Patents
Literature
103 results about "Identifying goals" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
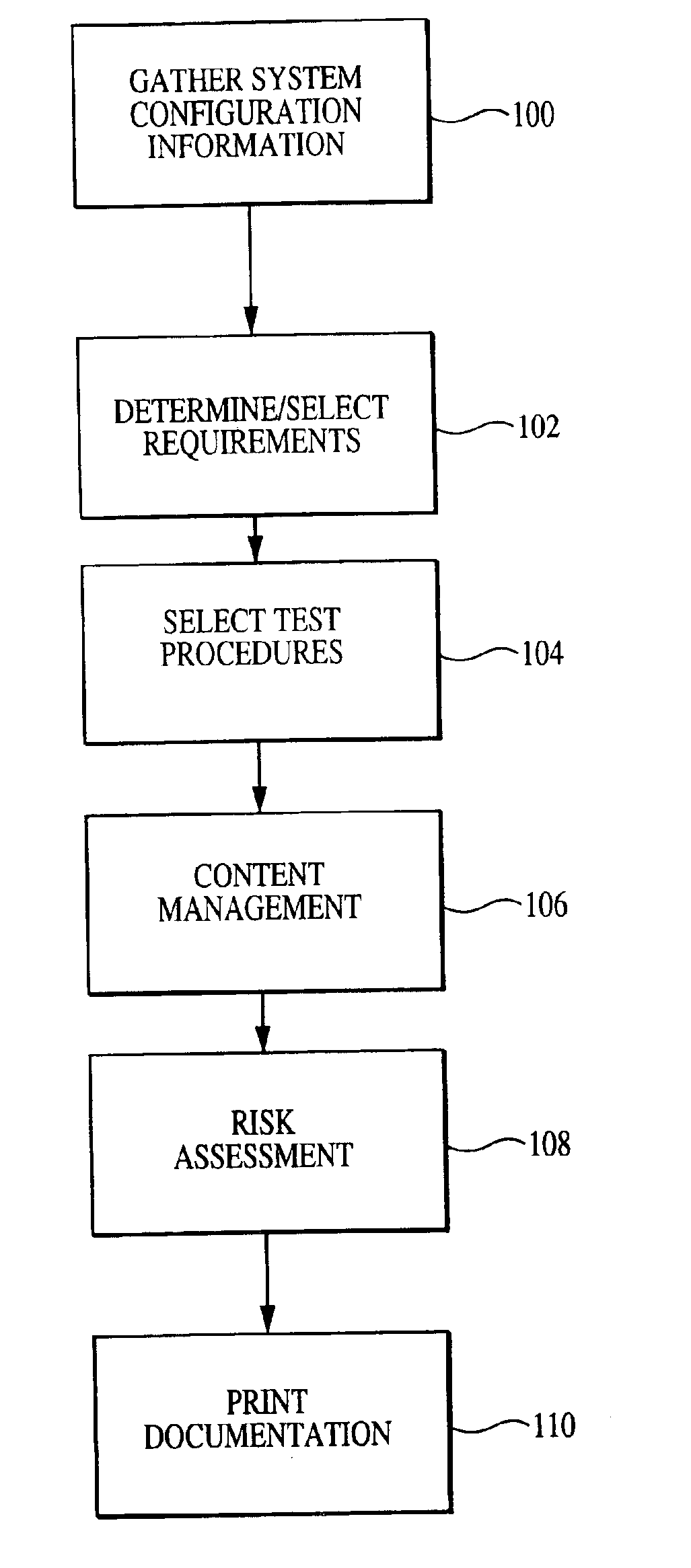
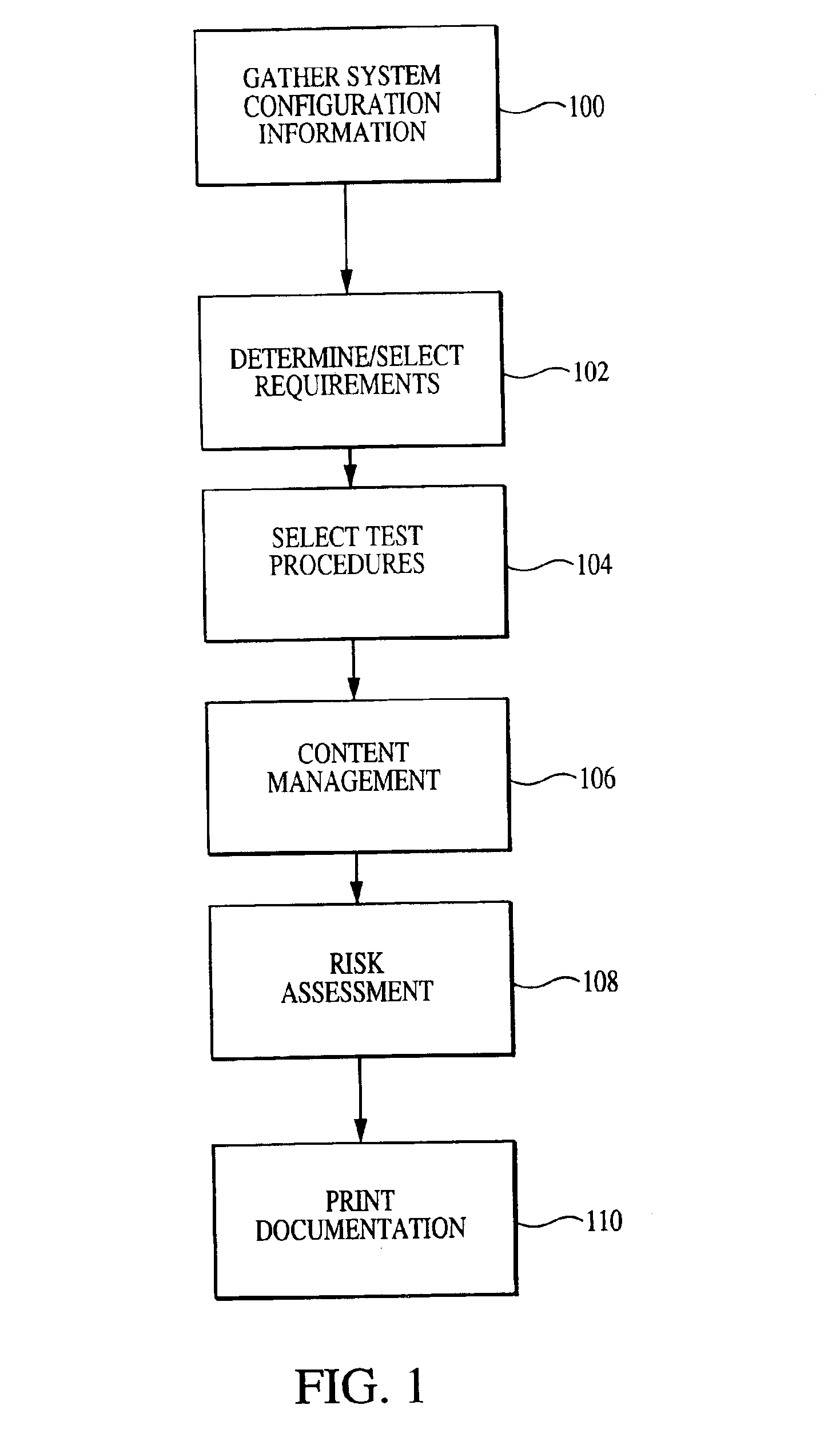
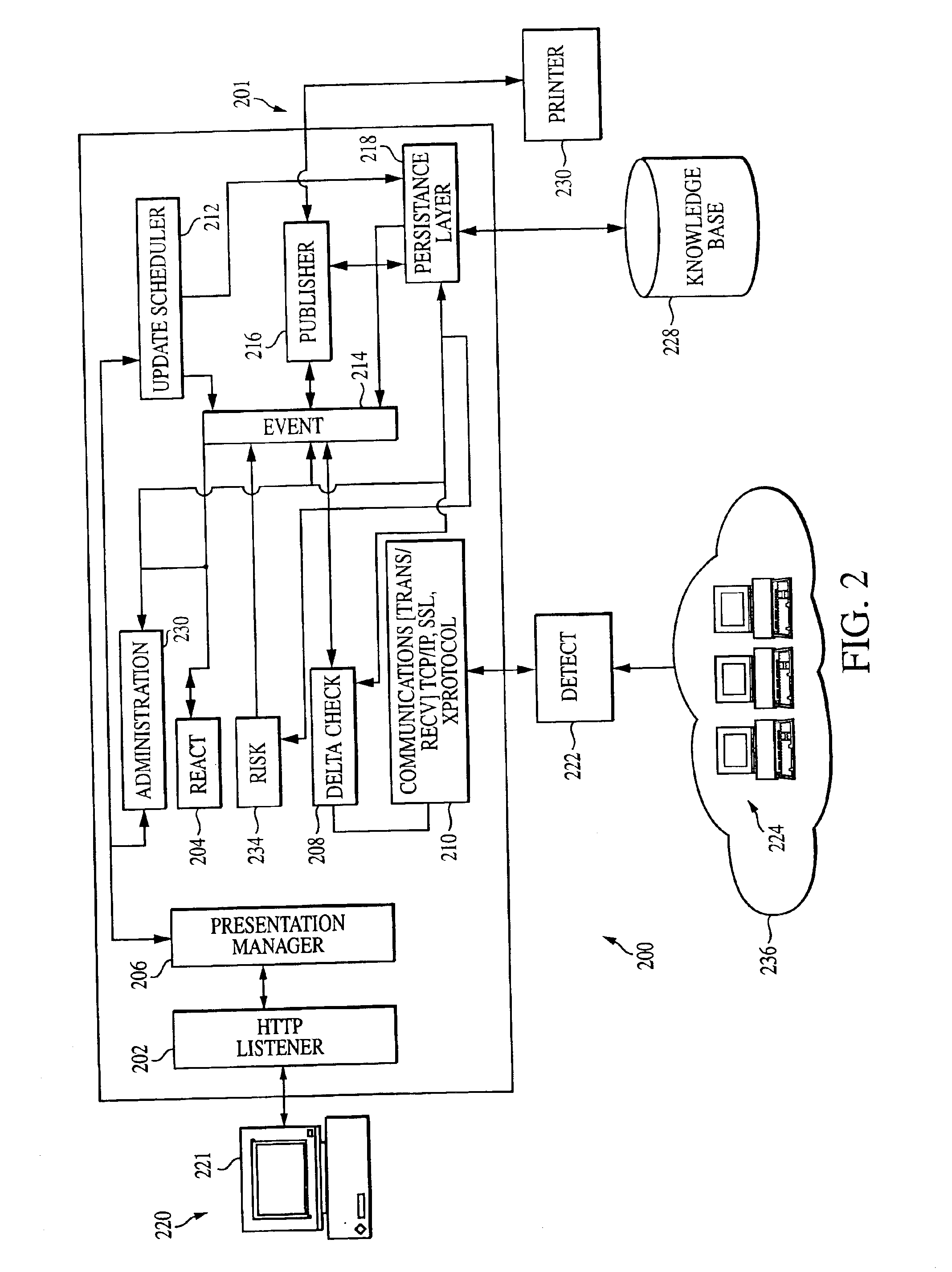
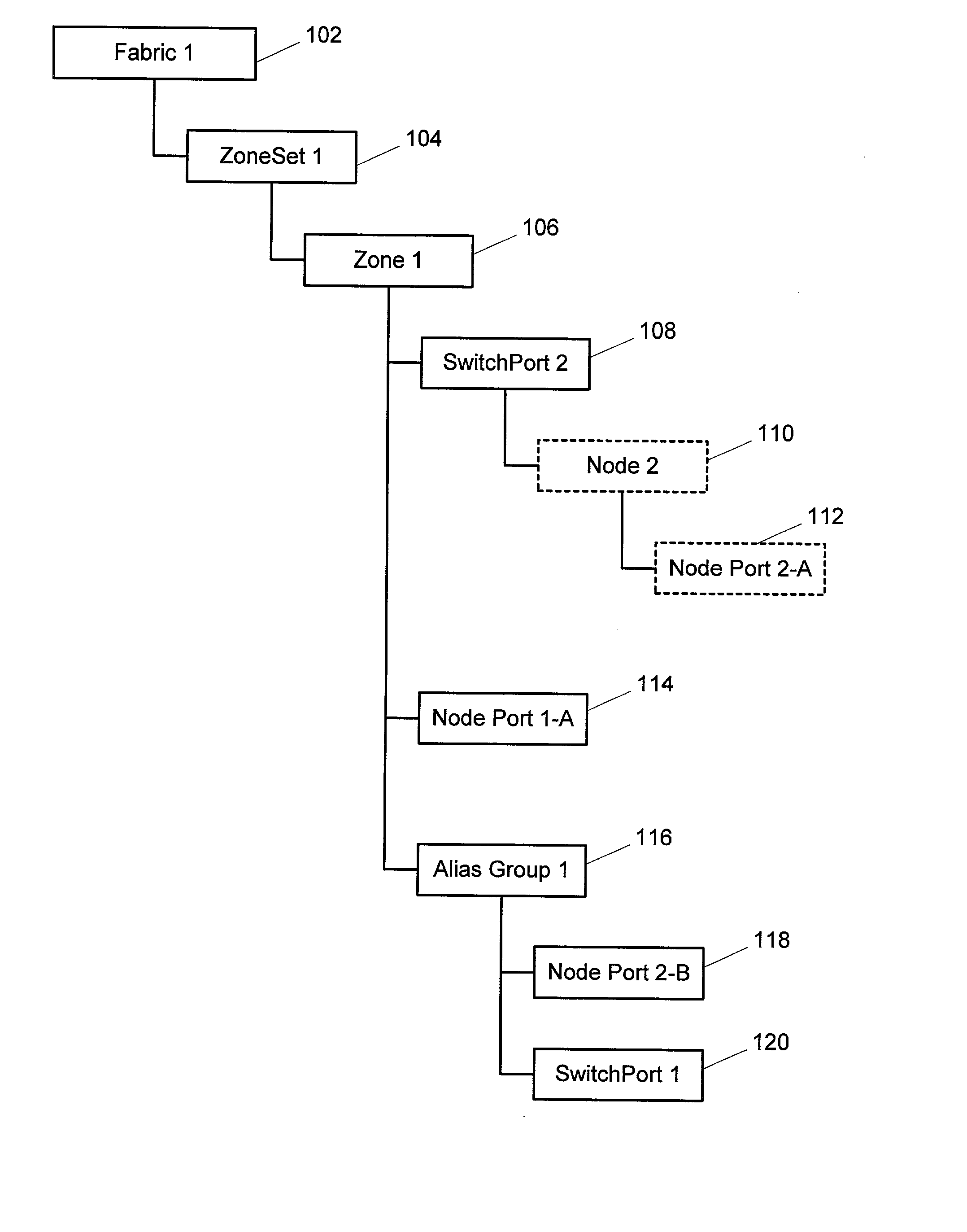
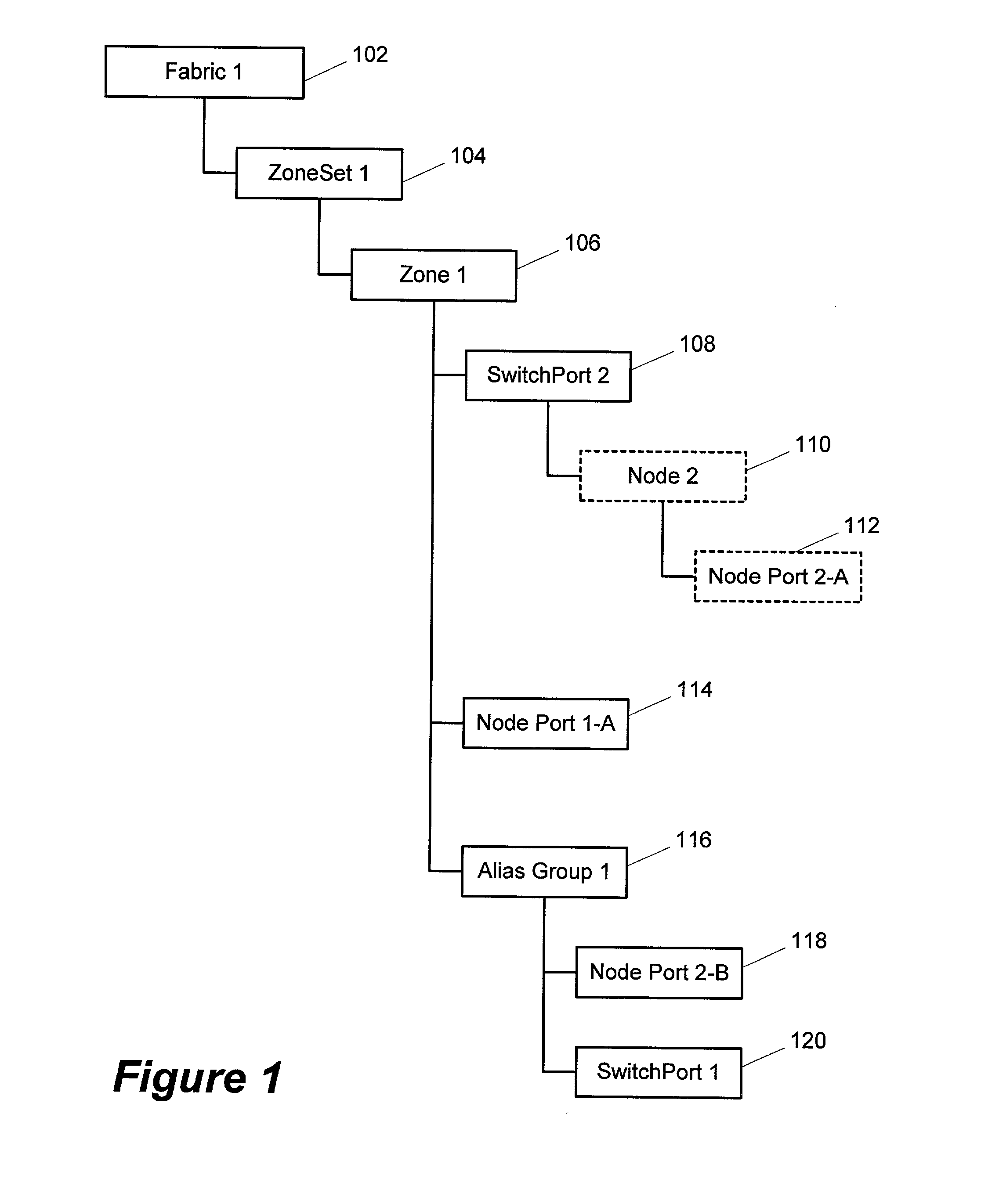
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing continuous risk assessment
InactiveUS6980927B2Enhances and facilitates security risk assessmentsMemory loss protectionError detection/correctionTechnical standardComputer-aided
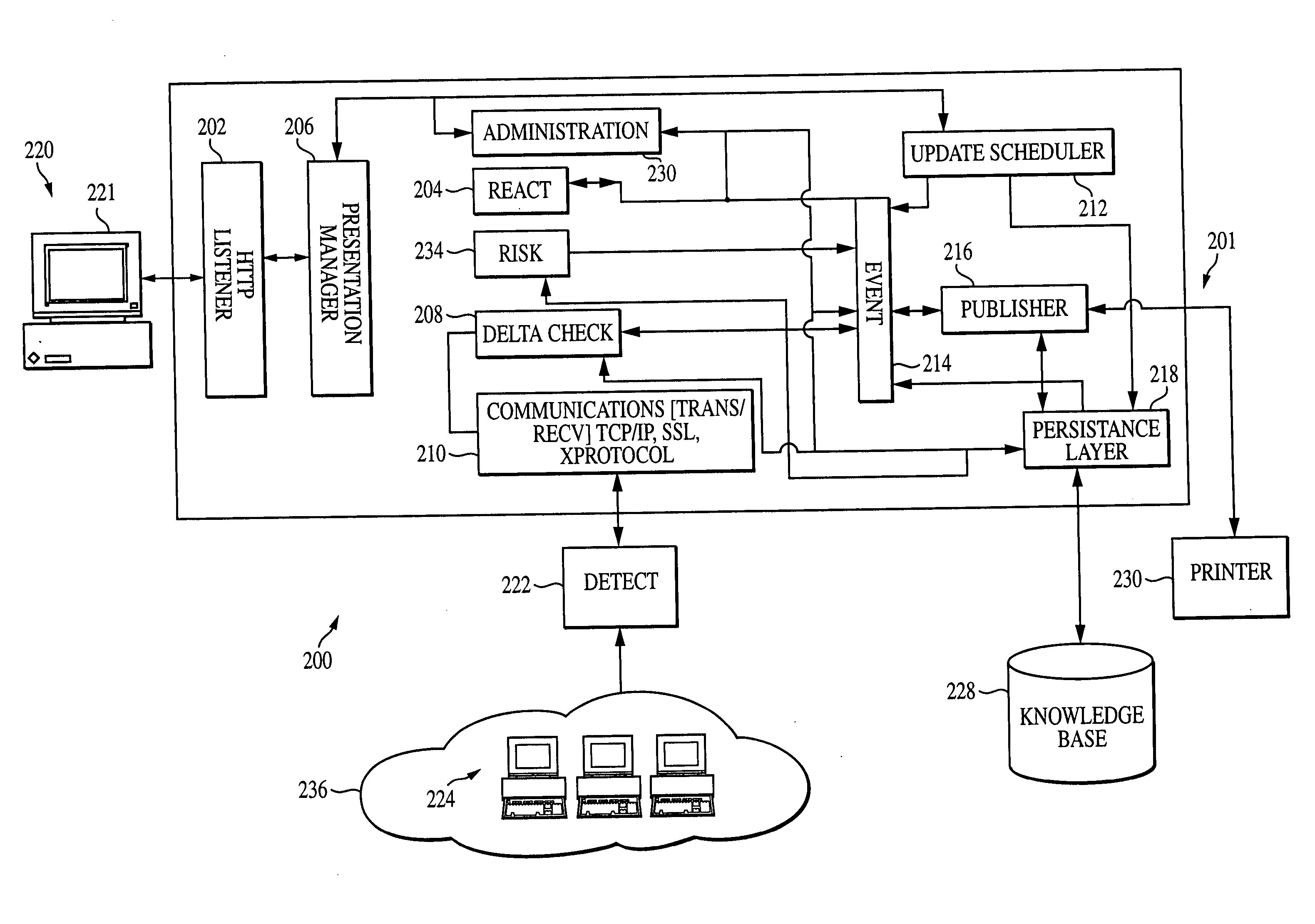
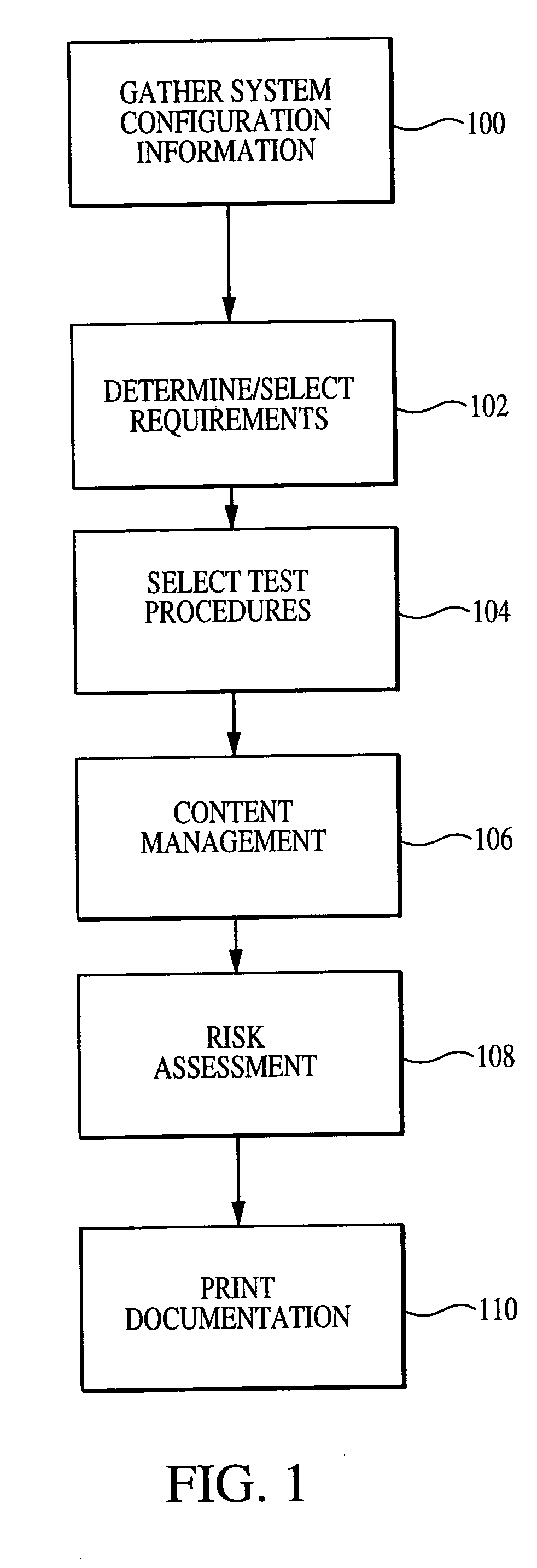
A computer-assisted system, medium and method of providing a risk assessment of a target system. The method includes electronically scanning, on a predetermined basis, hardware and / or software characteristics of components within a target system to obtain and store target system configuration information, receiving and storing target system operational environment information, using information collected in the scanning and receiving steps to select one or more security requirements in accordance with the at least one predefined standard, regulation and / or requirement, selecting one or more test procedures used to determine target system compliance with the security requirements, and producing a risk assessment of the target system.
Owner:TELOS CORP
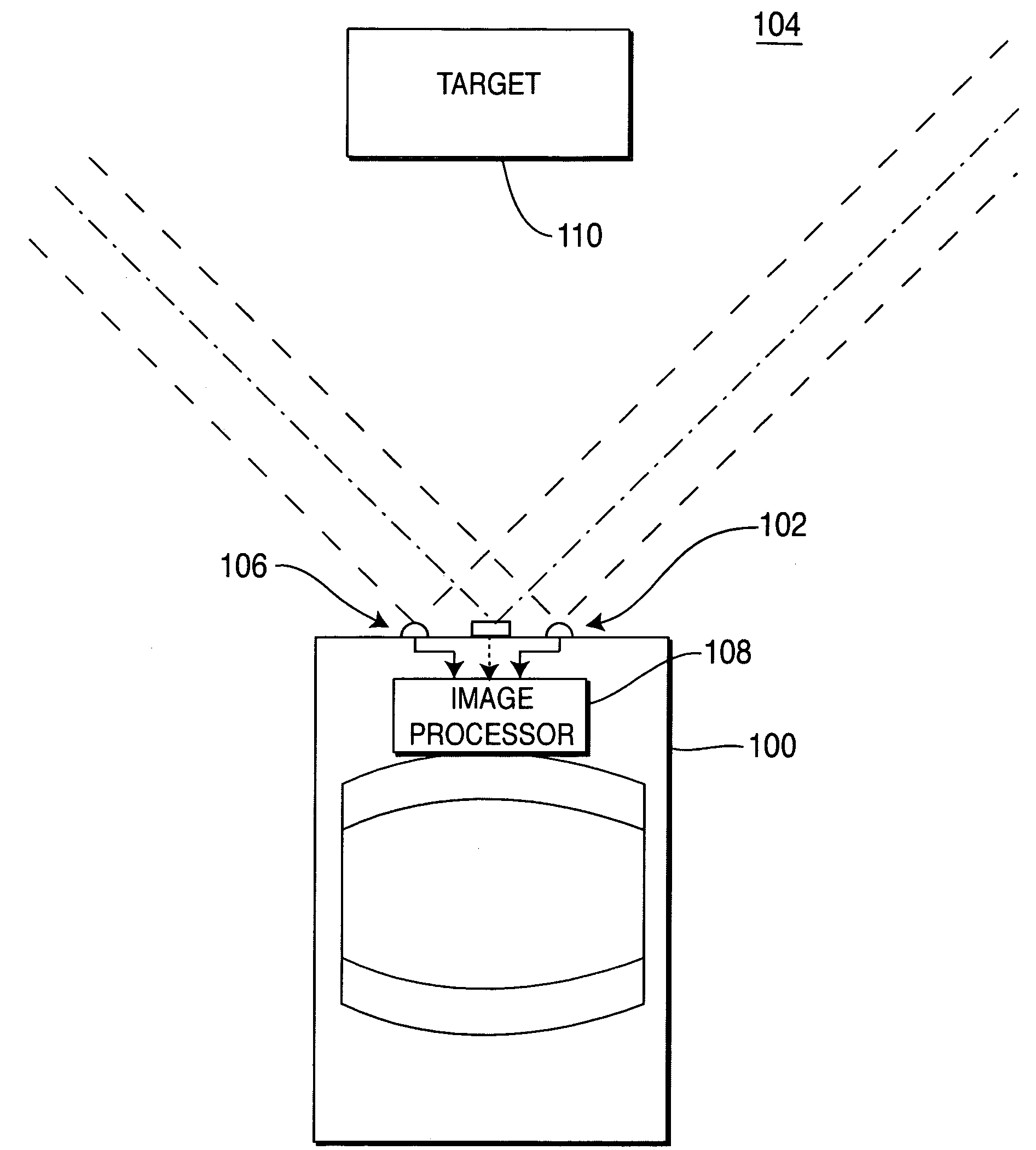
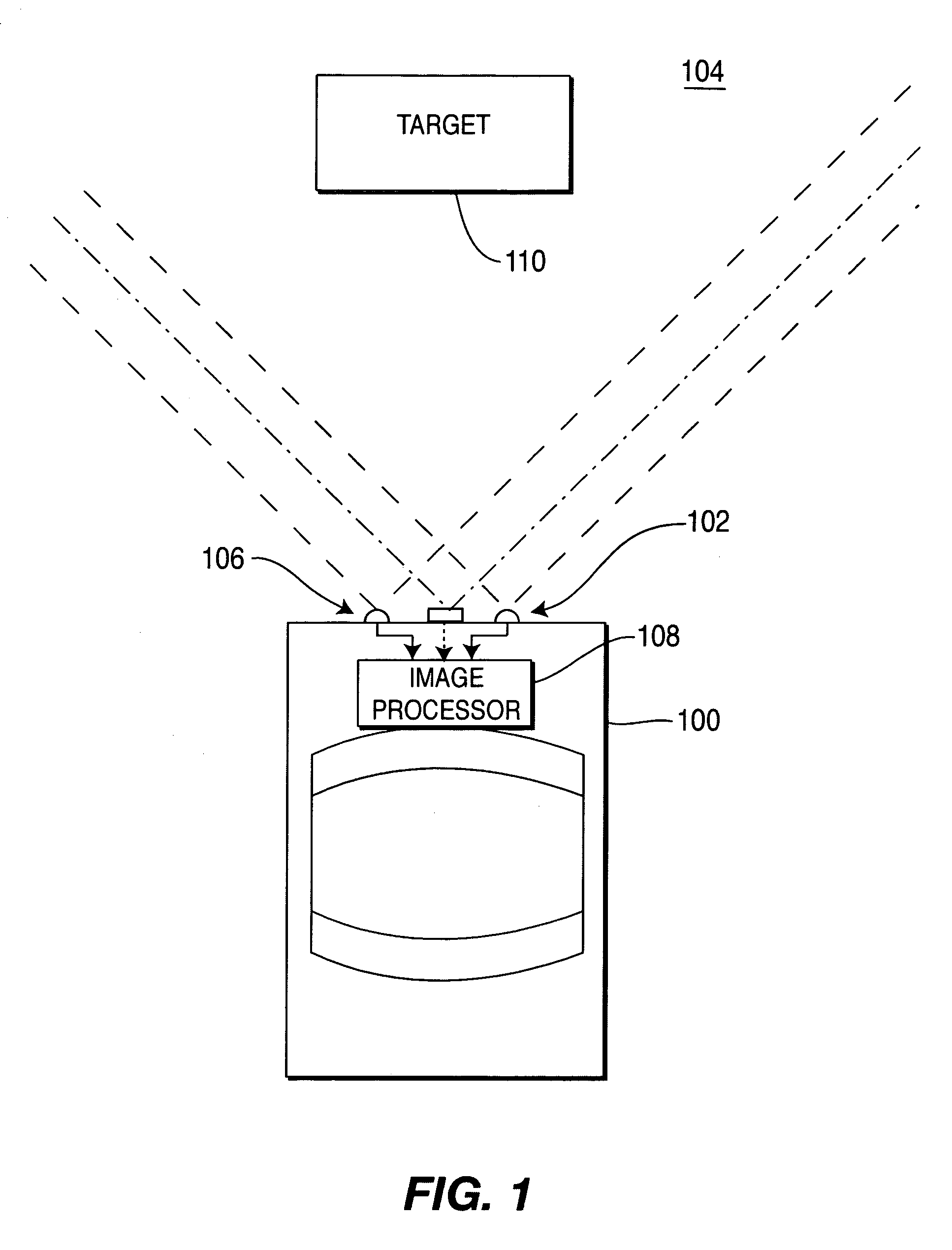
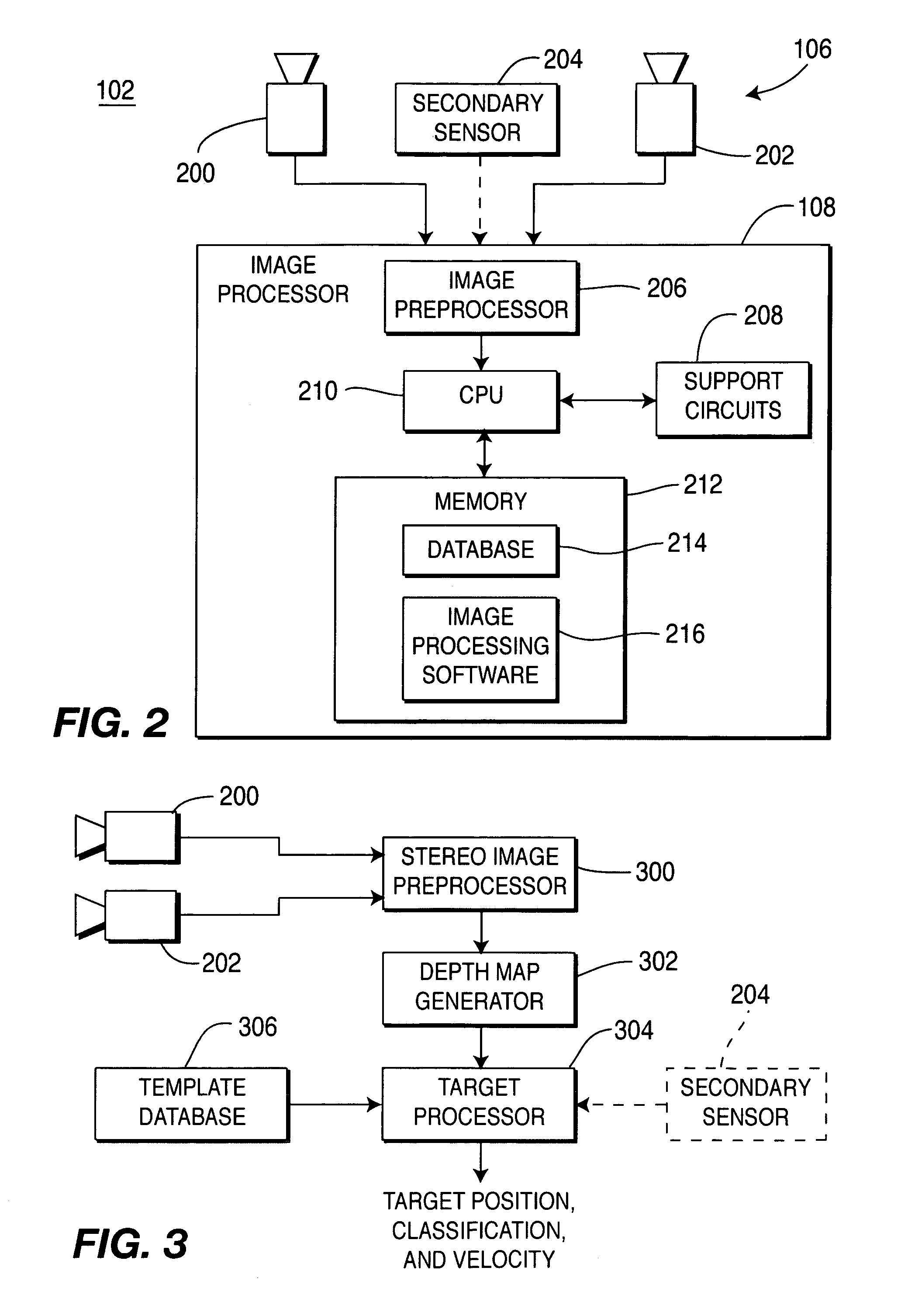
Vehicular vision system
ActiveUS7263209B2Safely avoidedReduce harmImage enhancementImage analysisSensor arrayDriver/operator
A vision system for a vehicle that identifies and classifies objects (targets) located proximate a vehicle. The system comprises a sensor array that produces imagery that is processed to generate depth maps of the scene proximate a vehicle. The depth maps are processed and compared to pre-rendered templates of target objects that could appear proximate the vehicle. A target list is produced by matching the pre-rendered templates to the depth map imagery. The system processes the target list to produce target size and classification estimates. The target is then tracked as it moves near a vehicle and the target position, classification and velocity are determined. This information can be used in a number of ways. For example, the target information may be displayed to the driver, the information may be used for an obstacle avoidance system that adjusts the trajectory or other parameters of the vehicle to safely avoid the obstacle. The orientation and / or configuration of the vehicle may be adapted to mitigate damage resulting from an imminent collision, or the driver may be warned of an impending collision.
Owner:FORD MOTOR CO
Simulation-based functional verification of microcircuit designs
InactiveUS7130783B1Shorten the timeConfidenceDetecting faulty computer hardwareAnalogue computers for electric apparatusTest designFormal methods
System, methods, and apparatus for verifying microcircuit designs by interleaving between random and formal simulation techniques to identify input traces useful for driving designs under test into sequences of device states. In a method aspect the invention provides process for beginning random simulation of a sequence of states of a microcircuit design by inputting a sequence of random input vectors to a design under test model in order to obtain a sequence of random simulation states; monitoring a simulation coverage progress metric to determine a preference for switching from random simulation to formal methods of simulating states in the design under test; beginning formal simulation of states in the design under test and monitoring a formal coverage progress metric to determine a preference for resuming random simulation of states of said microcircuit design; and resuming random simulation. Preferably the process of interleaving simulation methods continues until an input vector suitable for driving the design under test model into each of a set of previously-identified goal states has been obtained.
Owner:SYNOPSYS INC
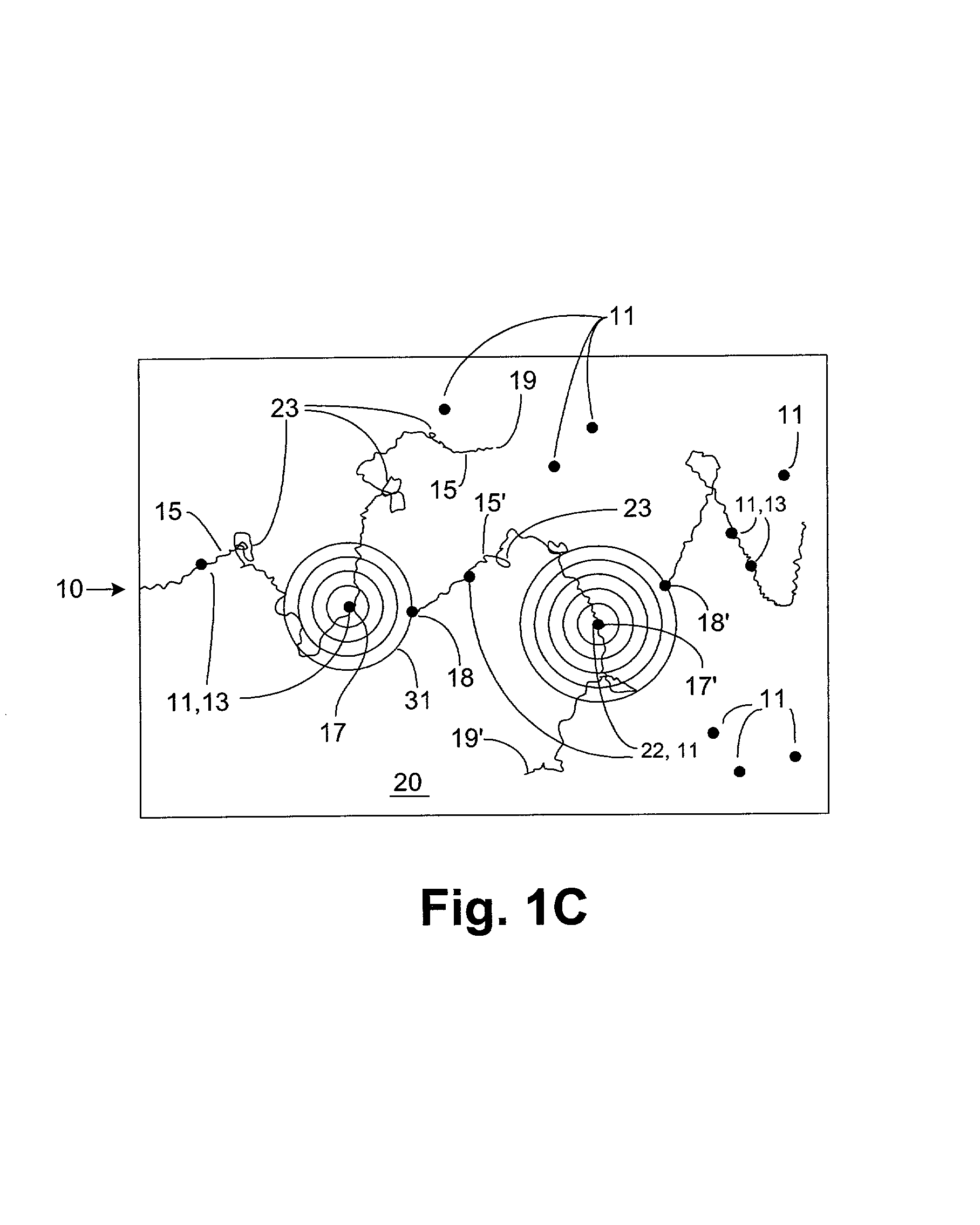
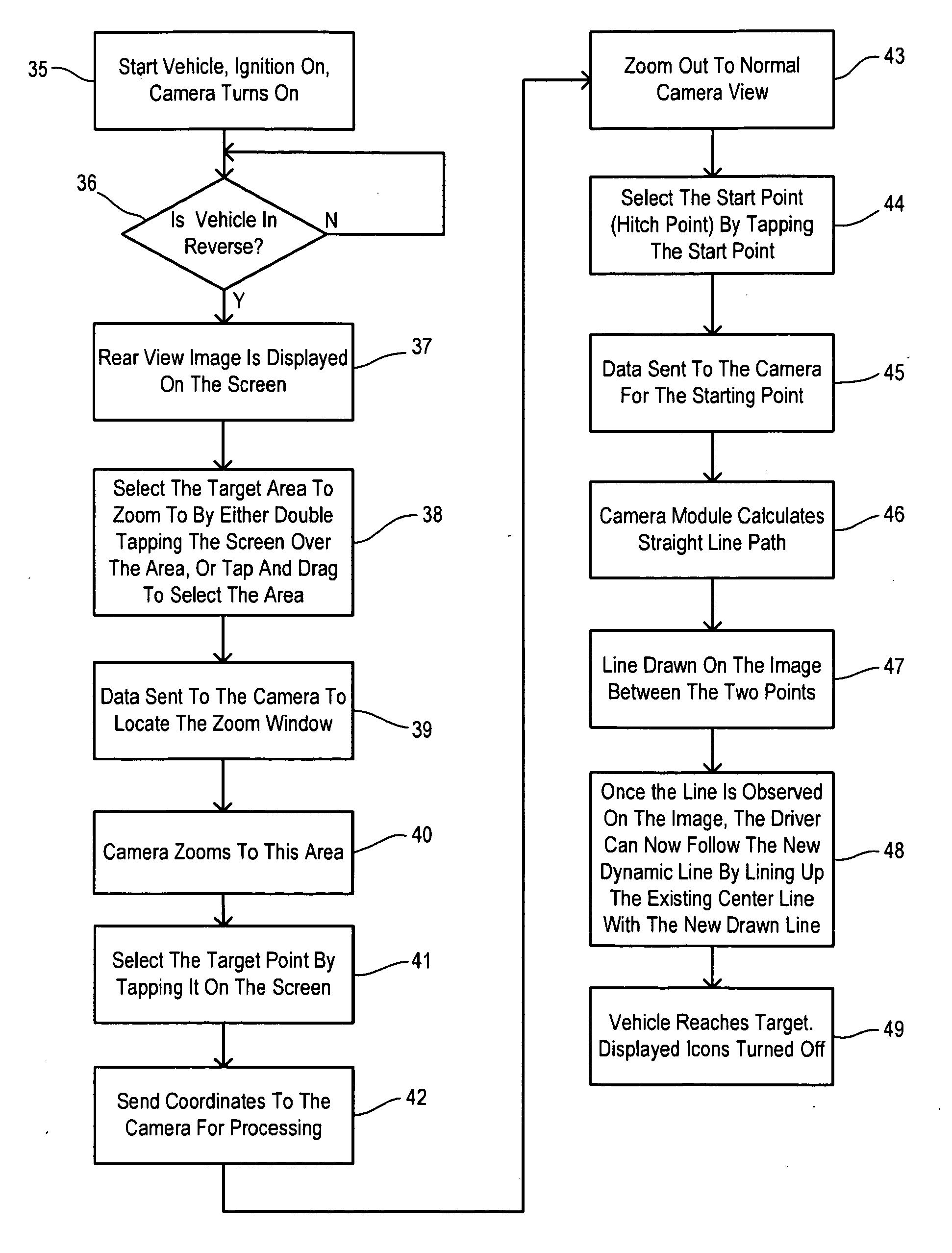
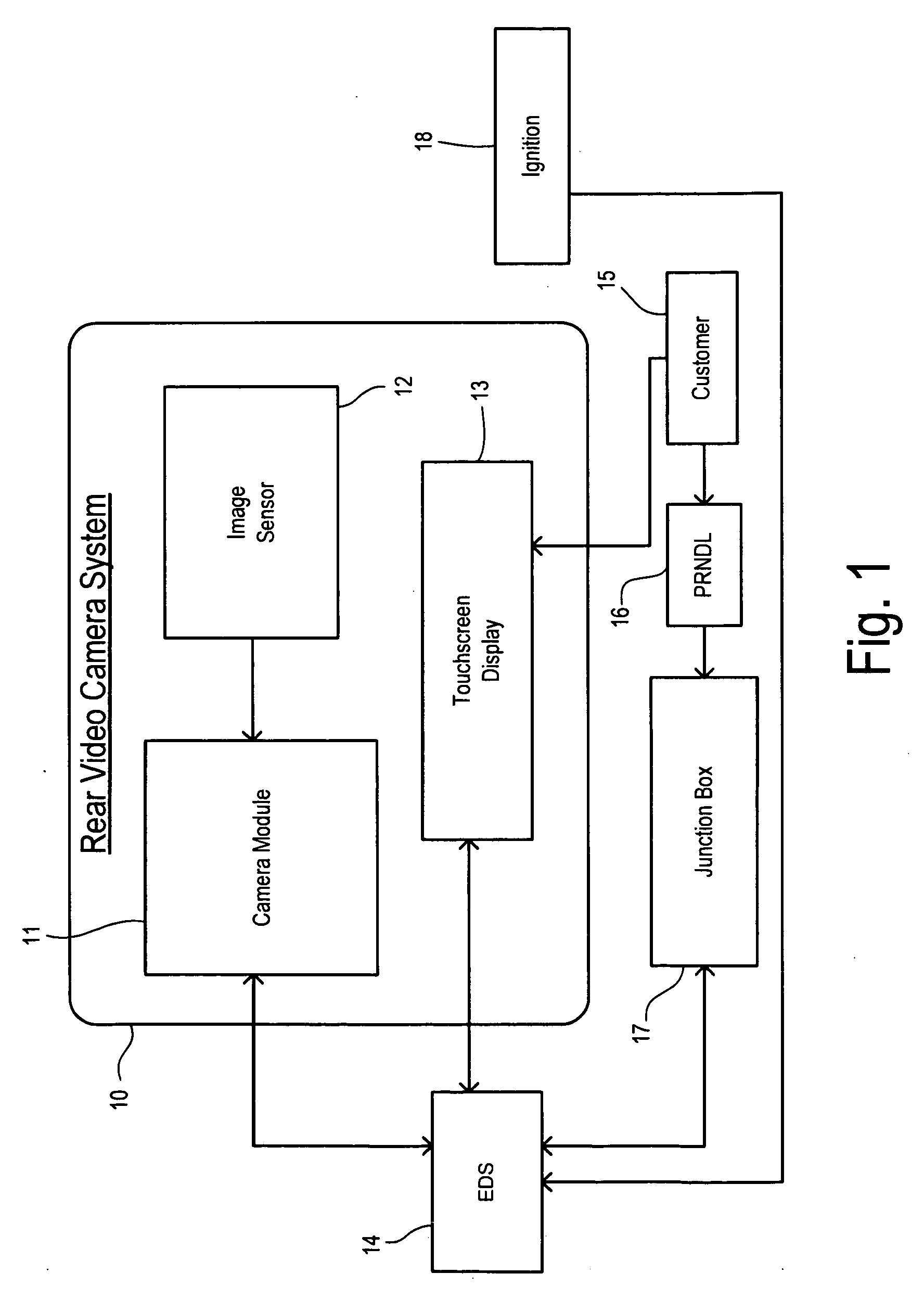
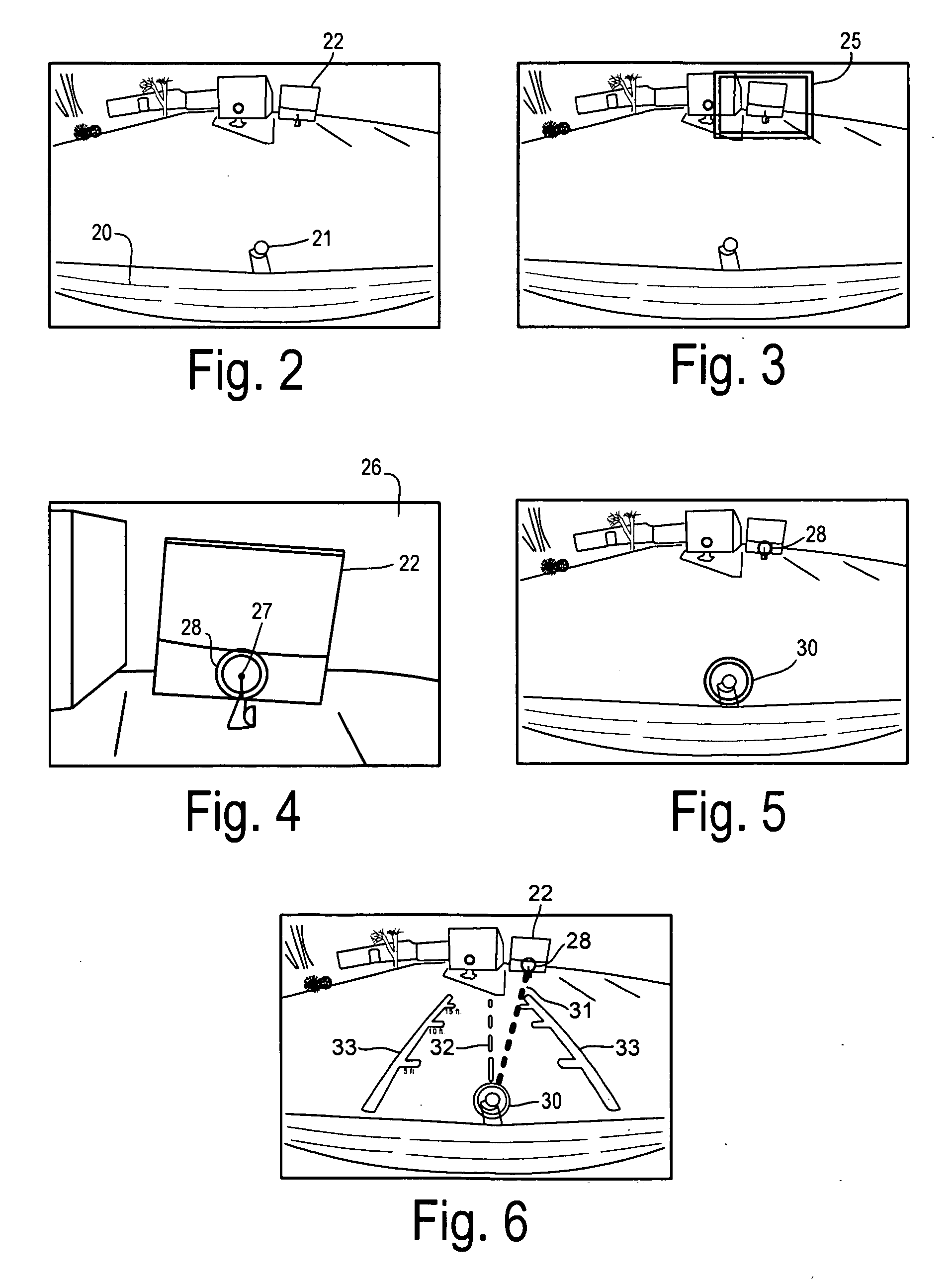
Rear Camera Backup Assistance With Touchscreen Display
InactiveUS20110001614A1Television system detailsImage analysisMobile vehicleComputer graphics (images)
Assistance for a backup maneuver of a motor vehicle in which a first point of interest on the vehicle is moved toward a second point of interest remote from the vehicle. A rear contextual view is displayed on an electronic display obtained from a rearward directed image sensor on the vehicle. A zoom window is manually placed on the electronic display to include the second point of interest. The zoom window is enlarged, and the location of the second point of interest is manually identified within the enlarged zoom window. The identified location of the second point of interest is transformed into target positional coordinates. The rear contextual view redisplayed with a target icon at the target positional coordinates. The location of the first point of interest is manually identified on the rear contextual view and transformed into starting positional coordinates. A start icon is displayed at the starting positional coordinates in the rear contextual view. A target line is determined between the target positional coordinates and the starting positional coordinates. A path line icon is displayed in the rear contextual view corresponding to the determined target line. A bearing line is displayed in the rear contextual view extending from the start icon. The target positional coordinates are re-determined as the rear contextual view shifts during the backup maneuver. The target icon and the path line icon are updated in response to the re-determined target positional coordinates.
Owner:FORD GLOBAL TECH LLC
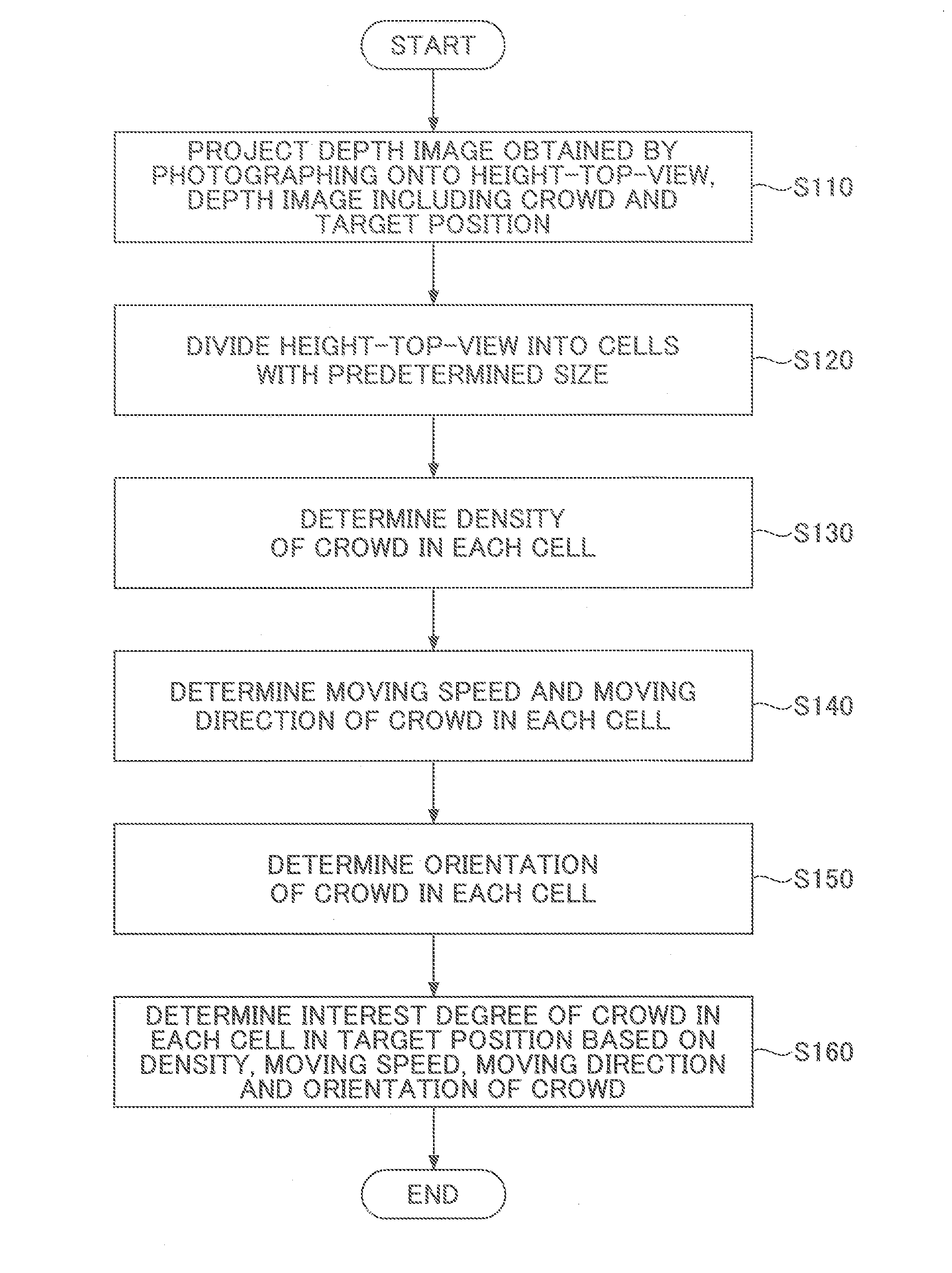
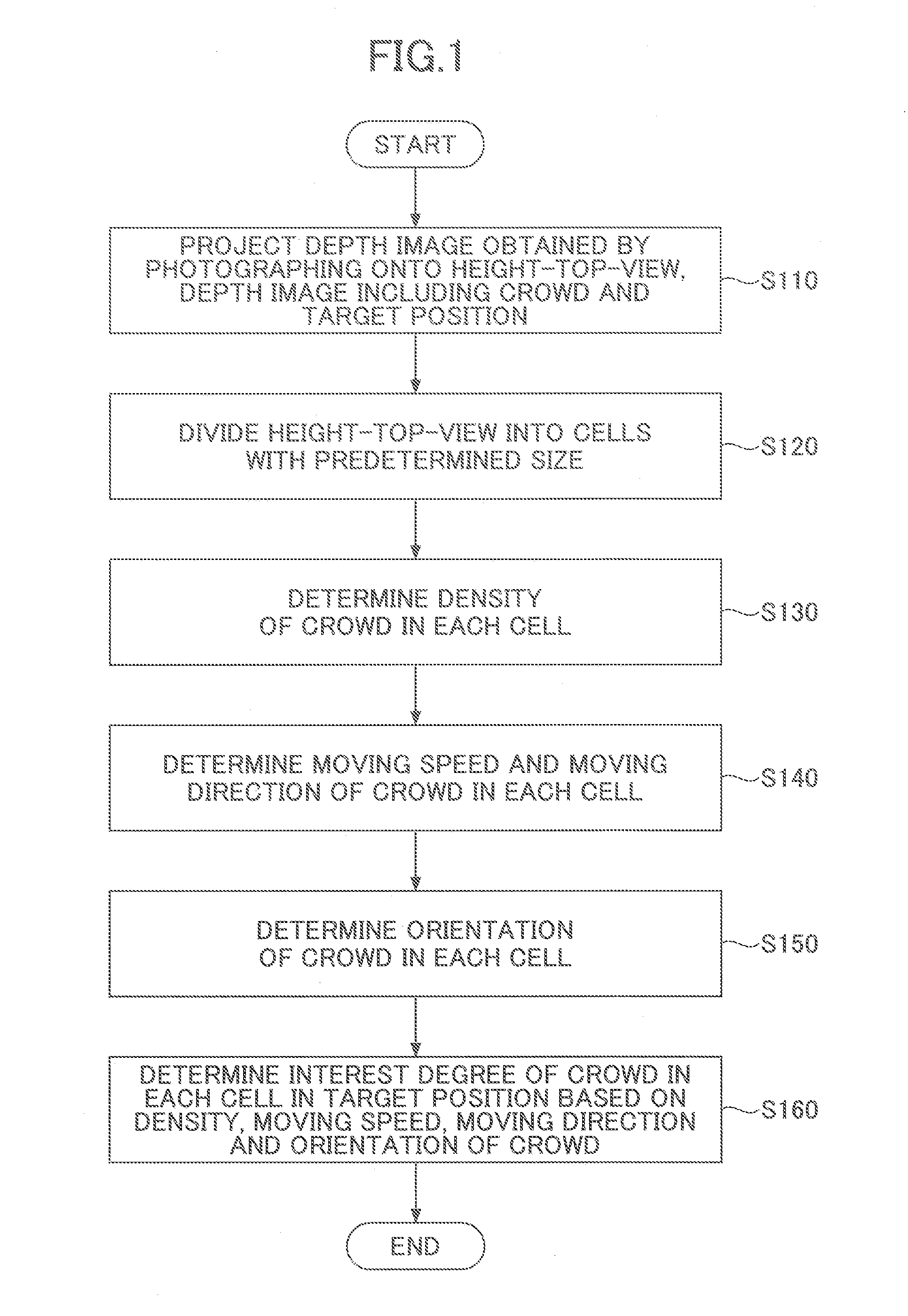
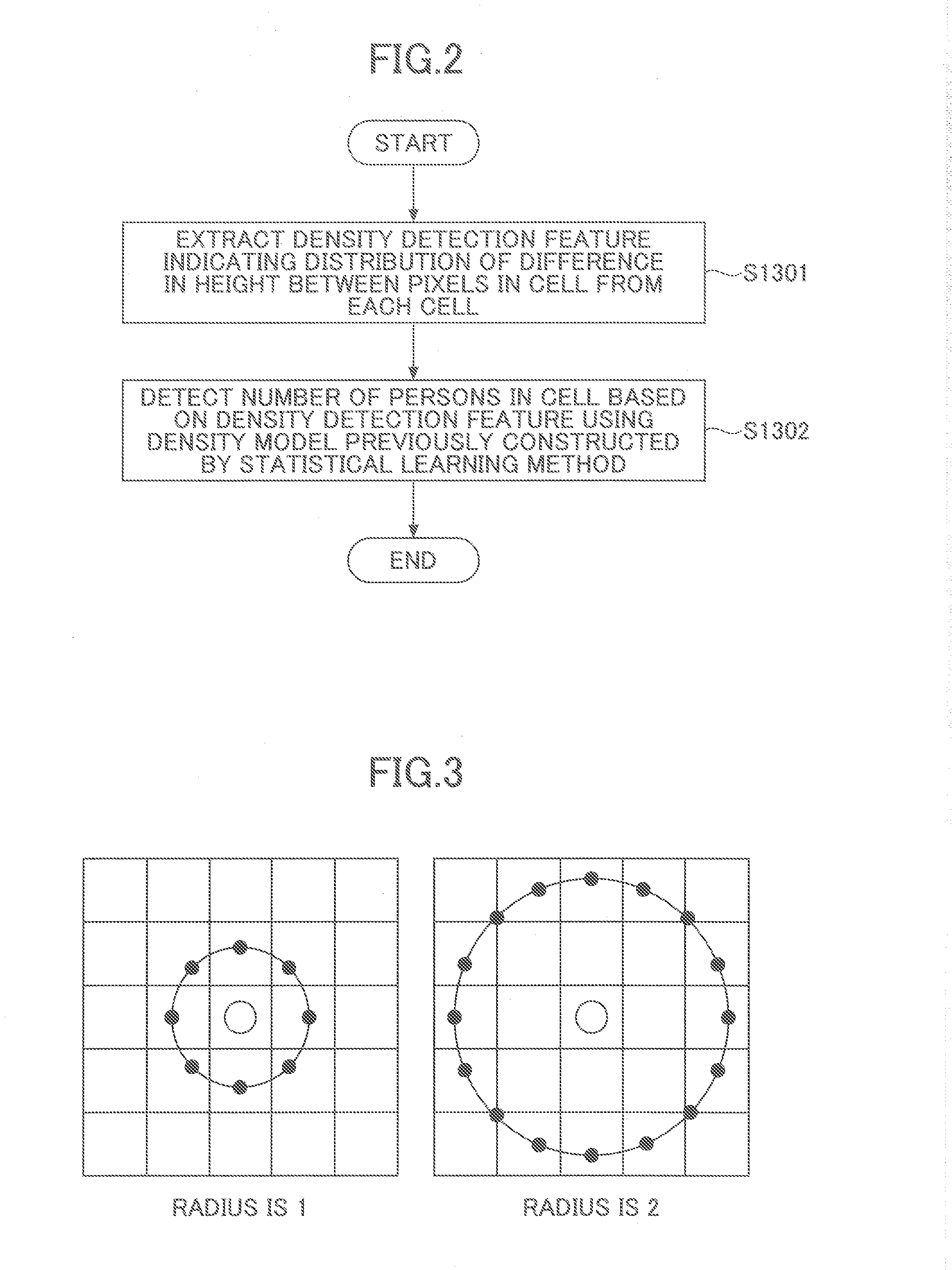
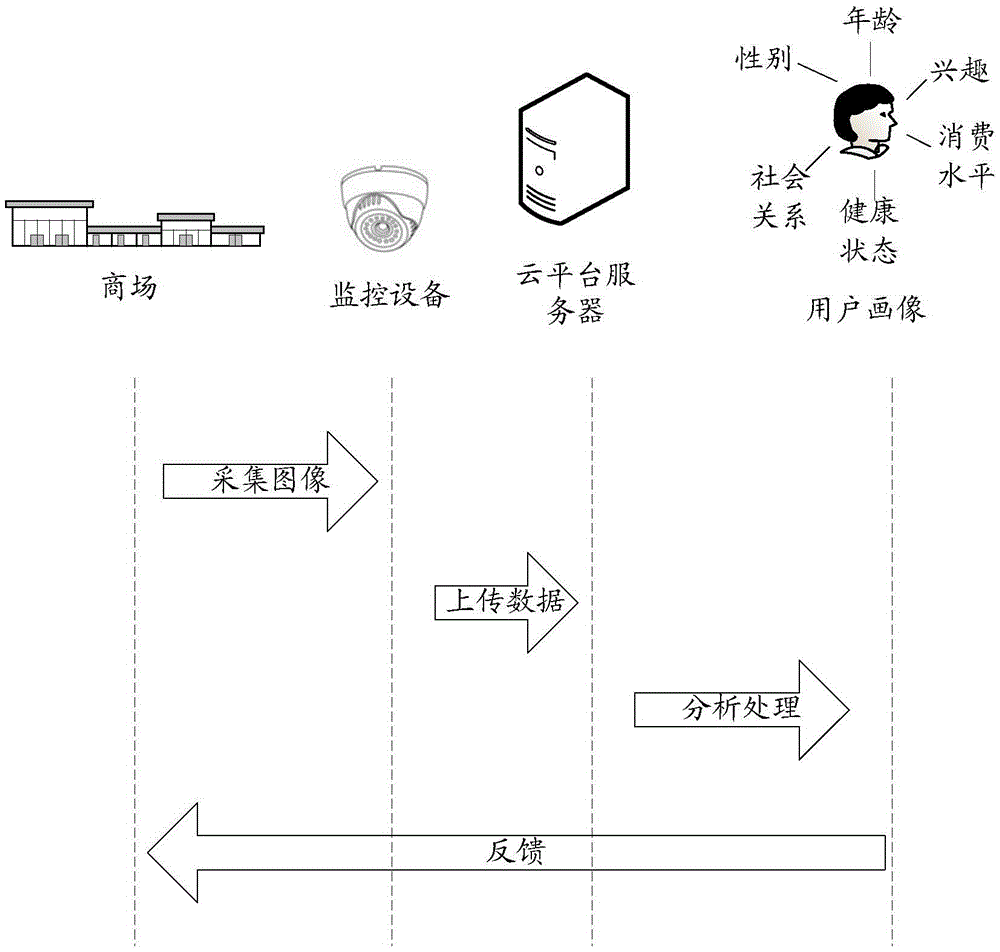
Method for detecting crowd density, and method and apparatus for detecting interest degree of crowd in target position
ActiveUS20160133025A1Optimize detection resultsMore accurateImage enhancementImage analysisComputer graphics (images)Density based
A method and an apparatus for detecting an interest degree of a crowd in a target position are disclosed. The interest degree detection method includes projecting a depth image obtained by photographing onto a height-top-view, the depth image including the crowd and the target position; dividing the height-top-view into cells; determining density of the crowd in each cell; determining a moving speed and a moving direction of the crowd in each cell; determining orientation of the crowd in each cell; and determining, based on the density, the moving speed, the moving direction and the orientation of the crowd, the interest degree of the crowd in each cell in the target position. According to this method, the interest degree of the crowd in the target position can be detected accurately, even at a crowded place where it is difficult to detect and track a single person.
Owner:RICOH KK
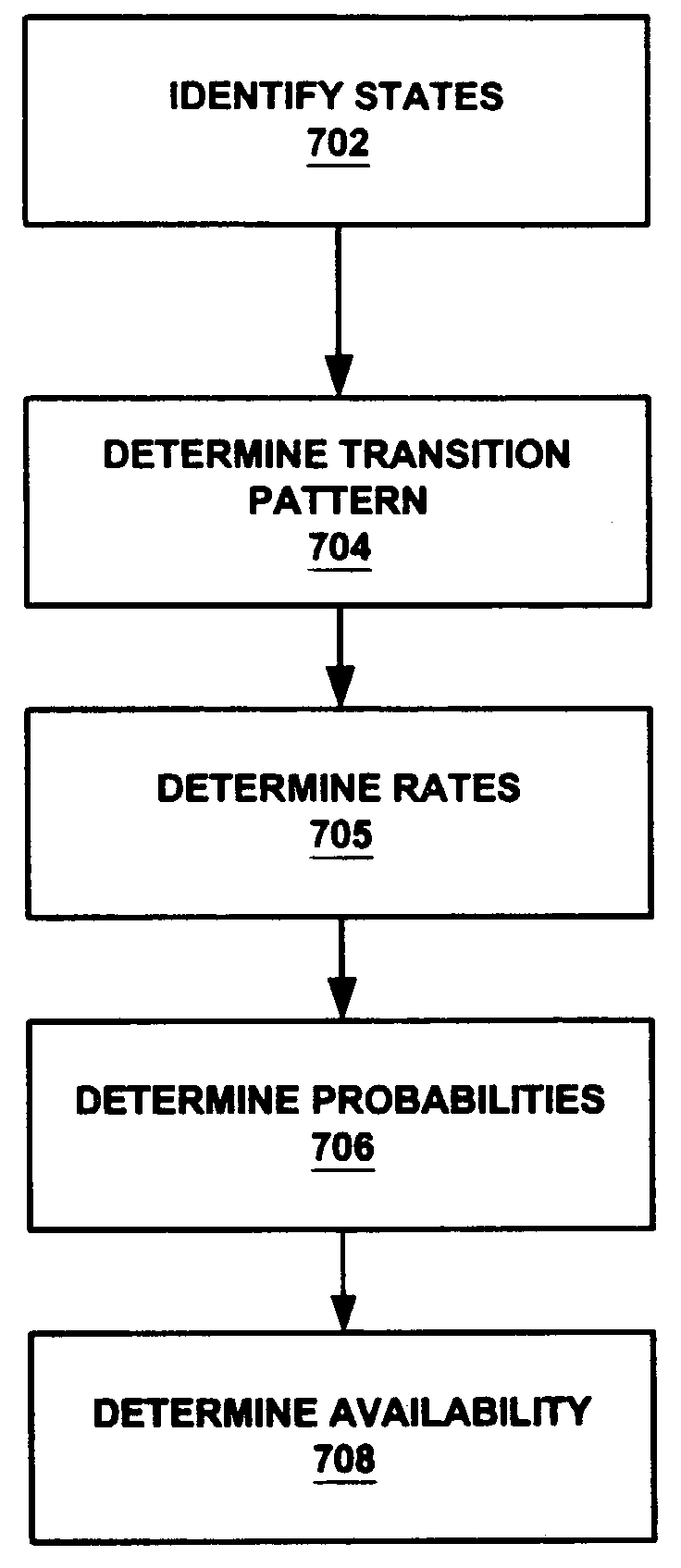
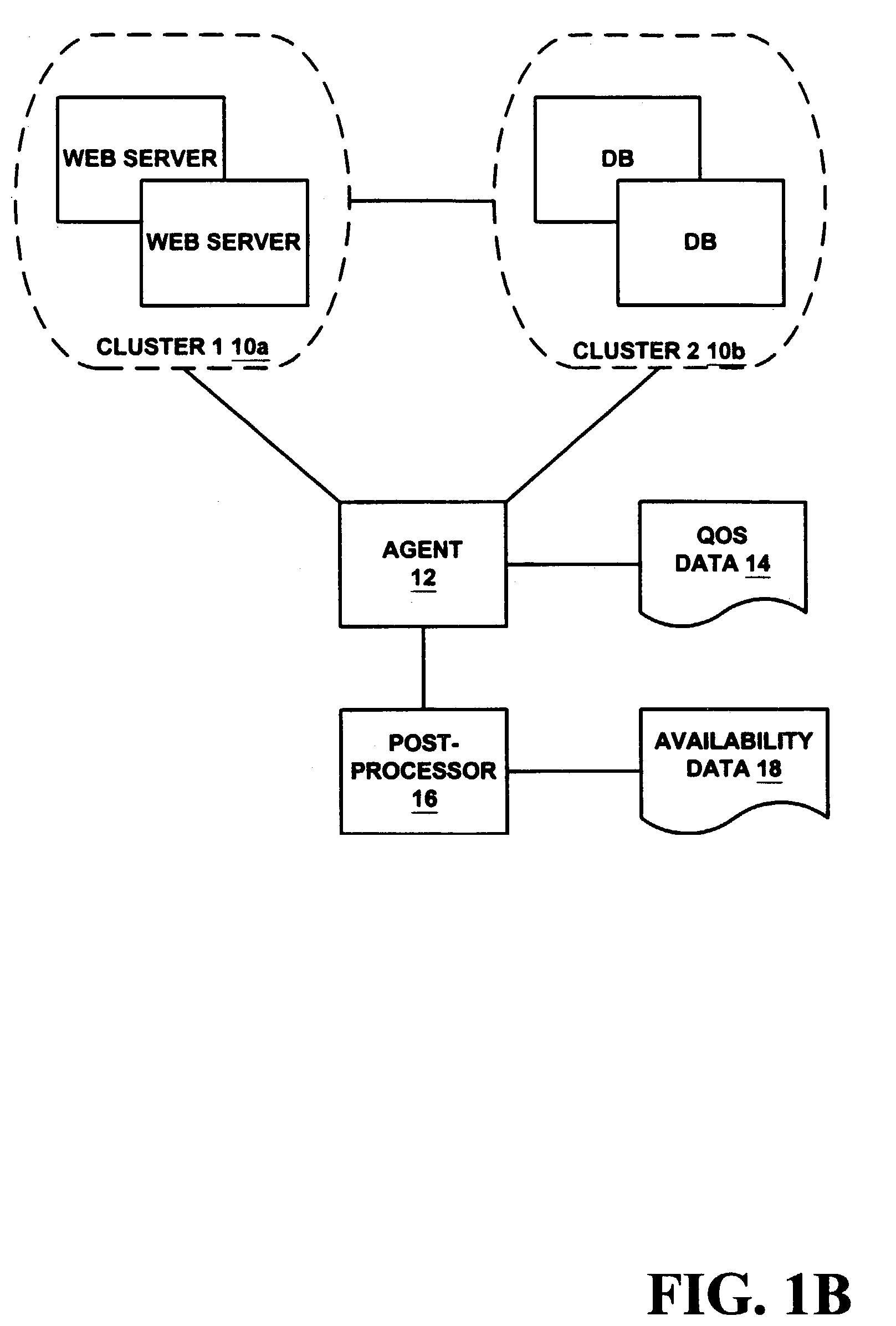
Markov model of availability for clustered systems
Availability of a clustered system is determined by identifying all possible states of a cluster, mapping the connections between the states are mapped and determining the probability of the cluster being in each of the states is determined. Availability of the cluster is the sum of the probabilities of being in those states in which the cluster is at least partially available. Parameters affecting the availability of the cluster include the rates at which a cluster transitions from state to state, including the reciprocal of Mean Time To Fail, Mean Time to Fail-Over, Mean Time To Fail-Back and Mean Time To Restore. Availability of statefull and stateless clusters may be determined. Availability of clusters including any number of nodes (e.g., a Internet service) can be determined. In one embodiment of the invention, a target availability is determined and parameters are varied to determine the most efficient approach to reach the target availability.
Owner:MICROSOFT TECH LICENSING LLC
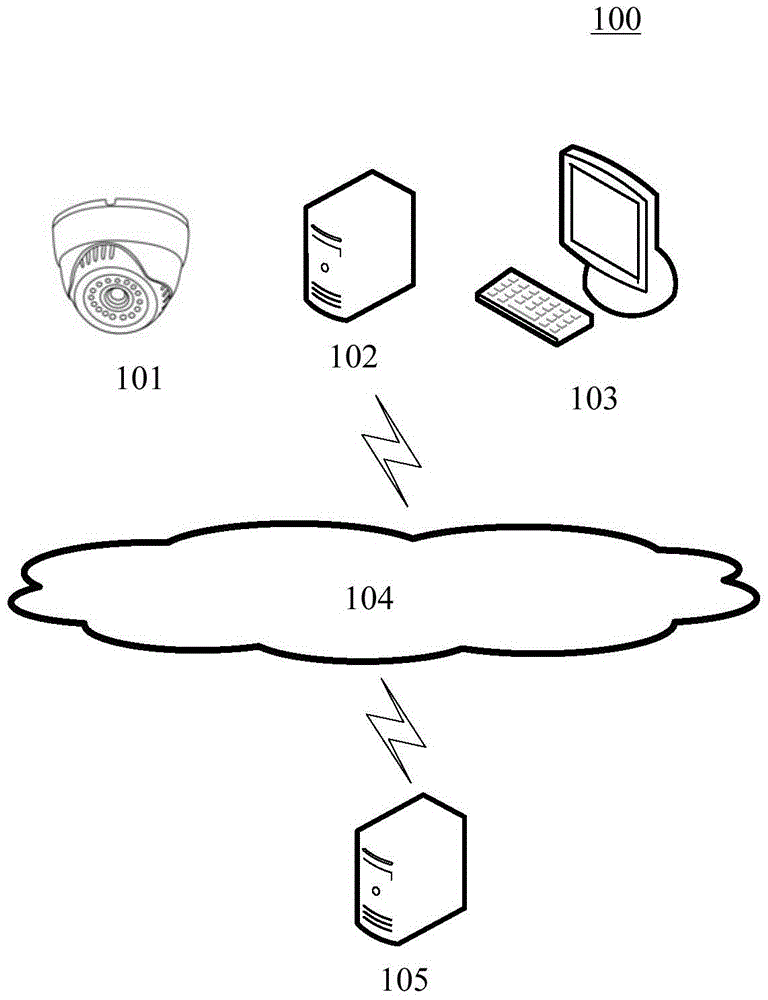
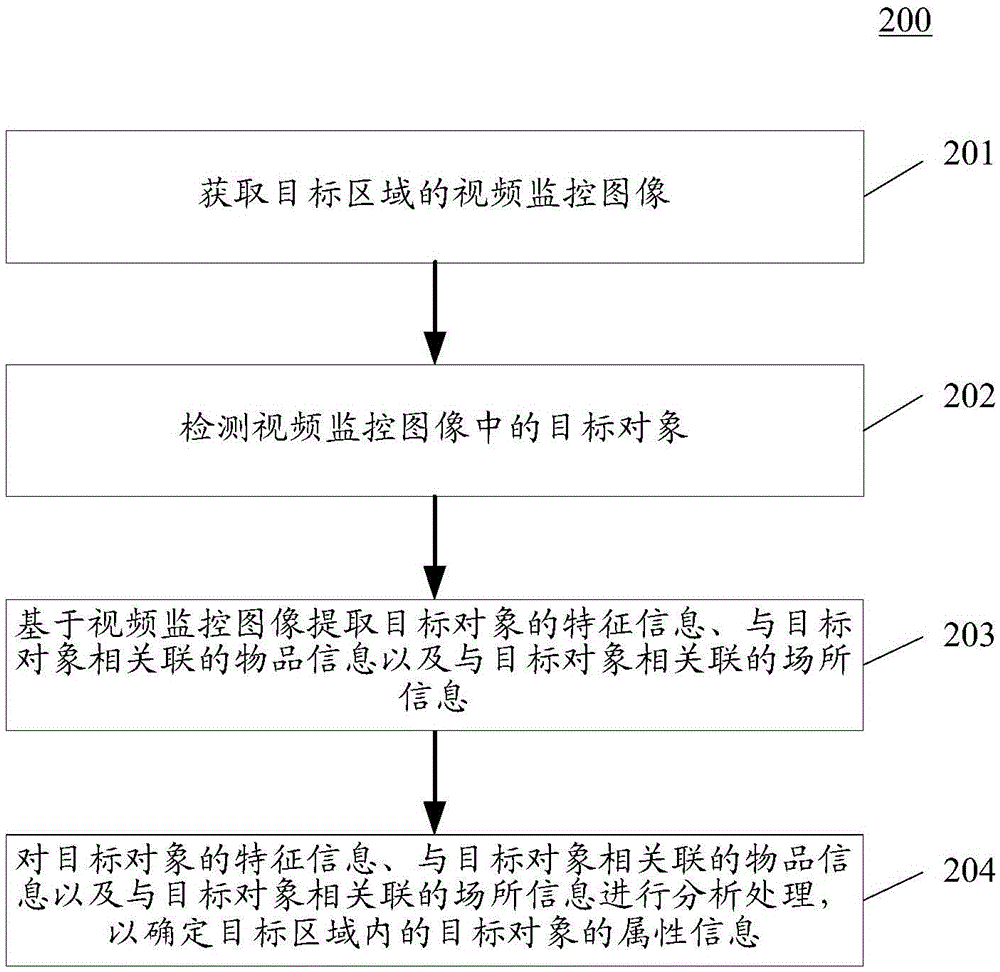
Method and device for determining attribute information of target object
ActiveCN106776619AAccurate analysisAdvertisementsCharacter and pattern recognitionVideo monitoringRelevant information
The invention discloses a method and device for determining attribute information of a target object. A specific embodiment way of the method comprises the steps that video monitoring images of a target area are obtained; the target object in the video monitoring images is detected and the target object comprises people in the target area; feature information of the target object, article information relevant to the target object and scene information relevant to the target object based on the video monitoring images are extracted; analysis and process are conducted on the feature information of the target object, the article information relevant to the target object and the scene information relevant to the target object to determine the attribute information of the target object in the target area. The method and device for determining the attribute information of the target object use relevant information of richer target objects and achieve more precise analysis of the attribute information of target objects.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
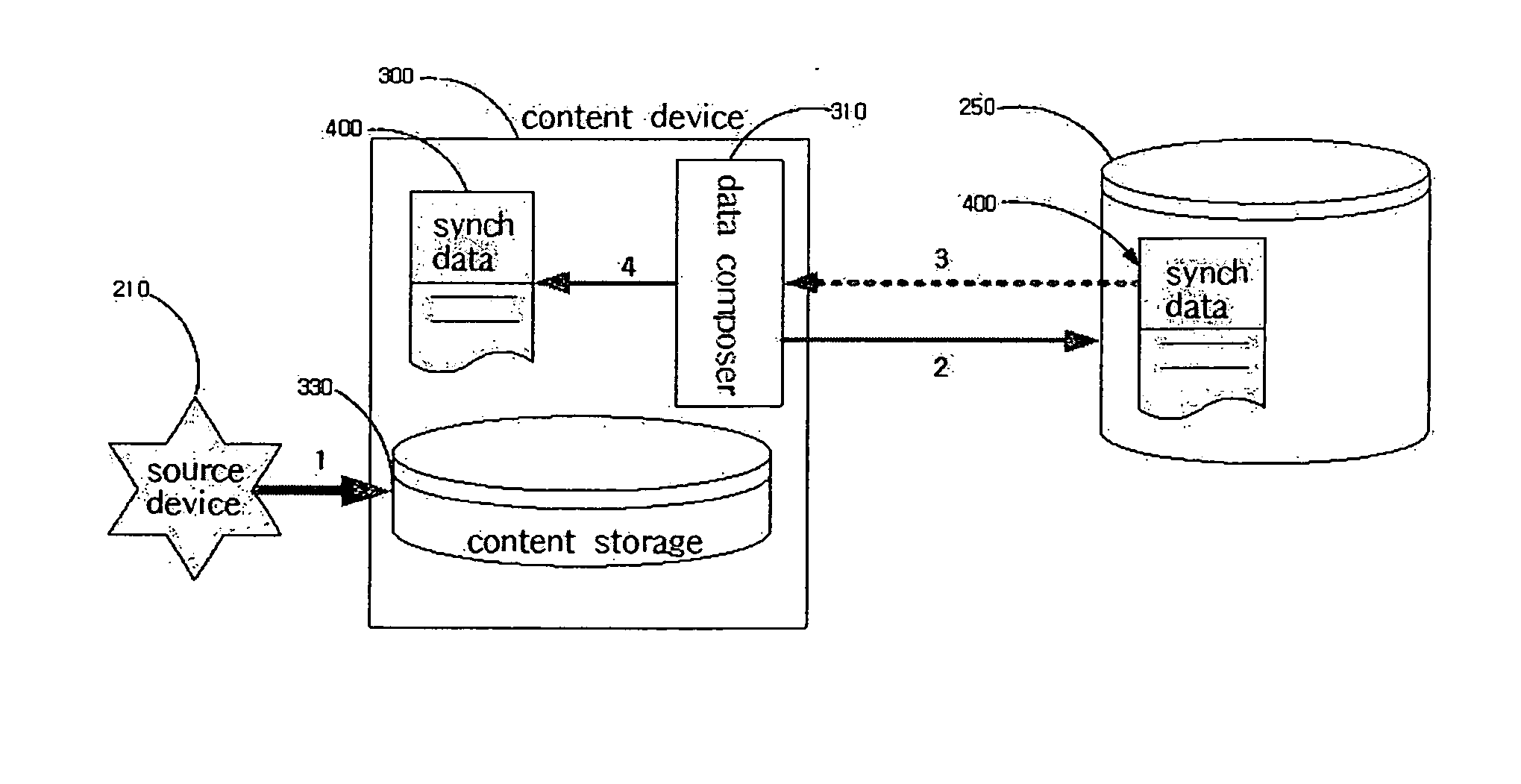
Method and data format for synchronizing contents
InactiveUS20050021866A1Carrier indexing/addressing/timing/synchronisingMultiple digital computer combinationsTechnical standardIdentifying goals
A method and data format for synchronizing contents. The method includes a content device downloading the contents from a source device, storing synch data required to synchronize the downloaded contents, determining a target device by interpreting the synch data, and executing the contents through the target device. The data format includes SynchTime for defining a time at which contents stored in a content device are executed in a target device, SynchAction for defining actions that are required to allow the content device to execute the contents in the target device, ContentInfo for defining the kinds of contents, PreferenceInfo for defining the basic information of an owner if the owner of the contents exists, and SelectDeviceInfo for defining a certain criterion to select a certain device if a plurality of devices providing the corresponding service exist at the time of synchronization.
Owner:SAMSUNG ELECTRONICS CO LTD
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing continuous risk assessment
InactiveUS20040102923A1Memory loss protectionError detection/correctionTechnical standardComputer-aided
A computer-assisted system, medium and method of providing a risk assessment of a target system. The method includes electronically scanning, on a predetermined basis, hardware and / or software characteristics of components within a target system to obtain and store target system configuration information, receiving and storing target system operational environment information, using information collected in the scanning and receiving steps to select one or more security requirements in accordance with the at least one predefined standard, regulation and / or requirement, selecting one or more test procedures used to determine target system compliance with the security requirements, and producing a risk assessment of the target system.
Owner:TELOS CORP
Systems and methods for analyzing remote sensing imagery
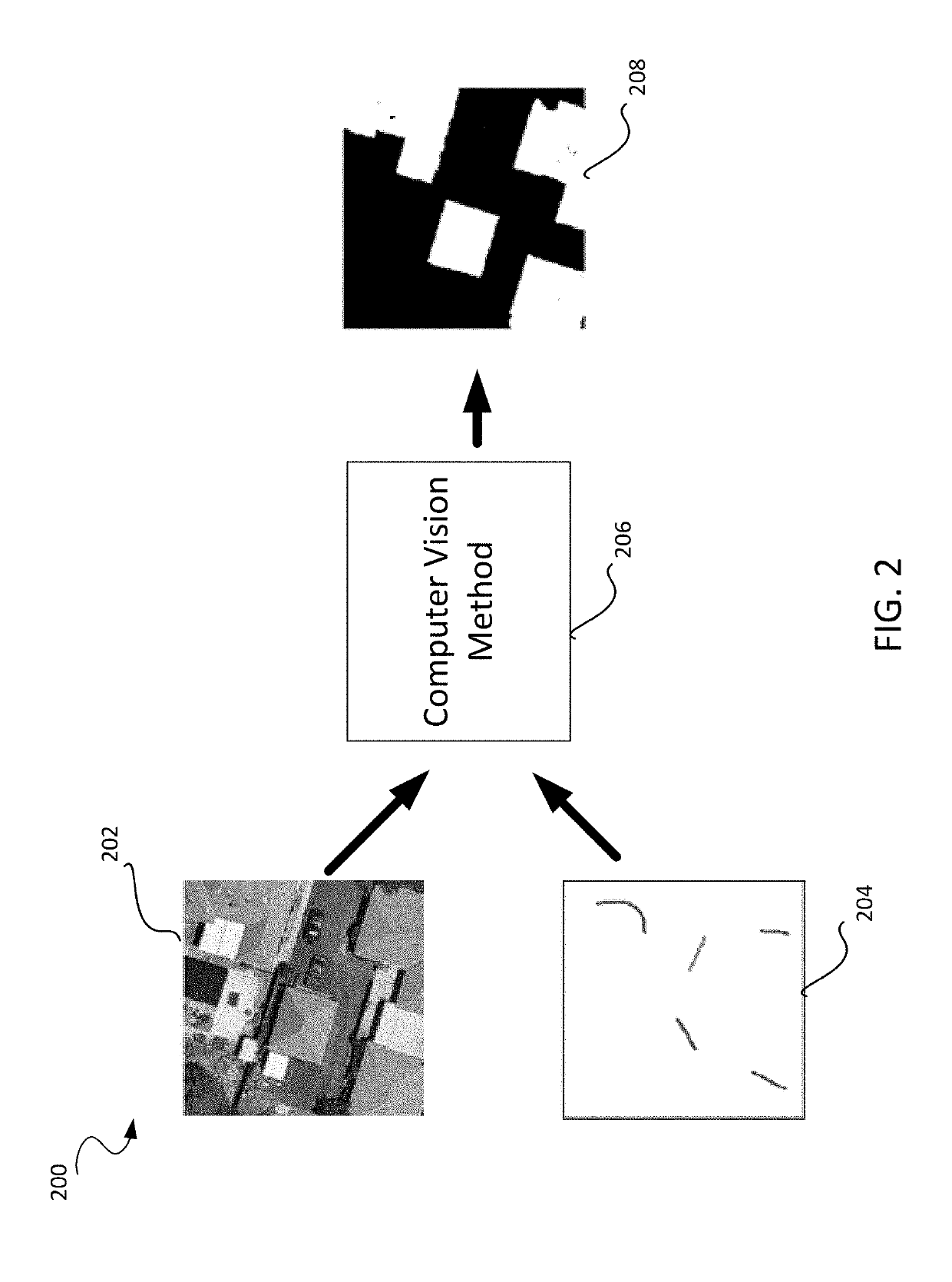
ActiveUS10311302B2Television system detailsCharacter and pattern recognitionTransformation parameterIdentifying goals
Disclosed systems and methods relate to remote sensing, deep learning, and object detection. Some embodiments relate to machine learning for object detection, which includes, for example, identifying a class of pixel in a target image and generating a label image based on a parameter set. Other embodiments relate to machine learning for geometry extraction, which includes, for example, determining heights of one or more regions in a target image and determining a geometric object property in a target image. Yet other embodiments relate to machine learning for alignment, which includes, for example, aligning images via direct or indirect estimation of transformation parameters.
Owner:CAPE ANALYTICS INC
Rule matching method, device and system
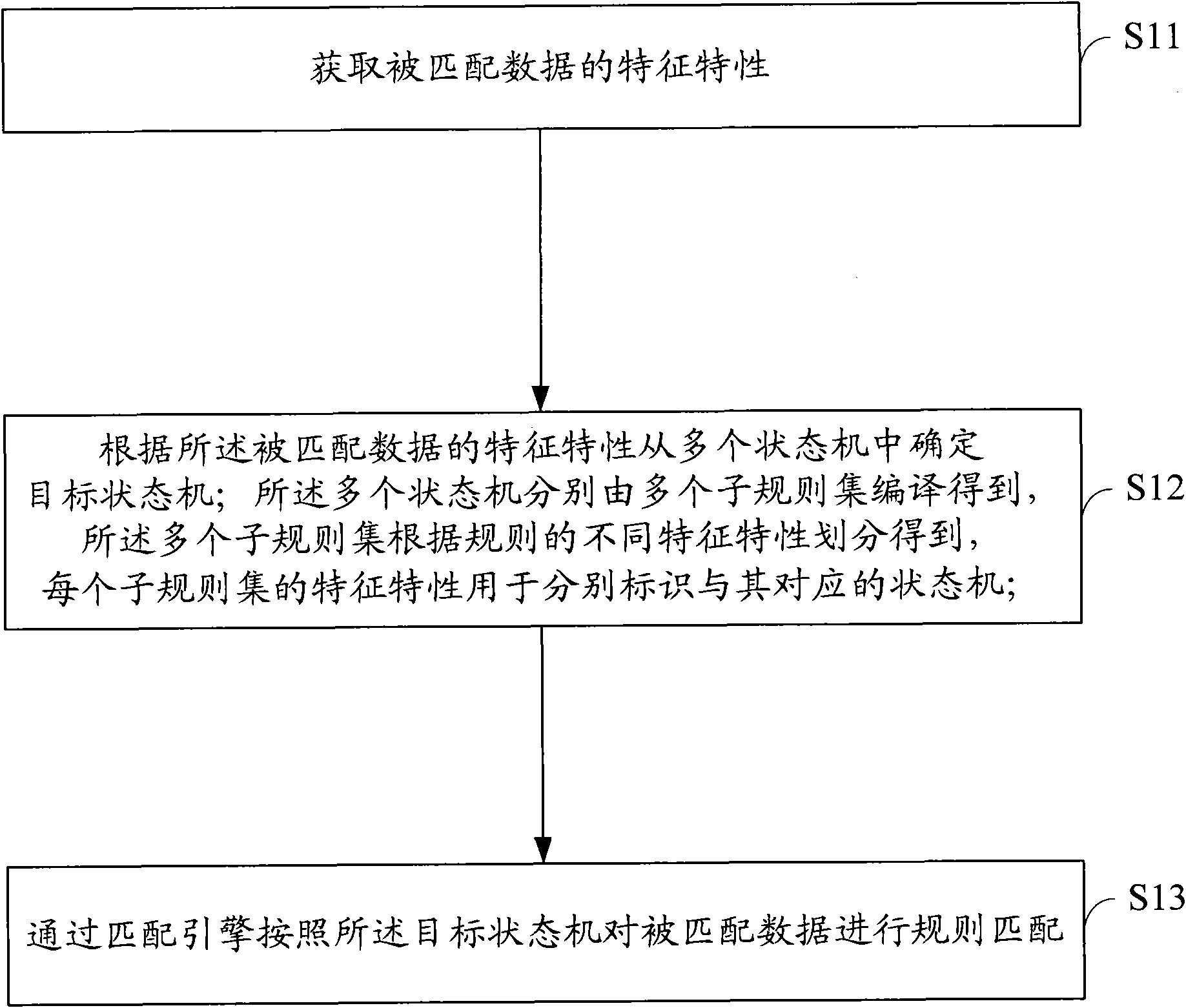
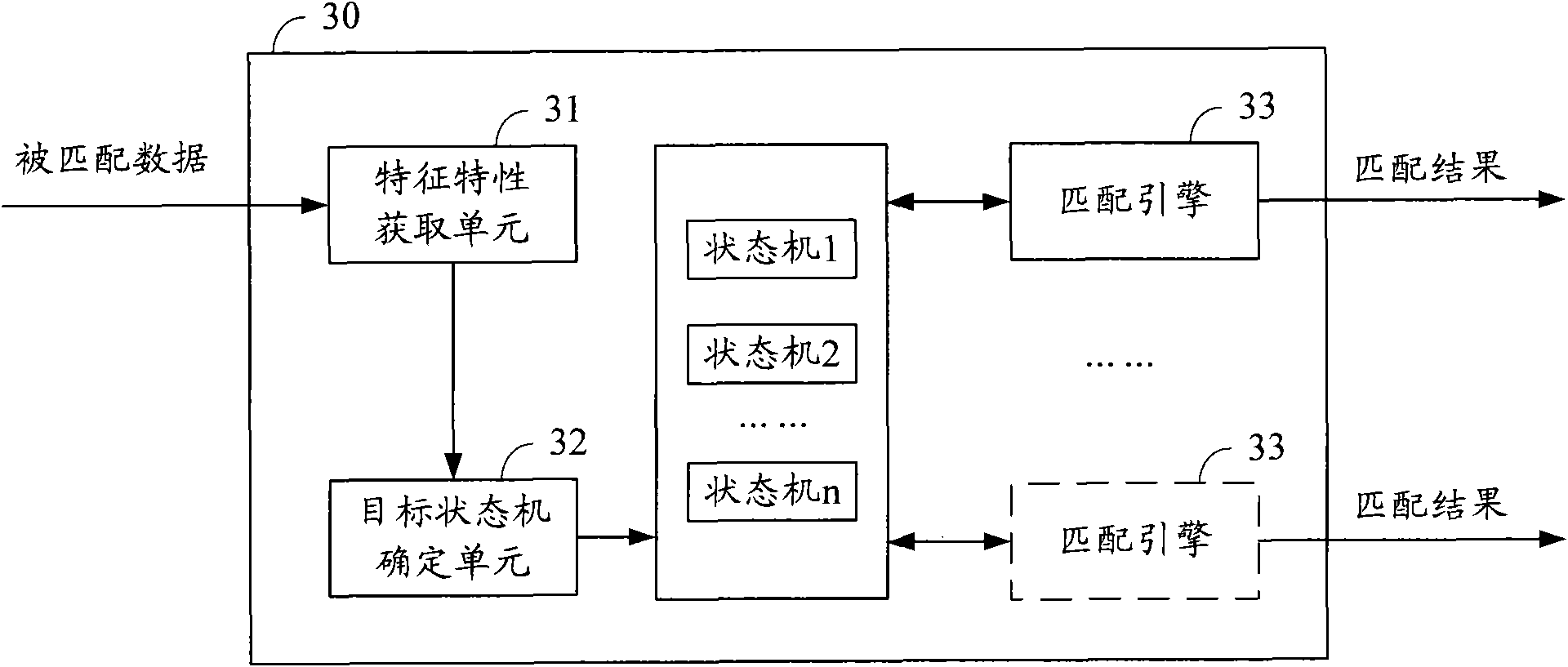
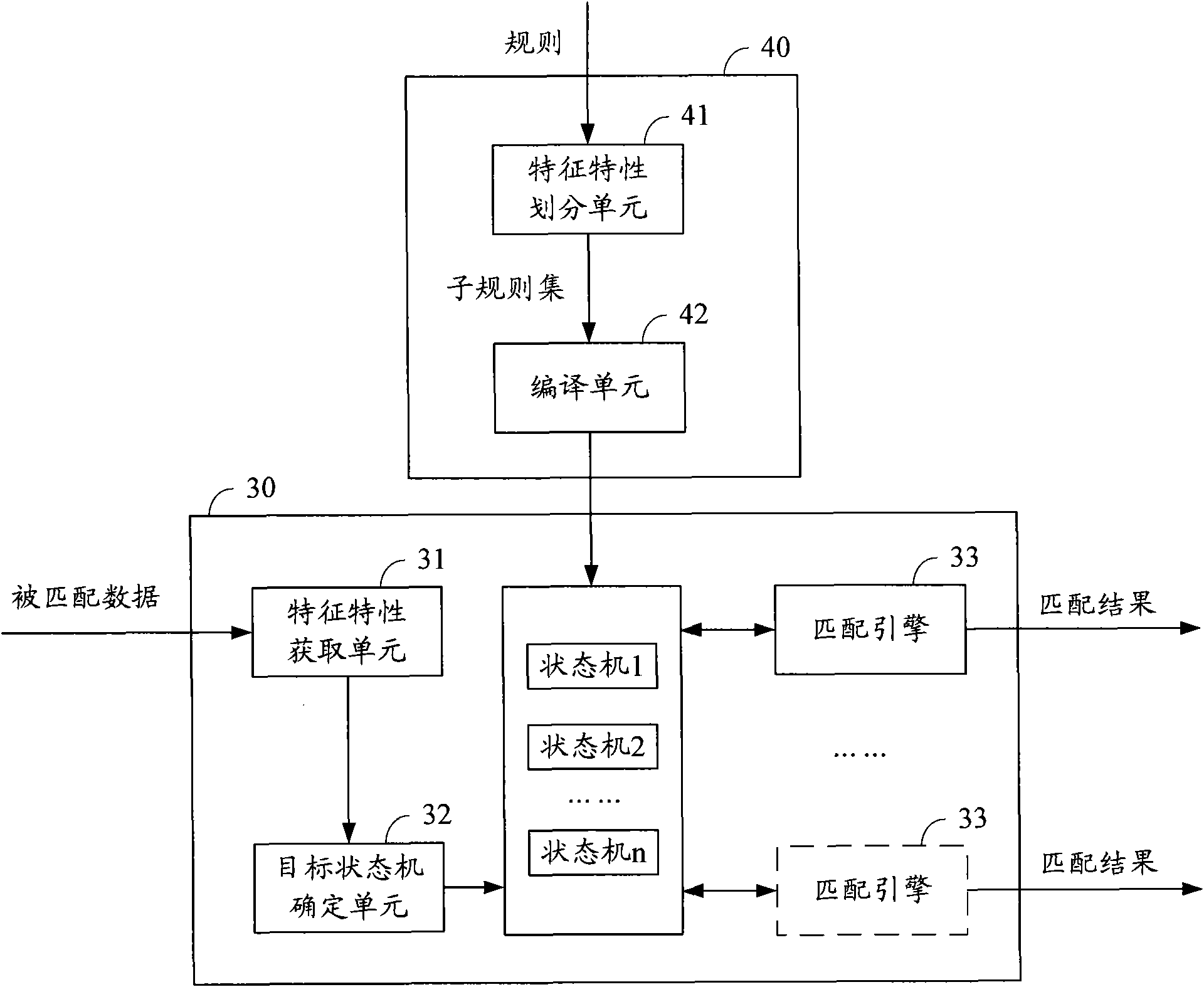
InactiveCN101841546AReduce the size of the rulesetReduce branchesTransmissionSpecial data processing applicationsFinite-state machineIdentifying goals
The embodiment of the invention discloses a rule matching method, a device and a system, wherein the rule matching method comprises the steps of: obtaining the characteristic of the matched data; determining the target state machine from a plurality of state machines according to the characteristic of the matched data; obtaining the plurality of state machines by compiling a plurality of sub-rulesets; obtaining the plurality of sub-rule sets according to the division of different characteristics of the rule; the characteristic of each sub-rule set is used for respectively identifying the state machine which corresponds to each sub-rule set; and carrying out the rule matching by matching an engine according to the target state machine. The embodiment of the invention effectively reduces the size of the rule set in the state machine and causes the branch of the state machine to reduce and the depth of the state to becomes small, thus being capable of reducing the matching period of therule matching and saving the cost and time of the system resources, and further increasing the matching efficiency.
Owner:HUAWEI TECH CO LTD
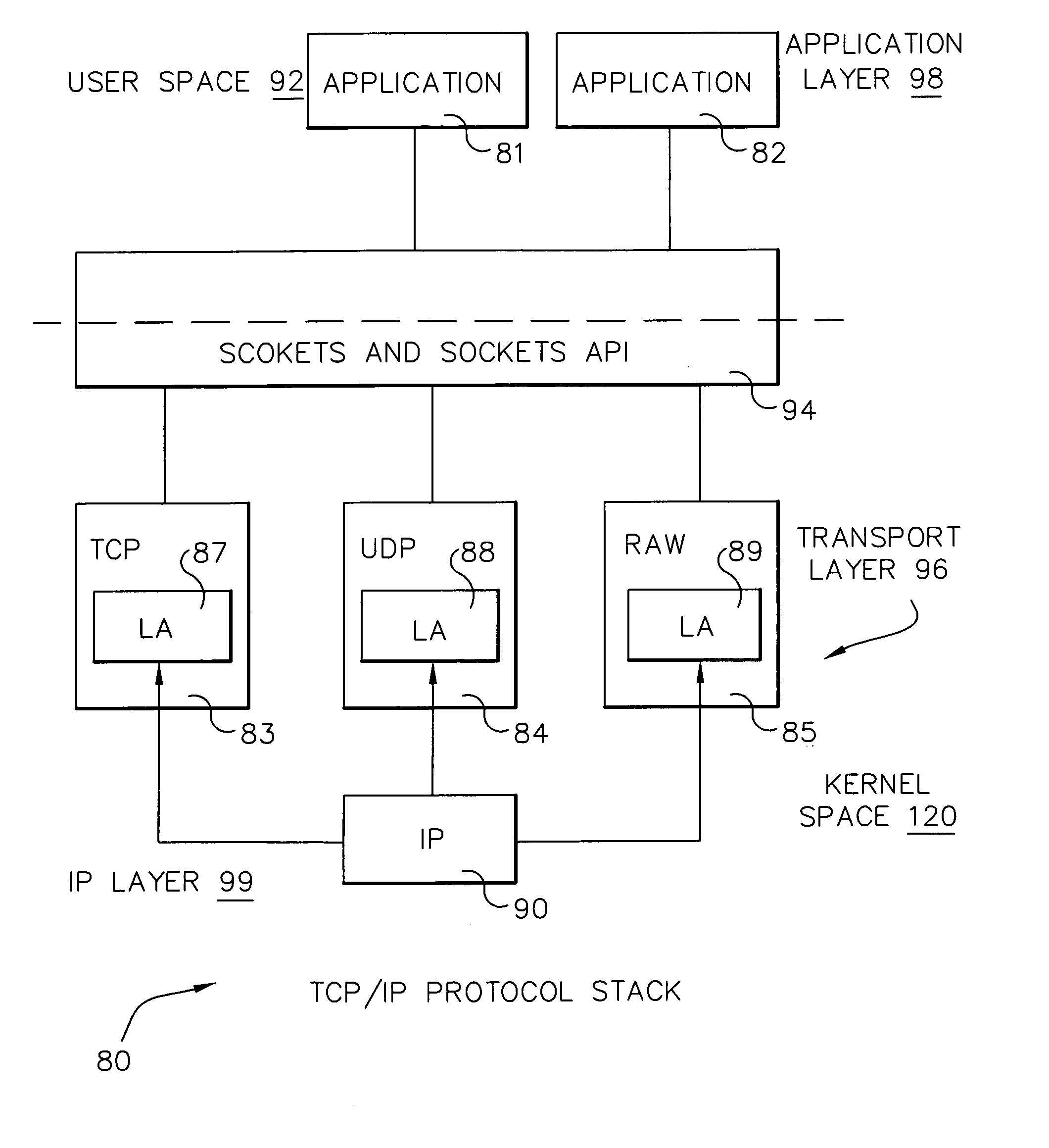
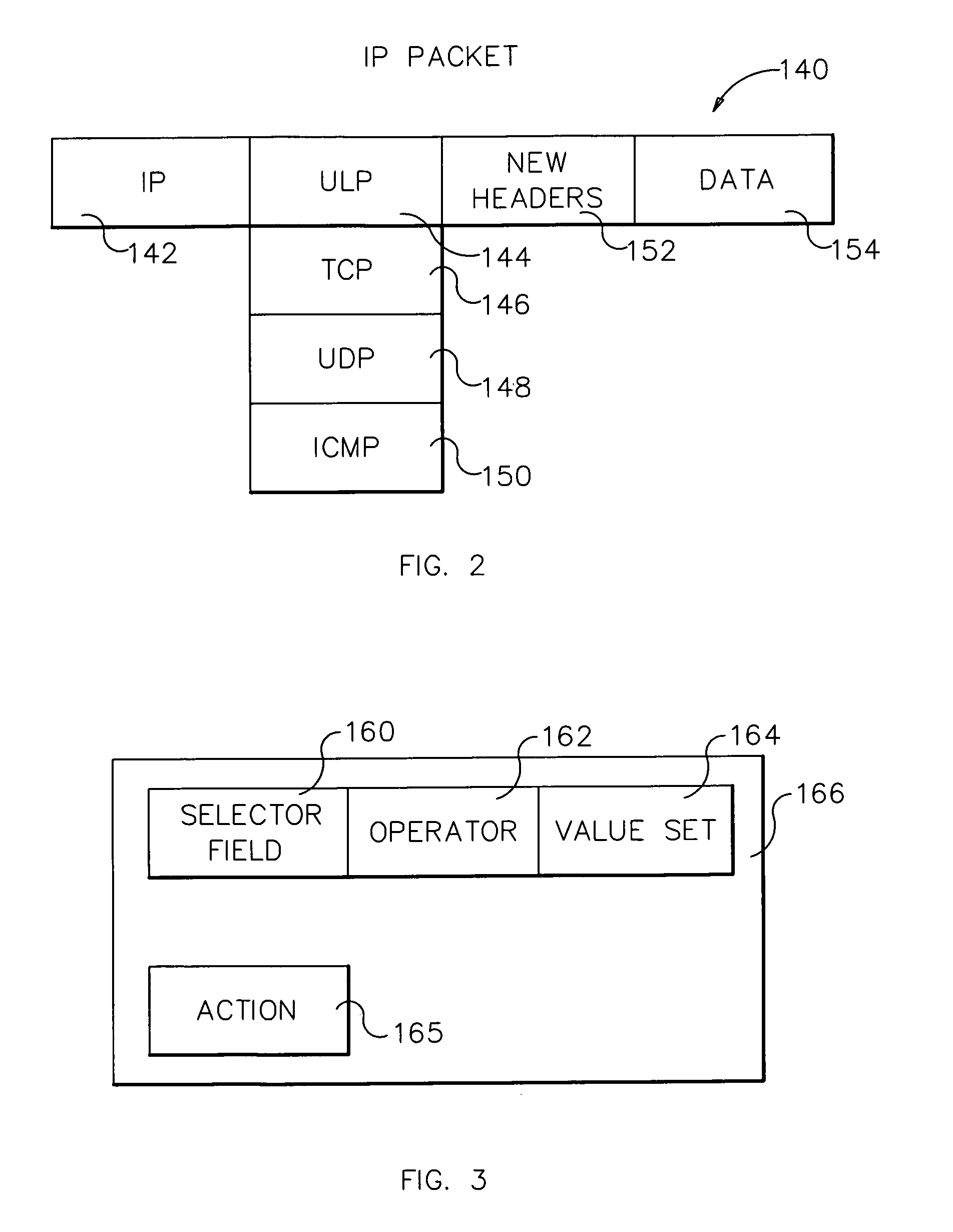
System and method for IP packet filtering based on non-IP packet traffic attributes
InactiveUS7209962B2Multiple digital computer combinationsTransmissionTraffic capacityOperational system
Control and management of communication traffic. IP packet filtering occurs in an operating system kernel implementation of, for example, the TCP / IP protocol suite. Access rules are expressed as filters referencing system kernel data; for outbound processing, source application indicia is determined; for inbound packet processing, a look-ahead function is executed to determine target application indicia; and responsive to the source or target application indicia, filter processing is executed.
Owner:TREND MICRO INC
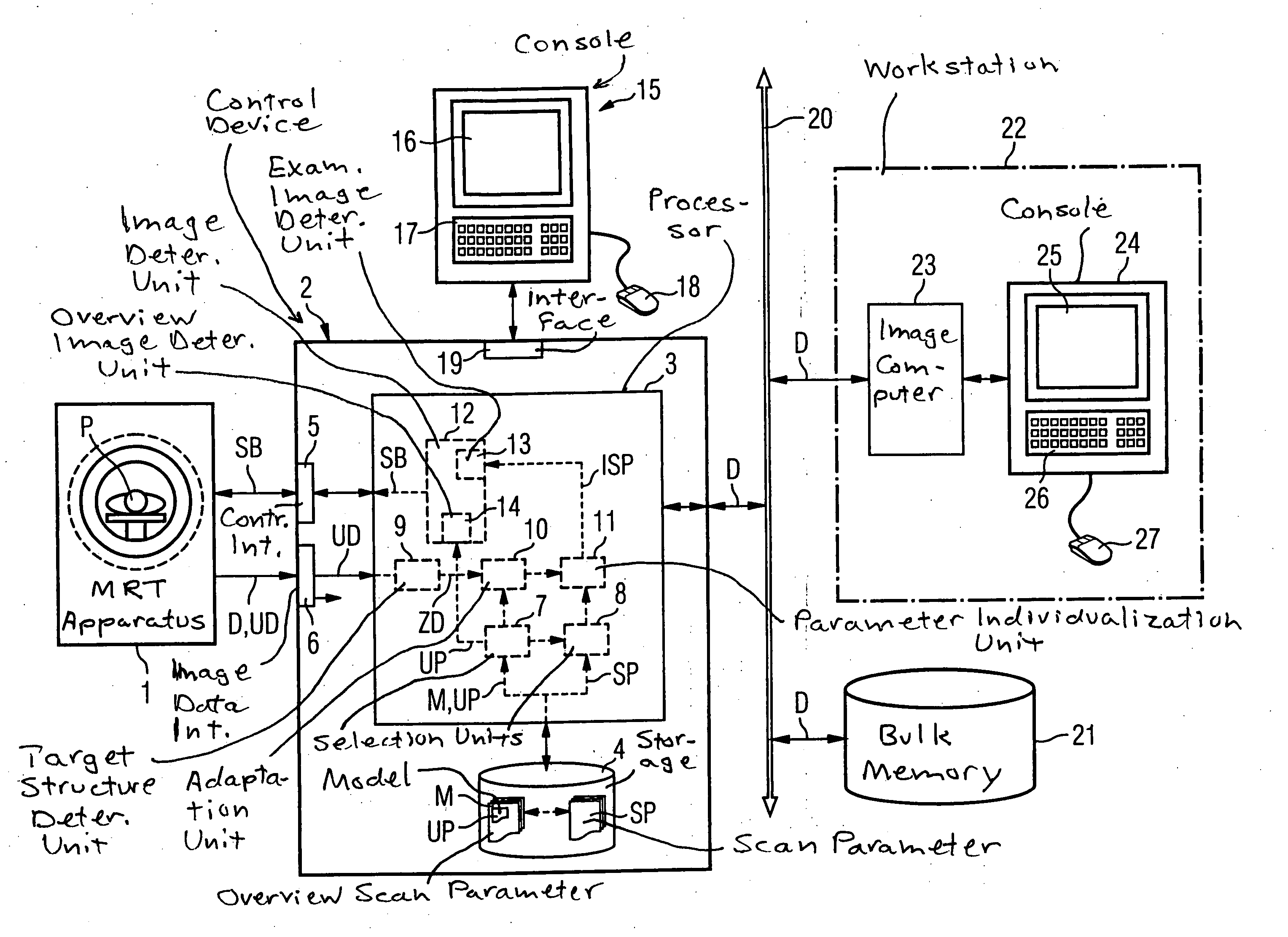
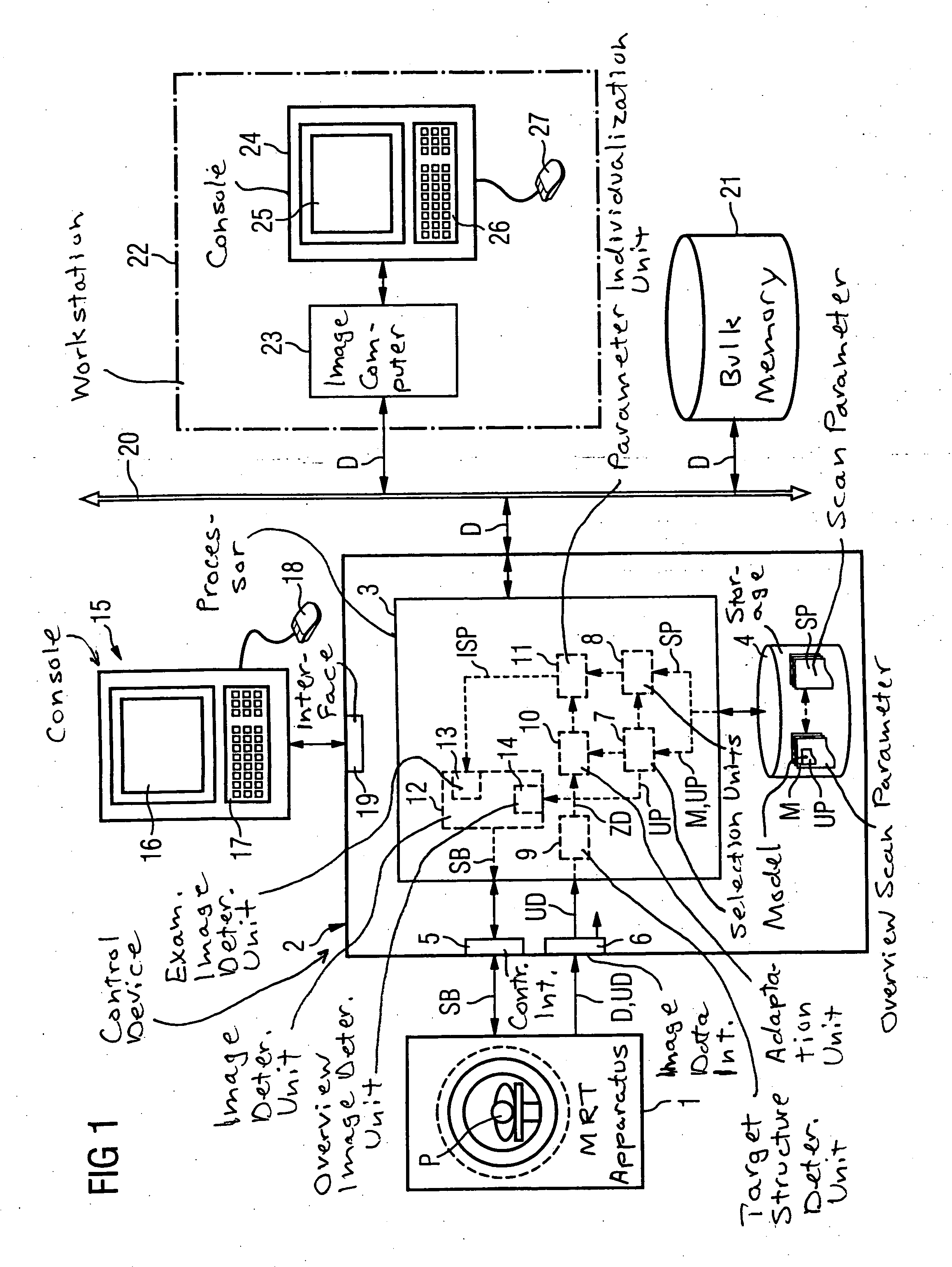
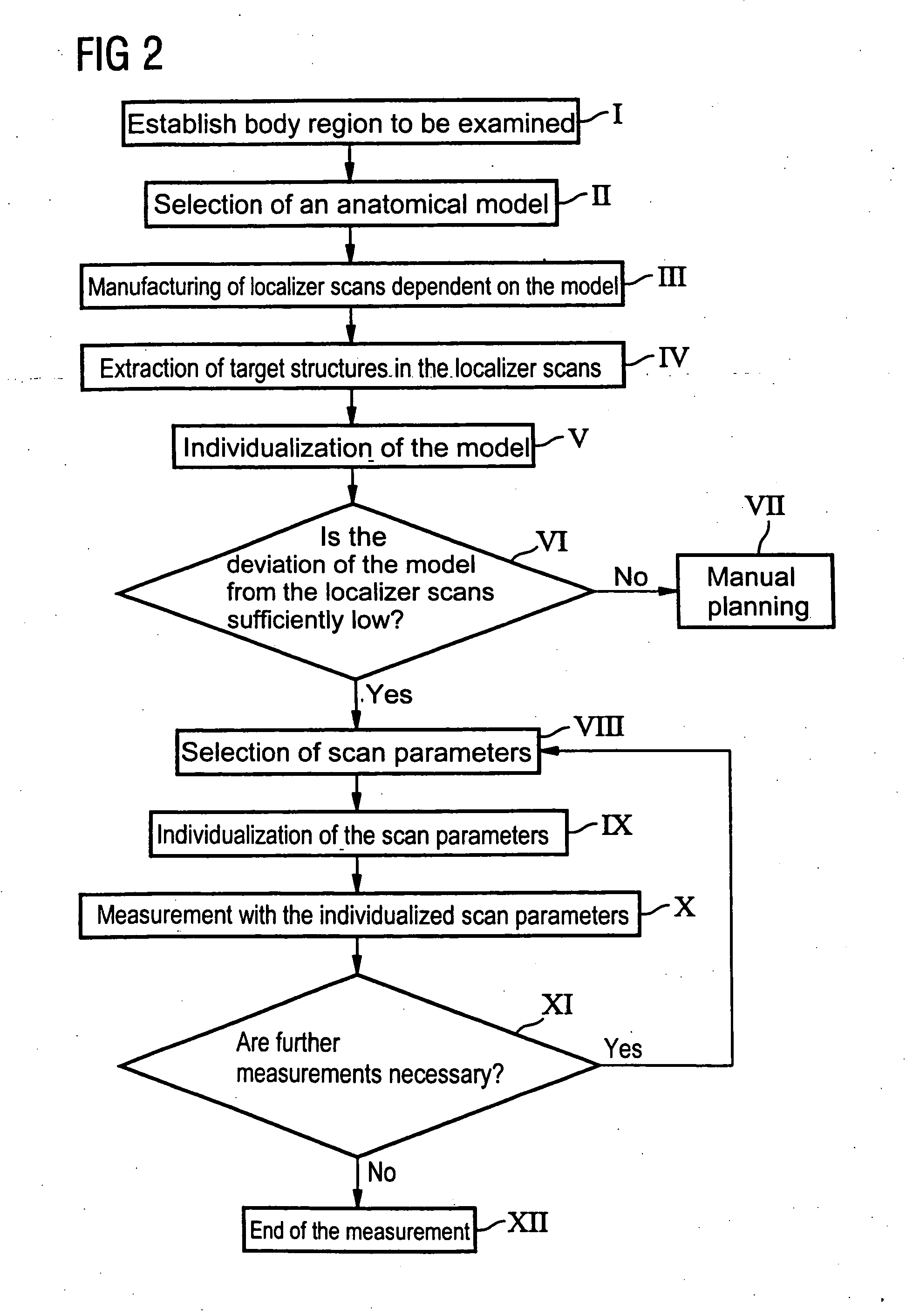
Method and control device to operate a magnetic resonance tomography apparatus
InactiveUS20050154292A1Diagnostic recording/measuringMeasurements using NMR imaging systemsPersonalizationResonance
In a method and control device for the operation of a magnetic resonance tomography apparatus, initially an anatomical normal model whose geometry is variable is selected for an examination subject to be examined dependent on a diagnostic inquiry. Then a number of overview images of a region of the examination subject are obtained, with various overview scan parameters with which the acquisition of the overview images is controlled being established dependent on the selected anatomical normal model. In the slice image data of the acquired overview images, a target structure is determined and the normal model is individualized for adaptation to the determined target structure. Scan parameters for control of the magnetic resonance tomography apparatus for acquisition of subsequent slice images dependent on the selected normal model and a diagnostic inquiry are then selected and individualized corresponding to the individualized normal model. The acquisition of the slice image exposures the ensues on the basis of these individualized scan parameters.
Owner:SIEMENS AG
Real-time tracking method of nonspecific target based on partitioning
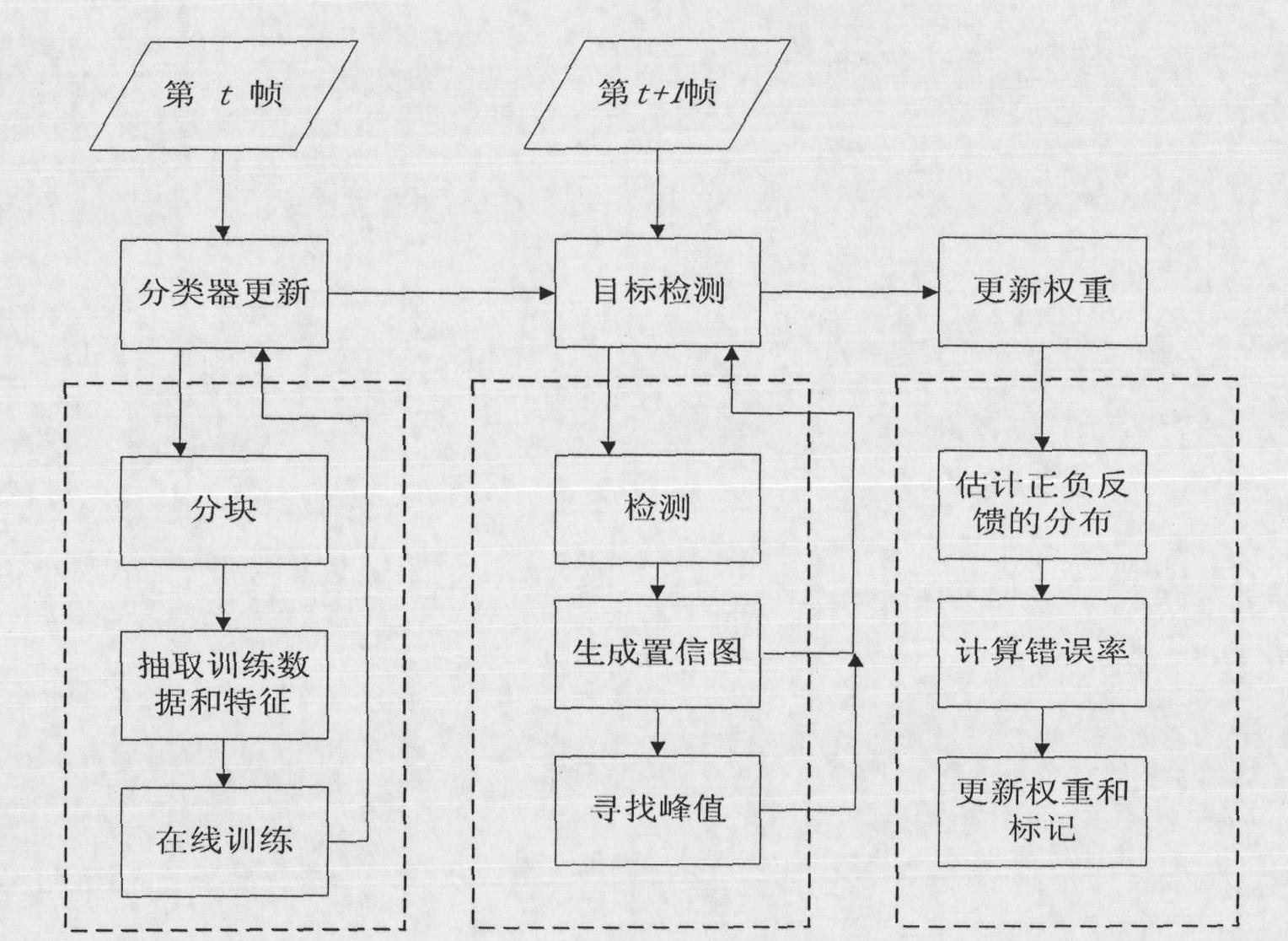
InactiveCN101867699AReduce the right to speakReduce distractionsTelevision system detailsImage analysisVideo monitoringComputation complexity
The invention relates to a real-time tracking method of a nonspecific target based on partitioning, comprising three steps of classifier updating, target detection and weight updating. In the method, the target region is divided into multiple blocks; a classifier is used for maintaining each block, and updating is conducted frame by frame; the detection result of each classifier is comprehensively considered to determine the position of the target in the new video frame. In the method, an automatic weight updating mechanism is designed, so as to enable the blocks which are relatively stable to have greater decision-making power over the judgment of results, thus reducing the influence of various interferences; and the tracking performance is better than multiple international published algorithms recently. In the method, changes of appearances of objects caused by various interferences can be captured and accurate tracking can be conducted; the method has universality on target objects in various shapes and types; the calculation has low complexity and can be processed at real time. The invention has wide application prospect in various occasions needing tracking techniques, such as video monitoring, automatic driving, man-machine interaction, intelligent traffic, robot, airborne early warning and the like.
Owner:UNIV OF SCI & TECH OF CHINA
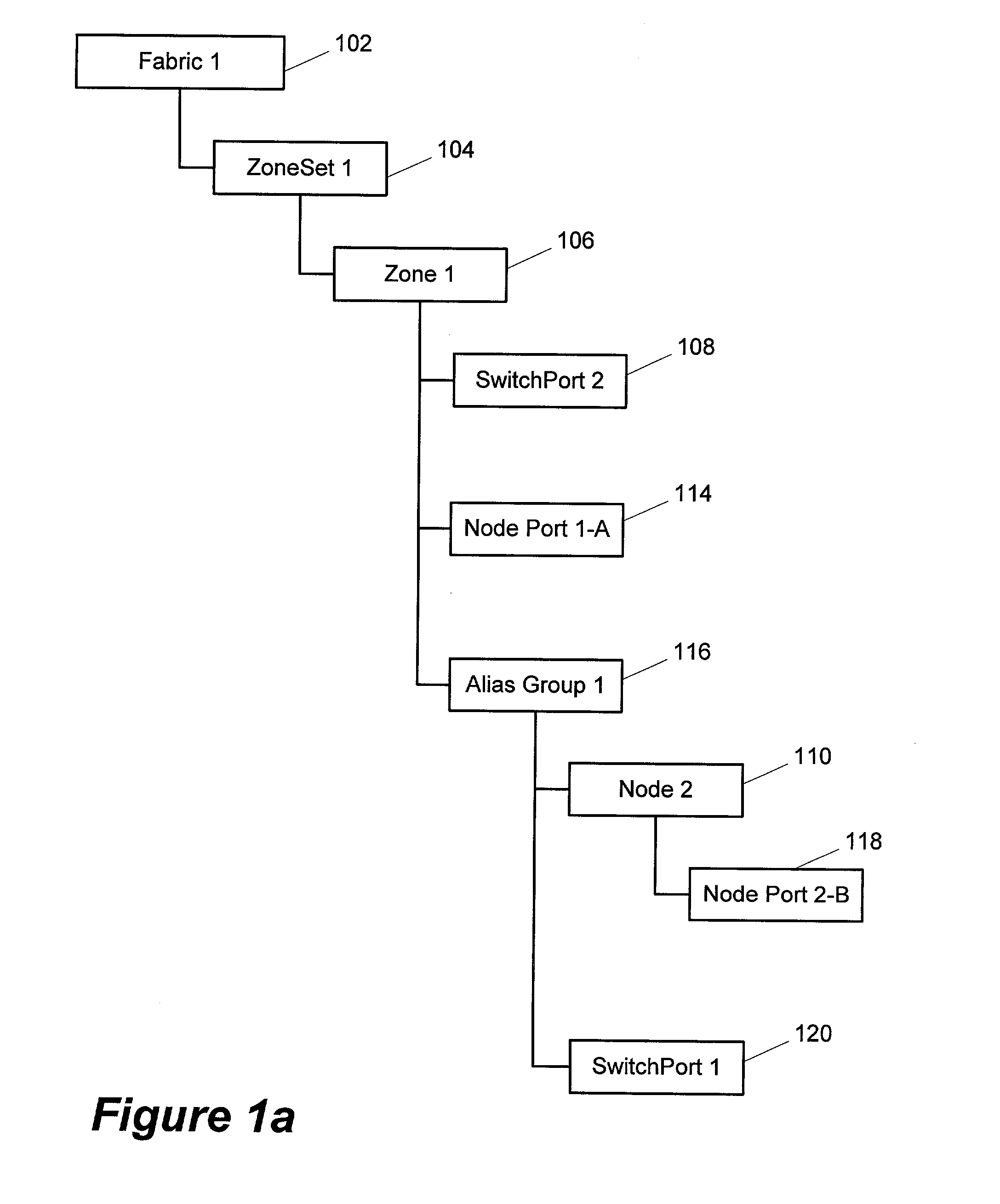
System and method for allocating unique zone membership
InactiveUS20030195956A1Risk minimizationMore complexInput/output to record carriersDigital computer detailsEngineeringIdentifying goals
The present disclosure describes a method and apparatus for ensuring the unique zoning membership representation in a network environment. In one aspect, the members of a container may be evaluated to determine whether any are subordinate to or children of a target member of the same container. The subordinate or child members may be removed from the container's configuration. Generally following the removal of any subordinate or child members of the target member, a determination may be made as to whether the target member is a child of or subordinate to any container members remaining in the container's configuration. If the target member is determined to be subordinate to or a child of a remaining container member, the target member may be removed from the container's configuration. Consequently, redundant member entries, unintentional communication paths and the complexities associated with creating a zoning configuration may be avoided.
Owner:CIPHERMAX
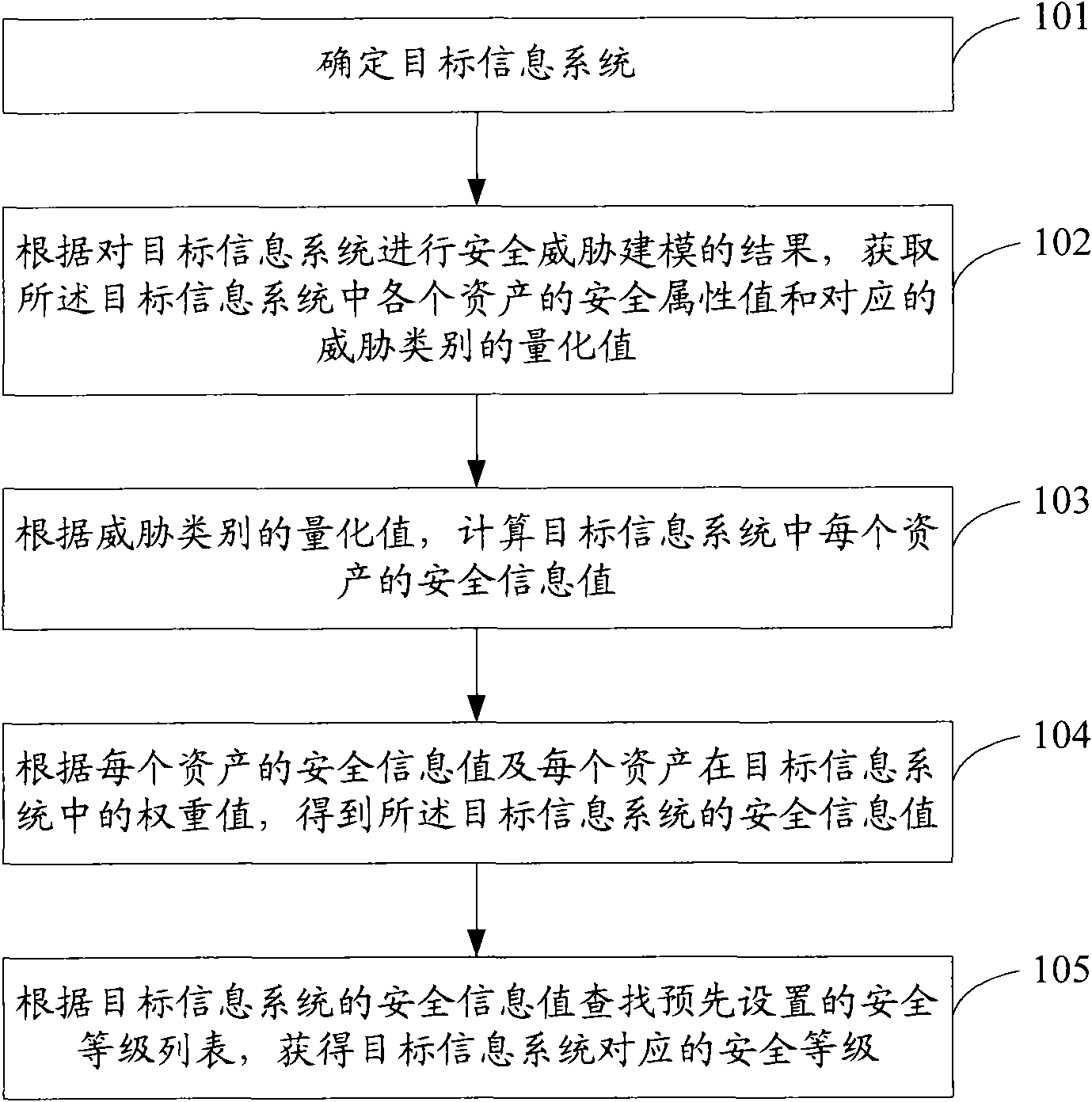
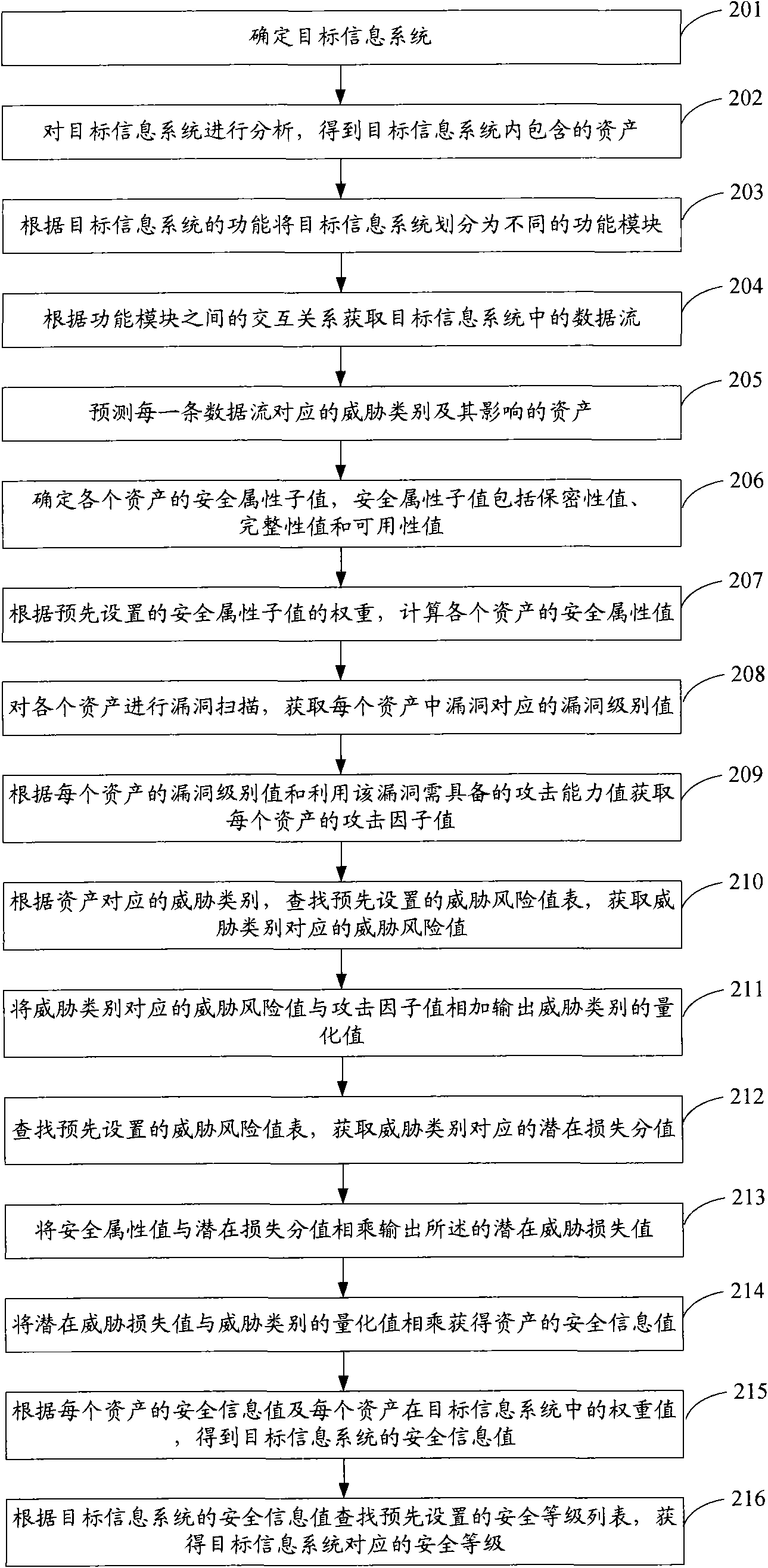
Method and device for conducting security identification on information system
InactiveCN101674302ASatisfy the requirements for security identificationInternal/peripheral component protectionTransmissionObjective informationSecurity properties
The embodiment of the invention discloses a method and a device for conducting security identification on an information system. The method includes the following steps: determining a target information system; according to the result of security threat modeling of the target information system, acquiring the security attribute value of each property in the target information system and the quantization value of the corresponding threat category; according to the quantization value of the threat category, calculating the security information value of each property in the target information system; according to the security information value of each property and the weight value of each property in the target information system, obtaining the security information value of the target information system; and according to the security information value of the target information system, searching for a preset security level list and obtaining the corresponding security level of the target information system. By quantizing the property, threat and leak in the information system and comprehensively considering the security risk in the information system, the embodiment meets the requirement of the information system on security identification.
Owner:BEIJING LEADSEC TECH
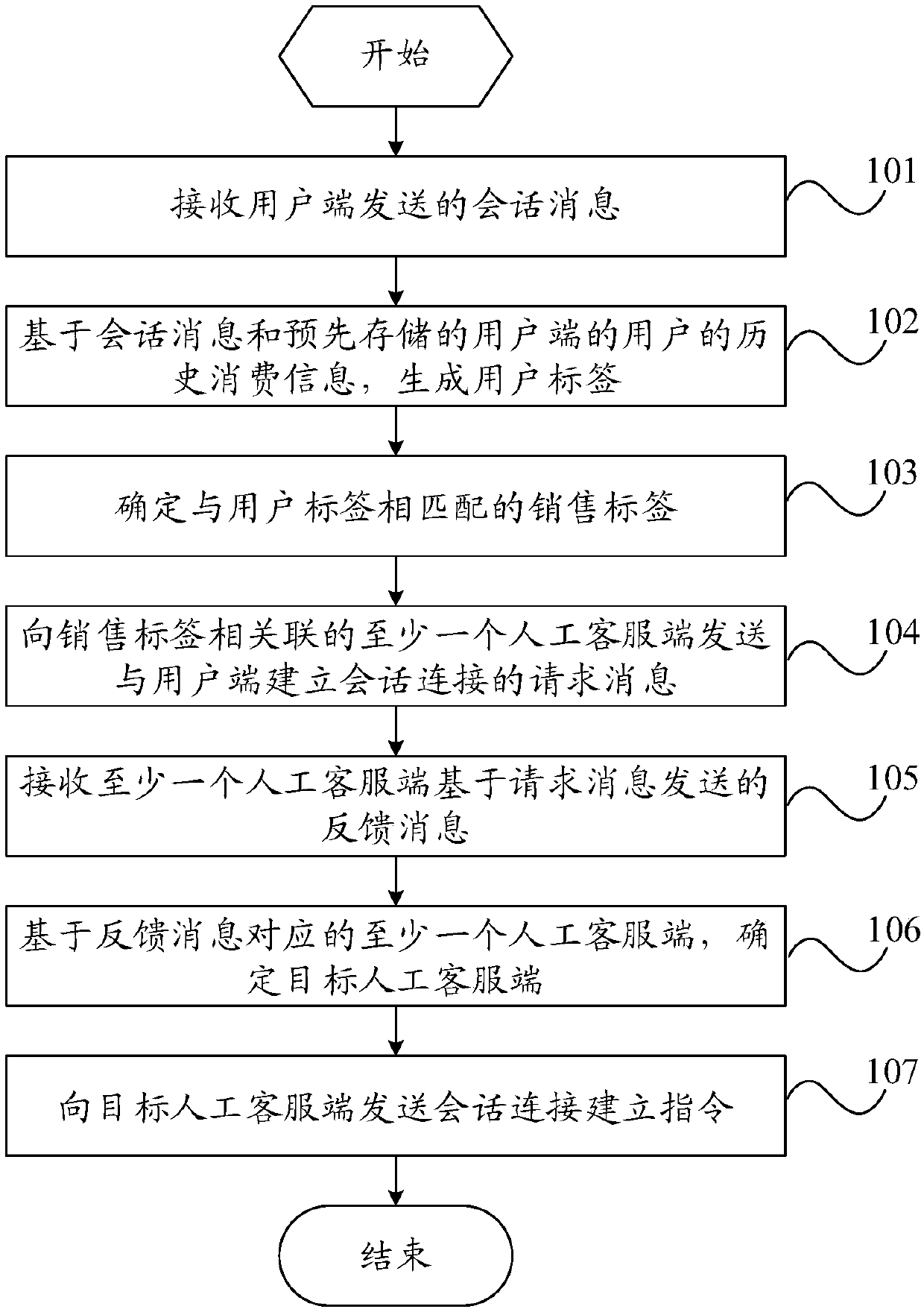
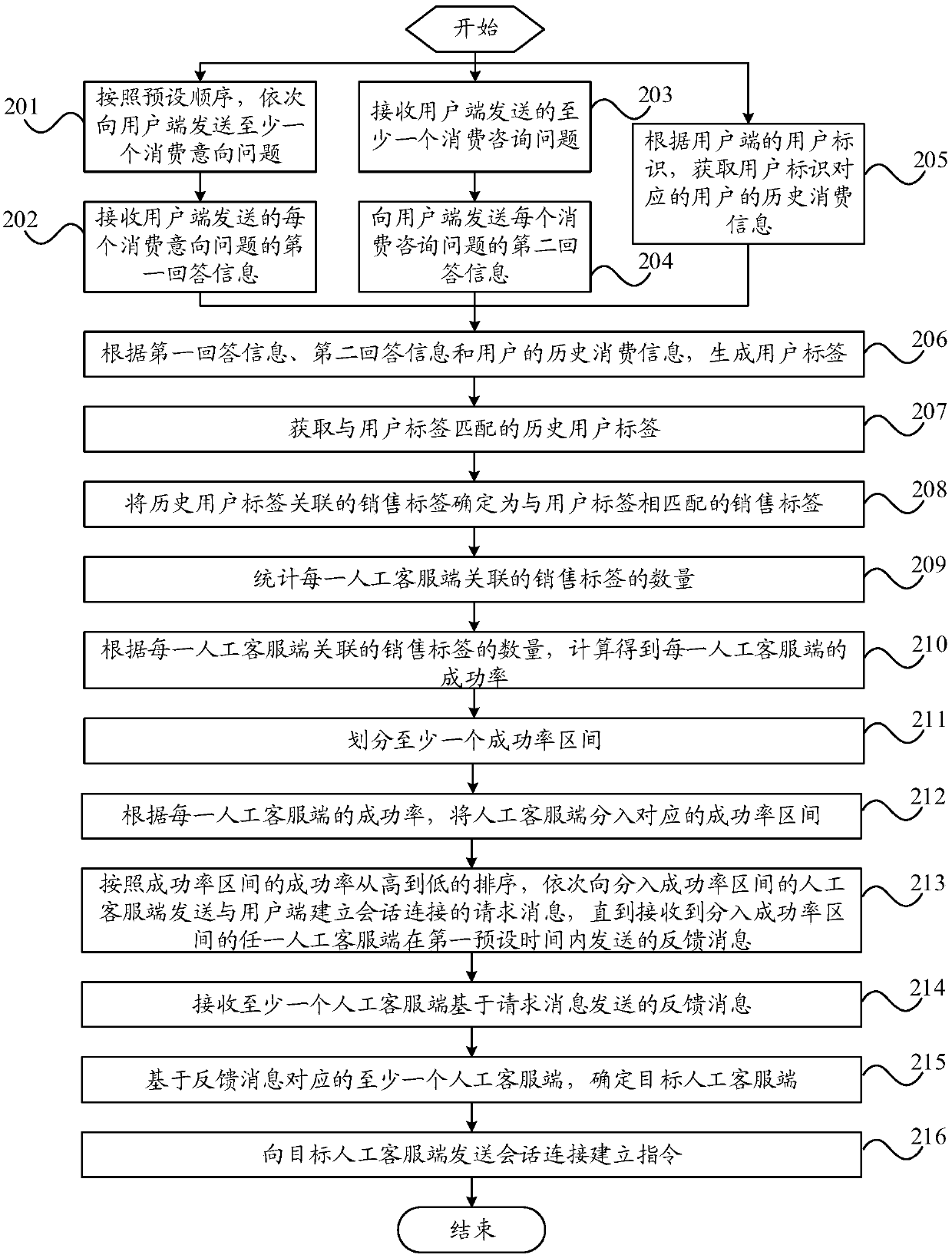
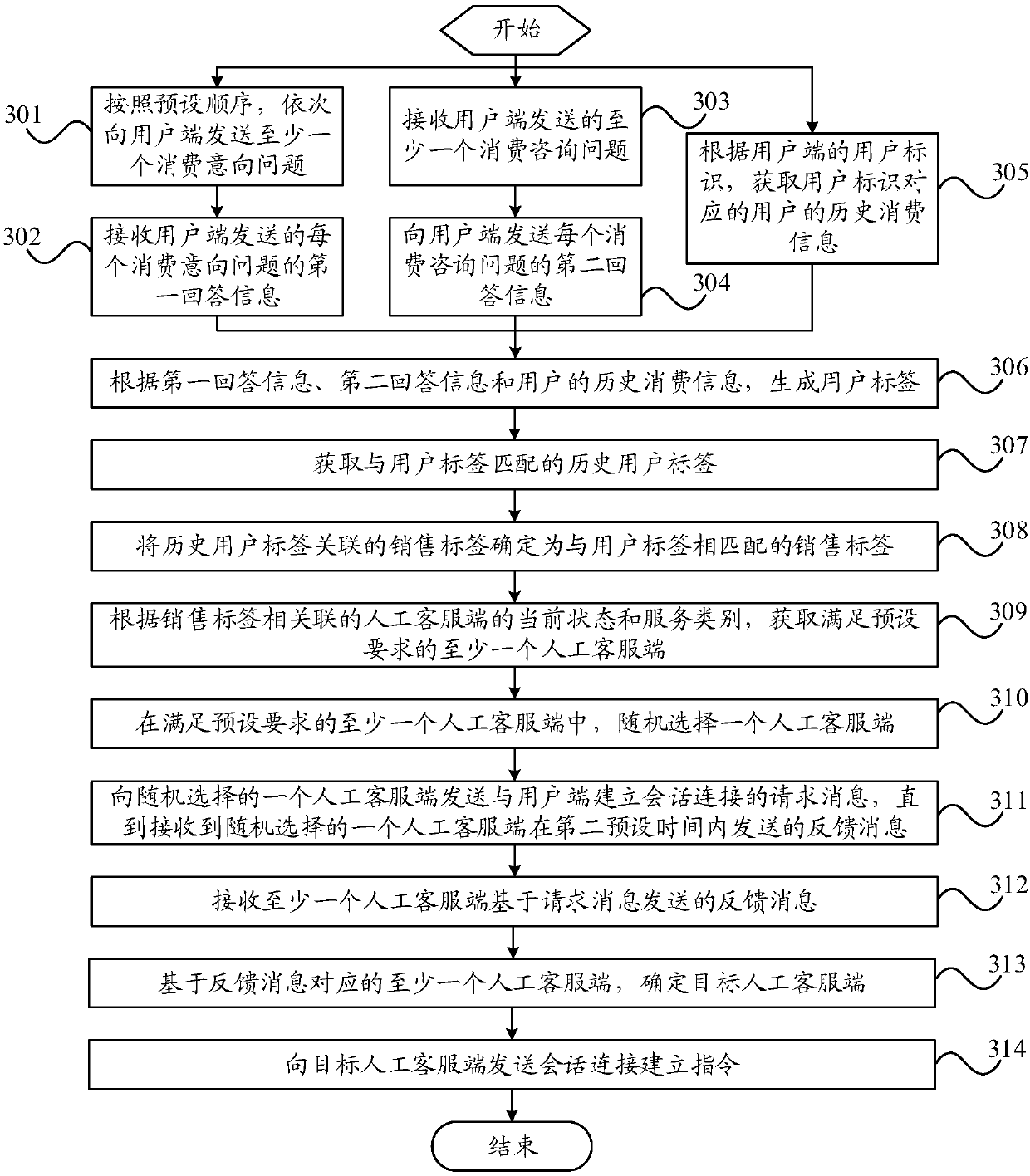
Marketing method, robot customer service side, staff customer service side and user side
Embodiments of the invention provide a marketing method, a robot customer service side, a staff customer service side and a user side. The method is applied to the robot customer service side and comprises the following steps of: receiving a session message sent by the user side; generating a user label on the basis of the session message and pre-stored history consumption information of a user ofthe user side; determining a marketing label matched with the user label; sending a request message for establishing session connection with the user side to at least one staff customer service sideassociated with the marketing label; receiving feedback message sent by the at least one staff customer service side on the basis of the request message; determining a target staff customer service side on the basis of the at least one staff customer service side corresponding to the feedback message; and sending a session connection establishing instruction to the target staff customer service side. According to the marketing method, the target staff customer service side is determined to market commodities or services to the user side, so that the marketing success rate is improved.
Owner:VIVO MOBILE COMM CO LTD
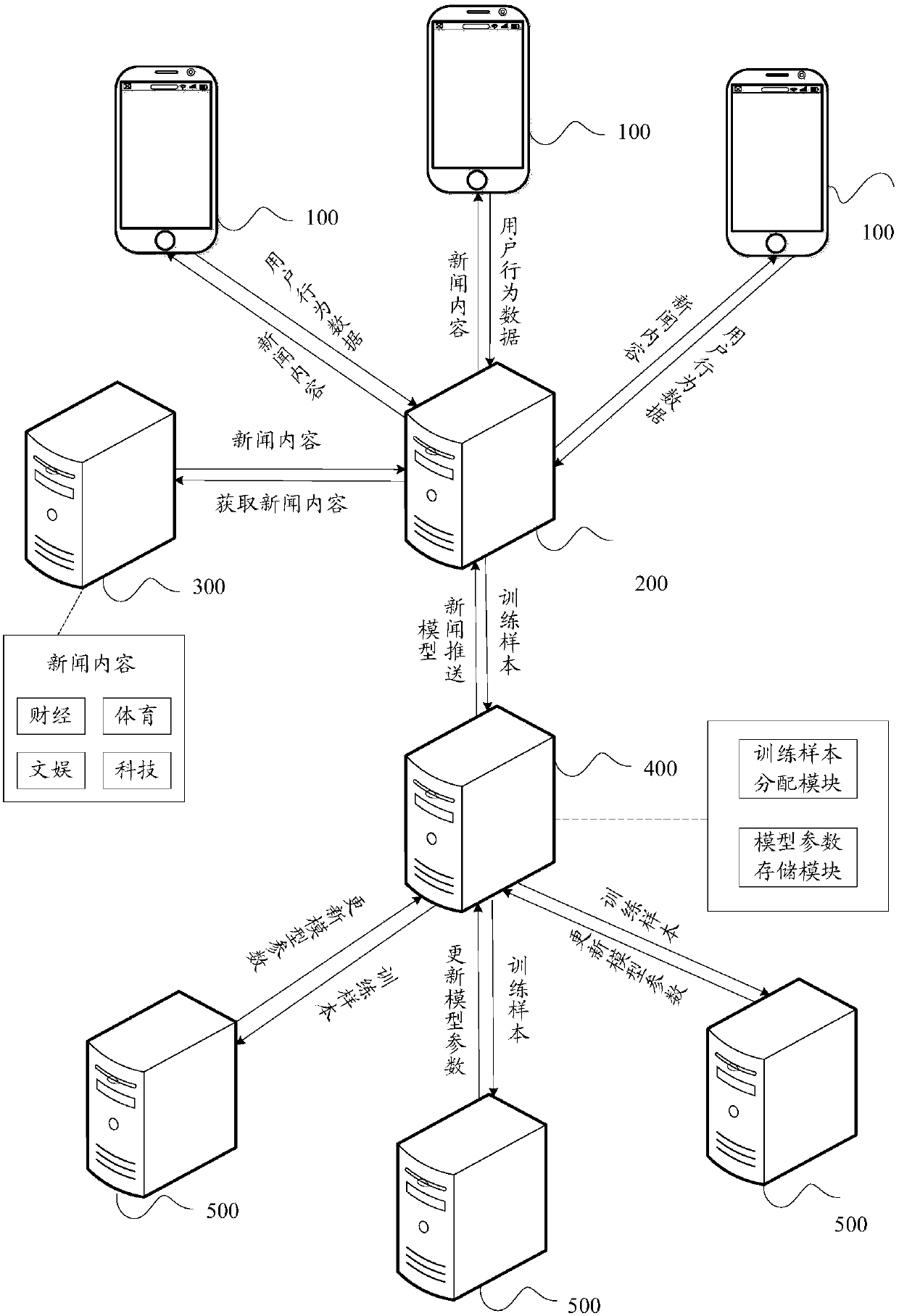
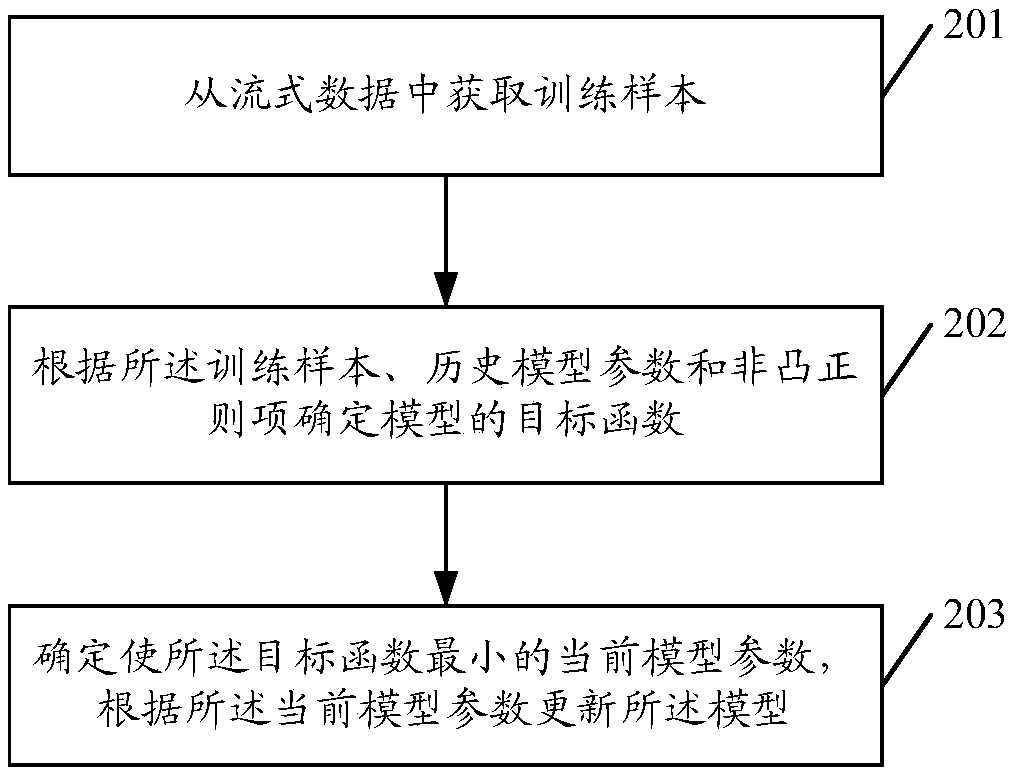
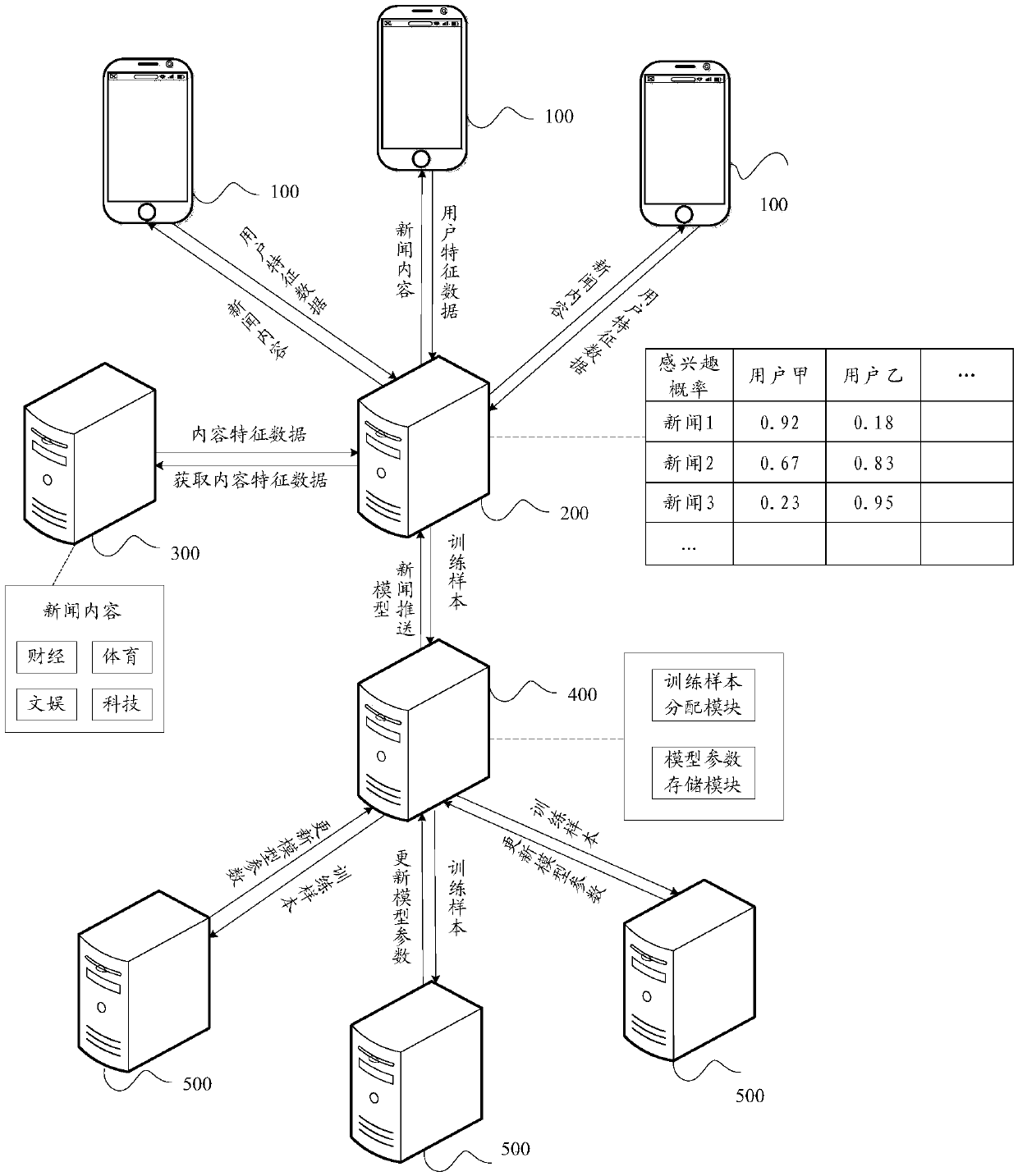
Online model training method, pushing method, device and equipment
ActiveCN110321422AImprove sparsityImprove forecast accuracyDigital data information retrievalCharacter and pattern recognitionHistorical modelStreaming data
The embodiment of the invention discloses an online model training method. The method comprises the steps of obtaining a training sample from streaming data, determining an objective function of the model according to the training sample, historical model parameters and non-convex regular terms, determining current model parameters enabling the objective function to be minimum, and updating the model according to the current model parameters. In the online training process, since the non-convex regular term is adopted to replace the L1 regular term for feature screening, the penalty deviationcan be reduced, effective features can be screened out, the sparsity is guaranteed, and the generalization performance of the model is improved. The invention further provides an information pushing method. The method comprises: obtaining user feature data and content feature data, based on the pushing model obtained by the online training model method, determining the probability that a target user is interested in target information according to the user feature data, the content feature data and the pushing model, and determining whether pushing is conducted or not according to the probability that the target user is interested in. The invention further provides an online model training device and an information pushing device.
Owner:TENCENT TECH (SHENZHEN) CO LTD
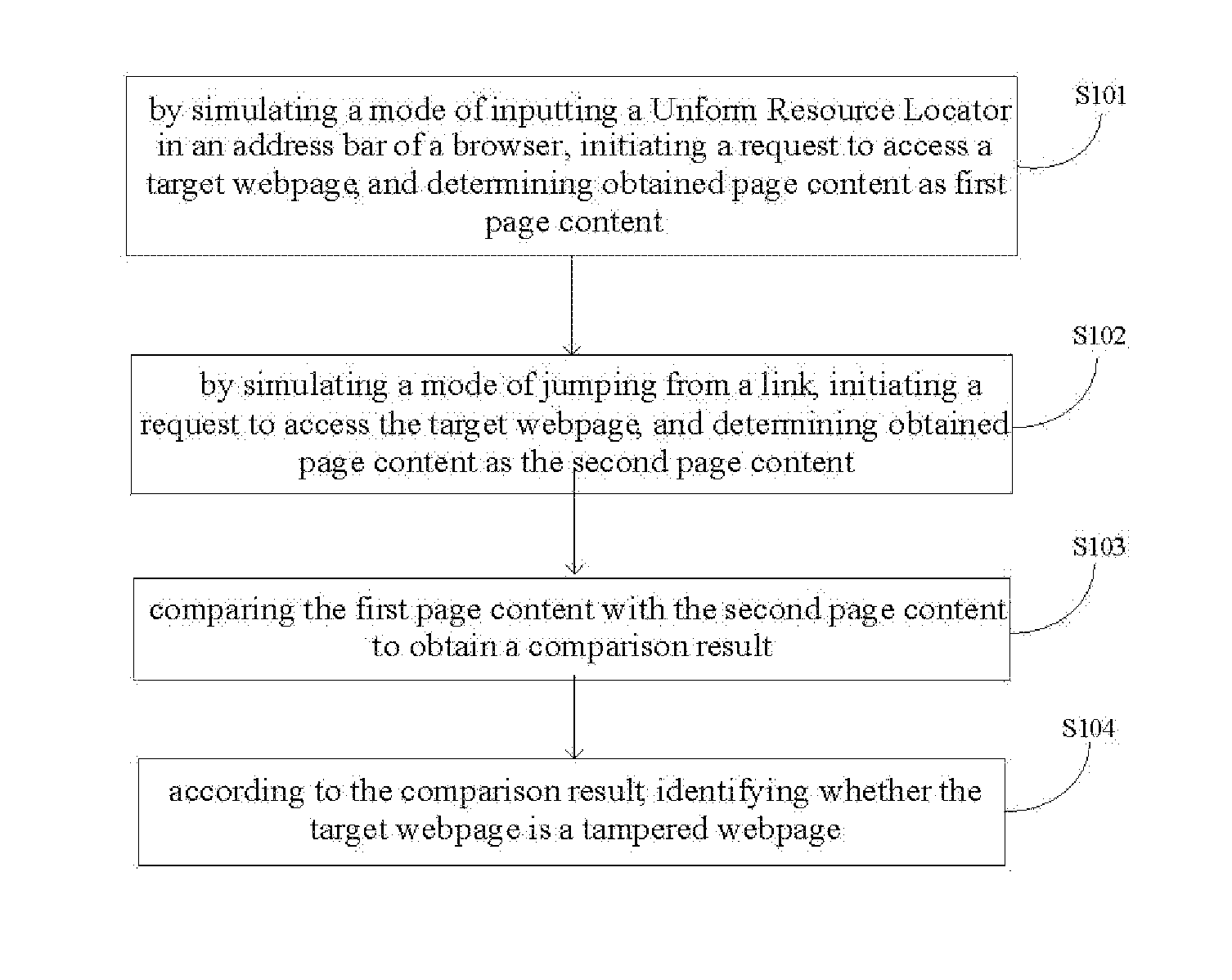
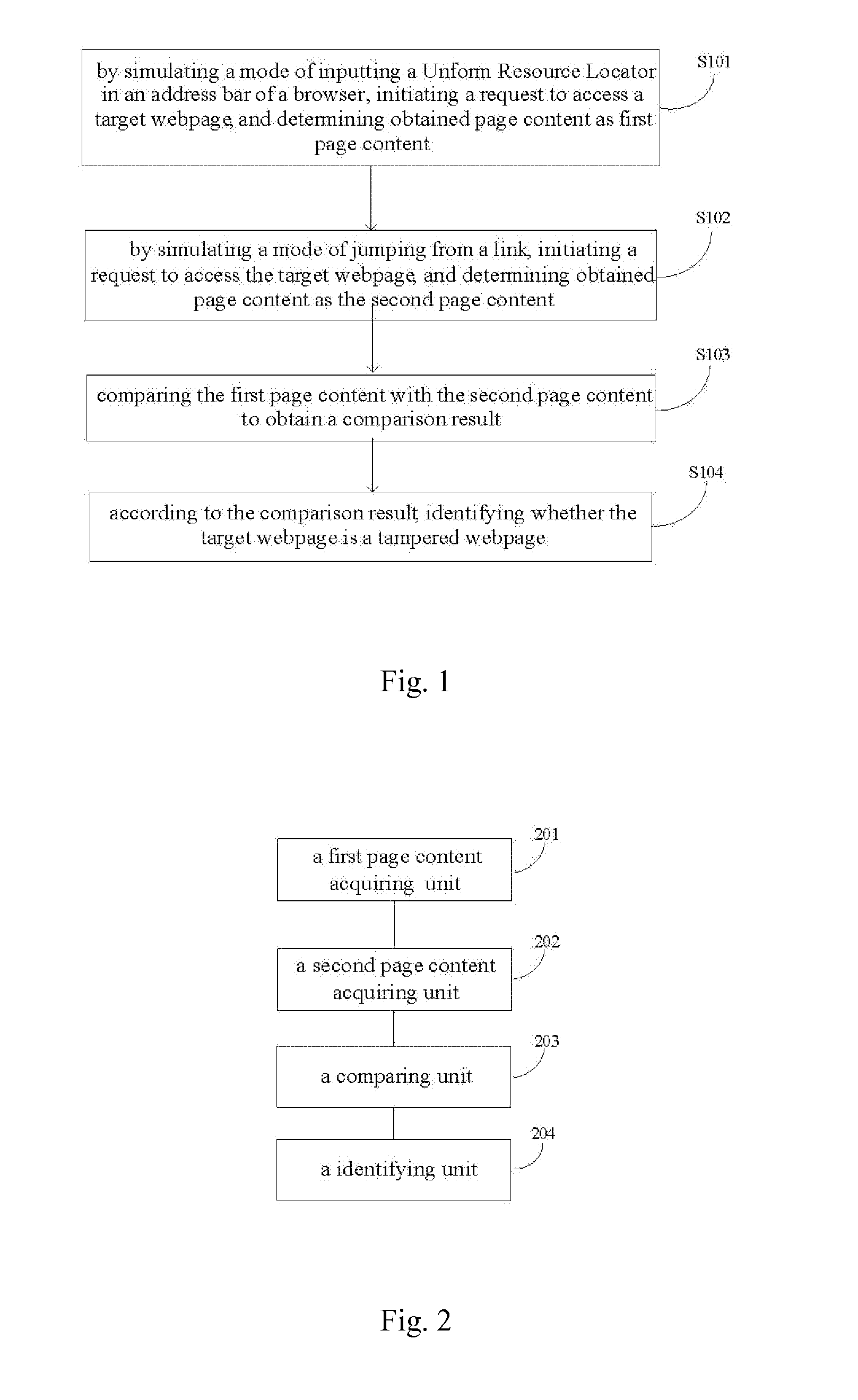
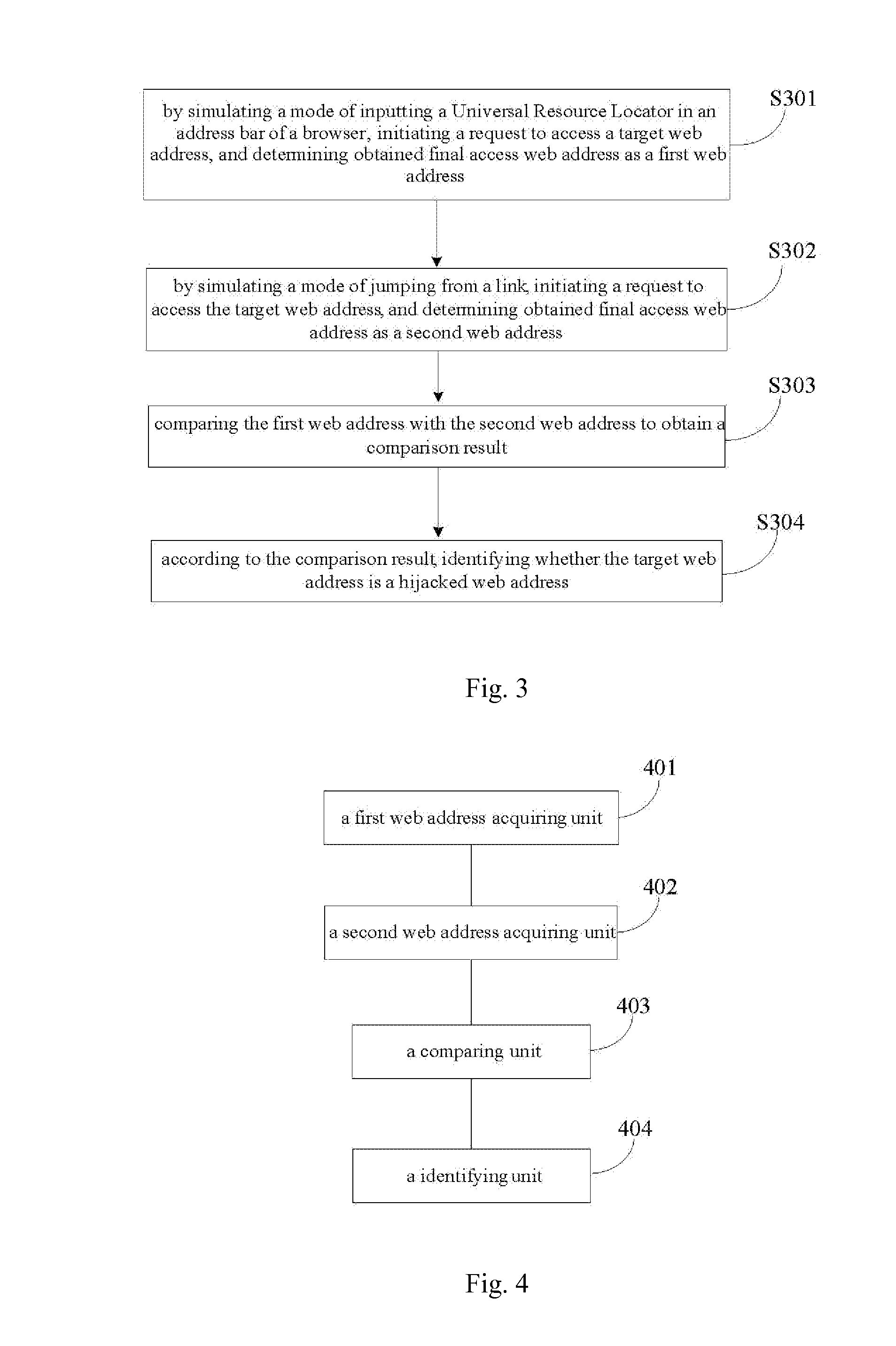
Methods and devices for identifying tampered webpage and inentifying hijacked web address
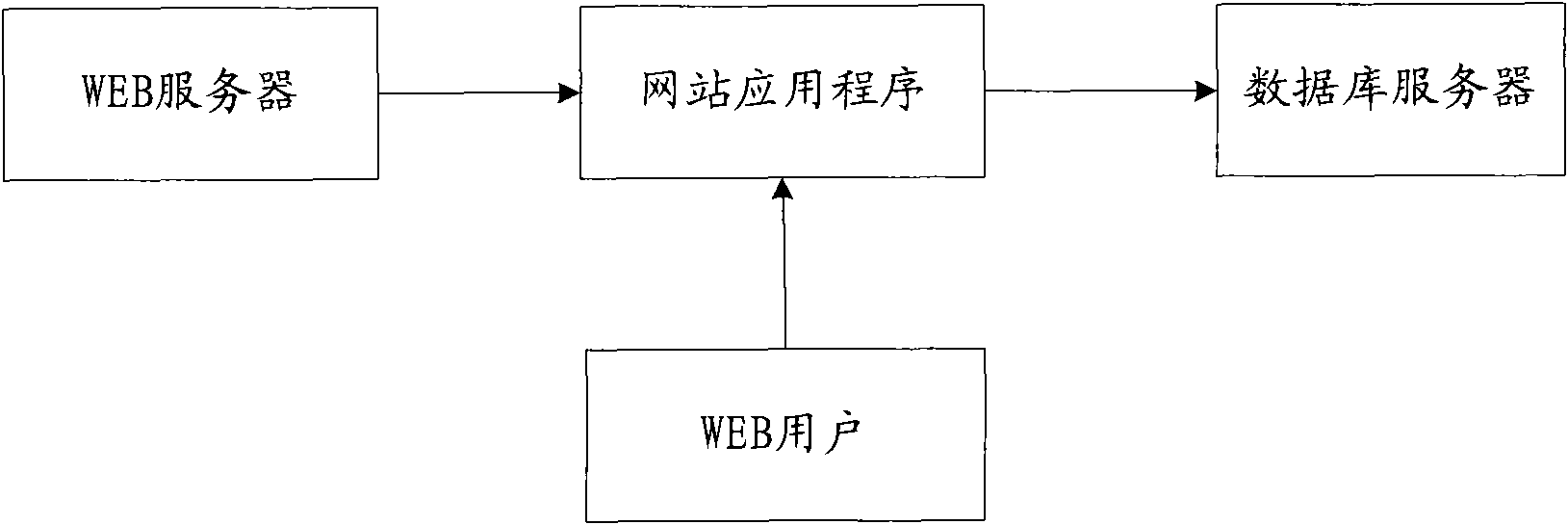
InactiveUS20140380477A1Overcome problemsEfficient identificationWeb data indexingMemory loss protectionService provisionAddress bar
Disclosed are methods and devices for identifying a tampered webpage and identifying a hijacked web address. The method for identifying a tampered webpage comprises: by simulating a mode of inputting a URL in an address bar of a browser, initiating a request to access a target webpage, and determining obtained page content as the first page content; by simulating a mode of jumping from a link, initiating a request to access the target webpage, and determining obtained page content as the second page content; comparing the first page content with the second page content to obtain a comparison result; and identifying, according to the comparison result, whether the target webpage is a tampered webpage. The present invention can effectively identify whether a target webpage is a tampered webpage, so that an effective means for determining whether a target webpage is tampered is provided to a user and computer services.
Owner:BEIJING QIHOO TECH CO LTD
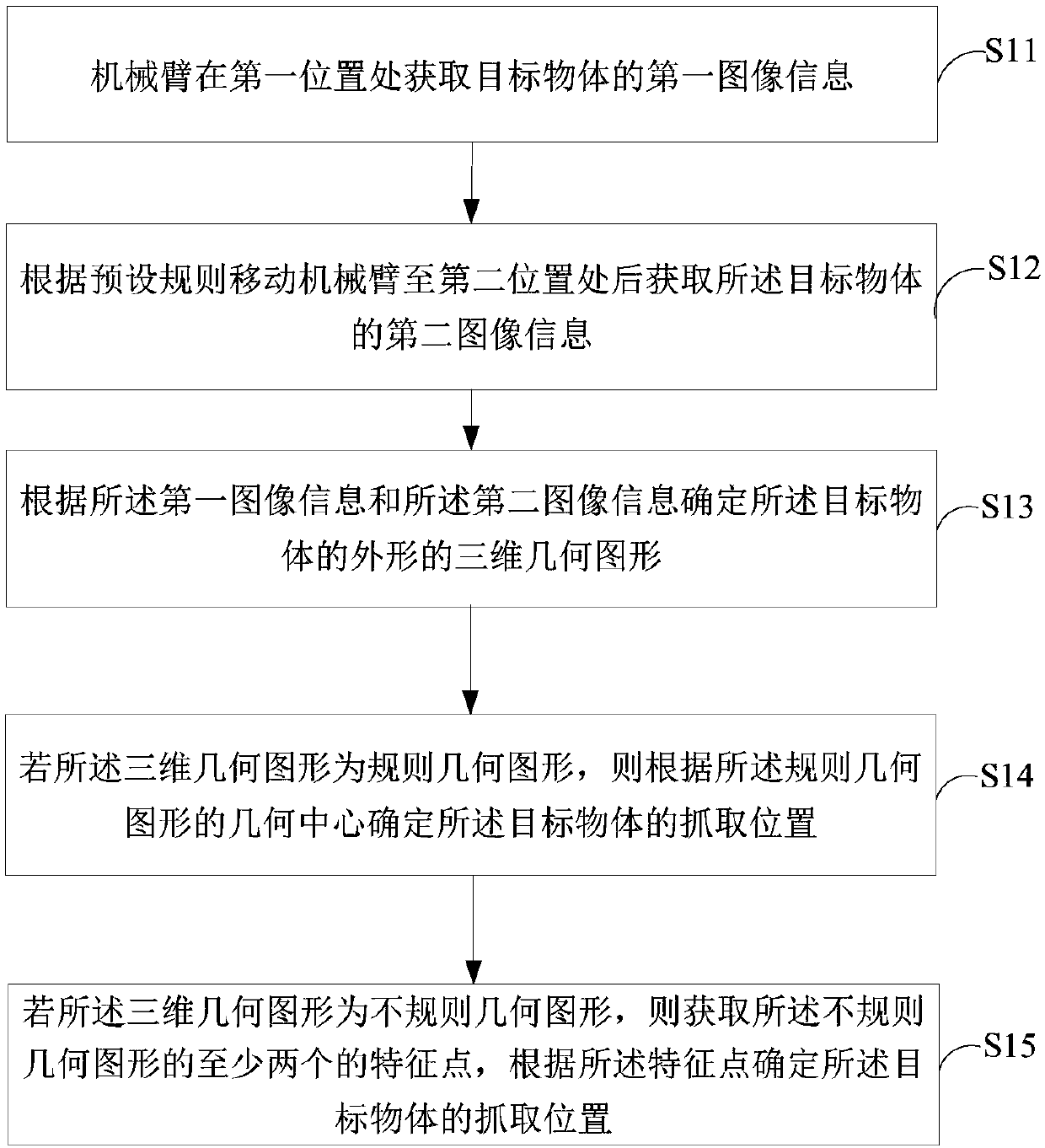
Grabbing position detecting method and device and mechanical arm
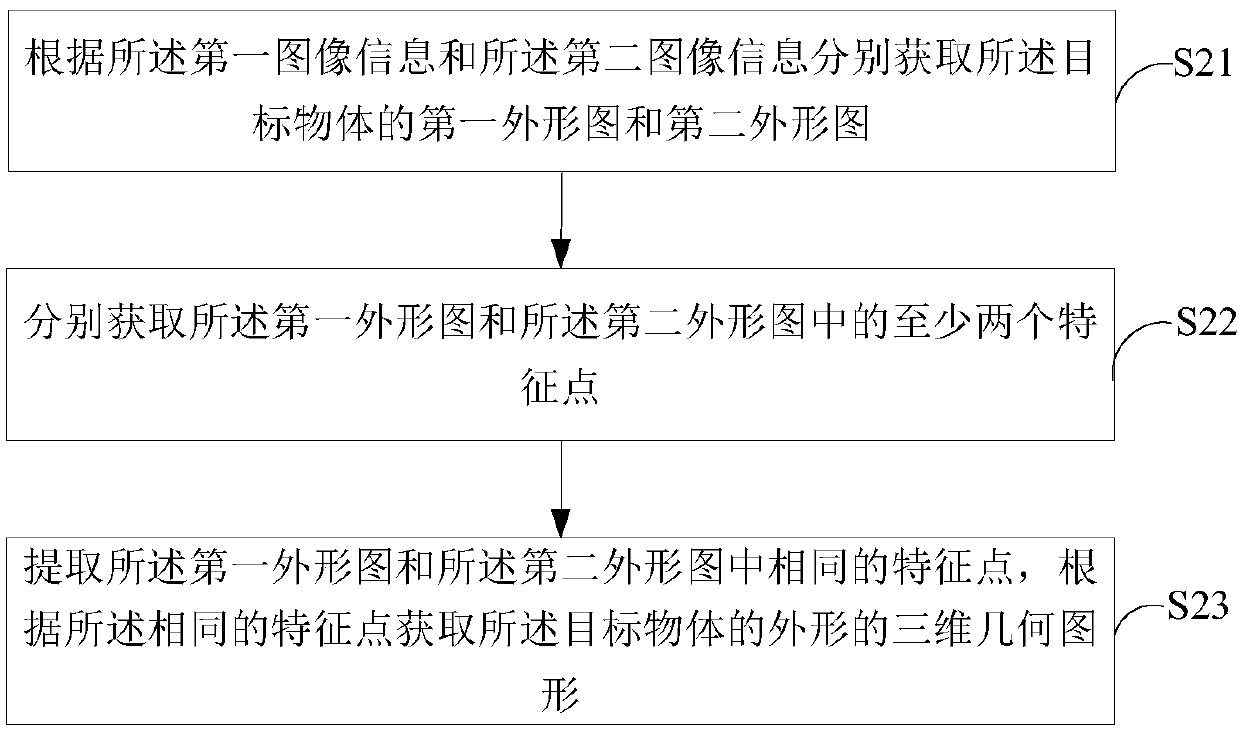
ActiveCN108044627AIncrease the chances of a successful crawlImprove accuracyProgramme-controlled manipulatorImage analysisGraphicsComputer vision
The invention is suitable for the technical field of intelligent detection, and provides a grabbing position detecting method and device and a mechanical arm. The method includes the steps that the mechanical arm obtains first image information and second image information of a target object at the first position and the second position correspondingly, and a three-dimensional geometric figure ofthe appearance of the target object is determined; if the three-dimensional geometric figure is a regular geometric figure, the grabbing position of the target object is determined according to the geometric center of the geometric figure; or at least two feature points of an irregular geometric figure are obtained, and the grabbing position of the target object is determined according to the feature points. In the process, according to the image information, obtained at different positions, of the target object, three-dimensional geometric figure of the appearance of the target object is determined, and the accuracy of the detected appearance of the target object is improved; and different methods are adopted for target objects with different appearances for determining the grabbing position, the appropriate grabbing positions are found quickly and accurately according to self features of the target objects, and the successful grabbing rate of the mechanical arm is improved.
Owner:SHENZHEN YUEJIANG TECH CO LTD
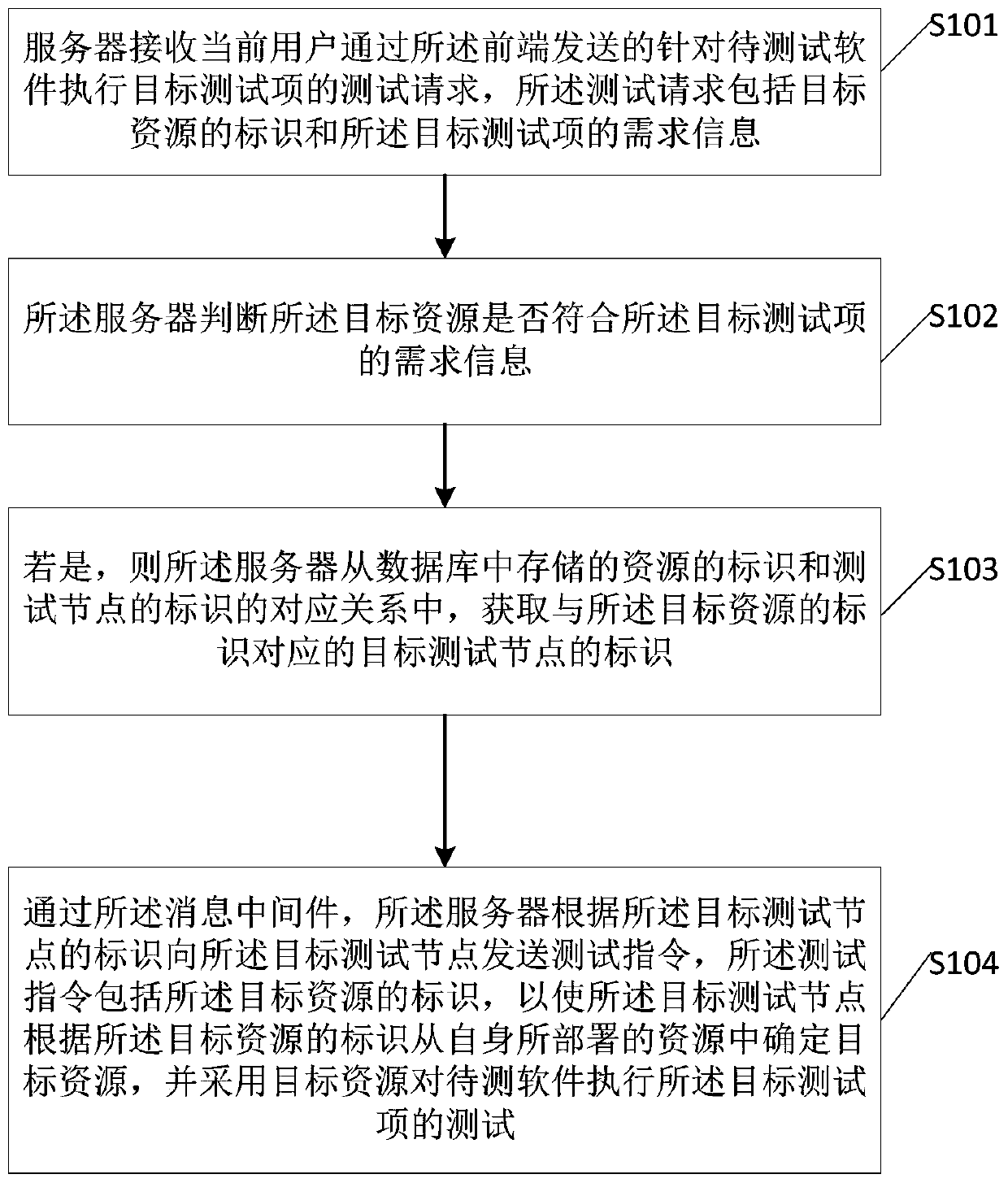
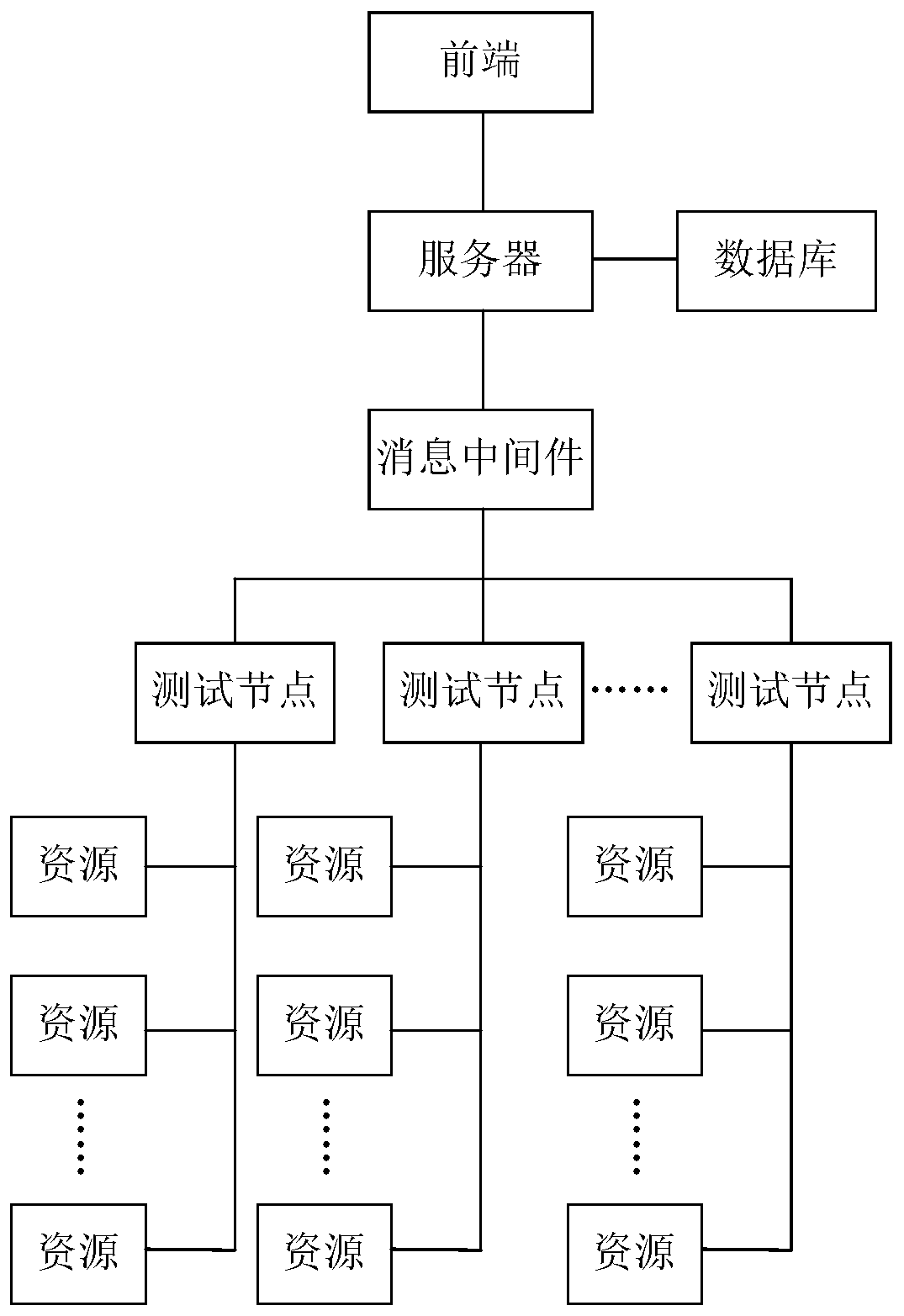
Software testing method and software testing system based on distributed testing node cluster
The invention provides a software testing method and a software testing system based on a distributed testing node cluster, and the method comprises: a server receiving a testing request which is sentby a current user through a front end and is used for executing a target testing item for to-be-tested software, and the testing request comprising an identifier of a target resource and demand information of the target testing item; the server judging whether the target resource meets the demand information of the target test item or not; if yes, the server obtaining an identifier of a target test node corresponding to the identifier of the target resource from a corresponding relation between the identifier of the resource stored in the database and the identifier of the test node; througha message-oriented middleware, the server sending a test instruction to the target test node according to the identifier of the target test node, wherein the test instruction comprises the identifierof the target resource, so that the target test node determines the target resource from the resources deployed by the target test node according to the identifier of the target resource, and tests the target test item on the to-be-tested software by adopting the target resource, so that the software test efficiency is improved.
Owner:合肥移瑞通信技术有限公司
Log data processing method, system and device and storage medium
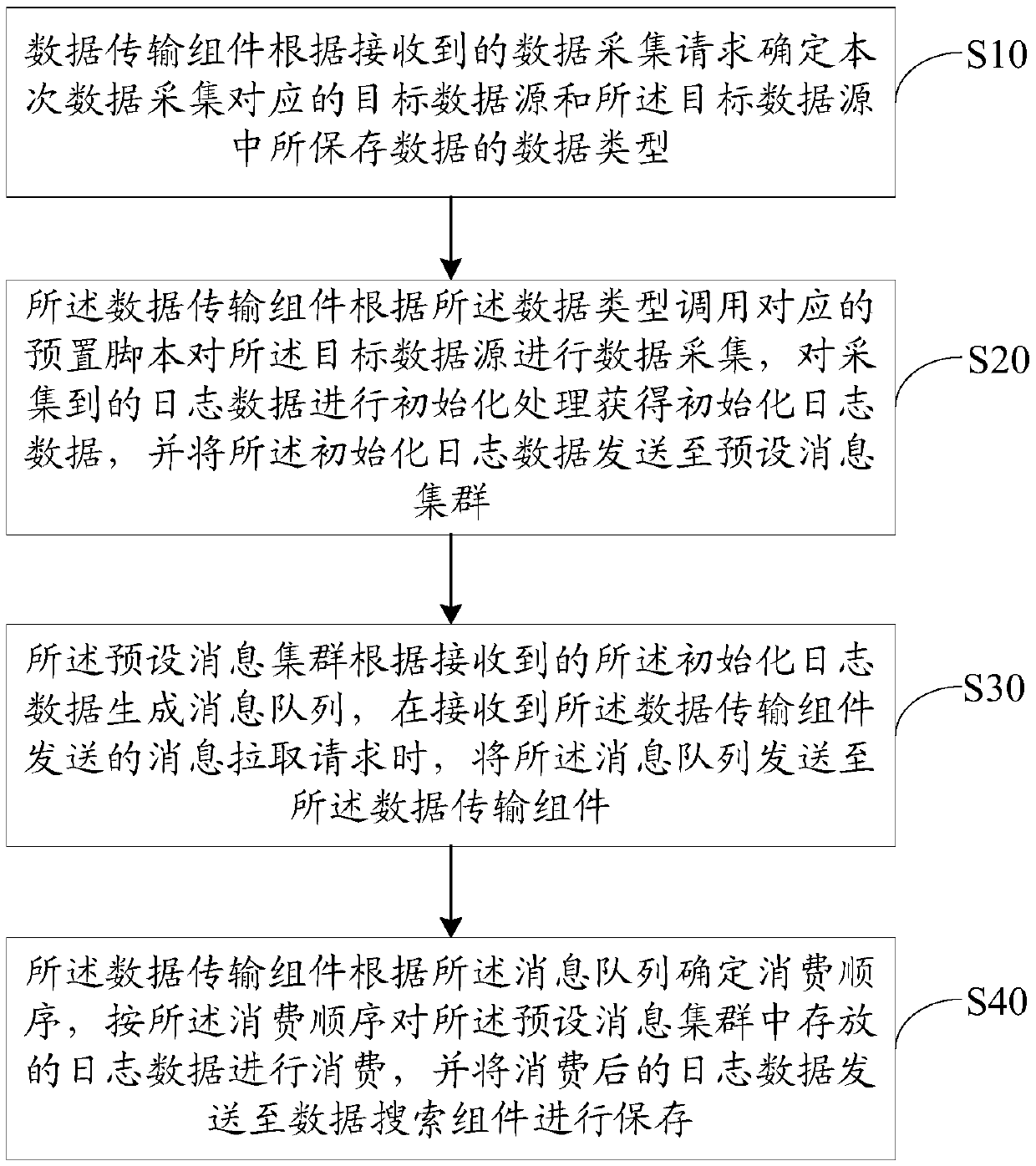
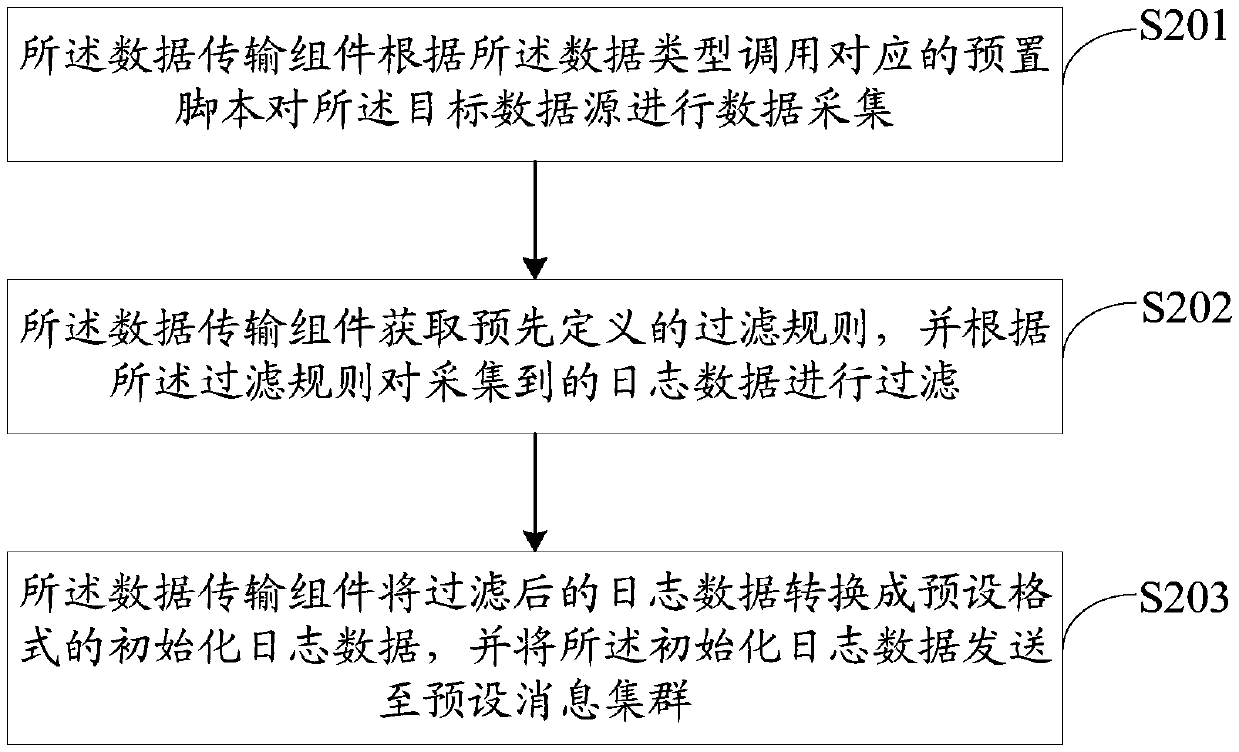
PendingCN109684370ARealize acquisitionRealize diverse collectionWeb data retrievalData switching networksData acquisitionData store
The invention discloses a log data processing method, System, device and storage medium, The method comprises the following steps: a data transmission component determines a target data source and a data type of data in the target data source according to a data acquisition request, calls a preset script according to the data type to perform data acquisition, performs initialization processing onacquired log data and sends the log data to a preset message cluster; The preset message cluster generates a message queue according to the initialization log data and sends the message queue to the data transmission component; The data transmission component determines a consumption sequence according to the message queue; and consuming the log data stored in the preset message cluster accordingto the consumption sequence. According to the log data collecting method and device, the data source log data are collected through the data searching assembly and the consumed data are stored throughthe data searching assembly, and the corresponding scripts are called according to the data types of the data stored in the data source to collect the data source log data, so that the coverage of data collection is increased, and diversified collection of the log data is achieved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
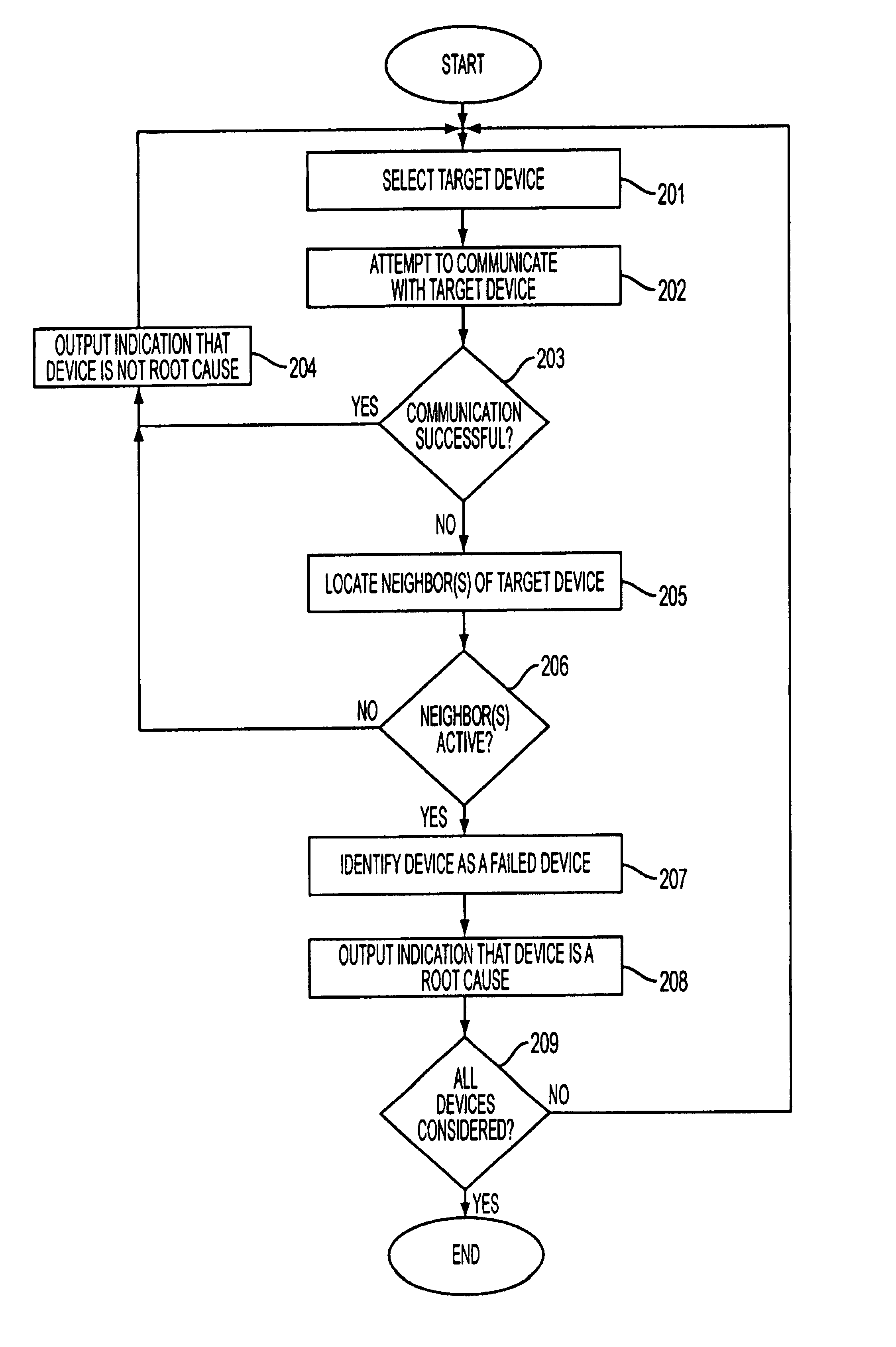
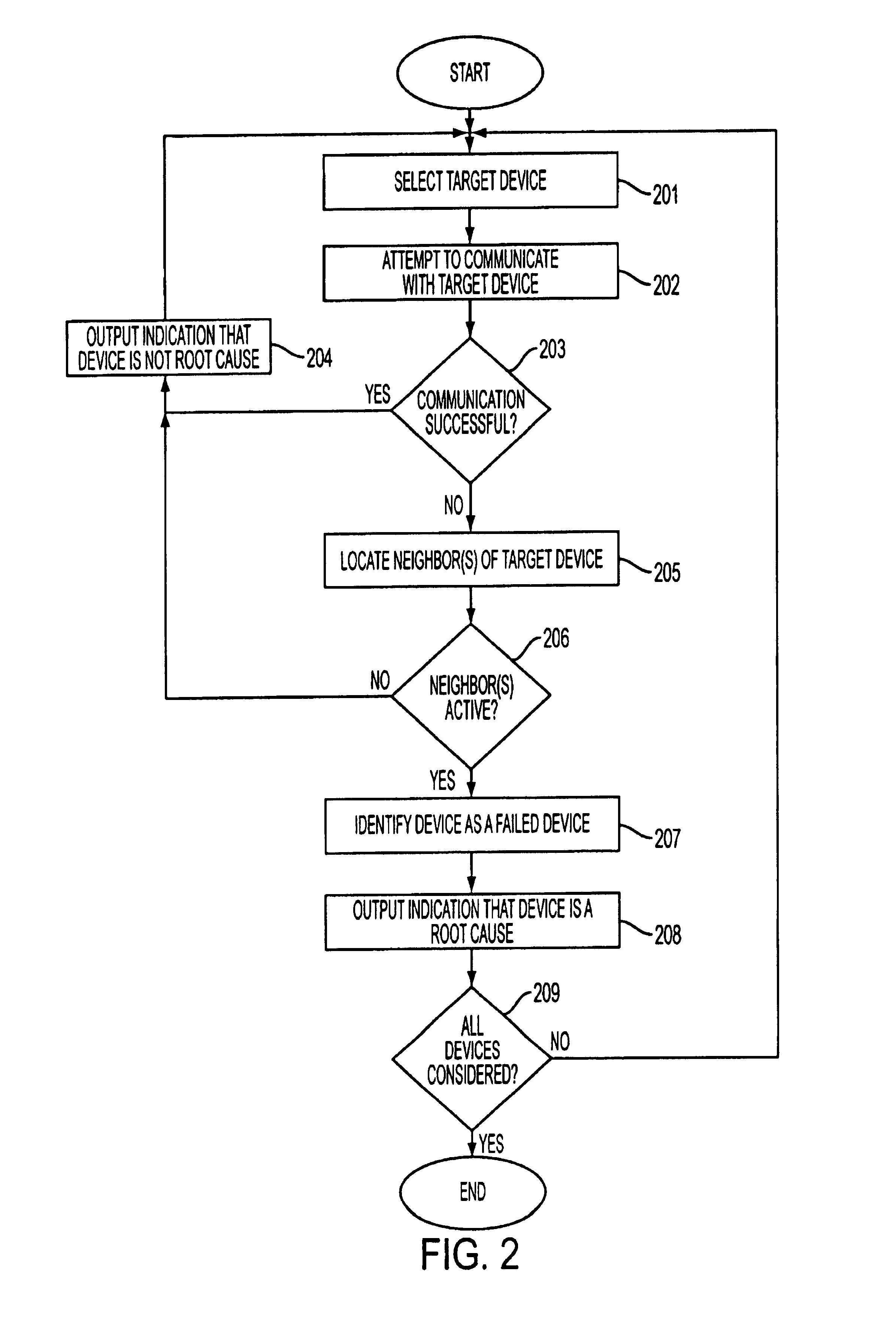
Identifying a failed device in a network
InactiveUS7287192B1Little informationNon-redundant fault processingTransmissionTelecommunicationsIdentifying goals
Owner:COMP ASSOC THINK INC
Identity authentication method and device and mobile terminal
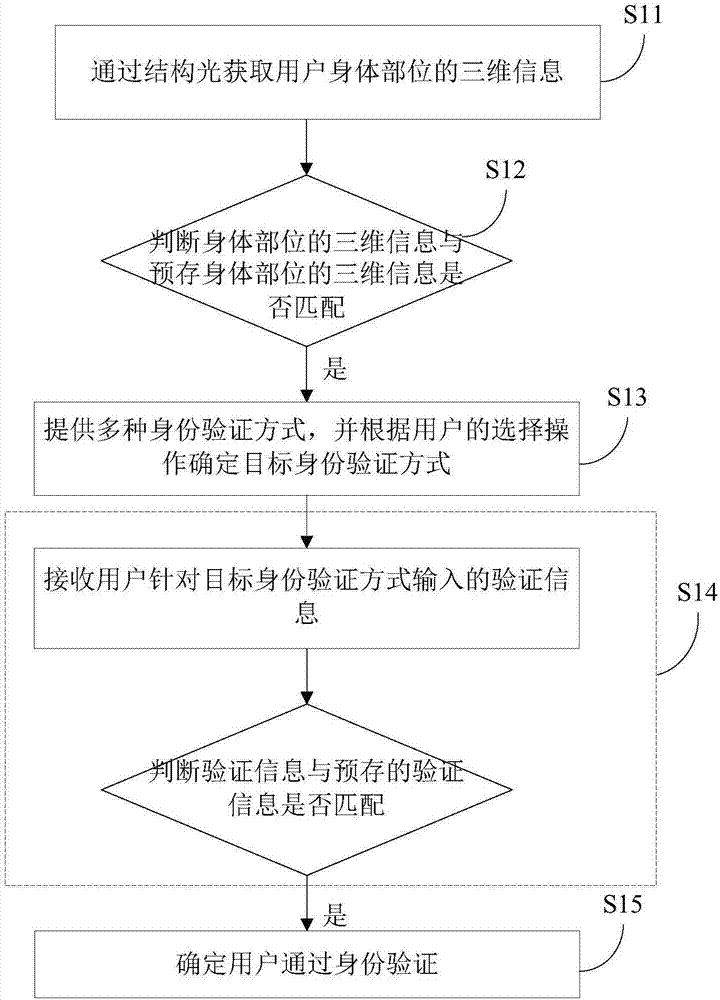
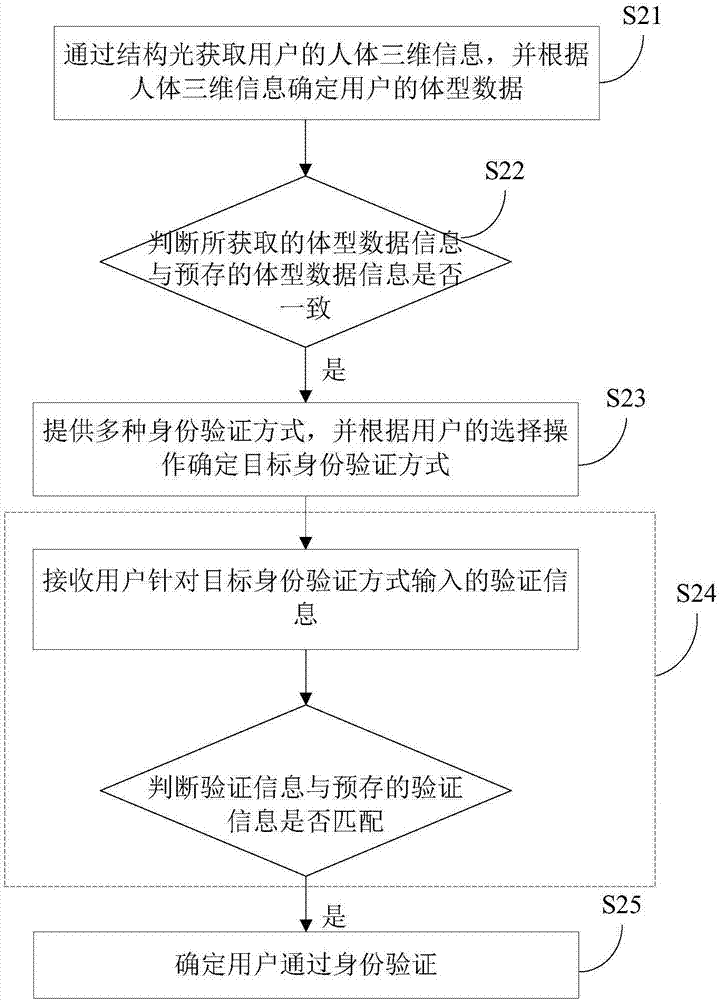
InactiveCN107277053AAuthentication is implemented accuratelyAvoid the risk of being easily stolen and disguisedBiometric pattern recognitionTransmissionComputer terminalIdentifying goals
The invention provides an identity authentication method and device and a mobile terminal. The method comprises the steps that the three-dimensional information of a body part of a user is acquired through structured light; whether the three-dimensional information of the body part matches the pre-stored three-dimensional information of the body part is determined; if the three-dimensional information of the body part matches the pre-stored three-dimensional information of the body part, a variety of identity authentication methods are provided, and the target identity authentication method is determined according to the selection operation of a user; authentication information input by a user for the target identity authentication method is received, and whether the authentication information matches pre-stored authentication information is further determined; and if the authentication information matches the pre-stored authentication information, the user passes identity authentication. According to the identity authentication method provided by the embodiment of the invention, the identity authentication of the user is accurately realized through the combination of three-dimensional authentication of the user identity part and other authentication methods; the risk of being stolen and disguised of authentication through biometric information such as fingerprints, irises and the like is avoided; and the safety is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Smart mobile law enforcement system and method
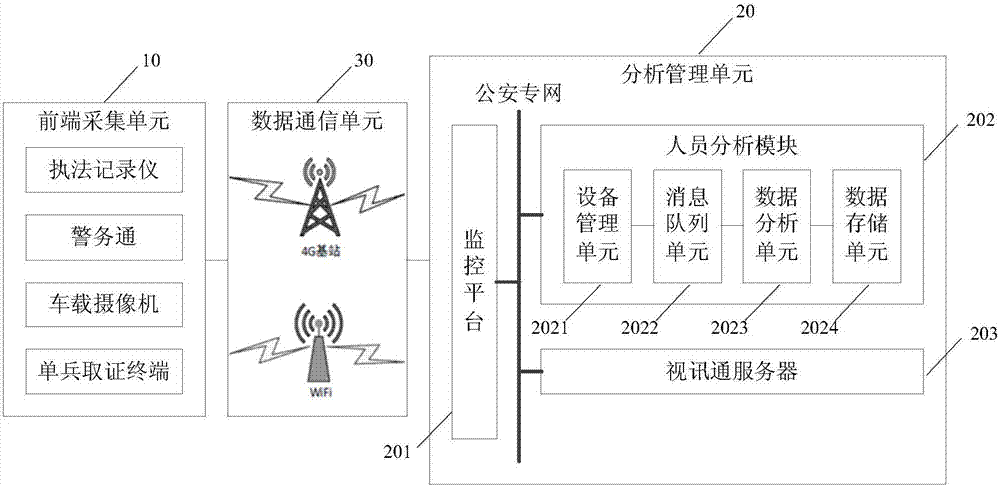
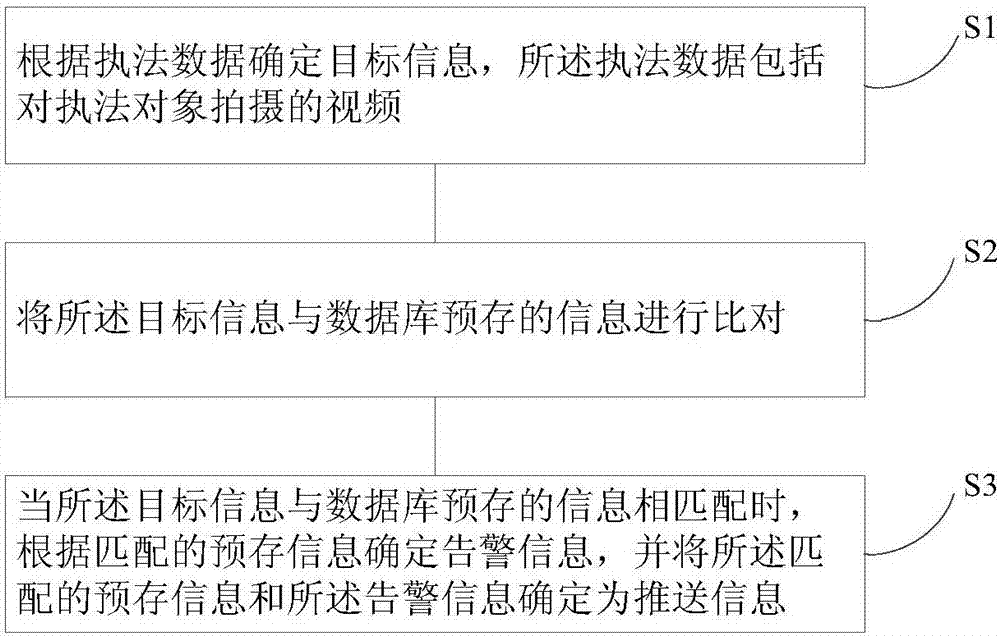
InactiveCN107220633ARealize automated queryImprove portabilityCharacter and pattern recognitionClosed circuit television systemsManagement unitHigh effectiveness
The invention provides a smart mobile law enforcement system and method. The smart mobile law enforcement system comprises a front-end acquisition unit for acquiring law enforcement data including video shot for an object of law enforcement, an analyzing and management unit for receiving and storing the law enforcement data, determining target information according to the law enforcement data, and comparing the target information with the information stored in the database in advance. When the target information matches with the information stored in the database in advance, alarm information is determined according to the matched information stored in the database in advance, and the matched information stored in the database in advance and the alarm information are determined to be pushing information and pushed to the front-end acquisition unit. The smart mobile law enforcement system and method improves the mobility and smart level for law enforcement by polices. The whole law enforcement process is recorded through video, and personal information in the video is analyzed and identified. Automatic query of target information is achieved, interrogating and examining time for law enforcement by polices can be shortened, and justice and high effectiveness of mobile law enforcement can be ensured.
Owner:SUZHOU KEDA TECH +1
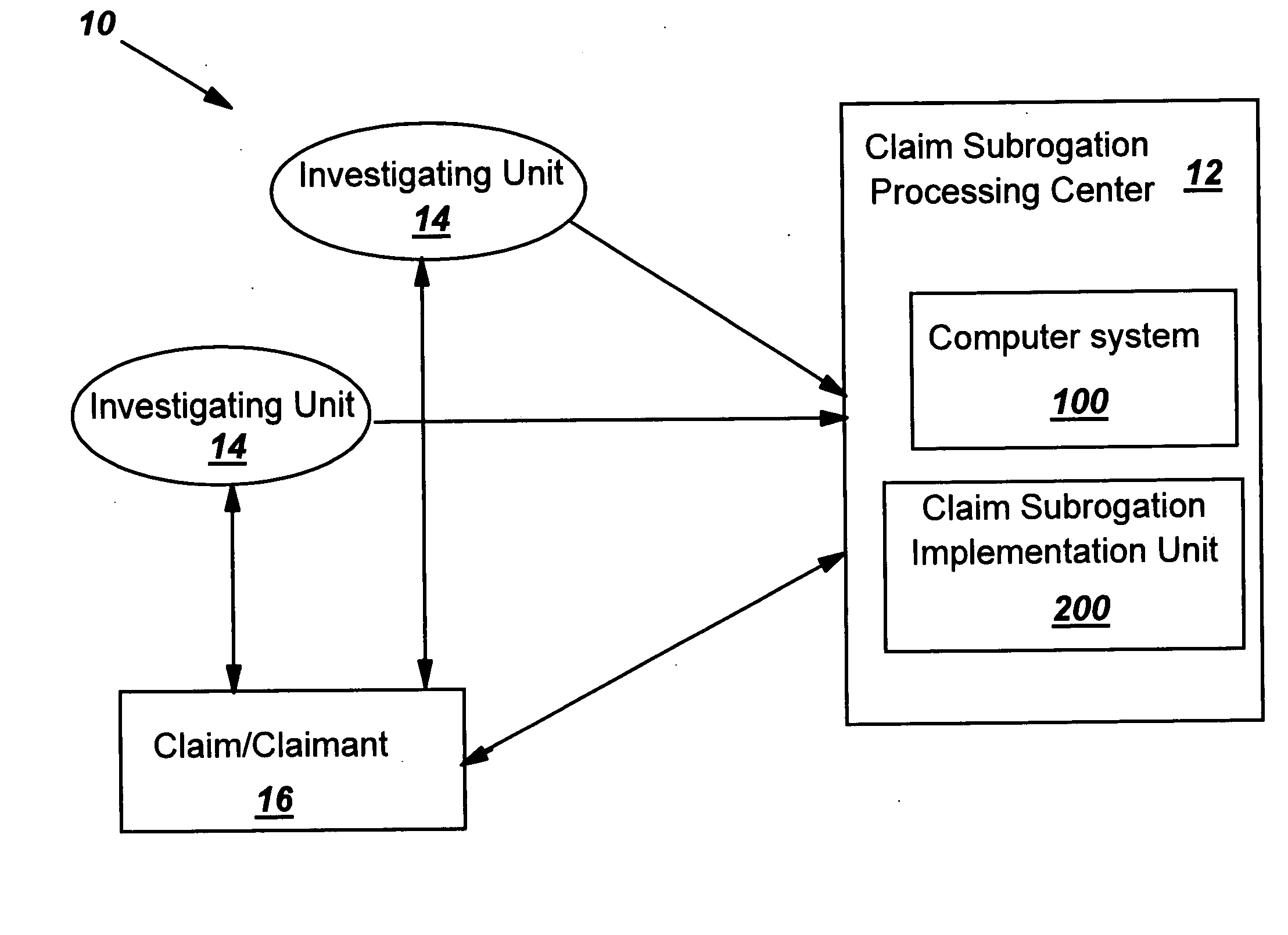
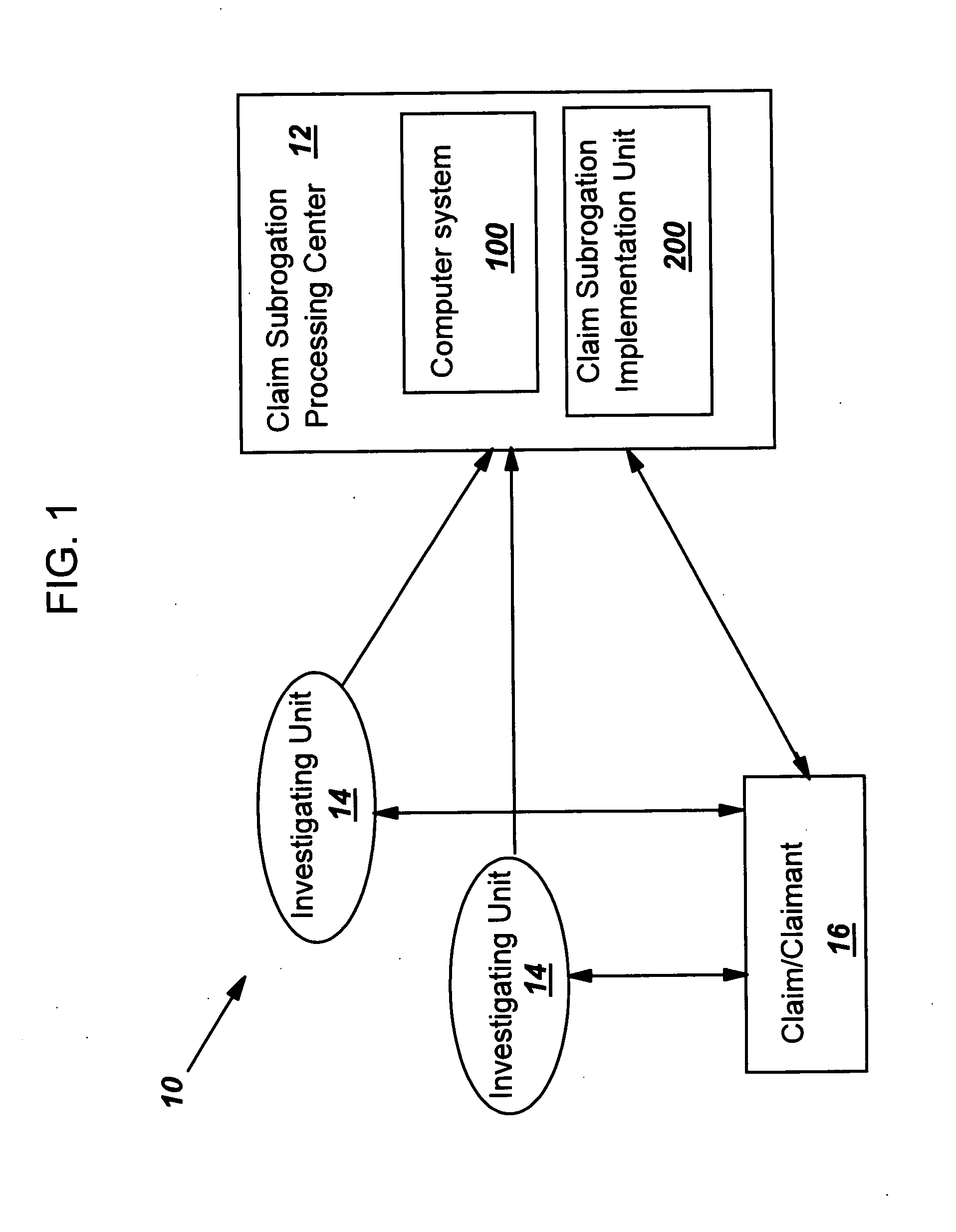
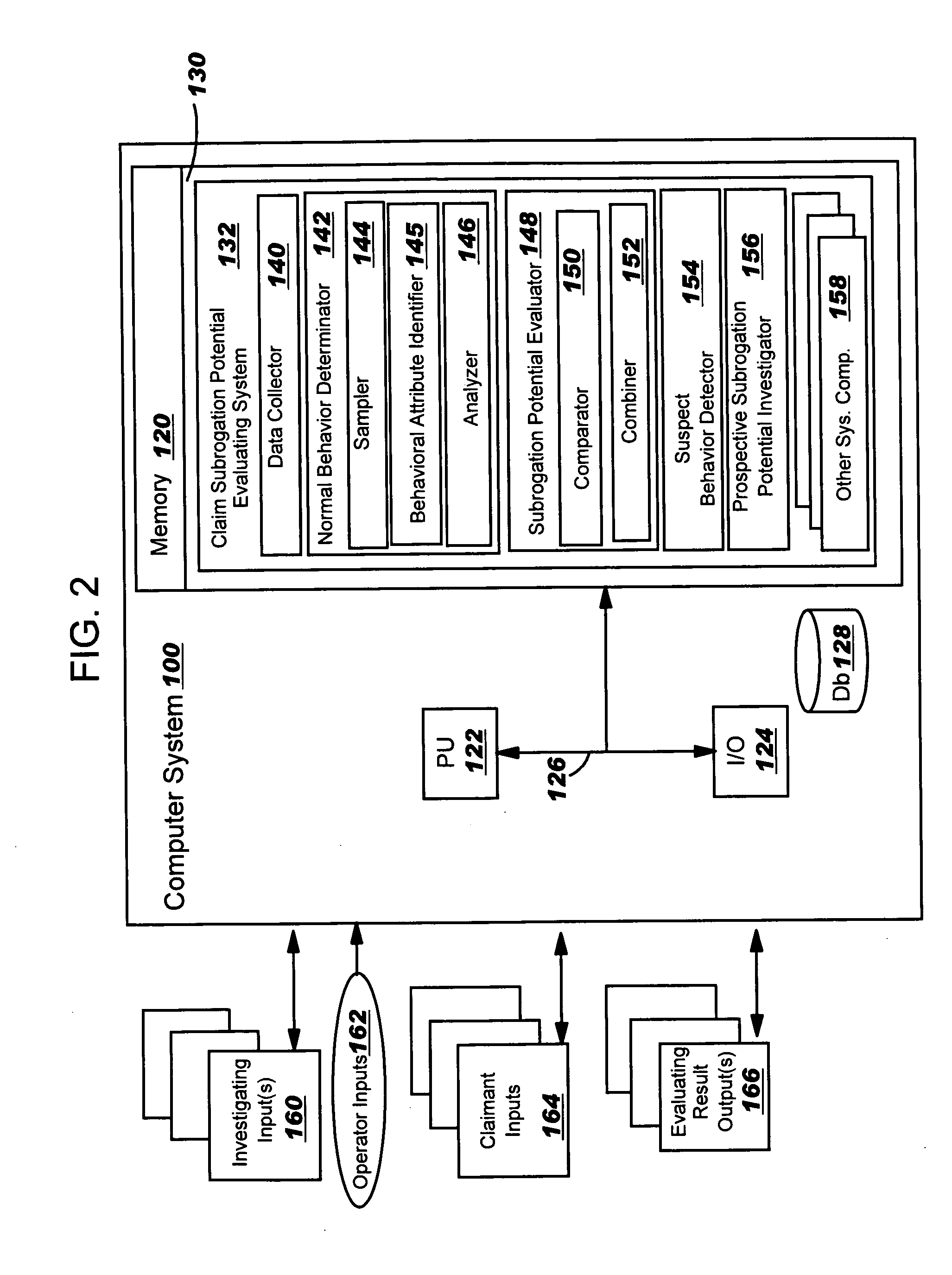
Evaluating a subrogation potential of an insurance claim
A method, system and computer program product for evaluating a subrogation potential of a target insurance claim is disclosed. A peer group of claims that are expected to include similar behaviors as the target claim and have been successfully subrogated is established to determine a normal behavior that the target claim is supposed to include. A behavior of the target claim is compared to the normal behavior to evaluate a subrogation potential of the target claim. Proper subrogation solutions are prospectively chosen based on the determined normal behavior to increase efficiency.
Owner:IBM CORP
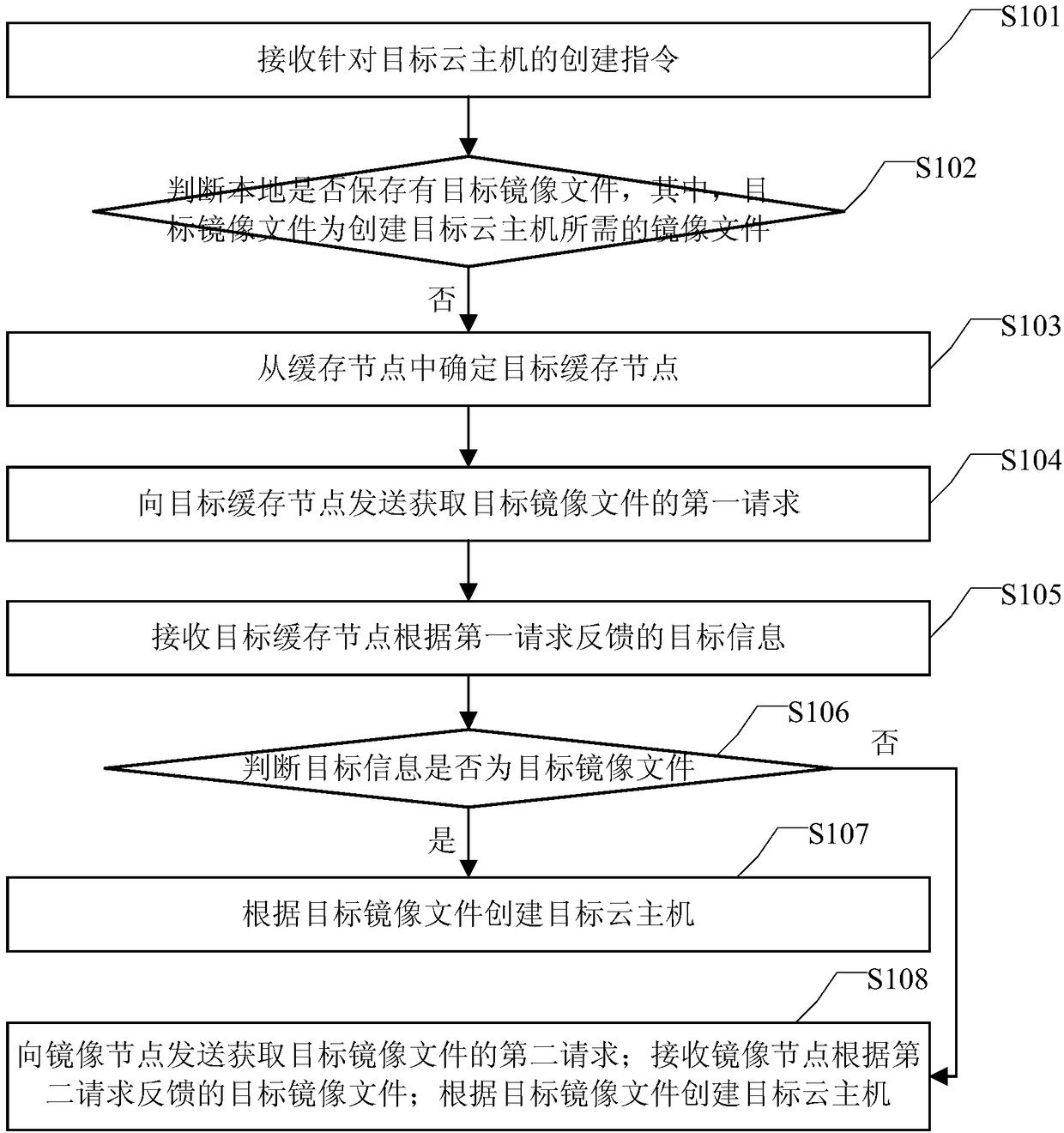
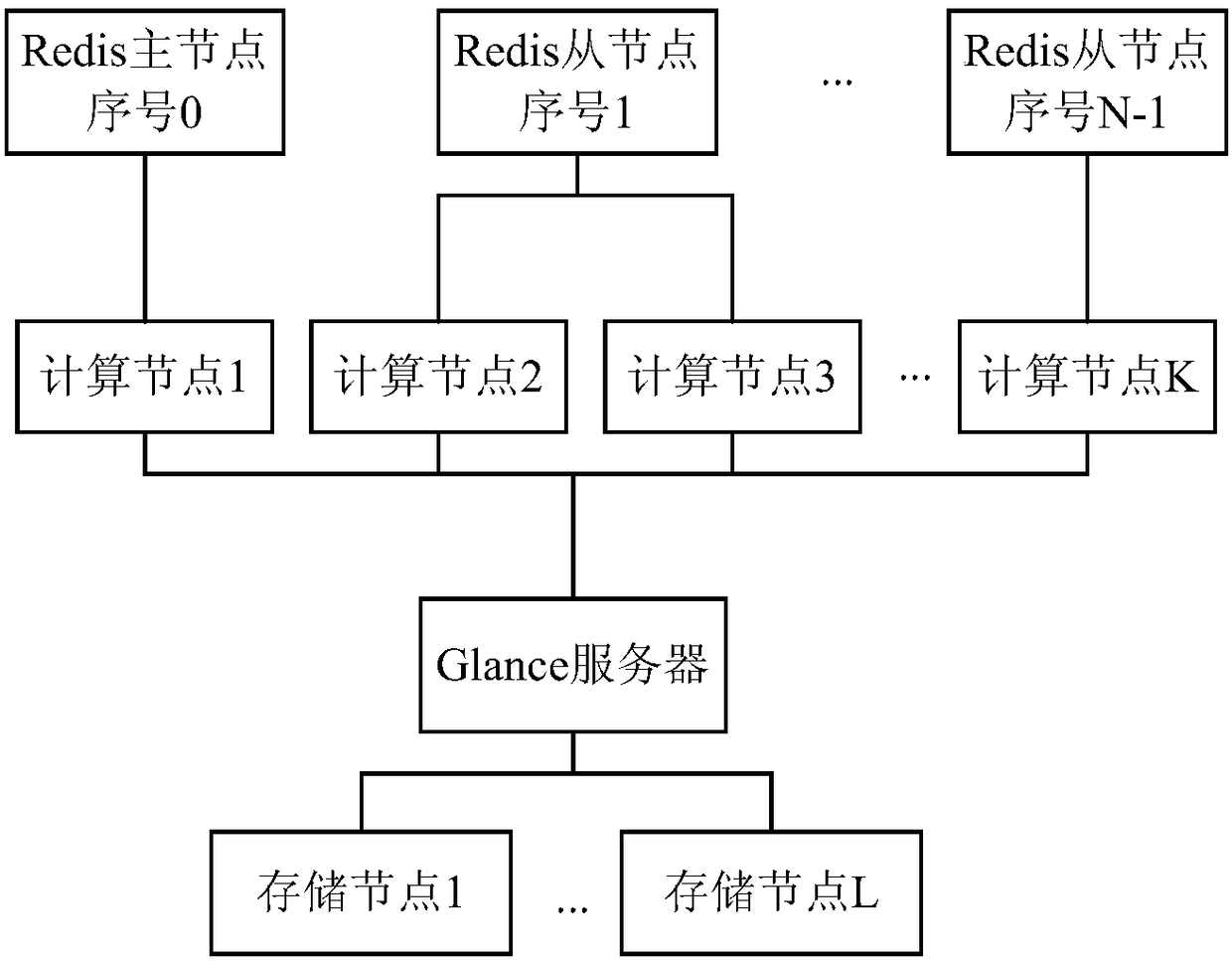
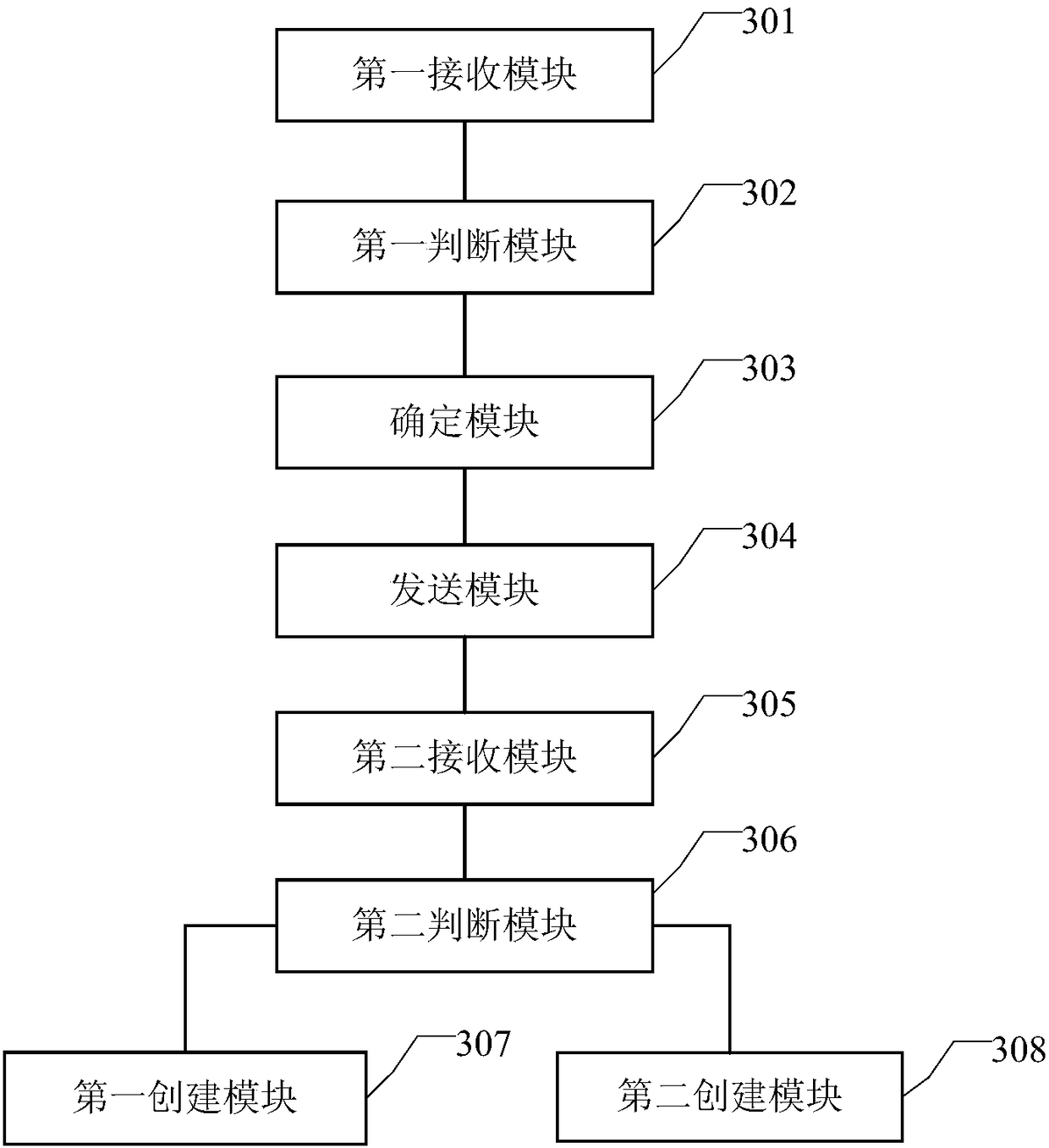
Cloud host creation method and device and cloud service system
InactiveCN108076078AReduce access pressureHigh concurrent downloadTransmissionSoftware simulation/interpretation/emulationObjective informationIdentifying goals
The embodiment of the invention discloses a cloud host creation method and device and a cloud service system. The method is applied to a target computing node in the cloud service system and comprisesthe steps that a creation instruction for a target cloud host is received; whether or not a target mirror file needed for creating the target cloud host is saved locally; if not, a target cache nodeis determined from cache nodes; a first request for acquiring the target mirror file is sent to the target cache node; target information fed back by the target cache node according to the first request is received; whether or not the target information is the target mirror file is judged; if yes, the target cloud host is created according to the target mirror file; if not, a second request for acquiring the target mirror file is sent to a mirror node; the target mirror file fed back by the mirror node according to the second request is received; and the target cloud host is created accordingto the target mirror file. According to the cloud host creation method and device and the cloud service system, the pulling time of the mirror file and the creating time of the cloud host can be shortened.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
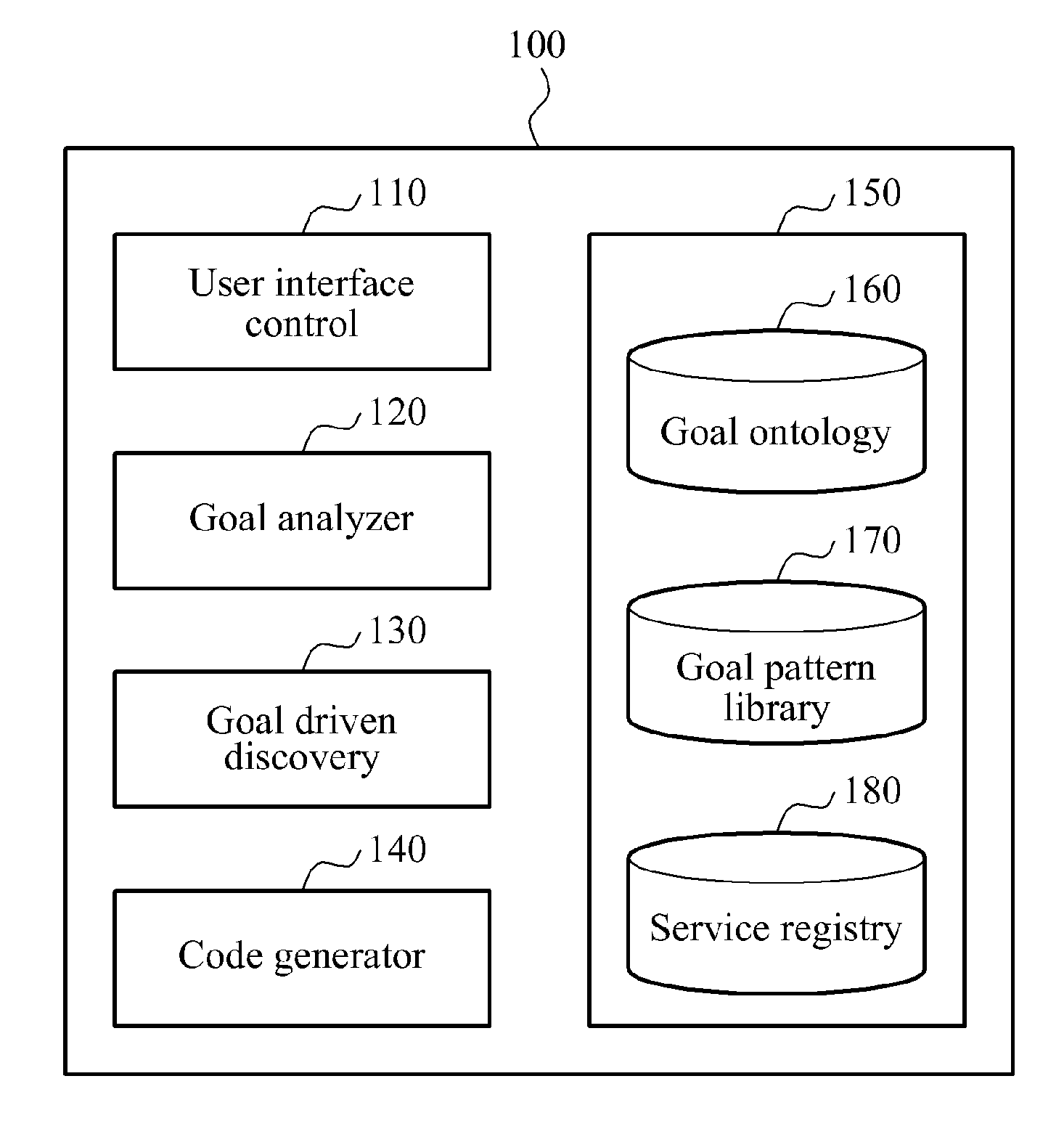
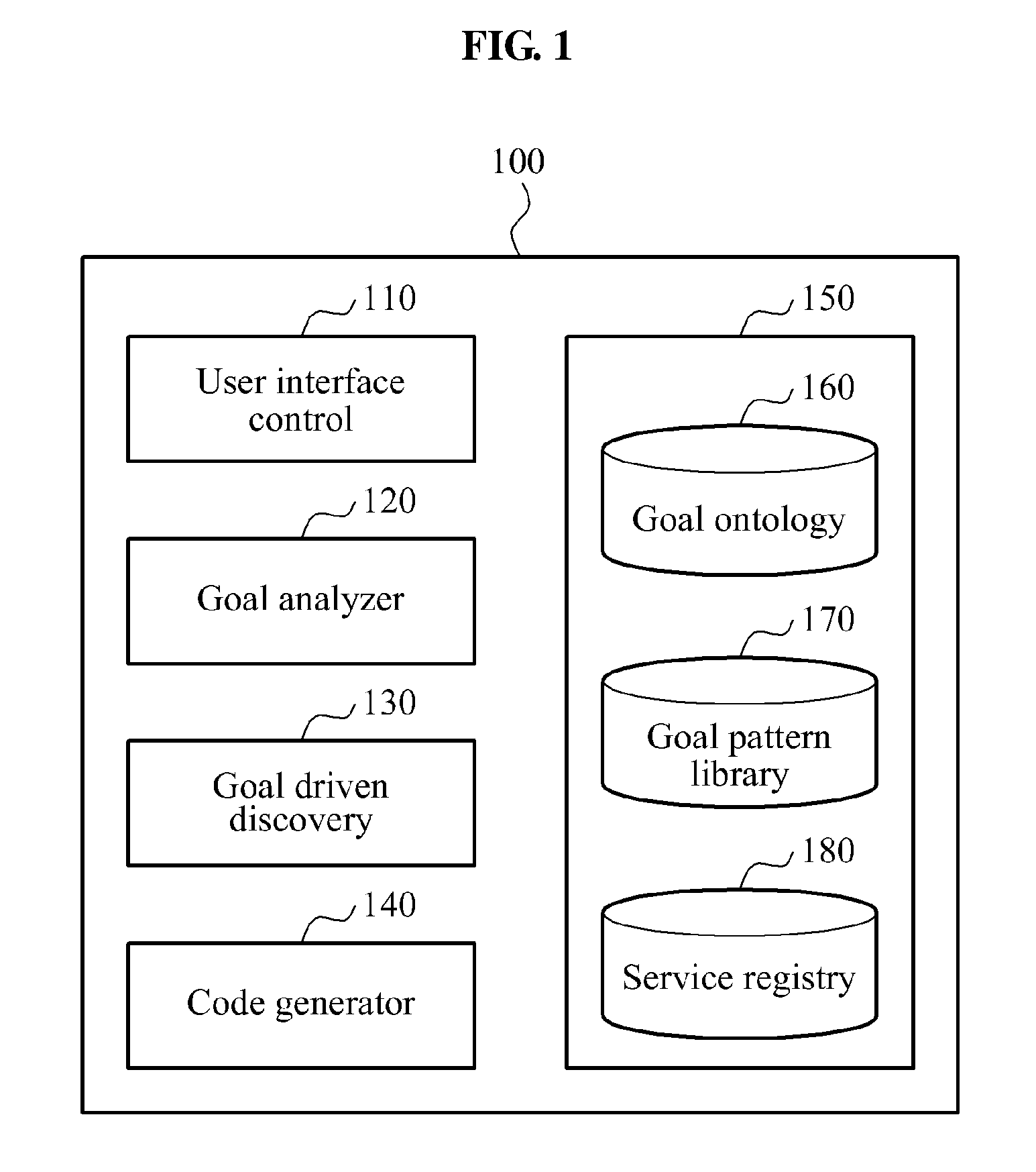
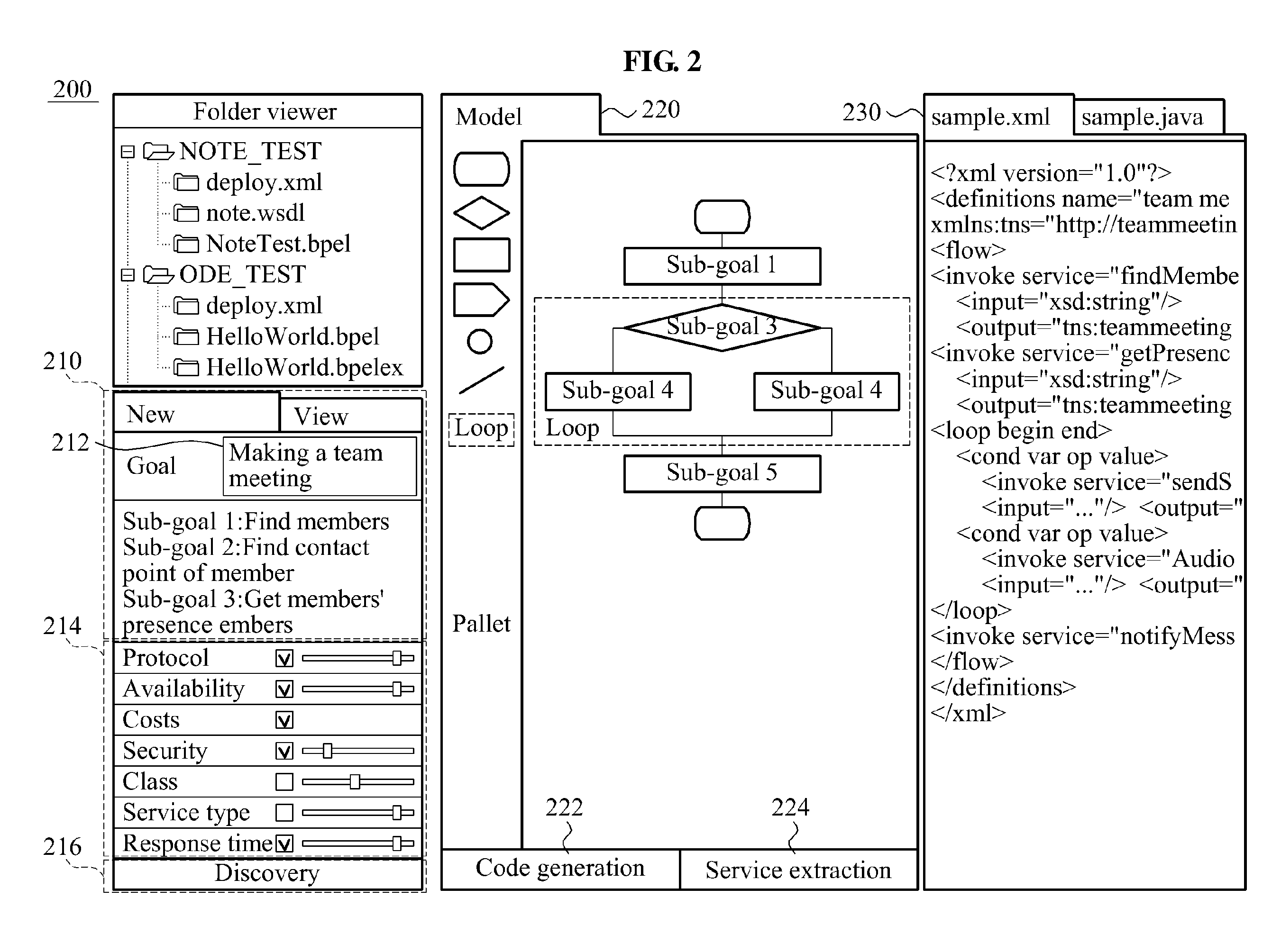
Method and apparatus for creating service flow based on user's goal-driven semantic service discovery
InactiveUS20120089959A1Multiple digital computer combinationsSpecific program execution arrangementsService flowIdentifying goals
Provided is a method and apparatus for automatically creating a service flow. A goal may be identified based on a keyword input from a user. The identified goal may be decomposed into at least one sub-goal, and a service may be discovered and determined with respect to each sub-goal. A service flow may be created based on the determined service, and a code may be generated based on the service flow.
Owner:ELECTRONICS & TELECOMM RES INST
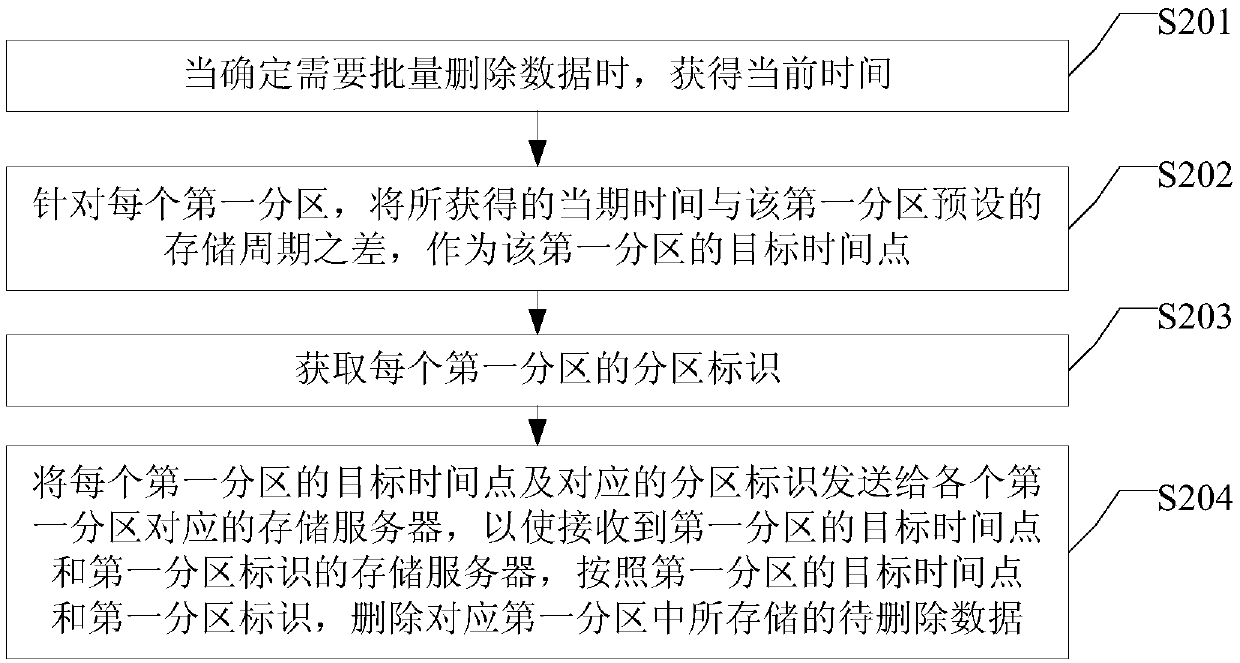
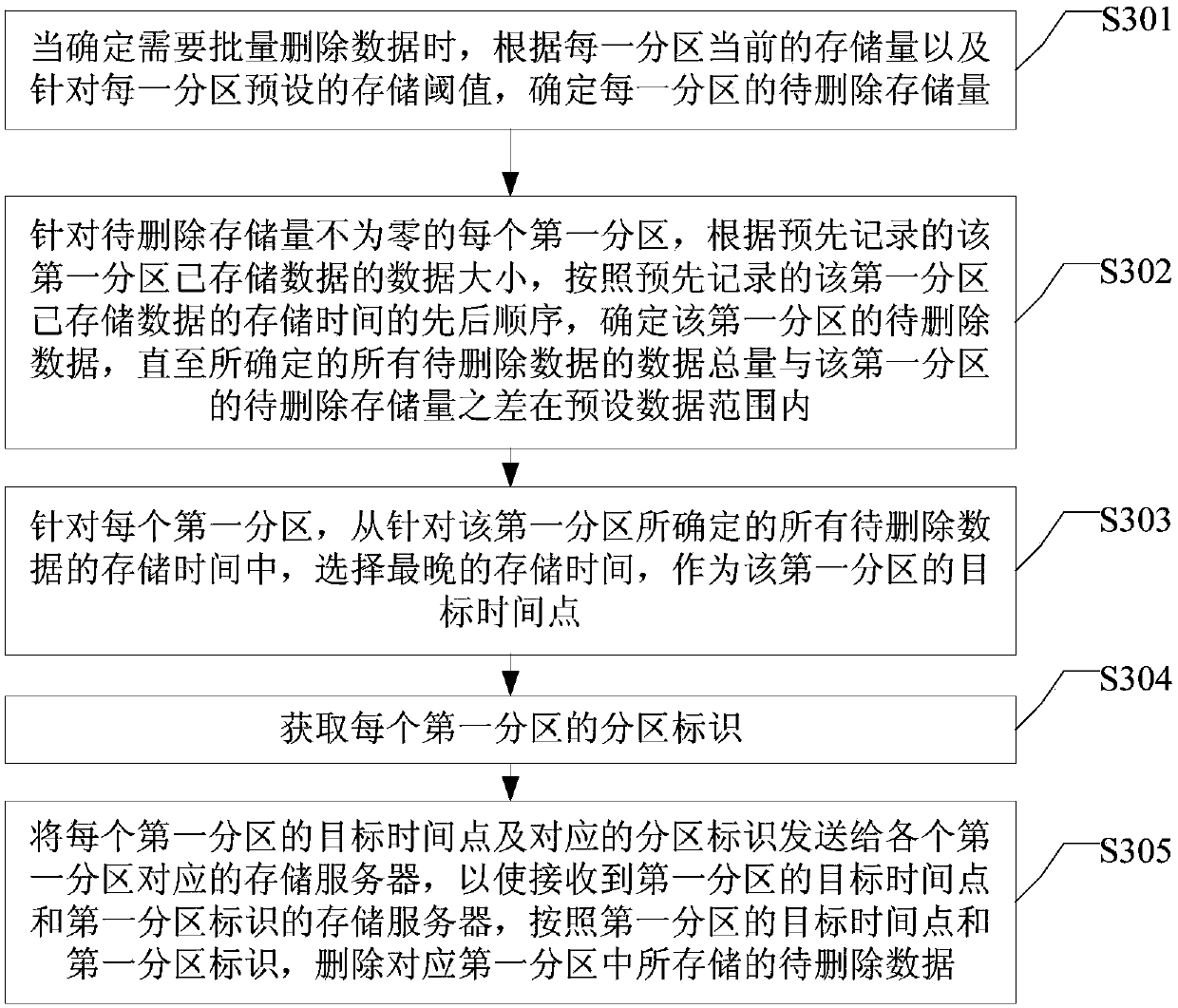
A data deletion method and a distributed storage system
ActiveCN109558065AShorten the timeReduce interactionInput/output to record carriersTransmissionData needsIdentifying goals
The embodiment of the invention provides a data deletion method and a distributed storage system, and a method applied to a management server in the distributed storage system, and the method comprises the steps of determining a target time point according to a preset data deletion rule when it is determined that data needs to be deleted in batches; and sending the determined target time point toa storage server, so that the storage server receiving the target time point deletes the to-be-deleted data according to the target time point, and the to-be-deleted data is the stored data of which the storage time is before the target time point. By applying the data deletion method provided by the embodiment of the invention, the storage space release efficiency can be improved.
Owner:HANGZHOU HIKVISION SYST TECH
Network attack detection method and apparatus, terminal device and computer storage medium
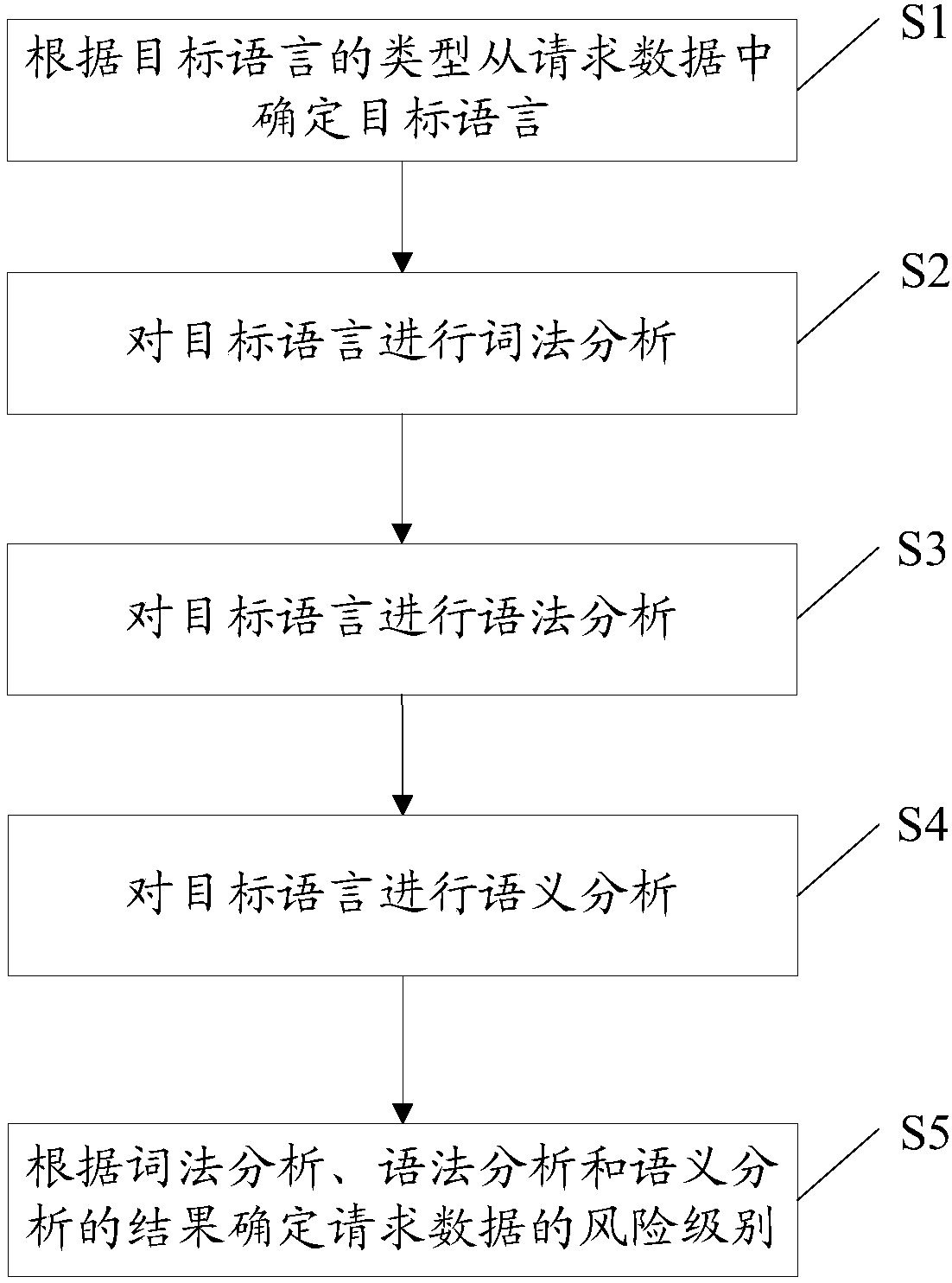
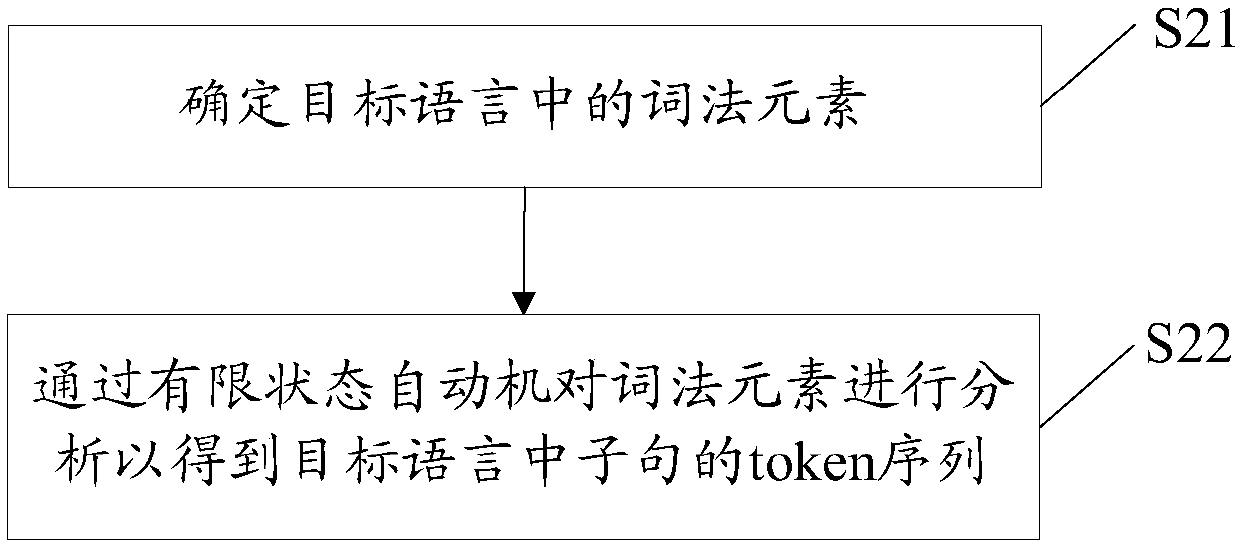
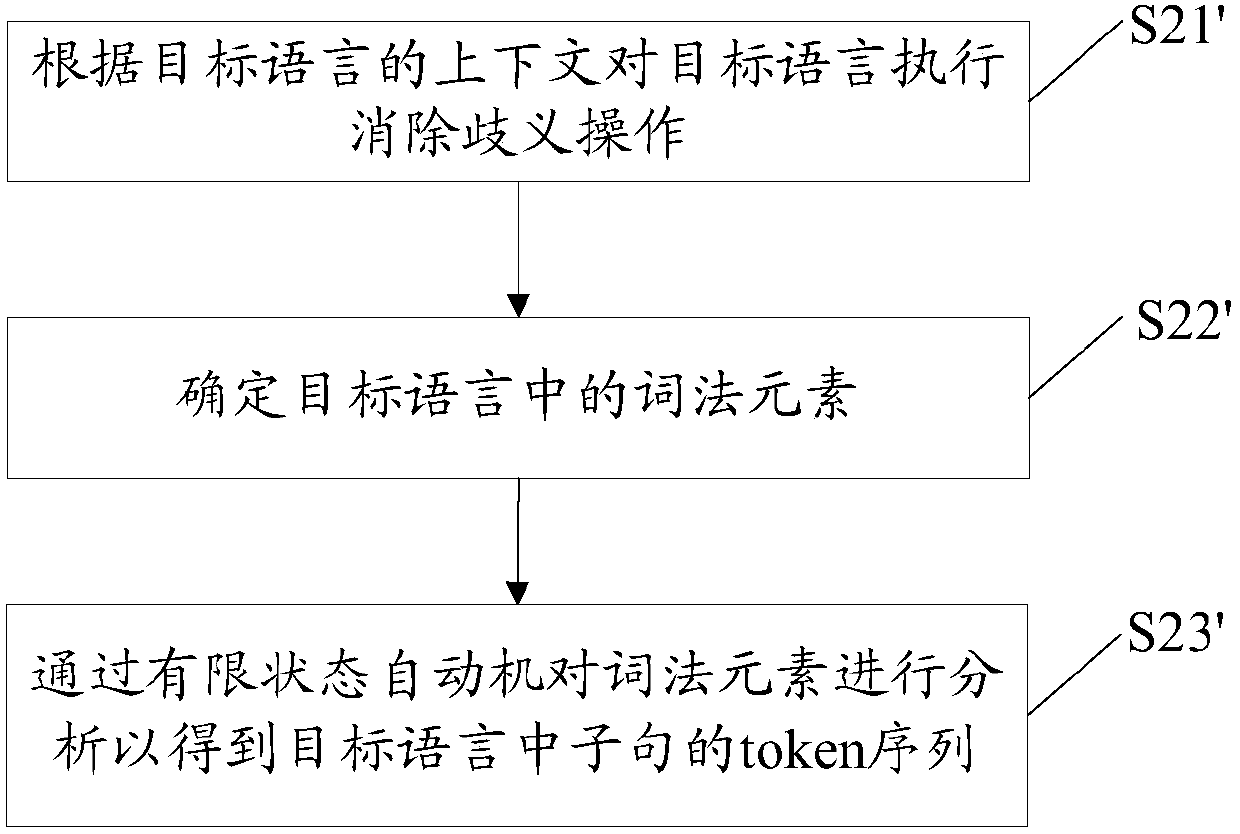
ActiveCN107659555AImprove compatibilityFast executionSemantic analysisPlatform integrity maintainanceRisk levelLexical analysis
The embodiment of the invention provides a network attack detection method and apparatus, a terminal device and a computer storage medium, and relates to the technical field of network security. The network attack detection method comprises the following steps: determining a target language from request data according to the type of the target language; performing morphological analysis, grammatical analysis and semantic analysis on the target language; and determining a risk level of the request data based on the results of the morphological analysis, grammatical analysis and semantic analysis. In the technical scheme provided by the invention, the target language is determined from the request data according to the type of the target language, so that the extraction operations of different types of target languages can be compatible to adapt to different detection targets, and thus the compatibility of network attack detection is improved.
Owner:北京长亭未来科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com