SDN edge computing network system based on blockchain encryption, encryption method and medium
An edge computing and network system technology, applied in the field of network systems, can solve the problems of not being able to know the identity of the attacker, data loss, etc., and achieve the effect of avoiding internal network attacks and data loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
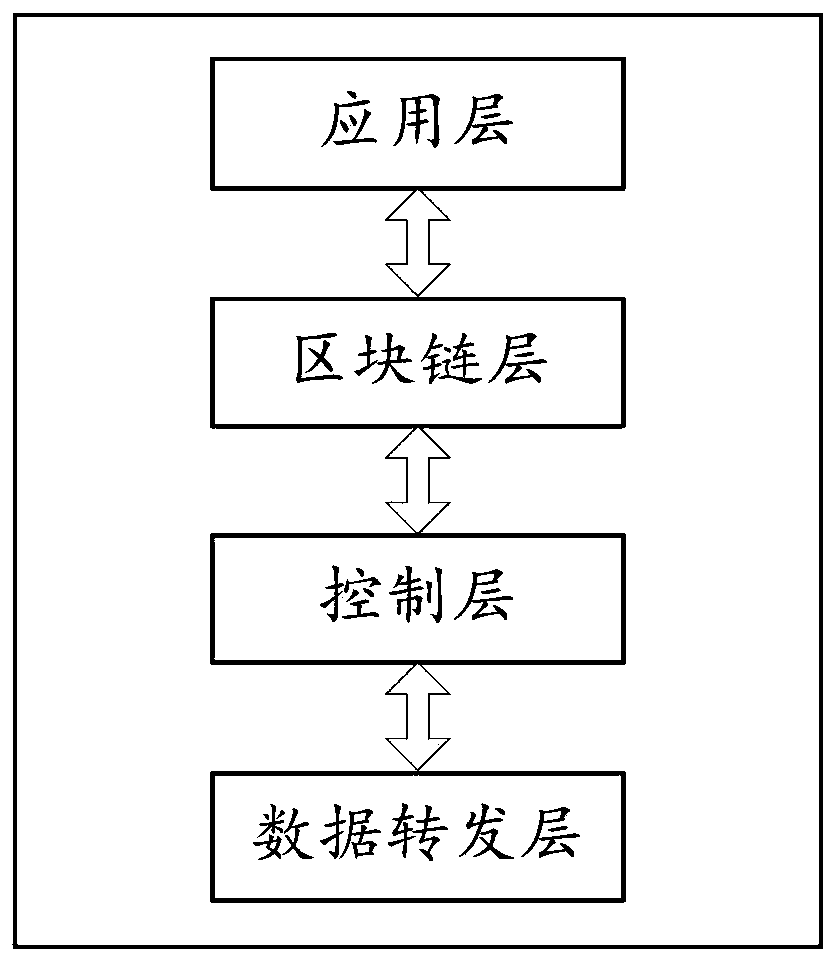
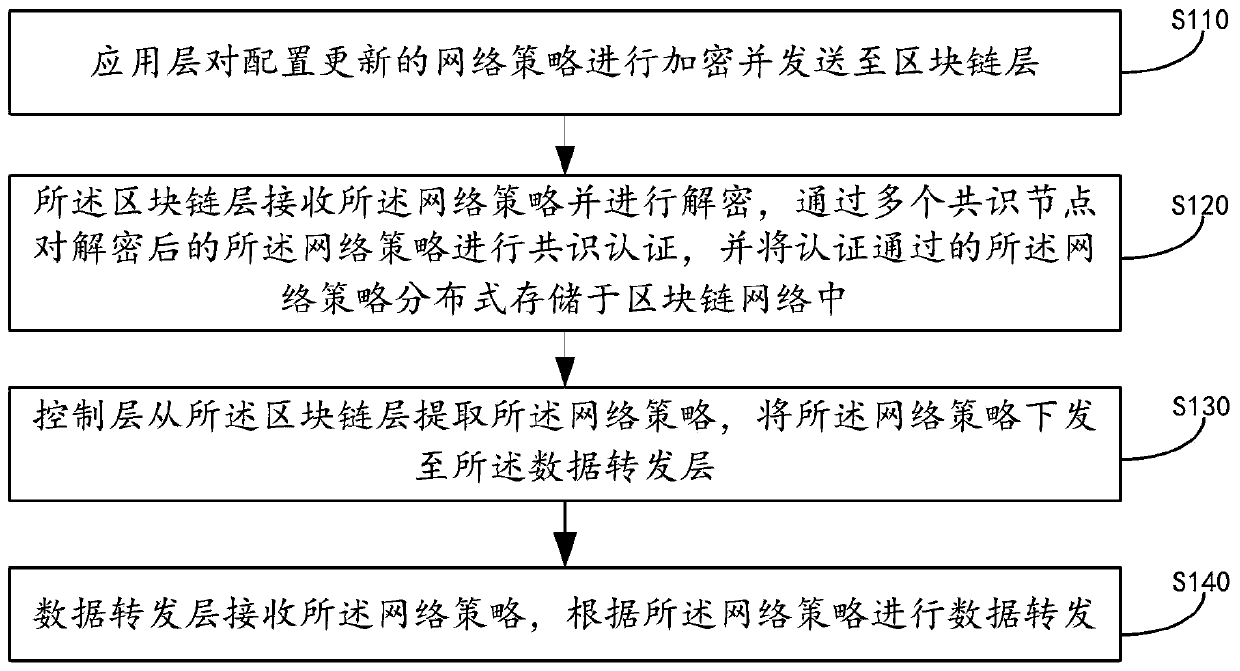
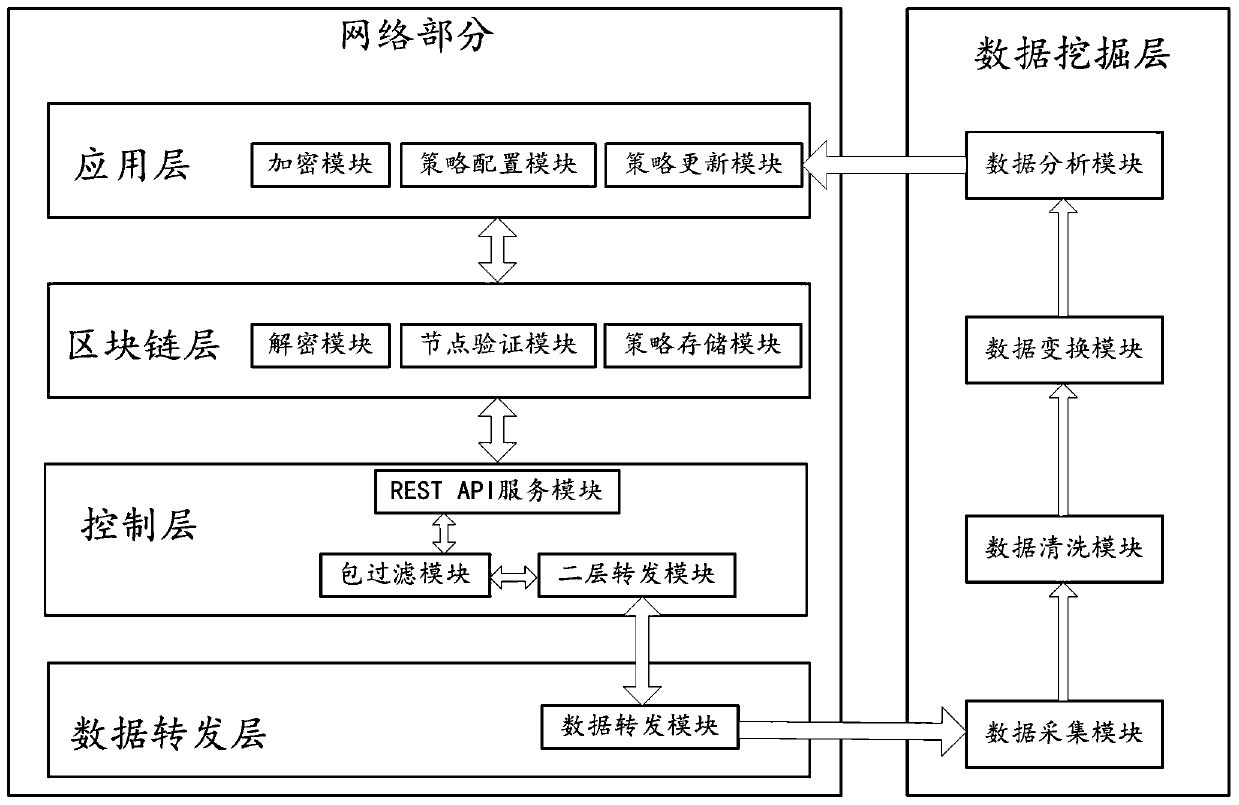
[0041] figure 1 A schematic structural diagram of an SDN edge computing network system based on blockchain encryption provided by Embodiment 1 of the present application is given. Refer to figure 1 , the SDN edge computing network system based on blockchain encryption includes: an application layer, a blockchain layer, a control layer, and a data forwarding layer; wherein the application layer is used for configuring and updating network policies, encrypting network policies and sent to the blockchain layer; the blockchain layer is used to decrypt the network strategy, and perform consensus authentication on the decrypted network strategy through a plurality of consensus nodes, and pass the authentication to the network The policy is distributed and stored in the block chain network; the control layer is used to extract the network policy from the block chain layer and send the network policy to the data forwarding layer; the data forwarding layer uses to perform data forward...
Embodiment 2
[0067] The embodiment of the present application also provides a storage medium containing computer-executable instructions, the computer-executable instructions are used to execute an encryption method of an SDN edge computing network system based on blockchain encryption when executed by a computer processor, The encryption method of the SDN edge computing network system based on block chain encryption includes: the application layer encrypts the network policy of configuration update and sends it to the block chain layer; the block chain layer receives the network policy and decrypts it, Perform consensus authentication on the decrypted network strategy through multiple consensus nodes, and distribute and store the authenticated network strategy in the blockchain network; the control layer extracts the network strategy from the blockchain layer , delivering the network policy to the data forwarding layer; the data forwarding layer receives the network policy, and forwards da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com