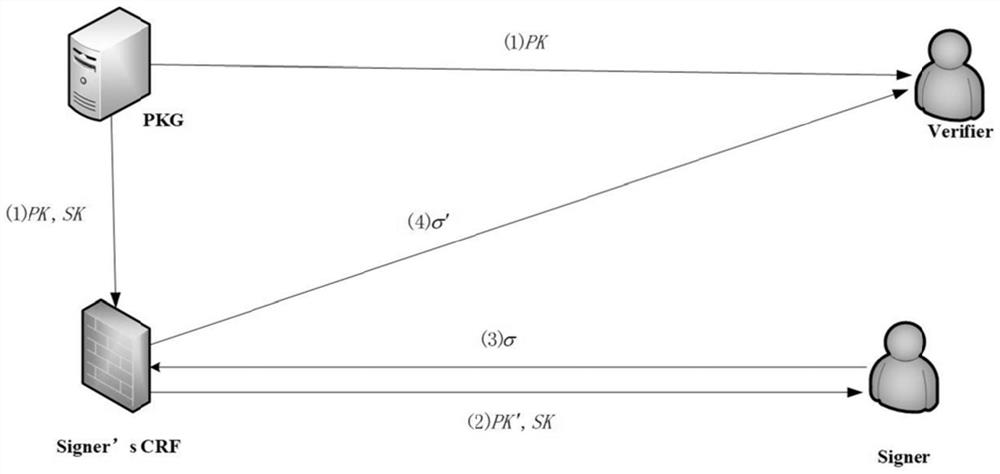
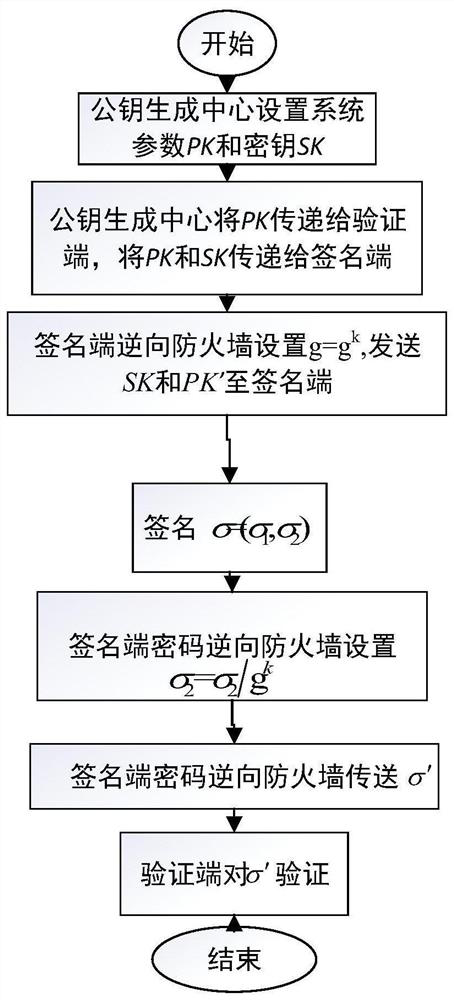
A Cryptographic Reverse Firewall Applicable to Digital Signature
A digital signature and firewall technology, which is applied in the field of information security, can solve the problems of difficult implementation of password reverse firewall technology and high requirements for re-randomization, and achieve the effects of enhancing security, protecting privacy, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the implementation methods and accompanying drawings.
[0034] The invention is a cryptographic reverse firewall method suitable for digital signatures, comprising:
[0035] Due to the existence of hash functions in the algorithm implementation of most digital signatures (such as Schnorr signatures, DSS signatures, Hess signatures, etc.), and the irreversible nature of hash functions, the requirement of re-randomization cannot be realized. What the present invention uses is a kind of special signature, and this signature is Waters B in 2005 [Efficient Identity-Based Encryption Without Random Oracles.In: Cramer R. (eds) Advances in Cryptology–EUROCRYPT 2005.LNCS, vol 3494.Springer , Berlin, Heidelberg] in a signature proposed by the signer using Instead of the original H(ID) to represent th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com