Method for comprehensively analyzing and processing real-time alarms on basis of attack strategy graphs and intrusion detection system thereof
A processing method and comprehensive analysis technology, applied in transmission systems, electrical digital data processing, instruments, etc., can solve problems such as the influence of the accuracy of the correlation results, the inability to correlate the time span, and the large time span, so as to ensure the actual availability and improve the accuracy performance, improve processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
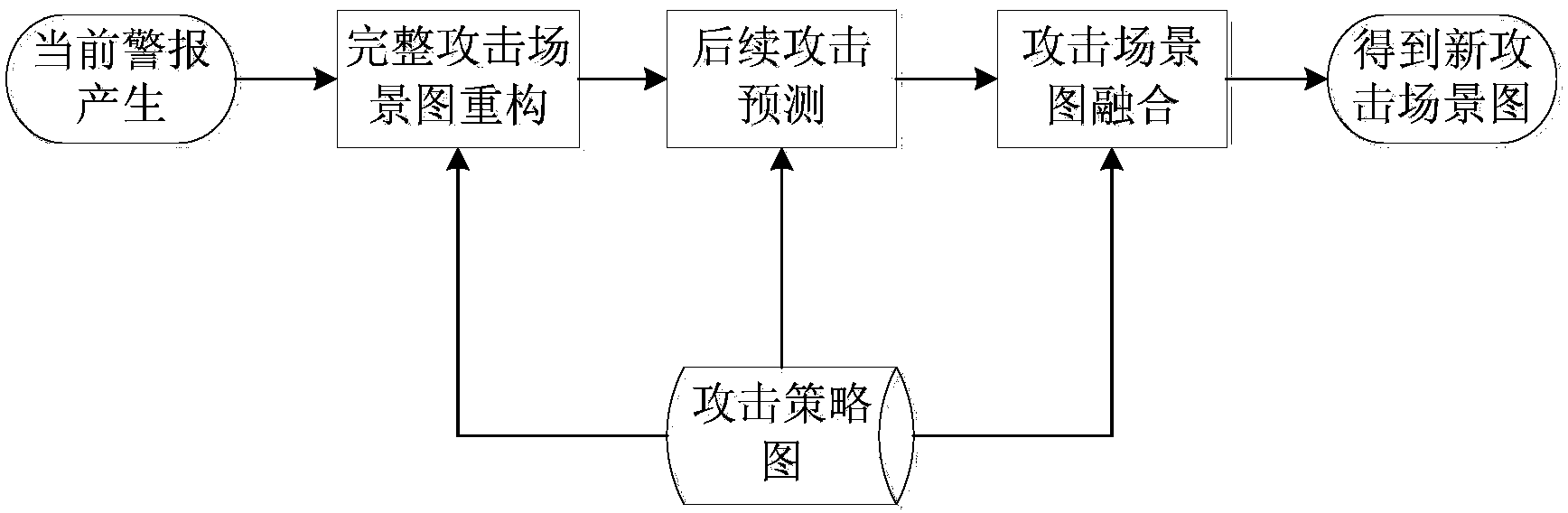
[0045] The real-time alarm comprehensive analysis and processing method based on the attack strategy diagram of the present invention, such as figure 1 shown, including the following steps.
[0046] Step 1, creation of attack strategy map.
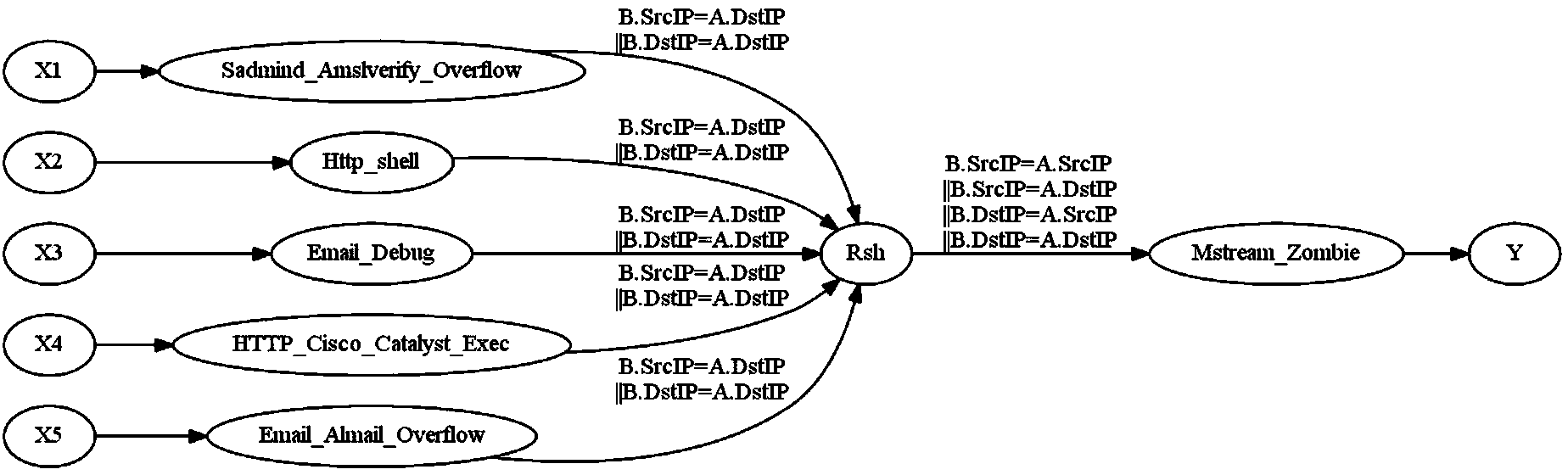
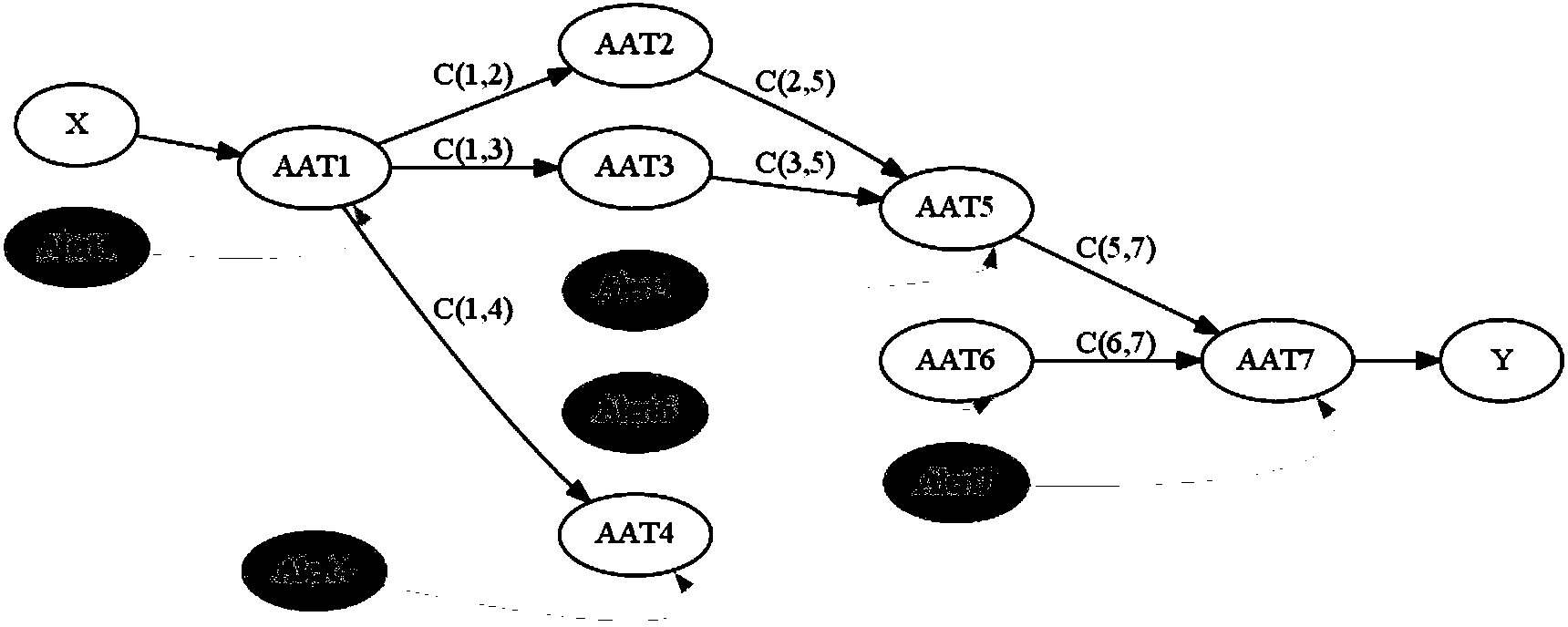
[0047] The attack strategy graph (Attack Strategy Graph, ASG) is a directed acyclic graph, which is used in the present invention to represent the prior knowledge of the attack, that is, the causal relationship between the attacks; in order to construct the ASG, the atomic attack type is first defined to expand And structure the original alarm information, and then construct the attack strategy map.
[0048] Definition 1 Atomic Attack Type (Atomic Attack Type, AAType), AAType is defined as: (AAttack, Require, Provide).
[0049] Among them, AAttack is t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com