Method and system for three-in-one smart card anti-side-channel-attack protection
A side-channel attack, trinity technology, applied in the field of information security, can solve problems affecting the availability of smart cards, etc., to achieve the effect of increasing difficulty, good effect, and meeting the cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
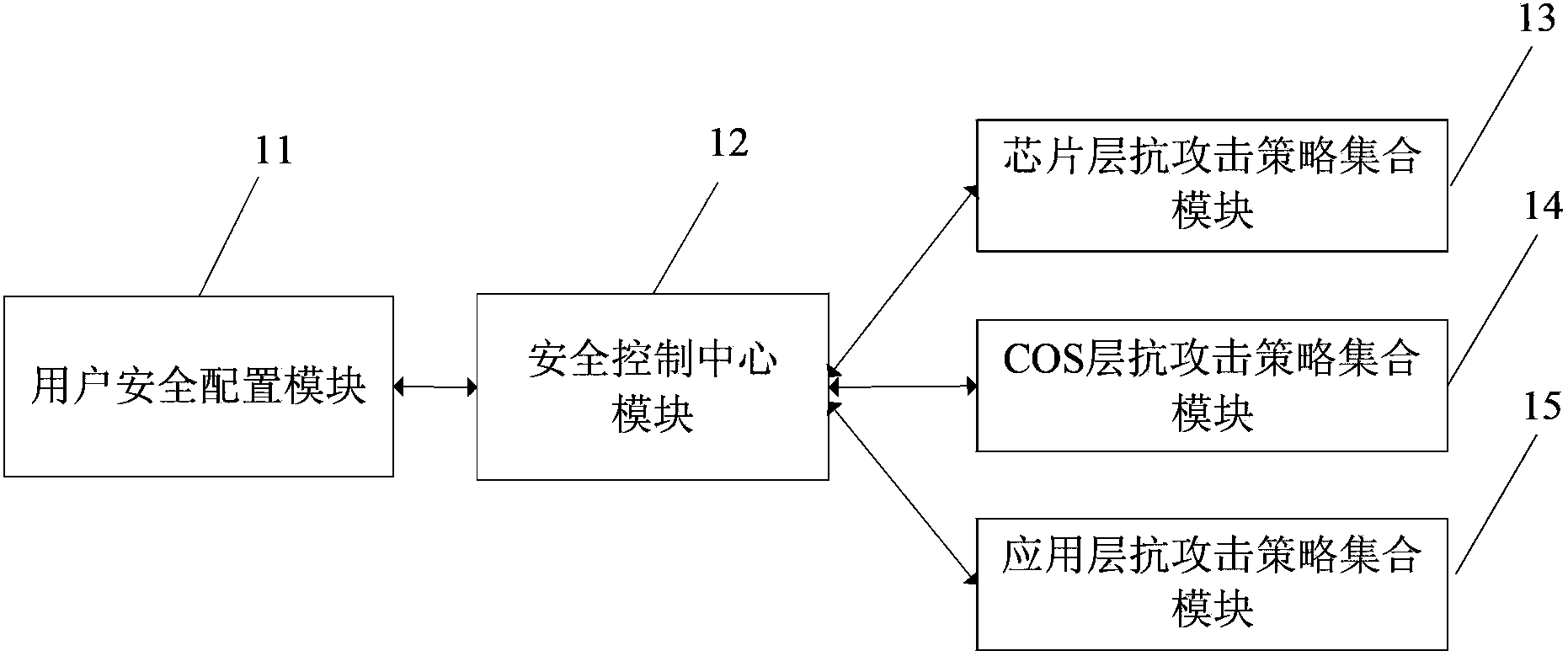
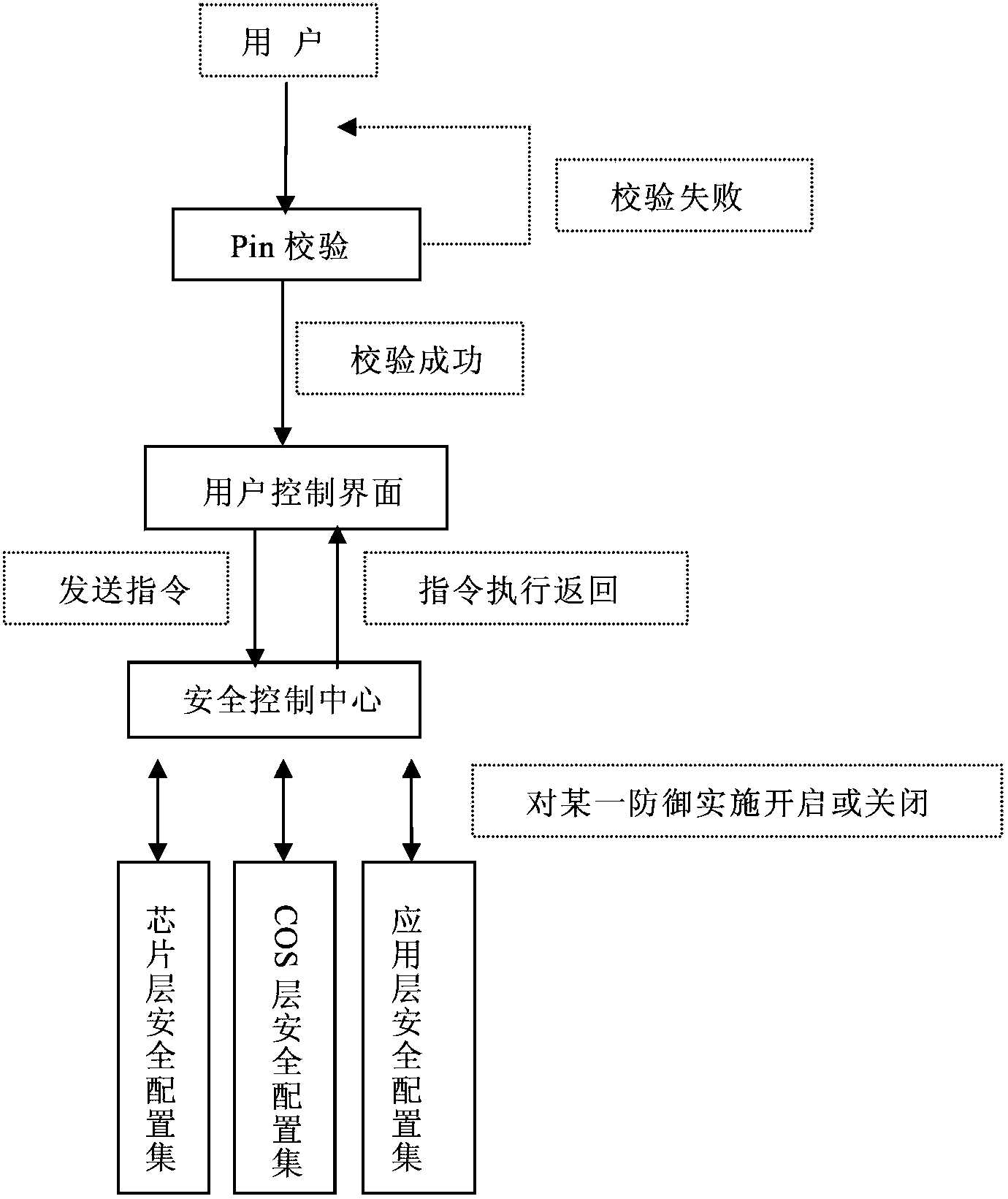
[0071] Such as figure 2 As shown, a smart card trinity anti-side channel attack protection system includes a user security configuration module 11 and a security control center module 12 connected thereto, a chip layer anti-attack strategy collection module 13 connected to the security control center module 12, and a COS layer anti-attack strategy module 13. Attack strategy collection module 14, application layer anti-attack strategy collection module 15, the detailed description of each module is as follows:
[0072] User security configuration module 11: It is convenient for users to perform reasonable configuration according to smart card application requirements. This module implements a user security configuration interface on the PC side. Legal users can operate the security control center through this user interface after completing PIN...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com