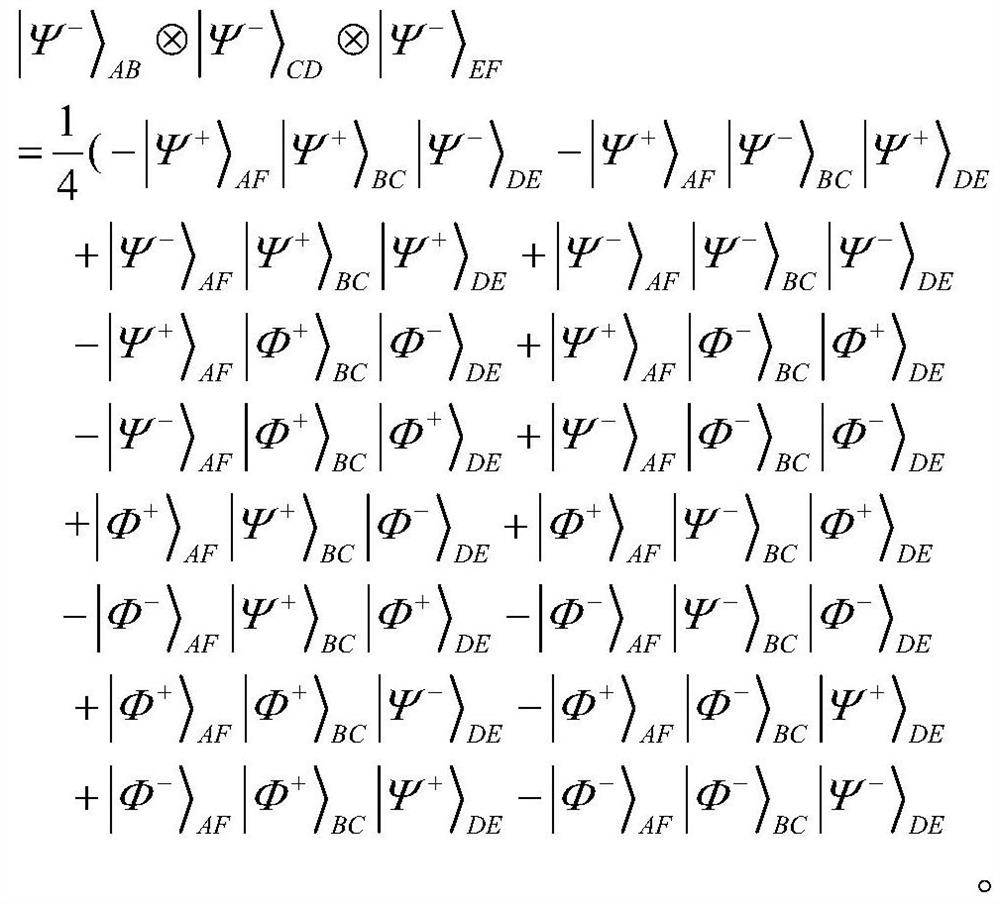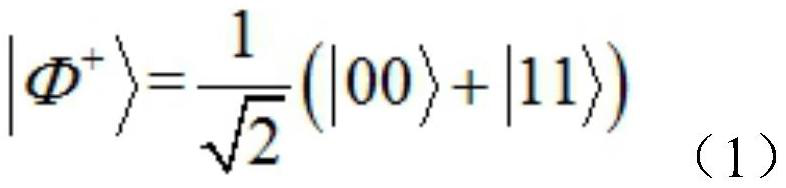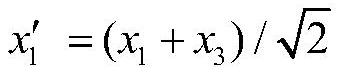Patents
Literature
43 results about "Insider attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An insider attack is a malicious attack perpetrated on a network or computer system by a person with authorized system access.
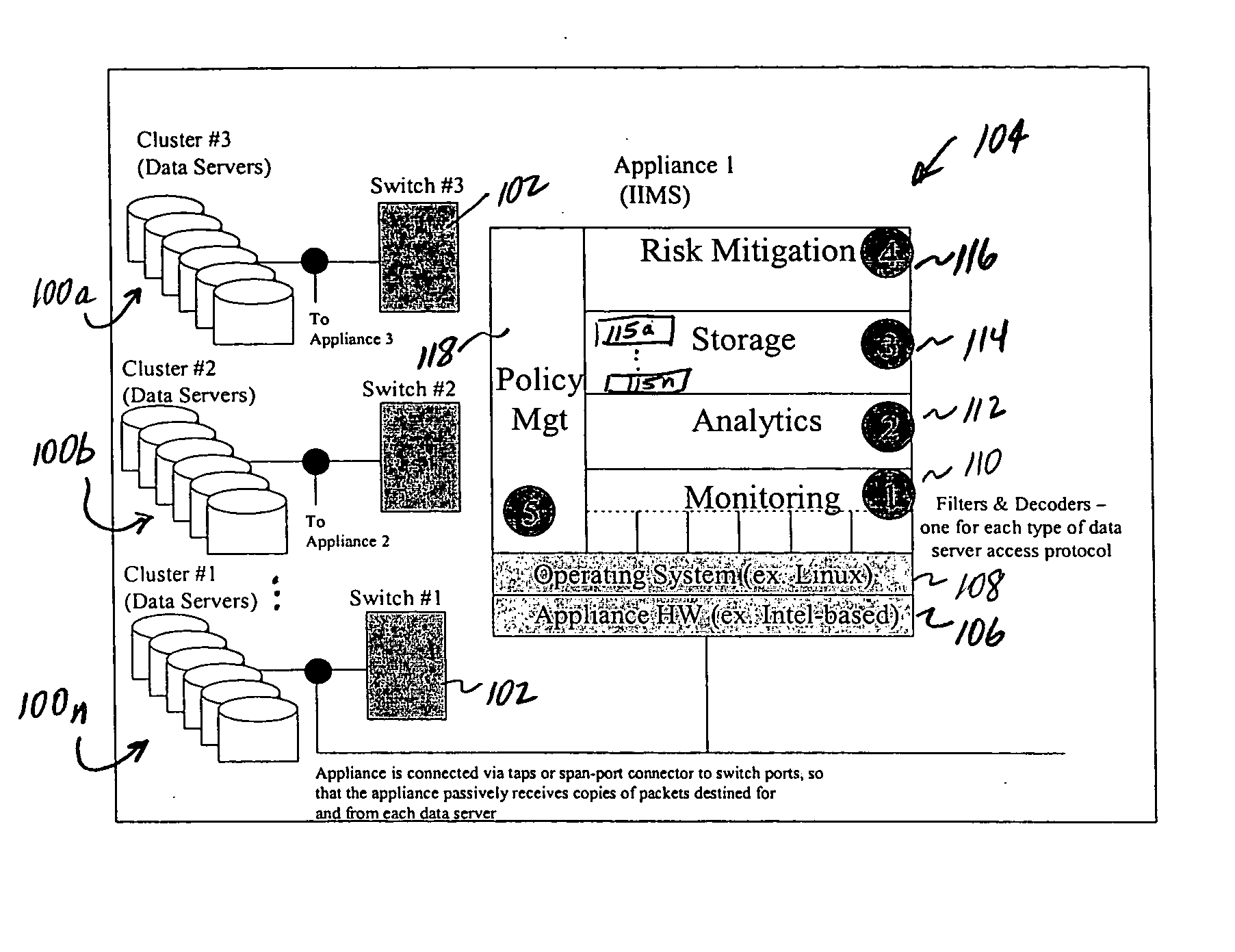
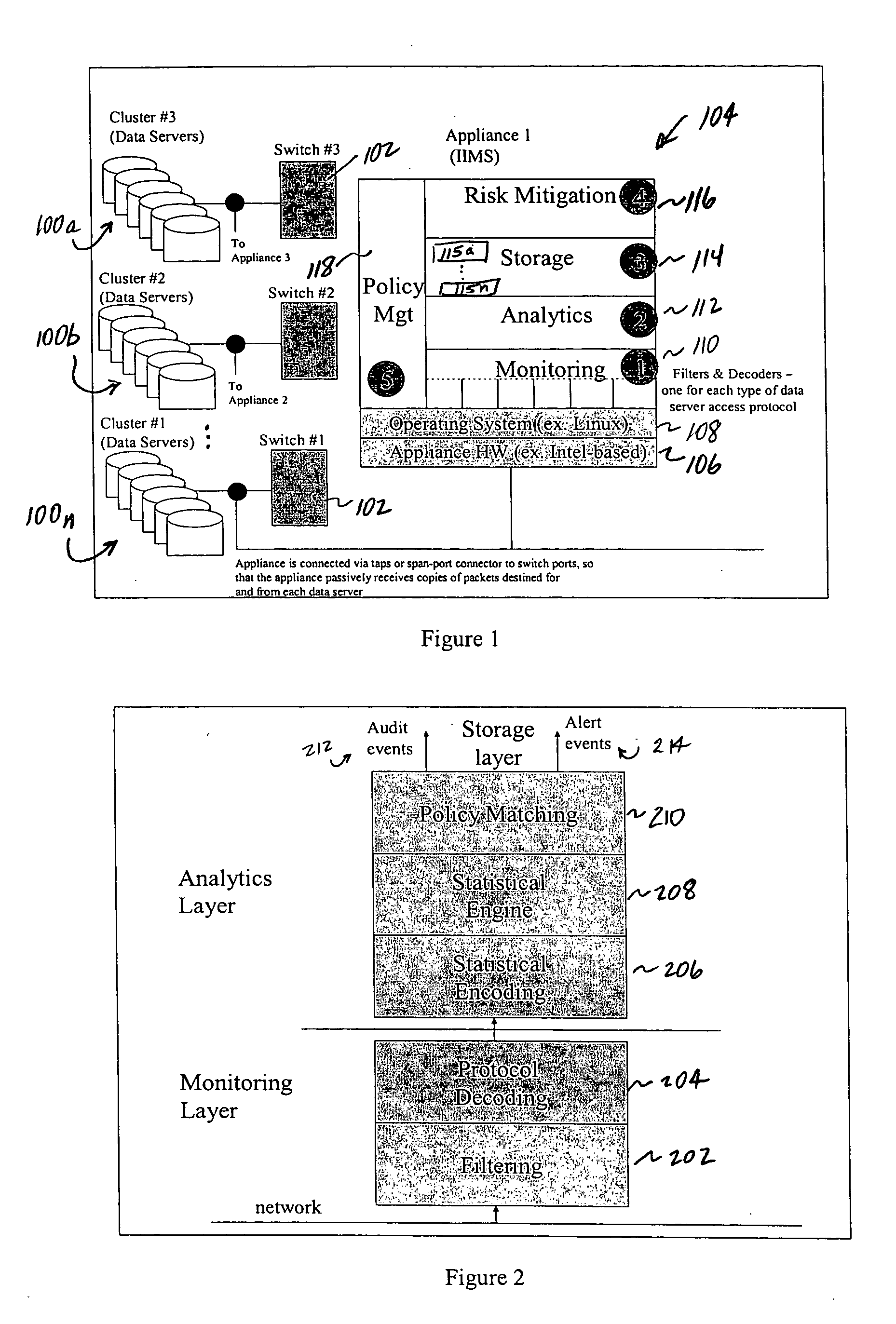
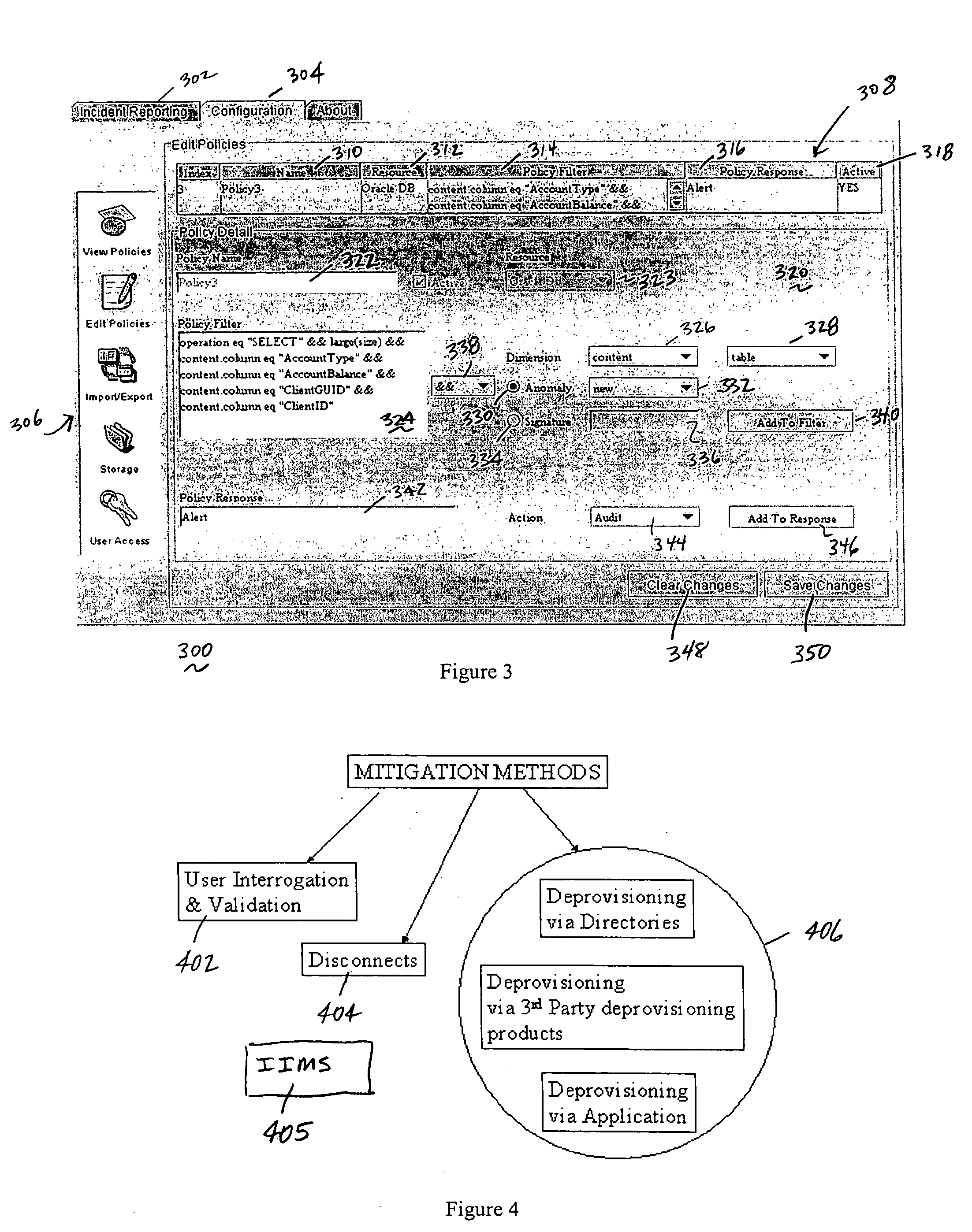
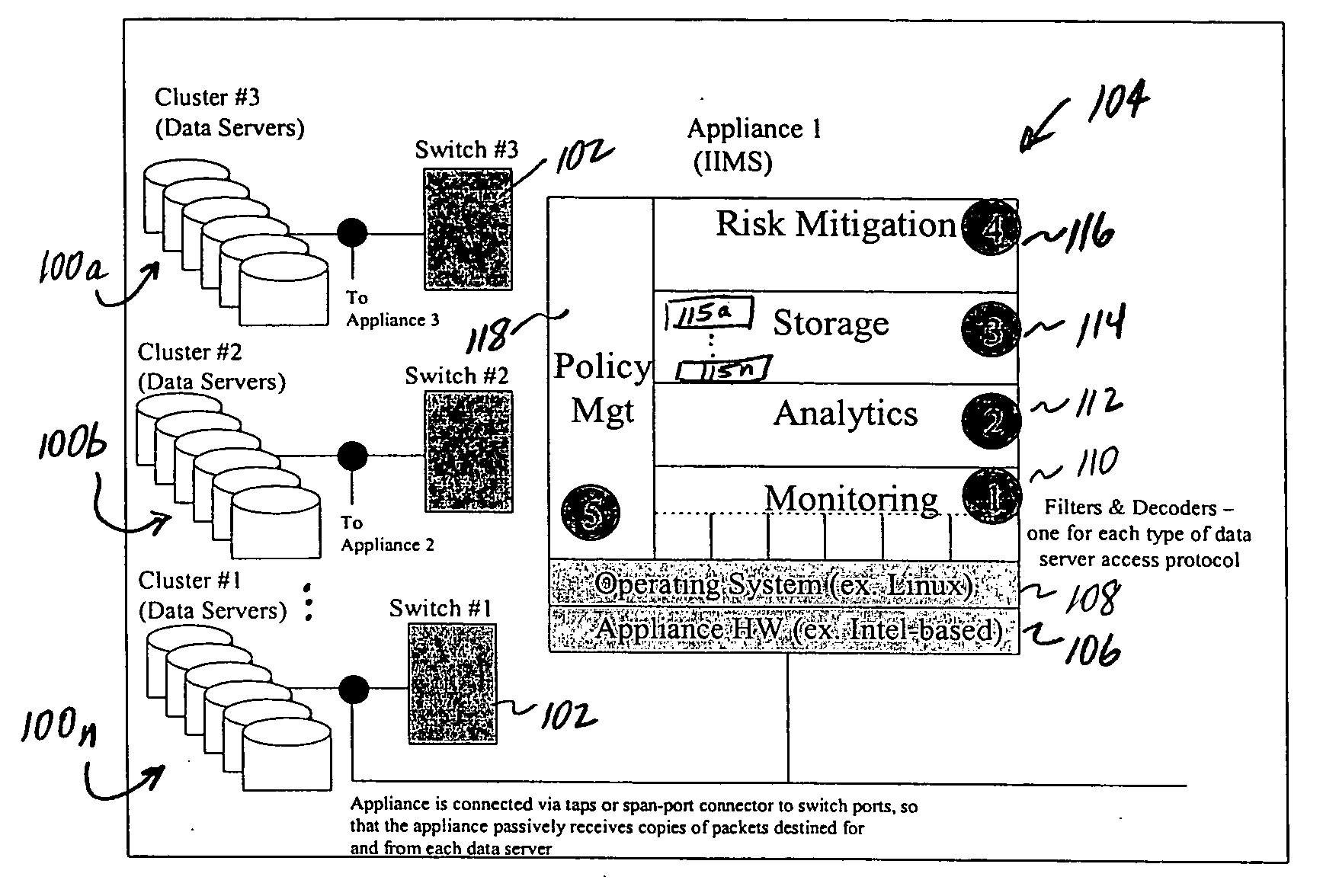
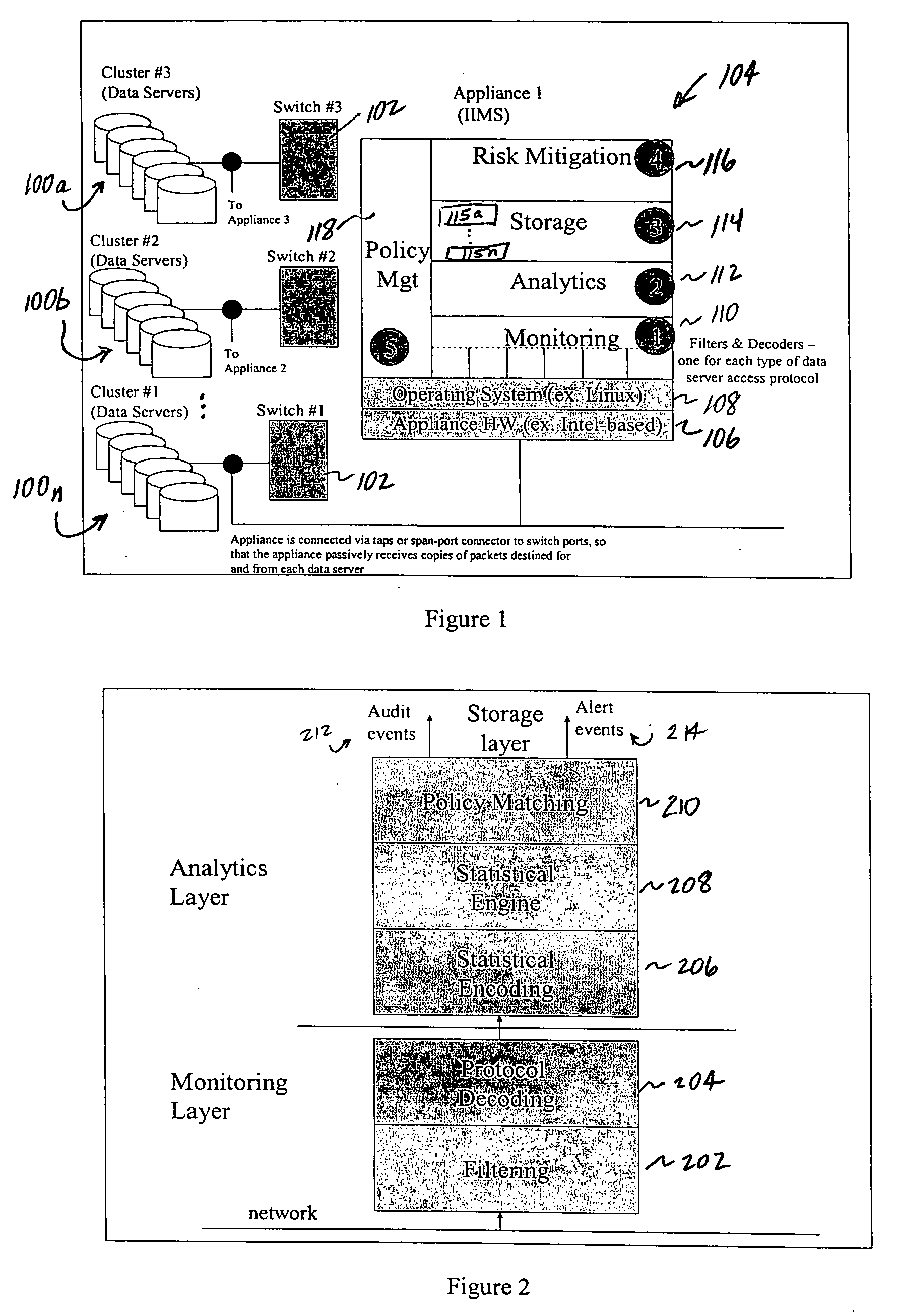
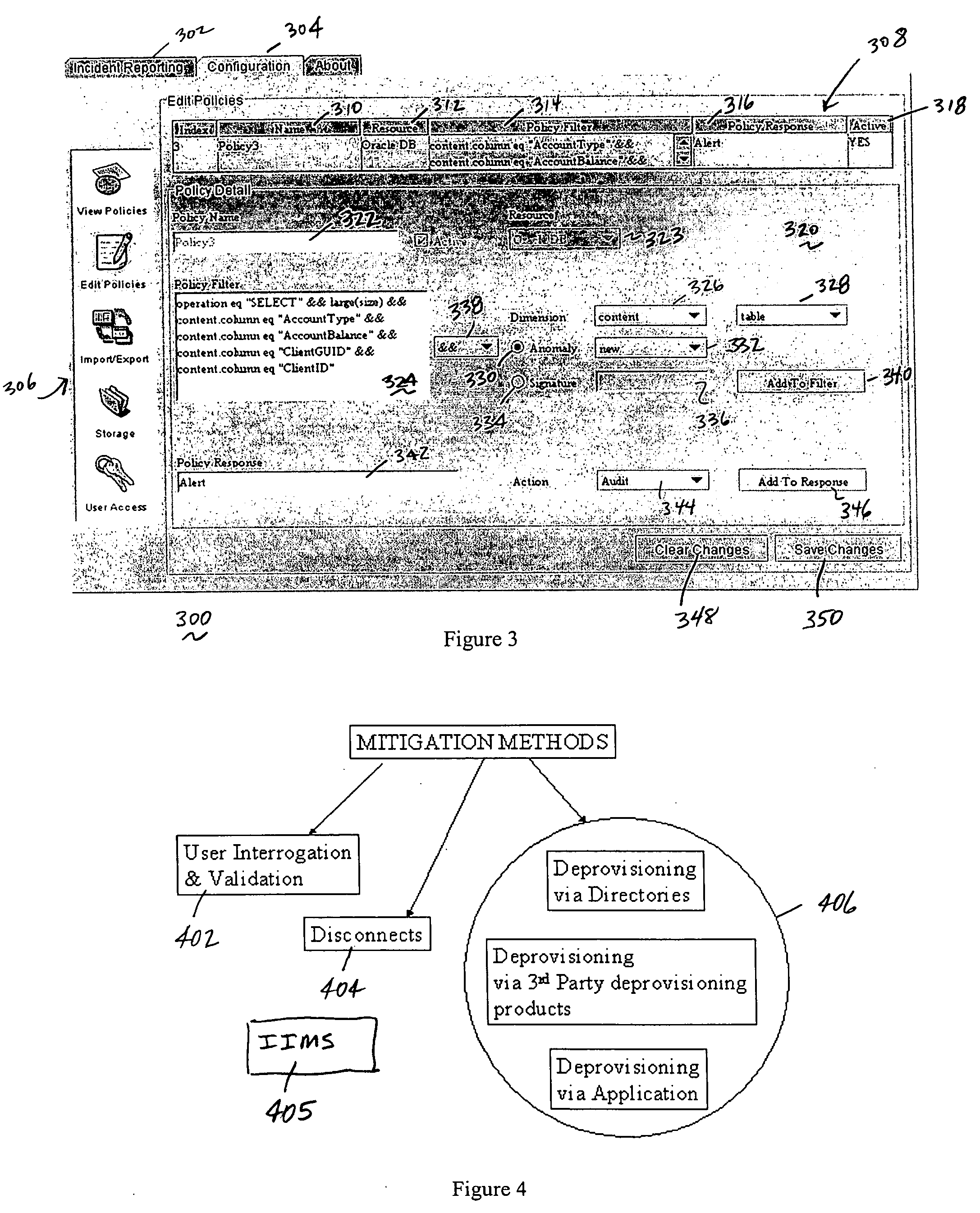
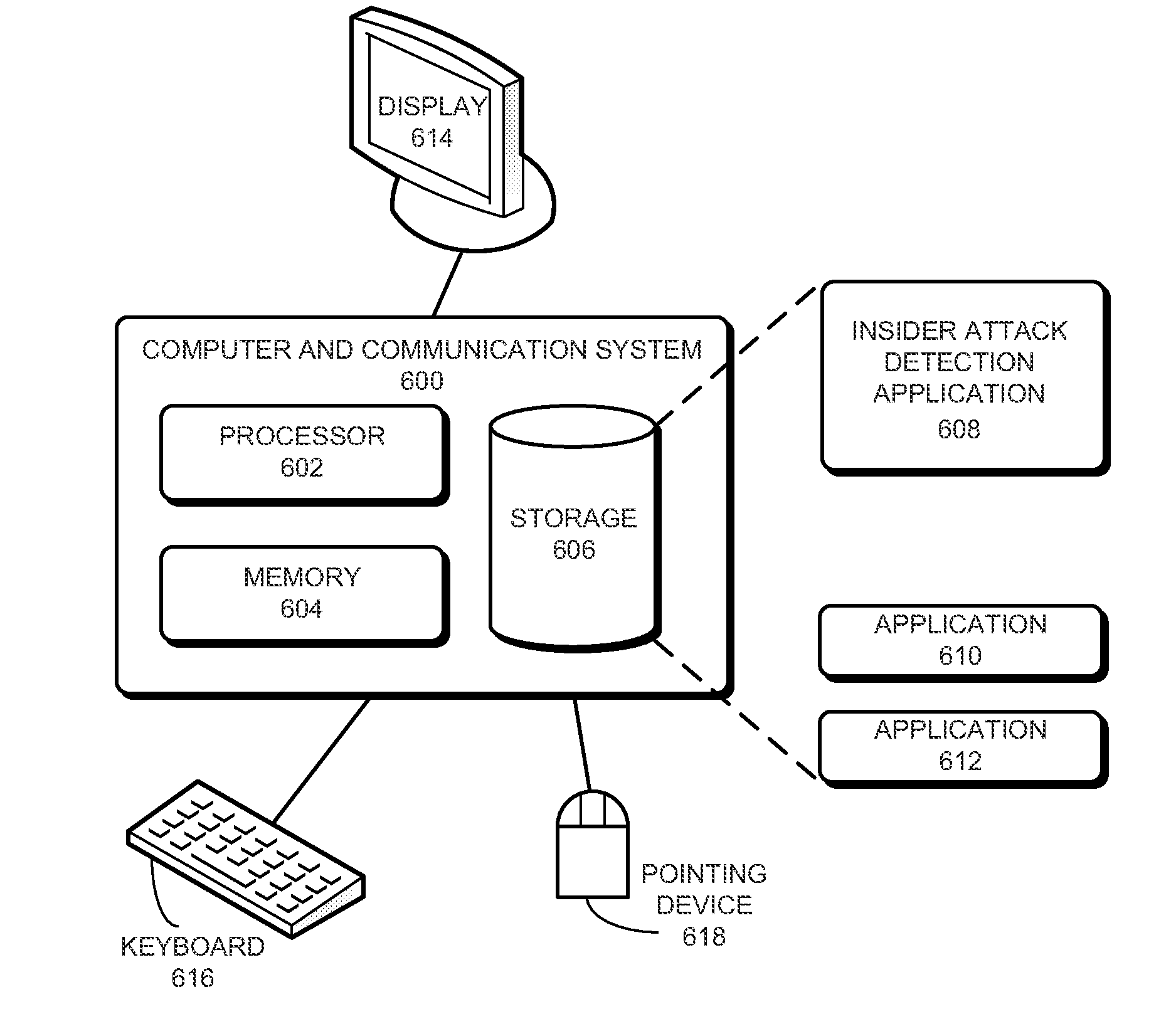
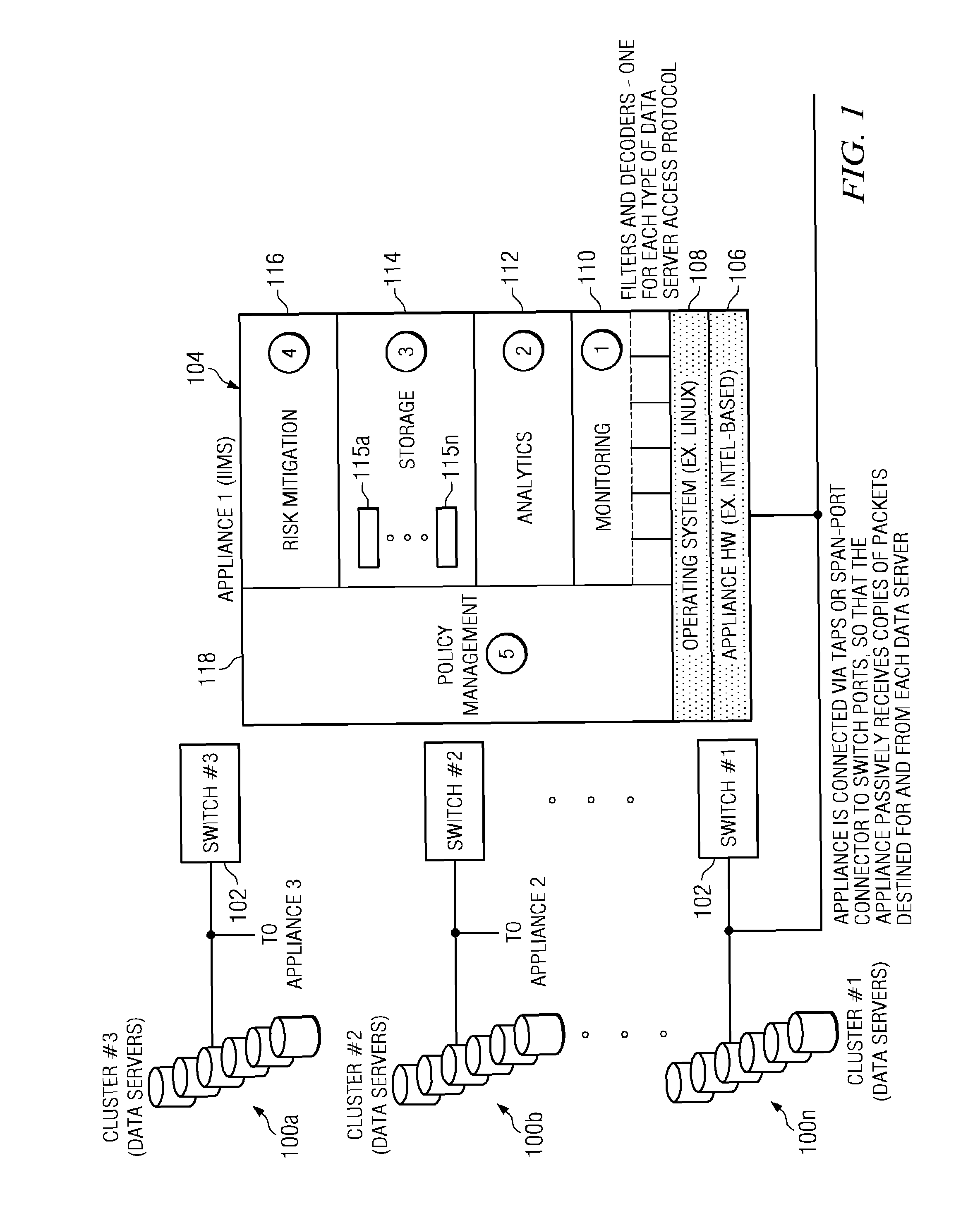
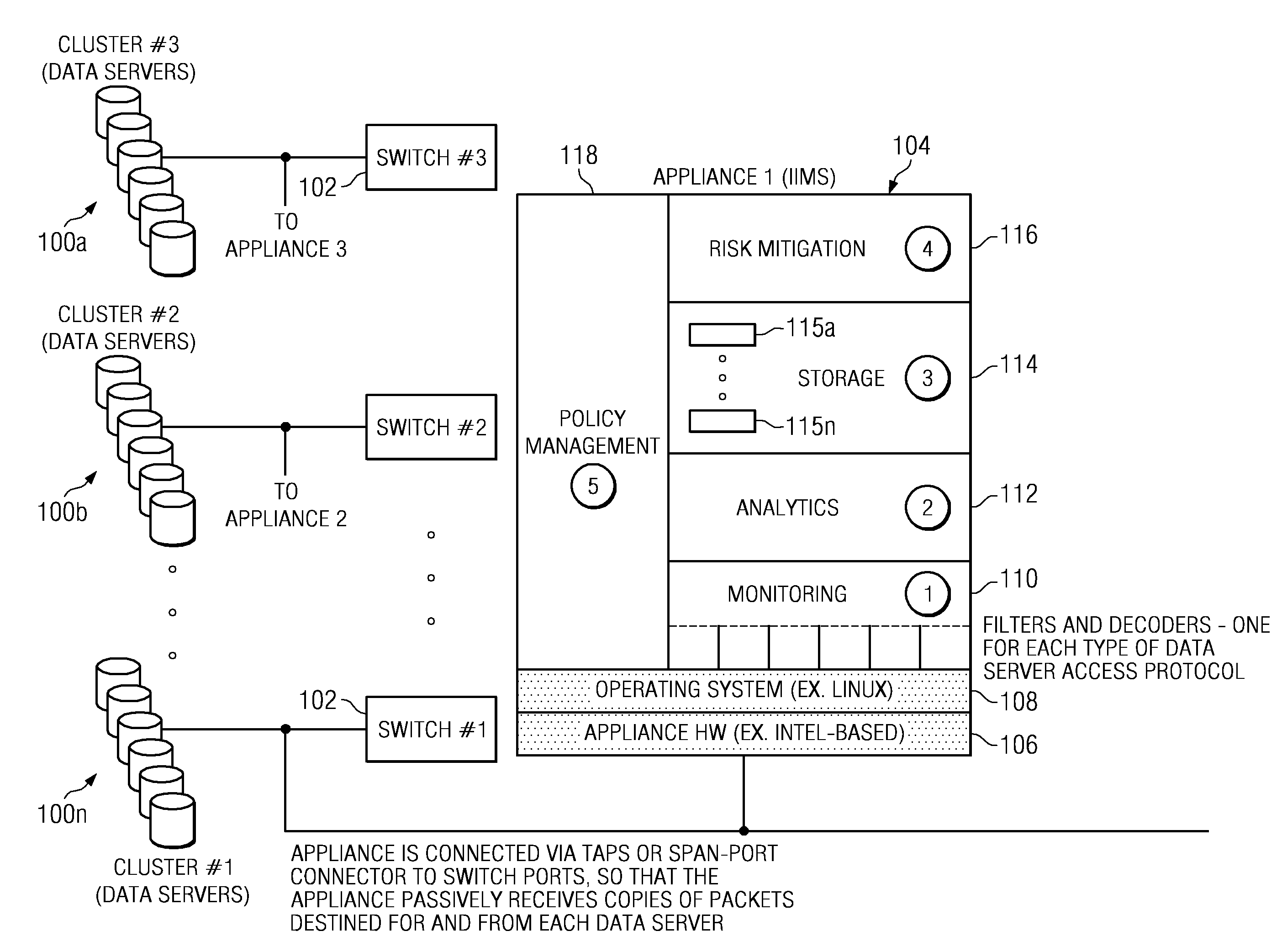
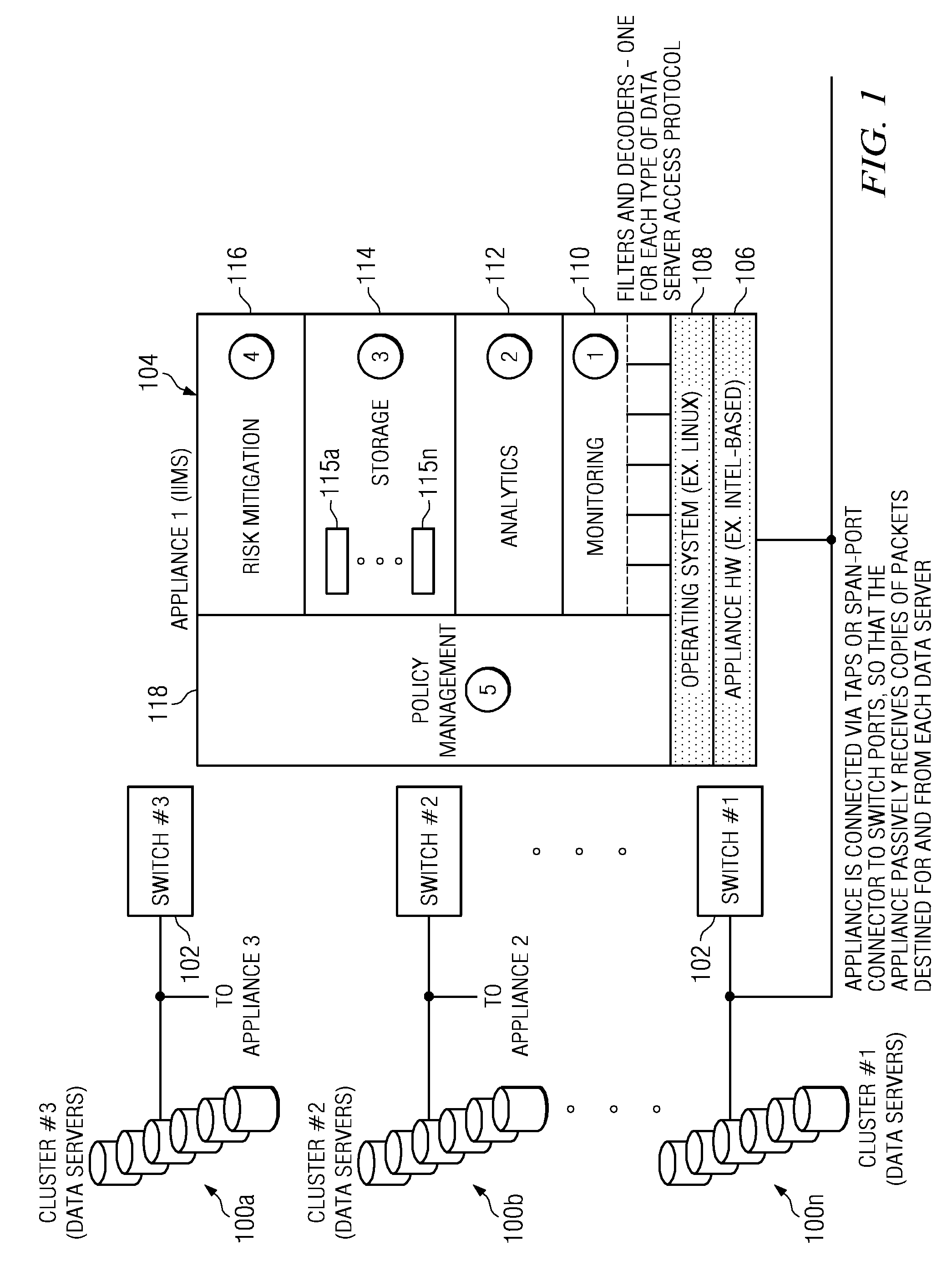
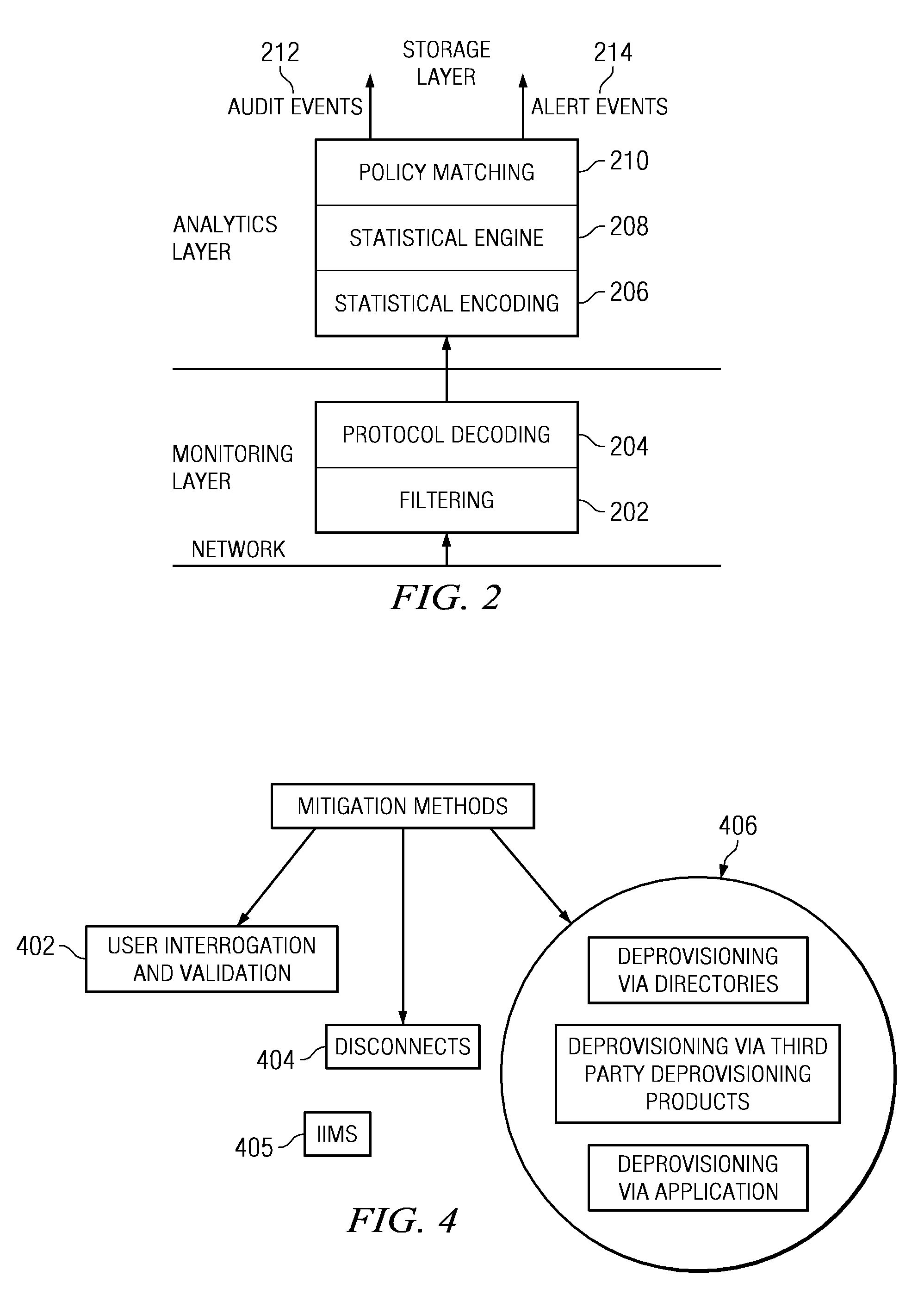
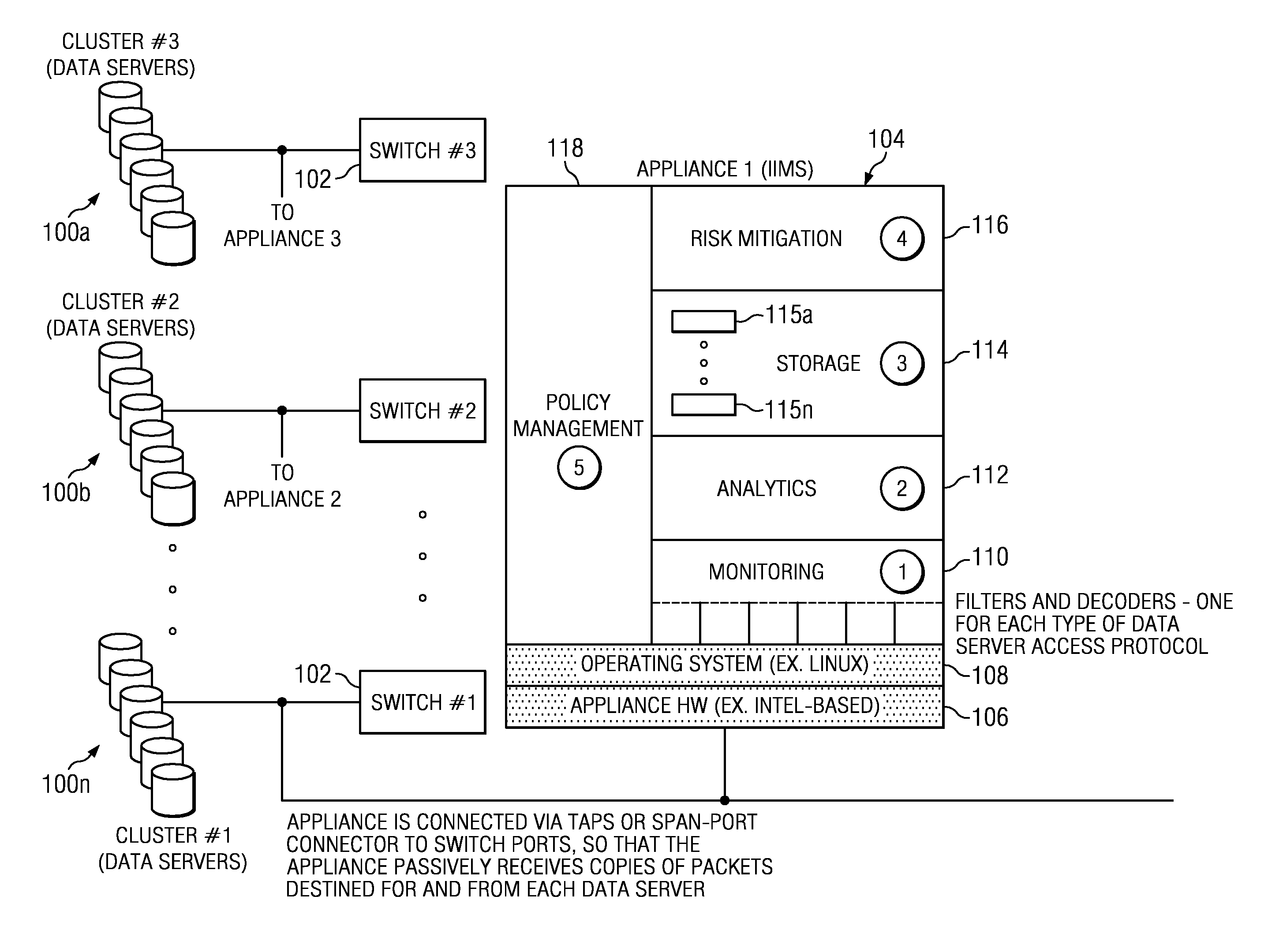
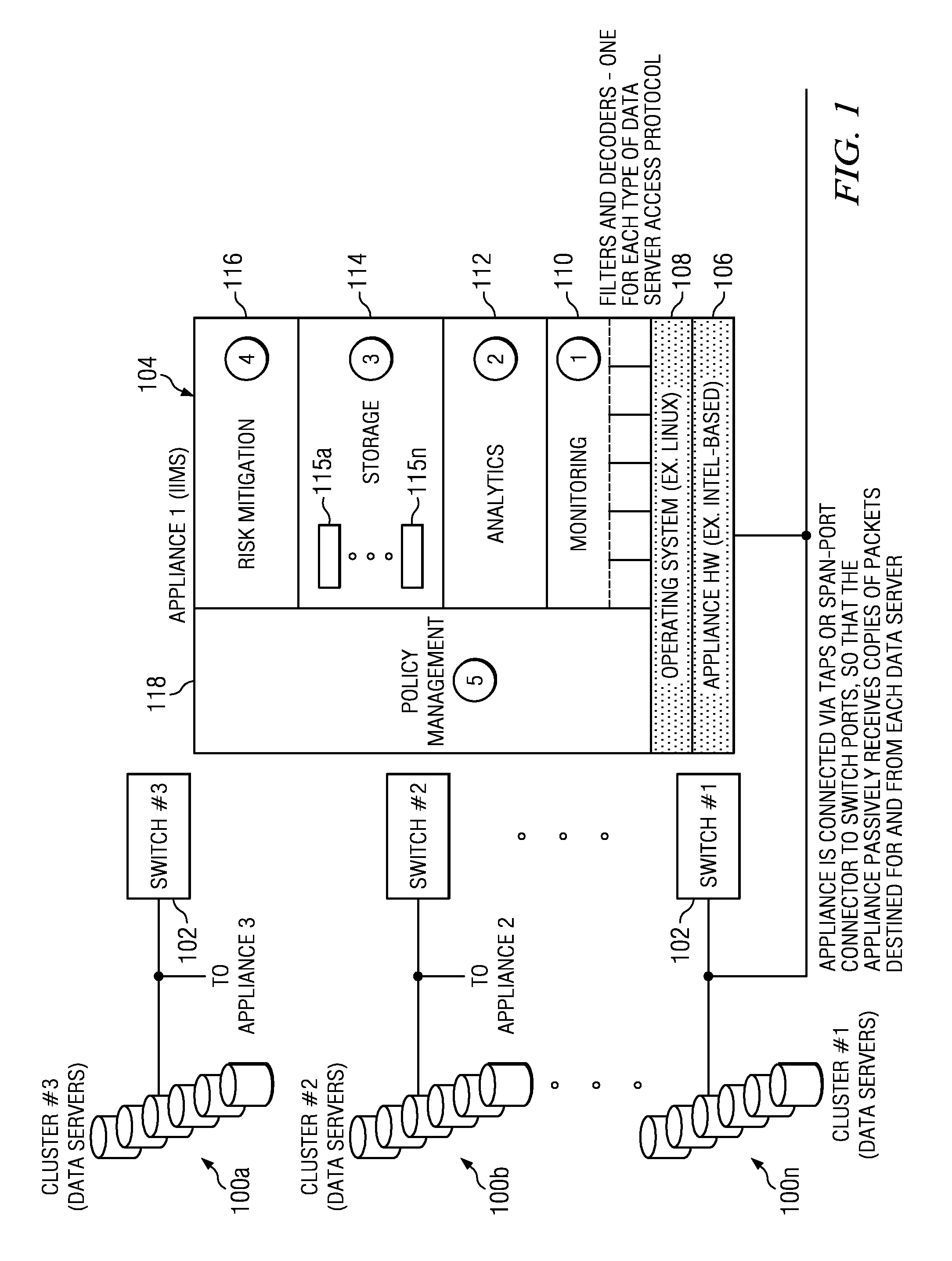
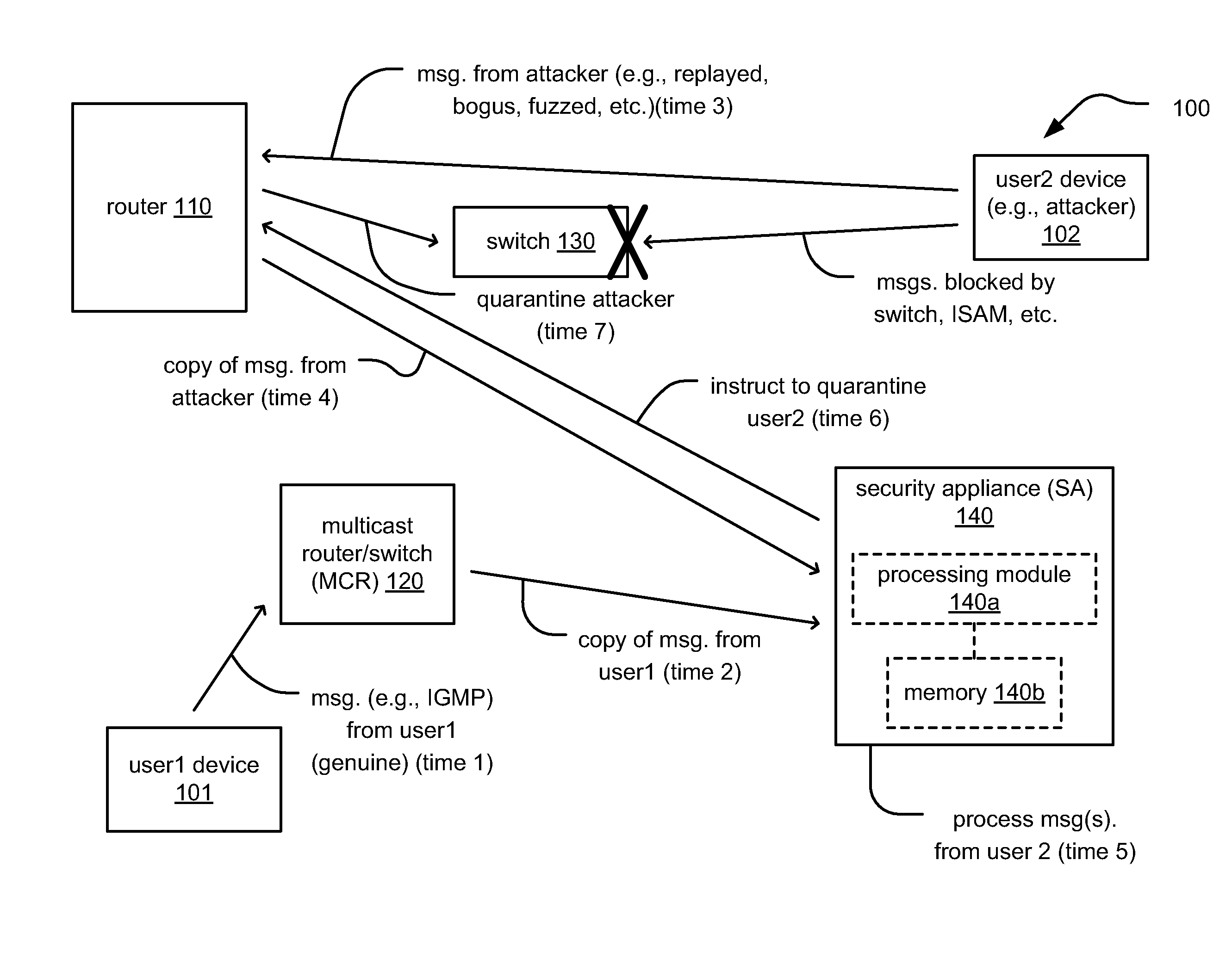
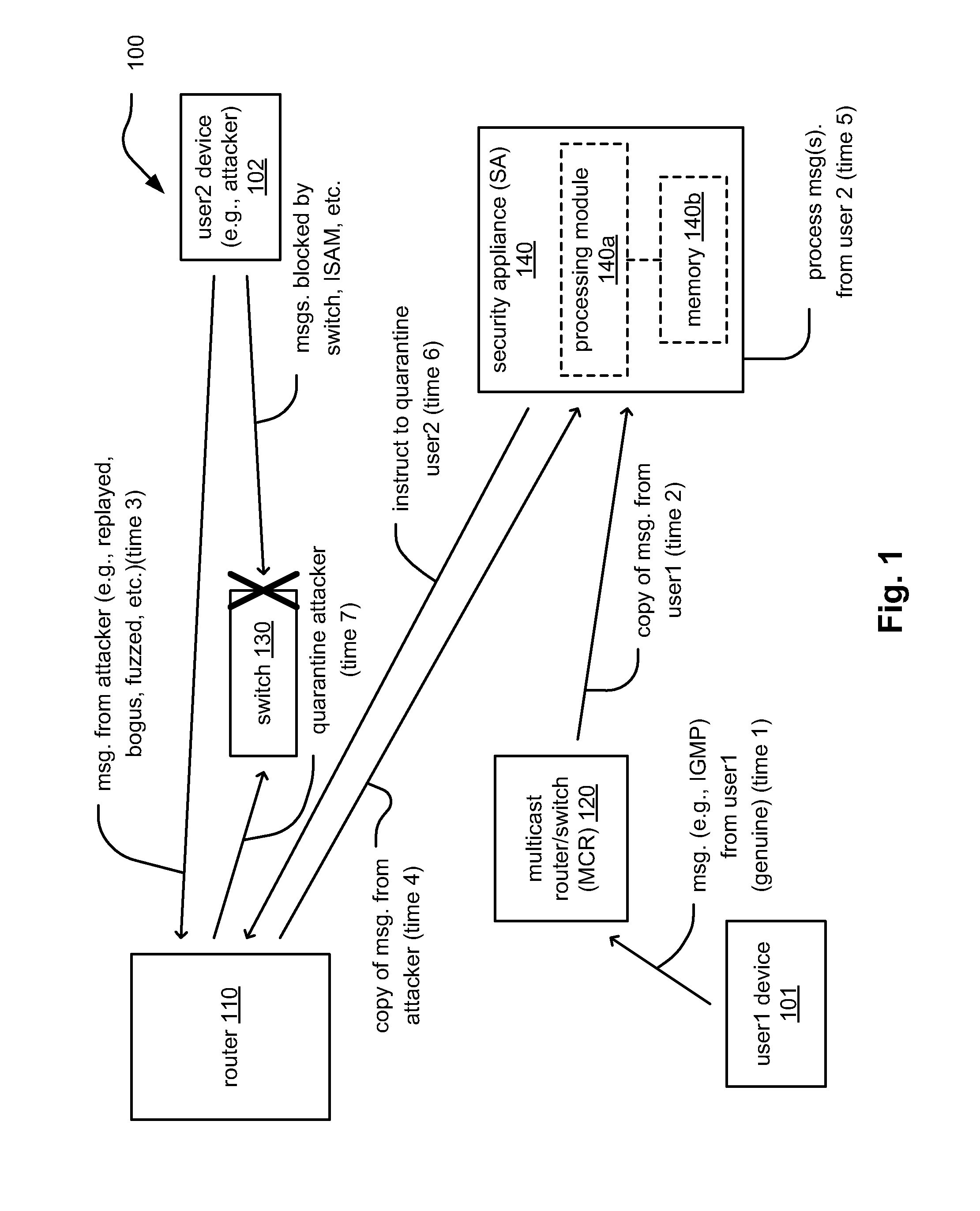
Method of and system for enterprise information asset protection through insider attack specification, monitoring and mitigation
ActiveUS20050071643A1Reduce harmComputer security arrangementsSecret communicationData accessAttack strategy
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of“anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
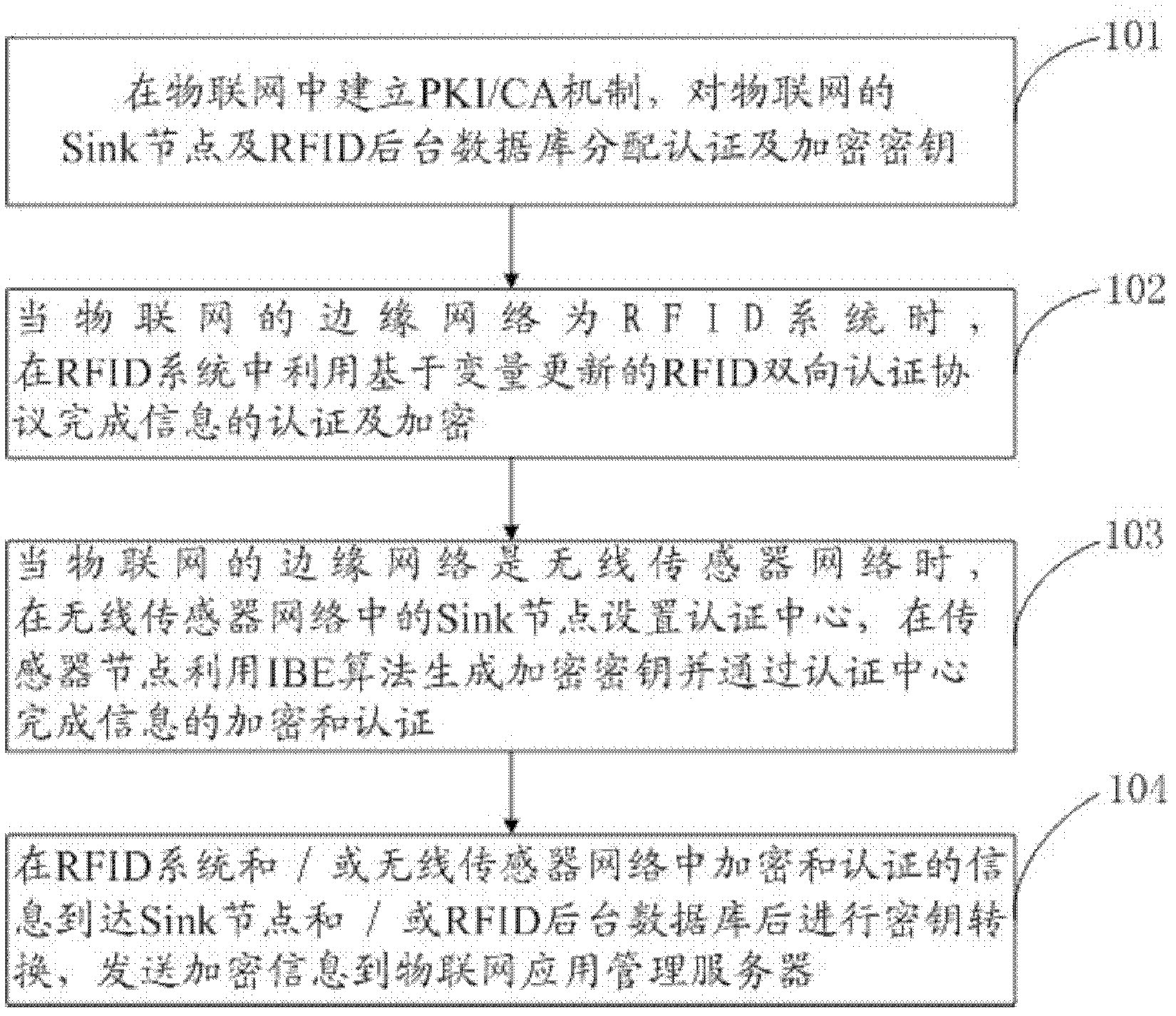
Method and system for internet of things information transmission
ActiveCN103166919AImprove securityGuaranteed privacyUser identity/authority verificationInformation transmissionThe Internet
The invention discloses a method and a system for internet of things information transmission. Firstly, a public key infrastructure / certificate authority (PKI / CA) mechanism is established in the internet of things and an authentication key and an encryption key are distributed to an aggregation node of the internet of things; transmitted information is encrypted and authorized in an edge network of the internet of things; and key conversion is conducted after the encrypted and authorized information reaches the aggregation node of the internet of things and the information encrypted again is sent to an application management server of the internet of things. According to the method and the system for the internet of things information transmission, the internet of things can effectively resist interior attack, information safety transmission level is improved and complexity of encryption and safety authentication calculation in the edge network of the internet of things is reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
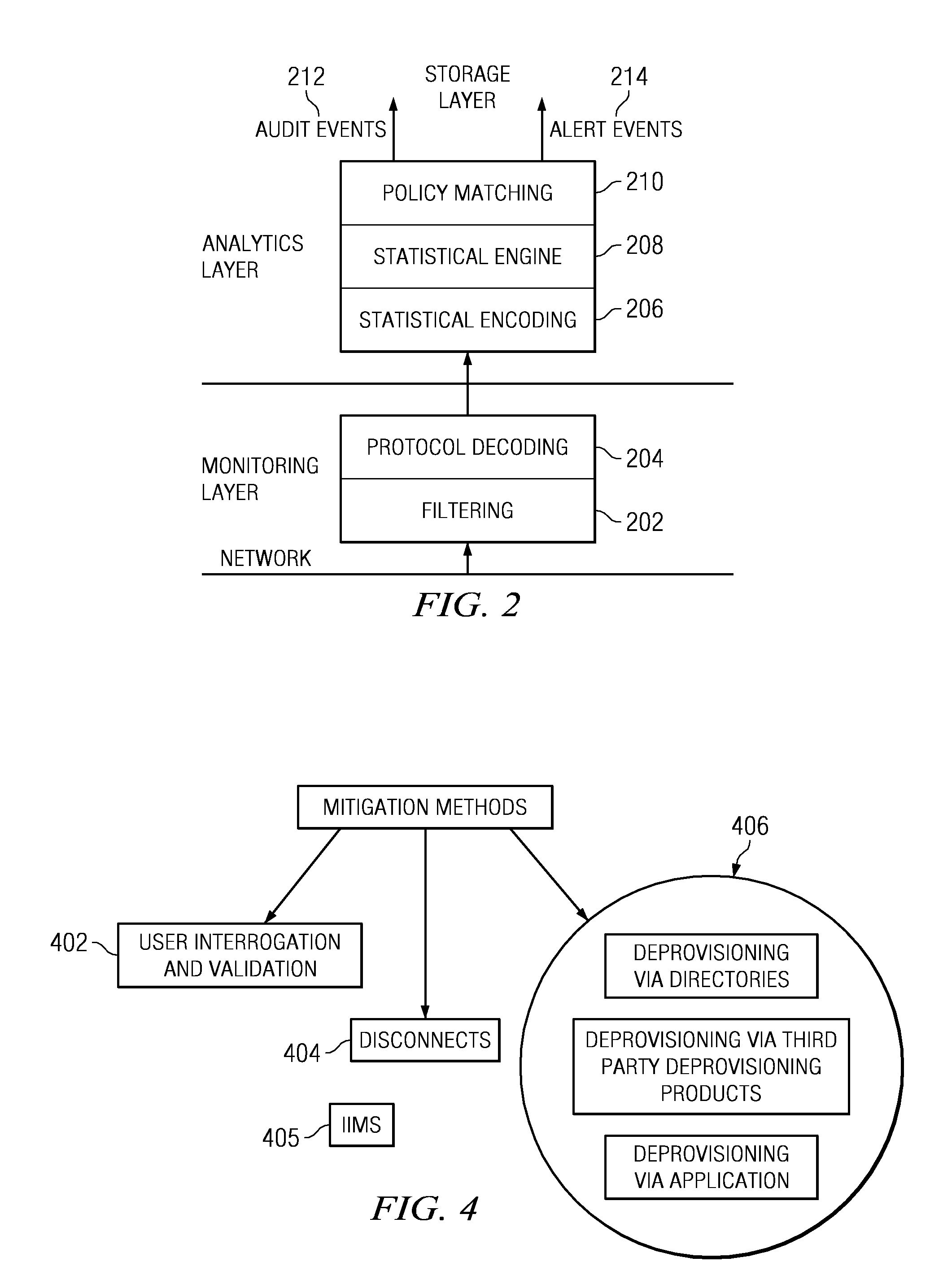
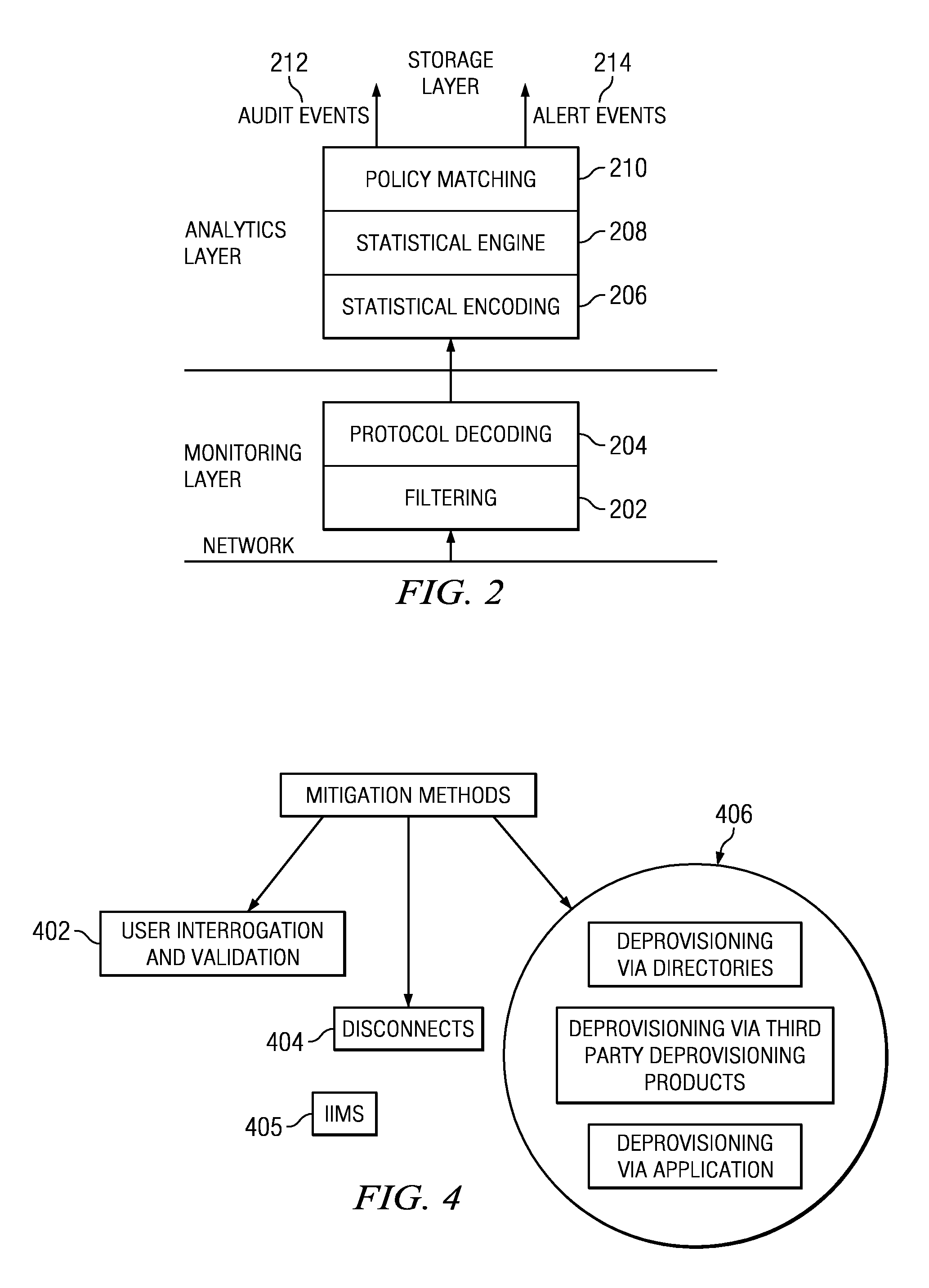
Real-time mitigation of data access insider intrusions
ActiveUS20050071642A1Reduce harmDigital data processing detailsComputer security arrangementsData accessInsider attack
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, network re-routing, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
Method and system for thwarting insider attacks through informational network analysis
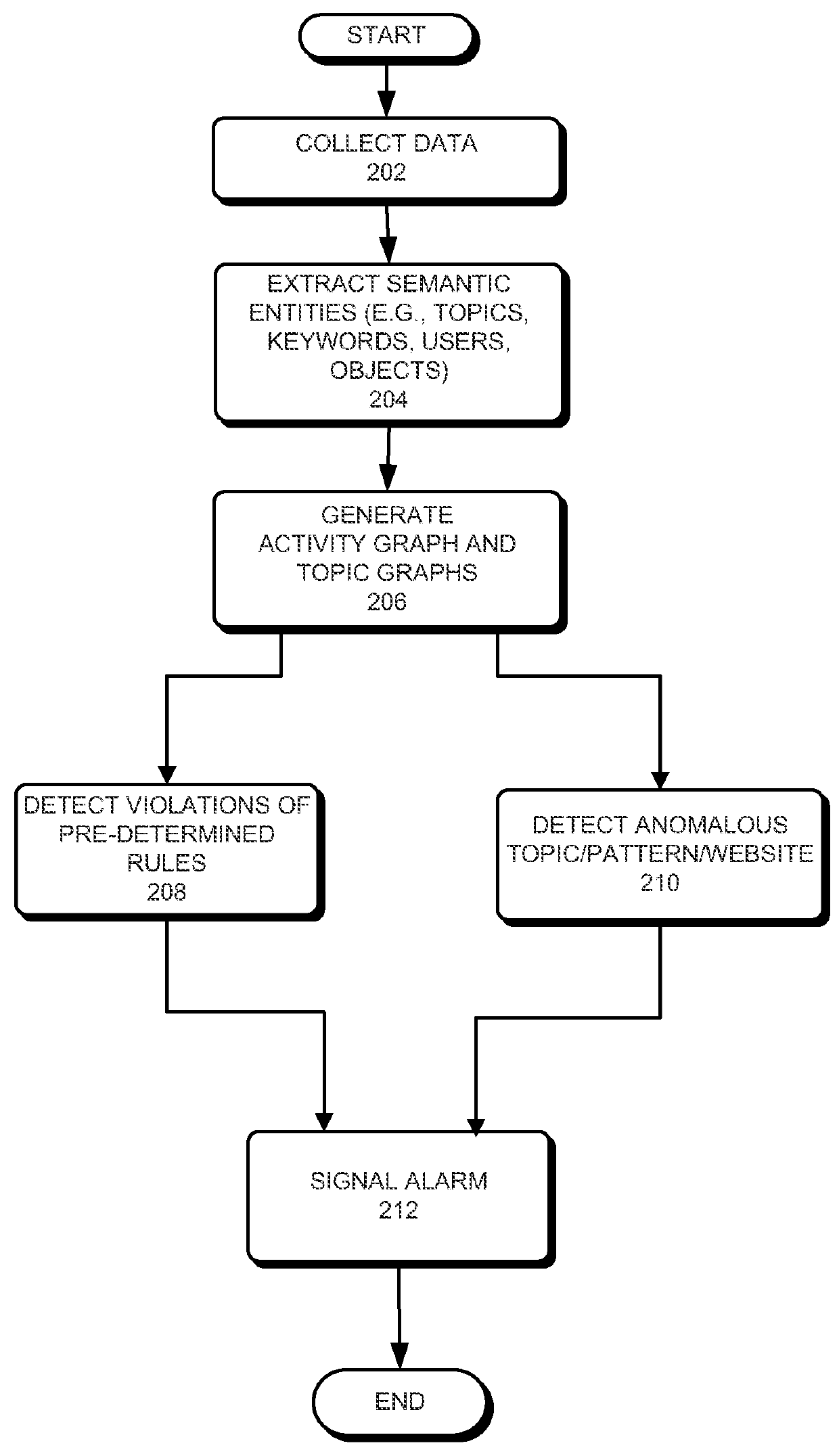
One embodiment of the present invention provides a system for detecting insider attacks in an organization. During operation, the system collects data describing user activities. The system extracts information from the data that includes user information and user communications. The system then generates a topic-specific graph based on the extracted information. The system analyzes a structure of the graph to determine if one or more rules have been violated. The system may determine that a rule associated with the graph has been violated and signal an alarm in response to detecting the rule violation.
Owner:XEROX CORP
Real-time mitigation of data access insider intrusions
ActiveUS7673147B2Reduce harmDigital data processing detailsComputer security arrangementsData accessInsider attack
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, network re-routing, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
Policy specification framework for insider intrusions
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, deprovision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
Anonymous connection method of broadband radio IP network
InactiveCN1564508ASave memoryWeak computing powerData switching networksSecuring communicationEncapsulated dataForeign agent
When mobile user logs on network to access host server, foreign agent FA and host agent HA are as network intermediate agent. Anonymity encapsulation method includes following step: selecting anonymous route in network layer, building anonymous connection, carrying out data encapsulation, as well as combination of polygenous network nested anonymous encapsulation and link encryption at intermediate router. Following measures are taken I the invention: encapsulating data packet transmitted, sharing anonymous channel, anonymous connection of distributed type route and anonymous encapsulation etc. The invention optimizes system capability of resisting interior attack to router and exterior attack to physical chain. Advantages are: favorable anonymity, transparency, expansibility and robustness.
Owner:XIDIAN UNIV
Safety authentication method of cloud storage system
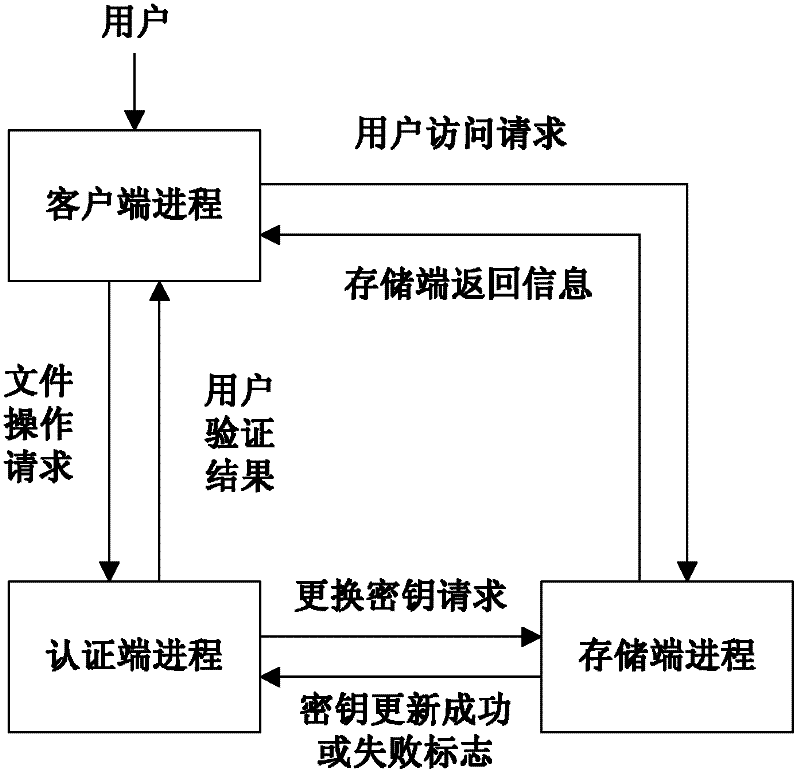
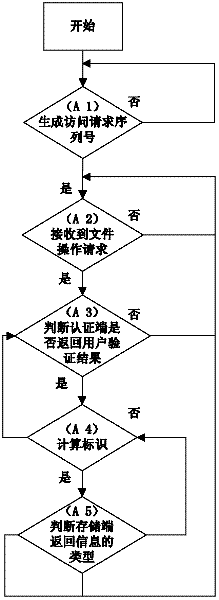
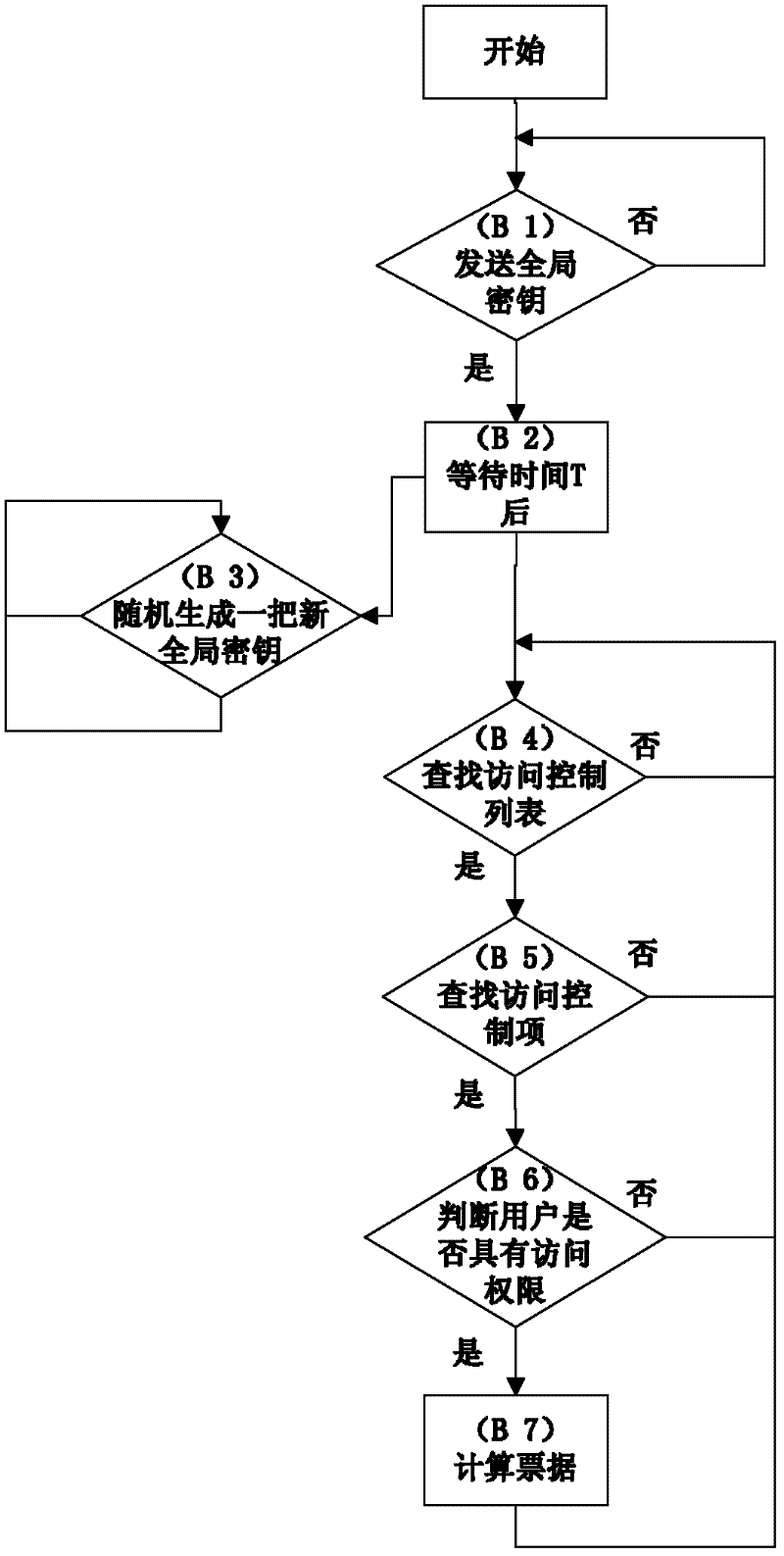
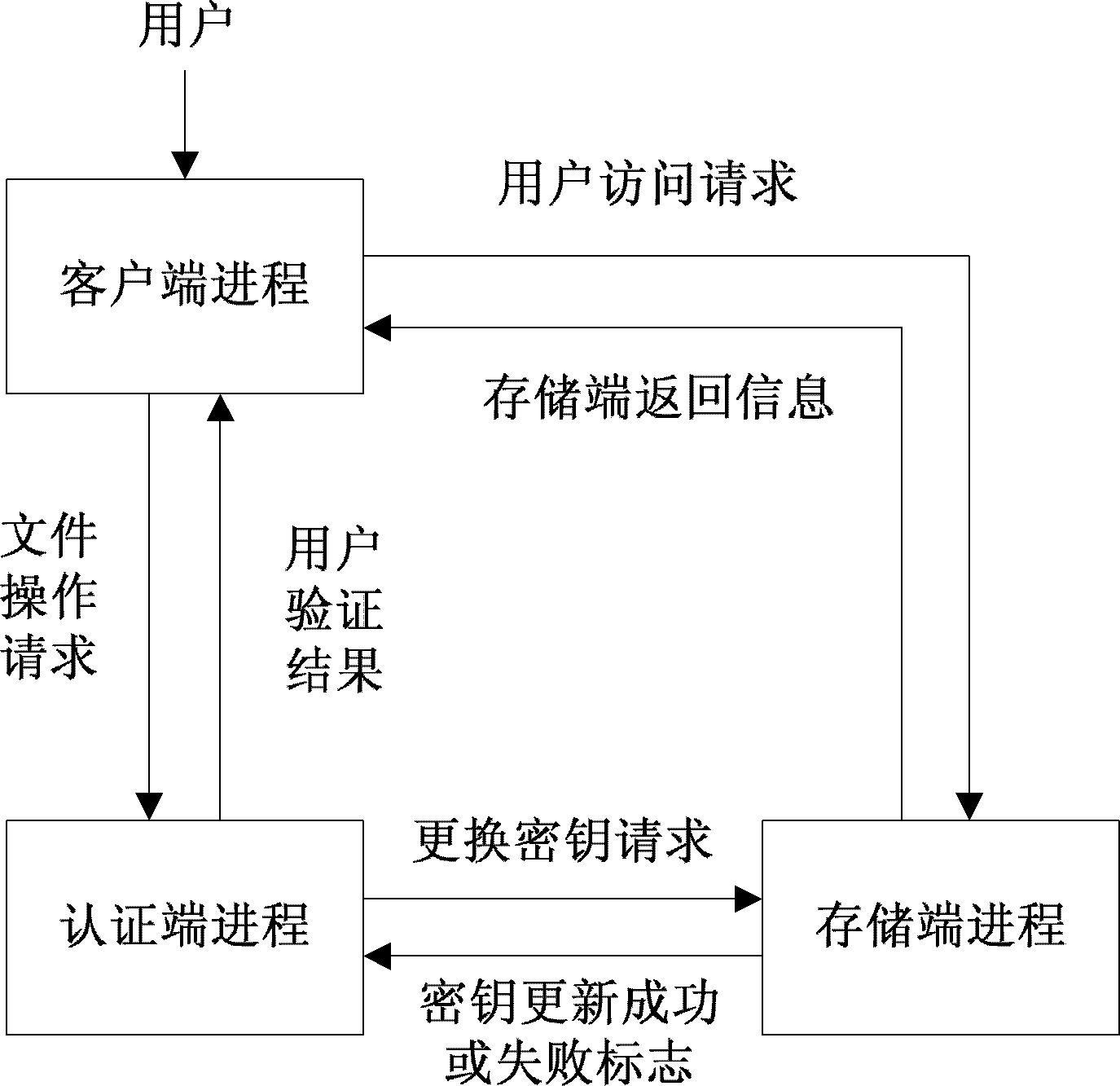
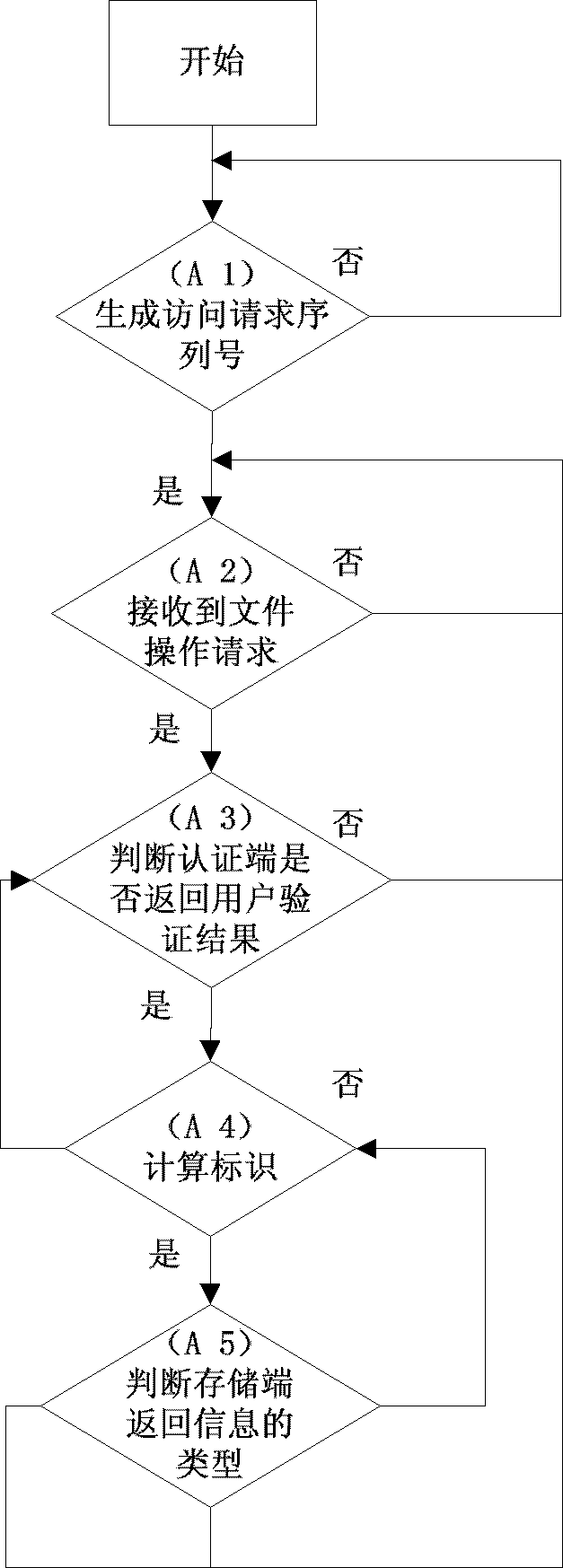
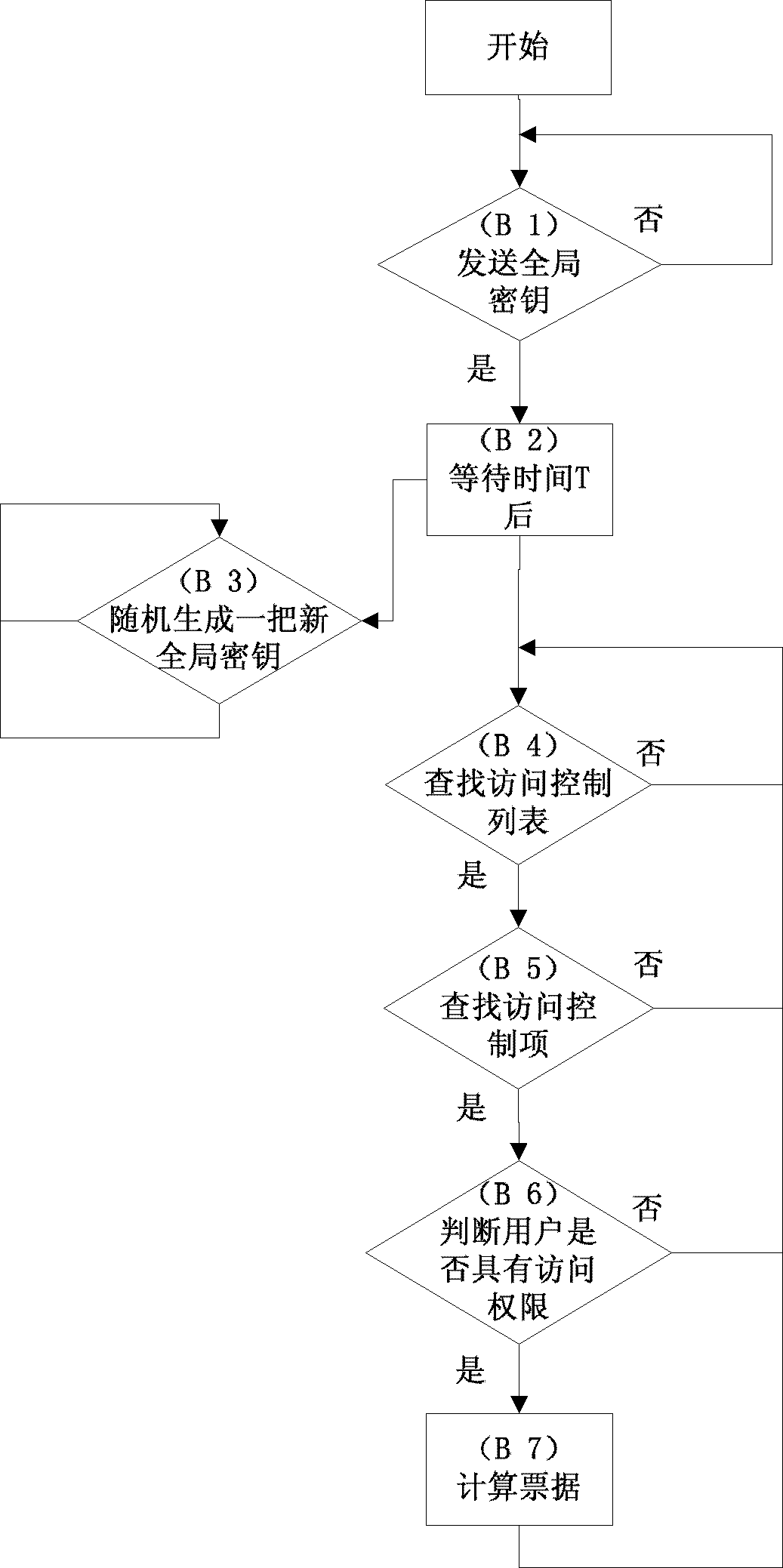
The invention relates to a safety authentication method of a cloud storage system, belonging to the field of storage technology and information security technology of computers. The method solves the problems that the existing safety authentication methods are complex in authentication process and great in authentication consumption, and aims at providing simple, flexible and efficient authentication with high expandability and high safety for service safety of a cloud storage system, so as to prevent invasion of external or internal attackers to the storage system. The method comprises a client process, an authentication end progress and a storage end progress; the client loads the user identifiers of all login users, and the authentication end loads an access control library. The method checks whether the operation authorization of the user is legal by calculating the verifying identifier, the storage end does not need to maintain the access control library any longer, and verification on the access request of the user can be completed with simple calculation, thereby greatly reducing expense of the storage system on access control, and providing flexible, safe, reliable and efficient file access for users having operation authorization in the large-scale cloud storage system.
Owner:HUAZHONG UNIV OF SCI & TECH
Enterprise information asset protection through insider attack specification, monitoring and mitigation
ActiveUS8880893B2Reduce harmMemory loss protectionError detection/correctionData accessInsider attack
The present invention provides a policy specification framework to enable an enterprise to specify a given insider attack using a holistic view of a given data access, as well as the means to specify and implement one or more intrusion mitigation methods in response to the detection of such an attack. The policy specification provides for the use of “anomaly” and “signature” attributes that capture sophisticated behavioral characteristics of illegitimate data access. When the attack occurs, a previously-defined administrator (or system-defined) mitigation response (e.g., verification, disconnect, de-provision, or the like) is then implemented.
Owner:SOFTWARE LABS CAMPUS UNLIMITED CO
Method and system for thwarting insider attacks through informational network analysis
ActiveUS9336388B2Error detection/correctionUnauthorized memory use protectionGraphicsSystems analysis
One embodiment of the present invention provides a system for detecting insider attacks in an organization. During operation, the system collects data describing user activities. The system extracts information from the data that includes user information and user communications. The system then generates a topic-specific graph based on the extracted information. The system analyzes a structure of the graph to determine if one or more rules have been violated. The system may determine that a rule associated with the graph has been violated and signal an alarm in response to detecting the rule violation.
Owner:XEROX CORP
Method and System for Secure Data Storage Exchange, Processing, and Access
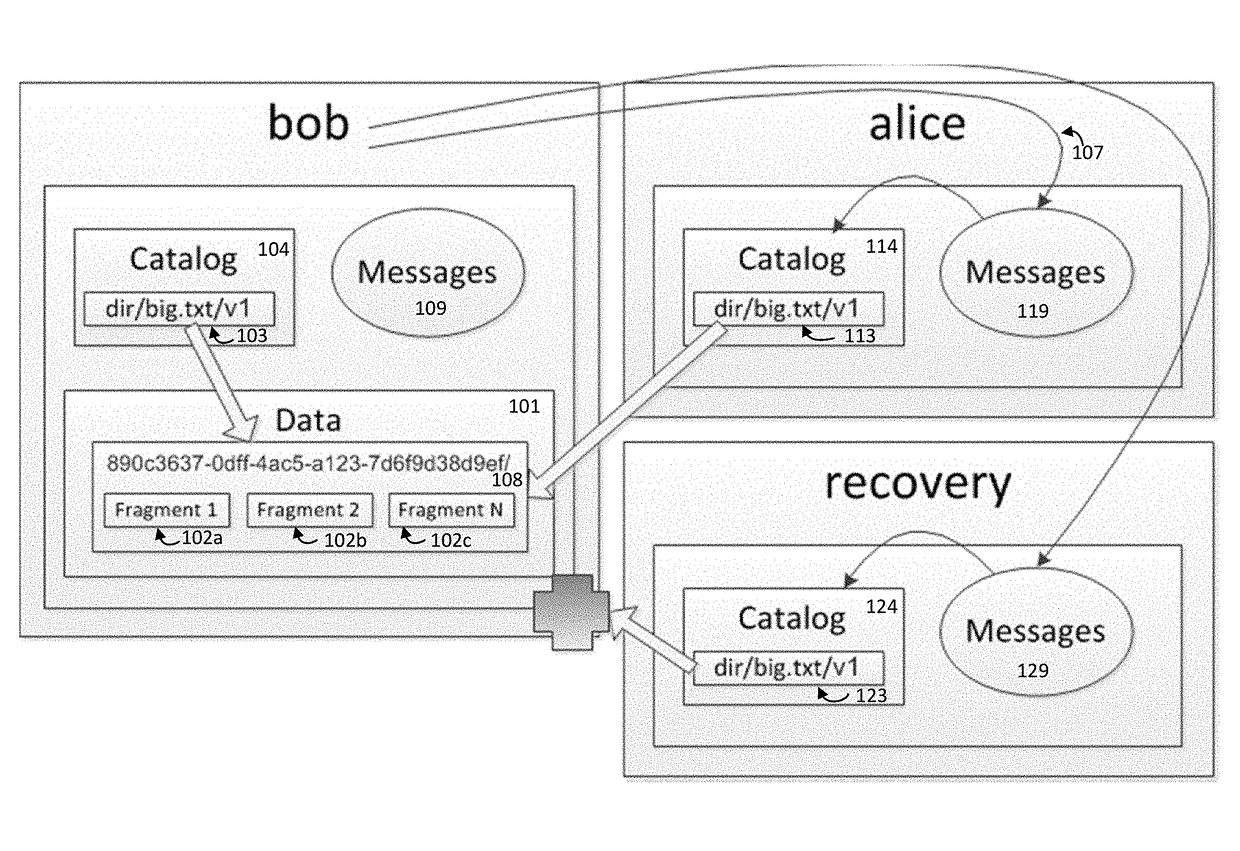
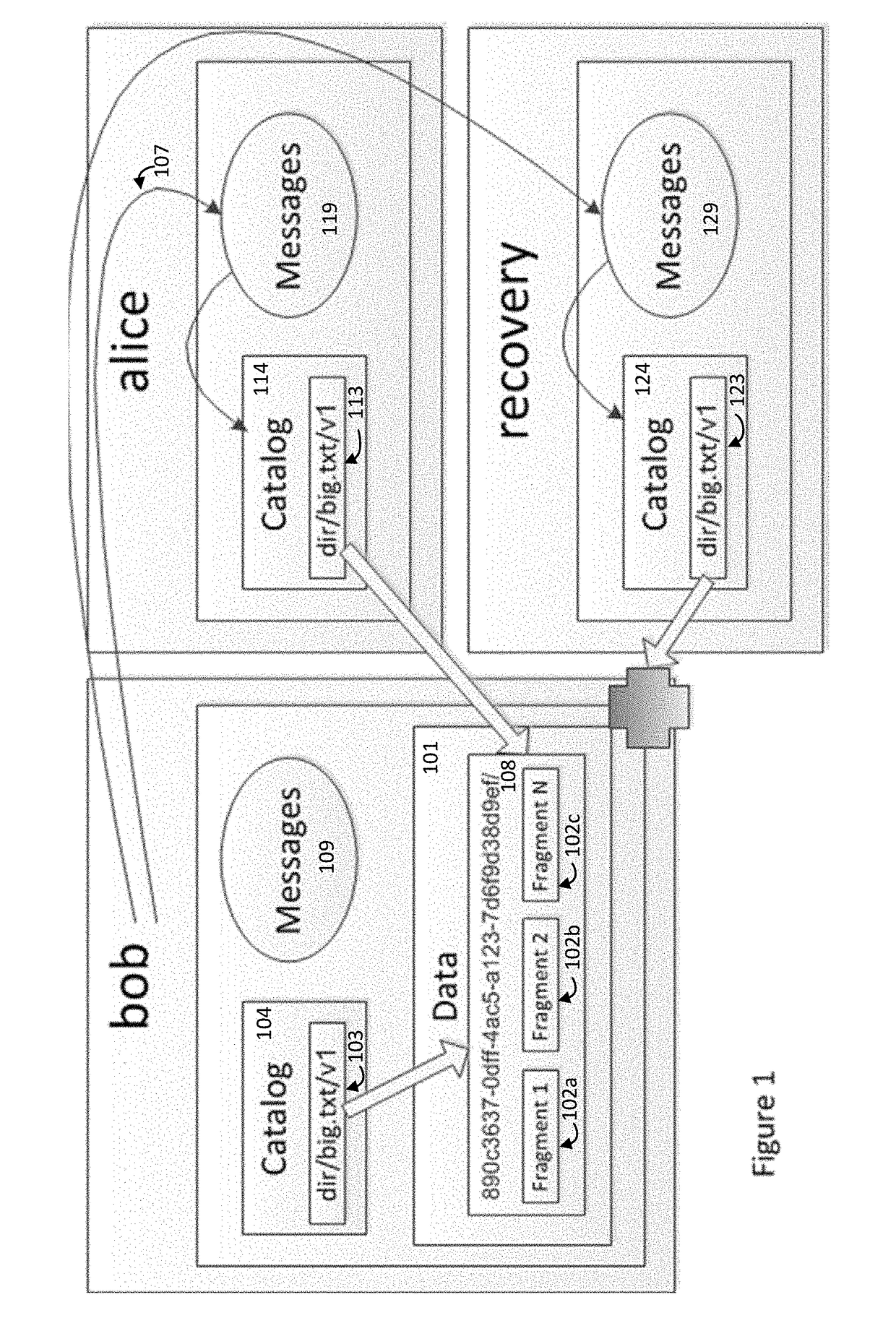
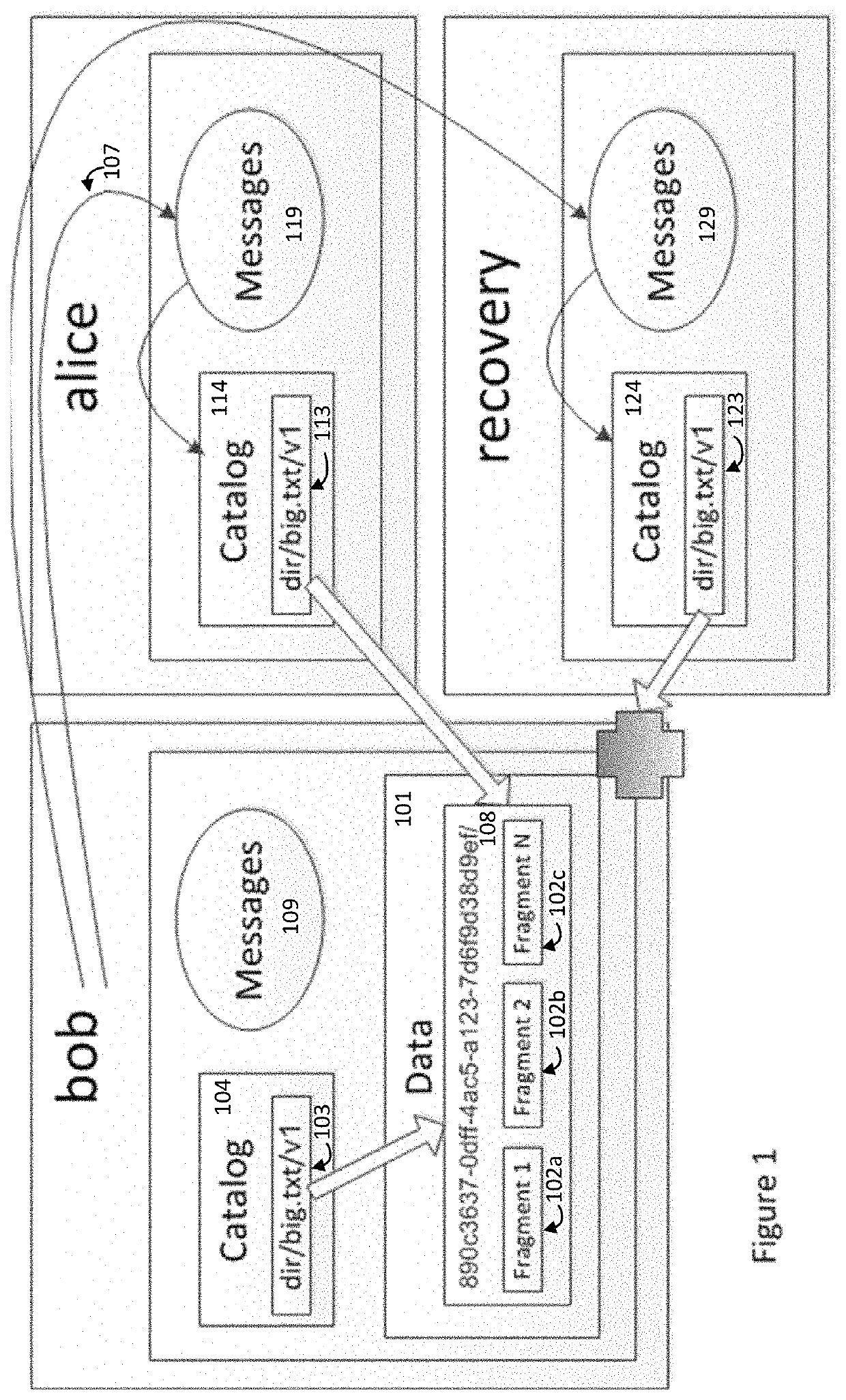
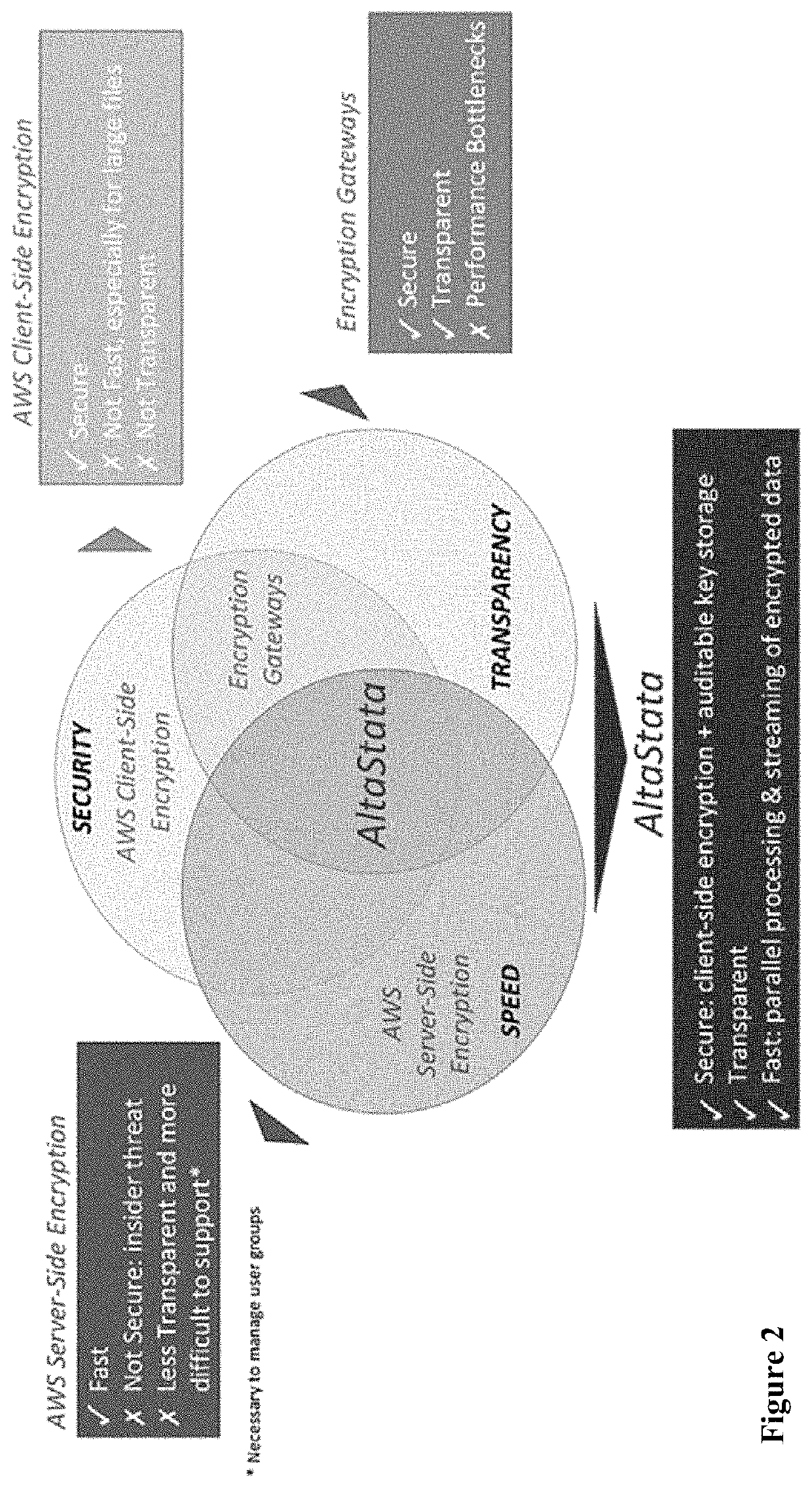
A multi-user encrypted secure data storage schema is described that is particularly suited for cloud based storage scenarios. This schema protects against an insider attacks be limiting administrator access to encrypted user data. The schema involves encrypting both the data set and user catalogs, where the catalogs contain data locations and data keys in metadata objects. The metadata objects may be share between users to provide others access to the data.
Owner:VILVOVSKY SERGE
Mechanism for identifying malicious content, DoS attacks, and illegal IPTV services
InactiveUS8769682B2Memory loss protectionError detection/correctionInsider attackProtocol for Carrying Authentication for Network Access
Mechanism for identifying malicious content, DoS attacks, and illegal IPTV services. By monitoring the characteristics of various control messages being transmitted within a network that services Internet protocol television (IPTV) content to identify suspicious behavior (e.g., such as that associated with malicious content, denial of service (DoS) attacks, IPTV service stealing, etc.). In addition to monitoring control messages within such a network, deep packet inspection (DPI) may be performed for individual packets within an IPTV stream to identify malicious content therein (e.g., worms, viruses, etc. actually within the IPTV stream itself). By monitoring control messages and / or actual IPTV content within a network (e.g., vs. at the perimeter of a network only), protection against both outside and inside attacks can be effectuated. This network level basis of operation effectively guards against promulgation of malicious content to other devices within the network.
Owner:RPX CORP
A routing method based on reputation evaluation of a wireless sensor network node
ActiveCN109874160AEfficient identificationIncrease success rateData switching networksWireless communicationWireless mesh networkMultipath routing protocol
The invention provides a routing method based on reputation evaluation of a wireless sensor network node. By studying a wireless sensor network, and based on an AOMDV multipath routing protocol, The method comprises the steps of establishing a routing vector model, an energy assessment model and a communication trust model respectively by combining a bayes algorithm, analyzing the influence of routing vector factors, communication factors and energy factors in the wireless sensor nodes on the reputation of the wireless sensor nodes through the models, and objectively selecting safe and efficient wireless sensor routing nodes, so that the wireless sensor network can identify attack nodes in the multi-factor network more effectively; the malicious node attacks are prevented, the success rateof data transmission is improved, the internal attack security problem which cannot be solved by a traditional password security authentication security mechanism is solved, and the internal attack security of the wireless sensor network in an open environment is more hierarchical.
Owner:ANHUI UNIVERSITY OF ARCHITECTURE
Method and system for secure data storage exchange, processing, and access
ActiveUS10693660B2Key distribution for secure communicationMultiple keys/algorithms usageData setInsider attack
A multi-user encrypted secure data storage schema is described that is particularly suited for cloud based storage scenarios. This schema protects against an insider attacks be limiting administrator access to encrypted user data. The schema involves encrypting both the data set and user catalogs, where the catalogs contain data locations and data keys in metadata objects. The metadata objects may be share between users to provide others access to the data.
Owner:VILVOVSKY SERGE
SDN edge computing network system based on blockchain encryption, encryption method and medium
InactiveCN111371588AEnsure safetyAvoid lossData switching networksSecuring communicationAttackEdge computing
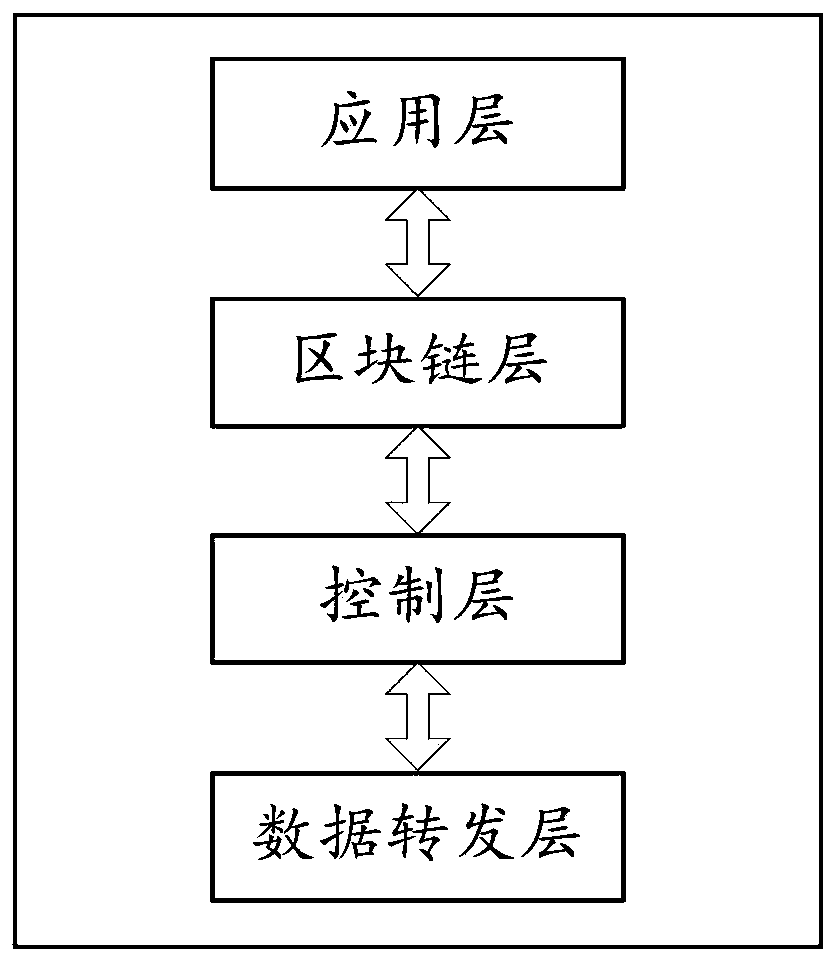
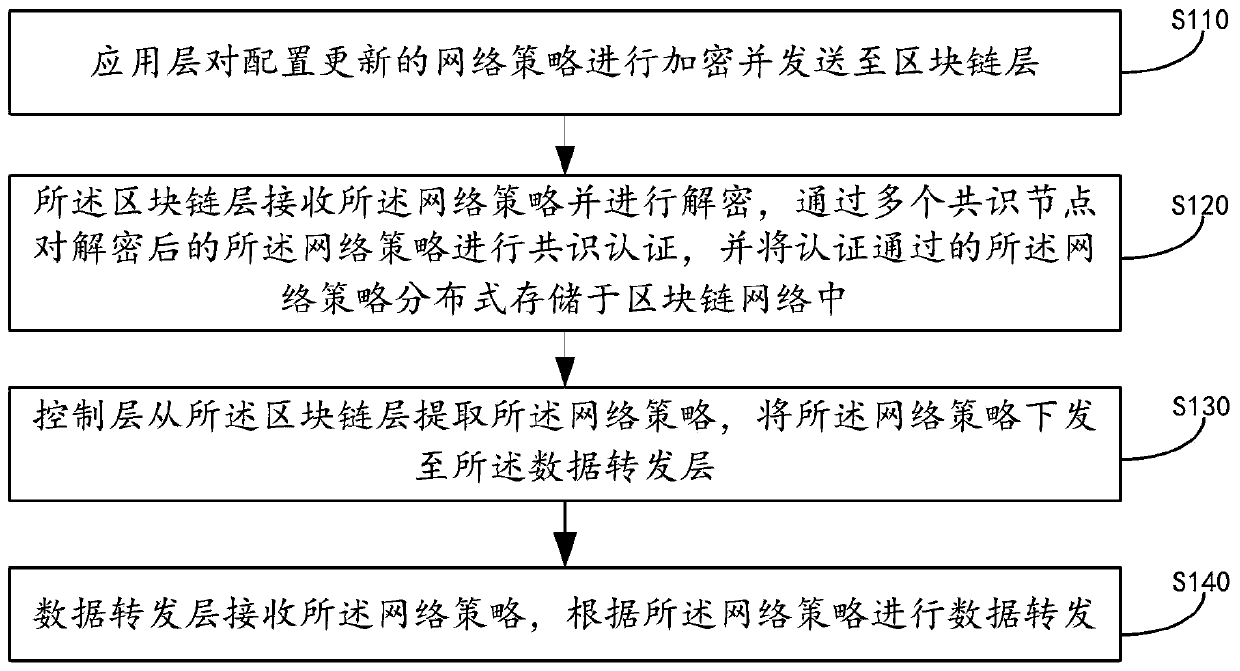
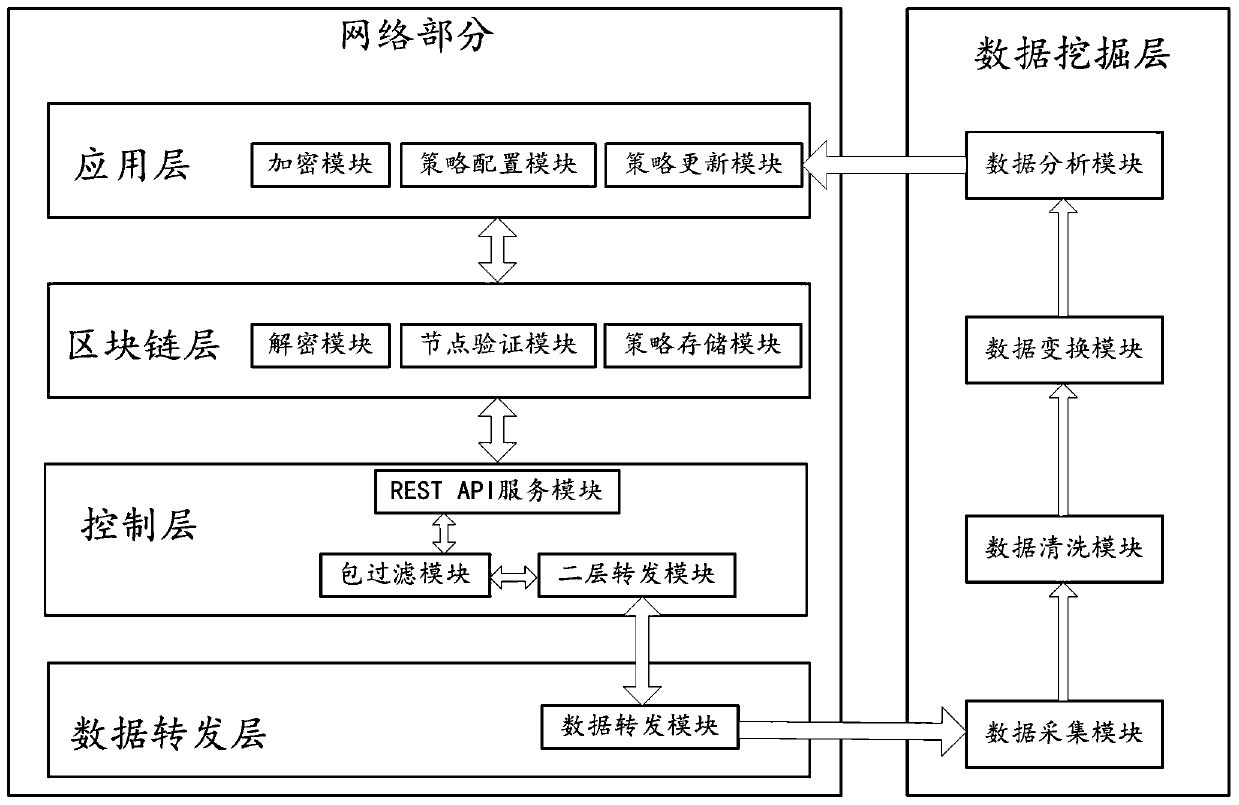
The embodiment of the invention discloses an SDN edge computing network system based on blockchain encryption, an encryption method and a medium. The embodiment of the invention provides a technical scheme. Encrypting the configured and updated network strategy through the application layer and sending the encrypted and updated network strategy to the blockchain layer; the block chain layer receives the network strategy and decrypts the network strategy; and performing consensus authentication on the decrypted network strategy through a plurality of consensus nodes, storing the authenticated network strategy in the blockchain network in a distributed manner, extracting the network strategy from the blockchain layer by the control layer, and issuing the network strategy to the data forwarding layer, so that the data forwarding layer performs data forwarding according to the network strategy. By adopting the technical means, the security of network strategy transmission and issuing can be guaranteed, and data loss and network internal attacks are avoided. And furthermore, by storing administrator account address information, the identity of a network strategy configurator is convenient to determine, so that a basis is provided for tracing the identity of an attacker in the network.
Owner:广州广大通电子科技有限公司
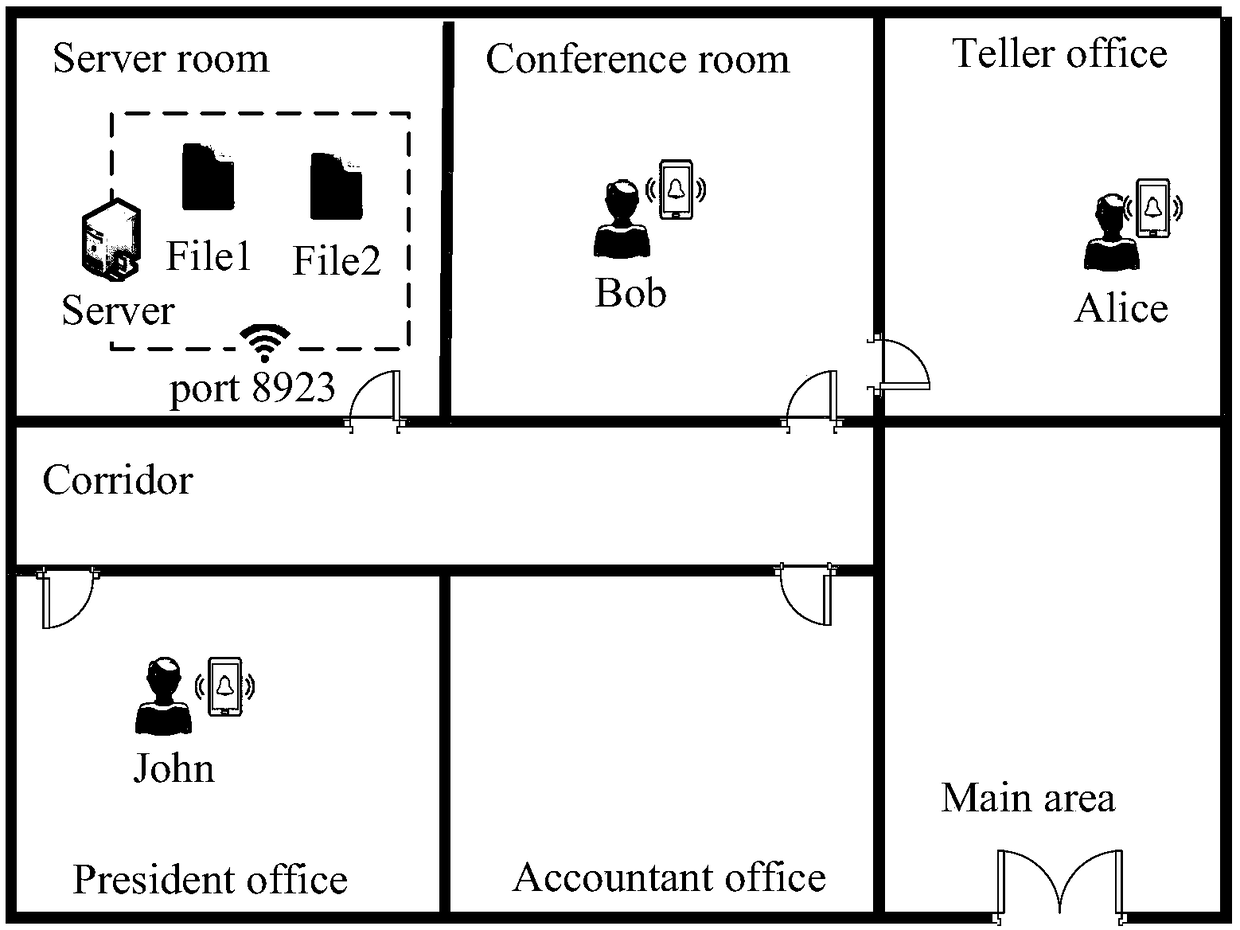
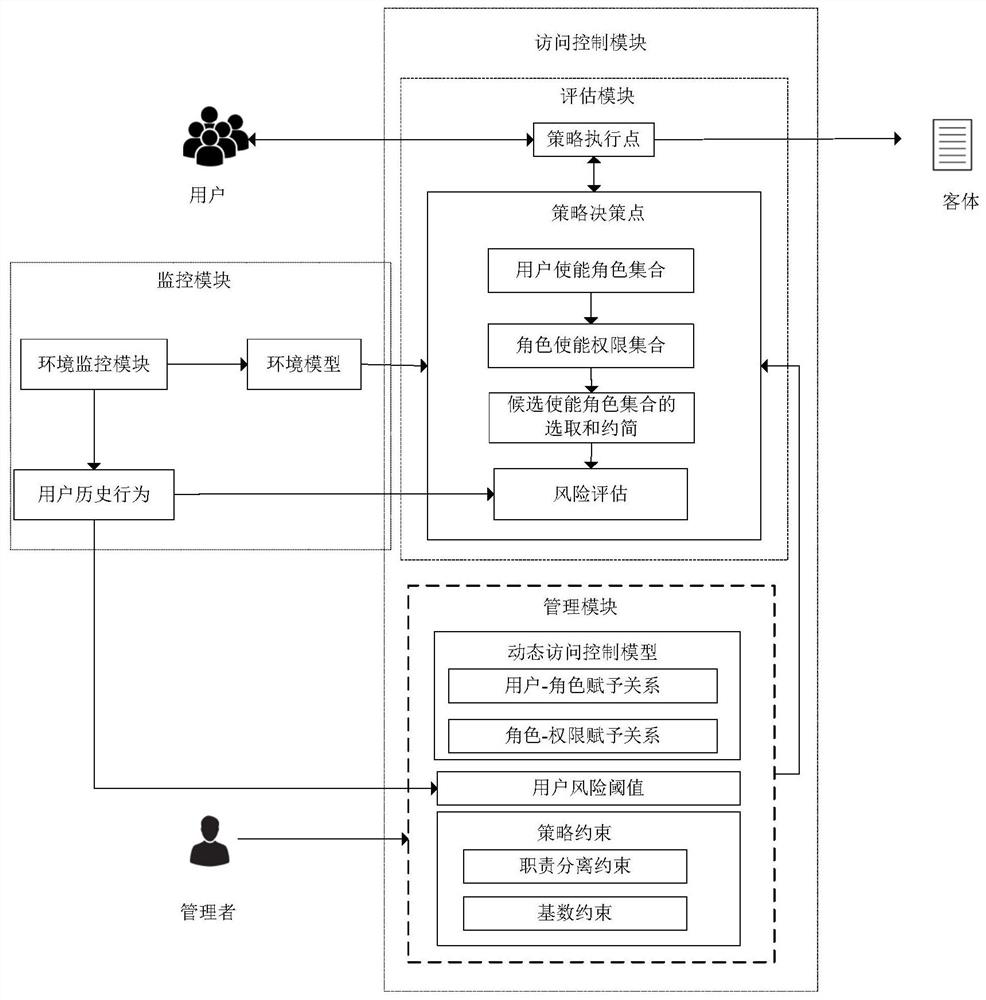
Dynamic access control framework facing internal attack
ActiveCN109495474ADynamic Access PreventionInsider attack preventionTransmissionRisk profilingUser Privilege
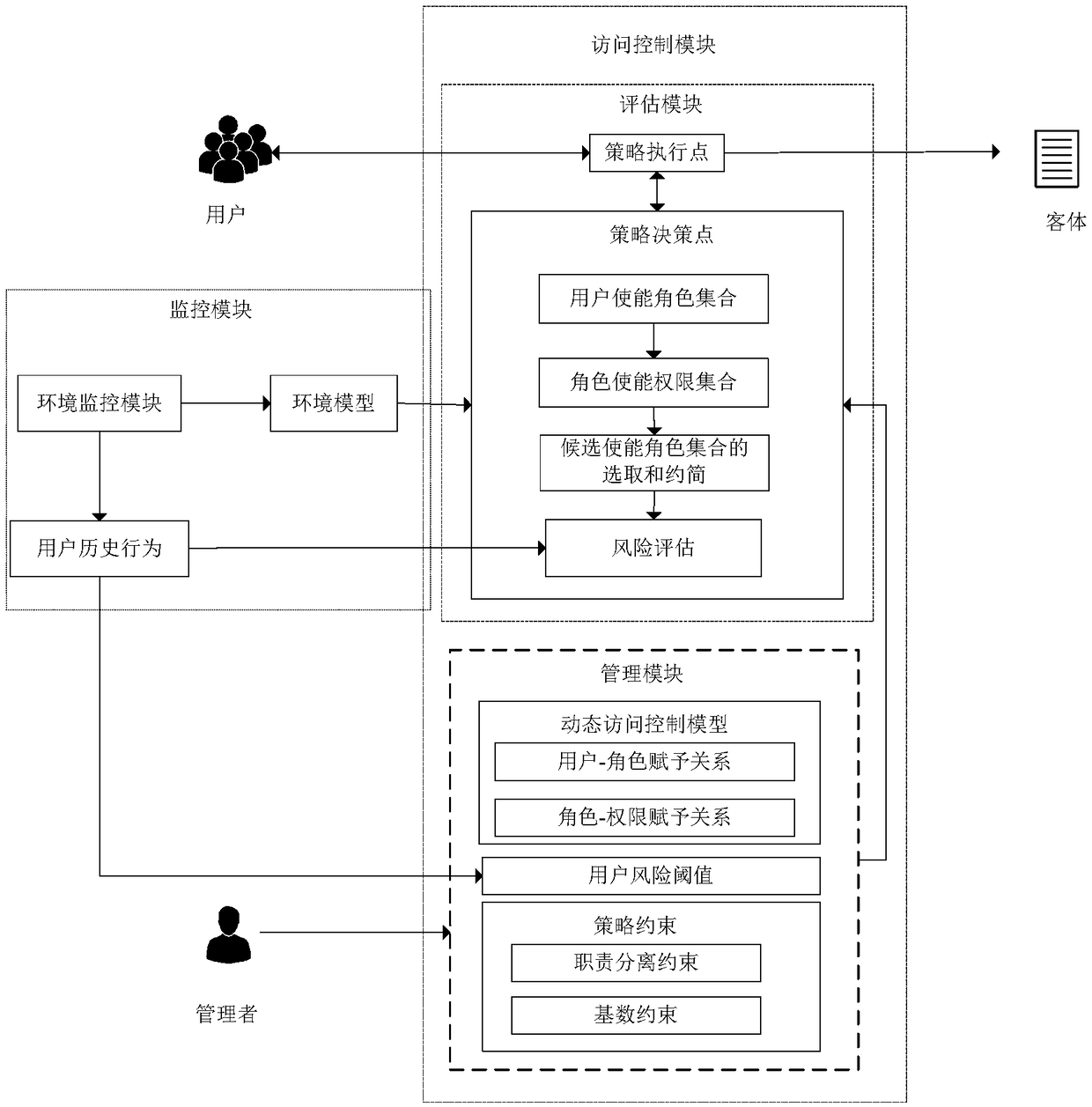
The invention discloses a dynamic access control framework facing internal attacks, and belongs to the technical field of information security access control. The dynamic access control framework comprises a submission of an access request, a calculation of user enablement roles, a calculation of enablement roles permissions, a selection of the enablement roles, a reduction of candidate enablementroles, and a calculation of risk values. According to the dynamic access control framework facing the internal attacks, the satisfiability of environmental constraints in an access control policy isevaluated by using an environment model, thereby achieving dynamic adjustment of user authority, and preventing accesses of illegal users; permission ranges of legal users are constrained according tostrategy constraints and risk analysis, thereby avoiding internal attacks of malicious users; and a triple control of access requests is achieved by analyzing environmental information, the strategyconstraints, and access risks, thereby preventing illegal and malicious access behaviors can in time, more effectively protecting network resources, and guaranteeing safe and efficient operation of the system.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
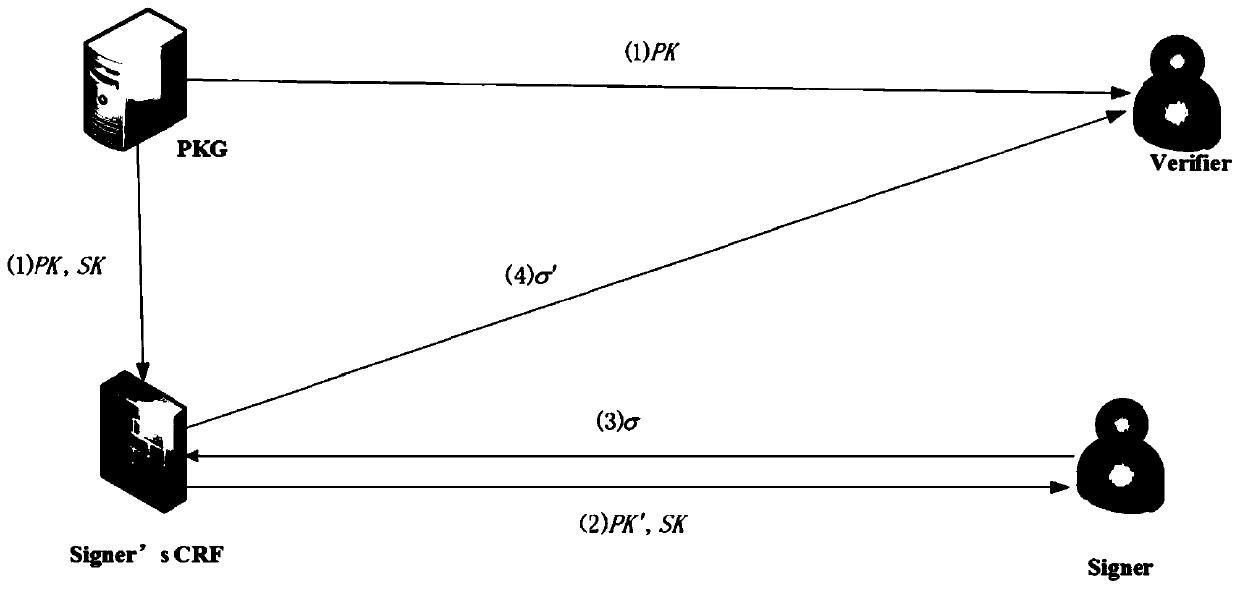
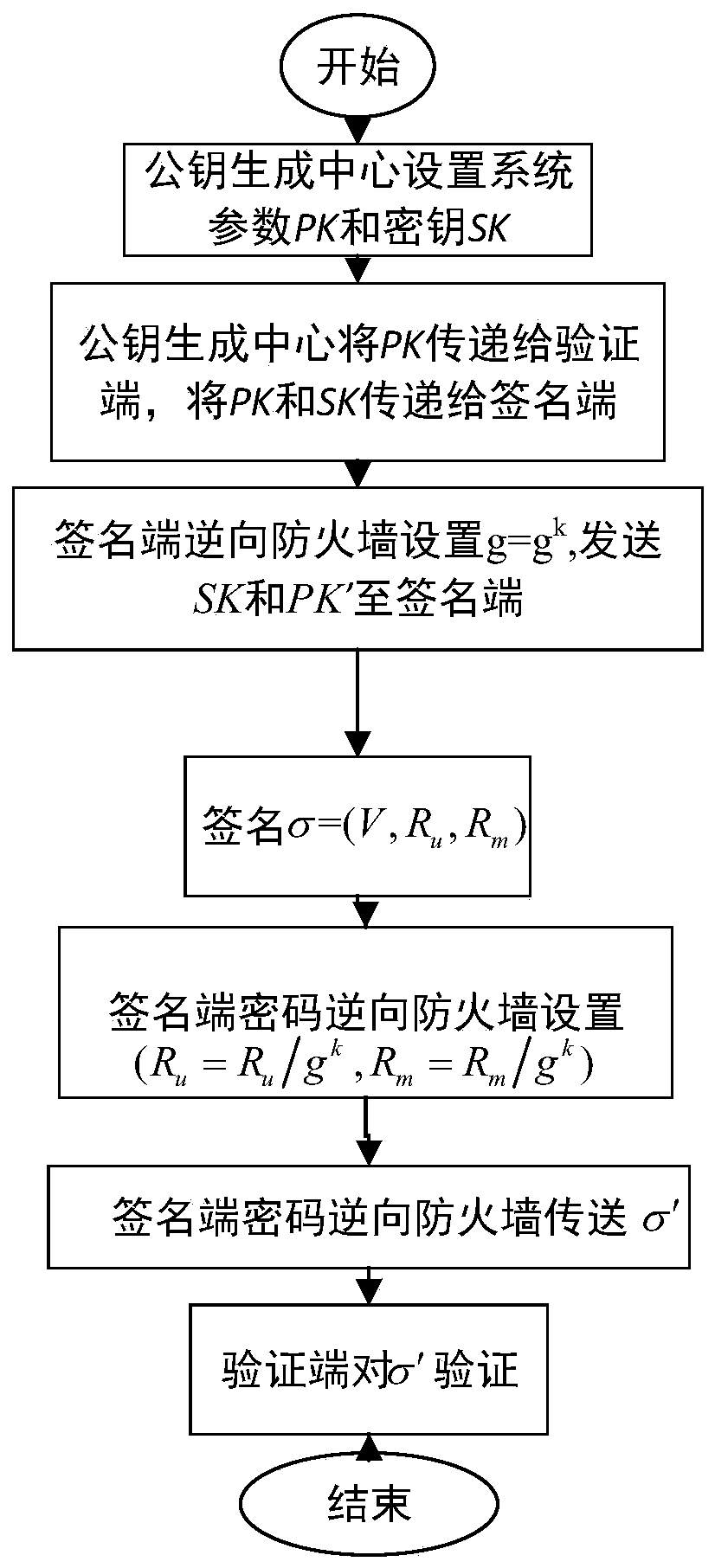
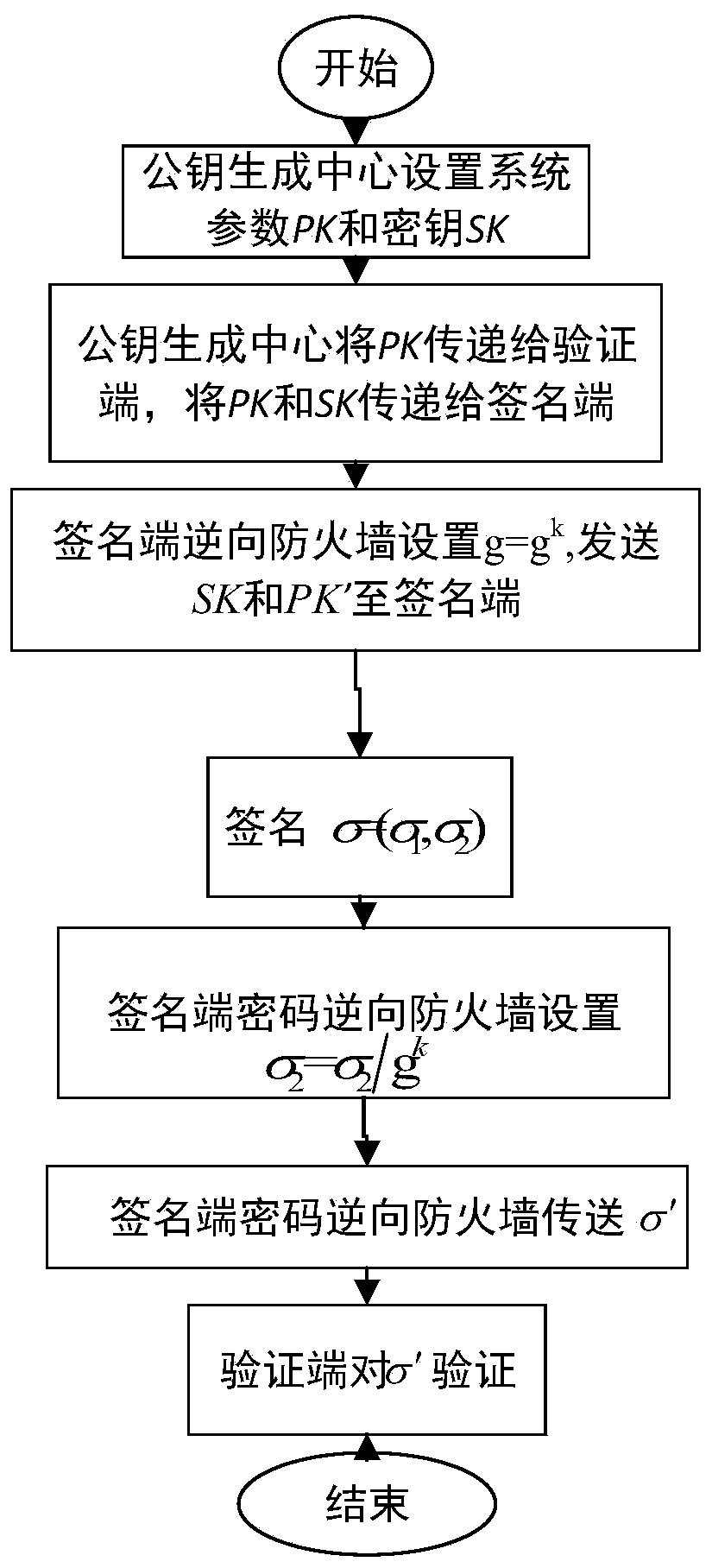
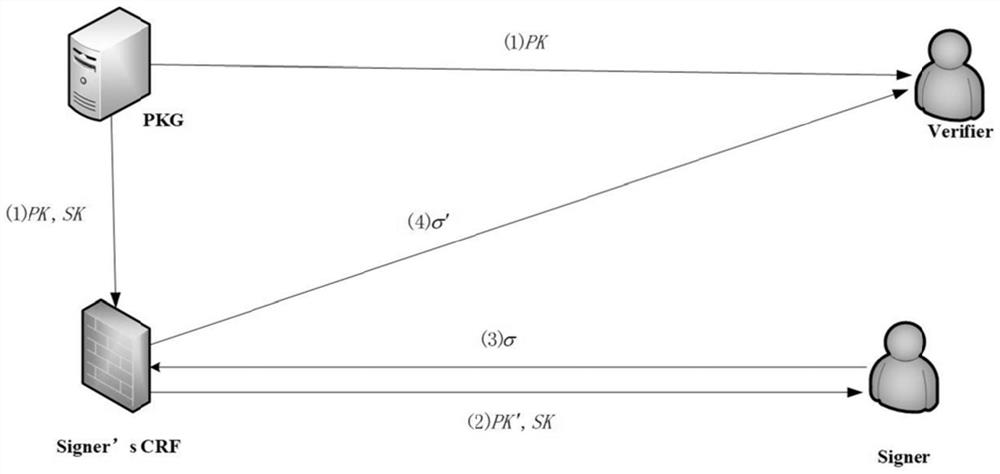
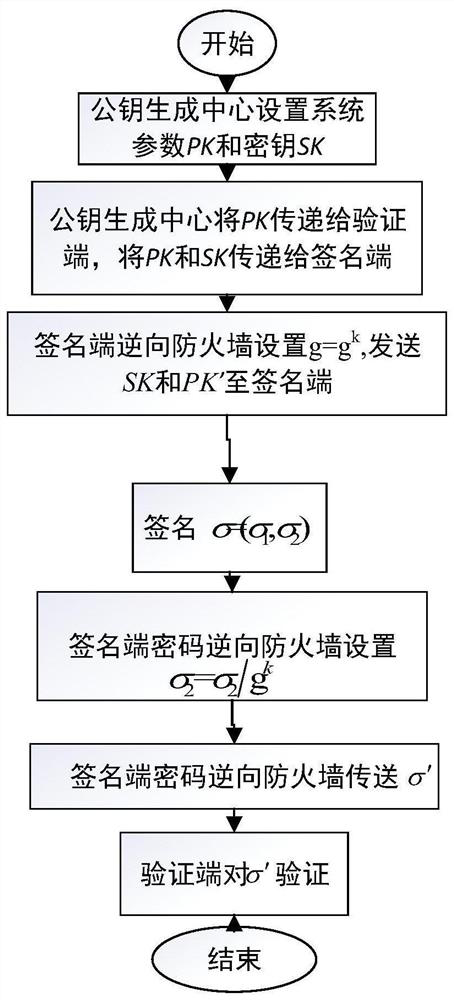
Identity-based digital signature password reverse firewall method
ActiveCN111245615AImprove securityPrivacy protectionKey distribution for secure communicationUser identity/authority verificationInternet privacyDigital signature
The invention discloses an identity-based digital signature password reverse firewall method, and belongs to the technical field of information security. The method comprises the following steps: firstly, a transparent and credible password reverse firewall is set at a signature end, and related system parameters are set; the password reverse firewall re-randomizes part of the received parametersand then transmits the re-randomized parameters and other non-re-randomized parameters to the signature end; the signature end carries out signature to obtain a signature result sigma = (V, Ru, Rm), the rear two parts of the signature result are reset through the password reverse firewall of the signature end, and then the partially reset signature result is transmitted to a verification end; andthe verification end verifies the legality of the received signature result, if the signature result passes the verification, 'acceptance' is output, and otherwise, 'rejection' is output. According tothe identity-based digital signature password reverse firewall method, transparency and credibility are realized, leakage is prevented, the safety of a user is improved, and the attack behavior of aninternal attacker is particularly protected.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
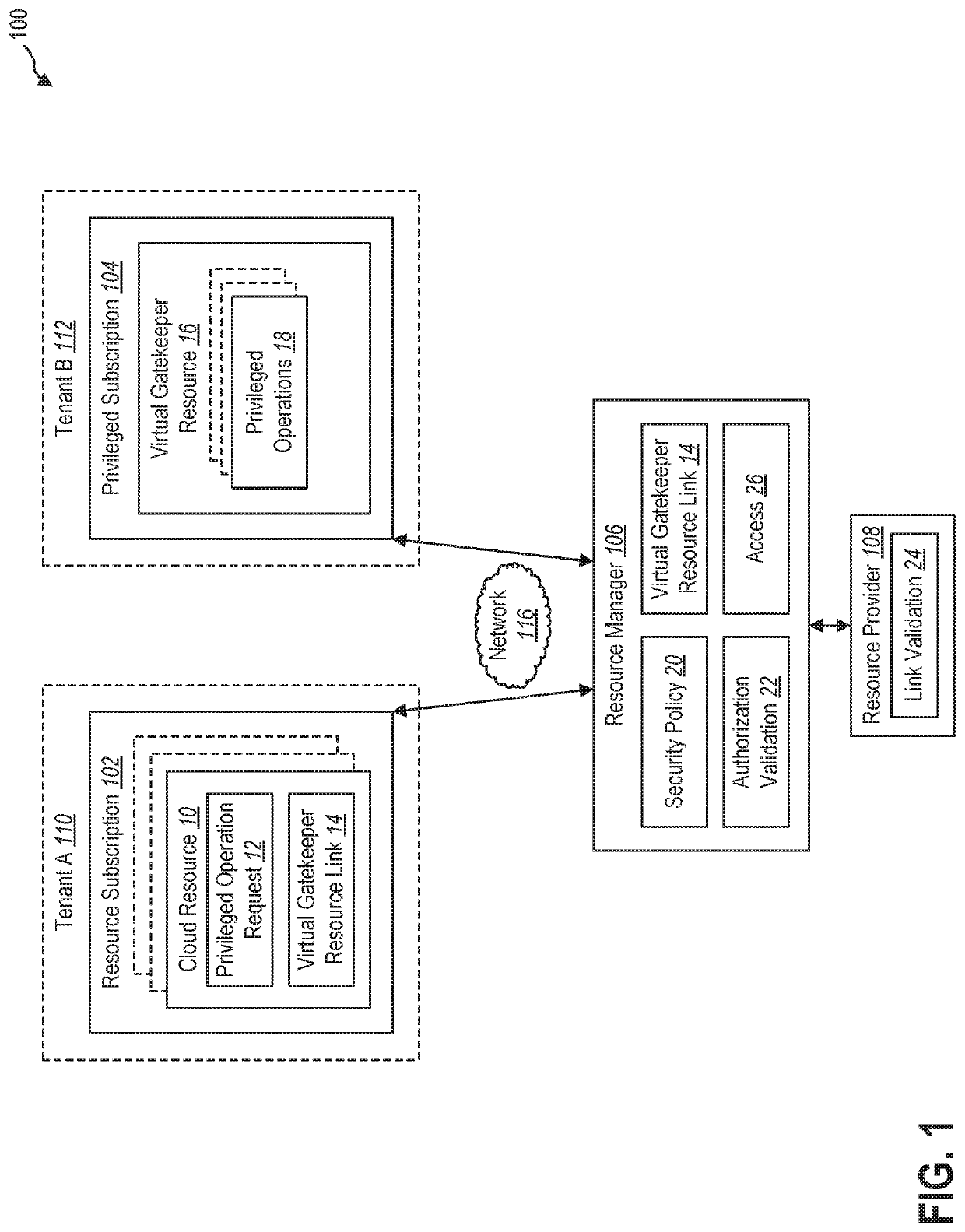
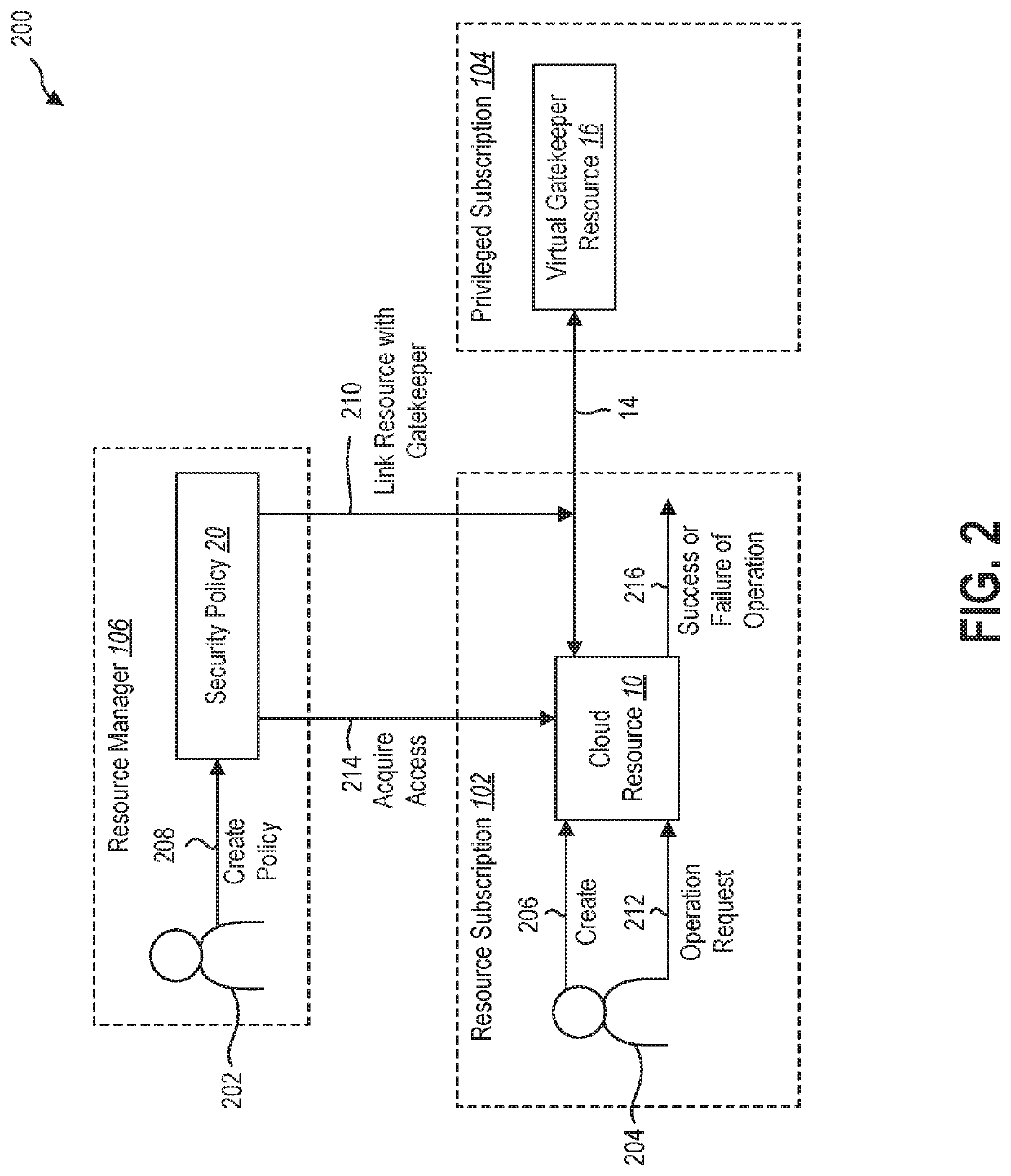
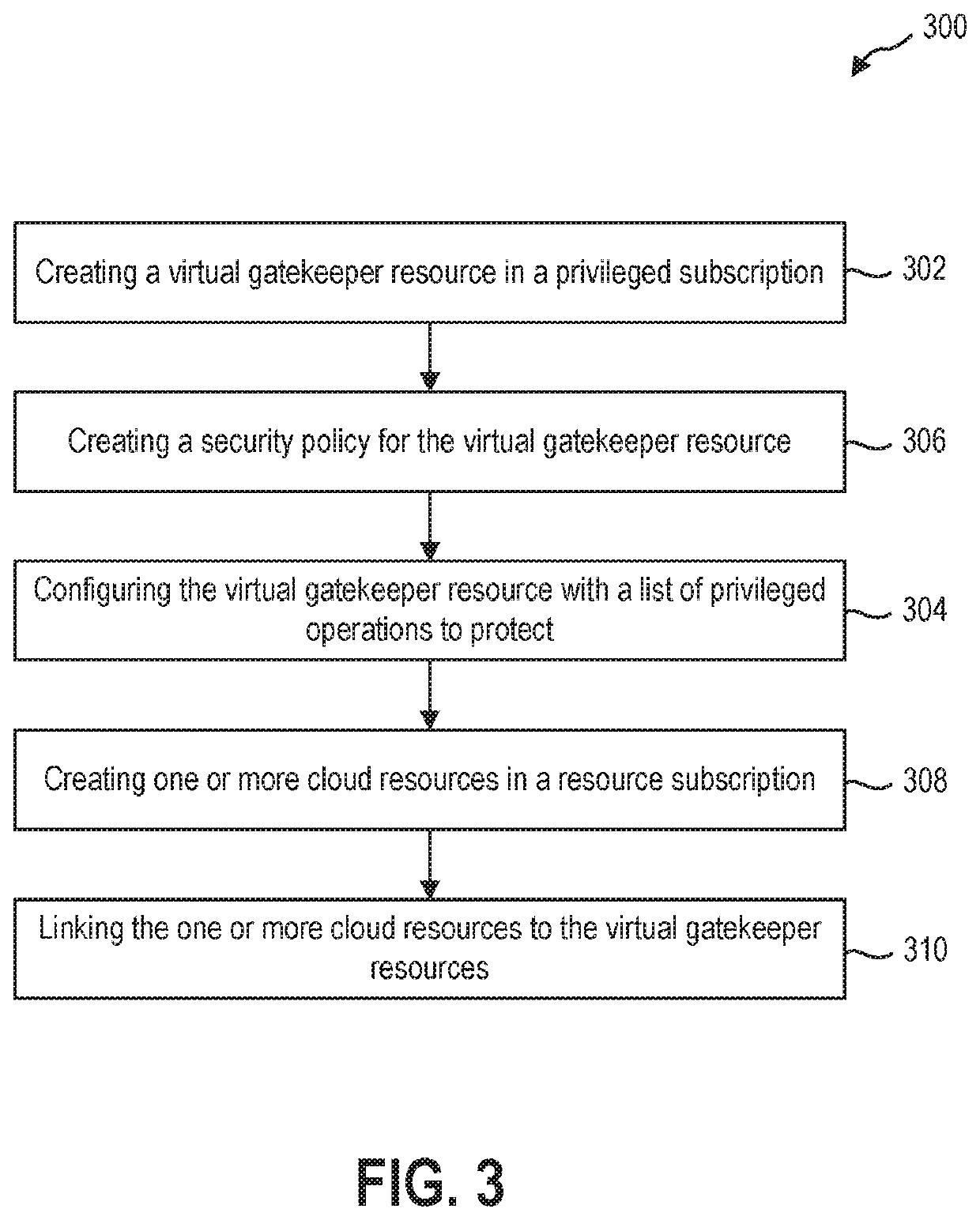
Gatekeeper resource to protect cloud resources against rogue insider attacks
The present disclosure relates to methods and systems for protecting cloud resources. The methods and systems may use a virtual gatekeeper resource to enforce secure access controls to cloud resources for a list of privileged operations. The cloud resources and the virtual gatekeeper resource may be in different security domains within a cloud computing system and the cloud resources may be linked to the virtual gatekeeper resource. A request may be sent to perform a privileged operation on the cloud resource. Access may be provided to the virtual gatekeeper resource in response to approval of the request and the access to the virtual gatekeeper resource may be used to perform the privileged operation on the cloud resource.
Owner:MICROSOFT TECH LICENSING LLC
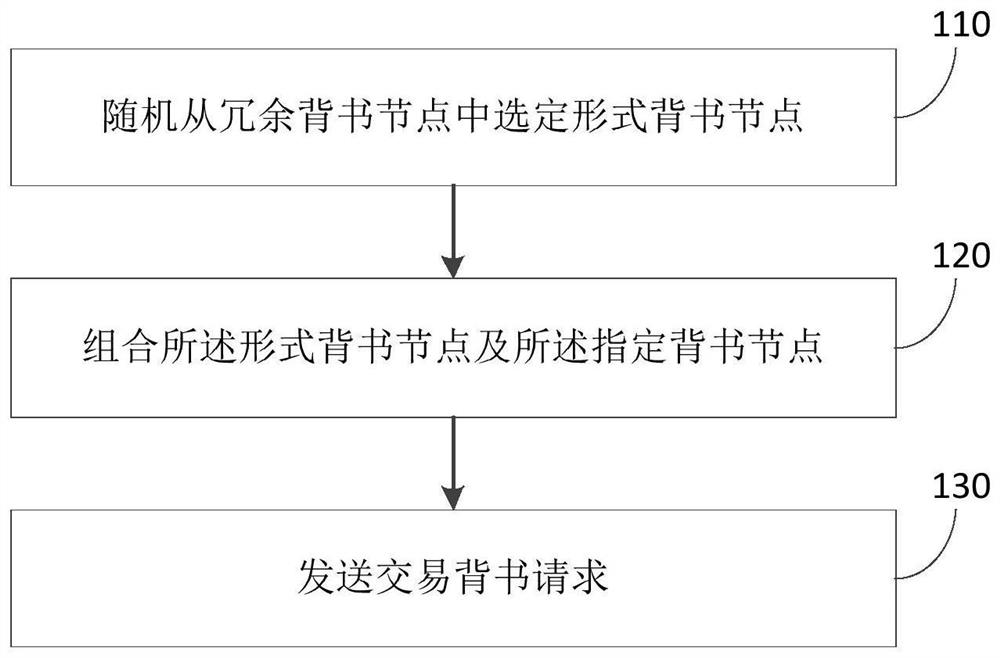
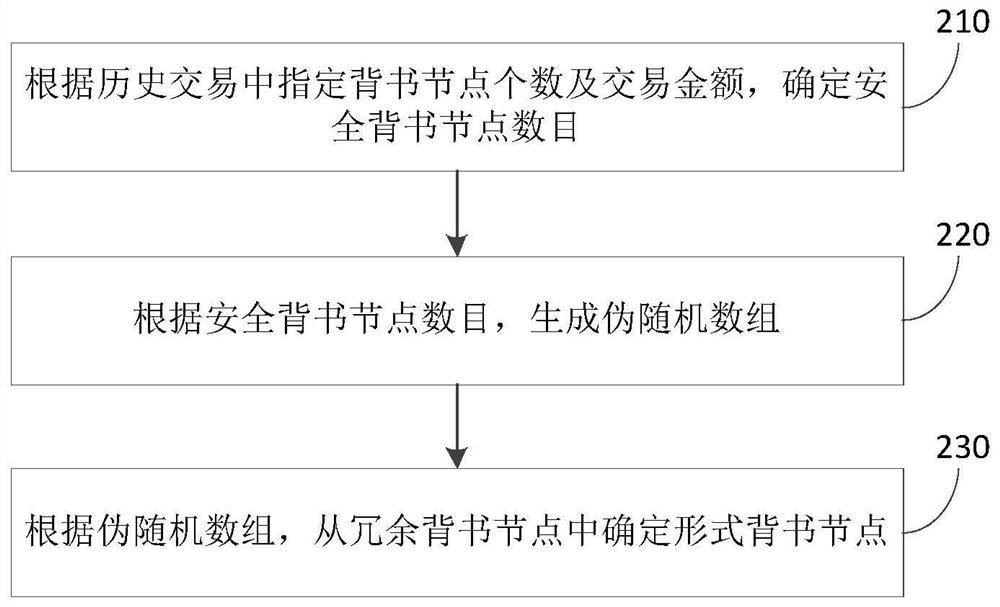
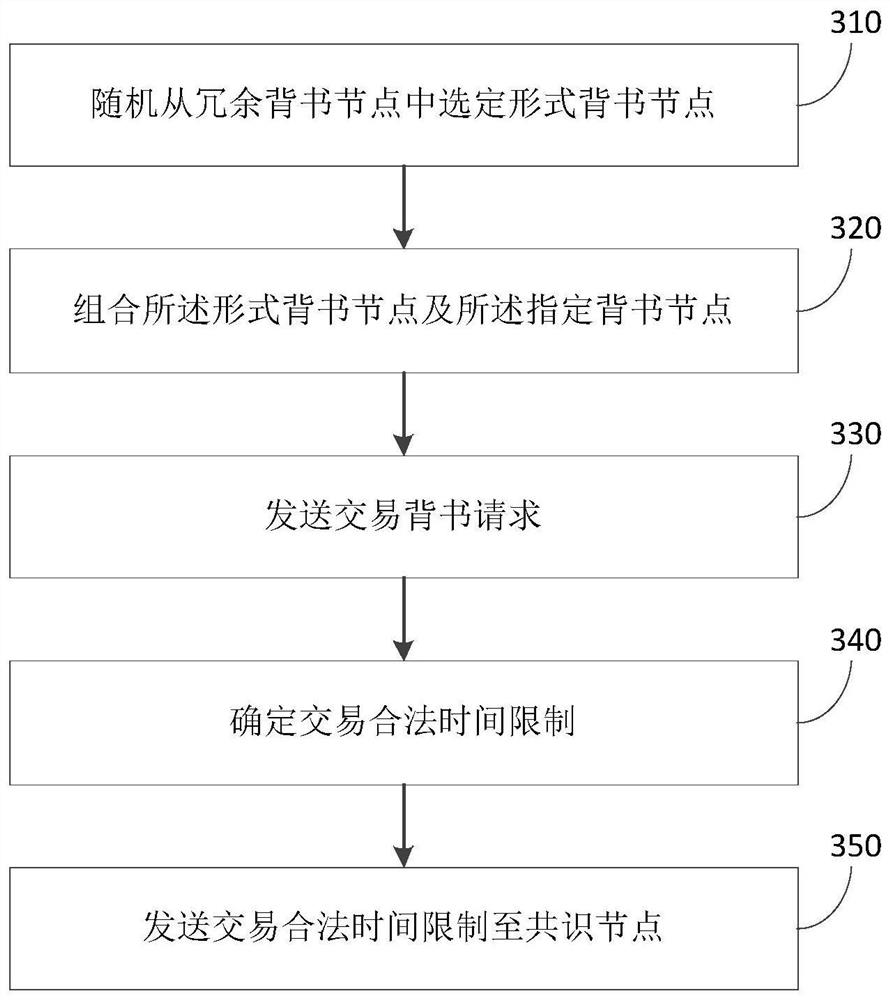
Method, system and device for resisting distributed denial of service attack and storage medium
The invention provides a distributed denial of service attack resisting method, system and device and a storage medium, and the method comprises the steps: randomly selecting a form endorsement node from redundant endorsement nodes, the redundant endorsement nodes being endorsement nodes except a designated endorsement node of a current transaction in a block chain; and sending a transaction endorsement request to the specified endorsement node and the formal endorsement node. According to the method, formalized endorsement is carried out by setting the formalized endorsement node, and the transaction endorsement request is randomly sent to the formalized endorsement node in the transaction process of the block chain node, so that false transaction type judgment information can be transmitted to the DDoS internal attacker, and the purpose of interfering the transaction type judgment of the DDoS internal attacker is achieved; and therefore, the attack measurement of an attacker in the DDoS is difficult to carry out effectively.
Owner:香港城市大学深圳研究院
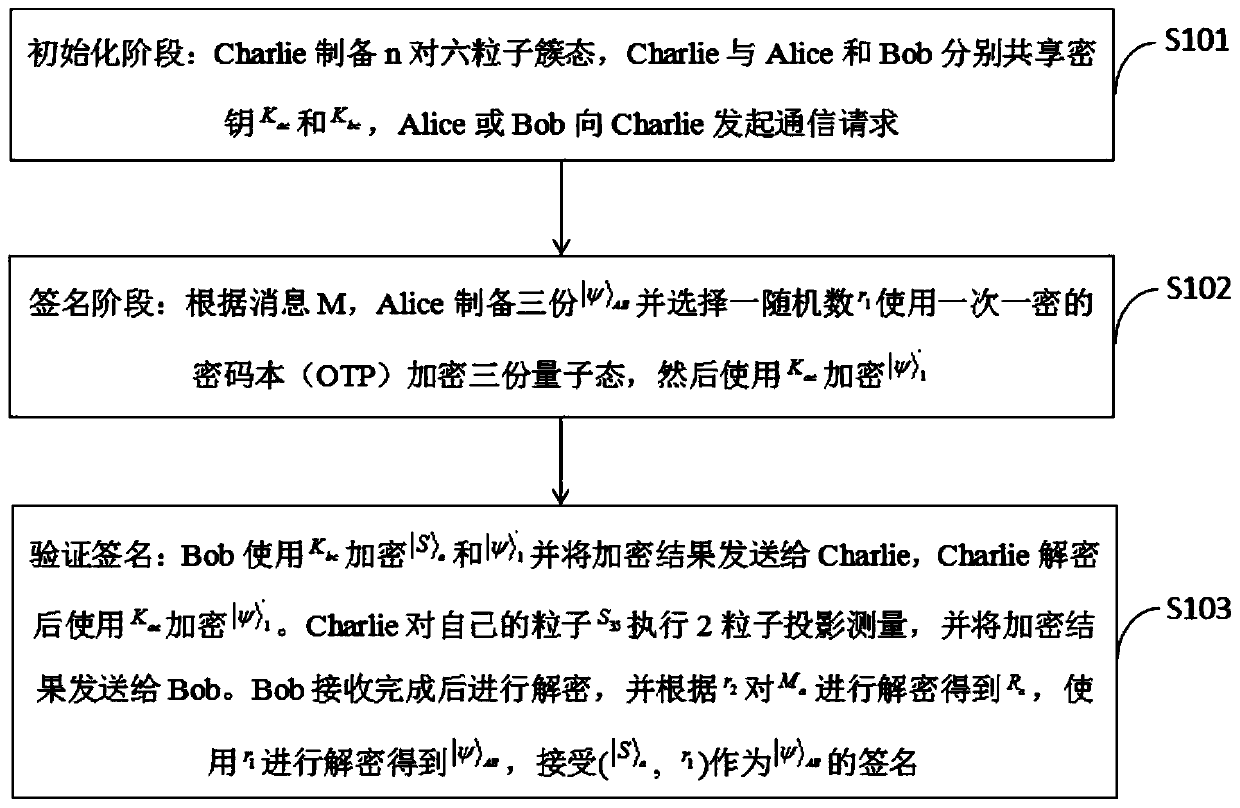
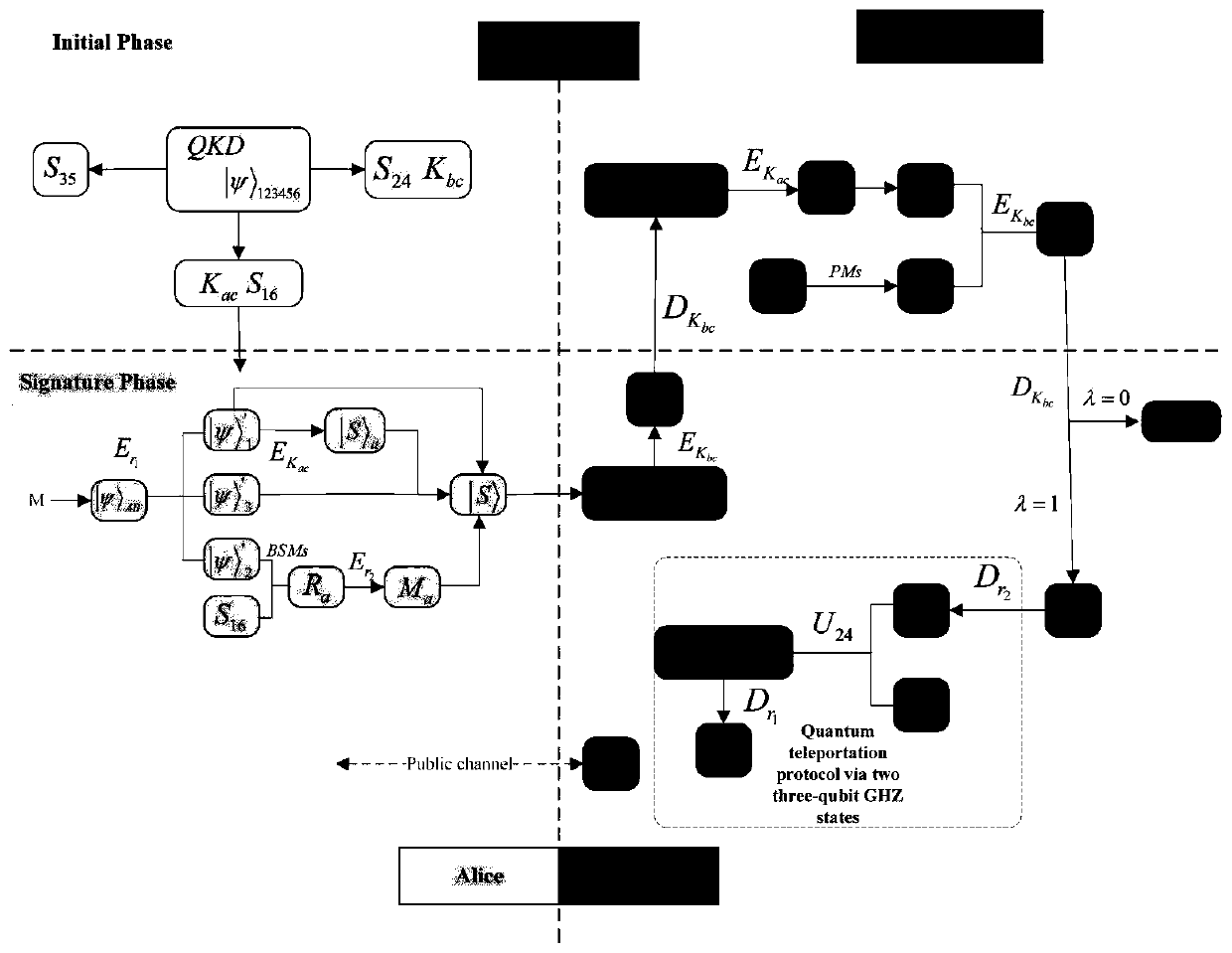
Quantum arbitration signature method and system based on six-particle stealth transfer
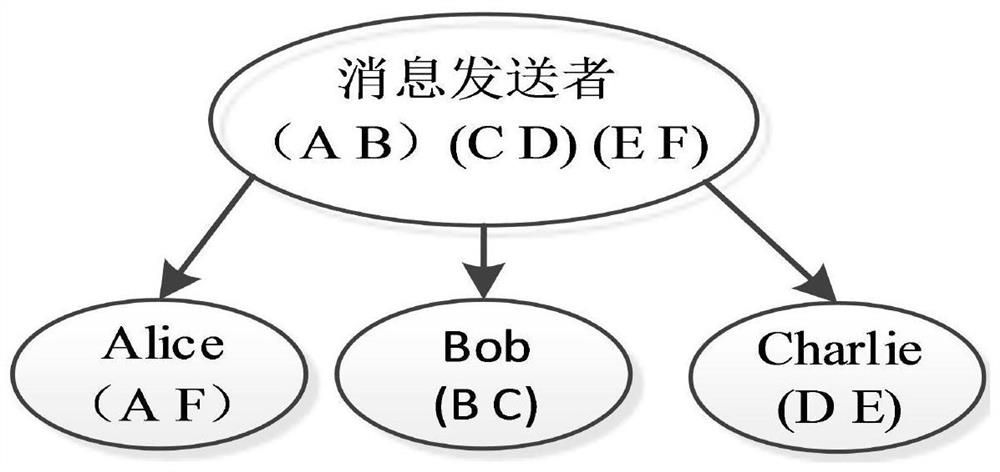
ActiveCN110912695AImprove efficiencyResist noise interferenceKey distribution for secure communicationUser identity/authority verificationAlice and BobInterference (communication)
The invention belongs to the technical field of quantum arbitration signature and discloses a quantum arbitration signature method and system based on six-particle stealth transfer, and the method comprises the steps: preparing n pairs of six-particle cluster states through Charlie, enabling the Charlie and Alice and Bob to respectively share secret keys Kac and Kbc, and enabling the Alice or Bobto initiate a communication request to the Charlie; preparing three parts of ABs (| psi > AB) according to the message M and Alice, selecting a random number r1, encrypting three parts of quantum states by using a one-time pad password book, and then encrypting the three parts of quantum states by using Kac (| psi > '1); verification signature. A six-particle entanglement system composed of two three-particle GHZ states is used, and the stable entanglement attribute of the six-particle entanglement system is utilized to realize long-term particle storage, so that noise interference existing ina quantum channel can be well resisted; internal attack and external attack strategies are resisted through a shared key pair; a three-party mutual identity authentication framework is established through key pairs shared by three parties respectively.
Owner:CHENGDU UNIV OF INFORMATION TECH
IP for switch-based ACL
InactiveCN104202293AProtected from insider attacksData taking preventionData switching by path configurationInsider attackAccess control list
A system that facilitates protecting an internal network from internal attacks comprises an entity that requests access to the internal network, wherein the internal network includes a plurality of items. A multi-layered security component determines that the entity is authorized to access the internal network, and restricts access of the entity to a subset of the items. In accordance with one aspect of the present invention, a switch can be employed to restrict access of the entity to a subset of the items.
Owner:ROCKWELL AUTOMATION TECH
Safety authentication method of cloud storage system
The invention relates to a safety authentication method of a cloud storage system, belonging to the field of storage technology and information security technology of computers. The method solves the problems that the existing safety authentication methods are complex in authentication process and great in authentication consumption, and aims at providing simple, flexible and efficient authentication with high expandability and high safety for service safety of a cloud storage system, so as to prevent invasion of external or internal attackers to the storage system. The method comprises a client process, an authentication end progress and a storage end progress; the client loads the user identifiers of all login users, and the authentication end loads an access control library. The method checks whether the operation authorization of the user is legal by calculating the verifying identifier, the storage end does not need to maintain the access control library any longer, and verification on the access request of the user can be completed with simple calculation, thereby greatly reducing expense of the storage system on access control, and providing flexible, safe, reliable and efficient file access for users having operation authorization in the large-scale cloud storage system.
Owner:HUAZHONG UNIV OF SCI & TECH
Password reverse firewall method suitable for digital signature
ActiveCN111404693AImprove securityPrivacy protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyDigital signature
The invention discloses a password reverse firewall method suitable for a digital signature, and belongs to the technical field of information security. The method comprises the following steps: firstly, setting a transparent and credible password reverse firewall at a signature party, and setting related system parameters; when the password reverse firewall receives the parameters, resetting partof the parameters and then forwarding to the signature party; the signature party signing the message based on the received parameters to obtain a signature result and transmitting the signature result to a password reverse firewall of the signature party, and the password reverse firewall resetting part of sub-signatures in the signature result and then transmitting the sub-signatures to the verification party; and the verification party carrying out verification processing on the received signature, verifying a legal signature about the message, outputting acceptance if the verification ispassed, and outputting rejection if the verification is not passed. The arrangement of the password reverse firewall meets three basic requirements of the password reverse firewall, transparency and credibility are achieved, leakage is prevented, the safety of a user is improved, and the attack behavior of an internal attacker is particularly protected.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
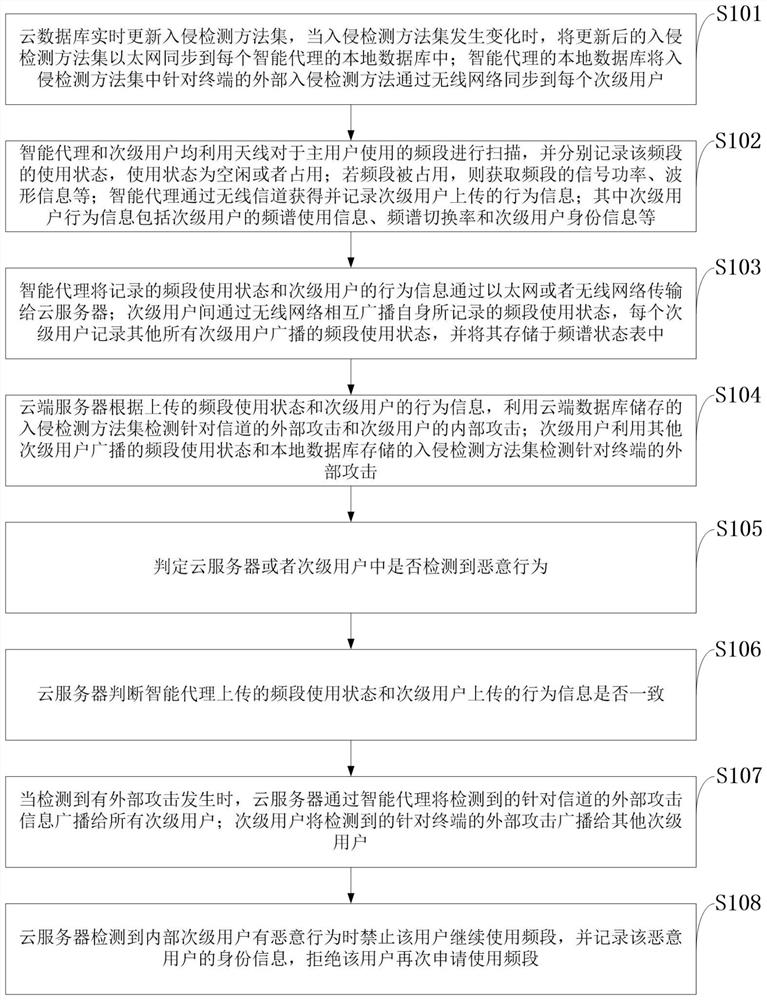
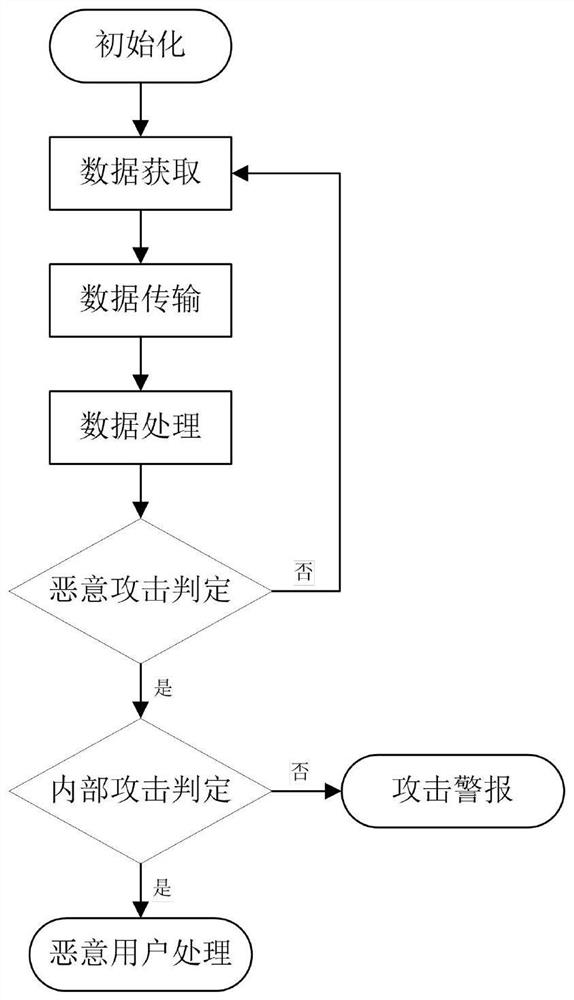
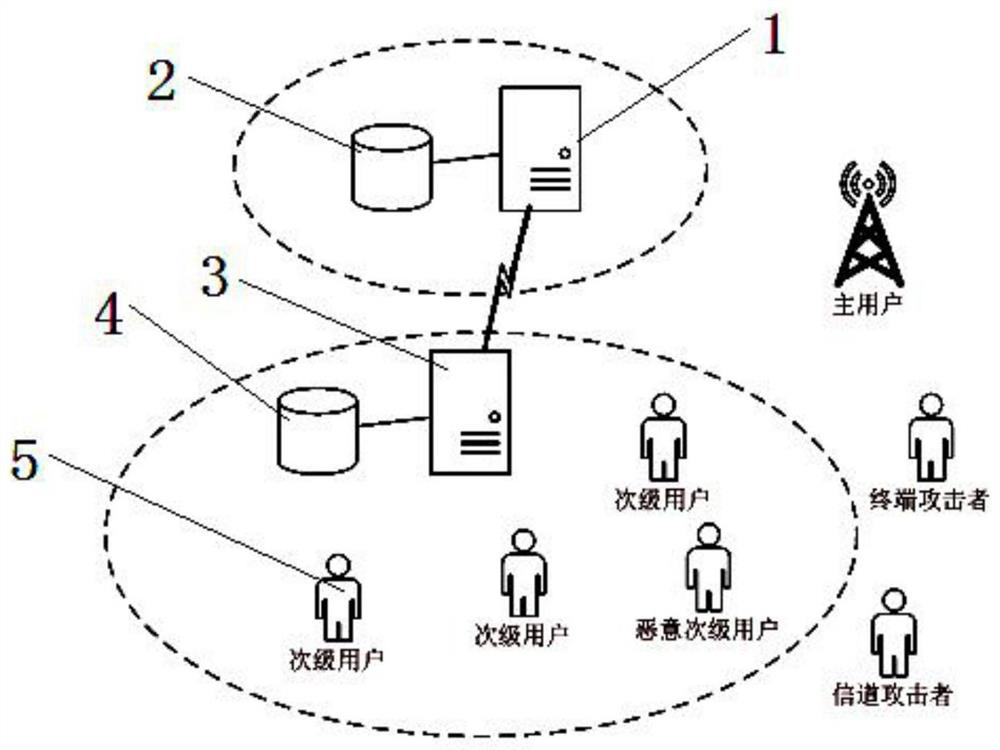
Two-way intrusion detection method and system based on cloud computing
ActiveCN107483413BSimplify functionsAvoid interactionTransmissionSecurity arrangementInformation processingRadio networks
Owner:XIDIAN UNIV
A Cryptographic Reverse Firewall Applicable to Digital Signature
ActiveCN111404693BImprove securityPrivacy protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyDigital signature
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A quantum secret information sharing method and system suitable for company property management
ActiveCN108512659BImprove securityEnsure safe sharingKey distribution for secure communicationAttackEngineering
The invention belongs to the technical field of data processing, and discloses a quantum secret information sharing method and system suitable for company property management, all entangled particles are prepared by a manager; when wiretapping detection is performed, the manager merges the first user and the second user 、Comparing the measurement results released by the third user with their own local operation code information, if they are inconsistent, stop the protocol operation; at the same time, a quantum secret information sharing system for company property management is disclosed. The invention can prevent external eavesdropping and internal attack, and ensure the safe sharing of secret information. If it wants to expand to more participants, only the sender needs to prepare a corresponding number of entangled particles.
Owner:孚普科技(北京)有限公司
Private information comparison method based on continuous variable ionic state
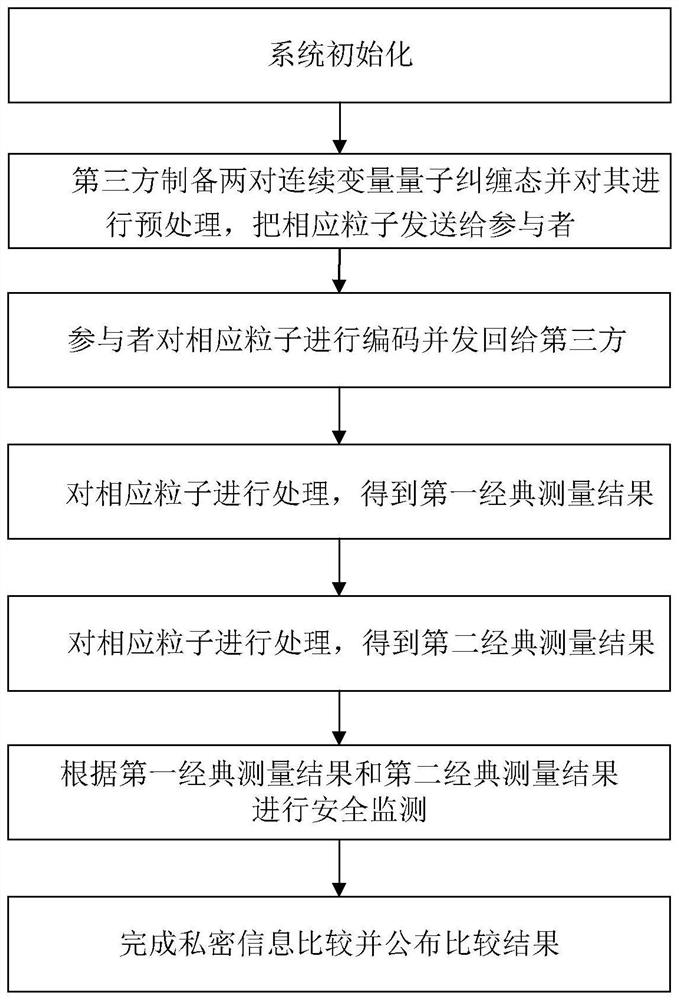
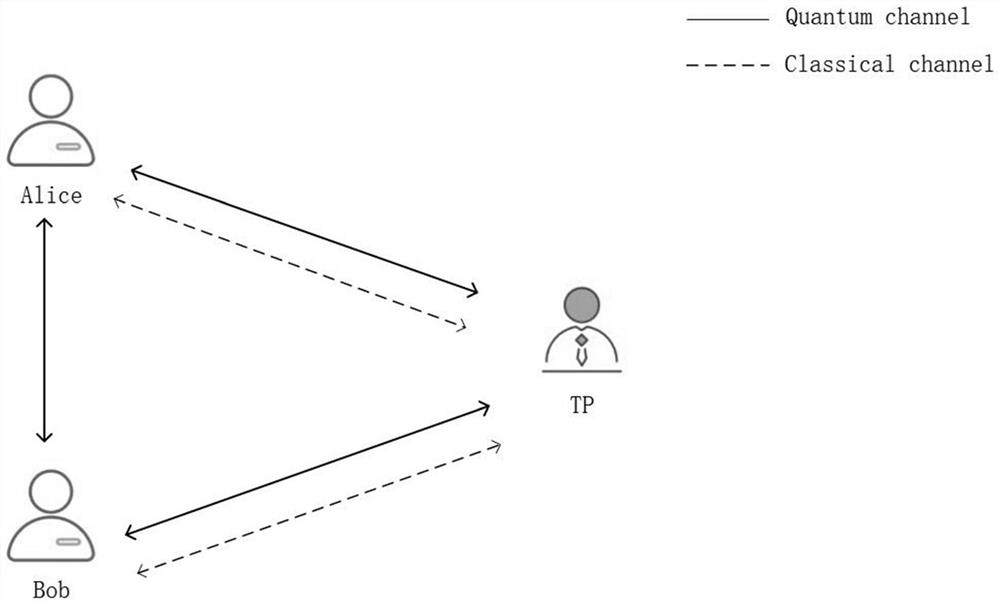
PendingCN114697023AEnsure safetyGuaranteed correctnessKey distribution for secure communicationCryptographic attack countermeasuresThird partyAttack
The invention belongs to the field of quantum communication and quantum cryptography, and particularly relates to a private information comparison method based on a continuous variable ionic state. The method comprises the following steps: initializing a system; the third party prepares two pairs of continuous variable quantum entangled states, preprocesses the continuous variable quantum entangled states and sends corresponding particles to the participants; the participant encodes the preprocessed corresponding particles and sends the encoded particles to the third party; the third party processes the corresponding particles to obtain a first classical measurement result and a second classical measurement result; the third party carries out safety monitoring according to the first classical measurement result and the second classical measurement result, if the safety monitoring is passed, private information comparison is completed according to the first classical measurement result and the second classical measurement result, and a comparison result is published, otherwise, system initialization is returned; according to the method, external attacks and internal attacks can be effectively resisted, the security and correctness of the protocol are ensured, quantum resources can be prepared, unified operation and measurement can be realized, and the method has higher practicability.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A Dynamic Access Control Method Facing Internal Attacks
The invention discloses a dynamic access control framework for internal attacks, belonging to the technical field of information security access control, including: submission of access requests, calculation of user enabled roles, calculation of role enabled permissions, selection of enabled roles, selection of candidate uses Reduction of functional roles, calculation of risk value, using the environment model to evaluate the satisfiability of the environment constraints in the access control strategy, realize the dynamic adjustment of user permissions, and prevent illegal users from accessing, and then, according to the policy constraints and risk analysis, Restrict the scope of authority of legitimate users to avoid internal attacks by malicious users. The present invention realizes triple control on access requests by analyzing environmental information, policy constraints, and access risks, can prevent illegal and malicious access behaviors in time, protect network resources more effectively, and ensure safe and efficient operation of the system.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
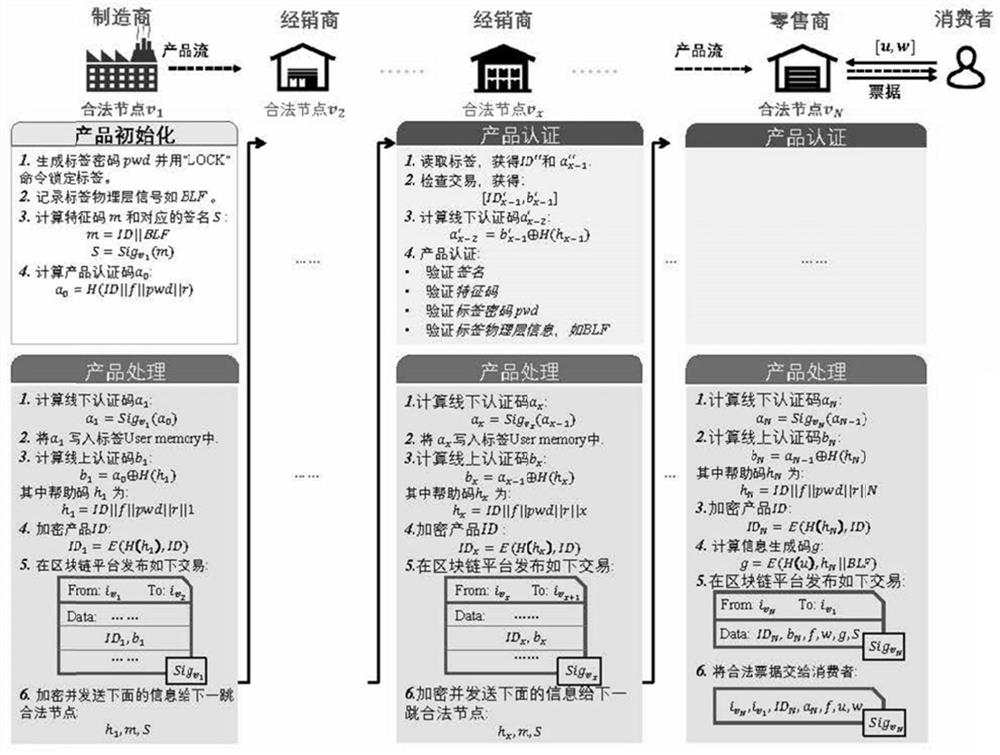
Whole industry chain product traceability authentication method and system based on block chain technology
PendingCN114565393ARealize decentralized managementTransparent serviceCo-operative working arrangementsDigital data protectionAttackProduct traceability
The invention discloses a whole industrial chain product traceability authentication method and system based on a block chain technology, which support all legal nodes on an industrial chain to carry out traceability and authentication on a product at any time, and can also provide a simple and easy-to-operate authentication service for an individual user without corollary equipment and resources. Meanwhile, decentralized credible traceability is realized through a block chain technology, that is, authentication does not need to depend on the reliability of a certain node, and an authentication result can be directly and automatically deduced from information disclosed in a block chain. The method can resist more than ten attack forms including external attacks, collusion attacks and internal attacks, and has high security.
Owner:XI AN JIAOTONG UNIV
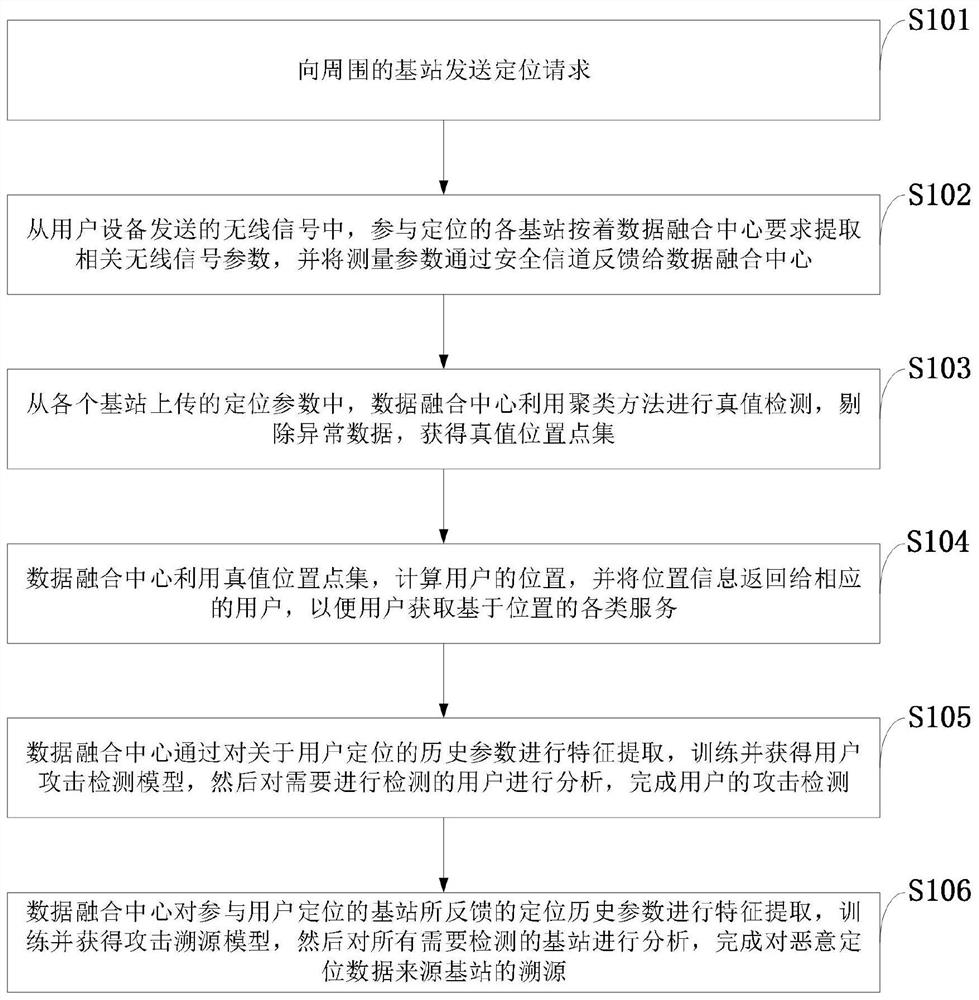
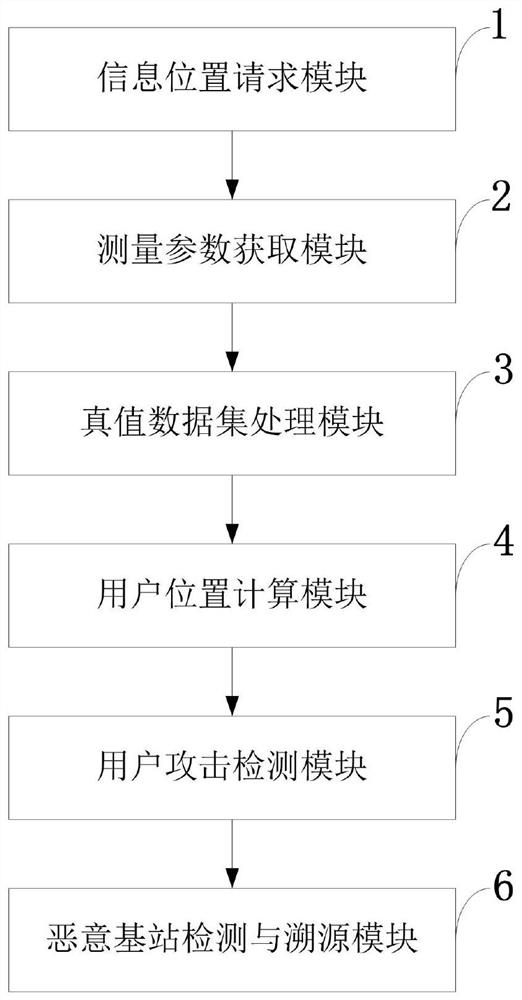
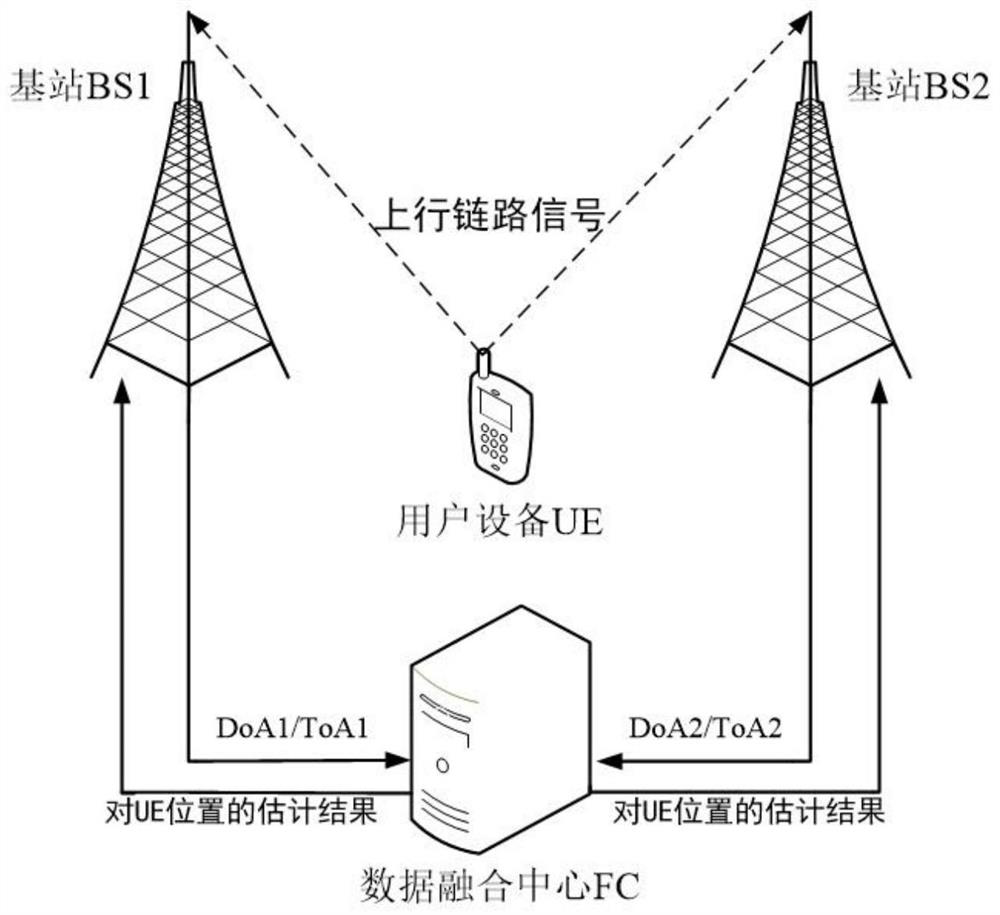
5g positioning truth detection and attack traceability method, system, equipment and application
ActiveCN112601173BHigh positioning accuracyGuaranteed to be authenticLocation information based serviceSecurity arrangementInterference (communication)Attack
The invention belongs to the technical field of user positioning security in mobile communication networks, and discloses a method, system, device and application for 5G positioning truth detection and attack traceability; relevant parameters are extracted from wireless signals sent by users, and the data fusion center utilizes clustering The method clusters the positioning data, excludes abnormal data, and realizes truth detection and credible positioning information calculation; uses the historical records of positioning parameters to extract relevant features, and completes the training of user attack detection model and base station traceability model. , respectively analyze the positioning parameters of the user to be detected and the parameters uploaded by the positioning base station, and effectively complete the attack detection of the target user and the attack traceability of the malicious base station. The invention can not only ensure the authenticity and reliability of user positioning, but also has extremely high positioning accuracy, and can effectively resist interference attacks on user wireless positioning signals and internal attacks on base stations responsible for positioning, ensuring the security of the positioning system, and has excellent robustness.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com