Protection of content stored on portable memory from unauthorized usage
a technology for protecting content and portable memory, applied in the protection of unauthorized memory, instruments, computing, etc., can solve the problems of counterfeit devices, inability to fit in the drive, and memory cannot be easily read by any reading device,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
Overview
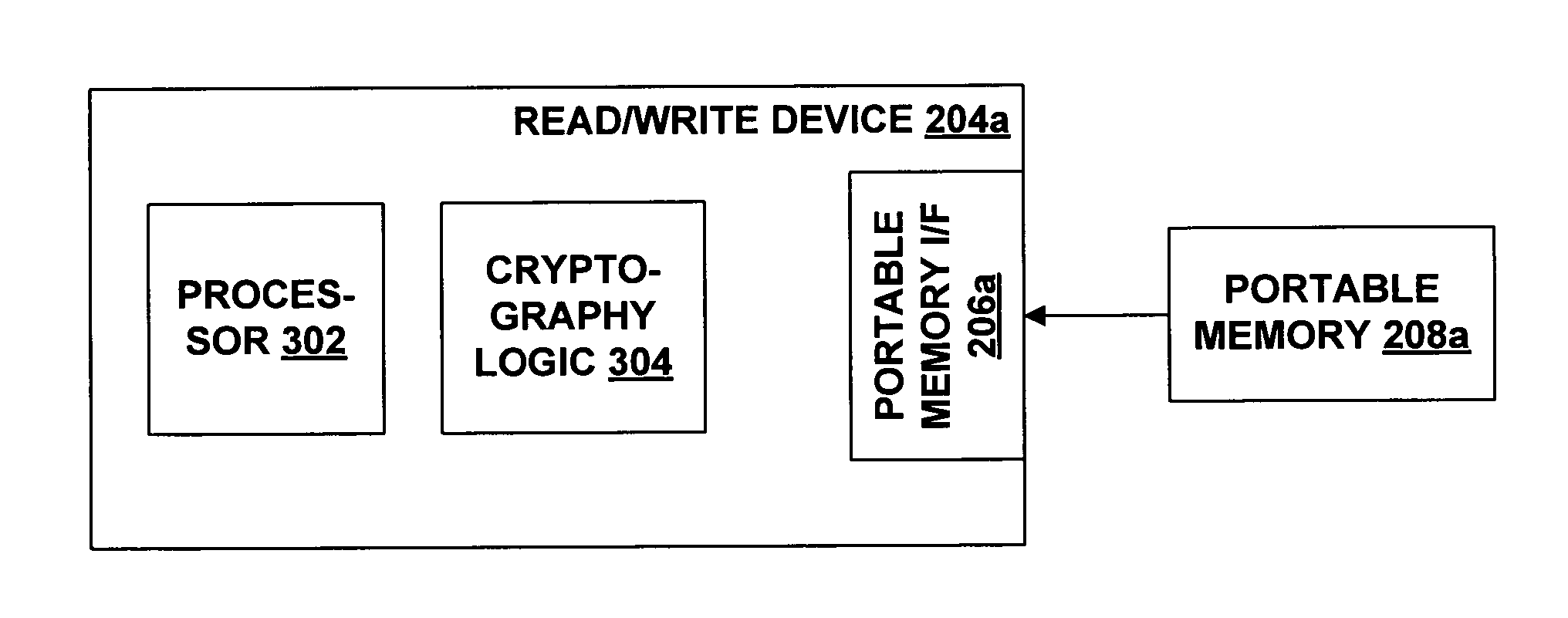
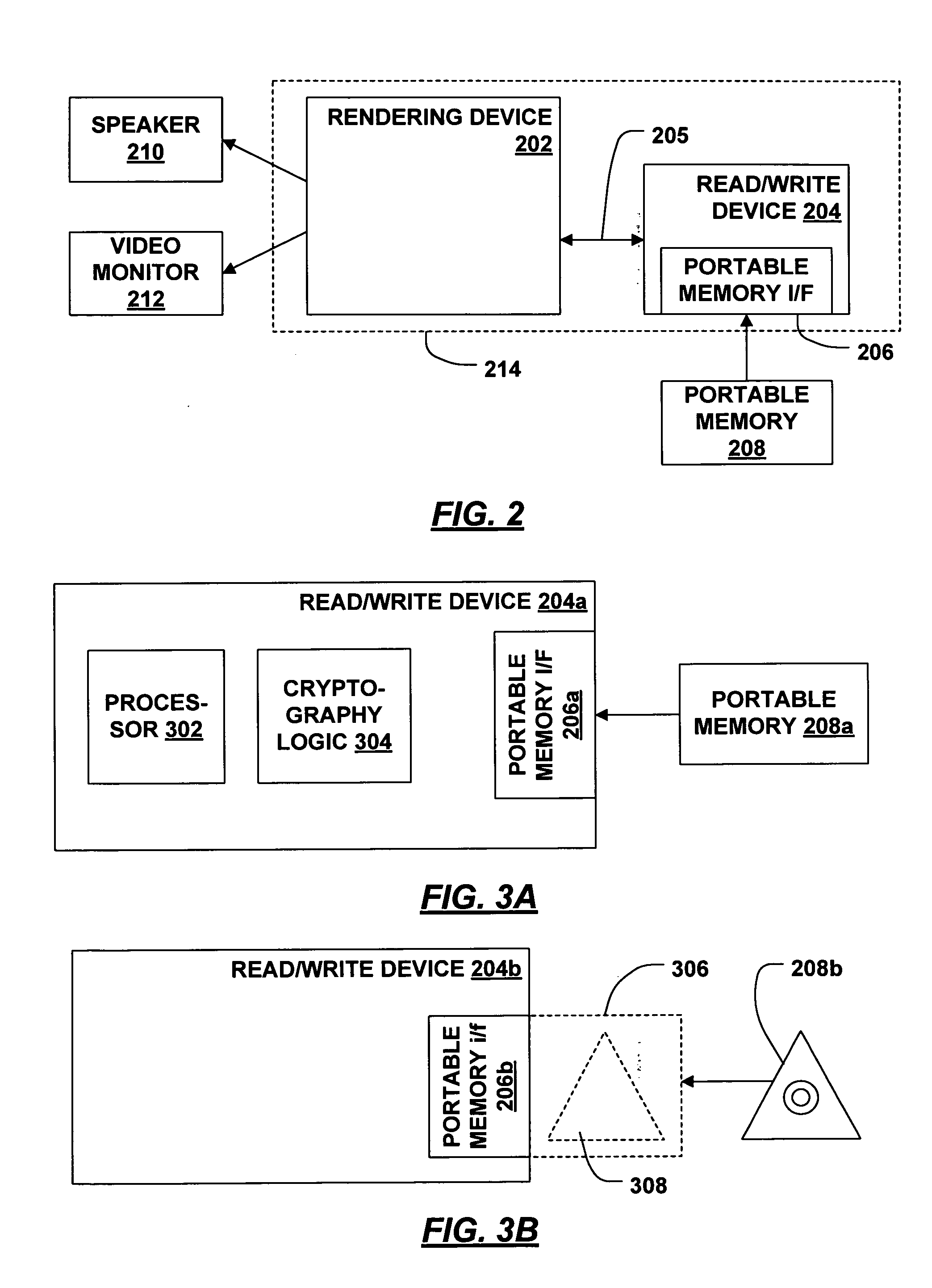
[0023] The invention is directed to the storage on portable memory of data that is subject to usage rules. “Rules,” in this context, means limitations on the usage of the data such as how it can be used (e.g., copying, printing, ephemeral rendering, etc.), when it can be used, and by whom it can be used. For example, a rule may state that a song may be played back on any host device, but that no copies may be made. A rule governing data may be global rule that applies to all data of a certain class. Alternatively, the rule could be described explicitly and stored with the data, or otherwise associated with the data. An explicitly described rule governing usage is sometimes referred to as an “electronic license” or “digital license.” Electronic licenses and protection of data are described in U.S. Pat. No. 5,715,403 entitled “System for Controlling the Distribution and Use of Digital Works Having Attached Usage Rights Where the Usage Rights Are Defined by a Usage Rights Gra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com