BBS user abnormal behavior auditing method based on Hidden Markov theory
A hidden Markov and behavior technology, applied in the field of BBS user abnormal behavior audit based on hidden Markov theory, can solve problems such as the reason why administrators cannot perform, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
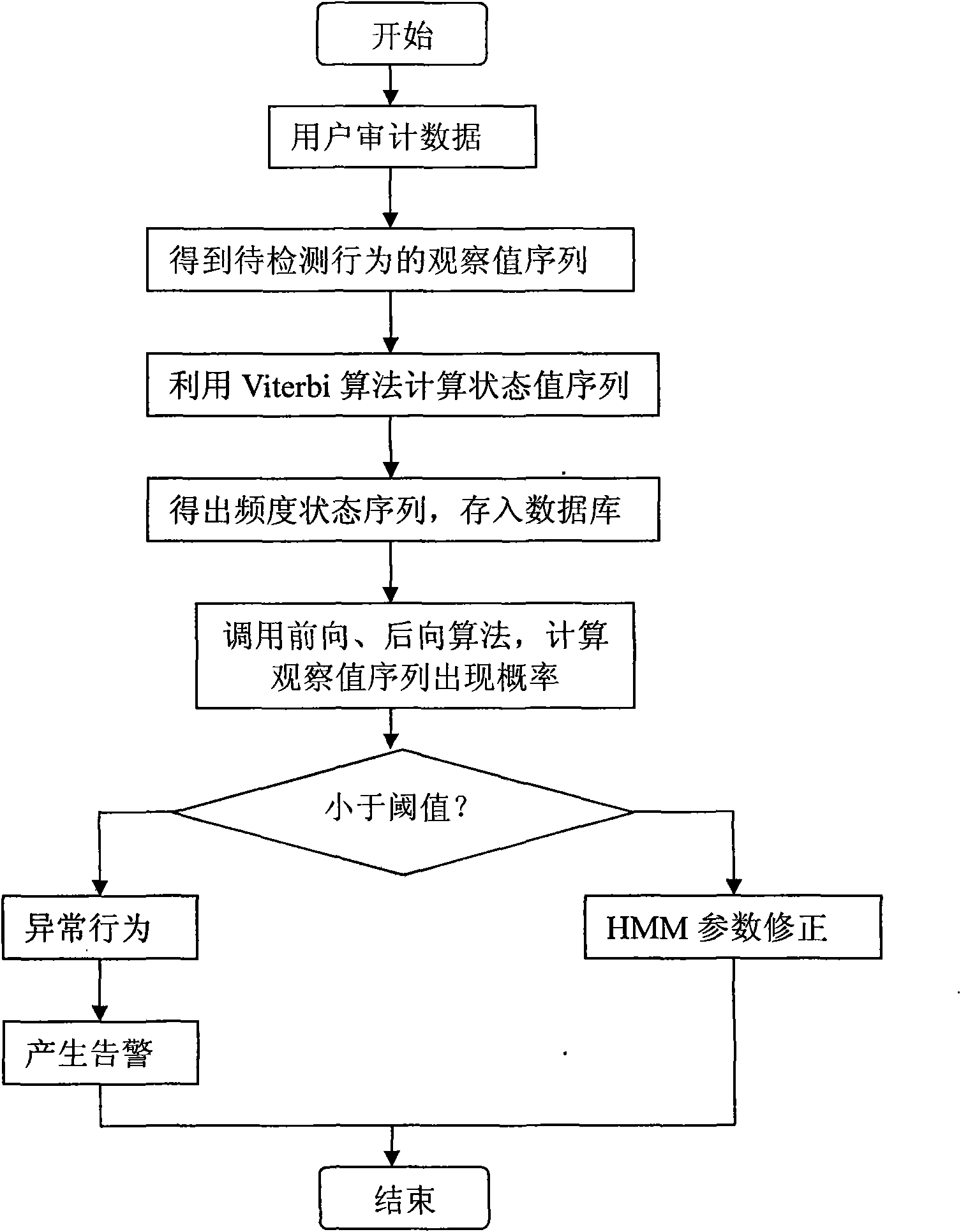
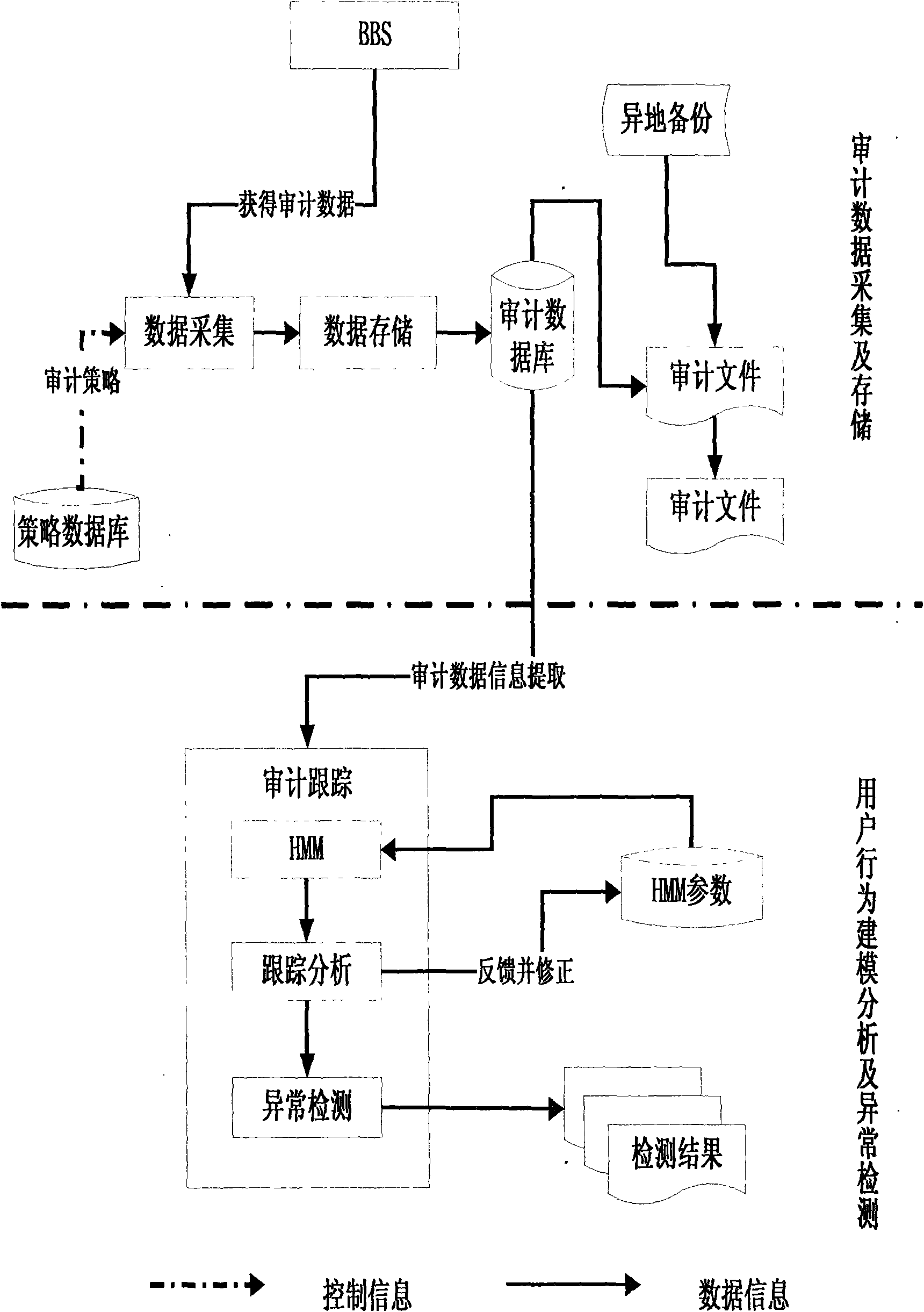
[0047] The overall block diagram of the BBS audit module is as follows: figure 2 shown.
[0048] The collected audit data includes published article audit data, modified article audit data, deleted article audit data, user information audit data, layout information audit data and the audit module's own audit data. The audit module's own data is composed of auditor login information audit data and auditor operation information audit data.
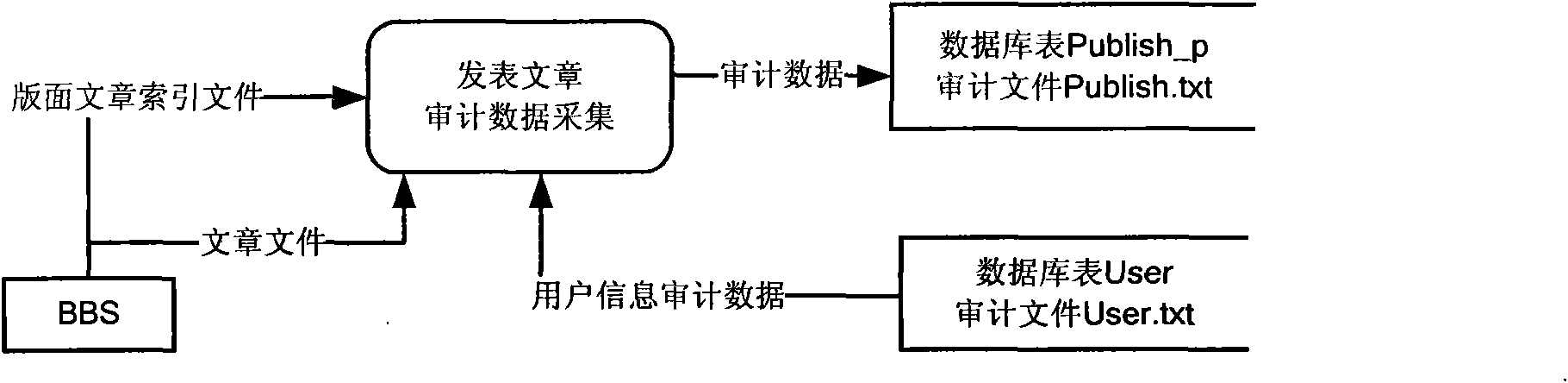
[0049] The collection process of published article audit data is as follows: image 3 shown. The audit data comes from the page index file and article file under the BBS. The page index file contains multiple fileheader structures, and each structure corresponds to an article. The corresponding data can be extracted from the index file, and the text of the article can be extracted from the text file. , all the data are processed and stored in the Publish_p table of the database and the audit file Publish.txt.
[0050] Modify the collect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com