Mobile phone privacy protection method
A mobile phone and privacy technology, which is applied in computer components, computer security devices, digital data authentication, etc., can solve problems such as threats to private information, and achieve the effect of strong confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
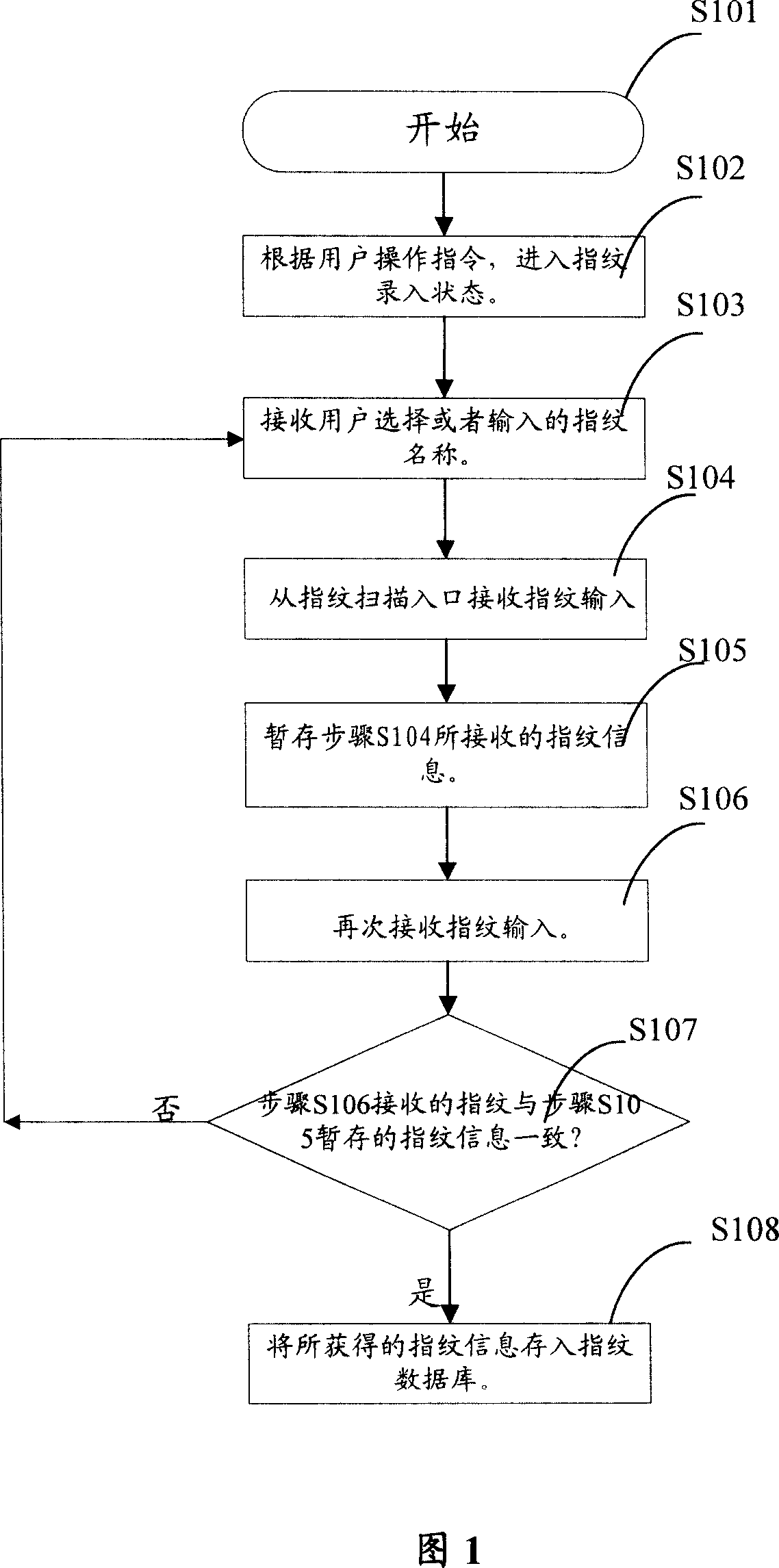
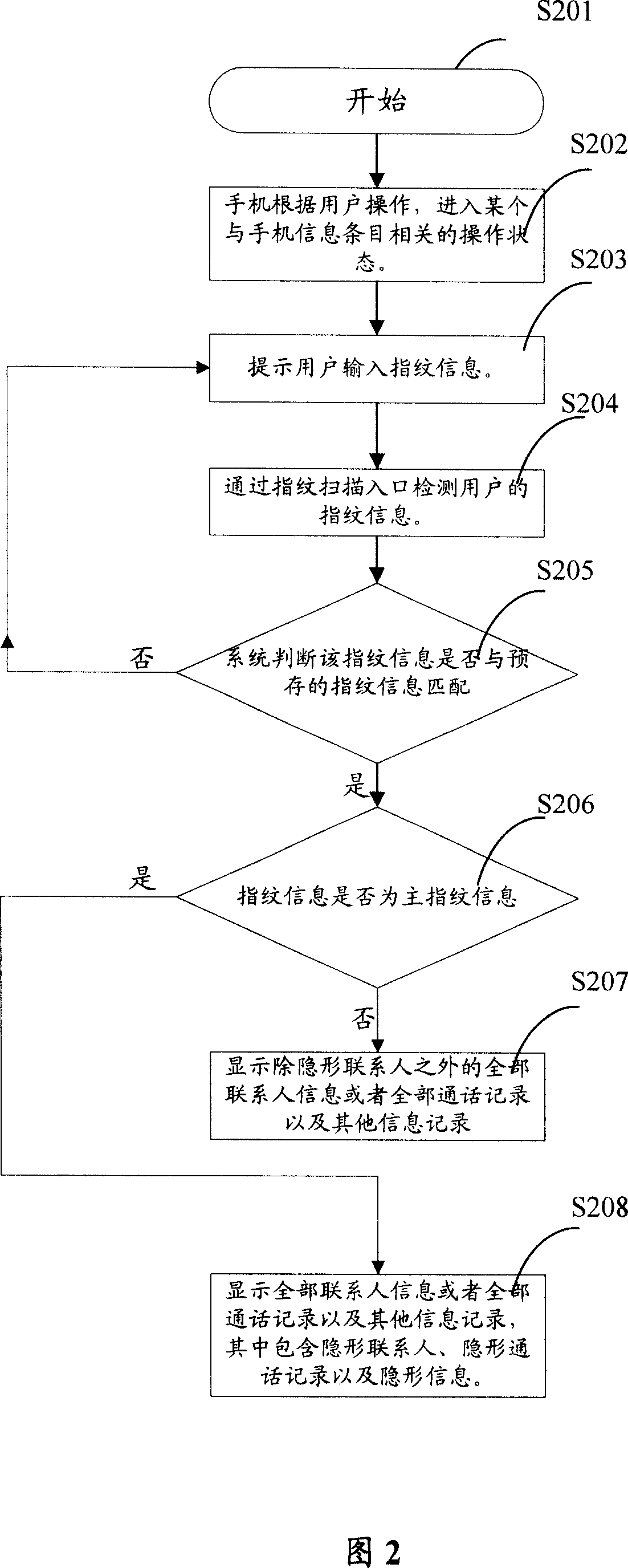
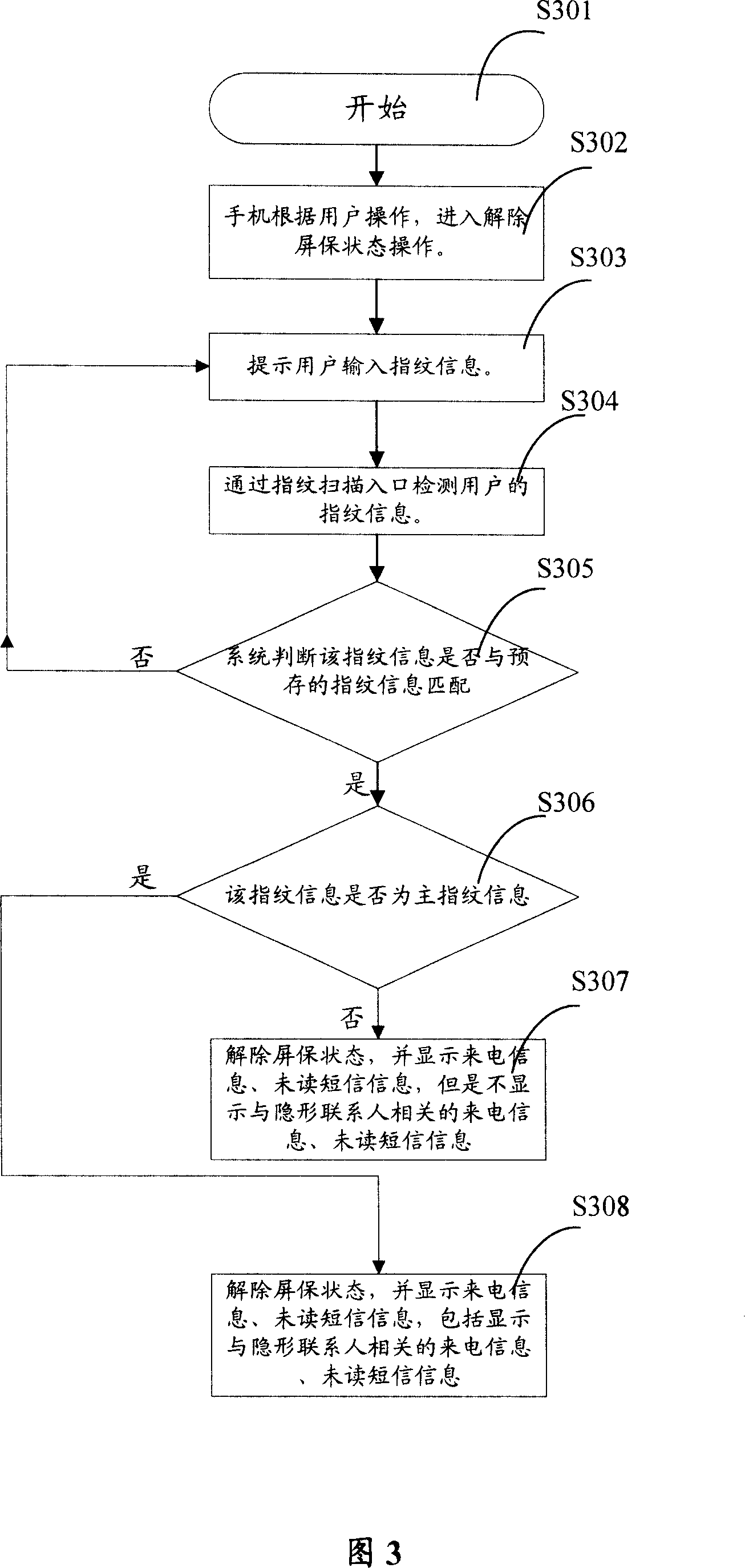
[0048] The following embodiments provide several specific implementation methods of using fingerprint information to realize information privacy protection in mobile phones.
[0049] It should be noted that in the prior art, there are already several technical solutions for using fingerprint recognition technology for personal computer privacy protection. The combination of fingerprint recognition instrument and mobile phone also has some prior art. For example, application number is 02287719 Chinese patent application, discloses a kind of mobile phone with fingerprint key, has provided the concrete mode of fingerprint sensor and mobile phone connection in this patent application. At present, there are many devices such as fingerprint sensors, which can be conveniently combined with mobile phones, so that mobile phones can receive and store fingerprint information, and even compare fingerprint information. The methods provided in the following embodiments are based on the fac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com