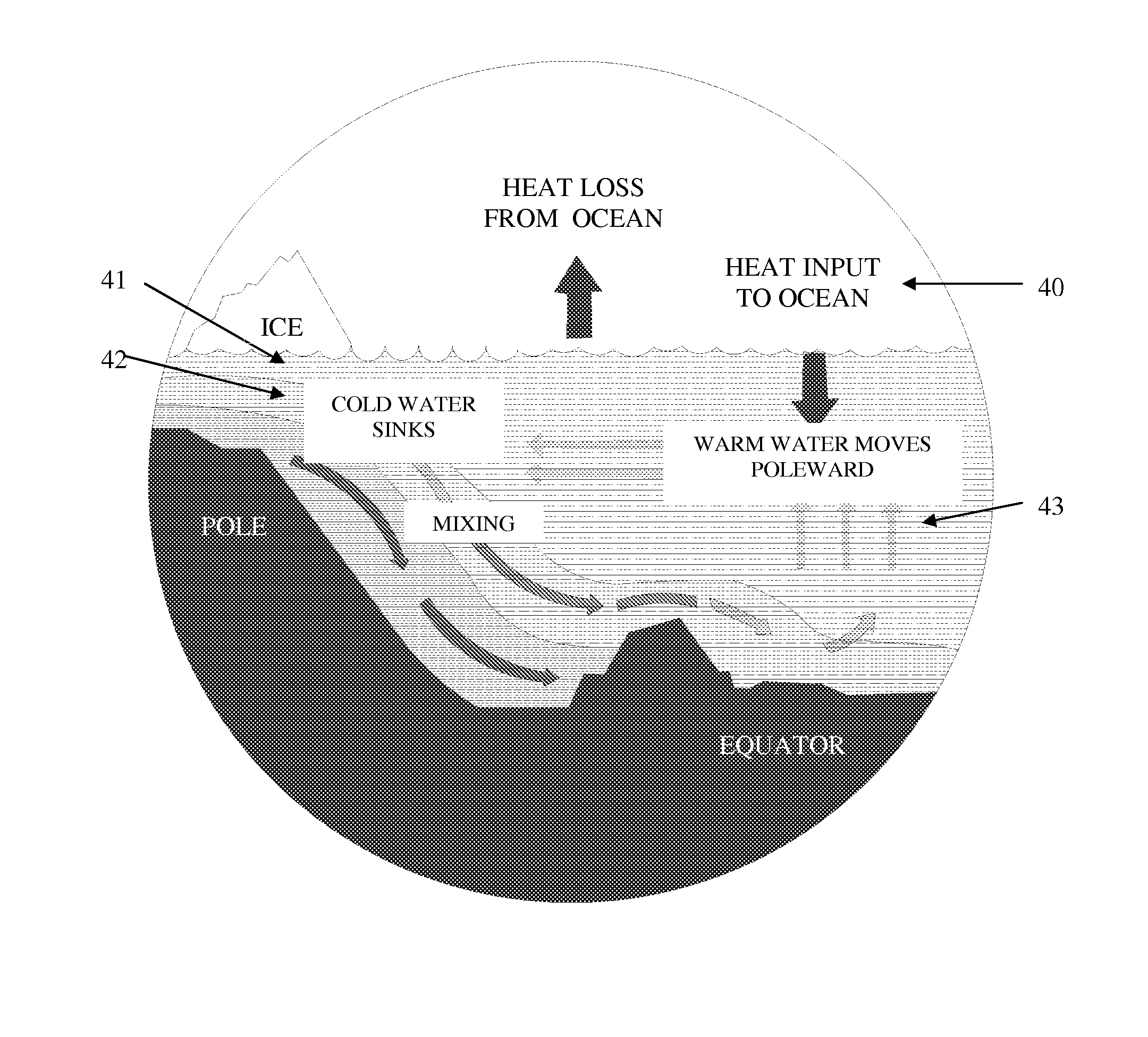
Global warming mitigation method
InactiveUS20110036919A1Stable levelBuildBio-organic fraction processingMethane captureElectrolysisSea level rise
The present invention provides a method of limiting sea level rise. In a first step heat that would otherwise cause thermal expansion of the ocean and resultant sea level rise is extracted to produce energy. The energy is used to convert a portion of the liquid ocean water to the gaseous elements hydrogen and oxygen by the process of electrolysis. The ocean level is reduced by the volume of water converted to gas. The hydrogen is captured for use as an energy source and is transported to a desert to be recombined with resident oxygen to produce energy and water for irrigation.
Owner:BAIRD JAMES RUSSELL
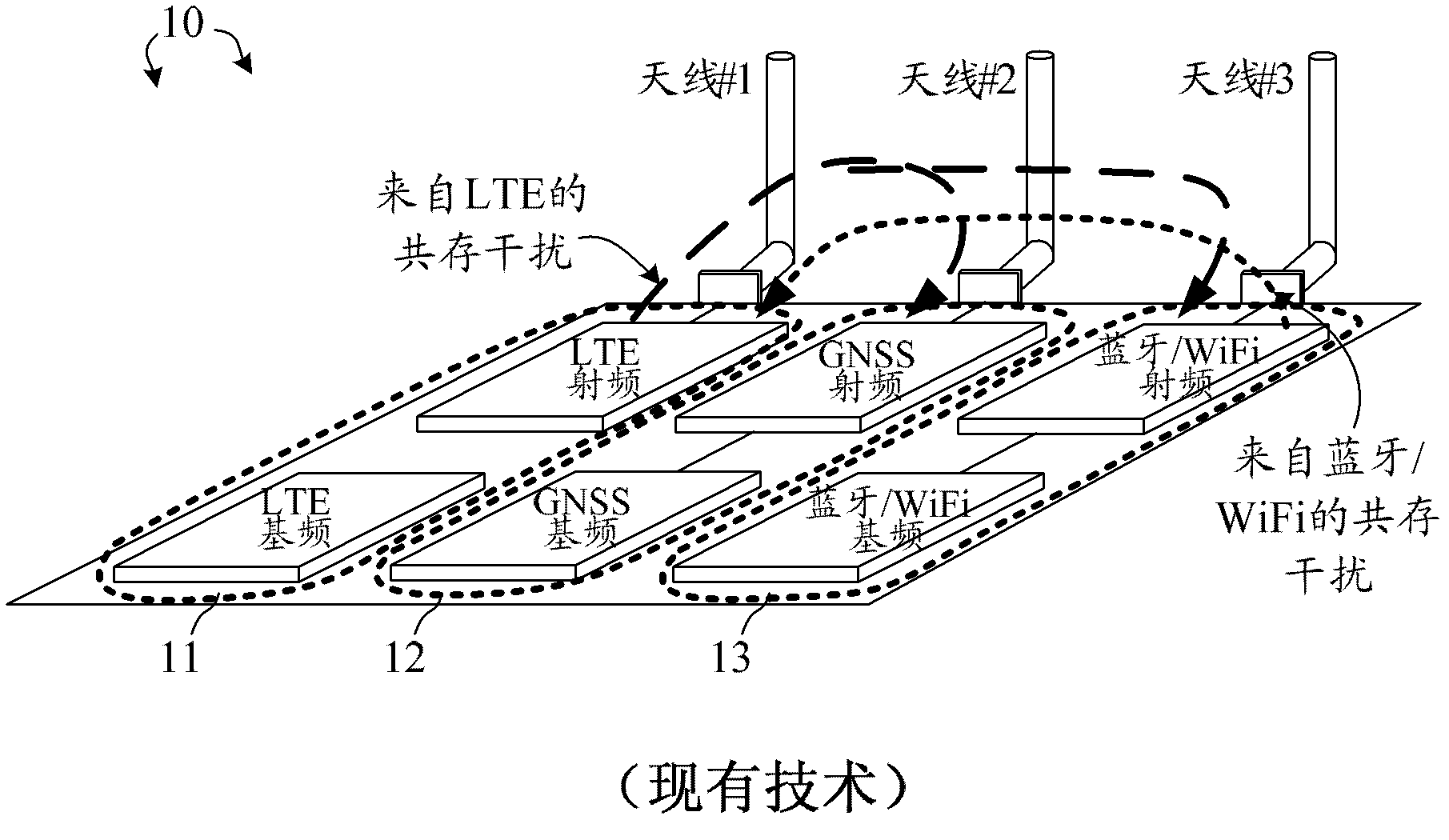
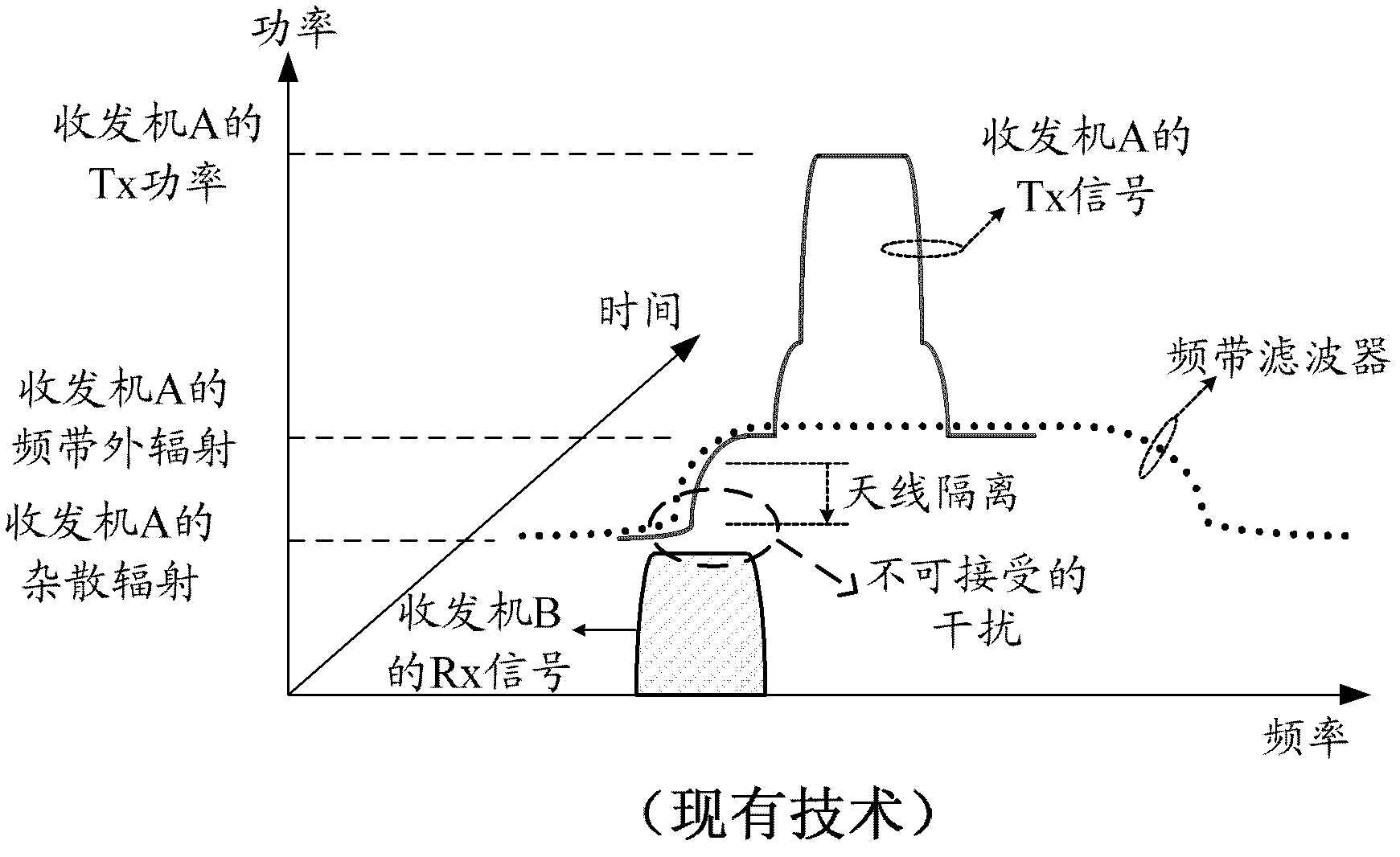
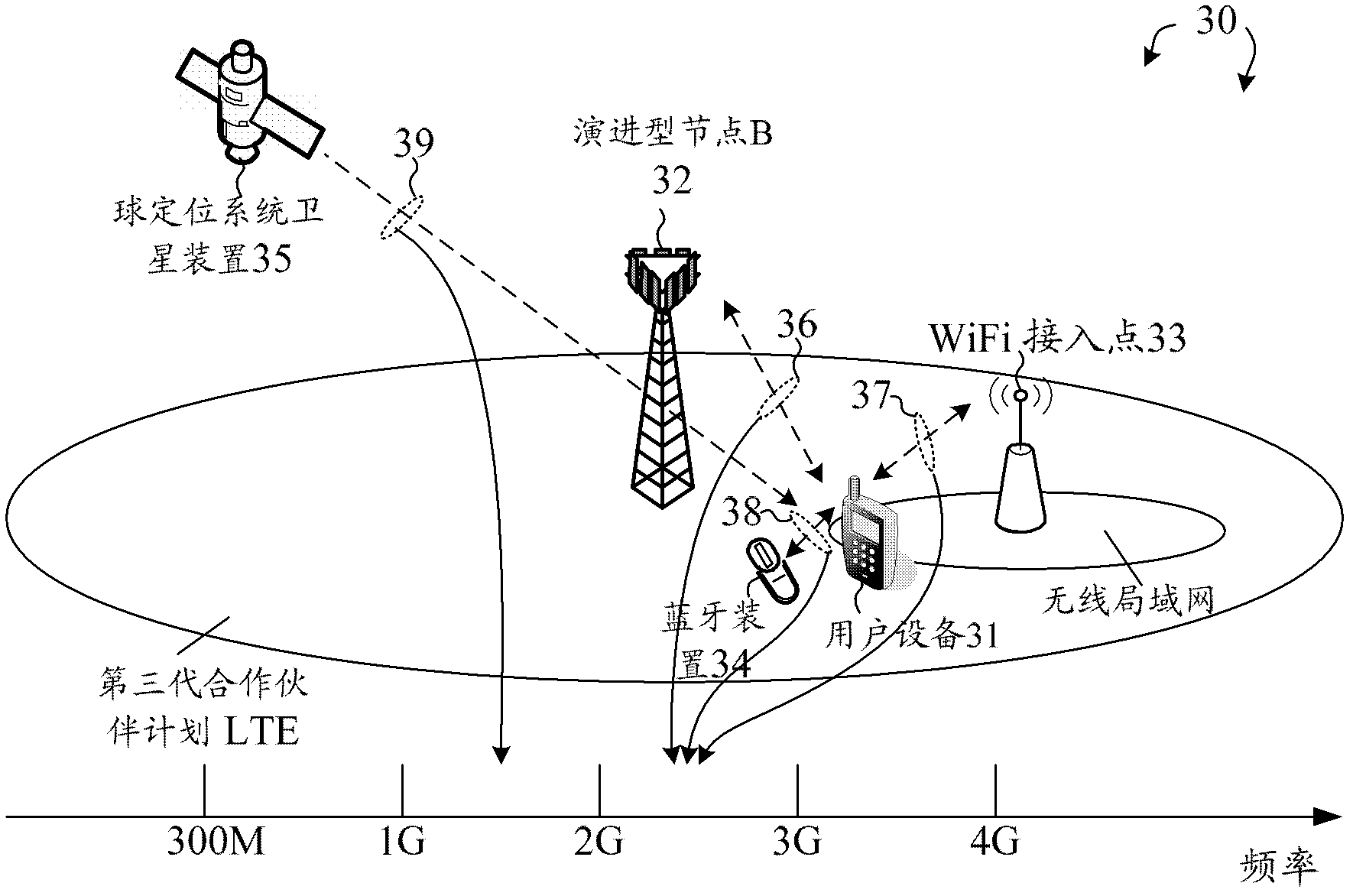
Method of in-device interference mitigation for cellular, bluetooth, wifi, and satellite systems coexistence
A coexistence interference mitigation method is provided. In a wireless network, a wireless device is equipped with multiple radios in the same device platform. The wireless device also has a control entity that communicates with the multiple co- located radio modules. A first radio module receives a notification from the control entity. The notification informs a critical signaling status of a second radio module co-located with the first radio module. Upon receiving the notification, the first radio module stops uplink transmission due to coexistence interference and transmits a coexistence indicator to its serving eNB. After a certain period, the first radio module receives a second notification that informs a completion status of the critical signaling of the second radio module. Upon receiving the second notification, the first radio module resumes uplink transmission and transmits a coexistence resume indicator to the eNB.
Owner:HFI INNOVATION INC
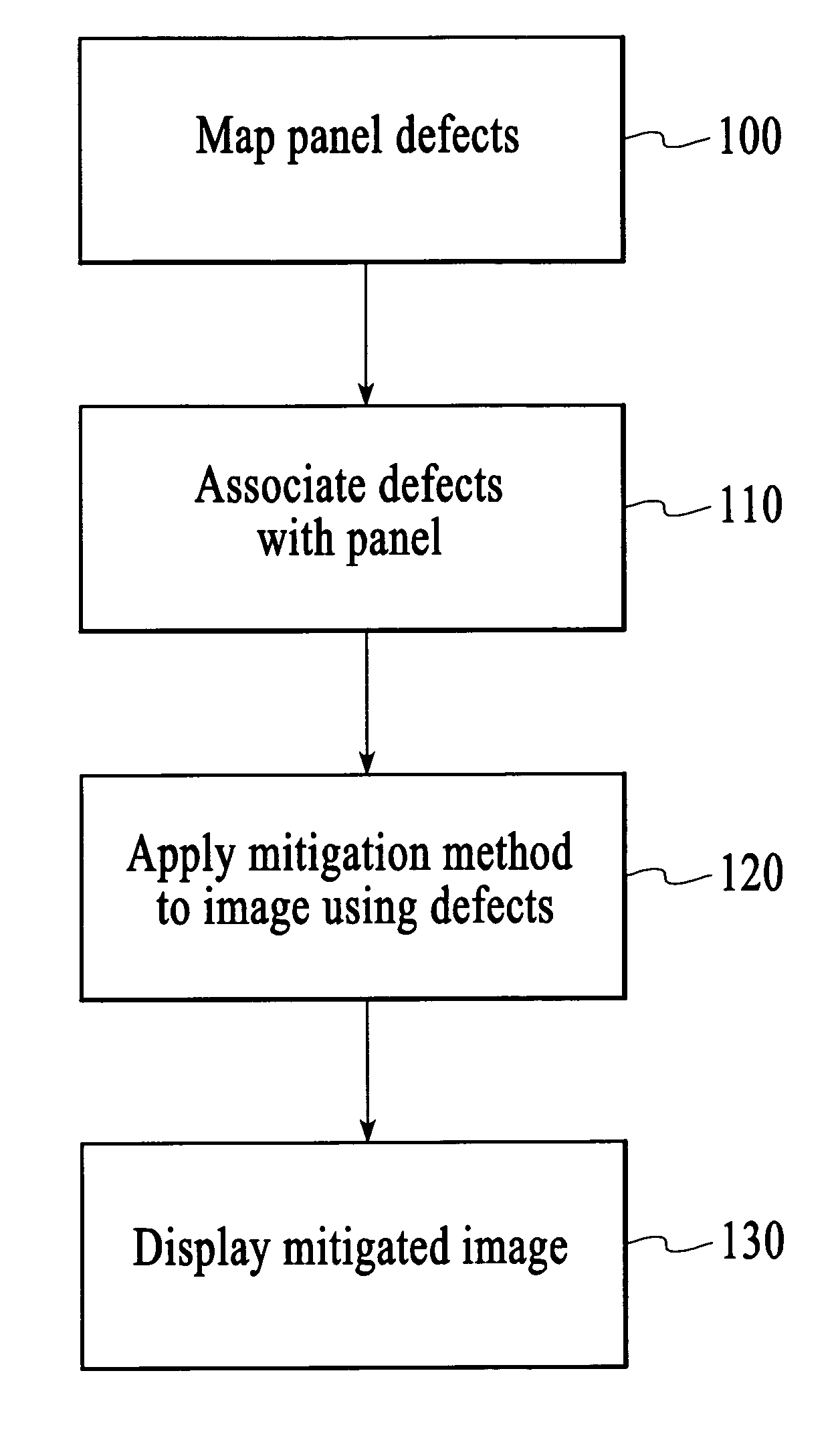
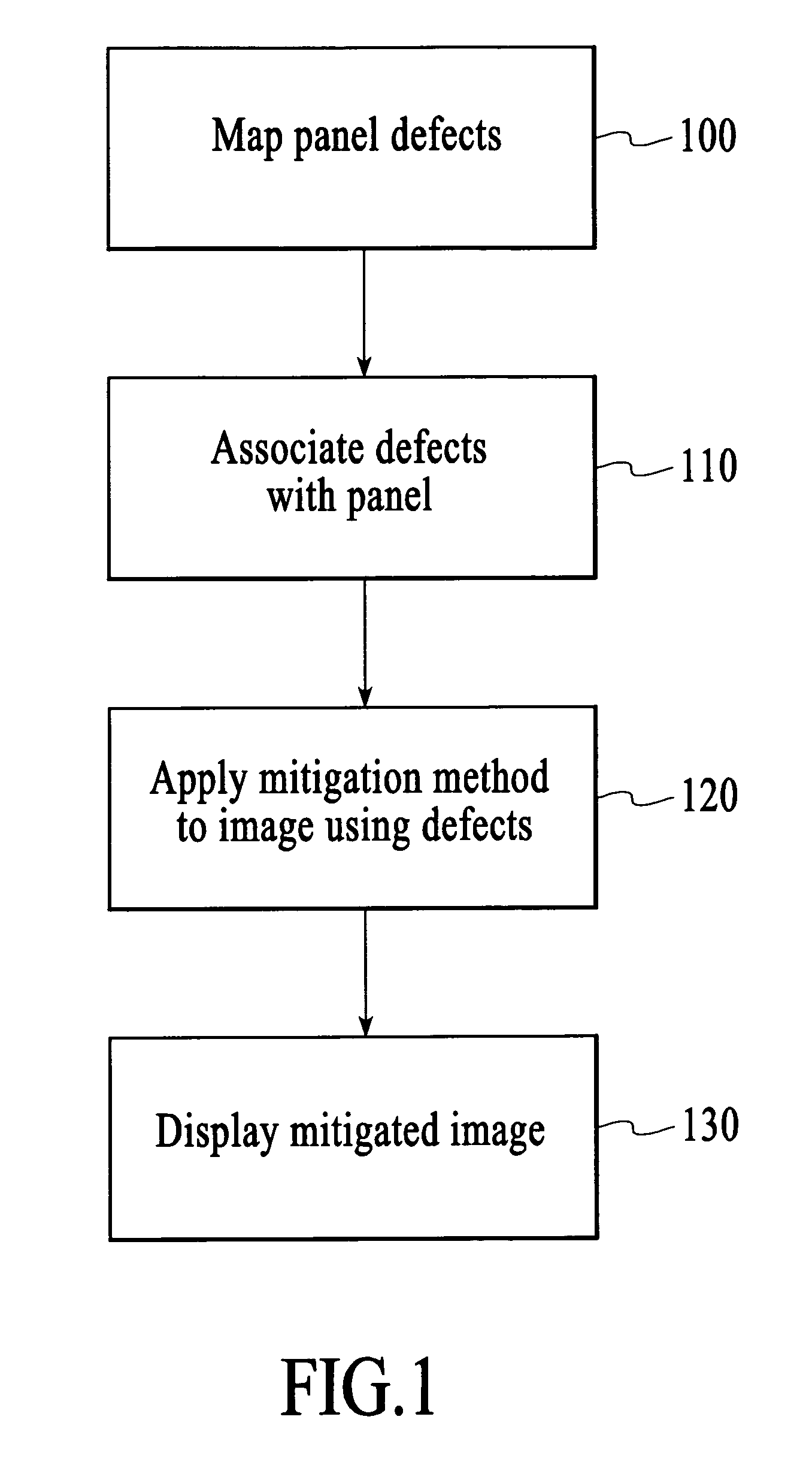
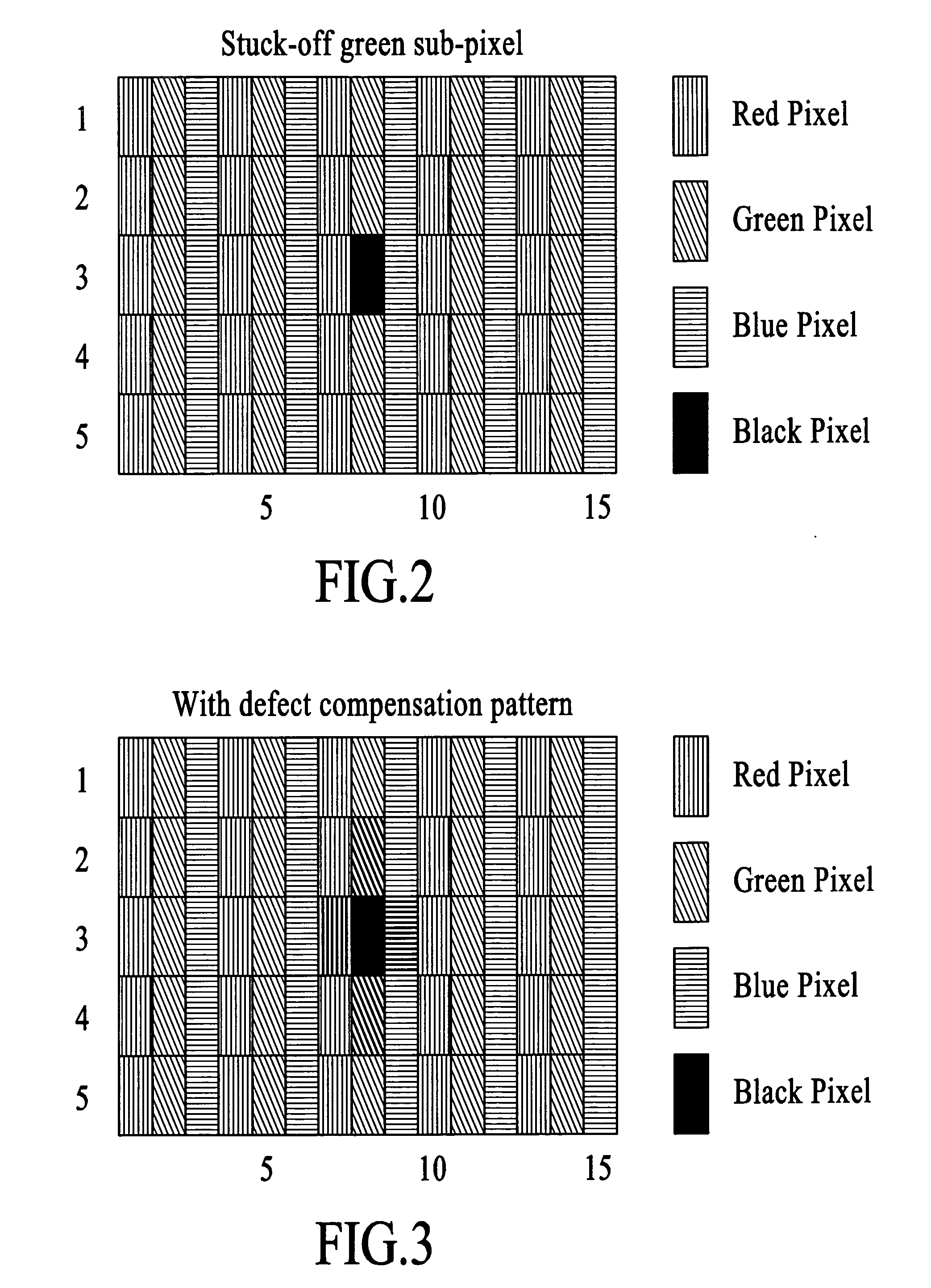
Defect mitigation in display panels
Defect mitigation in display panels. Defects in a display panel are mapped, and the defect information is associated with the display system or associated with the panel. During panel operation, the values of pixels neighboring defective pixels are altered to minimize their visibility to the observer. In a first model, luminance error caused by a defect is compensated by adjust neighboring pixels. In a second model, Error in luminance and one of the two chrominance channels is compensated by adjusting neighboring pixels. The defect mitigation methods seek to shift the errors introduced by defective pixels into high spatial frequency elements and chromatic elements, which the human eye is not sensitive to.
Owner:WISTRON CORP
Dynamic denial of service detection and automated safe mitigation
Methods, systems, and computer programs are presented for automated detection and mitigation of Denial of Service (DoS) attacks. One method includes an operation for collecting traffic data from service network routers that provide users access to a service. The traffic data is applied to security rules to identify a blacklist of illegitimate users to be blocked. Further, the method receives from the one or more servers a whitelist with information regarding legitimate users and their geographical location. A safe blacklist is determined for each router based on the blacklist and the whitelist, and the respective safe blacklist is sent to each router. Legitimate users are not blocked from accessing the service, but an illegitimate user spoofing a legitimate user is blocked by the routers when trying to access the service from a geographic location that is not the geographic location of the legitimate user.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
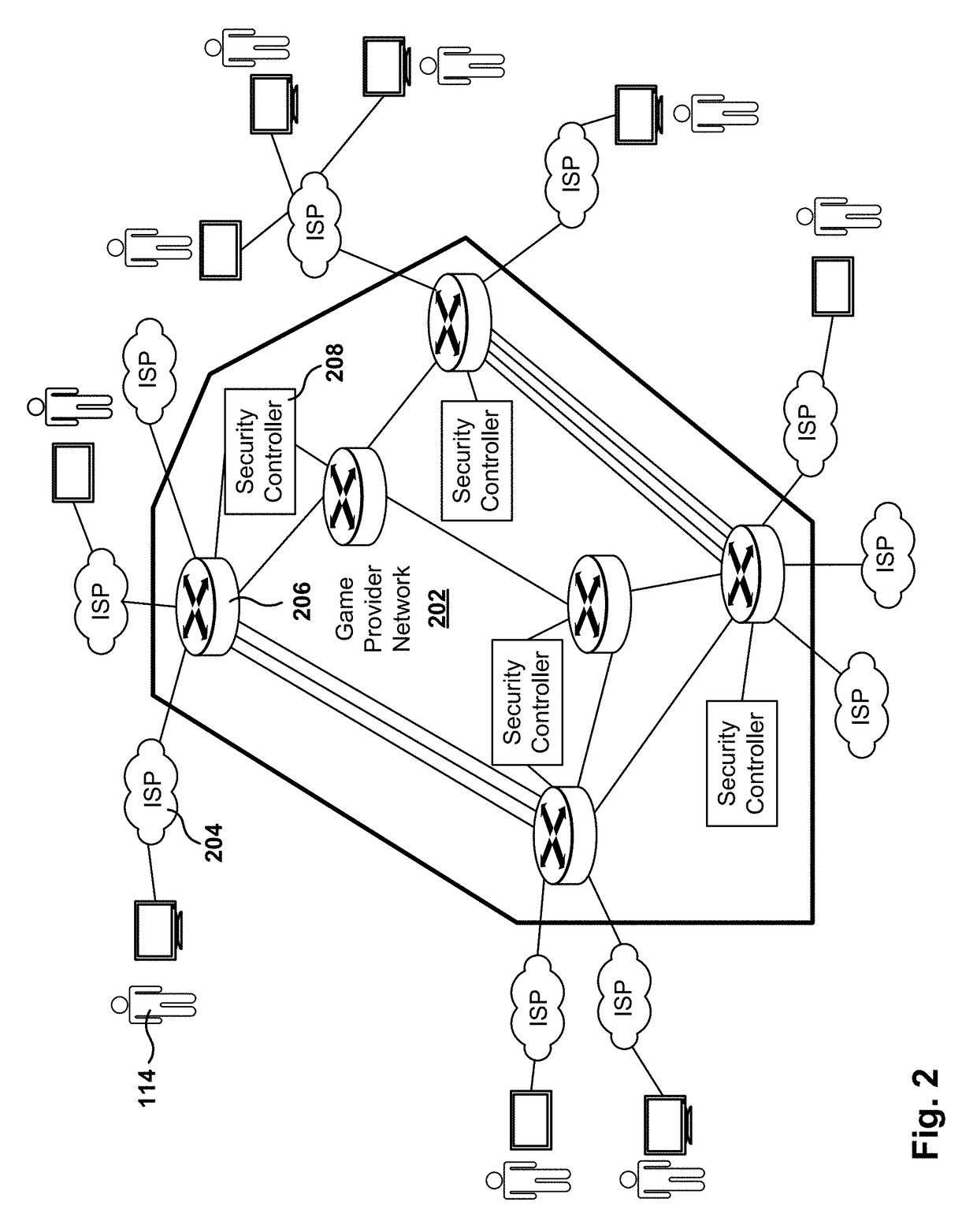
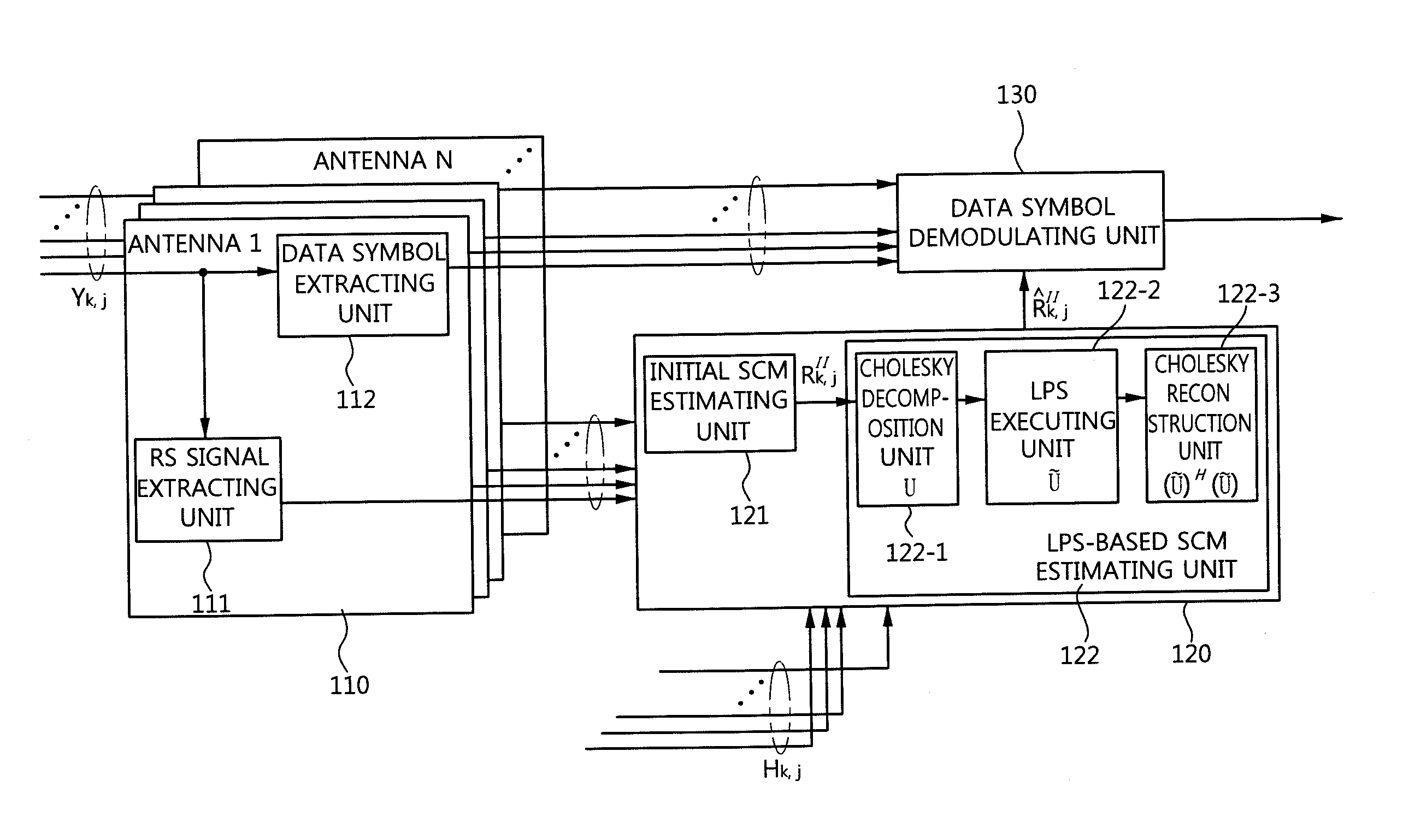
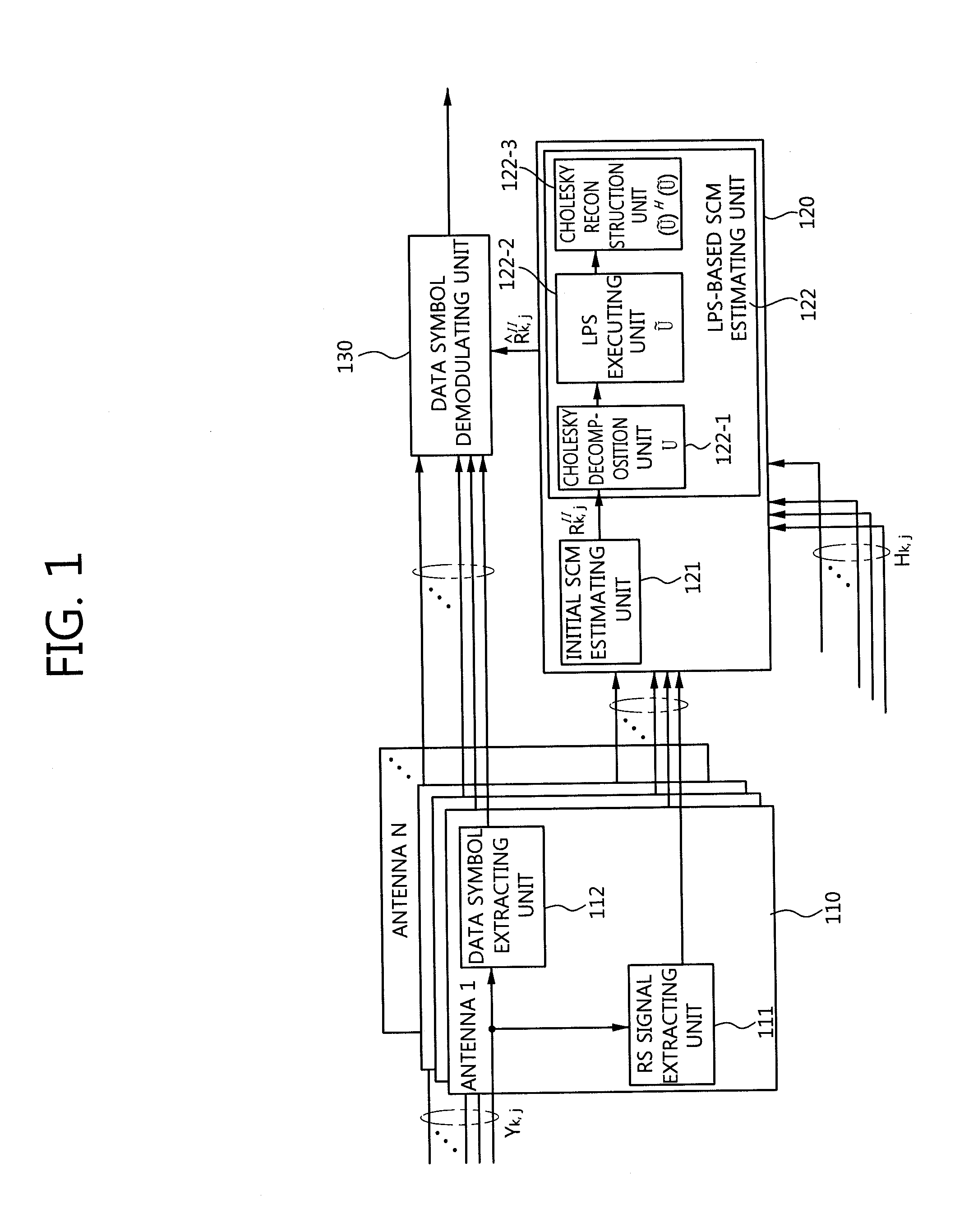
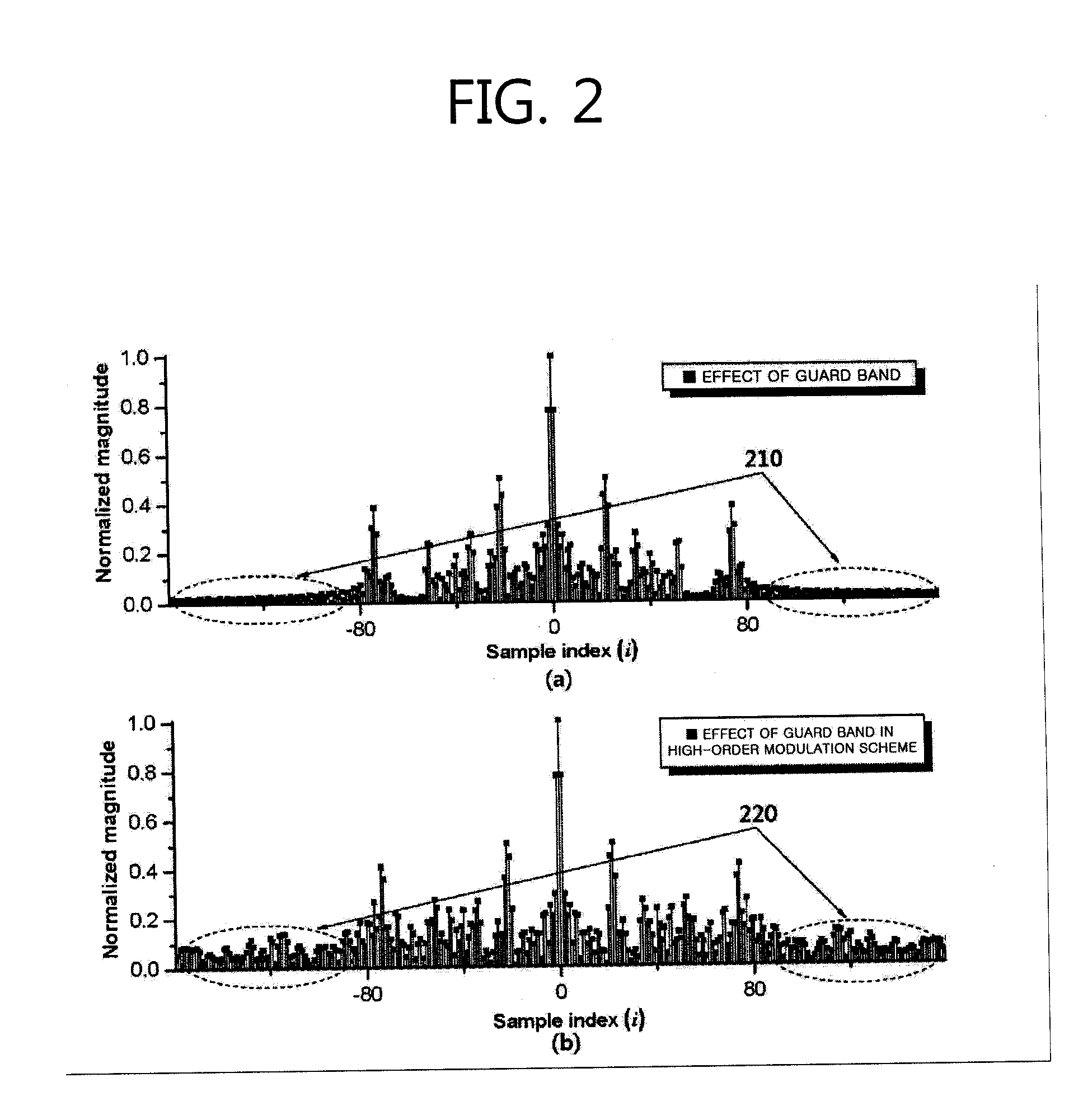
Inter-cell interference mitigation method using spatial covariance matrix estimation method for inter-cell interference mitigation of MIMO antenna OFDM system
ActiveUS20120063529A1Reduce errorsSimple designDiversity/multi-antenna systemsChannel estimationMulti inputMoving average
Disclosed is an inter-cell interference mitigation method using a spatial covariance matrix (SCM) estimation method in a multi-input multi-output (MIMO) orthogonal frequency division multiplexing (OFDM) communication system for mitigating interference between asynchronous cells. The inter-cell interference mitigation method includes extracting a reference symbol (RS) of a received OFDM symbol and performing channel estimation, estimating an initial SCM using the RS signal and the channel estimation result, applying time-domain sinc type weighting to the initial SCM and applying an SCM, and demodulating a data symbol with mitigated inter-cell interference using the channel estimation result and the estimated SCM. By applying time-domain sinc type weighting to SCM estimation, it is possible to reduce an SCM estimation error occurring due to a spectral leakage induced by an abrupt change in a signal at a border point between an effective sub carrier zone and a guard band zone, and a simple design of a moving average filter form for a frequency domain signal can be made instead of frequency-time-frequency domain transformation using an inverse fast Fourier transform (IFFT) and fast Fourier transfer (FFT).
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
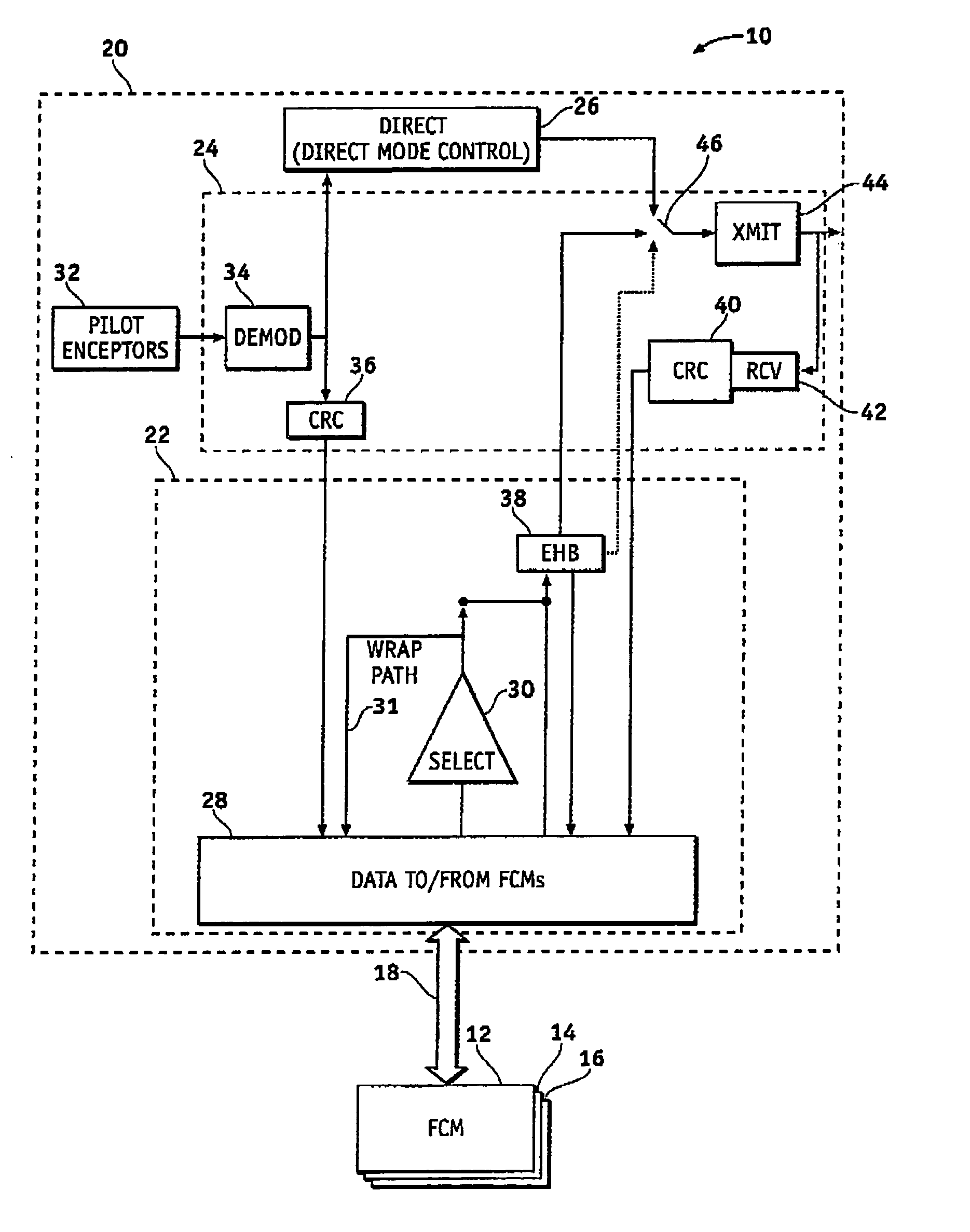
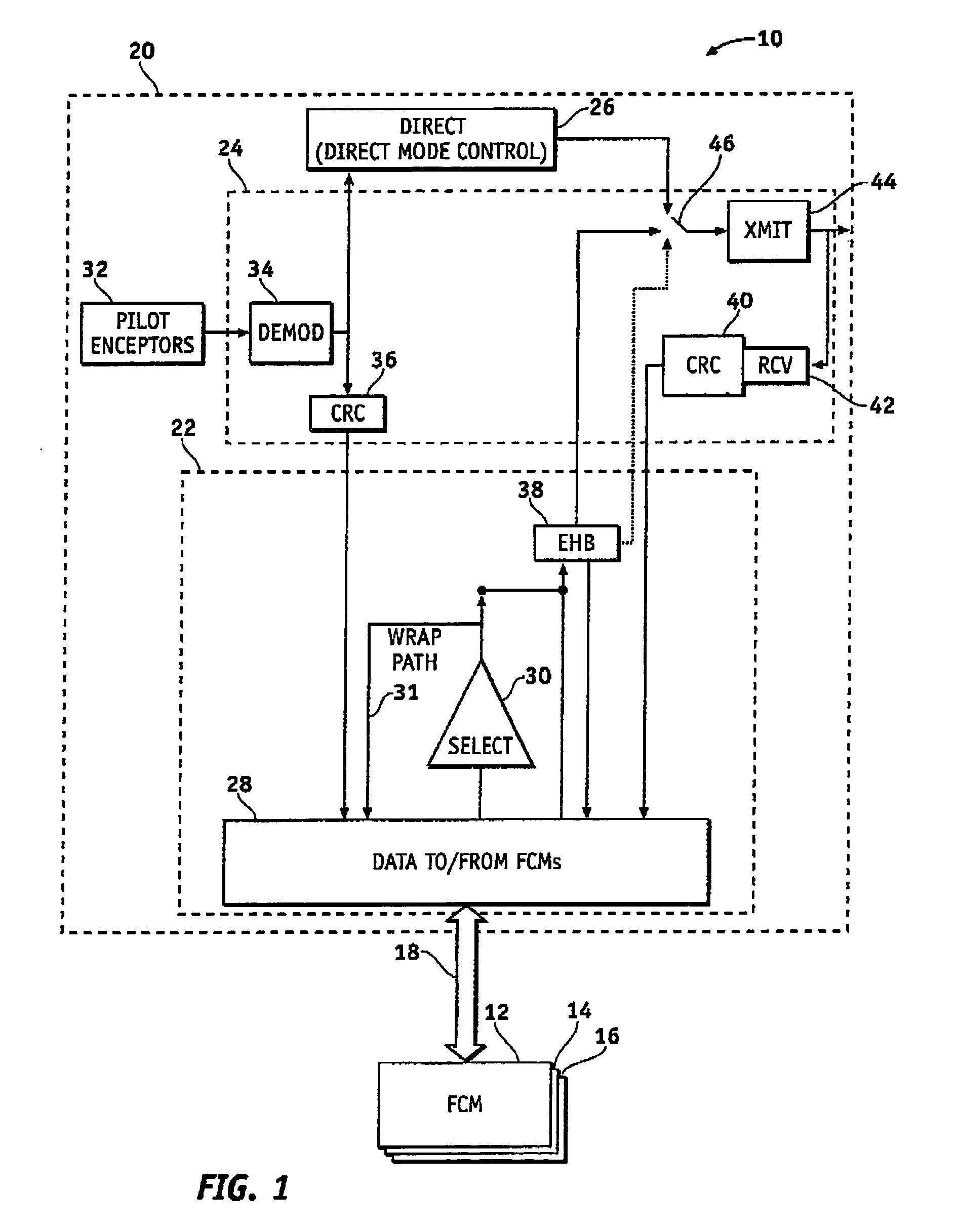
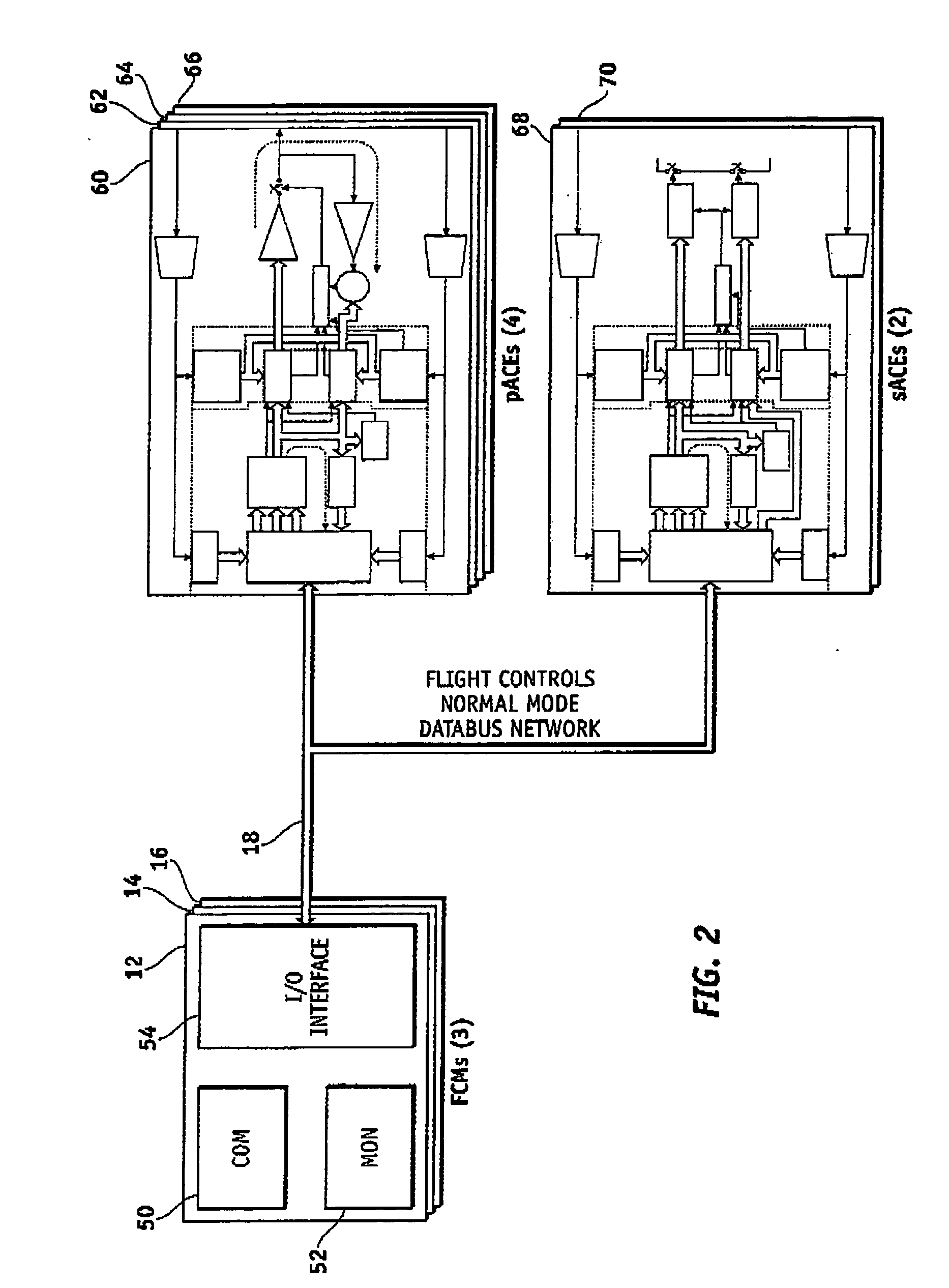
System and method of redundancy management for fault effect mitigation
Methods and systems are provided for redundancy management of a fly-by-wire avionics system. A control module for producing a control signal is provided comprising a common processing partition for receiving a flight input signal and at least one first mode input signal, a first processing partition coupled to the common processing partition and configured to receive the first mode input signals and flight input signal from the common processing partition, and a second processing partition coupled to the common processing partition. The first processing partition produces a first mode output signal in response to one of the first mode input signals and flight input signal. The second processing partition generates a second mode signal in response to the flight input signal when the first processing partition fails. The common processing partition produces the control signal in response to one of the first mode output signal and second mode signal.
Owner:HONEYWELL INT INC
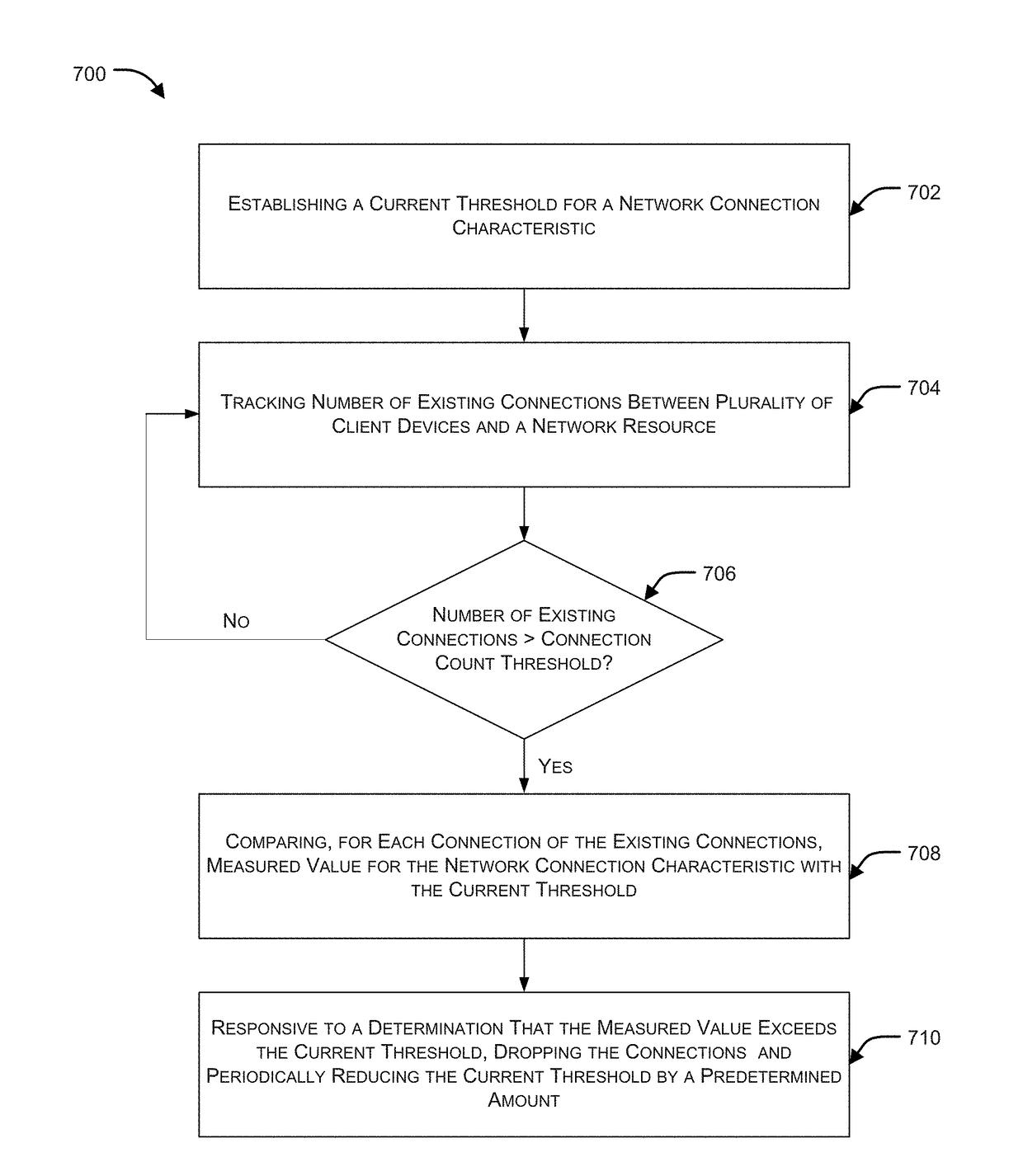
Denial-of-service (DOS) mitigation approach based on connection characteristics
Systems and methods for an improved DDoS mitigation approach are provided. According to one embodiment, a current threshold for a network connection characteristic is established within a Denial-of-Service (DoS) mitigation device logically interposed between a protected resource of a private network and multiple client devices residing external to the private network. A number of connections between the client devices and the protected network resource are tracked. During a period of time in which the number of connections exceeds a connection count threshold: (i) for each of the connections, a measured value for the network connection characteristic is compared to the current threshold; (ii) responsive to a determination that the measured value exceeds the current threshold, the connection is dropped; and (iii) the current threshold is periodically reduced, such that only those connections complying with the current threshold are maintained.
Owner:FORTINET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com