Safety authentication method of cloud storage system
A cloud storage system and security authentication technology, applied in the transmission system, electrical components, etc., can solve the problems of huge authentication consumption and complicated authentication process, and achieve the effect of efficient file access, reliable file access, and cost reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The invention describes a security authentication method and implementation of a cloud storage system, and is implemented in a distributed file system.
[0059] The present invention is further described below in conjunction with embodiment and accompanying drawing.
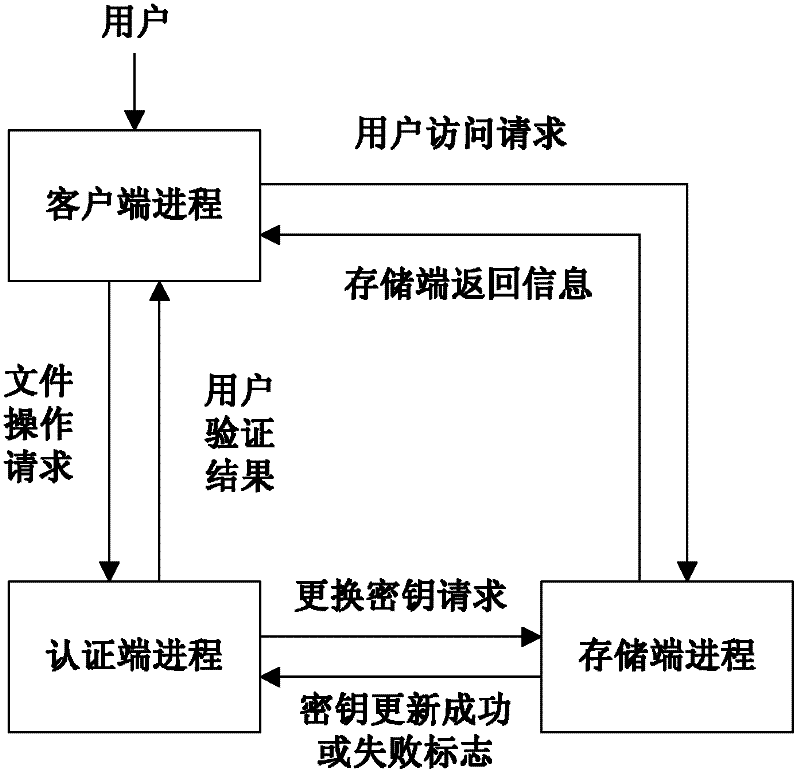
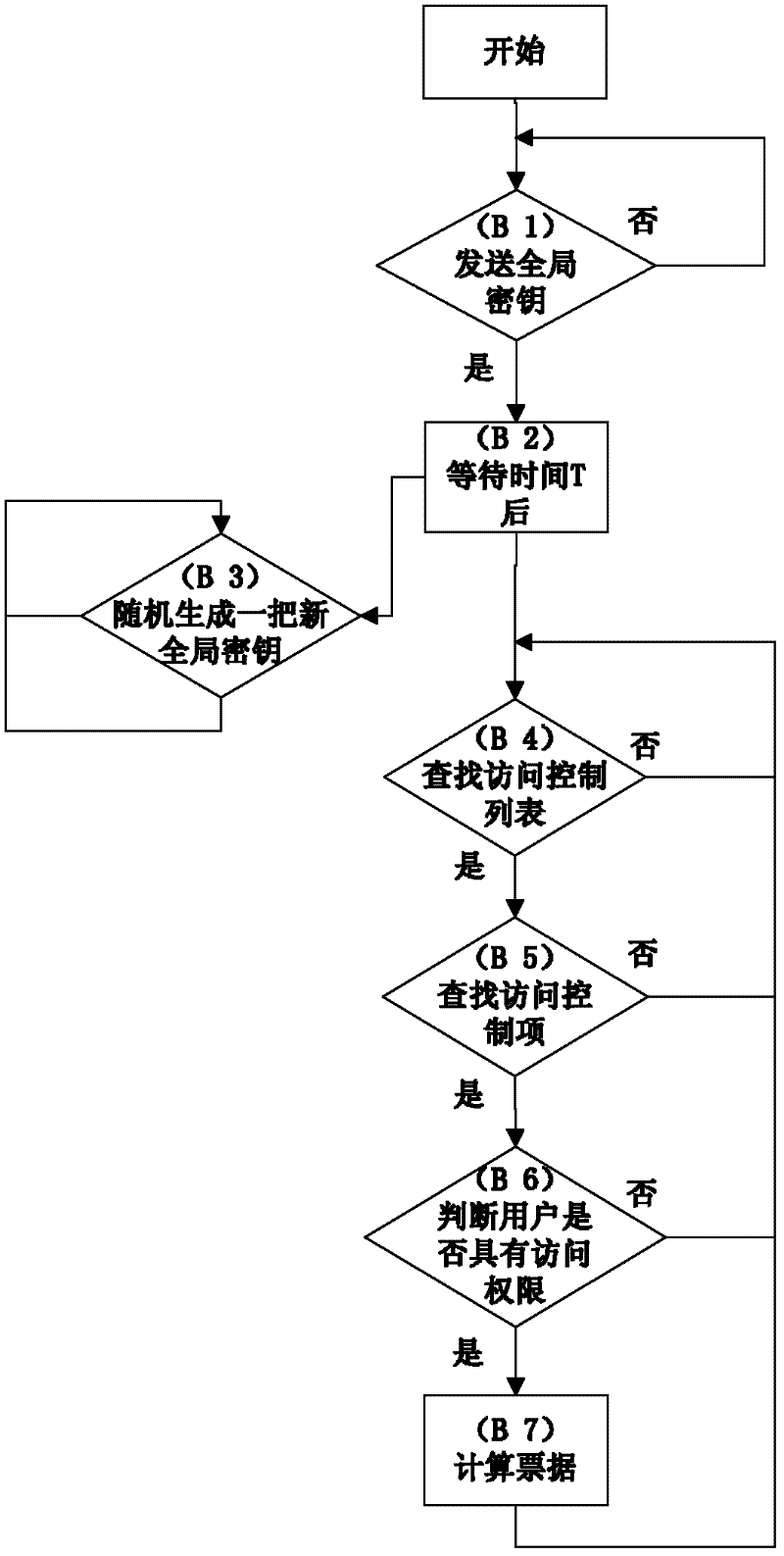
[0060] Such as figure 1 As shown, the embodiment of the present invention includes a client process, an authentication end process and a storage end process, respectively running on the client host, the authentication end host, and the storage end host of the distributed file system; User ID, the authentication end loads the access control library;
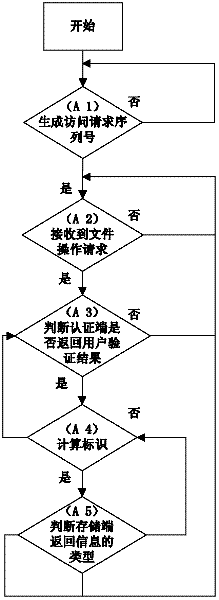
[0061] A. If figure 2 As shown, the client process includes the following steps:
[0062] (A1) The client randomly generates an access request serial number R0, sends it to the storage terminal, waits for the return information from the storage terminal, and after receiving the return information from the storage terminal, judges whether the information is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com