Defense strategy generation method based on three-party dynamic game
A generation method and dynamic game technology, applied in the field of network security, can solve problems such as inaccurate results and ignoring the influence of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
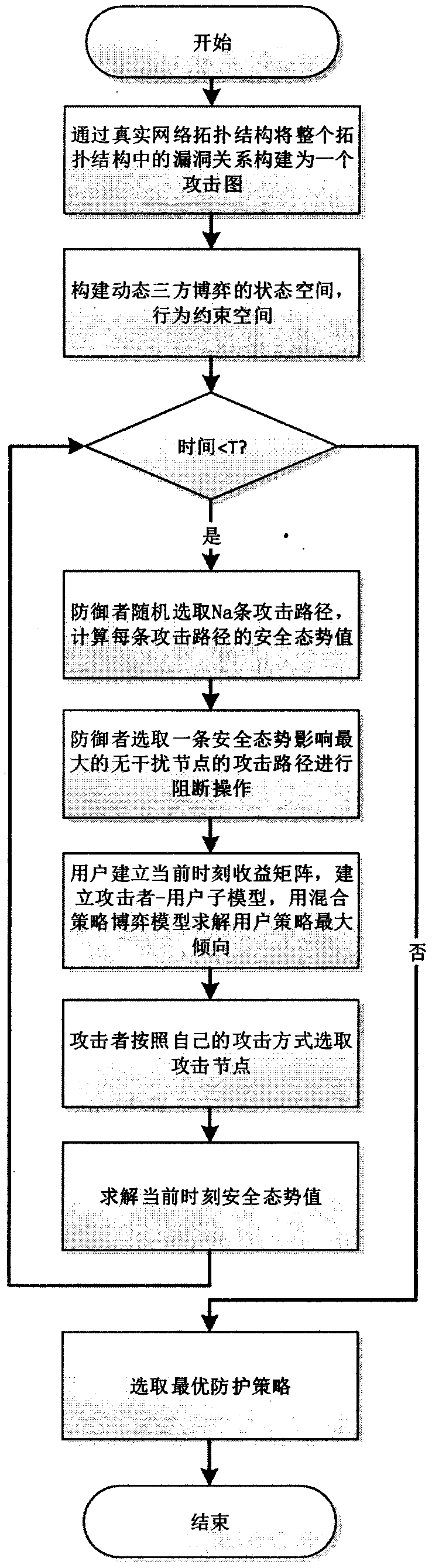
[0054] as attached figure 1 As shown, the present invention is a method for generating a defense strategy based on a three-party dynamic game, which is divided into three stages: a preprocessing stage, a dynamic game stage, and a strategy generation stage.
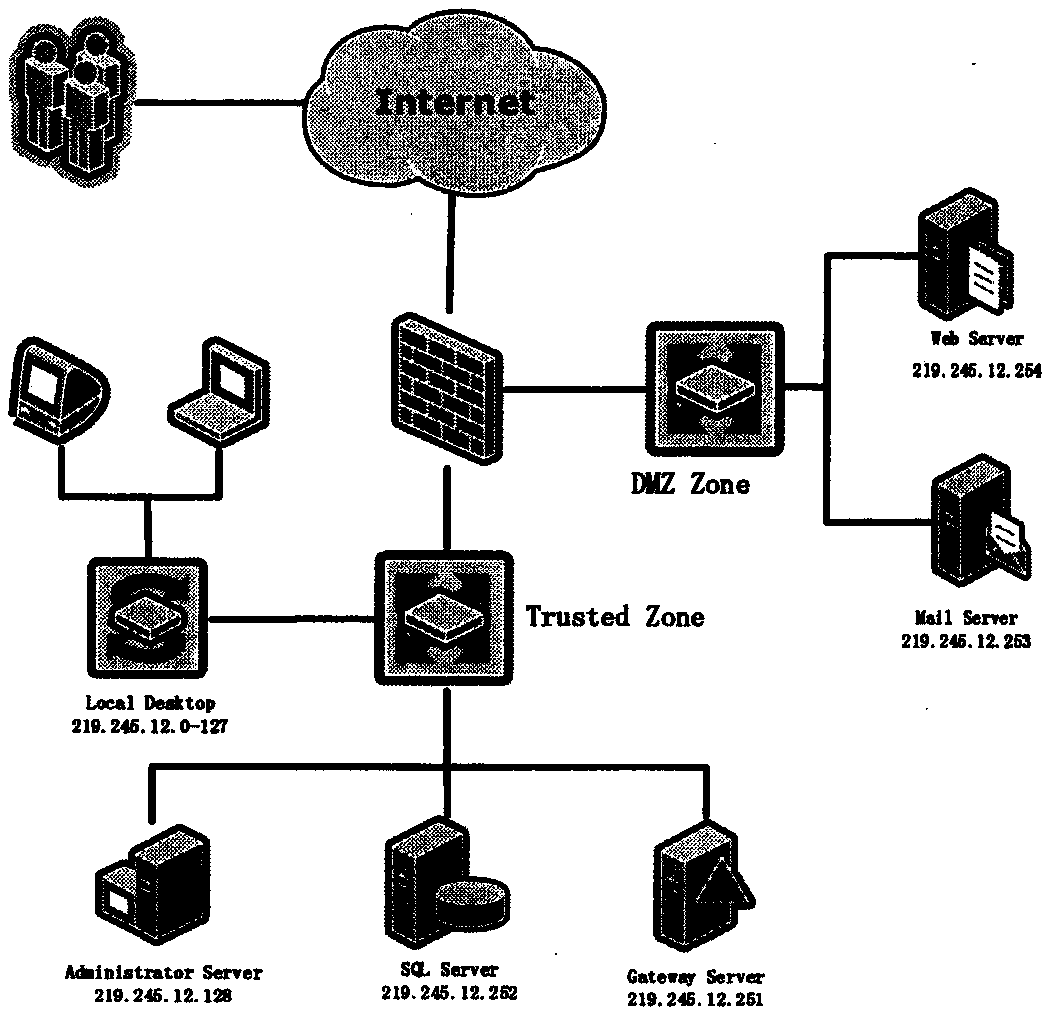
[0055] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, a detailed description will be given below in conjunction with the accompanying drawings and an actual topology example.
[0056] The steps of the defense strategy generation method based on the tripartite dynamic game are as follows:
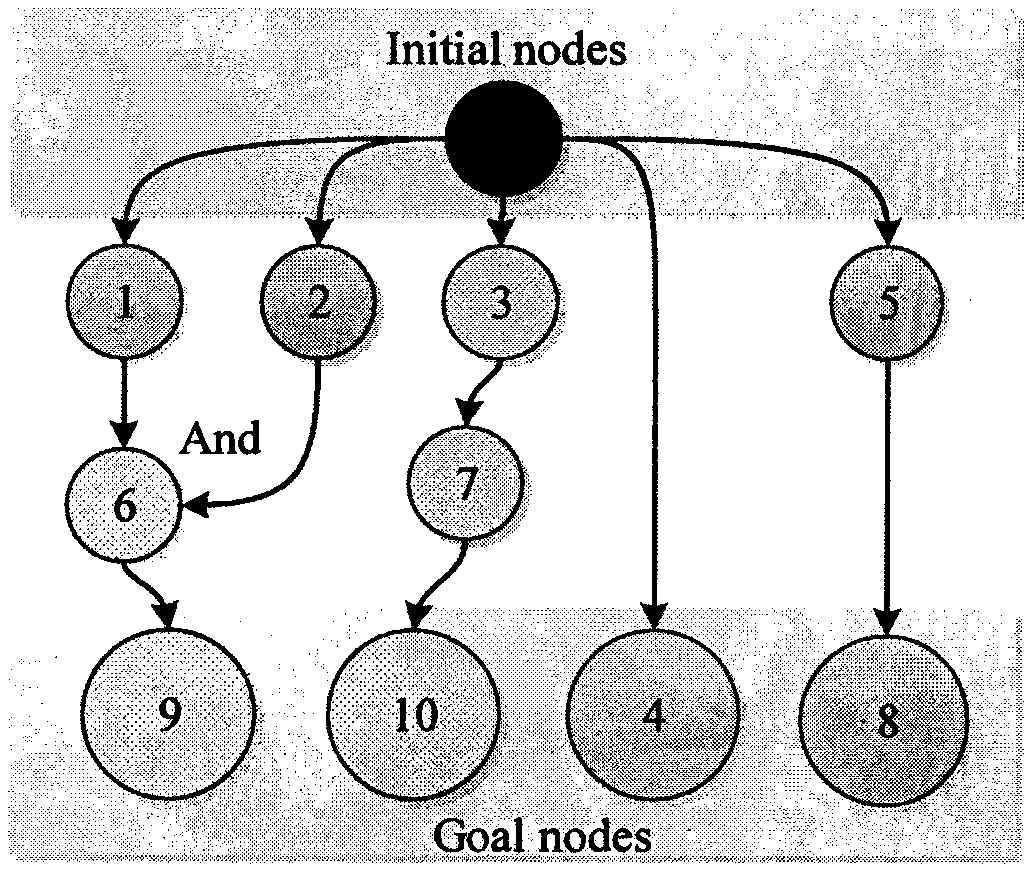
[0057] S1. Build the attack graph. Construct the vulnerability relationship in the entire topology structure as an attack graph through the real network topology structure;
[0058] S2. Construct the state space and behavior constraint space of the dynamic tripartite game;
[0059] S3. Use the balanced value propagation algorithm to quantify the attack graph n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com