Abnormal detection method for user access activity in attached net storage device
A network-attached storage and user technology, applied in the field of abnormal identification, can solve the problems of deployment without security weaknesses, unable to prevent system abnormal events, and limit the widespread promotion and application of NAS technology, so as to reduce query matching time, simple implementation, and The effect of small storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described below in conjunction with the accompanying drawings.
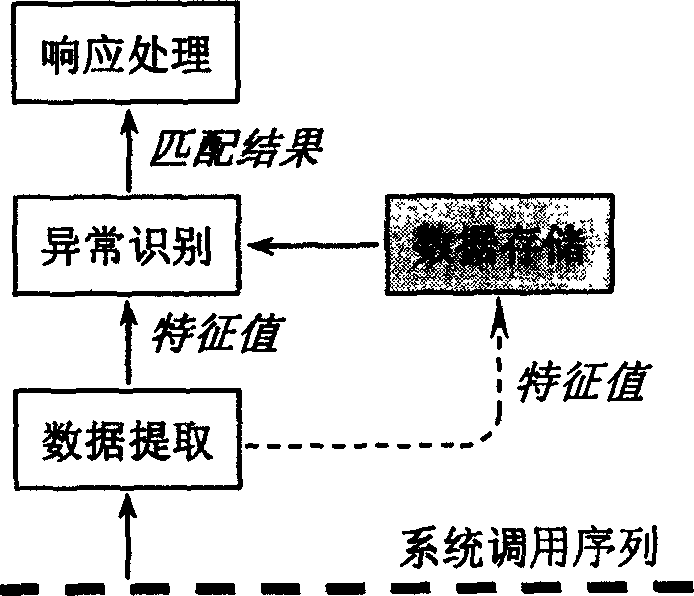
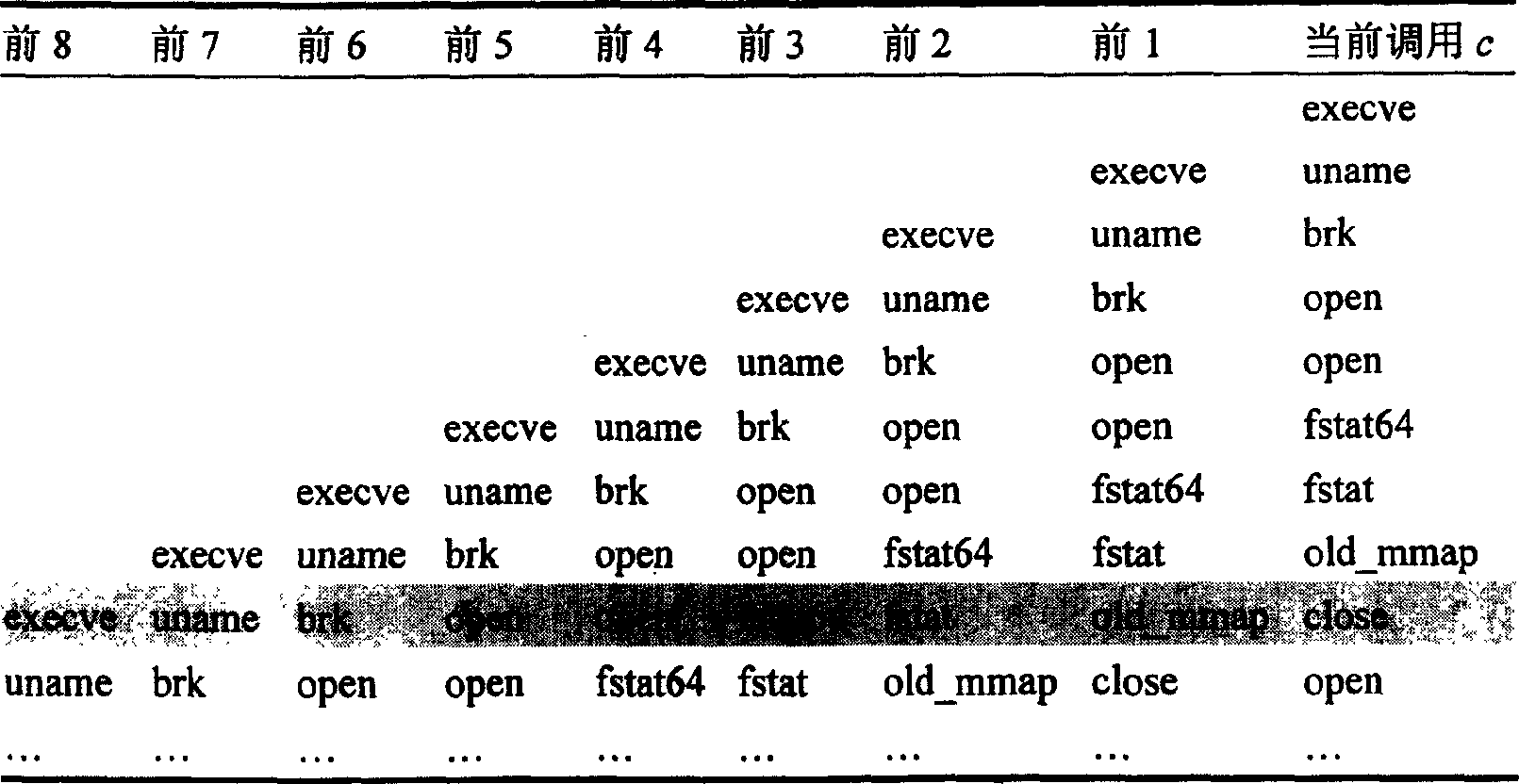
[0014] The purpose of the user's access to the NAS is to obtain files or manage the device. When legitimate users perform authorized operations, the process will generate corresponding system call sequences; similarly, when illegal users maliciously invade the system, and legitimate users perform unauthorized operations, the process of these abnormal behaviors will also generate corresponding System call sequence. The system call sequence generated by abnormal behavior and normal behavior is always different in the function name of the system call, the calling sequence, and the number of requests.
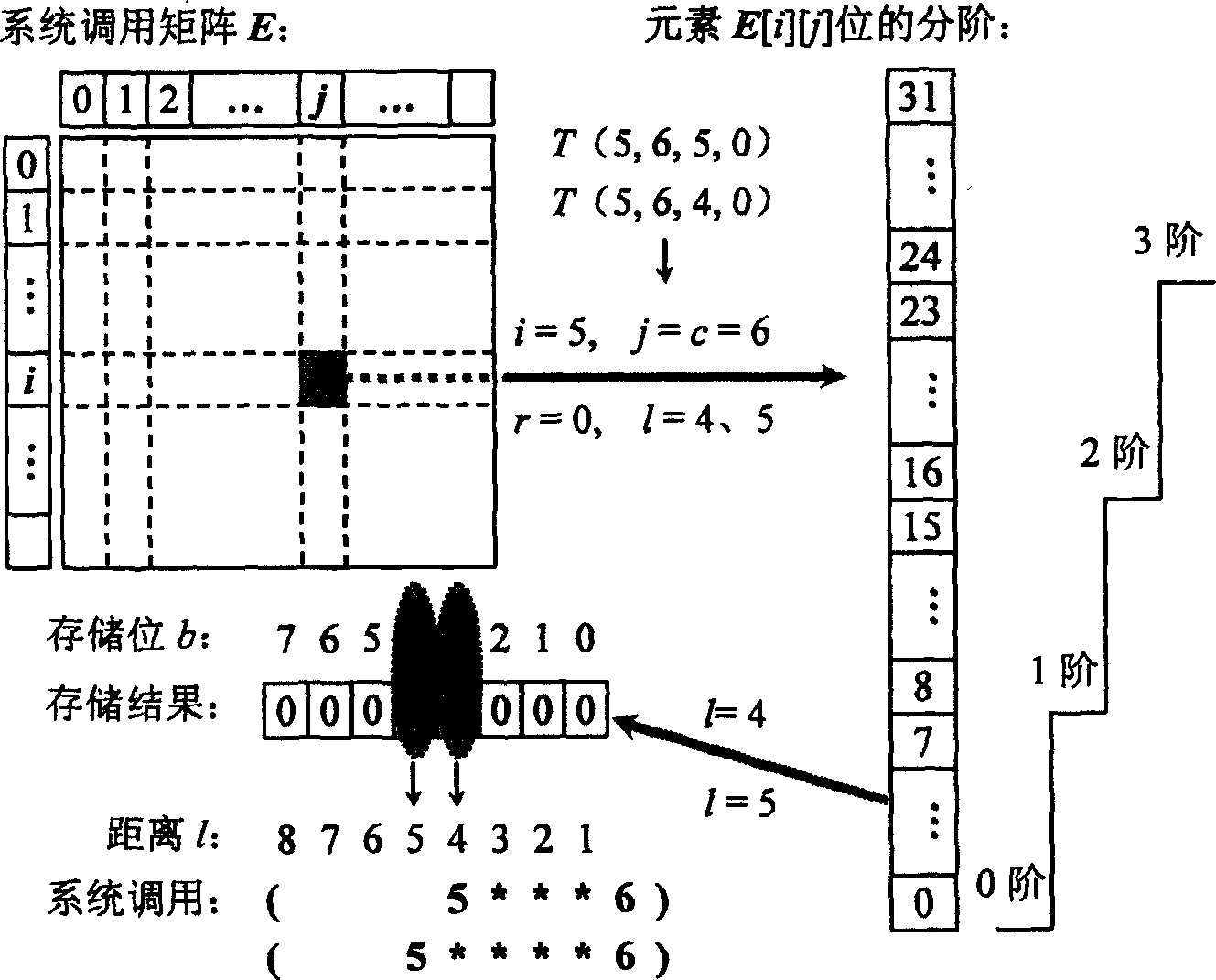
[0015] The abnormal detection method of user access behavior in network-attached storage devices provided by the present invention extracts and matches the characteristic values of the system call sequence generated by user access behaviors in network-attached storage de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com