A Dynamic Access Control Method Facing Internal Attacks
A dynamic access control and internal attack technology, applied in transmission systems, electrical components, etc., can solve problems such as only considering, not considering constraints, and ignoring the cumulative risk of users, so as to prevent access, protect network resources, and prevent illegal and the effect of malicious access behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] In order to make the technical solutions of the present invention clearer and clearer to those skilled in the art, the present invention will be further described in detail below in conjunction with the examples and accompanying drawings, but the embodiments of the present invention are not limited thereto.
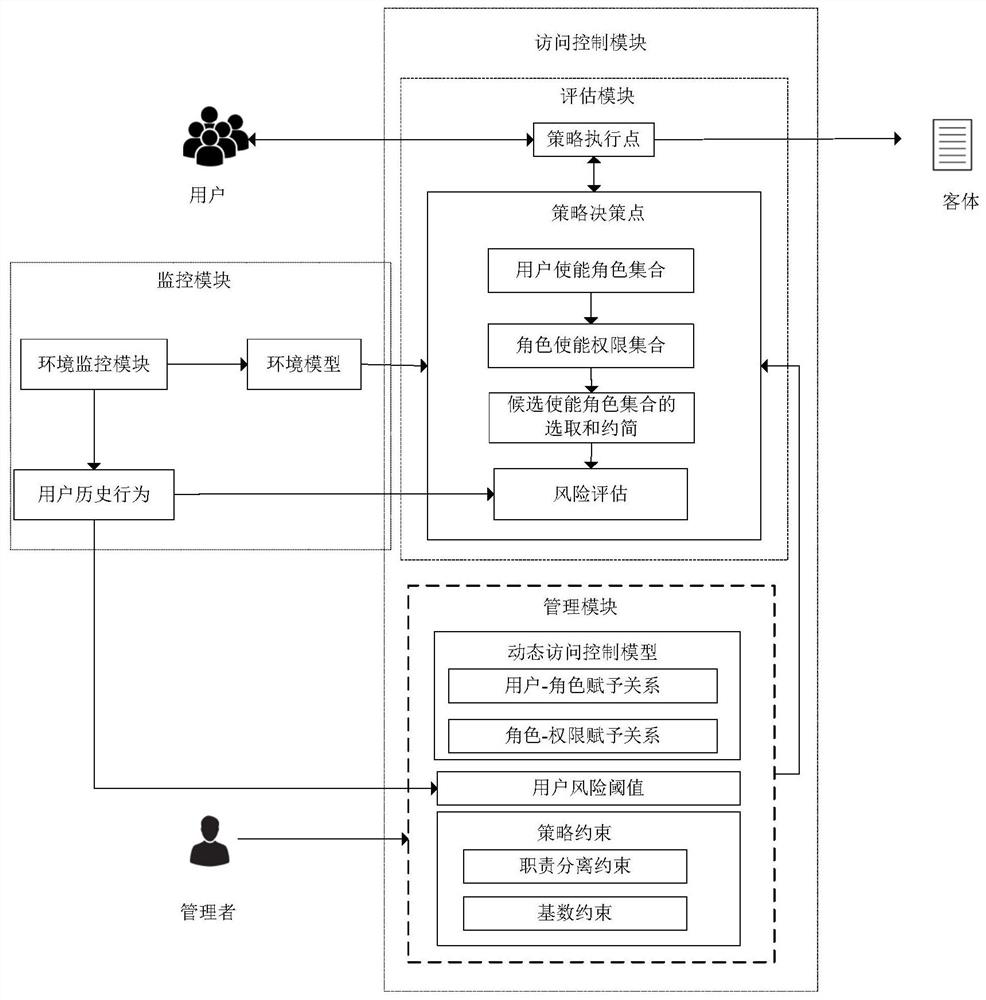
[0076] Such as figure 1 As shown, the internal attack-oriented dynamic access control method of this embodiment specifically includes the following steps:
[0077] Step 1) Submit access request phase:
[0078] The user submits the current access request, the policy enforcement point intercepts the access request, and forwards the access request to the policy decision point. In the stage of submitting the access request, the access request contains two attributes: access user and access right, and the access right includes access activity and object;
[0079] Step 2) Calculation of user enabled role set:
[0080] According to the current environment model and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com