A method and a server for software backend authentication
An authentication server and background authentication technology, which is applied in the field of MAC address authentication technology, can solve problems such as disregarding the production situation of hardware manufacturers, difficulty in agreeing, high authorization fees, etc., to achieve a good cooperation atmosphere, eliminate speculation, and eliminate damage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
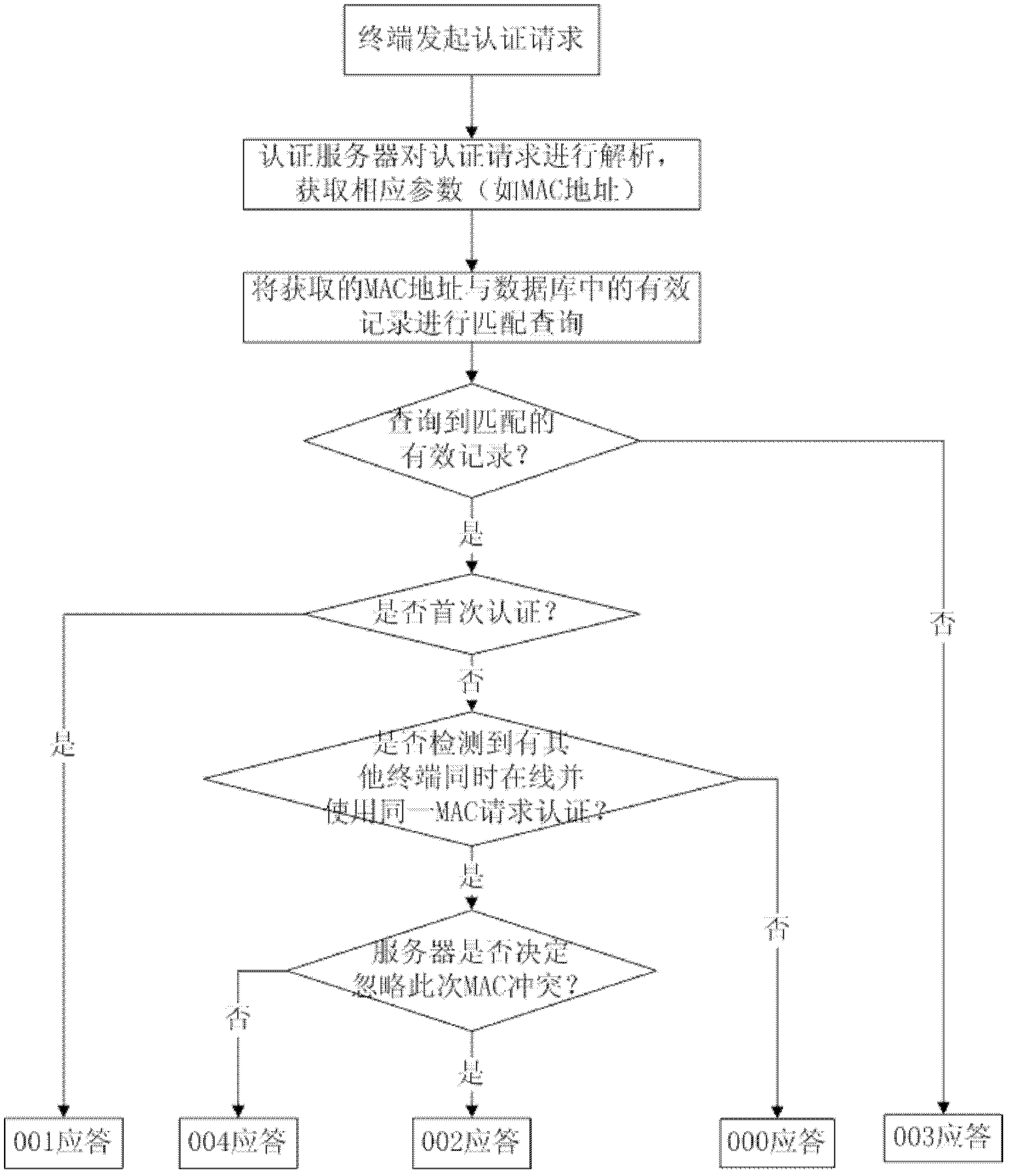
[0052] In this example, the software manufacturer embeds a non-detachable active authentication feature in the terminal software by releasing an upgrade package to the embedded software version previously released to the hardware manufacturer.
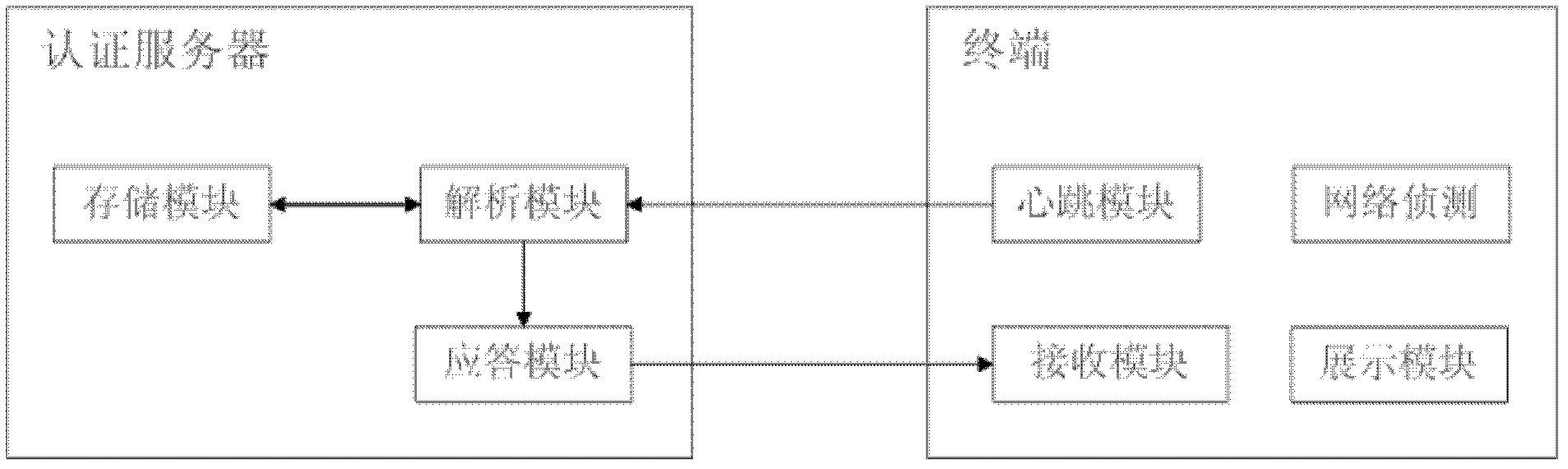
[0053] Please refer to figure 1 , figure 2 As shown, the authentication server in this example is a high-performance server built on the basis of Windows Server operating system, Microsoft SQL Server and . Detection module, heartbeat module, receiving module and display module, etc.
[0054] After the terminal is connected, once its network detection module detects that there is a valid Internet connection, the heartbeat module immediately initiates a heartbeat authentication request, that is, the authentication request is initiated periodically, for example, once every 60 seconds. The GET request of the protocol specification, the request command line contains the following parameters: protocol type, host domain name to be sent to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com