Automobile key-free control certification method, user terminal, vehicle-mounted device and server
A user terminal and authentication method technology, applied in the field of automotive electronics, which can solve problems such as poor safety and user experience satisfaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
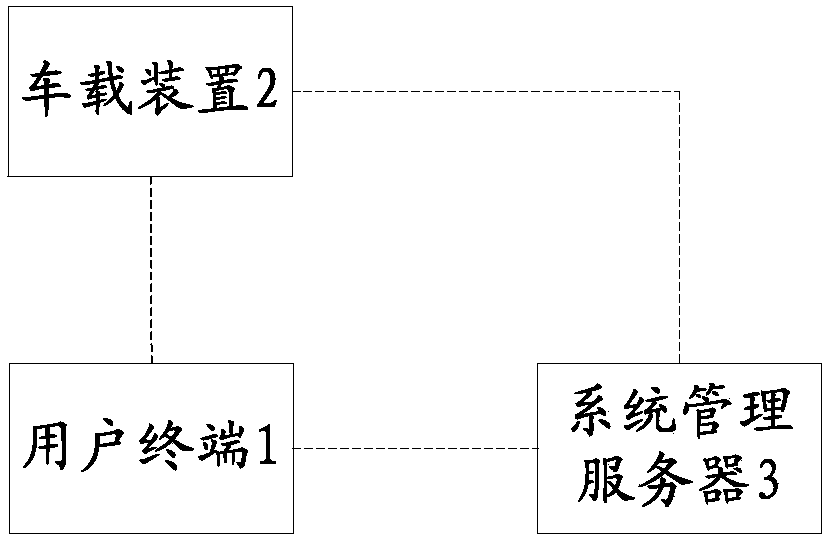
[0116] The car keyless entry system provided by this embodiment can be found in figure 1 As shown, it includes at least a user terminal 1, a vehicle-mounted device 2, and a system management server 3 as a system platform.
[0117] The user terminal 1 in this embodiment may be various smart terminals, such as various smart phones, IPADs, readers, and the like. The user terminal 1 in this embodiment can directly interact with the vehicle-mounted device 2 to complete the control of the keyless entry of the car, or can interact with the vehicle-mounted device 2 through the system management server 3 to complete the control of the keyless entry of the car.
[0118] The user terminal 1 in this embodiment is provided with a smart card, and the smart card has a security chip SE (SecurityElement). The smart card SE in this embodiment can be various types of smart cards with security chips, such as a smart subscriber identification card (Subscriber Identification Module, subscriber ide...
Embodiment 2
[0195] In order to facilitate the understanding of the solutions of the present invention, this embodiment is described in conjunction with an example structure of a user terminal, a vehicle-mounted device, and a system management server.
[0196] see Figure 13 As shown, the user terminal in this embodiment includes a smart card 131, and the smart card includes a security chip for storing a user identity key corresponding to user identification information and performing encryption and decryption processing.
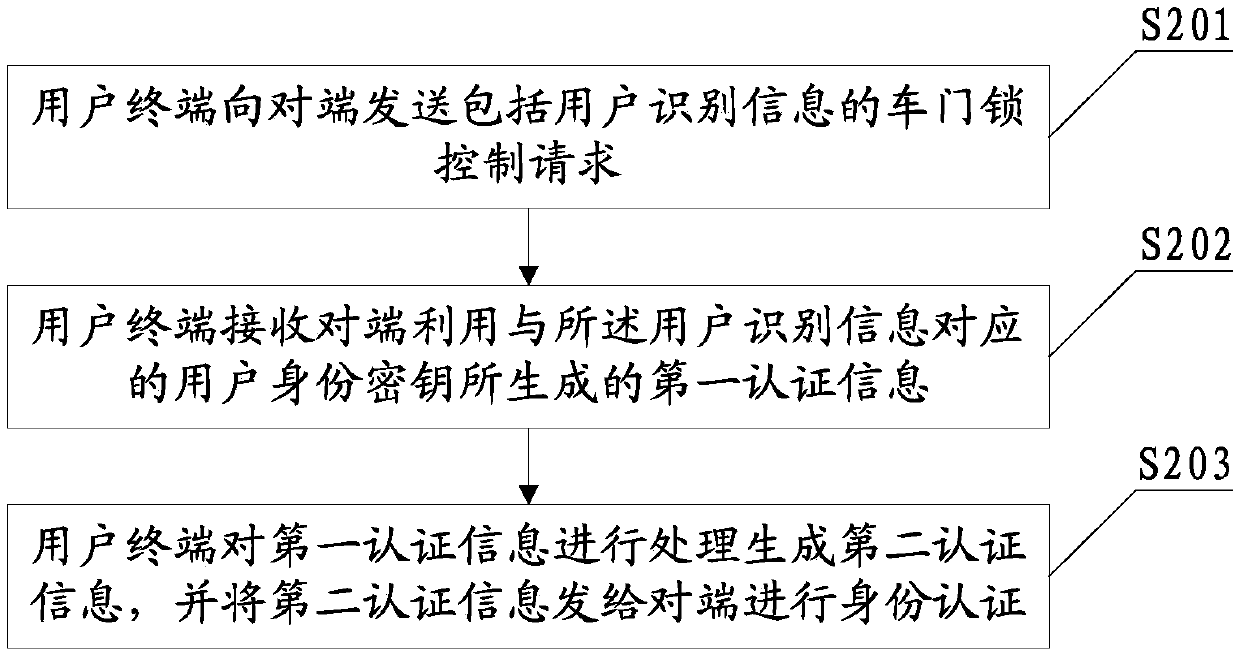
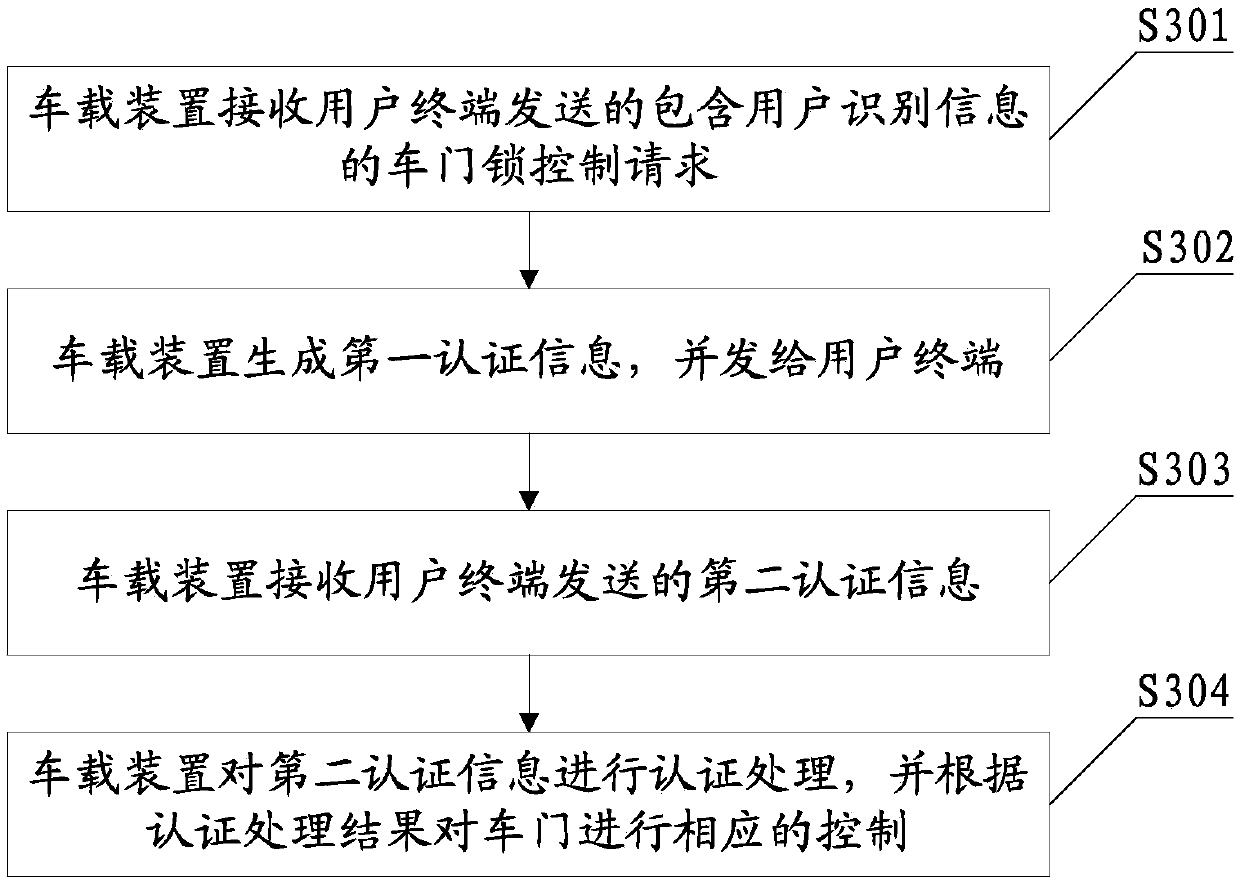
[0197] The smart card 131 is used to send a door lock control request including user identification information to the opposite end, and receive the first authentication information generated by the opposite end using the user identity key corresponding to the user identification information, and use the corresponding user identification information in the security chip. The user identity key processes the first authentication information to generate second authenticati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com