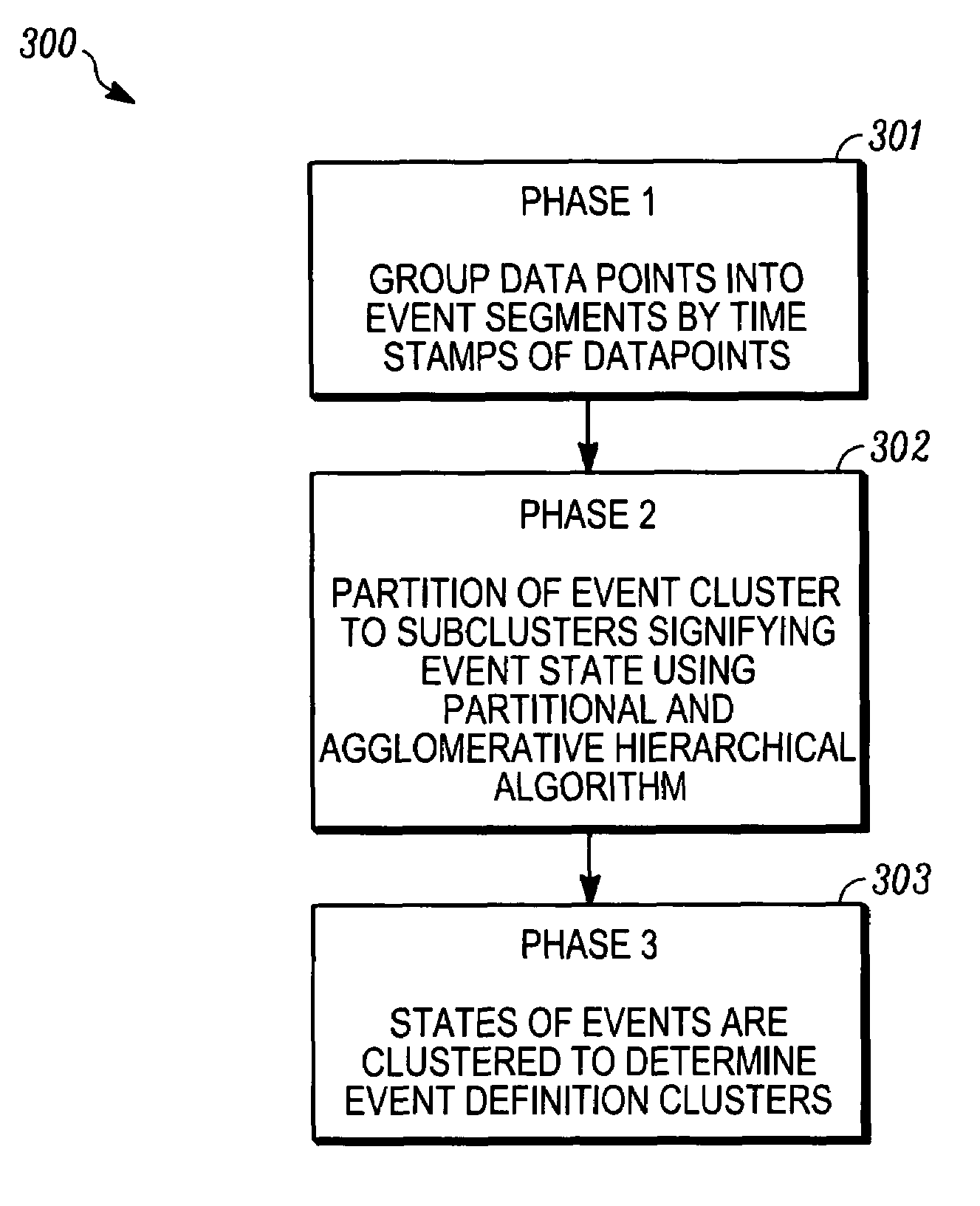
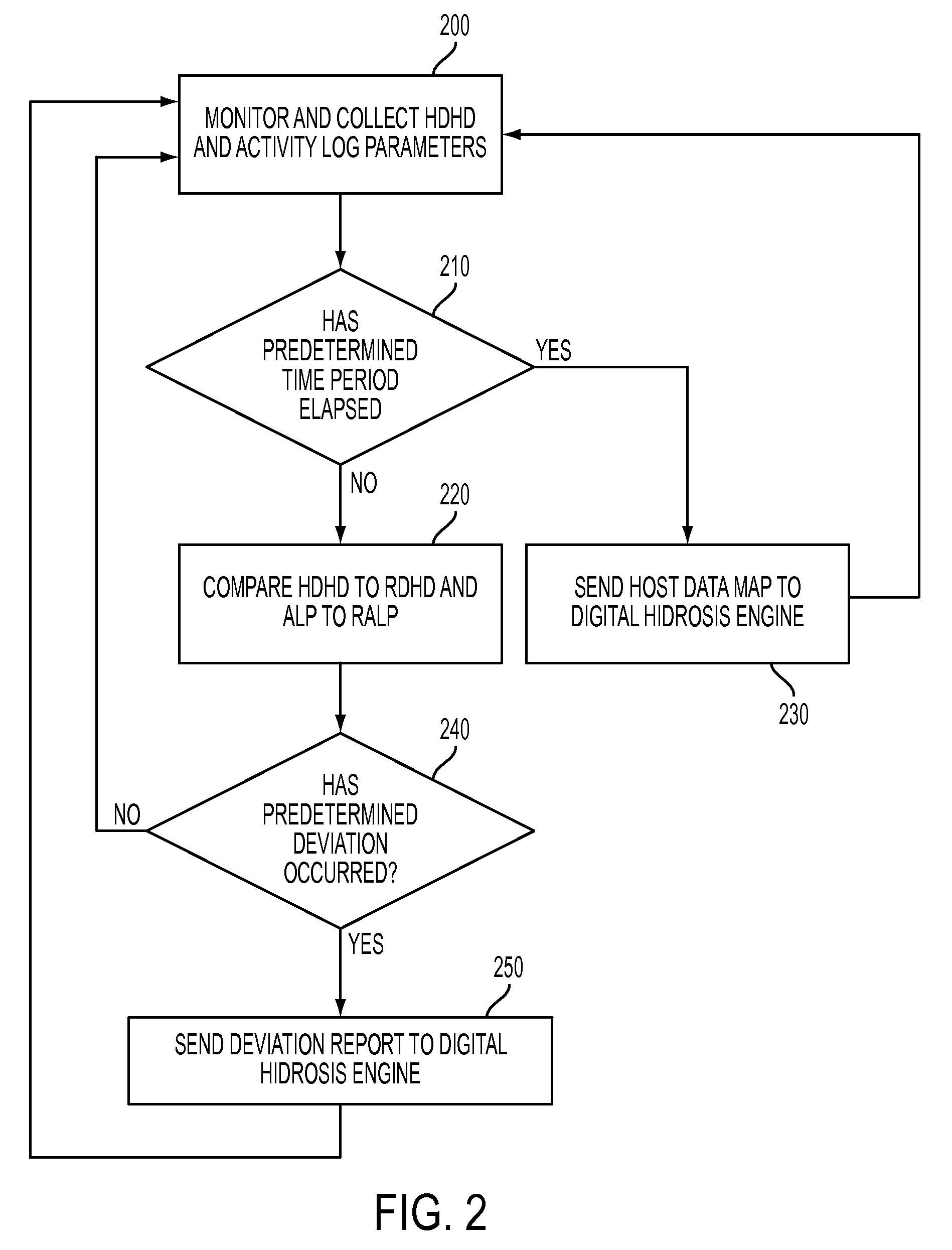
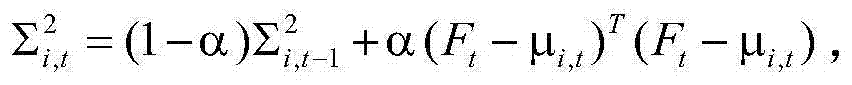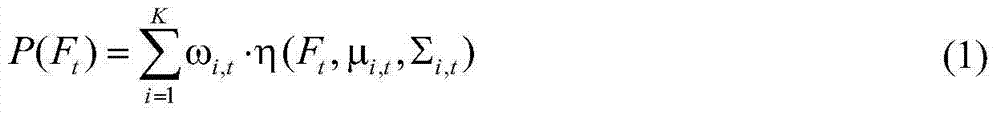Patents
Literature
133 results about "Normal behaviour" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
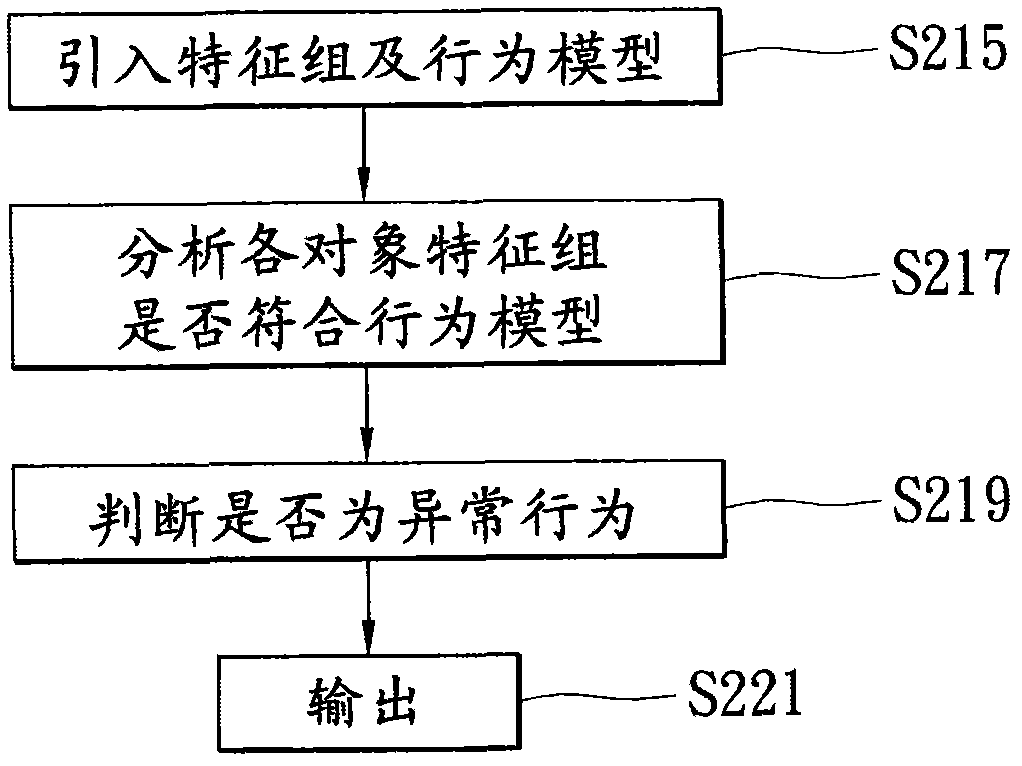
Normal behavior refers to expected behavior in individuals. The manner in which people interact with others, go about their lives are usually in accordance with the social expectations. When these expectations and individual behavior synchronize, the behavior is considered as normal.
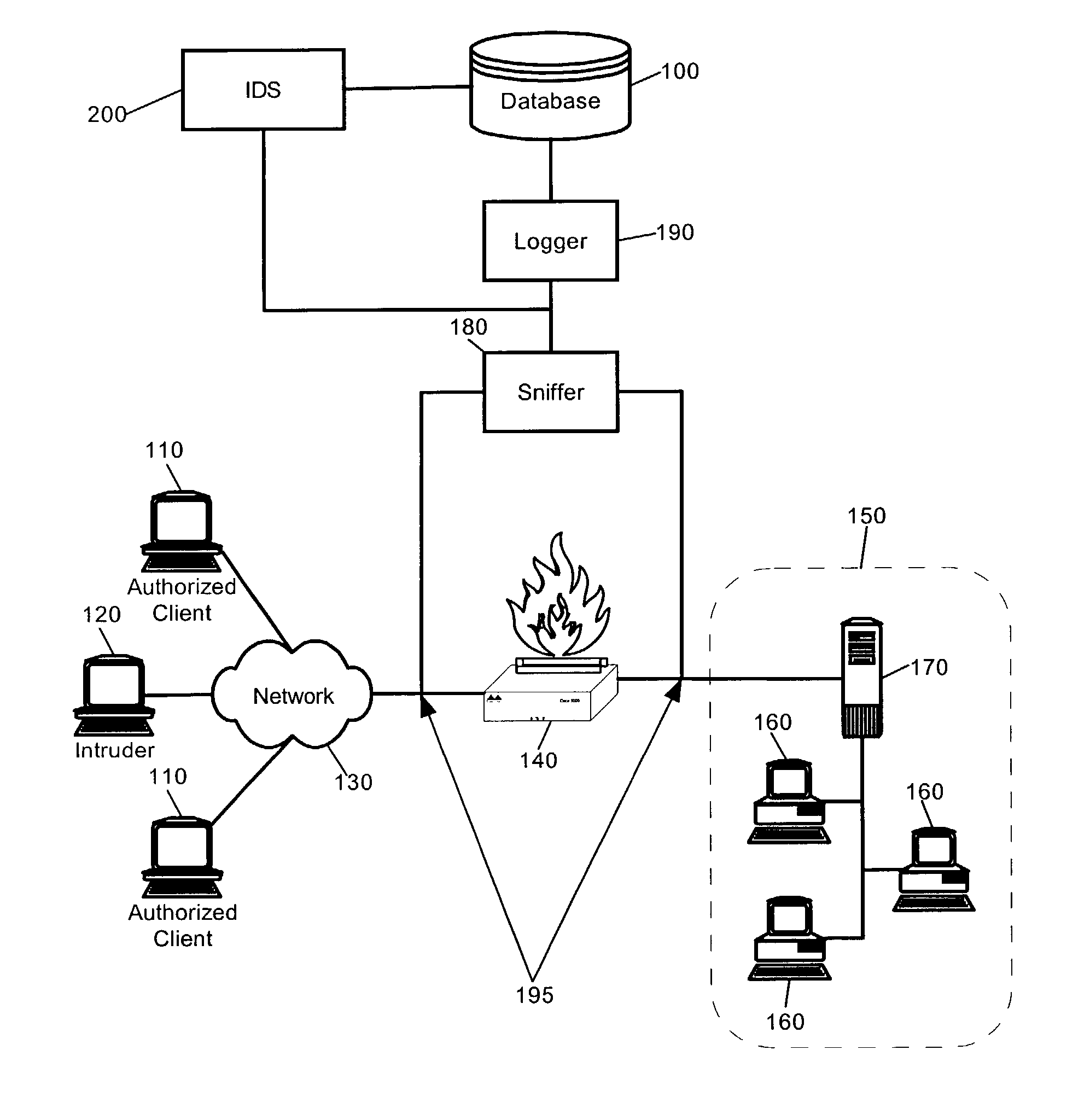
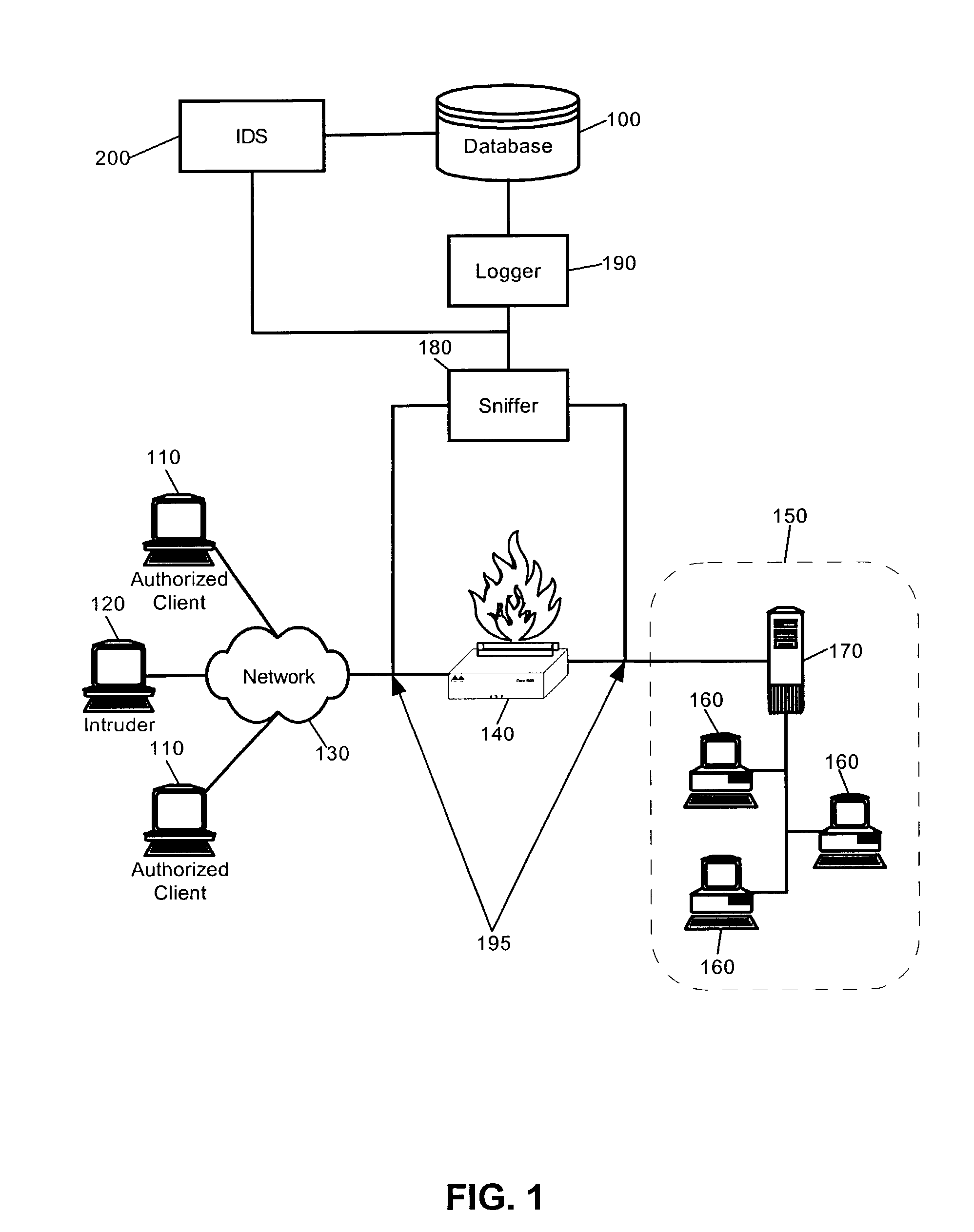
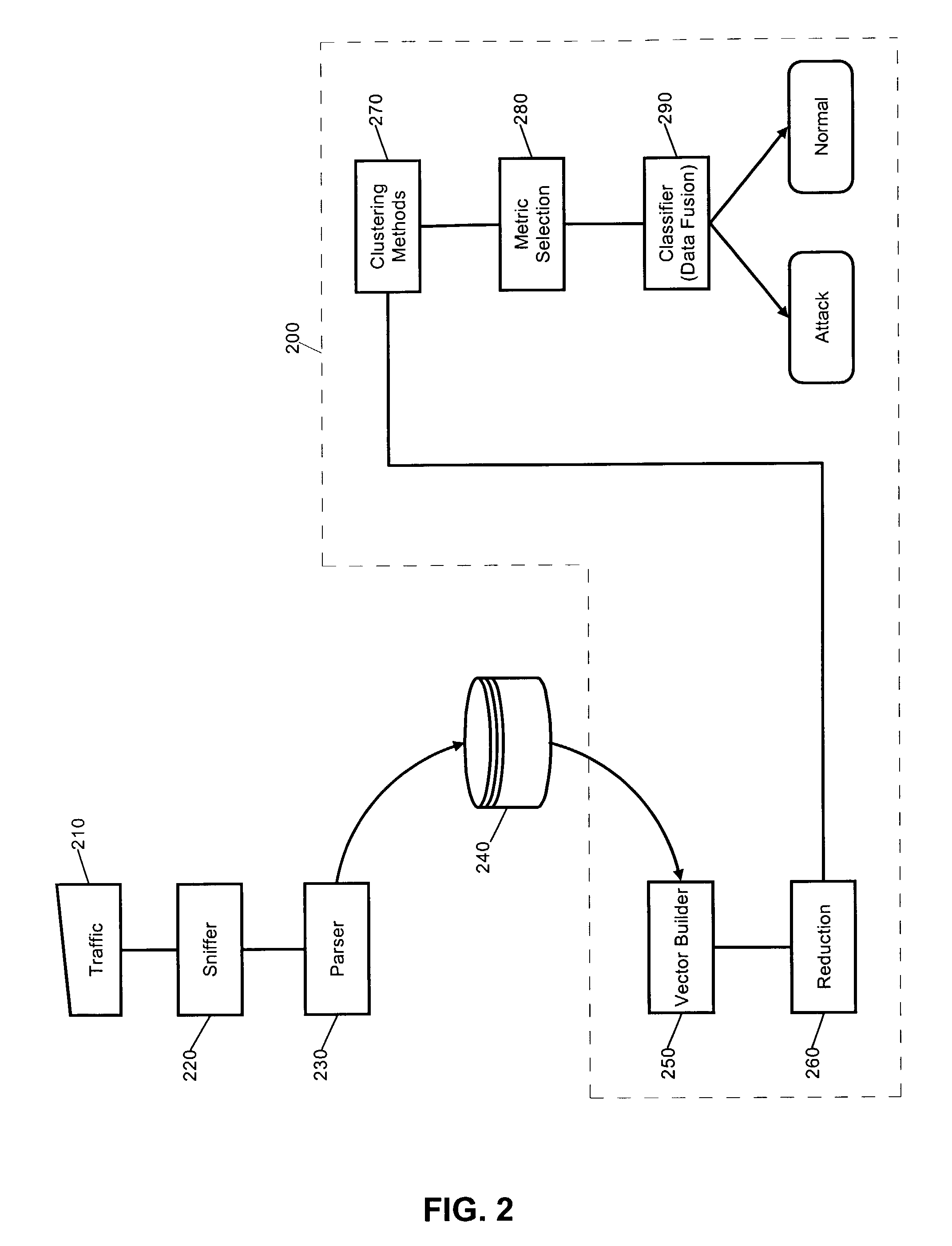
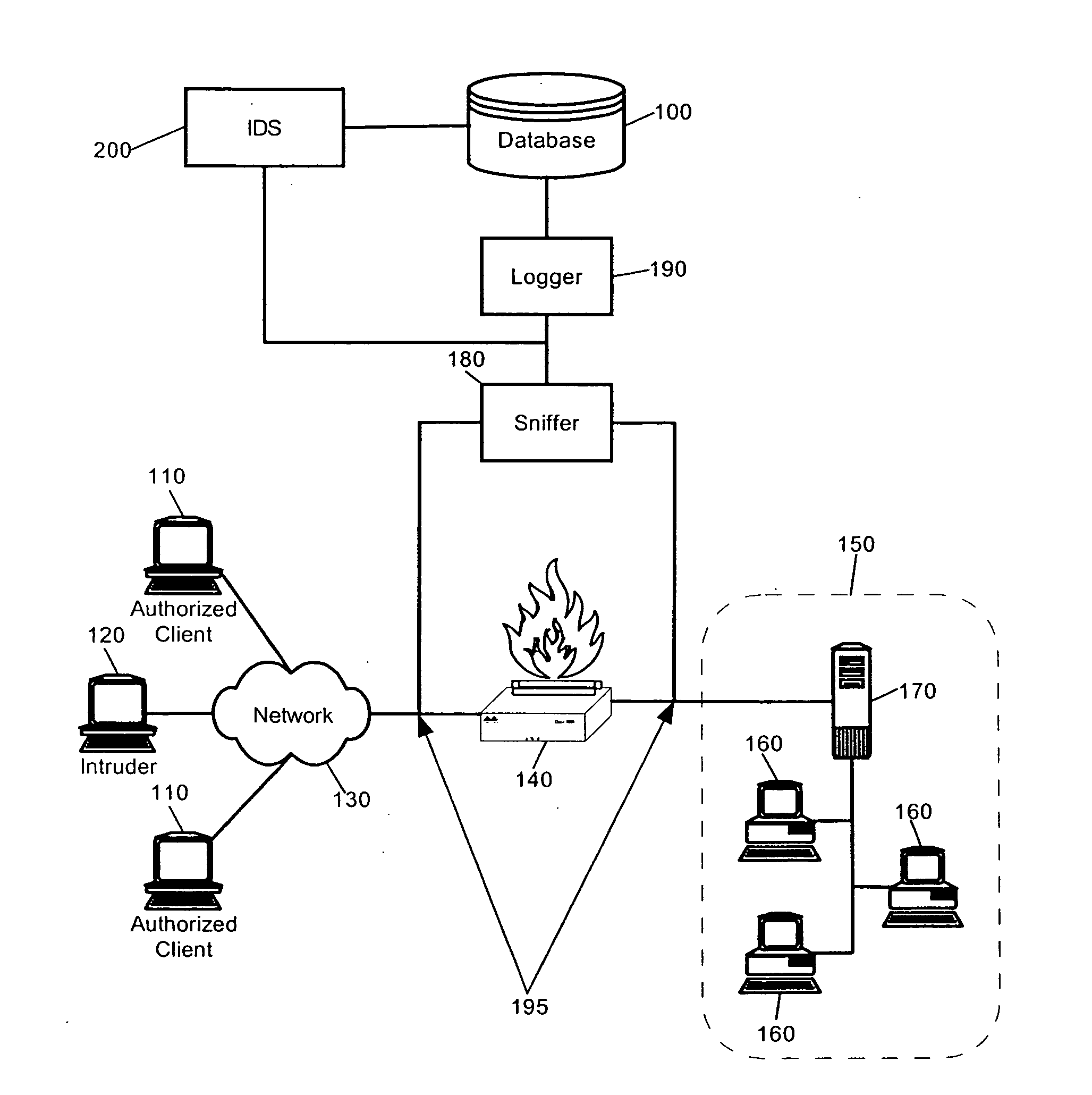
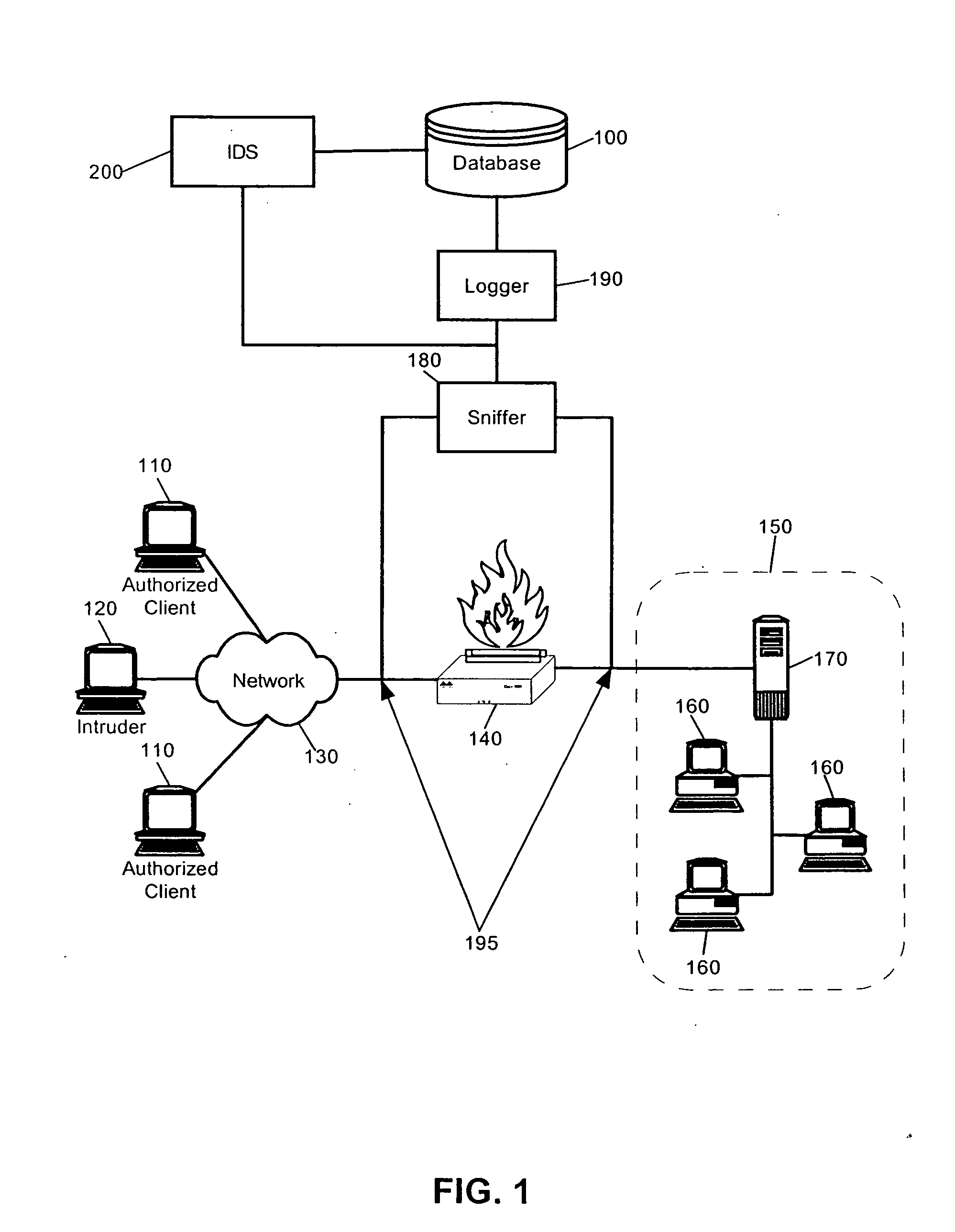
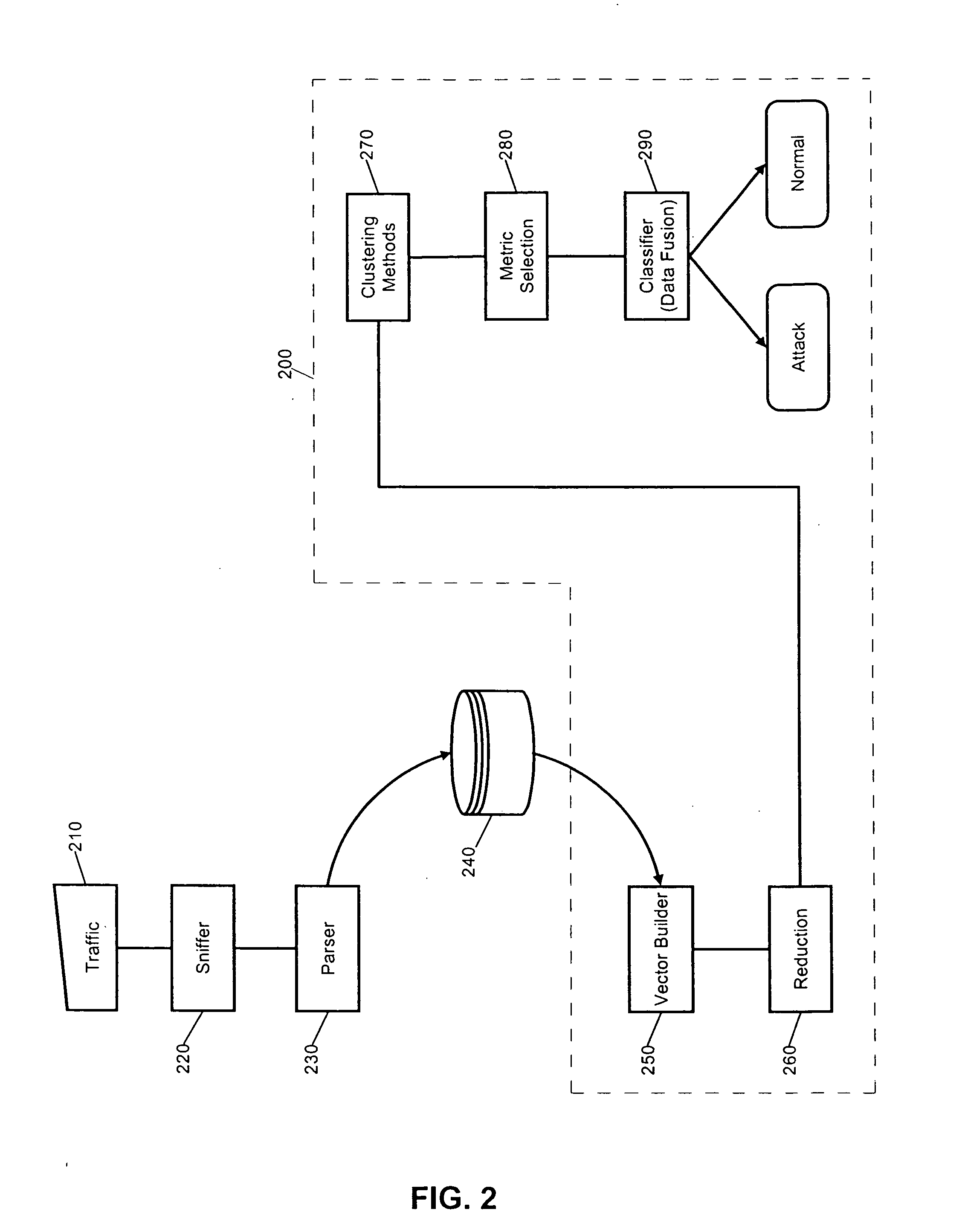
Intrusion detection system using self-organizing clusters
InactiveUS7017186B2Facilitate robust analysisOvercome limitationsMemory loss protectionError detection/correctionSelf organized mapNormal behaviour
An intrusion detection system (IDS). An IDS which has been configured in accordance with the present invention can include a traffic sniffer for extracting network packets from passing network traffic; a traffic parser configured to extract individual data from defined packet fields of the network packets; and, a traffic logger configured to store individual packet fields of the network packets in a database. A vector builder can be configured to generate multi-dimensional vectors from selected features of the stored packet fields. Notably, at least one self-organizing clustering module can be configured to process the multi-dimensional vectors to produce a self-organized map of clusters. Subsequently, an anomaly detector can detect anomalous correlations between individual ones of the clusters in the self-organized map based upon at least one configurable correlation metric. Finally, a classifier can classify detected anomalous correlations as one of an alarm and normal behavior.
Owner:LONGHORN HD LLC
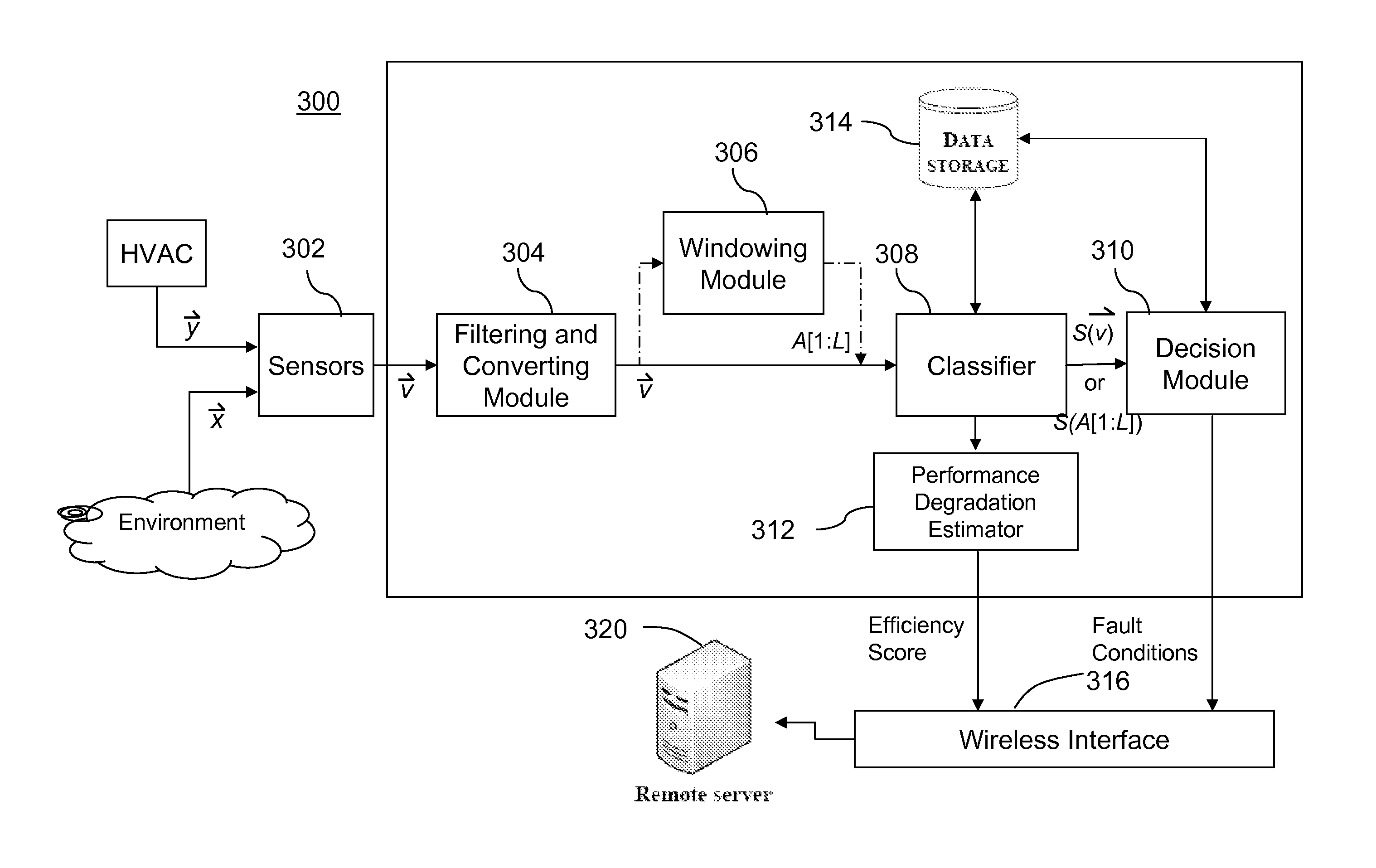
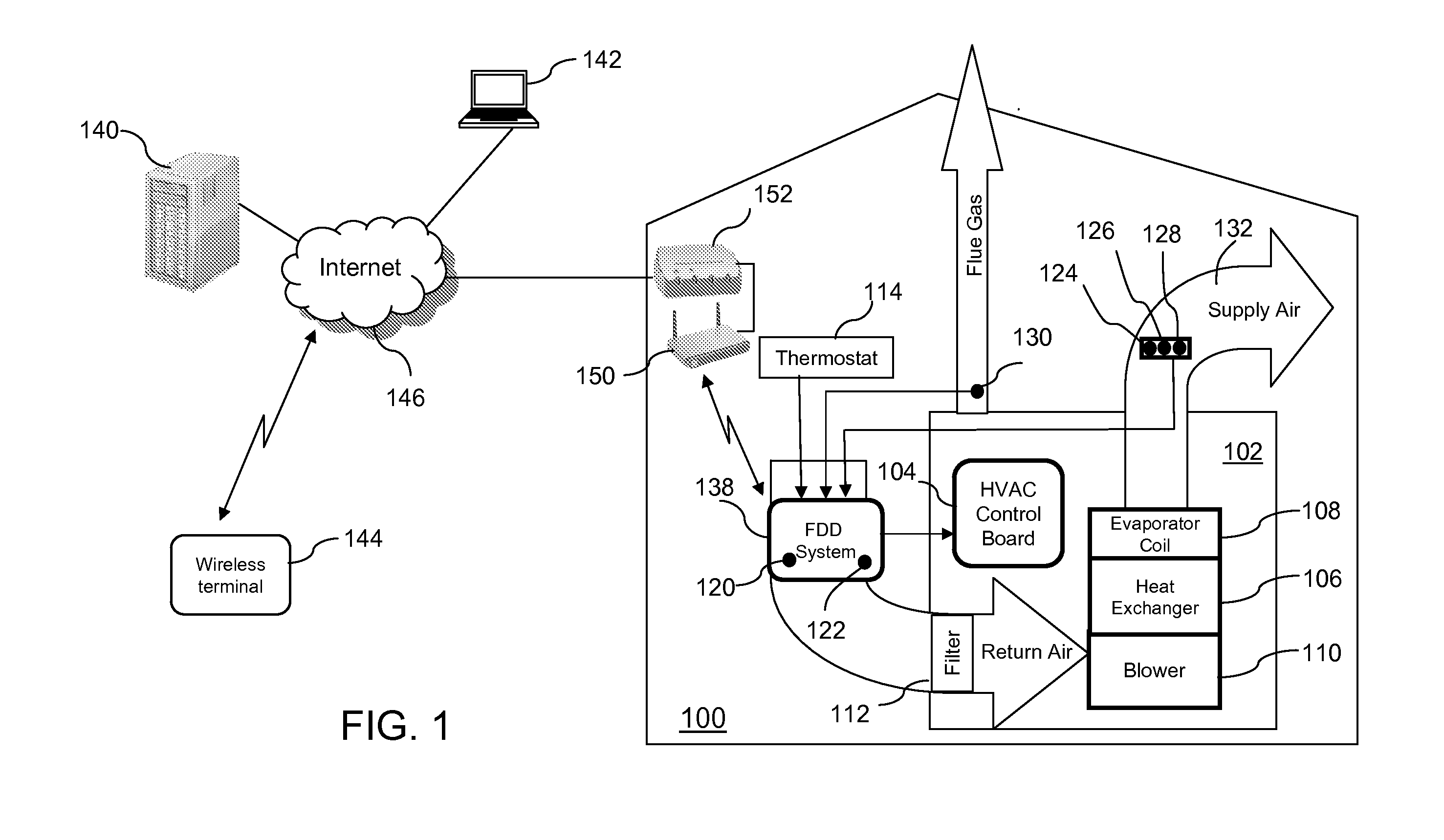
Intelligent system and method for detecting and diagnosing faults in heating, ventilating and air conditioning (HVAC) equipment
InactiveUS20120072029A1Lower performance requirementsTemperatue controlStatic/dynamic balance measurementTraining phaseComputer module
A system and a method for detecting and diagnosing faults in heating, ventilating and air conditioning (HVAC) equipment is described. The system comprises a sensor; a classifier modelling a normal behaviour of the HVAC equipment in situ in the installed operation environment, the classifier having a plurality of classifier parameters for computing a classifier score using an input data based on a measured value from the sensor, the plurality of classifier parameters being created during a training phase of the system using the input data during the training phase; and a decision module for comparing the classifier score to a decision threshold, the decision threshold being set during the training phase.
Owner:HEATVU
Intrusion detection system
InactiveUS20060156404A1Facilitate robust analysisOvercome limitationsMemory loss protectionDigital data processing detailsData packInternet traffic
Owner:LONGHORN HD LLC
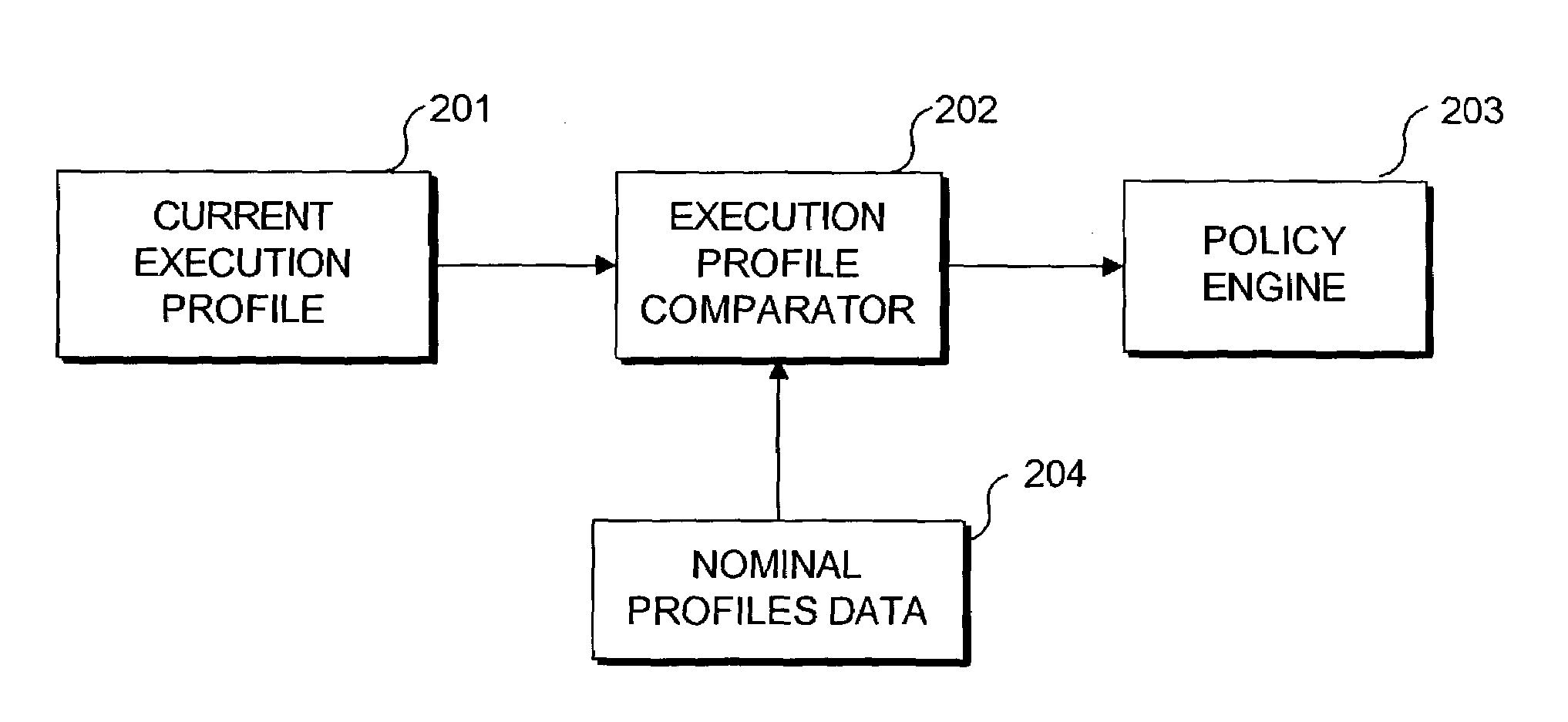
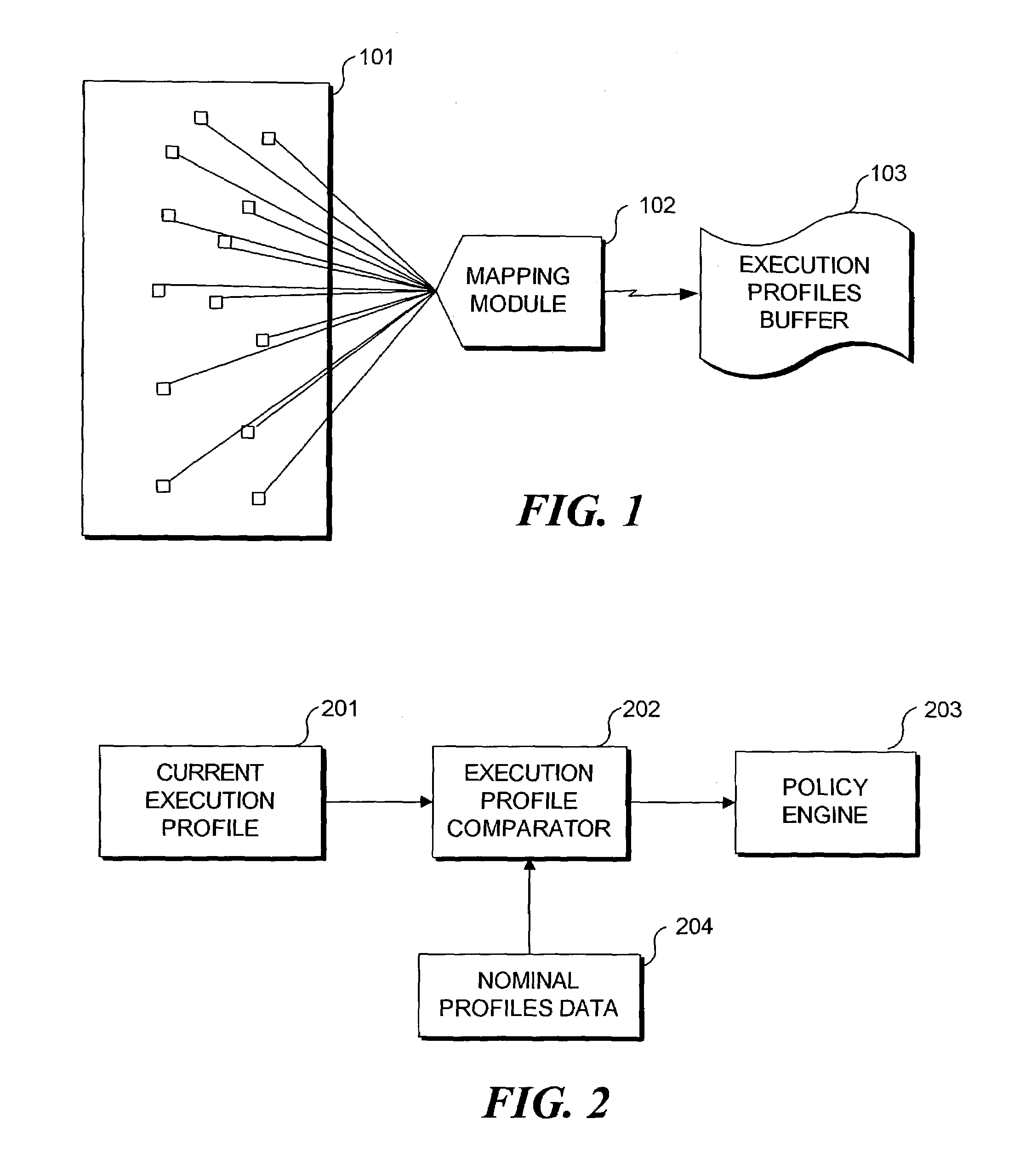
Method and system for establishing normal software system behavior and departures from normal behavior
InactiveUS7185367B2Memory loss protectionDigital data processing detailsStatistical analysisSoftware system
Detecting abnormal activity of a software system is based on behavioral information obtained from an instrumented computer program while it executes. As the program executes, it expresses information about the sequence and frequency with which program modules are called. Over time, this sequence and frequency defines the normal behavior of the program, and the information expressed on any given run is compared to this normal behavior. Statistical analysis of the differences between the normal behavior and the current run can be used to detect unauthorized or abusive use of the program. Program modules whose behavior is highly correlated can be grouped into a smaller number of virtual modules. Comparison between current and normal program behavior can then be made on the (smaller number of) virtual modules, thereby reducing the dimensionality of the problem of analyzing the differences between current and normal program behavior.
Owner:STRATACLOUD
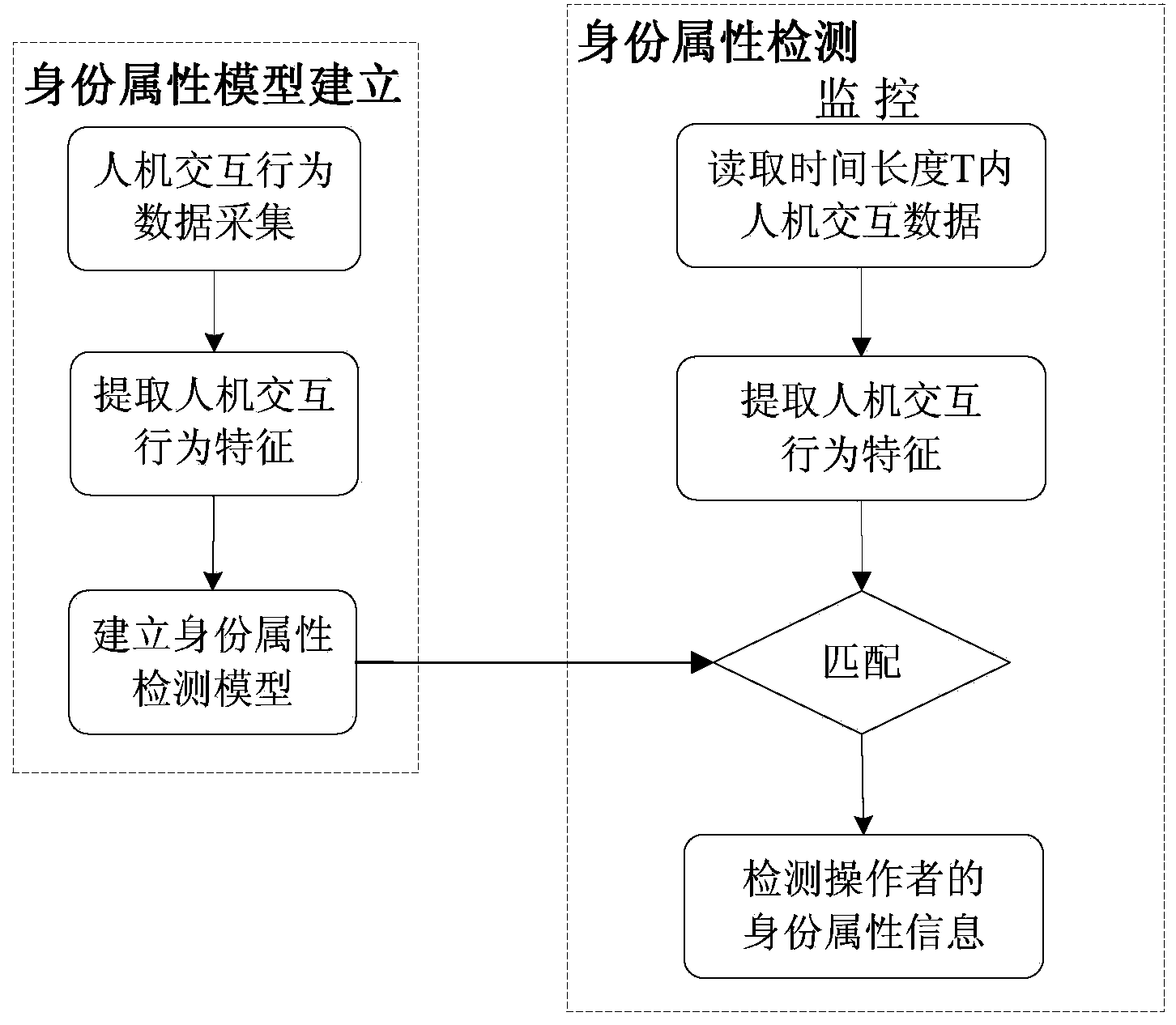
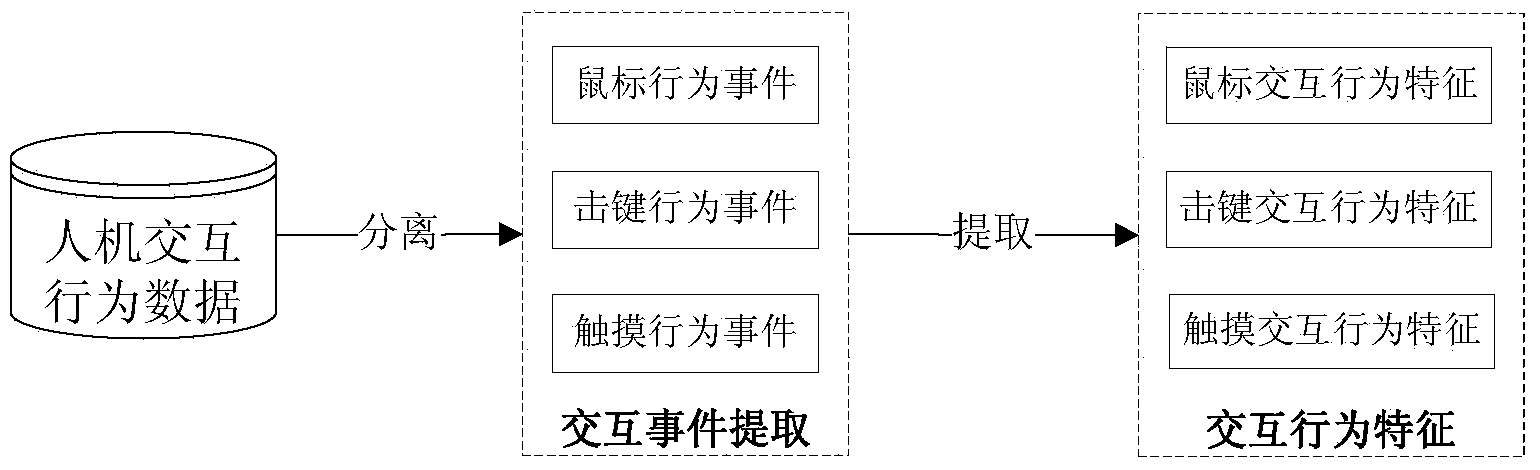
User identity attribute detection method based on man-machine interaction behavior characteristics
ActiveCN103530540ADoes not interfere with normal behaviorWide applicabilityInput/output for user-computer interactionDigital data authenticationPattern perceptionHuman–robot interaction
The invention discloses a user identity attribute detection method based on man-machine interaction behavior characteristics. The man-machine interaction behavior characteristics are extracted through analysis of man-machine interaction behaviors generated when man-machine interaction equipment, such as a mouse, a keyboard and a touch screen, operates in an interaction process between a user and an intelligent computer system, a user identity attribute template is established based on the man-machine interaction behavior characteristics, and identity attributes comprising genders, ages, races and the like of the user are detected and distinguished. The user identity attribute detection method has the advantages that the man-machine interaction behavior characteristics fill up blanks in analysis of identity attributes of operators in the intelligent computer system, and a brand new thought is provided for information perception analysis of users of computers and mobile networks. In addition, the user can be continuously analyzed through the method in the interaction process between the user and the intelligent computer system, and normal behaviors of the user cannot be disturbed.
Owner:XI AN JIAOTONG UNIV
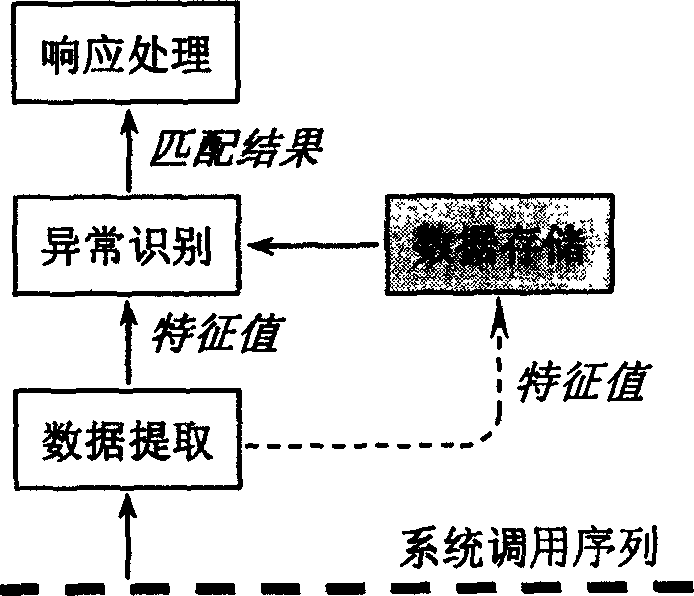
Abnormal detection method for user access activity in attached net storage device
InactiveCN1588889AReduce storage spaceReduce storage timeDigital computer detailsData switching networksAnomaly detectionSystem call
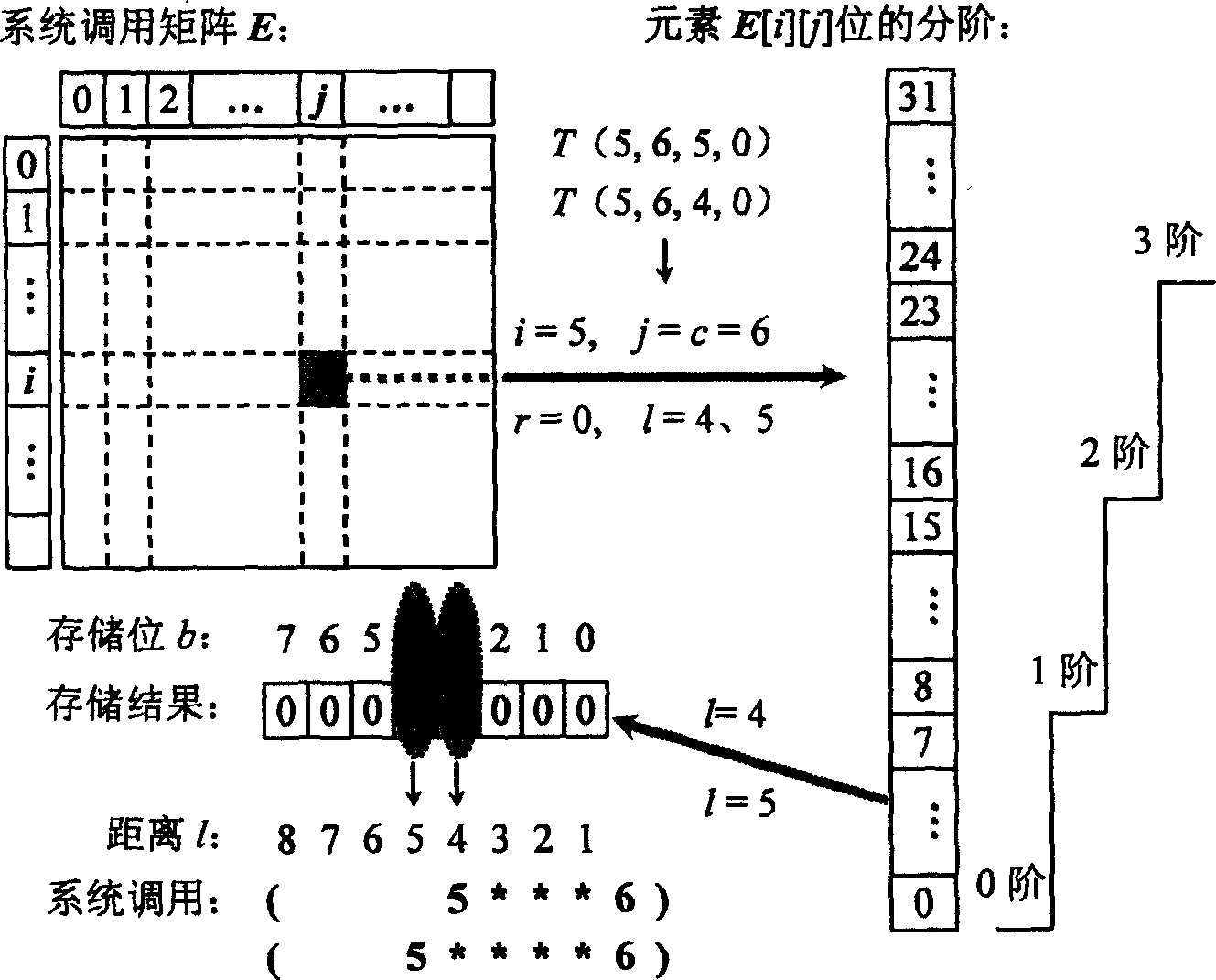
A method for testing abnormal access behaviors in attached network storage devices is to extract and match with the character value by a system dispatch series generated by user access behaviors to identify the abnormal behavior by normal behavior characters and generate response to prevent users in the network from abnormal access operation to the attached network storage device which not only can prevent the non-authorized users from illegal access, but also can prevent the authorized users from power-exceeds access.
Owner:TSINGHUA UNIV
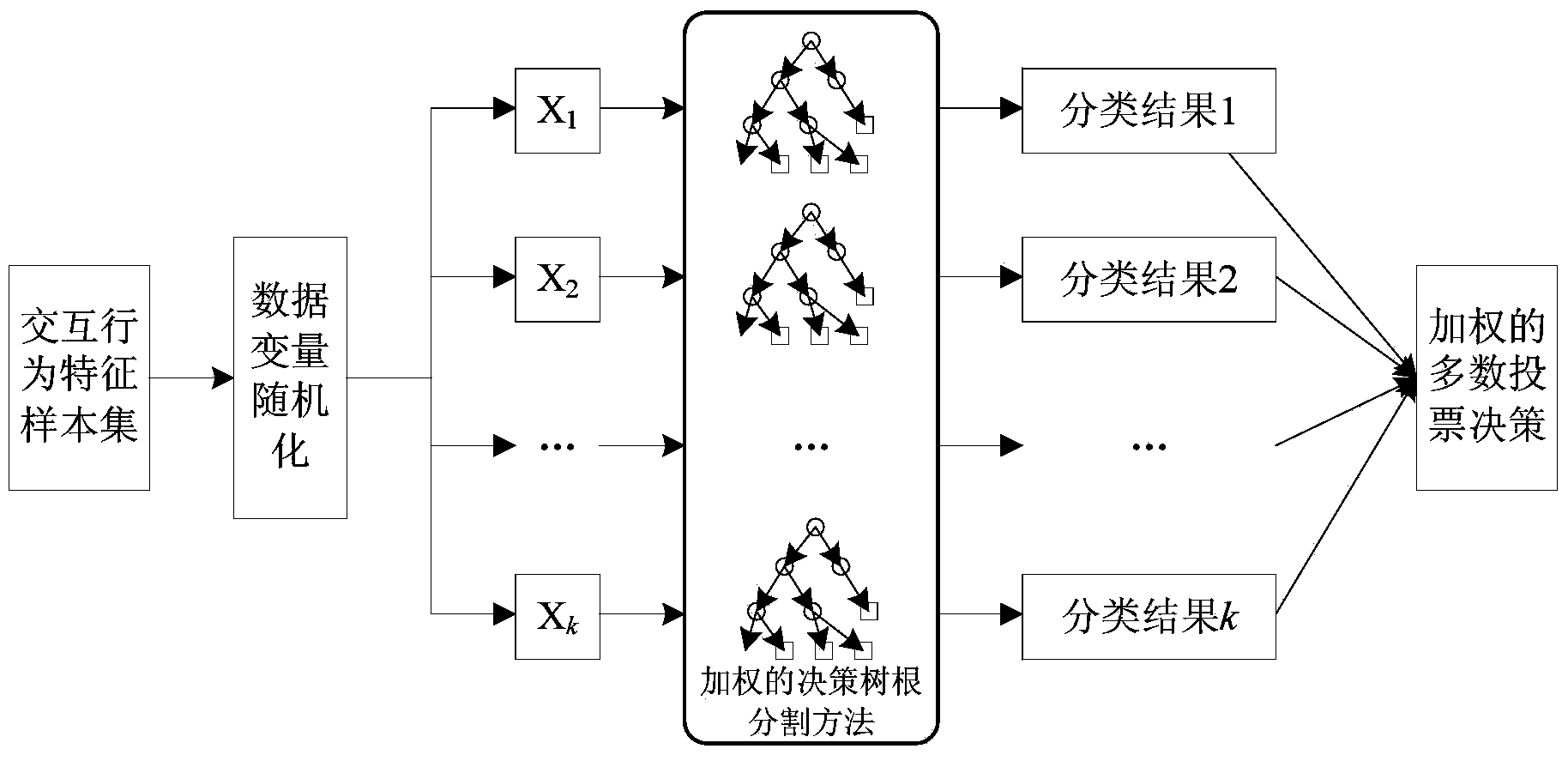
Abnormal behavior discovery method and system based on big data machine learning
ActiveCN106778259ASolve the problem that the number of labeled samples is too small at the beginningSolve the problem of too fewCharacter and pattern recognitionPlatform integrity maintainanceNormal behaviourComputer science
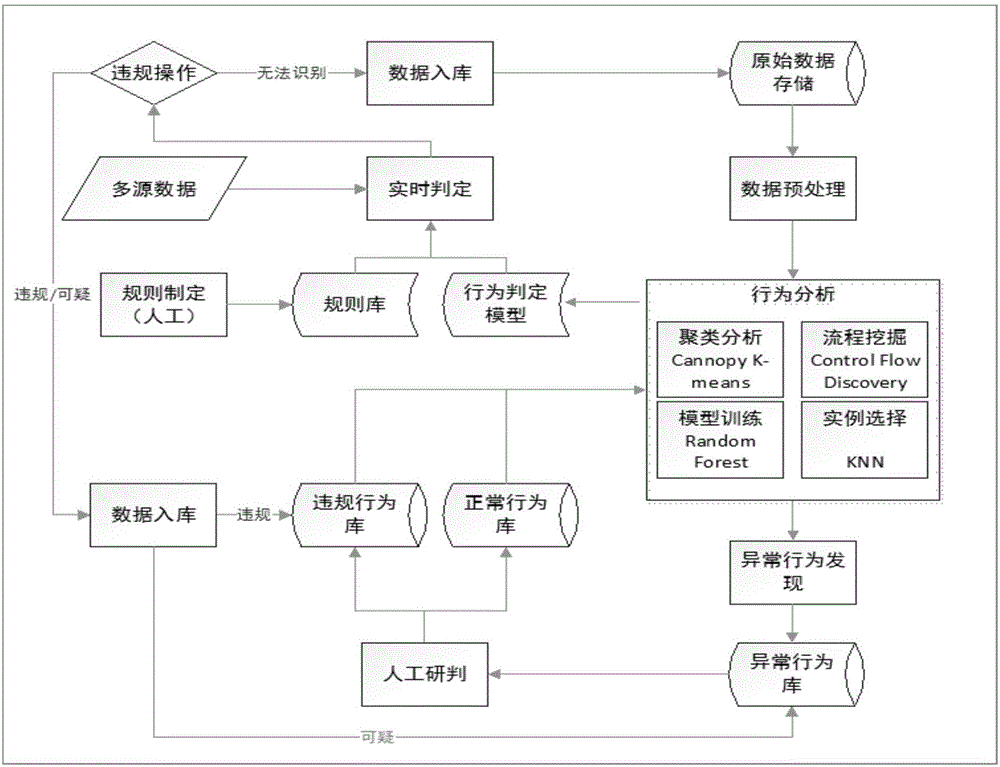
The invention discloses an abnormal behavior discovery method and system based on big data machine learning. The abnormal behavior discovery method disclosed by the invention comprises the following steps: carrying out pretreatment on the original security log data; extracting characteristic data from a pretreatment result; clustering the characteristic data, and determining an abnormal behavior library and a normal behavior library; acquiring new behavior sample data in the security log data, comparing with the normal behavior library and the abnormal behavior library, determining a new behavior to be a normal behavior or an abnormal behavior, and updating the normal behavior library or the abnormal behavior library with the new behavior sample data; and repeating the previous step, when the normal behavior library and the abnormal behavior library have enough normal behavior and abnormal behavior sample data, training a random forest model with sample data in the normal behavior library and the abnormal behavior library, and judging the abnormal behavior by utilizing the random forest model obtained through training. By adopting the scheme of the invention, the problem that quantity of label-containing samples in an initial stage is too low is solved, judging accuracy rate is improved, and misjudgement condition is effectively prevented from occurring.
Owner:北京明朝万达科技股份有限公司
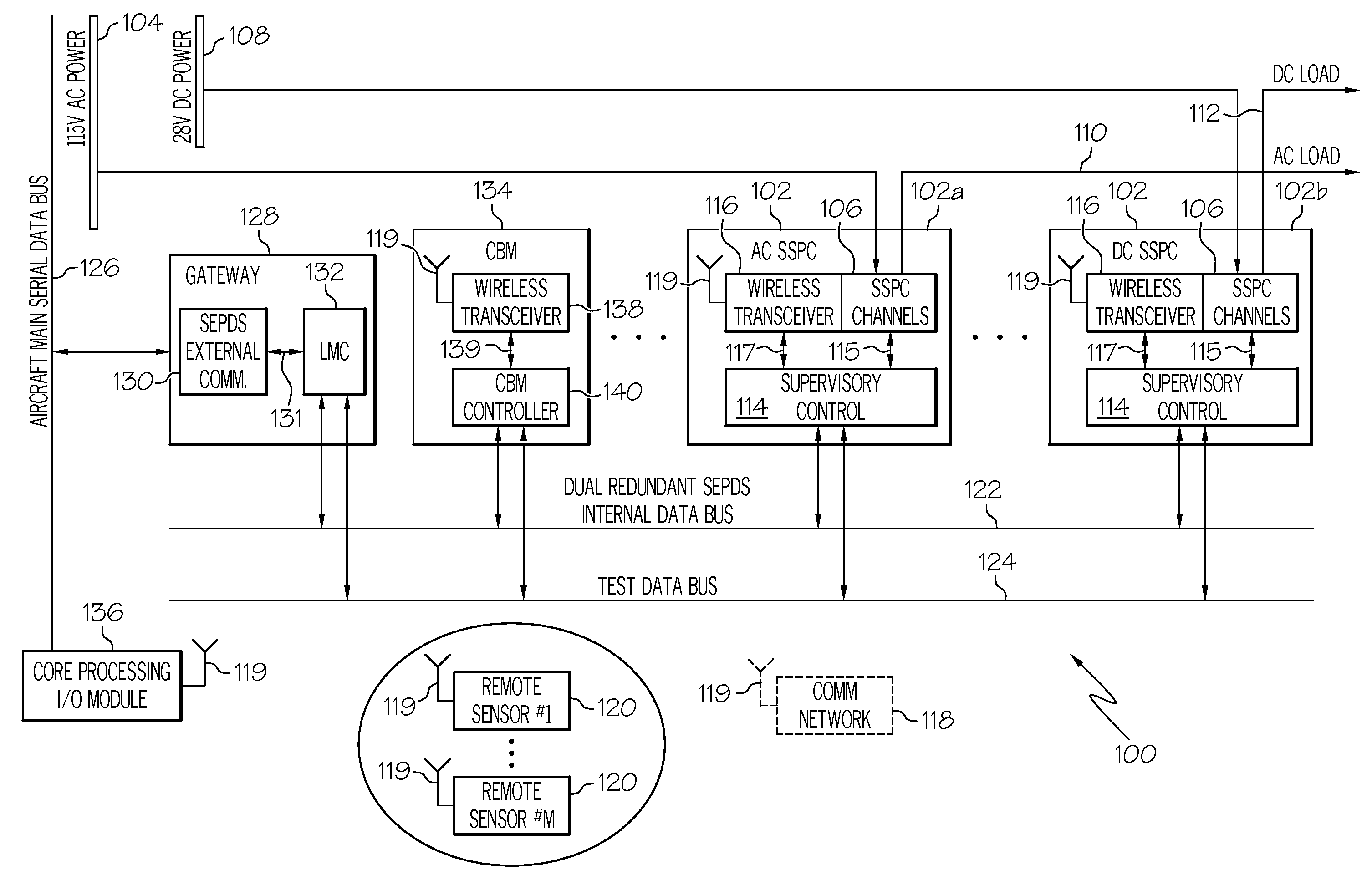
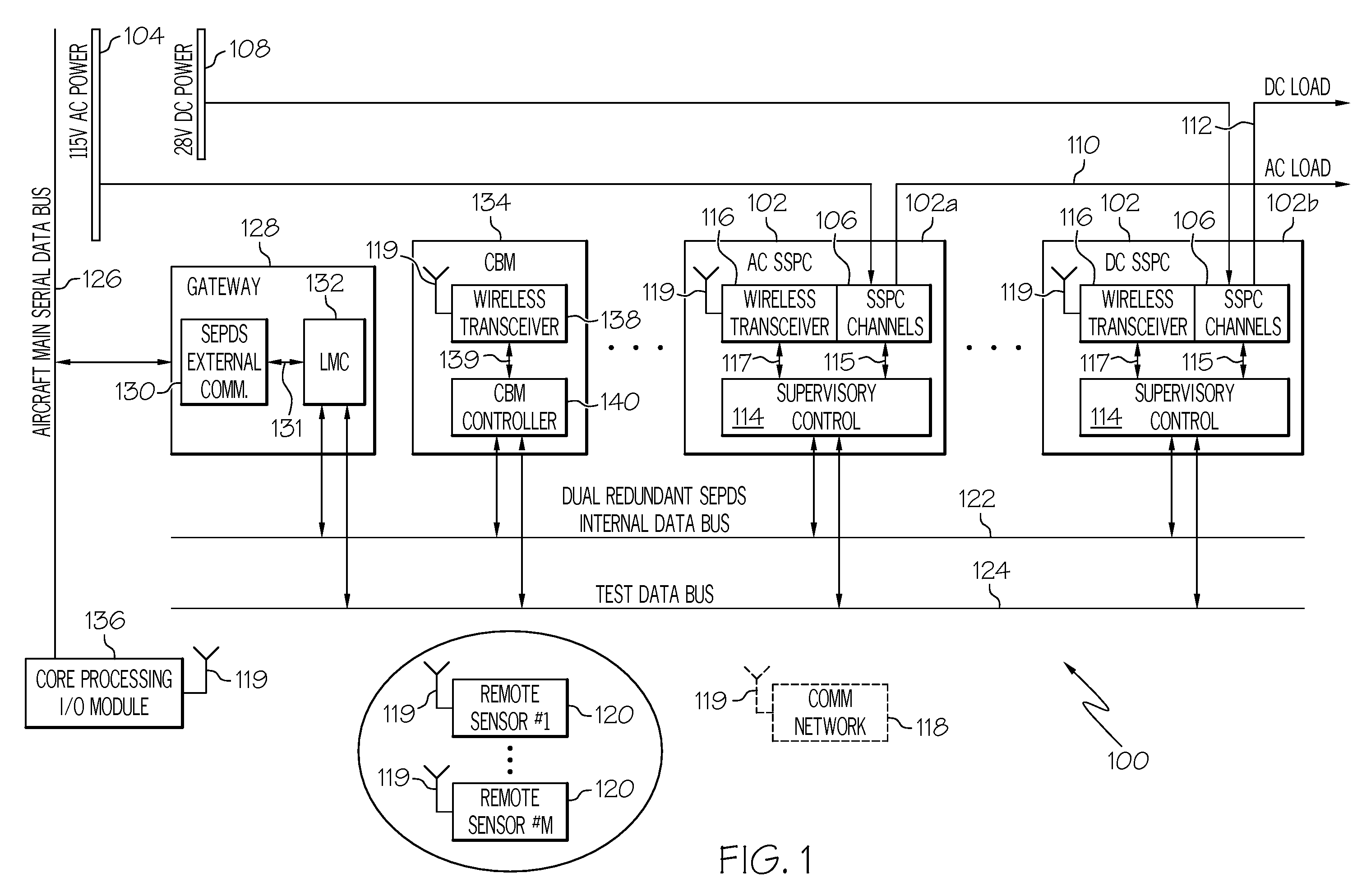
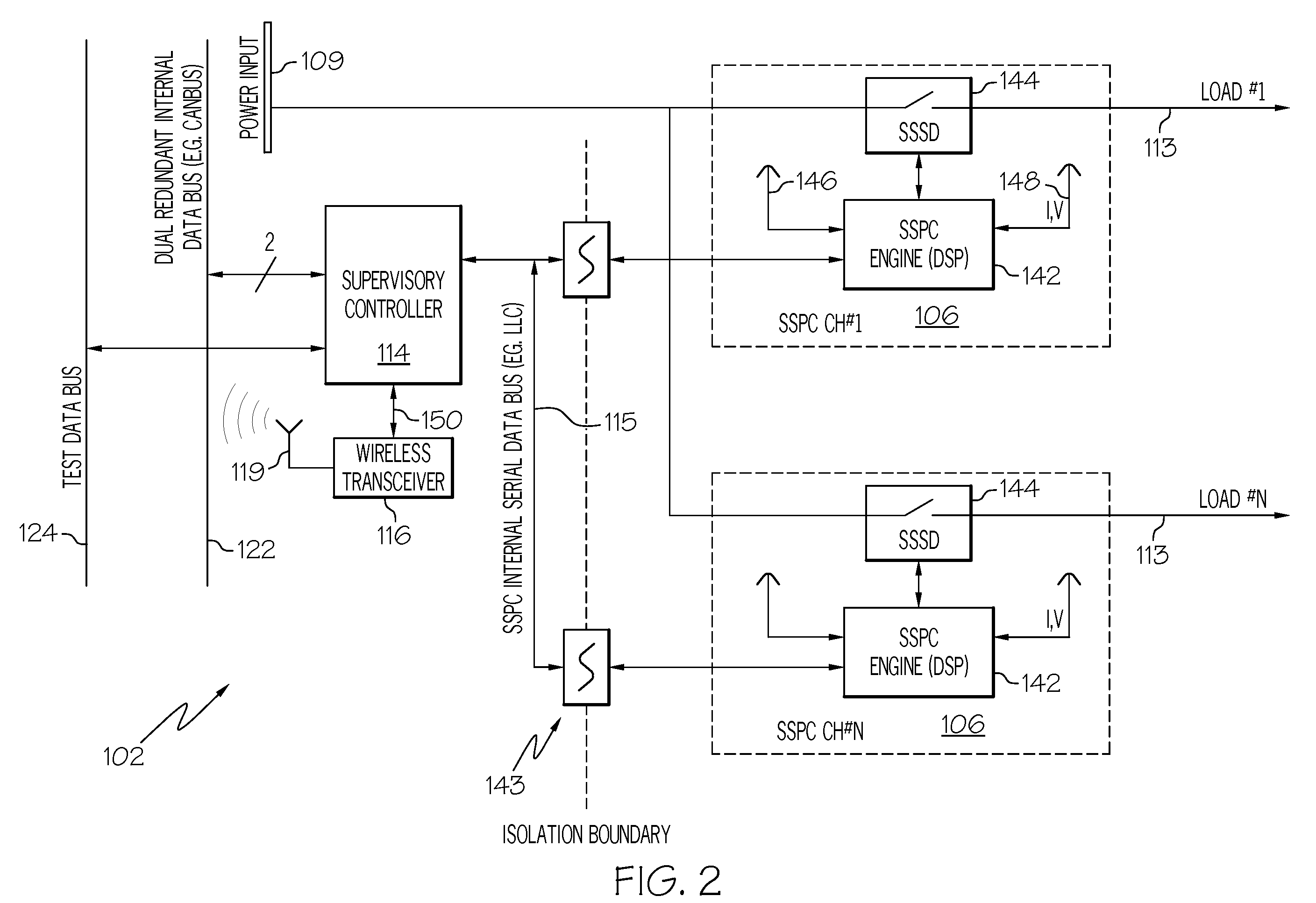
Intelligent aircraft secondary power distribution system that facilitates condition based maintenance
An electrical power distribution system comprises a solid state power controller in communication with an aircraft system main data bus via a gateway module and a condition based maintenance module in communication with the solid state power controller via a communication network distinct from the main data bus. A method of load / feeder health assessment for an electrical power distribution system includes applying a controlled excitation to a load; sampling information from the load / feeder system for the load; characterizing a normal behavior of the load / feeder system for the load; determining if the load characteristics are within the normal behavior profile for the load; and shutting down power to the load if load characteristics are not within the profile when immediate action is indicated or generating a health message for the load when immediate action is not required.
Owner:HONEYWELL INT INC
Automatic fault classification for model-based process monitoring
ActiveUS7533070B2Reduce dependenceTesting/monitoring control systemsDigital computer detailsKernel principal component analysisPrincipal component analysis
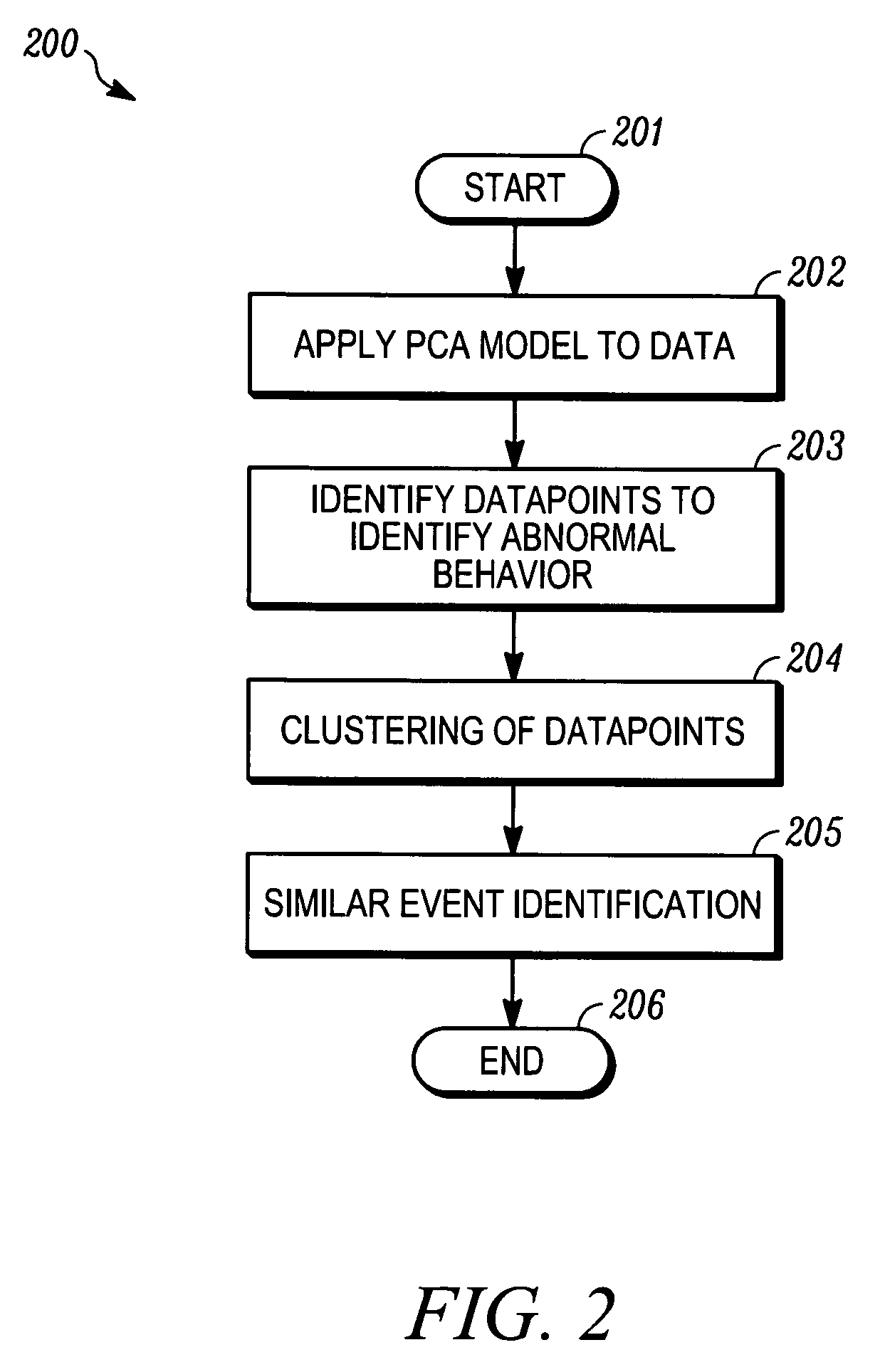
A computer implemented method, system and program product for automatic fault classification. A set of abnormal data can be automatically grouped based on sensor contribution to a prediction error. A principal component analysis (PCA) model of normal behavior can then be applied to a set of newly generated data, in response to automatically grouping the set of abnormal data based on the sensor contribution to the prediction error. Data points can then be identified, which are indicative of abnormal behavior. Such an identification step can occur in response to applying the principal component analysis mode of normal behavior to the set of newly generated data in order to cluster and classify the data points in order to automatically classify one or more faults thereof. The data points are automatically clustered, in order to identify a set of similar events, in response to identifying the data points indicative of abnormal behavior.
Owner:HONEYWELL INT INC
Method and device for detecting tumbling
ActiveCN102302370AReduce complexityEffective filteringDiagnostic recording/measuringSensorsFeature vectorCharacteristic space
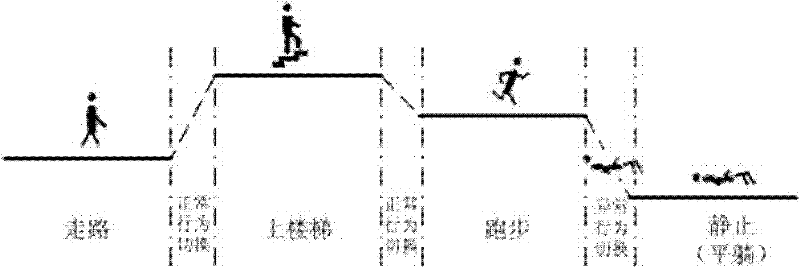
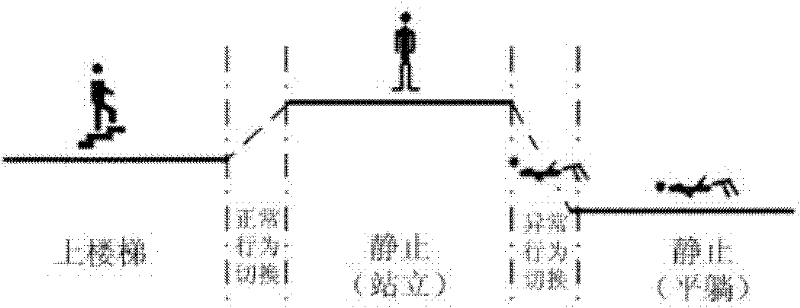
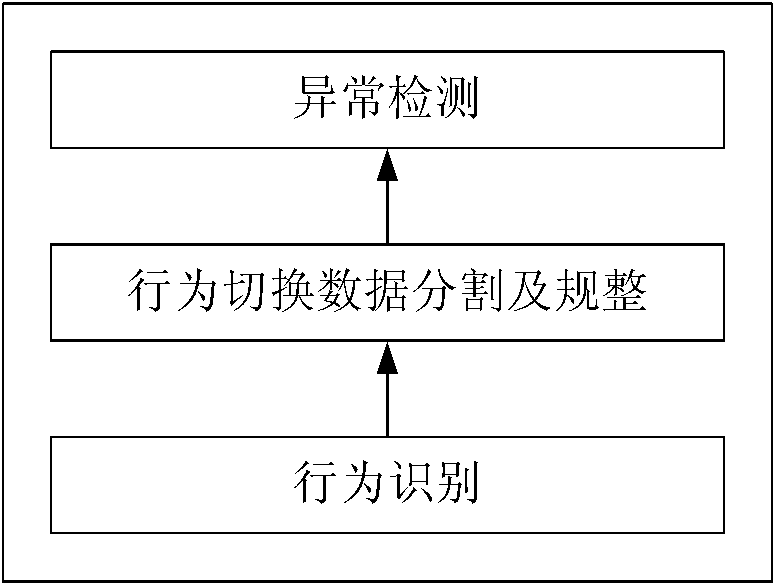
The invention provides a method and device for detecting tumbling. The method provided by the invention comprises the steps of: firstly, collecting behavioral data of a user; secondly, identifying behavior of the user according to the behavioral data of the user; thirdly, segmenting out behavioral switching data from the collected data according to a behavioral identification result, and warping the behavioral switching data into equilong characteristic vectors; and fourthly, performing tumbling detection according to the warped characteristic vectors. According to the method and device provided by the invention, tumbling detection is performed on the basis of behavioral switching, a great amount of normal behavioral data can be filtered, the complexity of a feature space is reduced, the separating capacity of models is enhanced, and the model detection rate is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
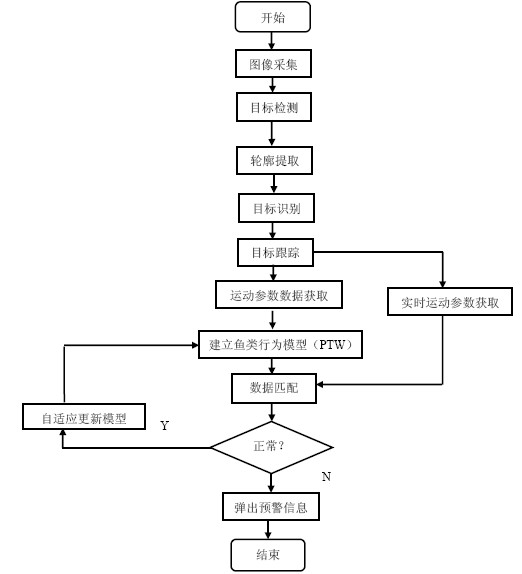
Biologic water quality monitoring system for perceiving fish behaviors based on vision
ActiveCN102012419AImprove reusabilityEnhanced couplingImage analysisGeneral water supply conservationData modelingVision based
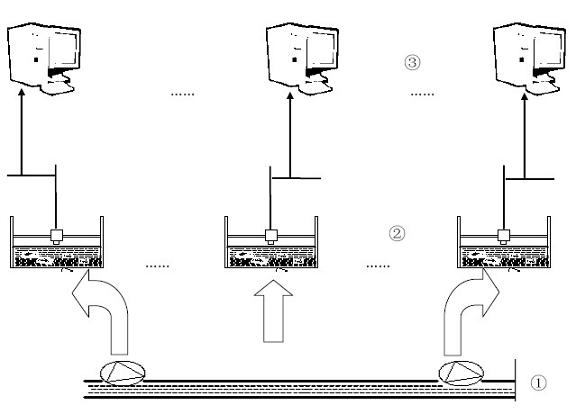
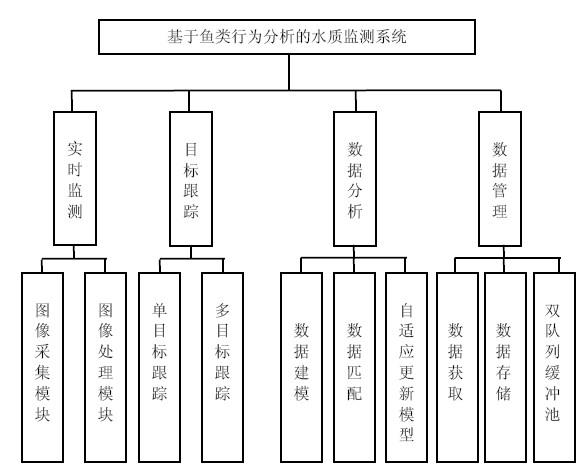
The invention relates to a biologic water quality monitoring system for perceiving fish behaviors based on vision, comprising a transparent aquarium for containing fishes, cameras for monitoring fish behaviors, video capture cards and a water quality monitoring center, wherein the aquarium is positioned in the visual ranges of the cameras; all cameras are in data communication link with the waterquality monitoring center by the video capture cards; and the water quality monitoring center comprises an image capture module, an image processing module, a target tracking module and a fish behavior data analysis module. The fish behavior data analysis module comprises a data modeling part and a data matching part, obtains data of image frame sequence of a water area to be analyzed and substitutes the data into model formals (6) and (7) for matching. If the difference between a present calculated value and a normal action value is in the range of a default threshold, the fact represents that the fish behaviors are normal and judges that water quality conditions are good. If the difference is beyond the range of the default threshold, the fact judges that the water is polluted. The biologic water quality monitoring system reduces cost, is suitable for large-scale application and has good practicality.
Owner:ZHEJIANG UNIV OF TECH
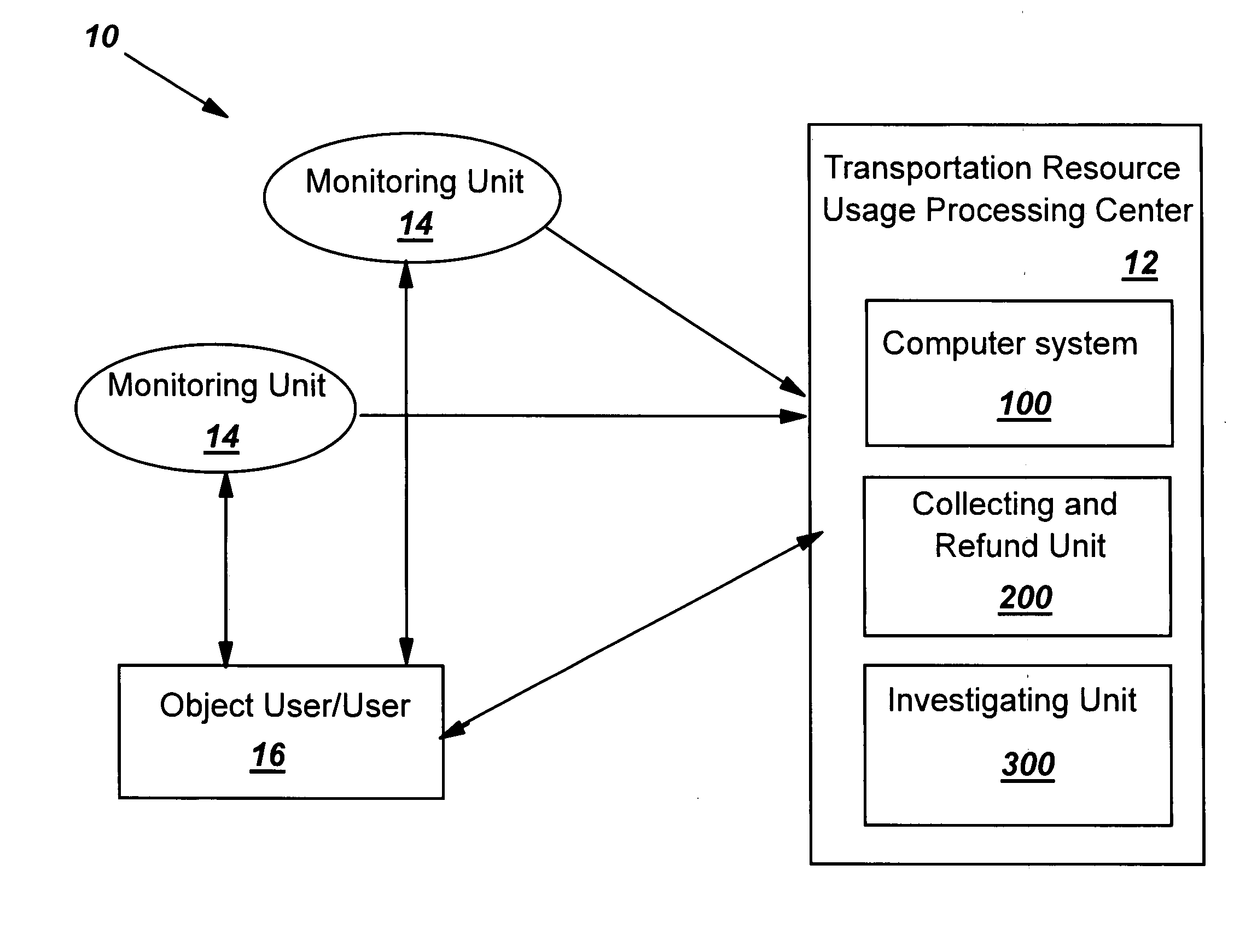
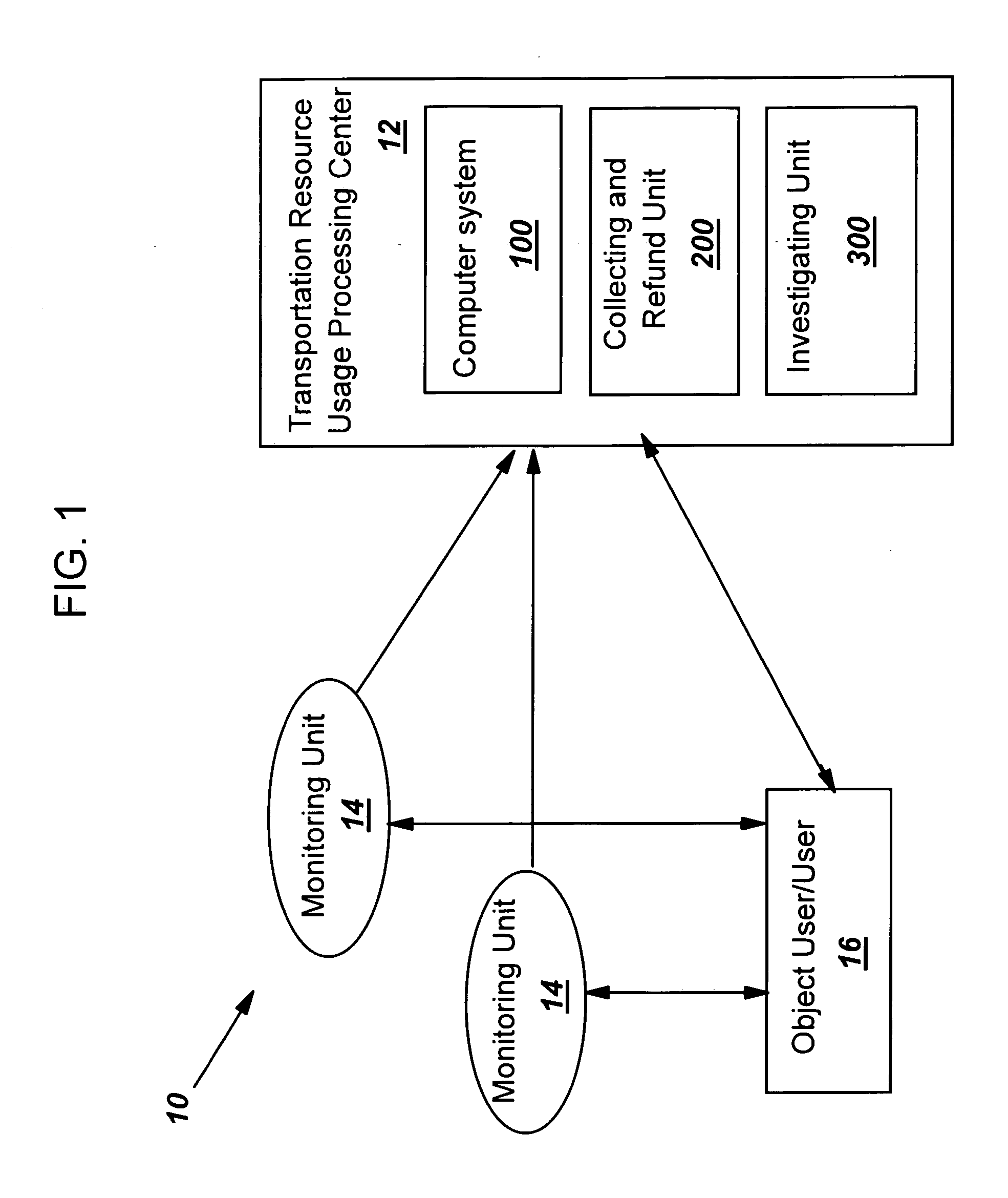
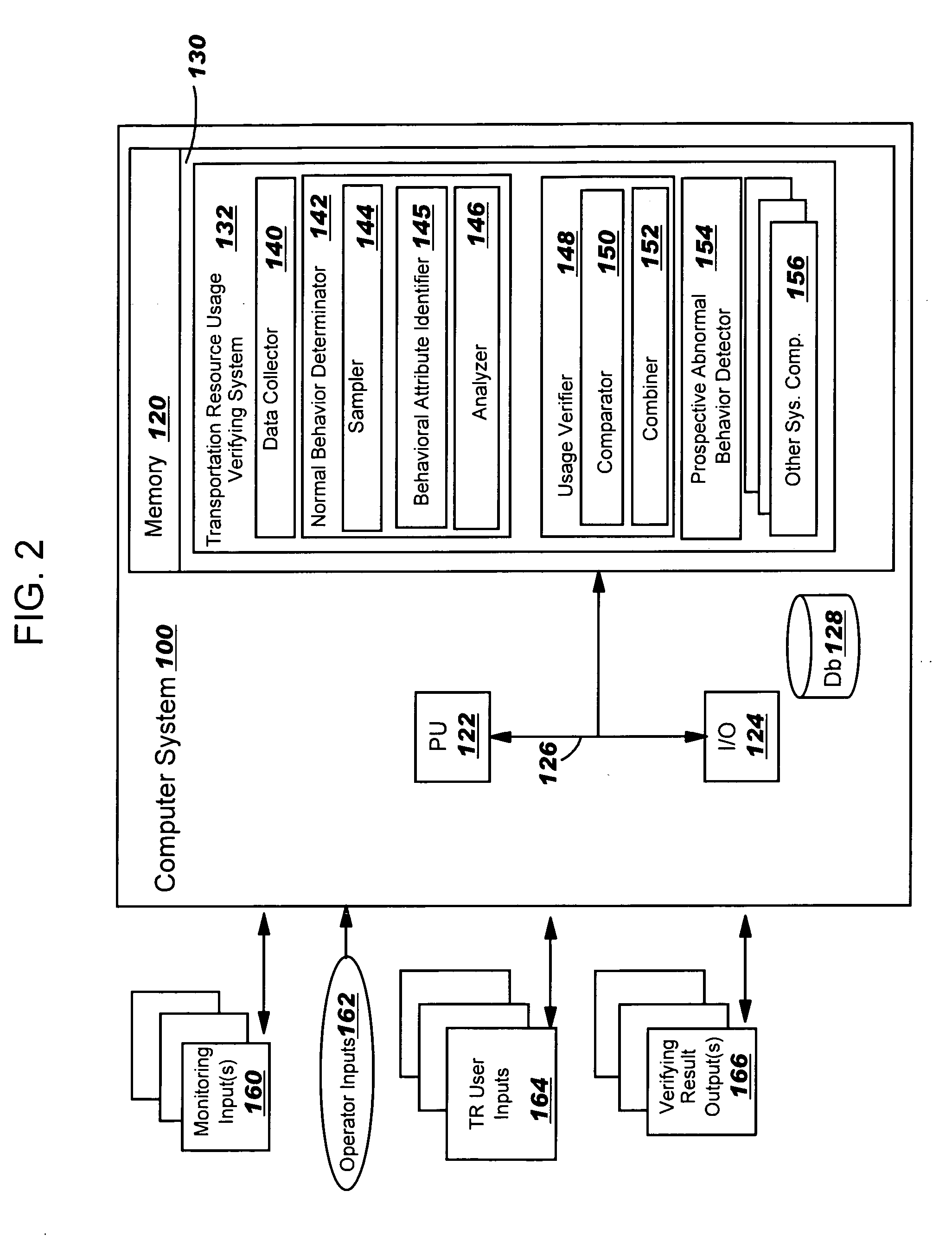
Verifying a usage of a transportation resource
A method, system and computer program product for verifying a usage of a transportation resource by an object user of the transportation resource is disclosed. A peer group of users that are expected to behave similarly as the object user is established to determine a normal behavior that the object user is supposed to act consistent with. An observed behavior of the object user is compared to the normal behavior to verify a usage of the transportation resource by the object user.
Owner:IBM CORP
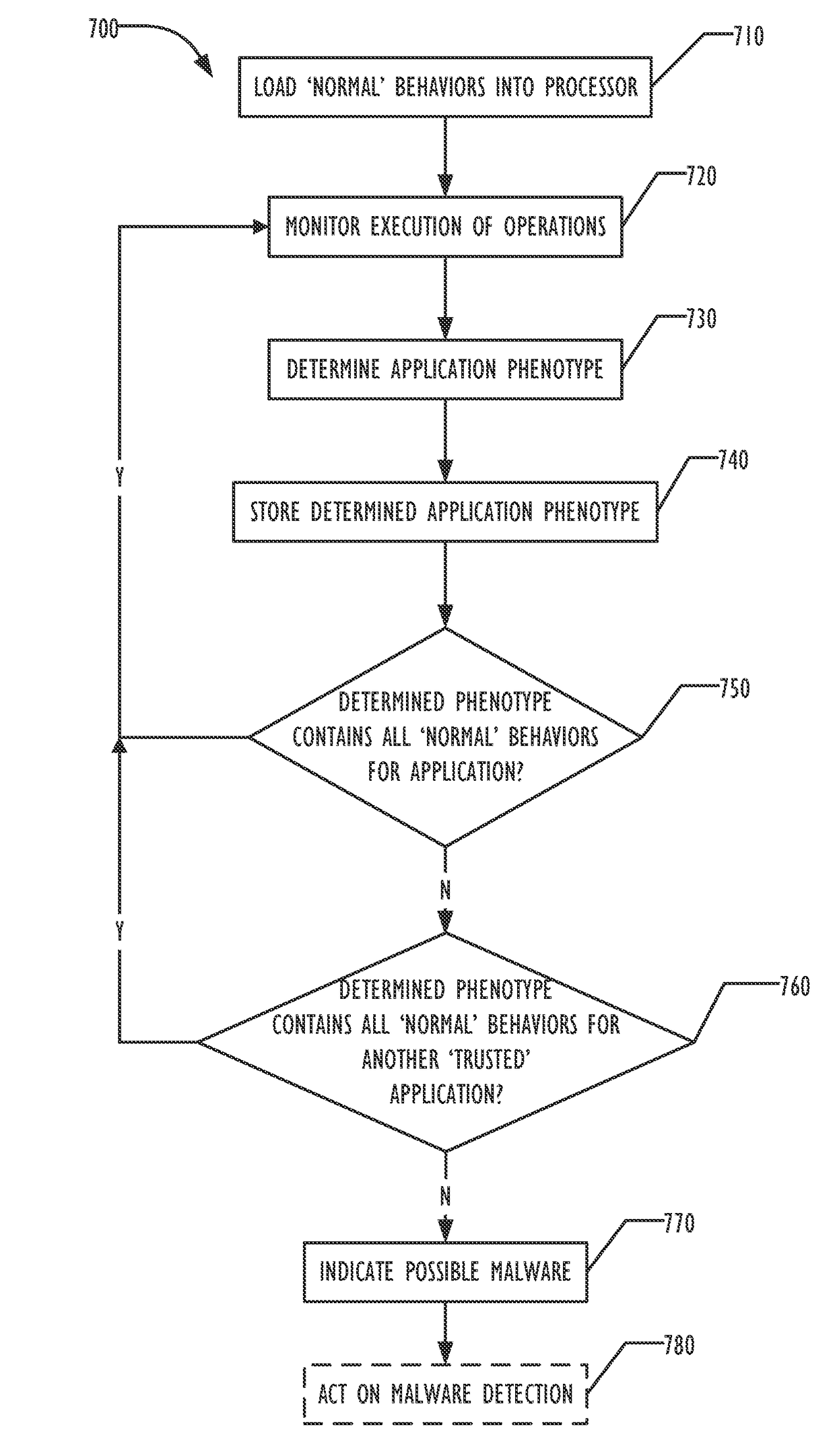
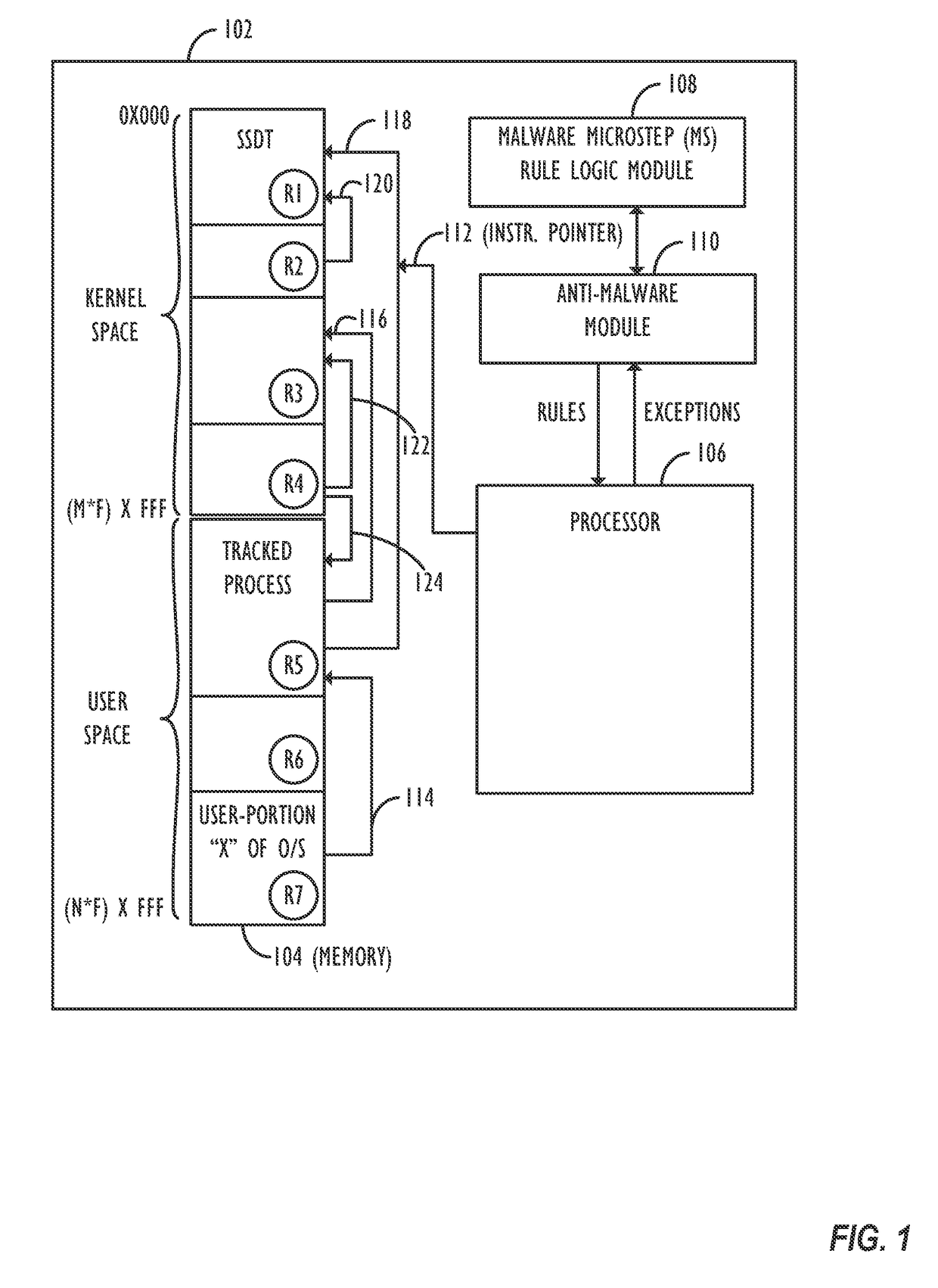
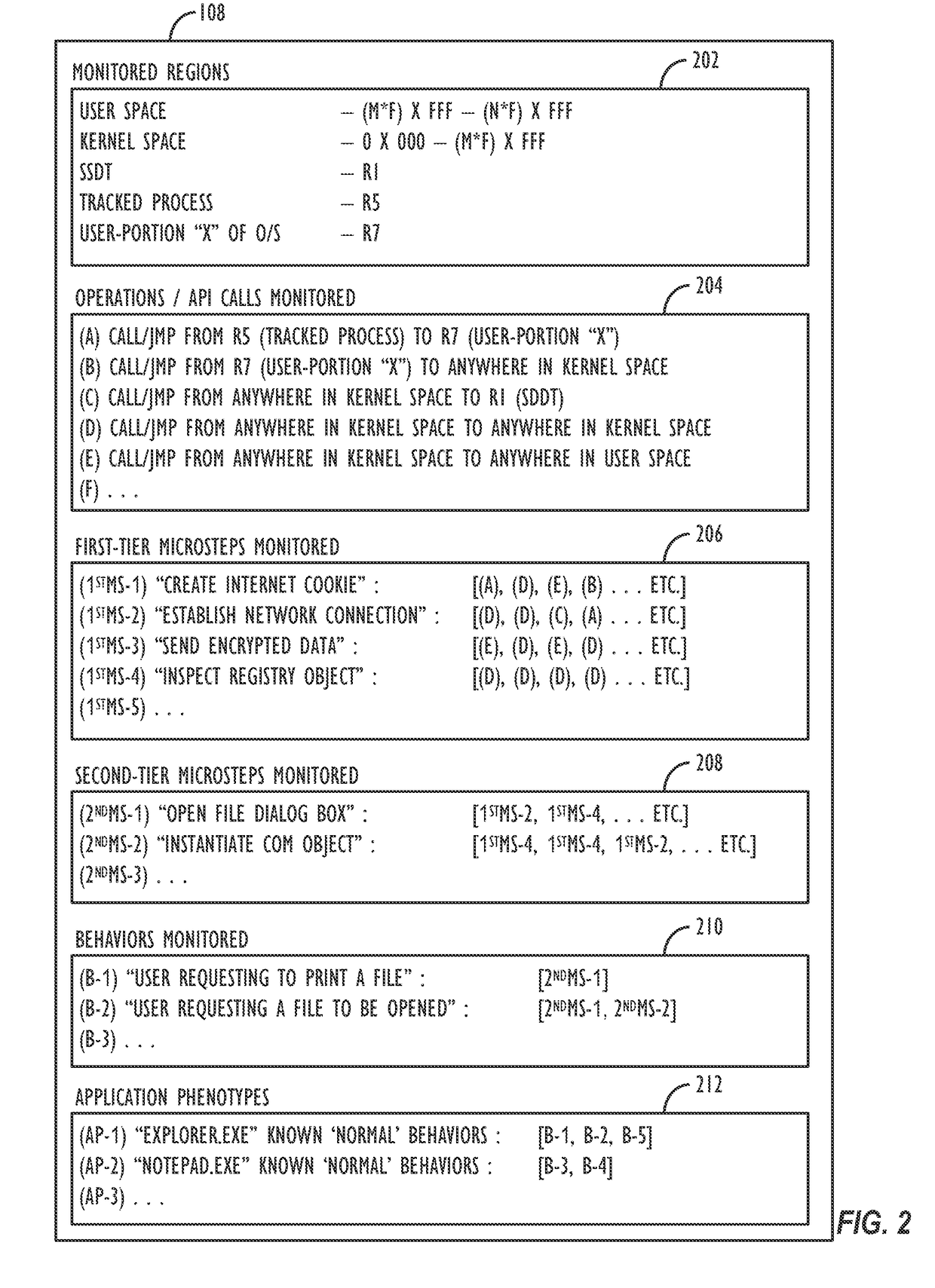
Application phenotyping
ActiveUS20170093897A1Digital data information retrievalComputer security arrangementsUser deviceInternet privacy
A collection of techniques is disclosed to allow for the detection of malware that leverages pattern recognition and machine learning to effectively provide “content-less” malware detection, i.e., detecting a process as being an ‘anomaly’ not based on its particular content, but instead based on comparisons of its behavior to known (and characterized) ‘trusted’ application behaviors, i.e., the trusted applications' “phenotypes” and / or the phenotypes of known malware applications. By analyzing the patterns of normal behavior performed by trusted applications as well as malware applications, one can build a set of sophisticated, content-agnostic behavioral models (i.e., “application phenotypes”)—and later compare the processes executed on a user device to the stored behavioral models to determine whether the actual measured behavior reflects a “good” application, or if it differs from the stored behavioral models to a sufficient degree and with a sufficient degree of confidence, thus indicating a potentially malicious application or behavior.
Owner:MCAFEE LLC
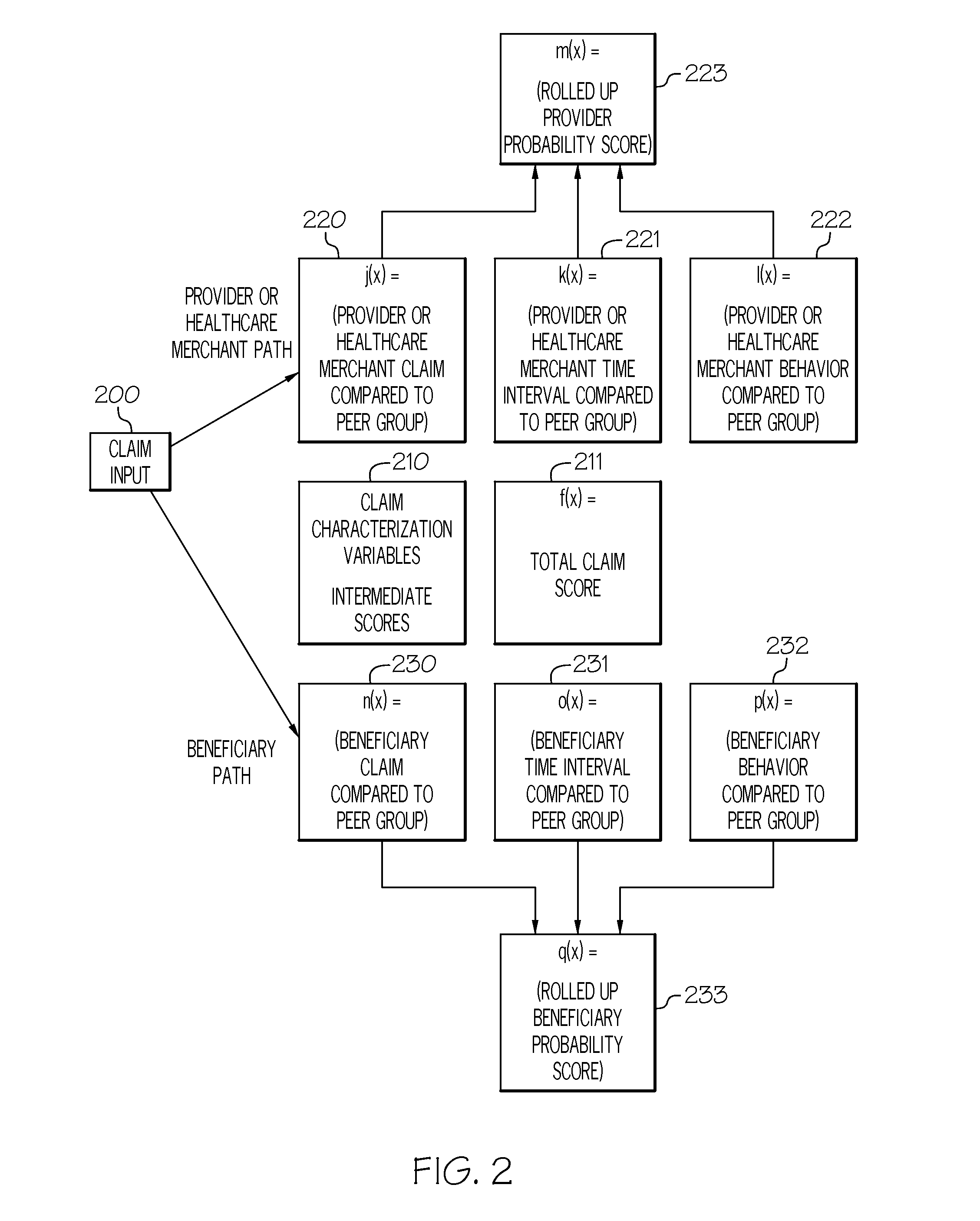
Characterizing healthcare provider, claim, beneficiary and healthcare merchant normal behavior using non-parametric statistical outlier detection scoring techniques
InactiveUS20130085769A1Predictive performanceHigh false positive rateOffice automationPatient-specific dataScalar ValueCrowds
This invention uses non-parametric statistical measures and probability mathematical techniques to calculate deviations of variable values, on both the high and low side of a data distribution, from the midpoint of the data distribution. It transforms the data values and then combines all of the individual variable values into a single scalar value that is a “good-ness” score. This “good-ness” behavior score model characterizes “normal” or typical behavior, rather than predicting fraudulent, abusive, or “bad”, behavior. The “good” score is a measure of how likely it is that the subject's behavior characteristics are from a population representing a “good” or “normal” provider, claim, beneficiary or healthcare merchant behavior. The “good” score can replace or compliment a score model that predicts “bad” behavior in order to reduce false positive rates. The optimal risk management prevention program should include both a “good” behavior score model and a “bad” behavior score model.
Owner:RISK MANAGEMENT SOLUTIONS
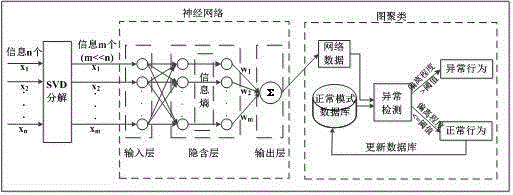
User abnormal behavior detection method based on neural network clustering
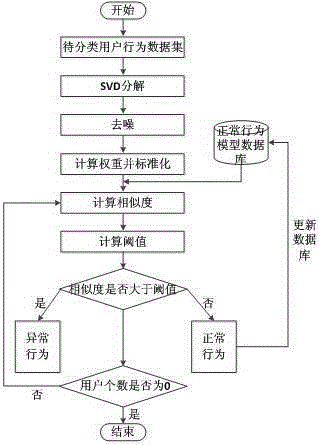
ActiveCN105224872AFacilitate accurate diagnosisImprove signal-to-noise ratioCharacter and pattern recognitionPlatform integrity maintainanceHidden layerNerve network
The invention discloses a user abnormal behavior detection method based on neural network clustering. The method comprises: firstly, performing SVD decomposition and denoising on a behavior data set matrix of a user, and inputting the denoised matrix to an input layer of a neural network, and then calculating weight of all attributes of each user in a hidden layer of the neural network, and standardizing the weight, outputting the weight in an output layer, and finally respectively calculating similarity value of each user and each user in a normal behavior model database and a threshold value, if the similarity value is larger than the threshold value, behavior being abnormal behavior, and carrying out corresponding prompt and precautionary measures, otherwise, the behavior being normal behavior, and combining the behavior in the normal model database to upgrade the database in real time. Through cooperation of each part, the method effectively realizes high detection rate and low false alarm rate.
Owner:HENAN UNIV OF SCI & TECH
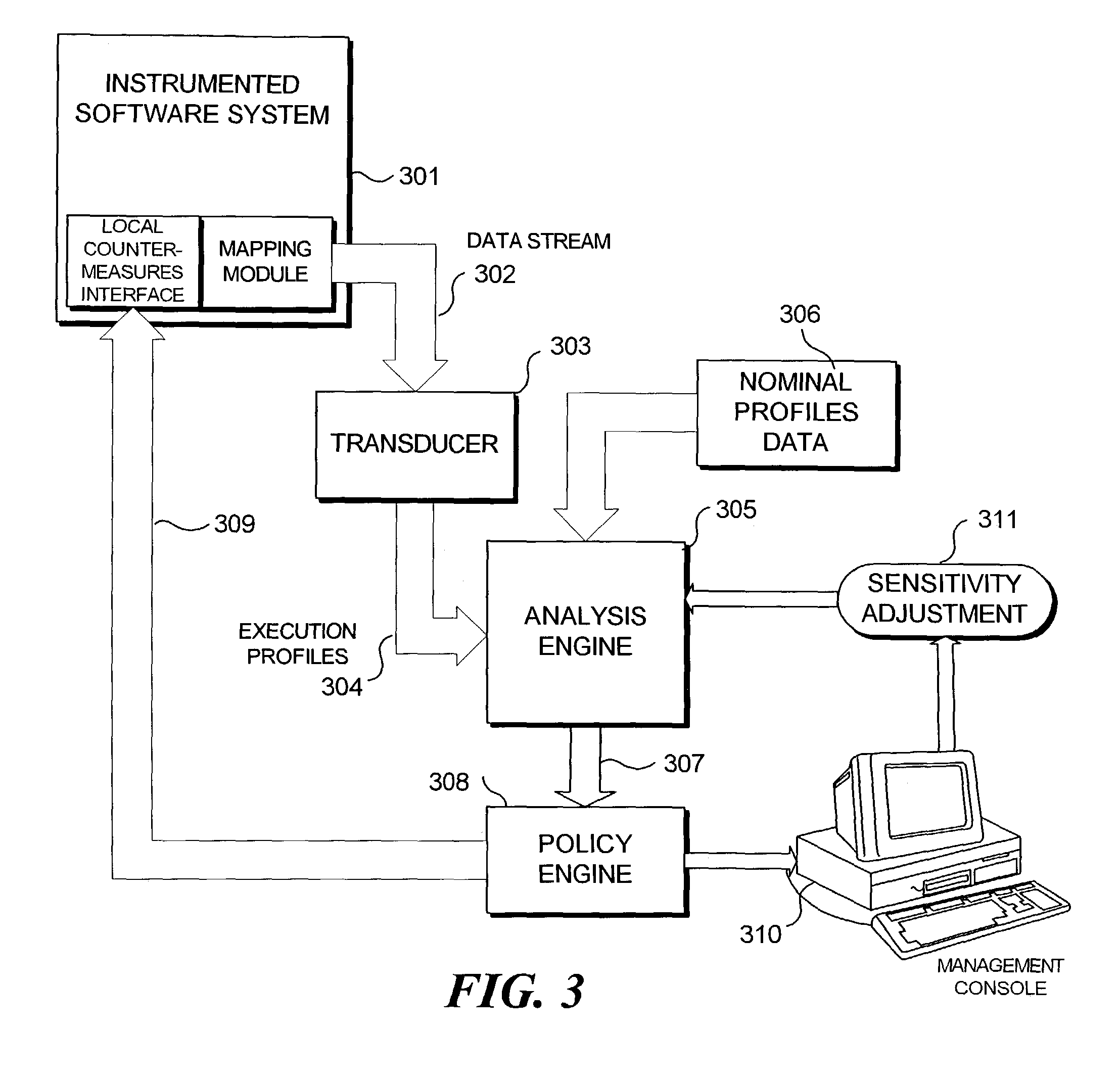
Method and system for simplifying the structure of dynamic execution profiles
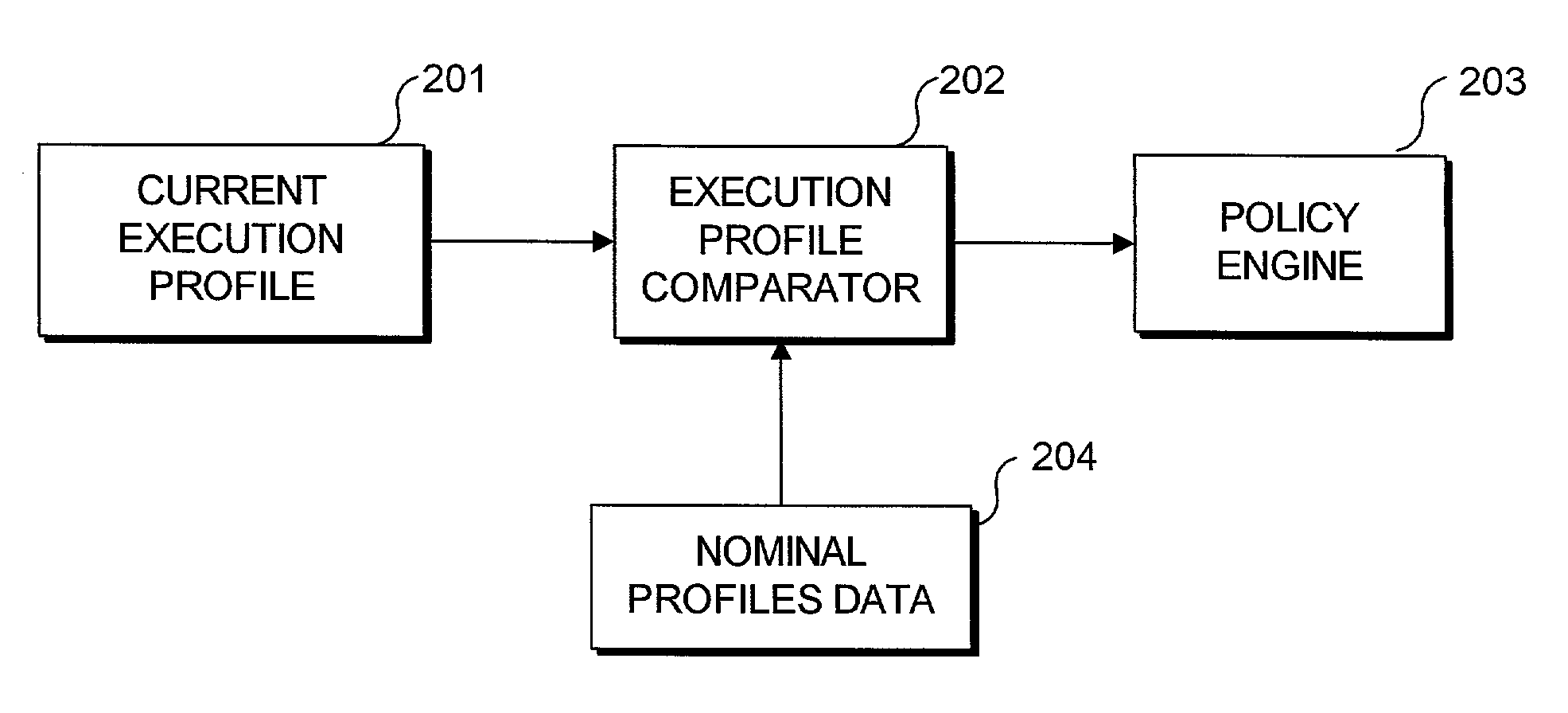
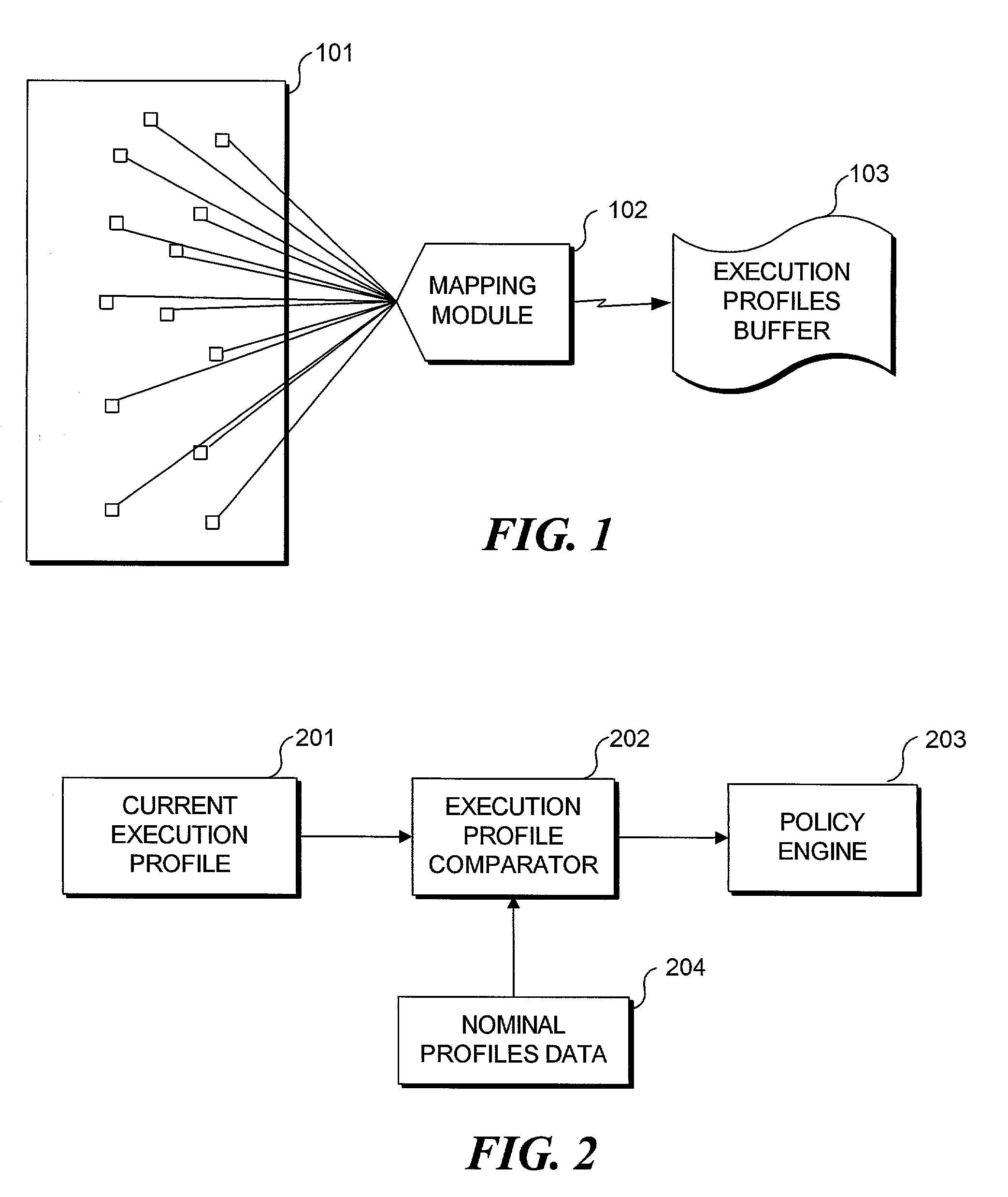
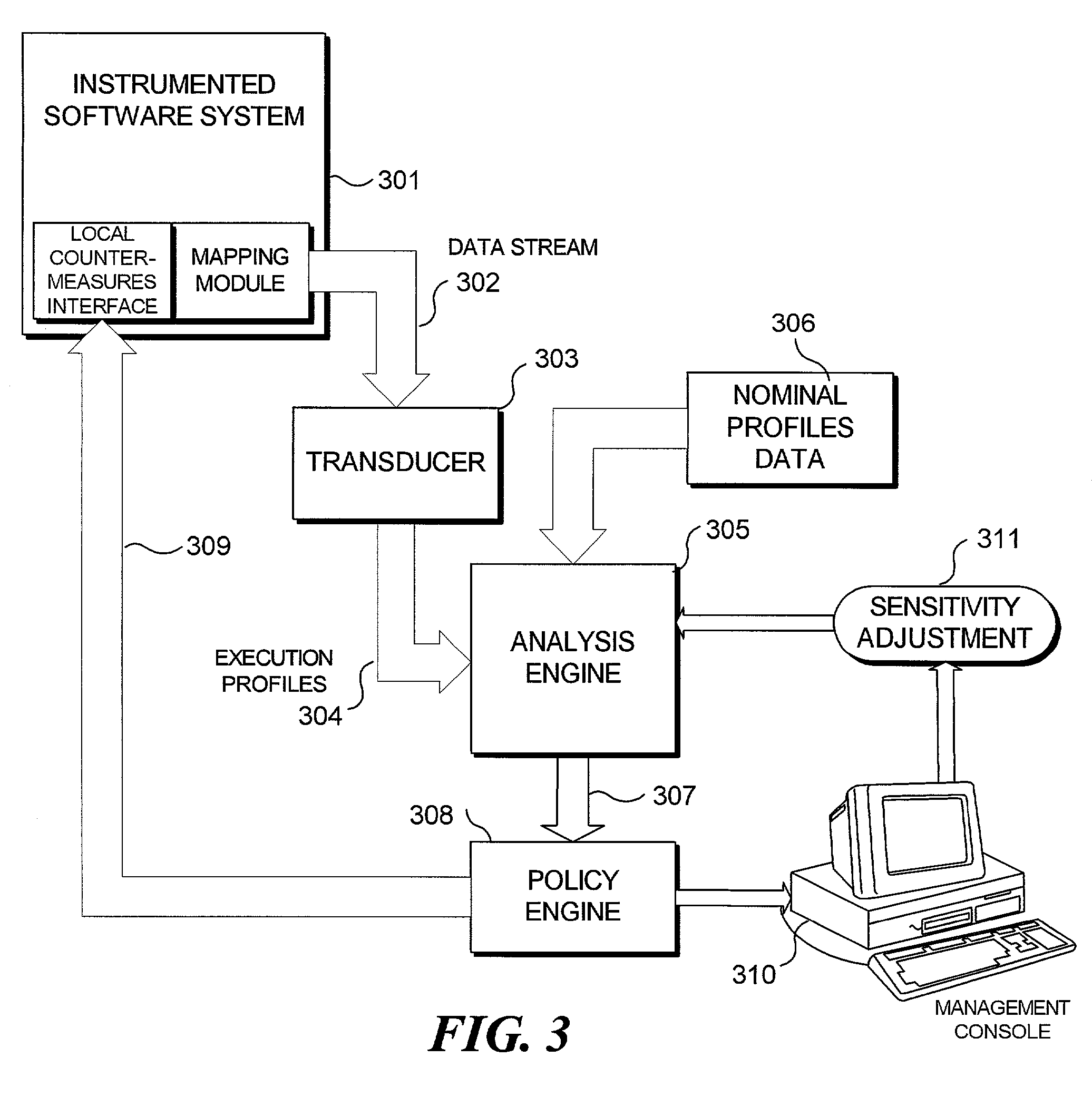
InactiveUS7096499B2Reduce dimensionalityReduce in quantityMemory loss protectionDigital data processing detailsSoftware systemTheoretical computer science
A real-time approach to detecting aberrant modes of system behavior induced by abnormal and unauthorized system activities indicative of abnormal activity of a software system is based on behavioral information obtained from a suitably instrumented computer program as it is executing. The theoretical foundation is founded on a study of the internal behavior of the software system. As a software system is executing, it expresses a set of its many functionalities as sequential events. Each of these functionalities has a characteristic set of modules that is executed to implement the functionality. These module sets execute with defined and measurable execution profiles among the program modules and within the execution paths of the individual modules, which change as the executed functionalities change. Over time, the normal behavior of the system will be defined by the boundary of the profiles. Abnormal activity of the system will result in behavior that is outside the normal activity of the system and thus result in a perturbation of the system in a manner outside the scope of the normal profiles. Such anomalies are detected by analysis and comparison of the profiles generated from an instrumented software system against a set of nominal execution profiles. Moreover, a method for reducing the amount of information necessary to understand the functional characteristics of an executing software system identifies the common sources of variation among the program instrumentation point frequencies and builds execution profiles based on a reduced set of virtual execution domains.
Owner:STRATACLOUD
All-weather defence home security alarm system based on behavioural analysis
InactiveCN101866521AAvoid false positivesImprove securityBurglar alarm by openingBurglar alarm short radiation actuationHuman bodyEngineering
The invention discloses an all-weather defence home security alarm system based on behavioural analysis, which comprises an identity recognizer, a vector door detector, a double curtain intelligent linked probe, a human body sensing counter and an anti-theft alarm mainframe; wherein the identity recognizer cooperates with the vector door detector to monitor and analyze the access behaviour of the human body through the door; the double curtain intelligent linked probe is matched with the human body sensing counter to monitor and analyze the access behaviour of the human body through the balcony; and the anti-theft alarm mainframe discriminate between the normal behaviour and the illegal behaviour, thereby realizing the all-weather defence of the home security alarm system, achieving more safety and reliable use and avoiding the leaking and fault alarm phenomenon .More importantly, the home security alarm system can not only increase the safety of the family belongings, but enhance the personal safety effectively.
Owner:叶斌 +2
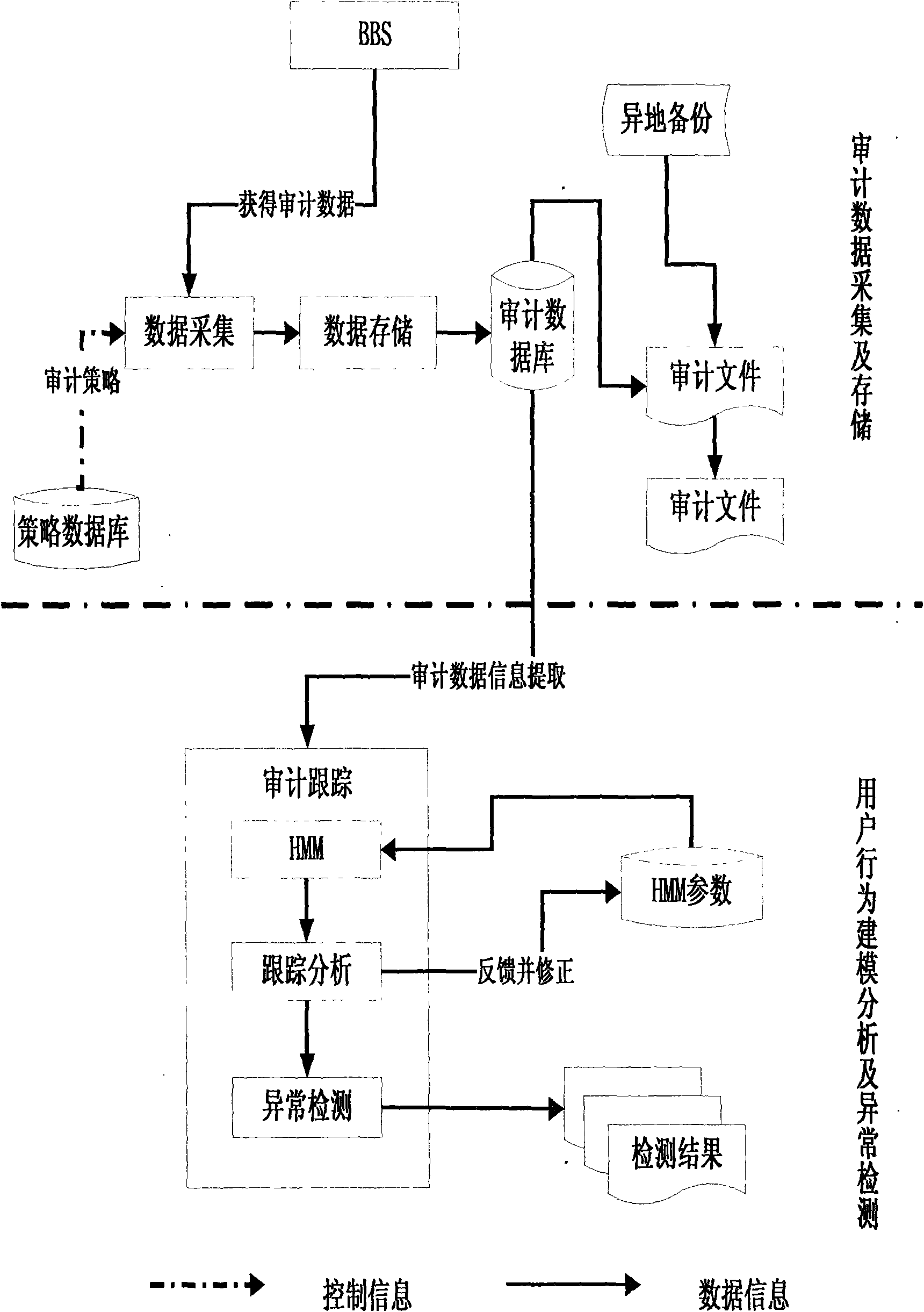
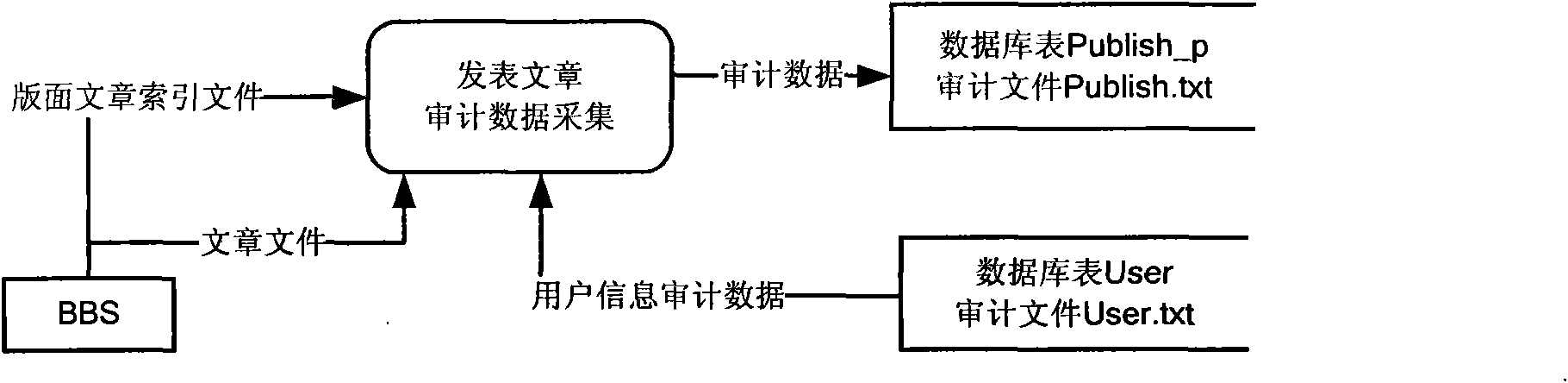
BBS user abnormal behavior auditing method based on Hidden Markov theory
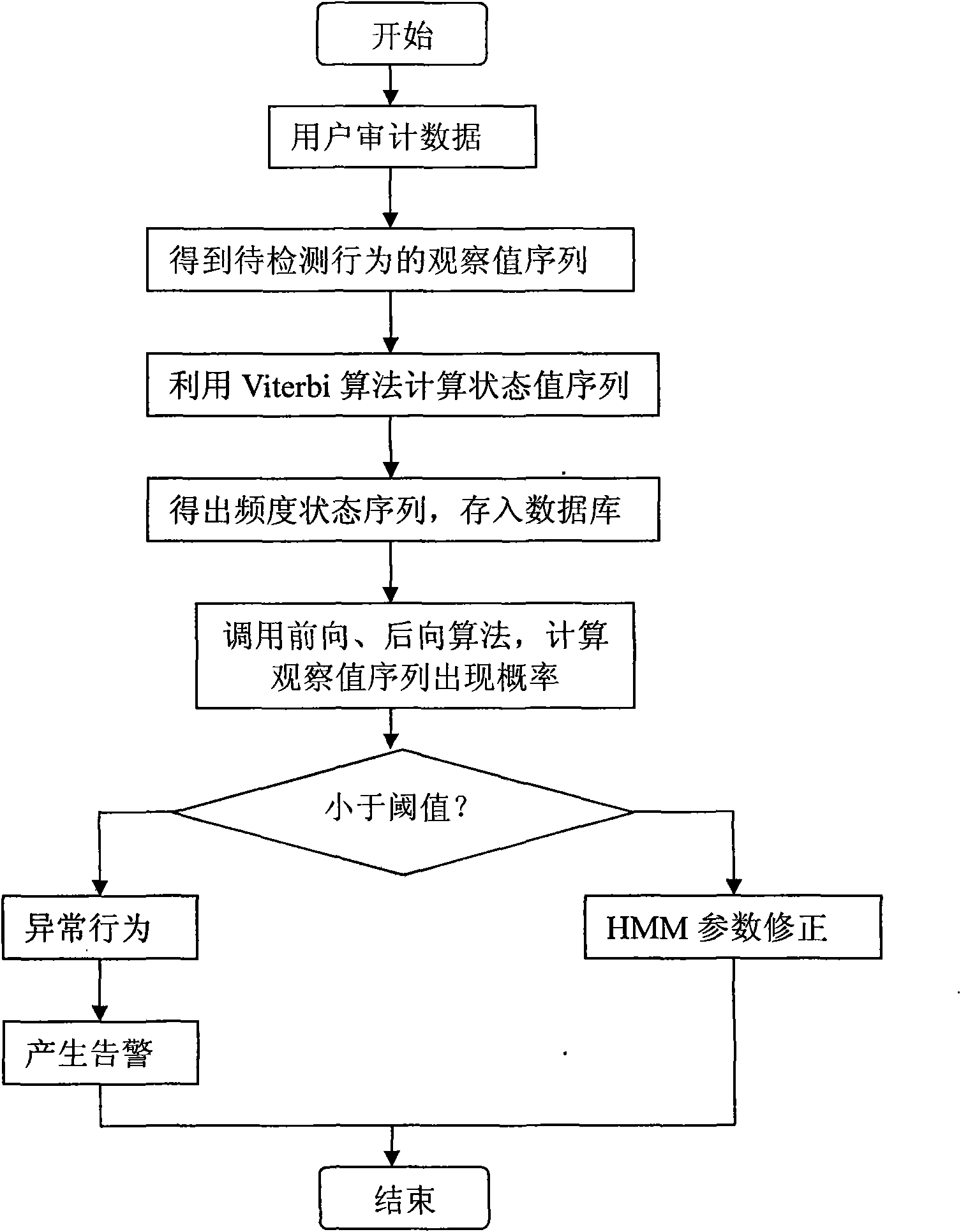
InactiveCN101615186AFree from harmImprove securityComputer security arrangementsData switching networksAlgorithmHide markov model
The invention relates to a BBS user abnormal behavior auditing method based on Hidden Markov theory, belonging to the technical field of computer and information safety. The method comprises the following steps: reading auditing data from a database to obtain behavior observed sequence to be detected; reading trained model parameters from a Hidden Markov model database; calculating a state value sequence by utilizing a Viterbi algorithm; calculating the observed value sequence probability by forward and afterward algorithms, comparing the observed value sequence probability with the preset threshold, and giving an alarm if the observed value sequence probability is lower than the threshold, otherwise, belonging to normal behavior, correcting the Hidden Markov model parameter and storing the Hidden Markov model parameter into a parameter file of the Hidden Marko model. The BBS added with audit tracking helps system managers to prevent systems and resources from being damaged by illegal authorized users and provides help when data is recovered. The audit tacking can realize associated targets of safety, comprising personal function, event reconstruction, intrusion detection and fault analysis, and greatly improves the safety of the system.
Owner:NORTHEASTERN UNIV
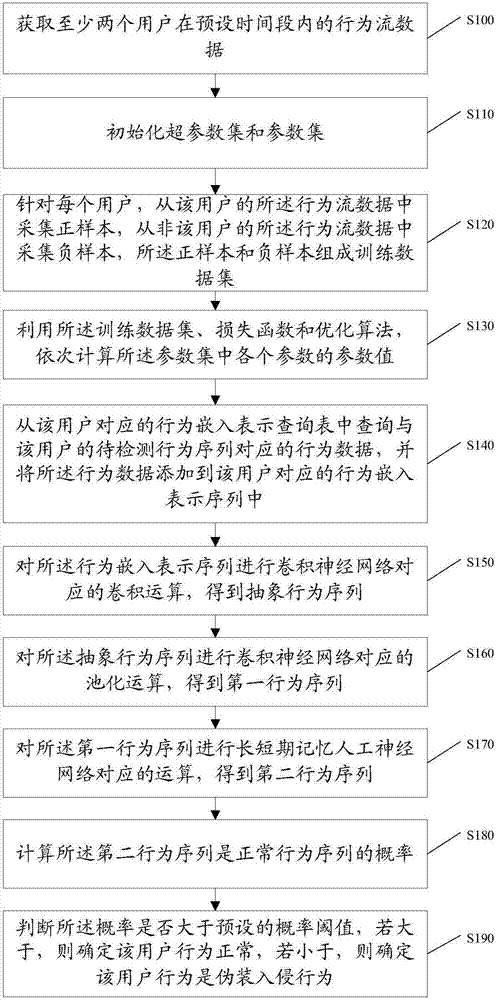
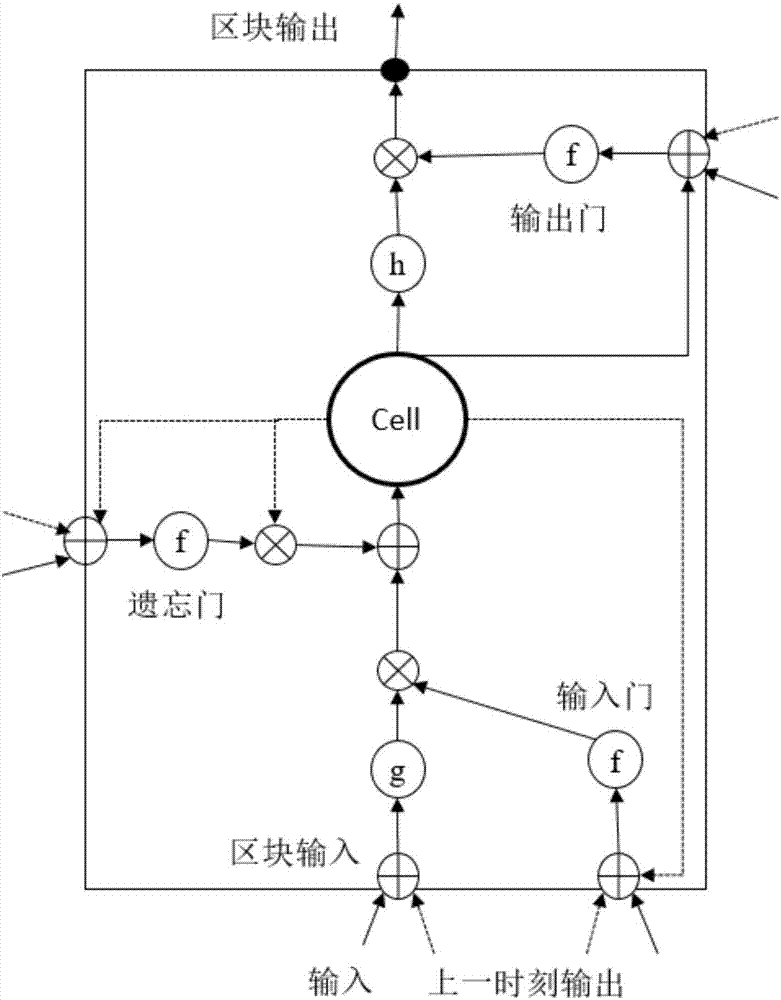
Masquerade intrusion detection method and device based on deep neural network
ActiveCN106951783ALocal strong correlationImprove accuracyPlatform integrity maintainanceNeural architecturesShort-term memoryNerve network
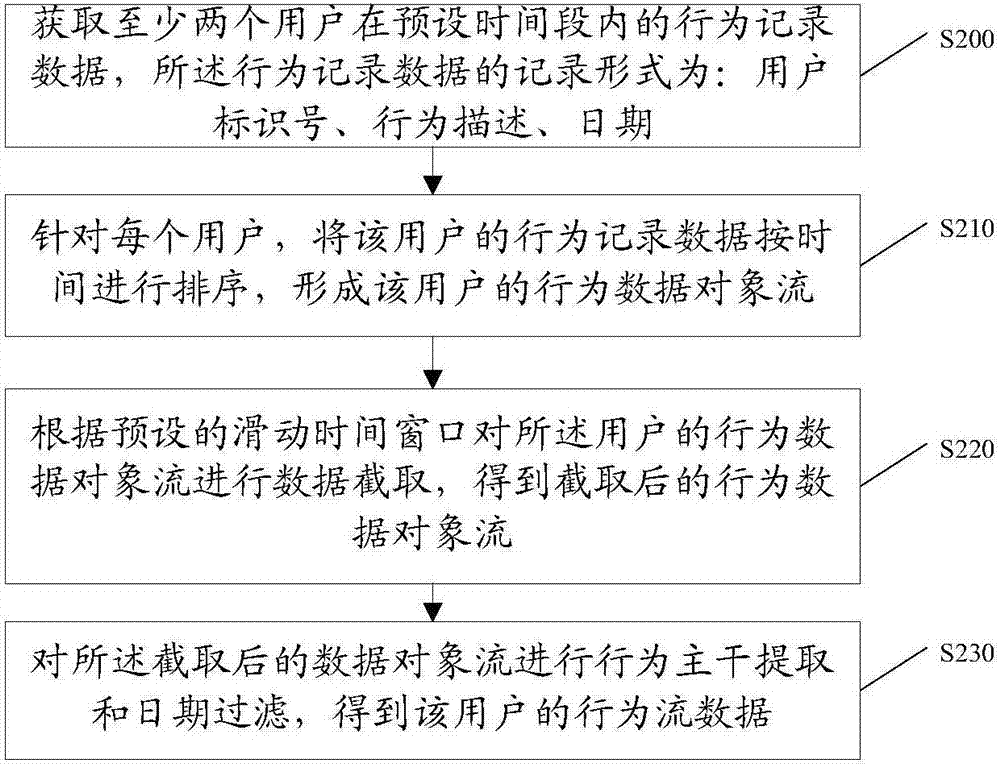
The invention discloses a masquerade intrusion detection method based on a deep neural network. The masquerade intrusion detection method comprises obtaining behavior flow data of at least two users; initializing a super parameter set and a parameter set; acquiring positive samples and negative samples to form a training data set by aiming at each user; sequentially calculating the parameter value of each parameter by means of the training data set, a loss function and an optimization algorithm; querying behavior data corresponding to the behavior sequence to be detected of the user from a behavior embedding representation query table and adding the behavior data to a behavior embedding representation sequence; carrying out convolution operation, pooling operation and operation corresponding to the long short-term memory artificial neural network on the behavior embedding representation sequence to obtain a second behavior sequence; calculating the probability of that the second behavior sequence is a normal behavior sequence; and determining whether the user's behavior is a masquerade intrusion behavior or not in dependence on the probability value. According to the invention, local strong relativity, long-range dependence and time sequence of the behavior are taken into account at the same time, and the masquerade intrusion detection accuracy is improved.
Owner:STATE GRID CORP OF CHINA +1
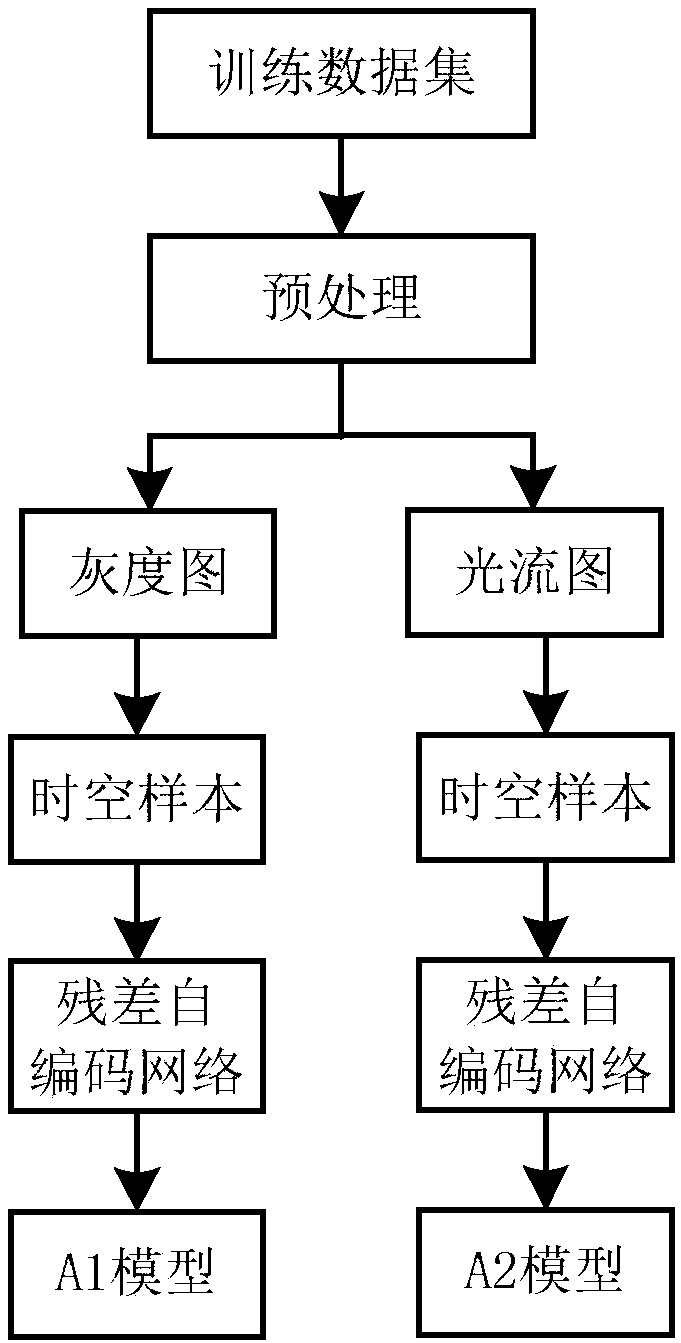
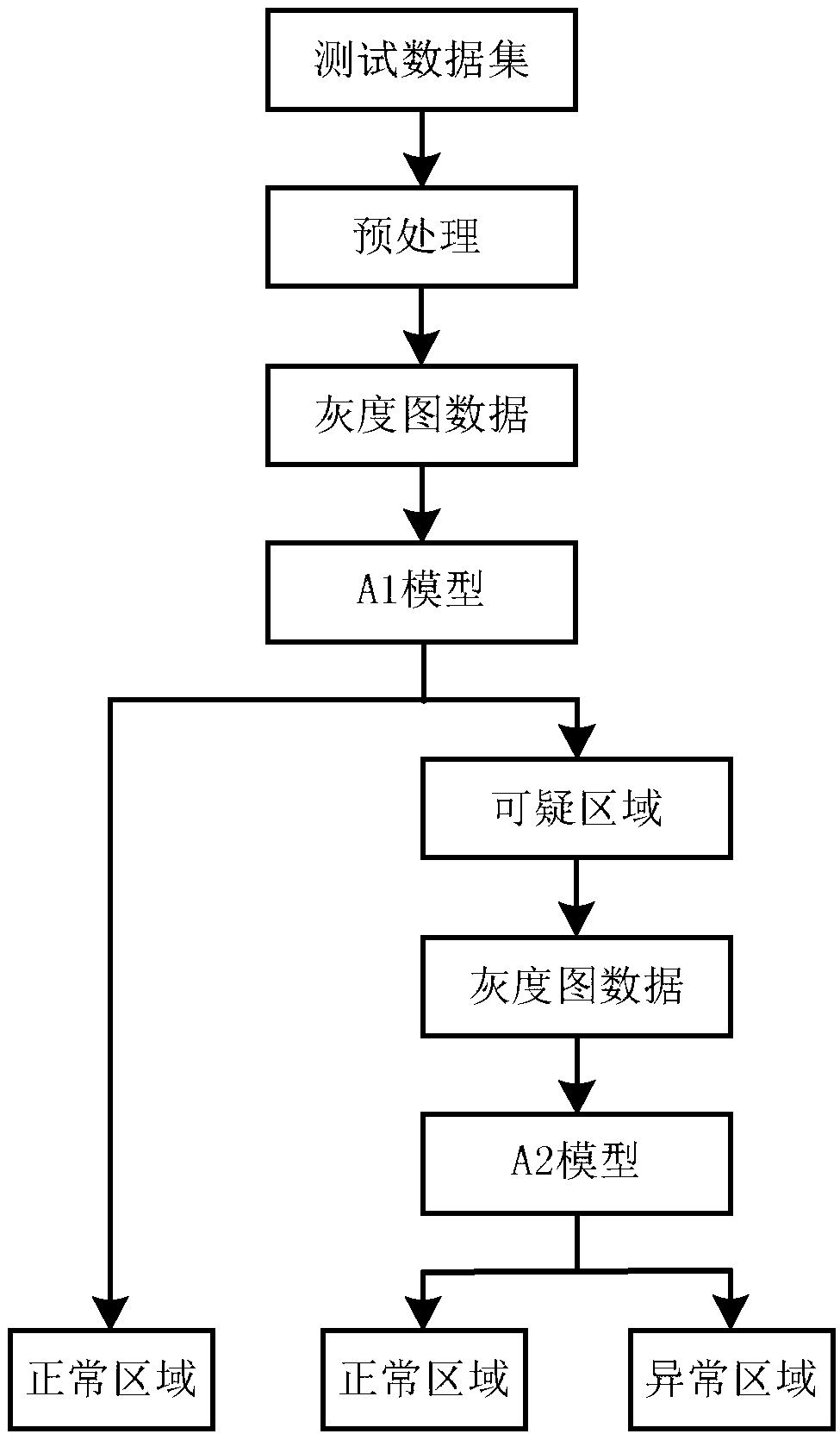
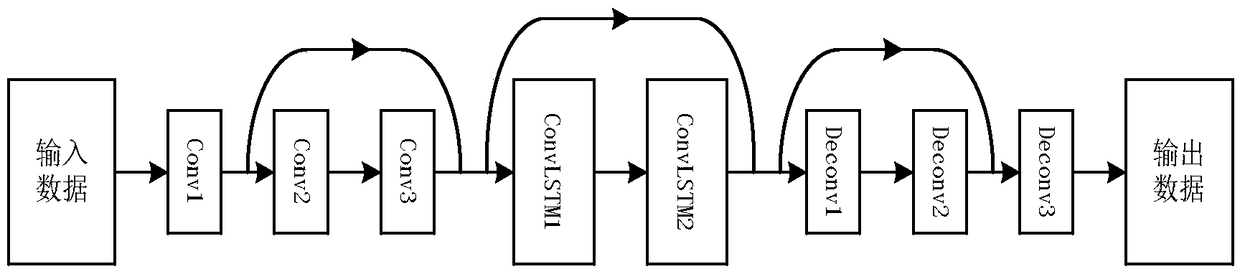
A video abnormal behavior detection method based on depth learning
The invention relates to a video abnormal behavior detection method based on depth learning. The method includes a training phase and a test phase. In the training phase, the training video sequence is converted into gray-scale image and optical flow image, which are respectively made into space-time blocks, and then input into residual self-coding model for training. Two models based on gray-scale image and optical flow image are established. The trained model contains the motion mode and appearance information of normal behavior, so it is more conducive to the reconstruction of normal behavior. In the test phase, the test data is made into space-time blocks of gray-scale map and optical flow map, At first, that space-time block of the grayscale image is input into the grayscale image model, The invention initially detects a normal area and a suspicious area, inputs the optical flow map space-time block of the suspicious area into the optical flow map model, detects the normal area and the abnormal area, and obtains the final abnormal judgment. The method of the invention can better identify the motion information and the appearance characteristic of the video data, thereby improving the detection rate of the abnormal behavior.
Owner:HANGZHOU DIANZI UNIV
Method, apparatus and system for detecting abnormal user behavior
InactiveCN108809745AQuick checkAccurate detectionComputer security arrangementsData switching networksNormal behaviourData mining
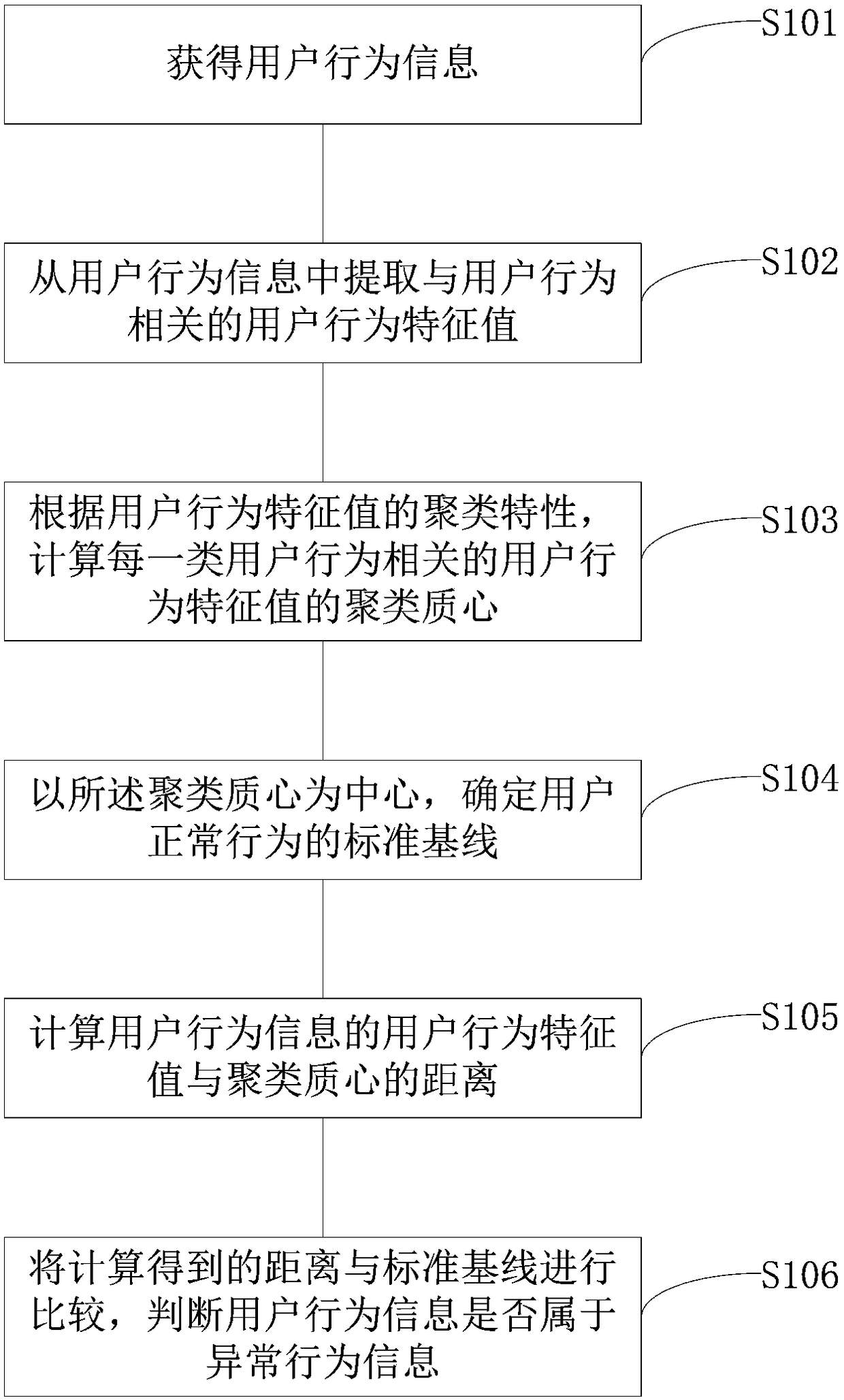
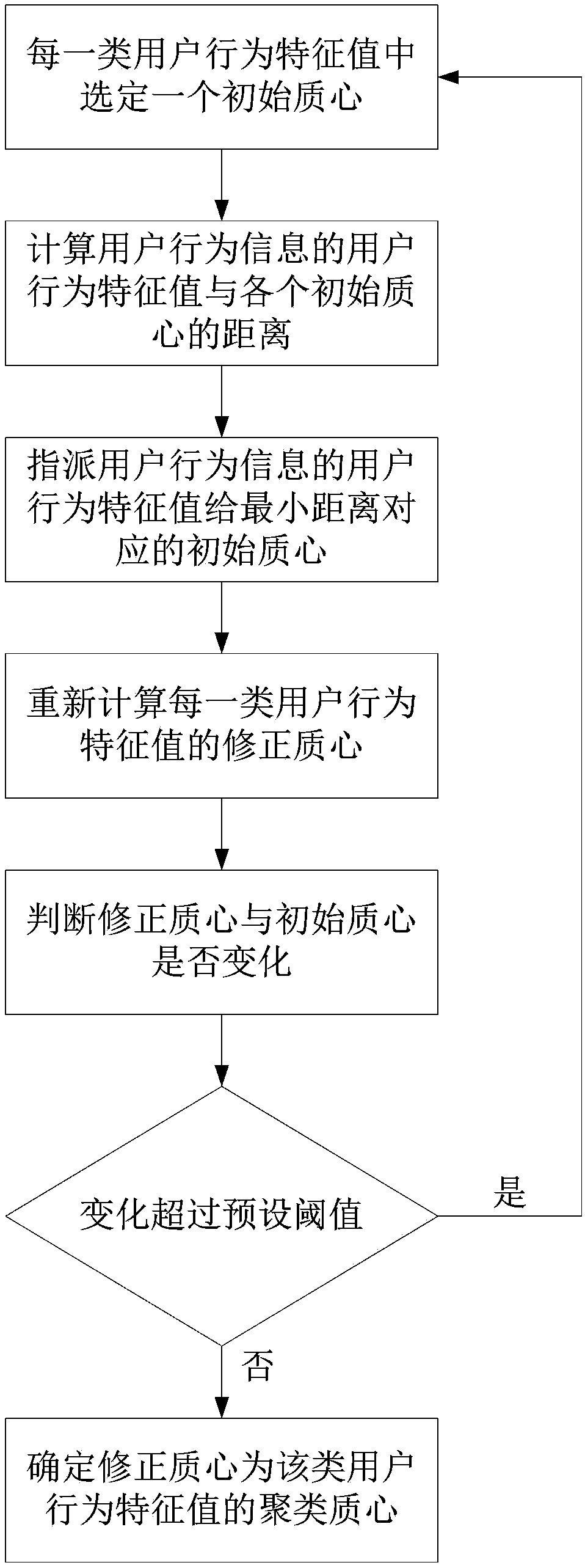
The invention provides a method, apparatus and system for detecting an abnormal user behavior. The method for detecting the abnormal user behavior comprises the following steps: obtaining user behavior information; extracting user behavior feature values related to user behaviors from the user behavior information; calculating a clustering centroid of the user behavior feature values related to each type of user behaviors according to the clustering characteristics of the user behavior feature values; determining a standard baseline of a normal user behavior by using the clustering centroid as the center; calculating the distance between the user behavior feature values of the user behavior information and the clustering centroid; and comparing the calculated distances with the standard baseline to judge whether the user behavior information belongs to abnormal behavior information. According to the method provided by the invention, by collecting the user behavior information, extracting the feature values from the user behavior information, and performing clustering analysis on the extracted feature values in combination with the normal behavior standard baseline to judge the abnormal situation of the user behaviors, thereby simplifying the judgment process of the abnormal user behavior and realizing fast and accurate detection of the abnormal user behavior.
Owner:中国移动通信集团重庆有限公司 +2
System and method for detecting potential threats by monitoring user and system behavior associated with computer and network activity
A system and method is provided to monitor user and system behavior associated with computer and network activity to determine deviations from normal behavior that represent a potential cyber threat or cyber malicious activity. The system and method uses a multi-factor behavioral and activity analysis approach to determine when a trusted insider might be exhibiting threatening behavior or when a user's computer or network credentials have been compromised and are in use by a third-party. As a result, changes in insider behavior that could be indicative of malicious intent can be detected, or an external entity masquerading as a legitimate user can be detected.
Owner:WINTERMUTE LLC
Fight behavior detection method based on spatio-temporal interest point
ActiveCN103279737AHigh fighting behavior recognition rateEffective fighting behavior detectionImage analysisCharacter and pattern recognitionPattern recognitionHuman body
The invention discloses a fight behavior detection method based on a spatio-temporal interest point. The fight behavior detection method based on the spatio-temporal interest point comprises the following steps: firstly, detecting the spatio-temporal interest point of the current frame; then, segmenting to extract an effective spatio-temporal interest point set; analyzing the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the effective spatio-temporal interest point set; according to the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the effective spatio-temporal interest point set, regulating the fight level of the current scene; and outputting the state information ''fight'' or ''normal''. According to the fight behavior detection method based on the spatio-temporal interest point, which is disclosed by the invention, the human body movement in a video is described by the spatio-temporal interest point, and the human body interaction acute degree is detected by analyzing the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the spatio-temporal interest point set so as to judge whether the fight behavior happens in the current monitoring scene. According to the fight behavior detection method based on the spatio-temporal interest point, the area with drastic movement in the current frame image can be accurately reflected, the fight behavior detection method is unlikely to be affected by the change of environment such as the change of illumination and has the advantages of high detection speed and better robustness, the fight behavior in the scene can be accurately and timely identified, normal behaviors of shaking hands and running and the like can be better distinguished, and the false alarm rate is effectively lowered.
Owner:SHANGHAI JIAO TONG UNIV
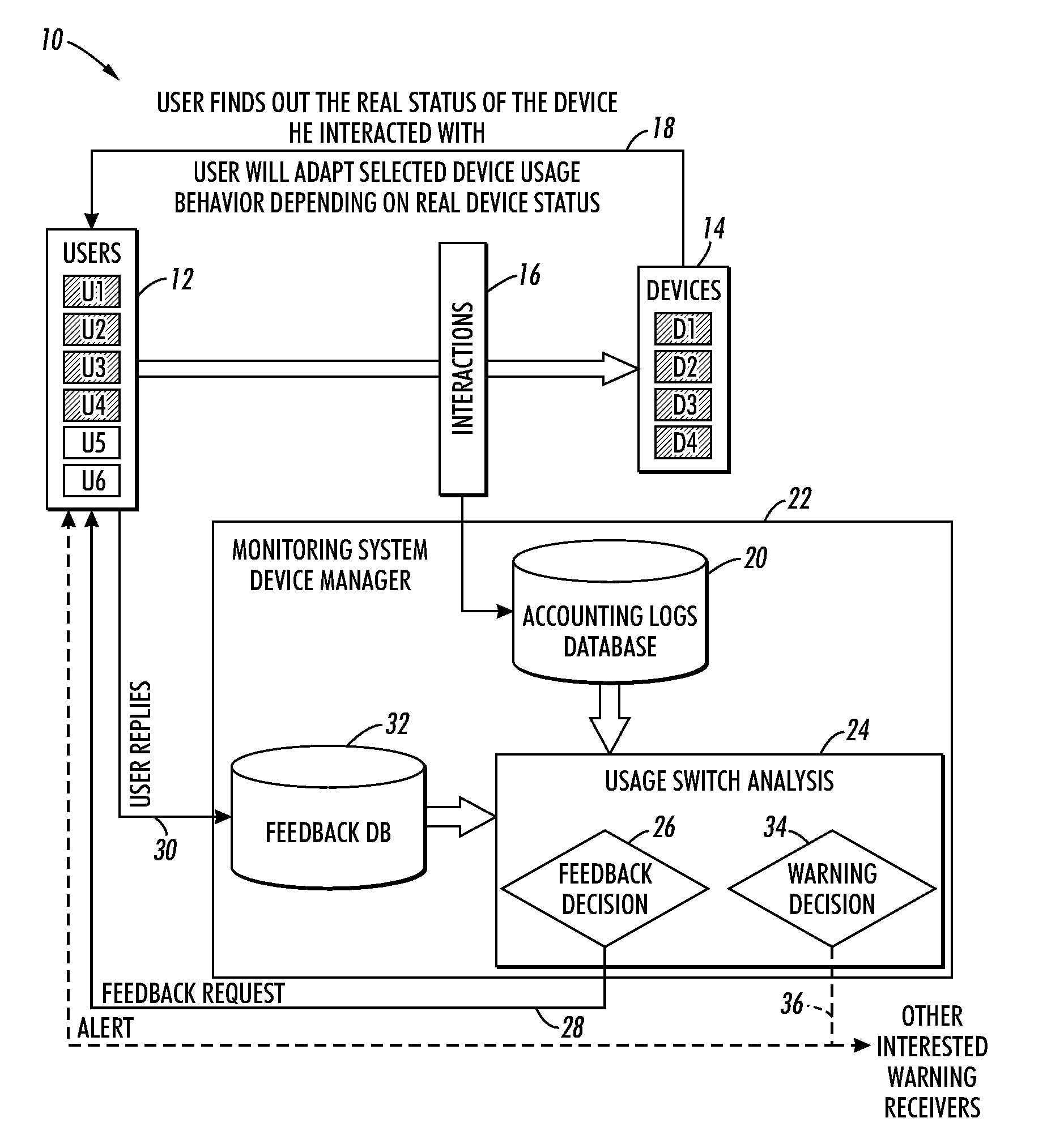
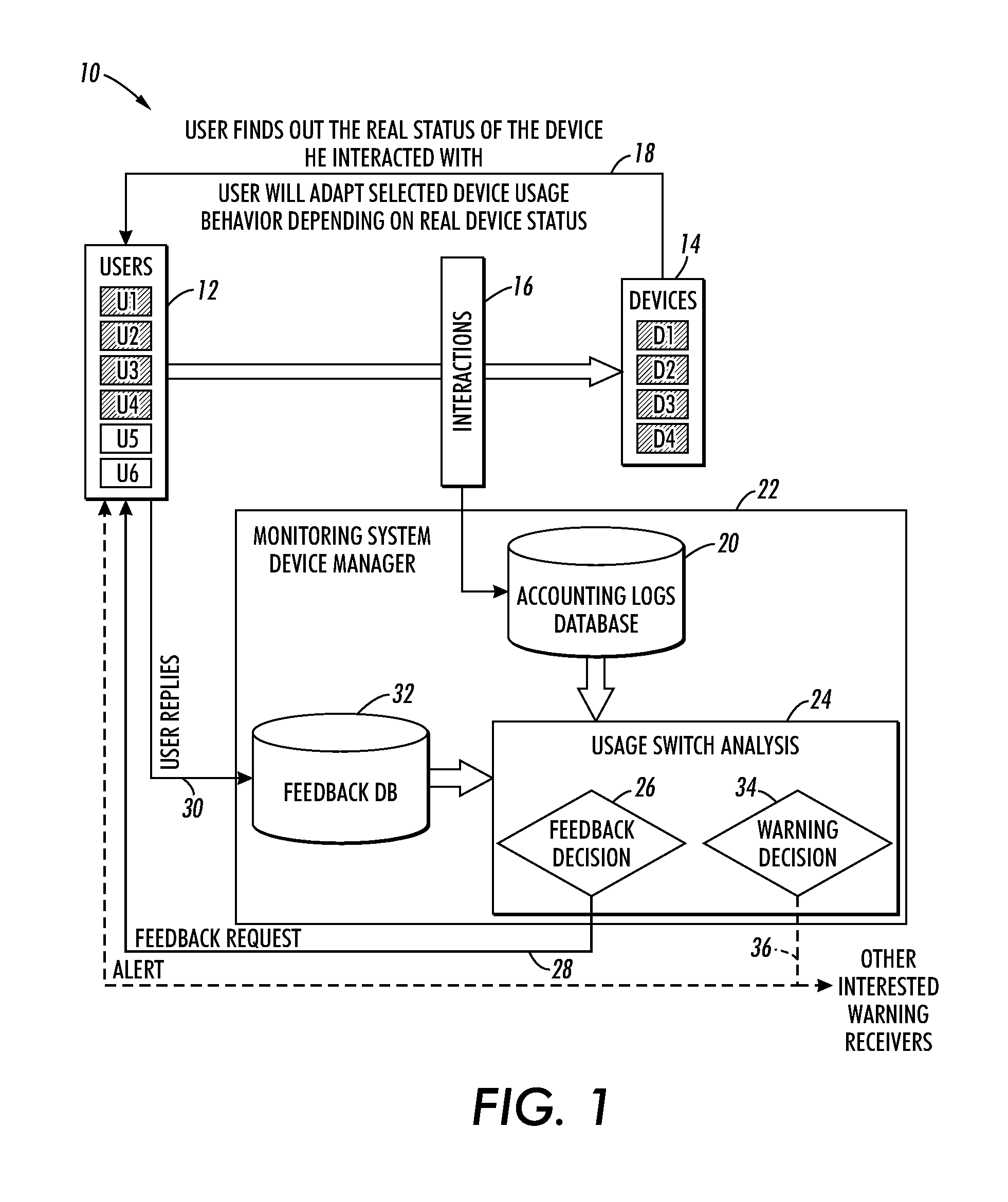
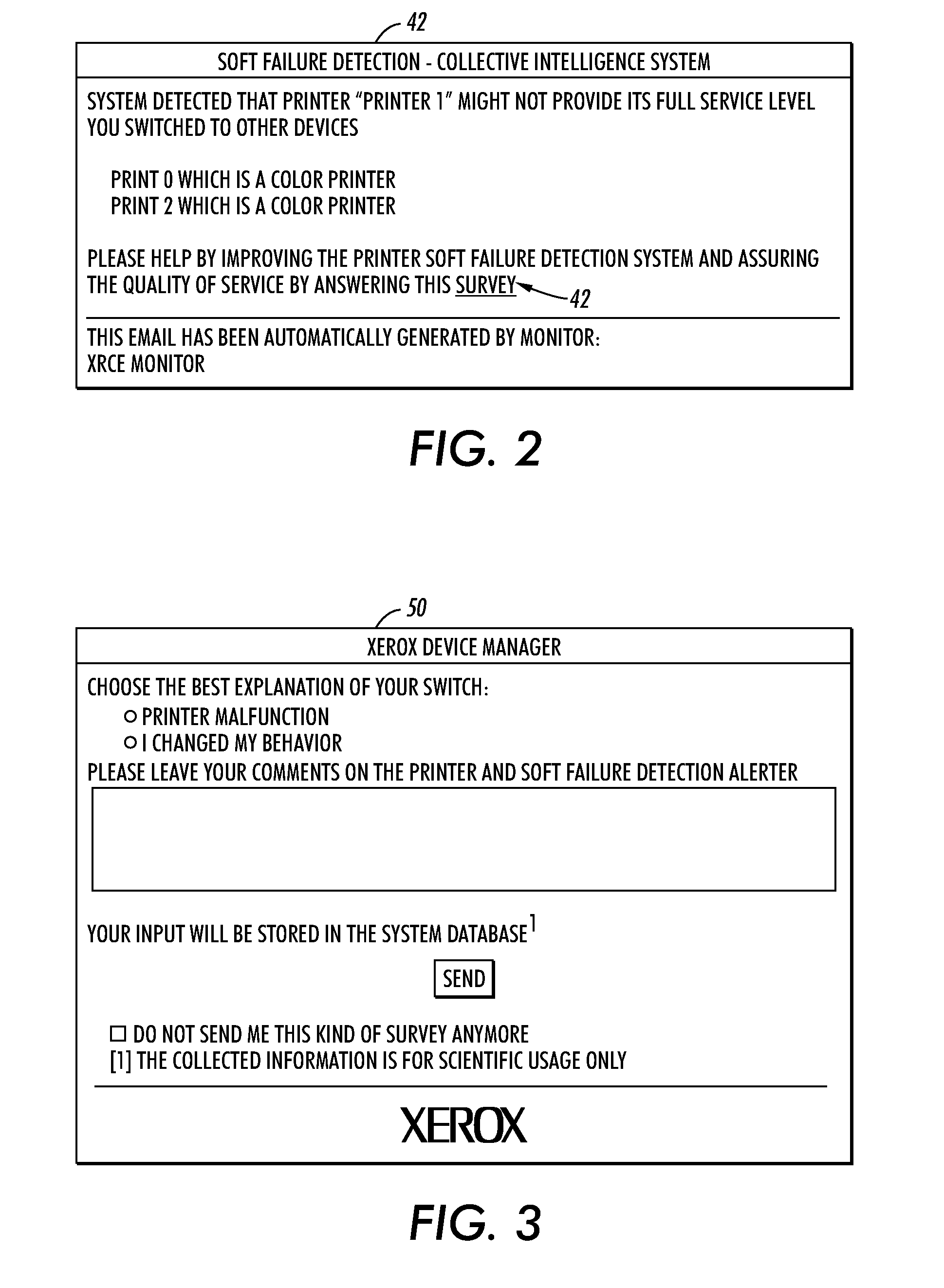
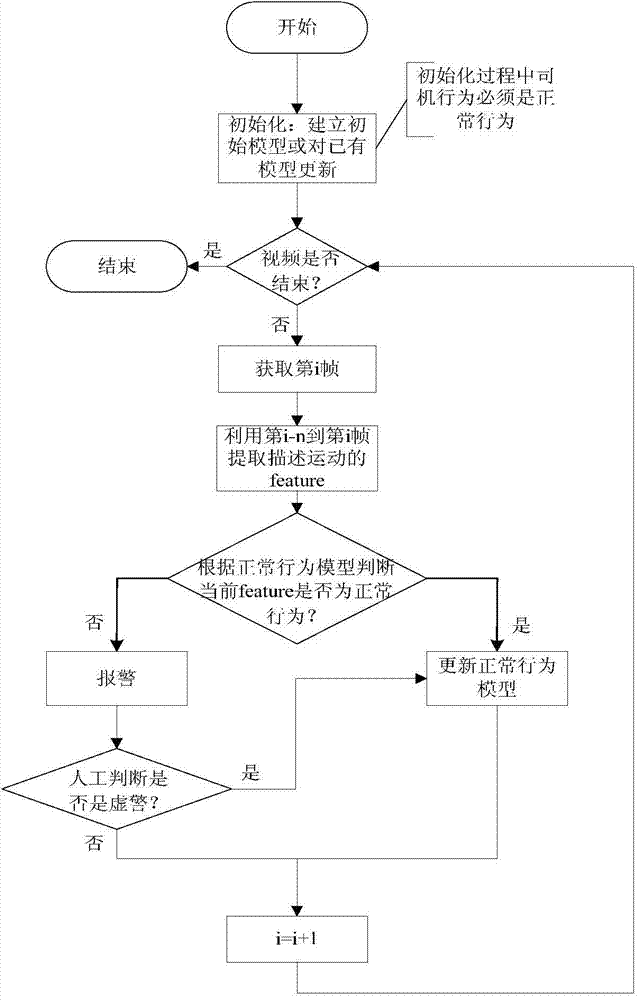
System and method for improving failure detection using collective intelligence with end-user feedback
InactiveUS20100145647A1Facilitate overcomingEasy to distinguishNuclear monitoringDigital computer detailsFault detection algorithmColor printing
Systems and methods are described that facilitate using end-user feedback to automatically distinguish between a normal behavior and a device failure which can be a hard failure (e.g., a device malfunction) or a soft failure. For instance, upon detection of a usage switch from a first device to a second device by a user, a survey message is sent to the user to solicit information regarding the reasons for the switch. If the switch was triggered by a device malfunction, the detected device failure is verified and an alert is sent to an administrator and / or potentially impacted users. If the switch was triggered by the user's need for functionality (e.g., color printing, collation, etc.) not provided by the first device, which is otherwise functioning properly, then the detected failure is determined to be a failure and the failure detection algorithm is updated accordingly.
Owner:XEROX CORP
Detection method of driver's abnormal behavior modeled based on online behavior
InactiveCN104504400ALess error rateImprove stabilityCharacter and pattern recognitionFeature extractionBehavioral modeling
The invention relates to a detection method of a driver's abnormal behavior modeled based on an online behavior and belongs to the technical field of image identification and monitoring. The method is based on a video analysis technology, the driver's abnormal behavior is detected by modeling the driver's normal behavior, and the method mainly comprises the following steps of: firstly, initializing and creating an initial model or updating the existing model; secondly, extracting driver's behavior characteristics in a driving process; thirdly, judging whether the driver's behavior is normal according to the initial model and the driver's behavior characteristics; fourthly, updating the model. The detection method is characterized in that the abnormal behavior is detected by a novelty detection way, multiple normal and abnormal behaviors can be treated by adopting a multi-mode modeling method, and false alarms are eliminated by a manual labeling method, thus the steadiness of the solution is increased and the error rate of the solution is reduced.
Owner:CHONGQING INST OF GREEN & INTELLIGENT TECH CHINESE ACADEMY OF SCI
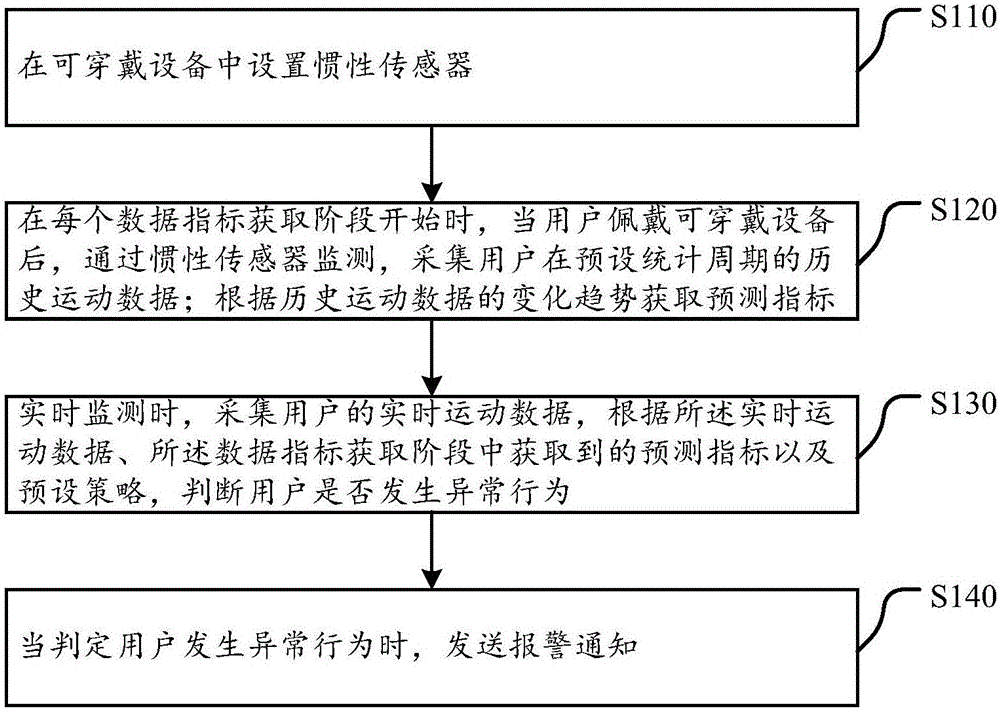
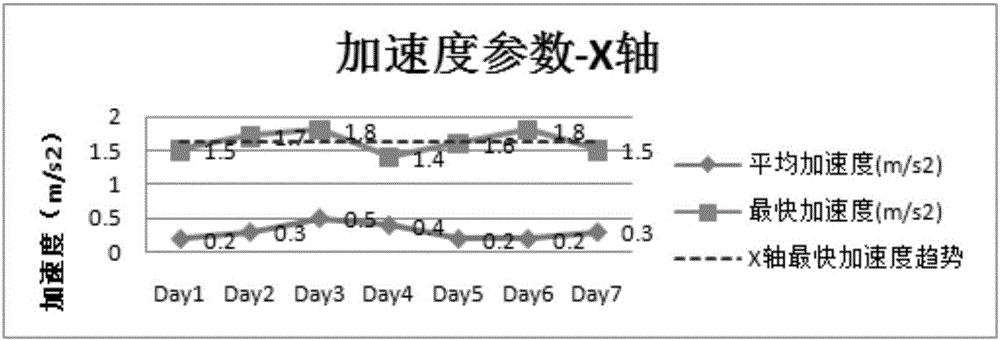
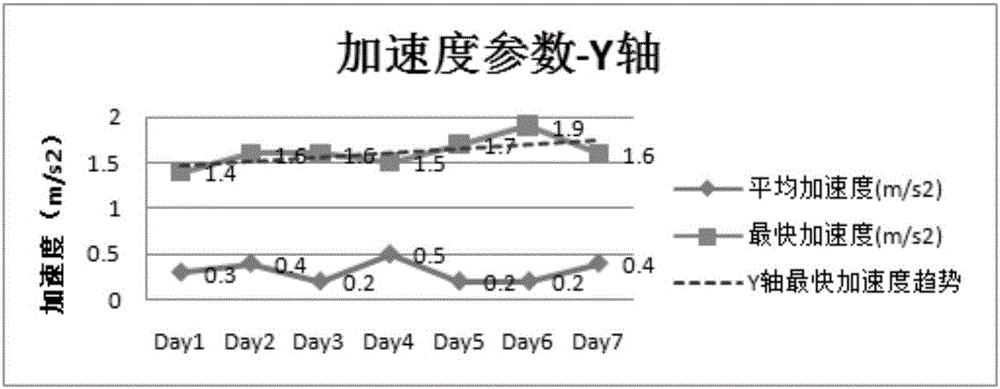
User behavior monitoring method and wearable equipment
The invention discloses a user behavior monitoring method and wearable equipment. The method comprises that the wearable equipment is internally provided with an inertia sensor; in the beginning of each data index obtaining stage, the inertia sensor is used for monitoring, and historical motion data of the user in a preset statistical period is collected; a prediction index is obtained according to the change trend of the historical motion data; during real-time monitoring, real-time motion data of the user is collected, and whether the user has an abnormal behavior is determined according to the real-time motion data, the obtained prediction index and a preset strategy; and an alarming notification is sent when it is determined that the user has the abnormal behavior. Aimed at different users, the personal historical motion data of each user serves as self-learning template data, the prediction index for motion of the user later is obtained by learning the template data continuously, the theoretical prediction index is combined with the real-time motion data collection practically at present to analyze and discover the abnormal behavior of the user, and customized high-precision behavior monitoring is realized.
Owner:GOERTEK INC
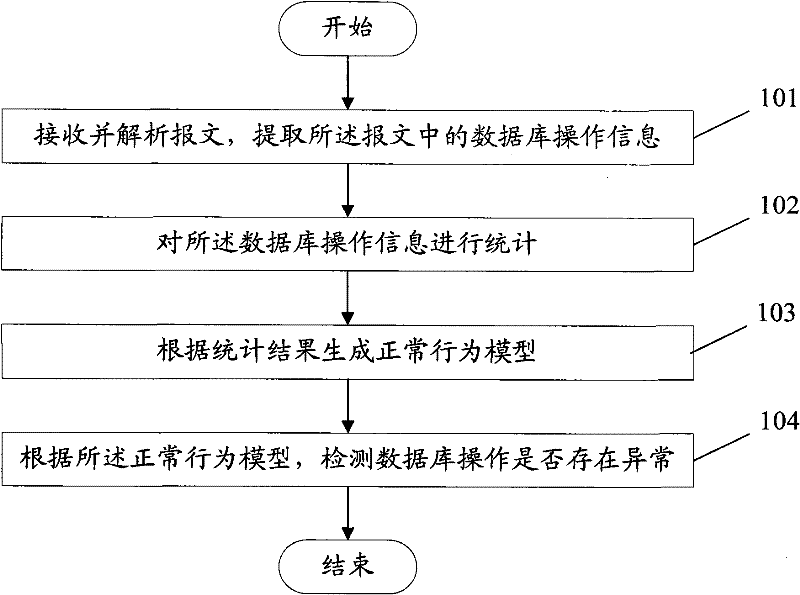
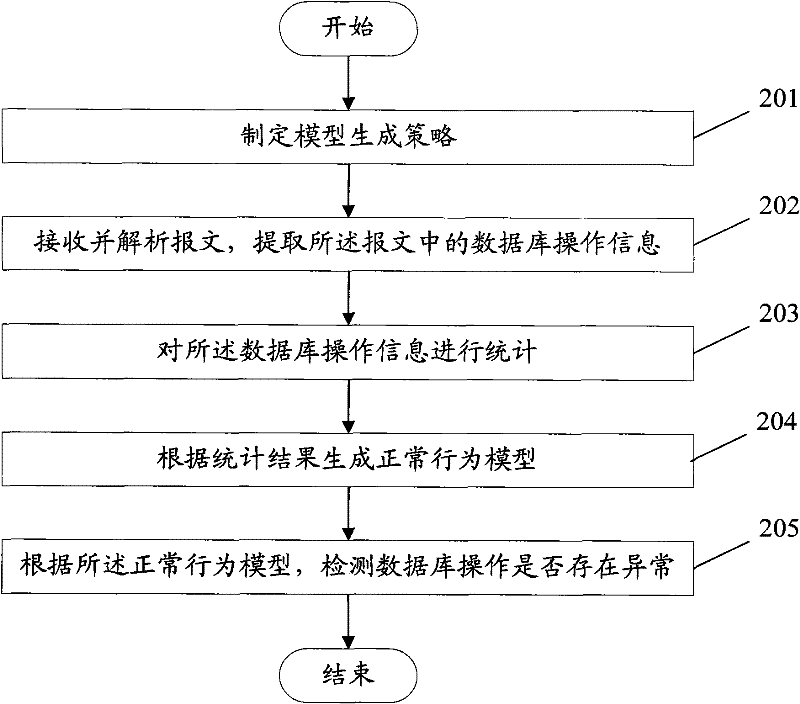
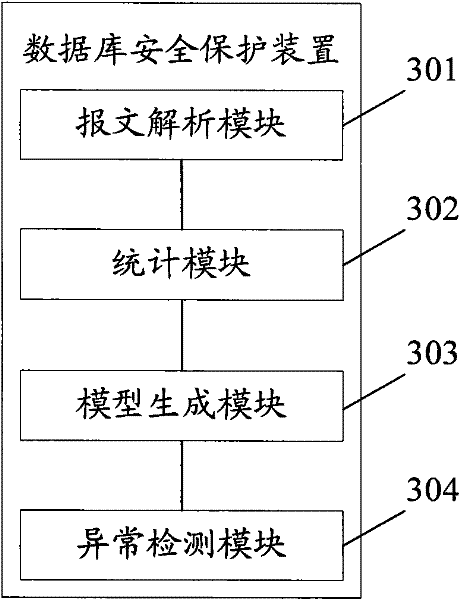
Database security protection method and device
InactiveCN102480385AImprove securityData switching networksSpecial data processing applicationsNormal behaviourDatabase security
The invention provides a database security protection method and device, relates to the technical field of networks, and solves the problem of low security of a database. The method comprises the following steps of: receiving and resolving a message, and extracting database operation information in the message; carrying out statistics on the database operation information; and generating a normal behavioral model according to a statistical result, and detecting whether the database operation is abnormal or not according to the normal behavioral model. The technical scheme provided by the invention is suitable for database security protection.
Owner:BEIJING VENUS INFORMATION TECH +1
Abnormal behavior detection system and method by utilizing automatic multi-feature clustering method
ActiveCN102385705ASave construction costSave maintenance costCharacter and pattern recognitionClosed circuit television systemsTraffic violationNormal behaviour
The invention provides an abnormal behavior detection system and a method by utilizing an automatic multi-feature clustering method; combine a feature group according to the obtained features of all monitoring data, for instance, multiple features are captured from a monitoring video; then build a normal behavior model and an abnormal behavior model after processing and analysis by a machine learning algorithm, and in one embodiment, the behaviors with low occurrence frequency are considered as the abnormal behavior. In the invention, supervised learning can also be adopted, the abnormal behavior model in the behavior models generated by automatic classification is defined artificially, so as to causing the abnormal behavior detection to be in accordance with the requirements of a user; and automatically classify into normal behaviors and abnormal behaviors according to the various captured features after the behavior model is built. In the invention, the system and the method are suitable for detecting various traffic abnormal behaviors such as traffic violation behaviors, for instance, running the red light, violation of right-lane driving and violation of right direction driving.
Owner:GORILLA TECH
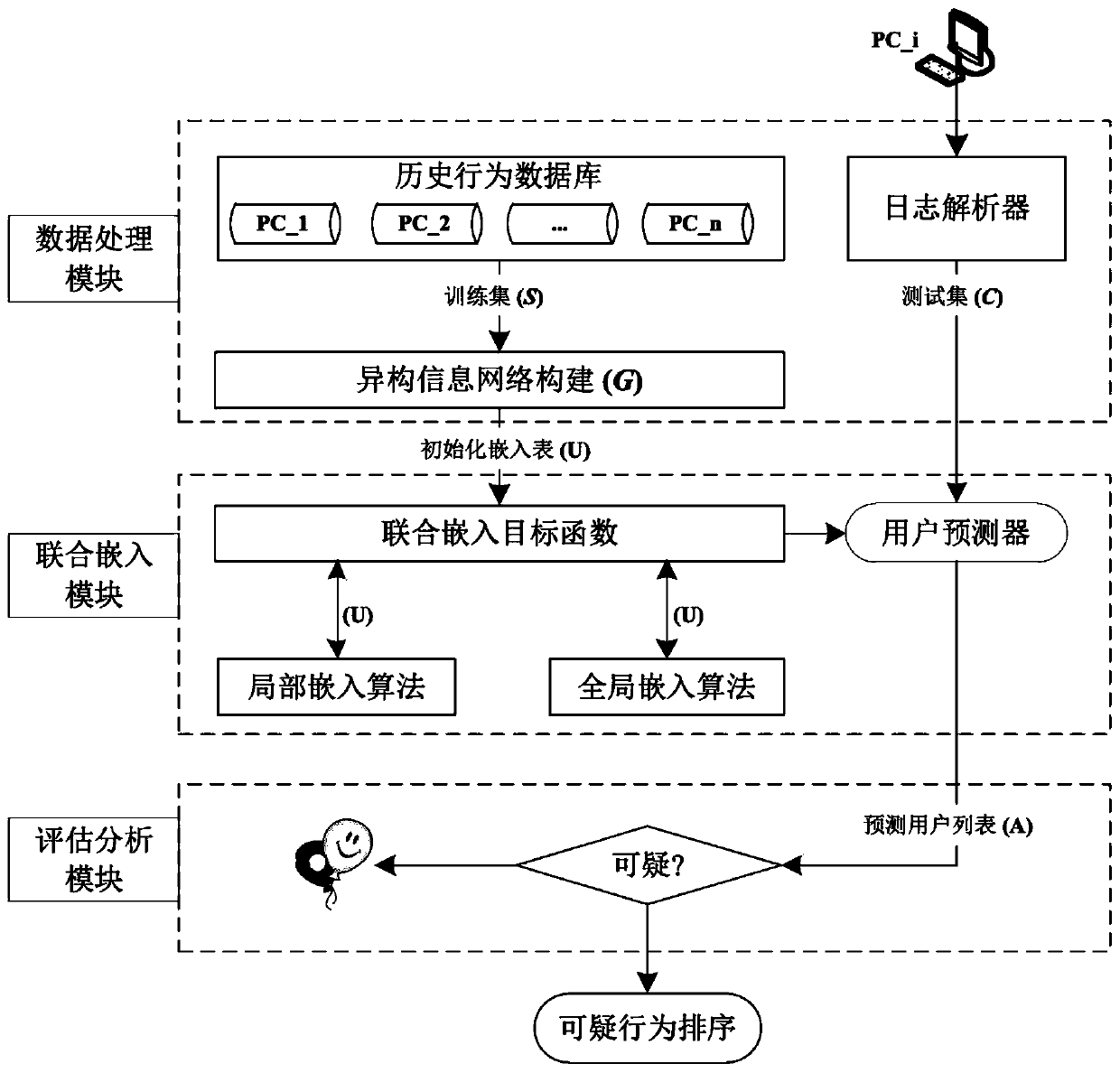
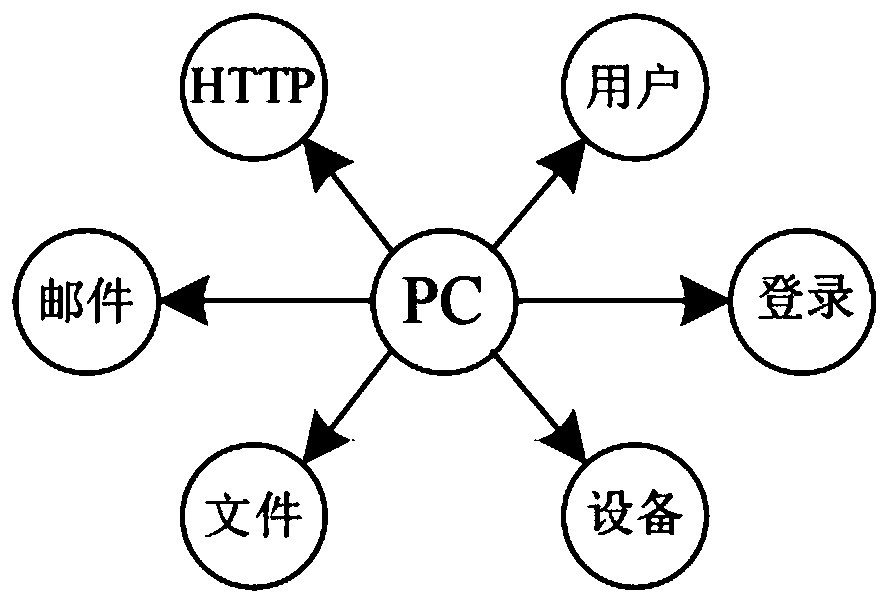
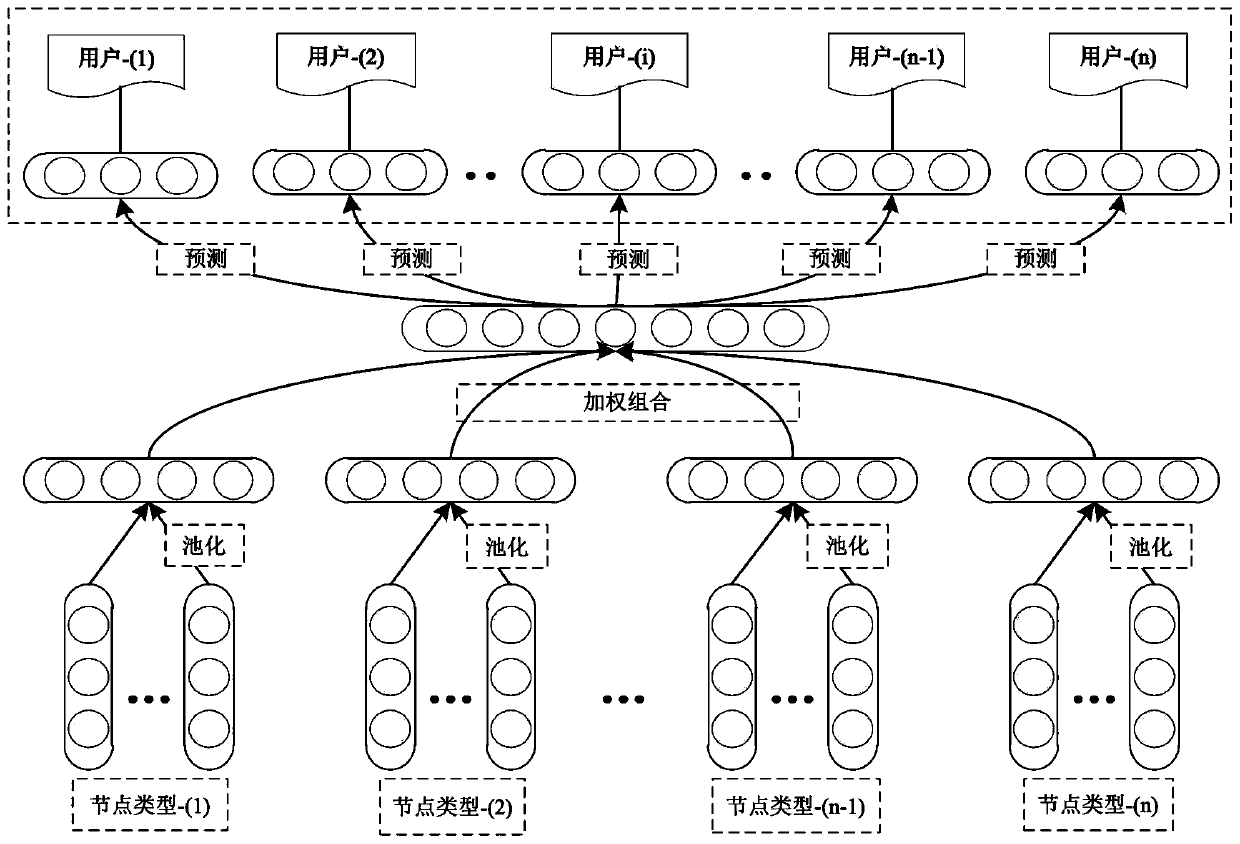
User identification system and method based on heterogeneous information network embedding algorithms
ActiveCN111163057AComprehensive Behavioral ModelingImprove recognition accuracyData switching networksNeural learning methodsAlgorithmInformation networks
The invention relates to a user identification system and method based on heterogeneous information network embedding algorithms. The user identification system comprises a data processing module, a joint embedding module and an evaluation analysis module. According to the invention, multi-source heterogeneous user behavior data is utilized for constructing a normal behavior model based on the thought of behavior analysis, and user identification is executed by comparing the similarity between a current behavior and the normal behavior model when behavior data of a new time period arrives. Forthe condition of identification errors, suspicious behavior sorting is given based on dot product similarity operation. The system and method can be applied to an enterprise intranet to detect potential internal threats, a more comprehensive and accurate behavior model can be obtained by combining two heterogeneous information network embedding algorithms, and the user identification accuracy isimproved by about 10%. In addition, event-level traceability clues can be provided for further analysis of the safety monitoring personnel.
Owner:INST OF INFORMATION ENG CAS
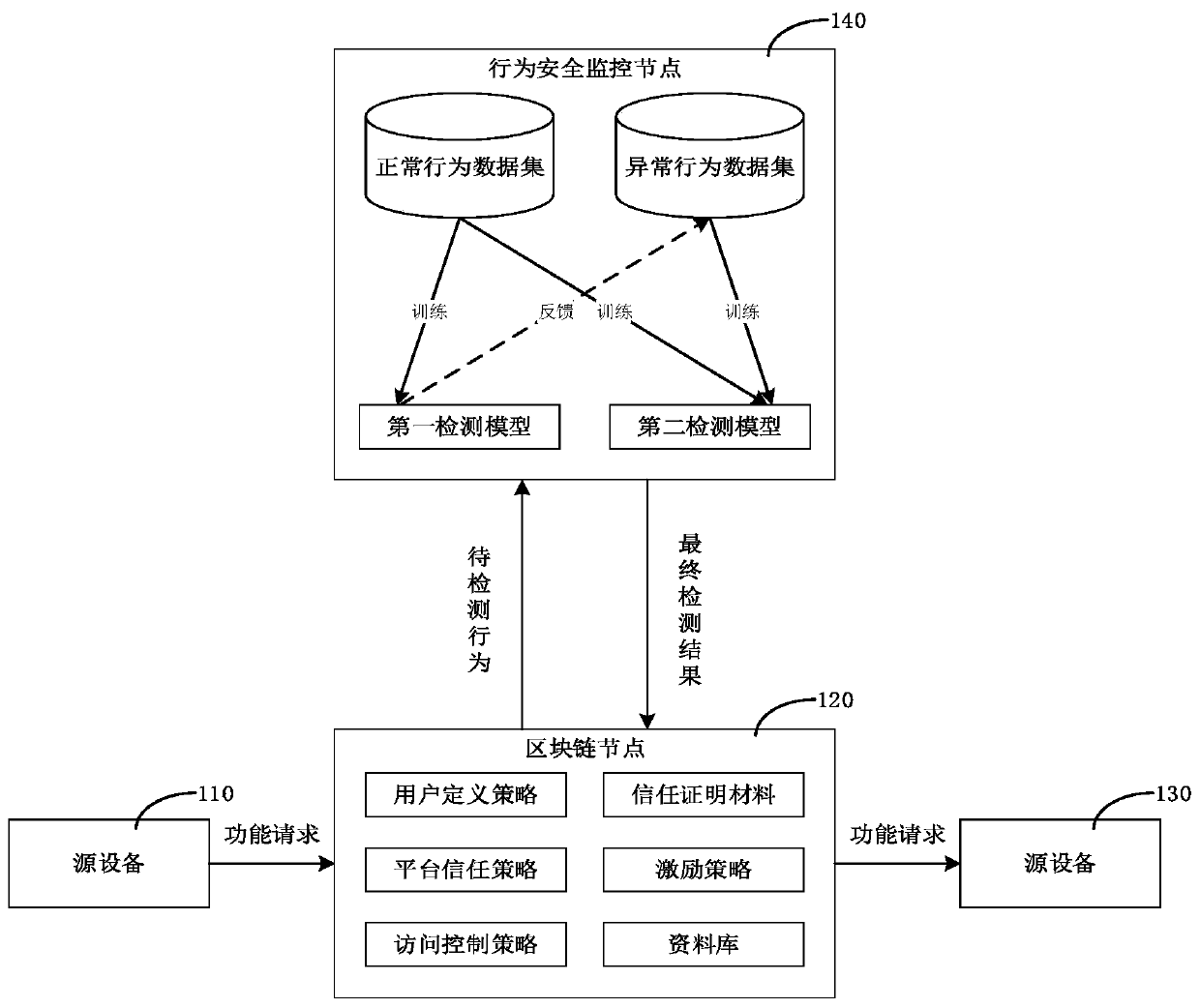
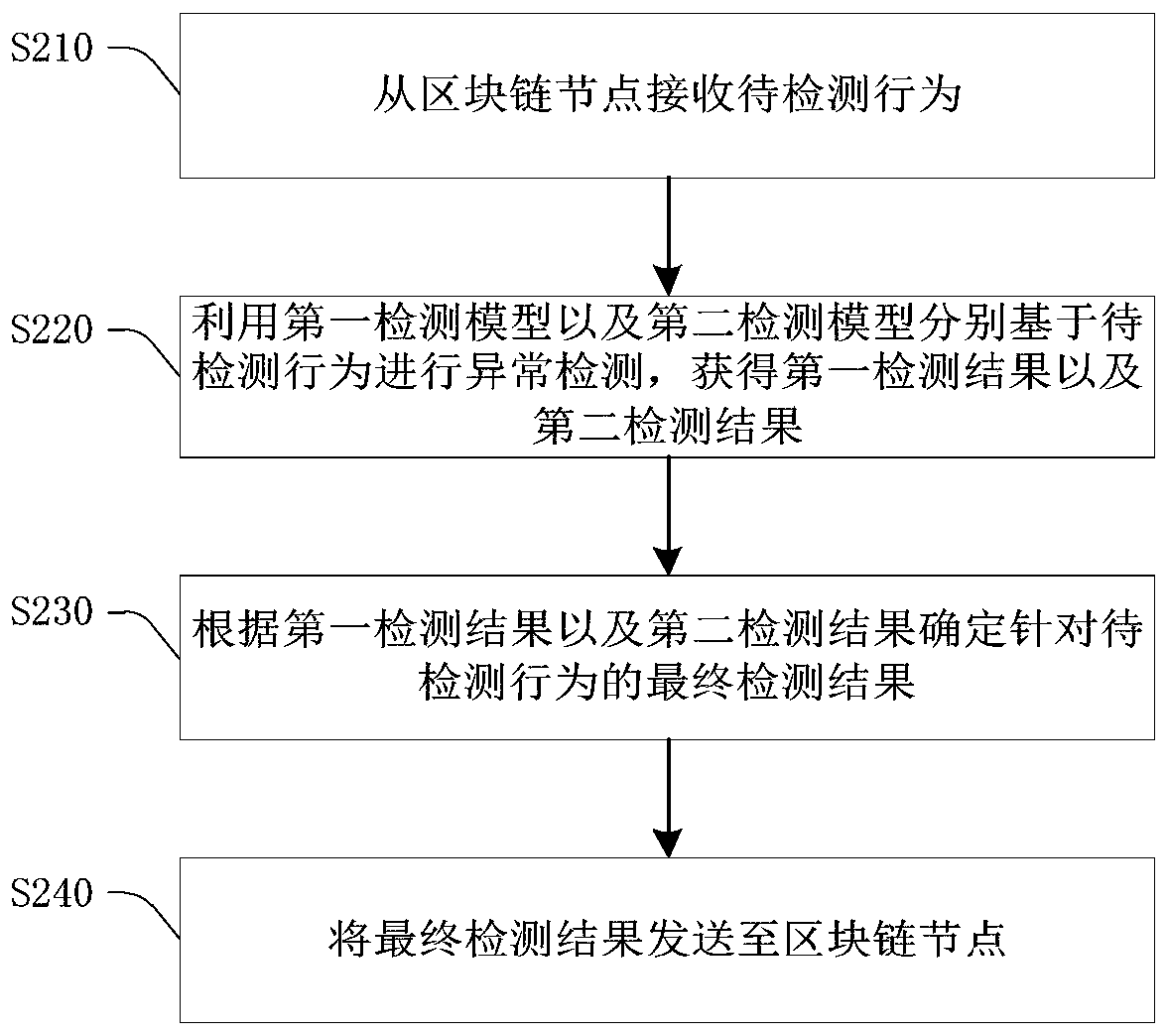
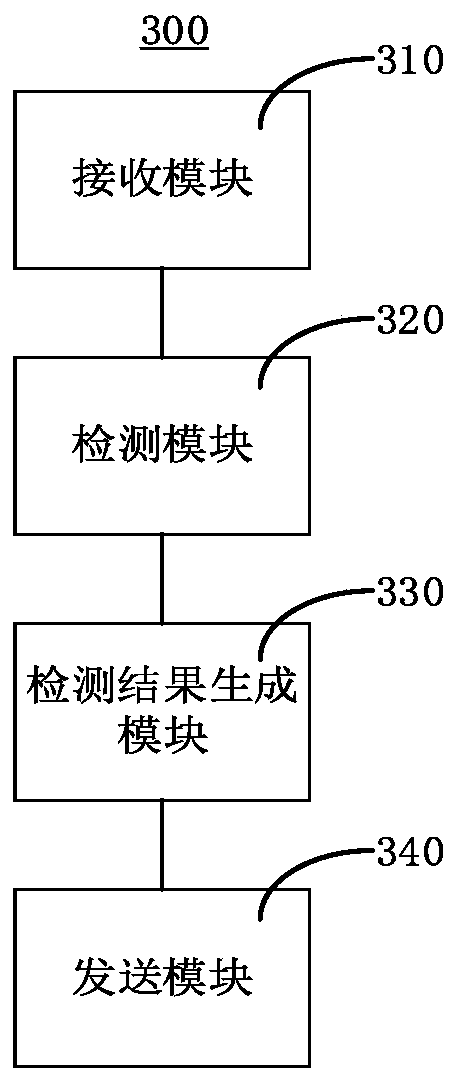
Abnormal behavior detection method and device and verification system
The invention relates to the technical field of behavior detection, and provides an abnormal behavior detection method and device and a verification system. The abnormal behavior detection method comprises the following steps: receiving a to-be-detected behavior from a block chain node; using a first detection model and a second detection model to perform detection based on to-be-detected behaviors to obtain a first detection result and a second detection result respectively, wherein the first detection model is obtained after unsupervised learning based on the normal behavior sample set, andthe second detection model is obtained after supervised learning based on the normal behavior sample set and the abnormal behavior sample set; determining a final detection result according to the twodetection results; and sending the final detection result to the block chain node, so that the block chain node forwards the function request sent by the source equipment to the target equipment whenthe final detection result is normal, otherwise, refusing to forward the function request to the target equipment. According to the method, the abnormal linkage behavior of the equipment can be effectively detected, and the safety of the equipment is improved.
Owner:SICHUAN PANOVASIC TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com