Secure container and design method thereof
A security container and design method technology, applied in the field of information security, can solve problems such as hidden dangers, attacks, failure to completely solve network information security problems, etc., and achieve the effect of ensuring its own security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
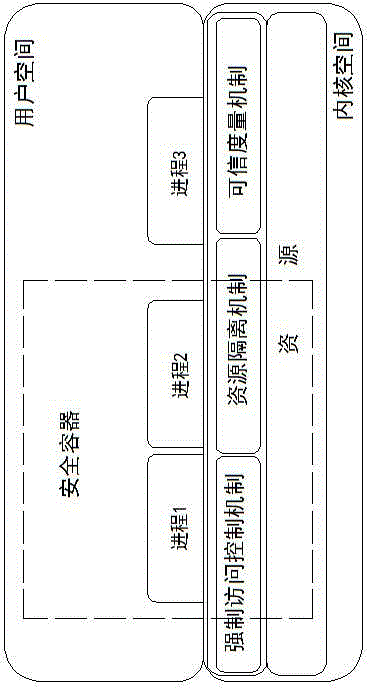
[0035] as attached figure 1 As shown, the security container of the present invention utilizes three mechanisms of mandatory access control, resource isolation and trusted measurement, so that a group of processes can be run in a region, and this group of processes can only perform operations on the resources (CPU, memory, etc.) of the region. Access, cannot access resources outside this area, and processes outside this area cannot access resources in this area, and conduct credible verification of policies in this area and applications in the area, and make different responses according to the verification results , this region forms a secure container.
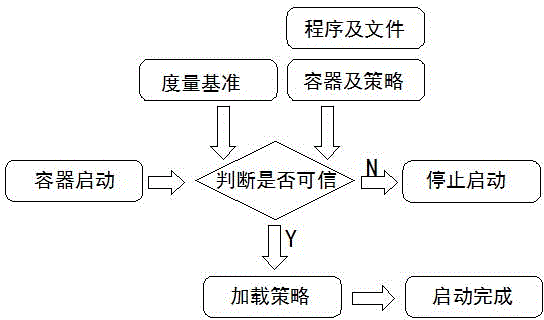
[0036] The security container design framework of the present invention is as attached figure 2 As shown, first add one or more applications to be protected or files to be accessed by programs to the security container, generate a series of policies by configuring the access rights of these programs or files, and specify ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com