Method for discovering illegally-accessed equipment
A technology of illegal access and equipment, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problems of heavy maintenance workload, unsatisfactory effect, complicated operation settings, etc., and achieve remarkable results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
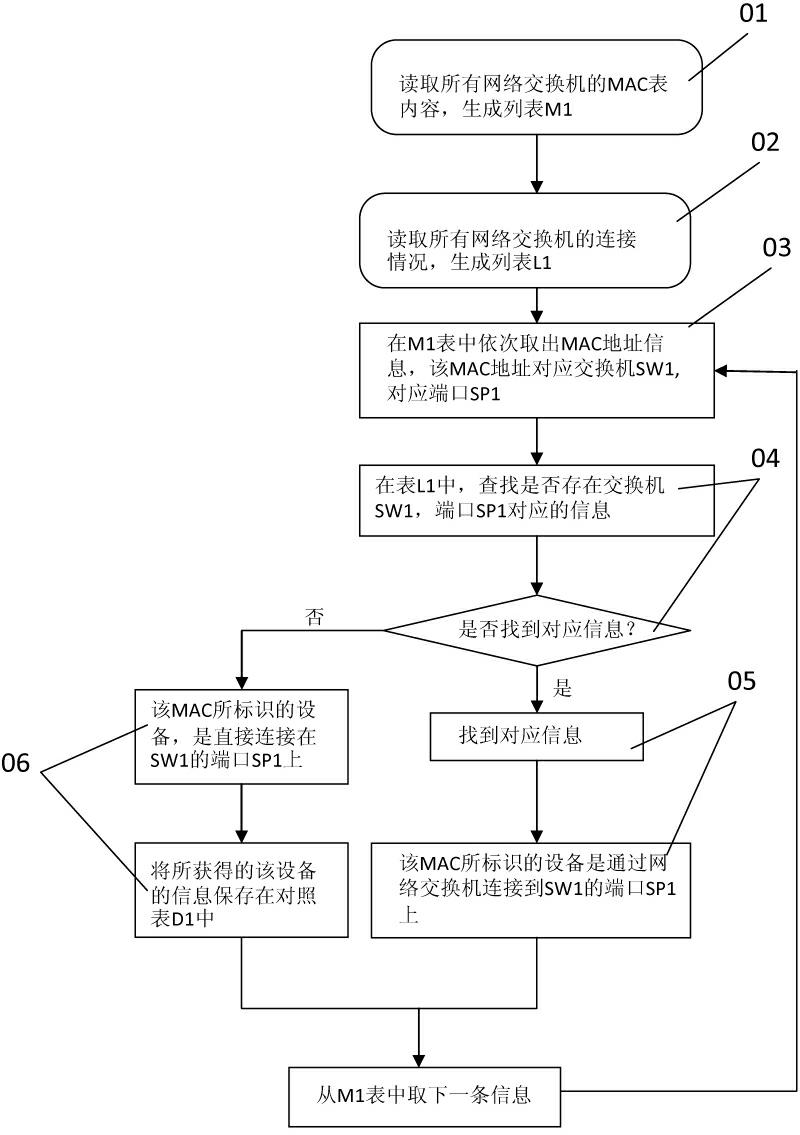
[0032] As above-mentioned concrete method step of the inventive method is:
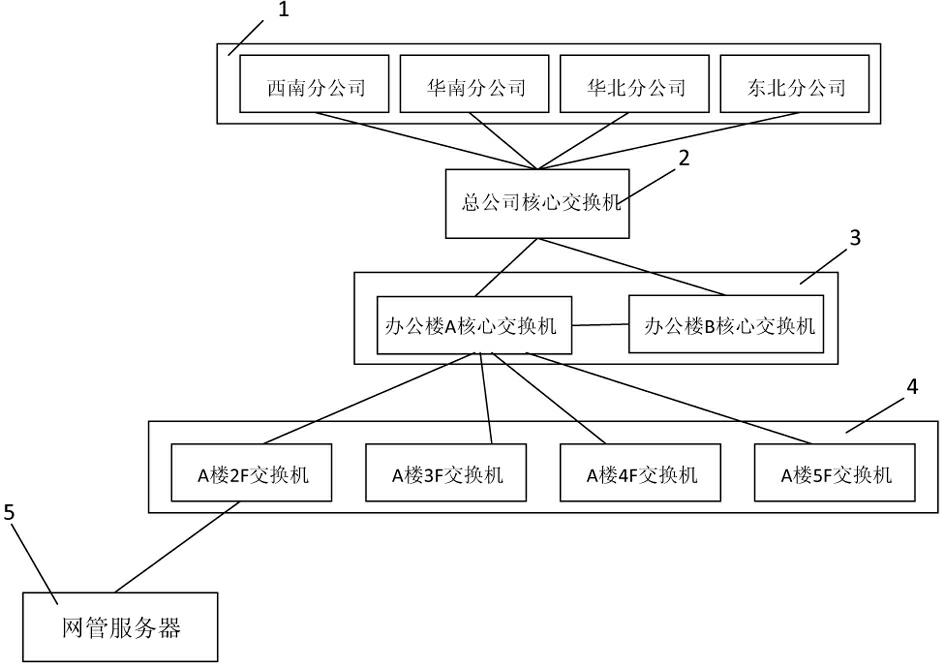
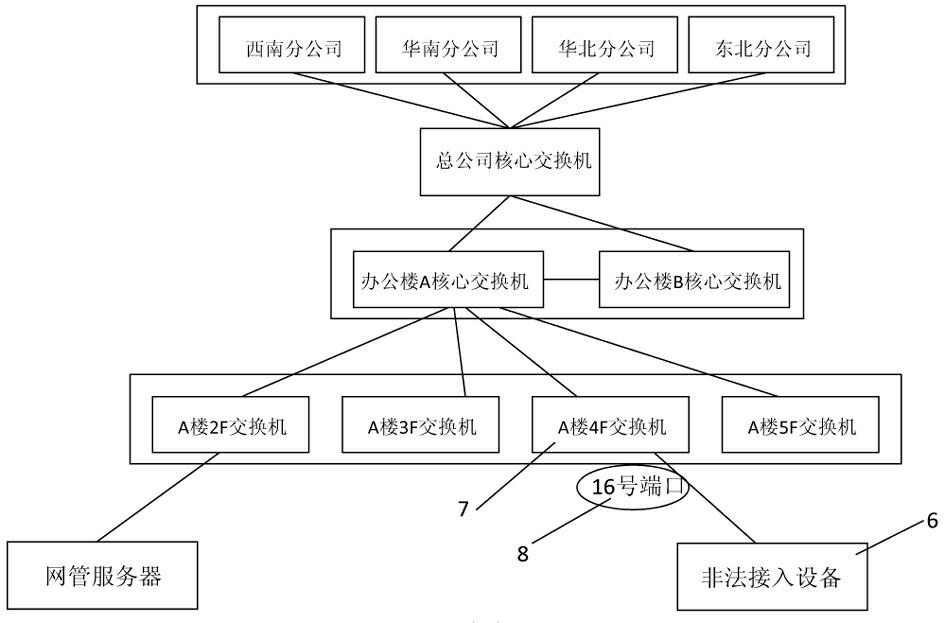
[0033] The first step is to use the physical topology map of the network management software to place all the network management servers, core switches and switches connected to each PC client in the local area network (or internal network) under its jurisdiction on the physical topology map. And show their relative positions and interconnection lines between them on the physical topology map. In this embodiment, the physical topology map is a physical topology map in BTNM3.6 network management software (hereinafter referred to as network management software) provided by Shanghai Beita Software Co., Ltd. The distribution of the company's internal network (local area network) equipment is shown on the physical topology map. like figure 1 As shown, including the core switch 2 of the head office as the core switch, the core switch 3 of the office building connected to the core switch 2 of the head offi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com