Method for landing by account number cipher for protecting network application sequence
A network application program and account technology, applied in the direction of user identity/authority verification, etc., can solve the problems of increasing network burden, unable to prevent virus and Trojan horse stealing behavior, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
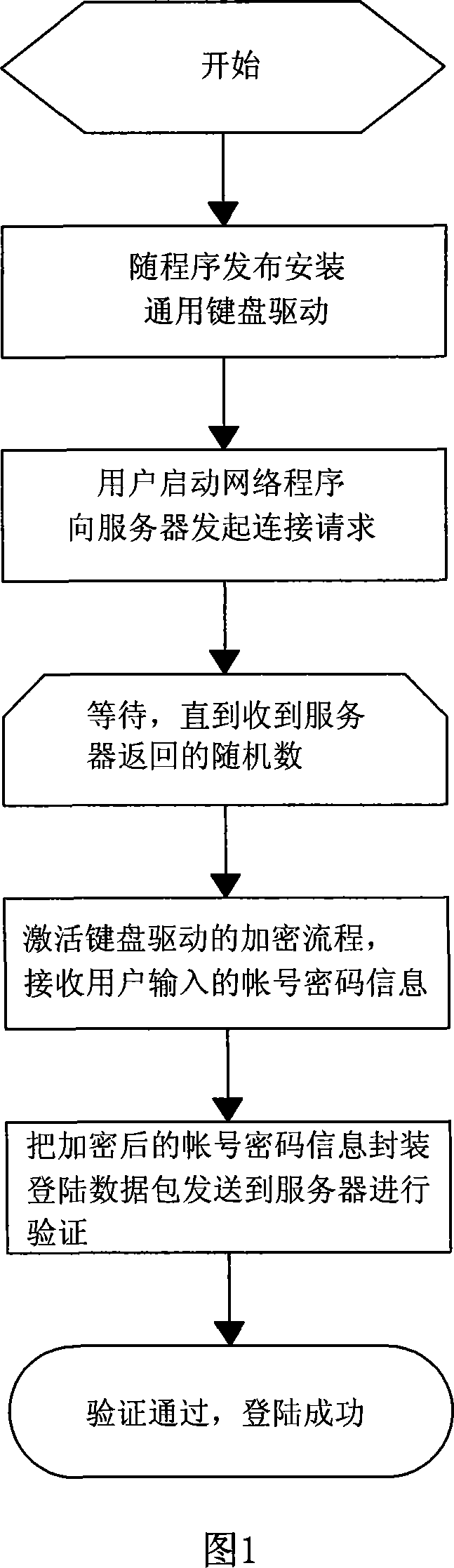
[0020] A method for protecting network applications using account passwords to log in. The client password is input, and then the server-side authentication is used to log in. The client is provided with a universal keyboard driver, and the keyboard driver is preset with an encrypted private key and Private key encryption module; at the same time, the server is also provided with an encryption private key and encryption module, which are consistent with the private key and private key encryption module used by the client.
[0021] The specific steps of use are as follows:
[0022] A. The client initiates a connection request to the server, the server generates a random number after receiving the connection request, the server keeps a record of the generated random number, and sends the random number to the client through the network connection;
[0023] B. After receiving and recording the random number returned by the server, the client activates the keyboard driver and accep...
Embodiment 2
[0028] A method for protecting network applications using account passwords to log in. The client activates the encryption function of the keyboard driver through the device driver's interactive interface DeviceIoControl. The key and private key encryption module encrypts the input keyboard code, puts the encrypted keyboard code into the application layer of the operating system, and the client gets the encrypted information of the password entered by the user. The algorithm of the private key encryption module adopts Data Encryption Standard (Data EncryptoinStandard, DES).
Embodiment 3
[0030] A method for protecting a network application program using an account password to log in. A client performs information digest encryption on combined data using an irreversible Safe Hash Algorithm (Safe Hash Algorithm, SHA). The client performs information digest encryption on the combined data of user account and keyboard driver encrypted user password + random number received from the server, and encapsulates the information digest data of SHA (Account) and SHA (Password+RandomWord) into login data package, sent to the server for verification.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com