Method and device for conducting security identification on information system
An information system and security technology, applied in the field of security identification of information systems, can solve the problem that threat identification is difficult to meet the security identification requirements of information systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
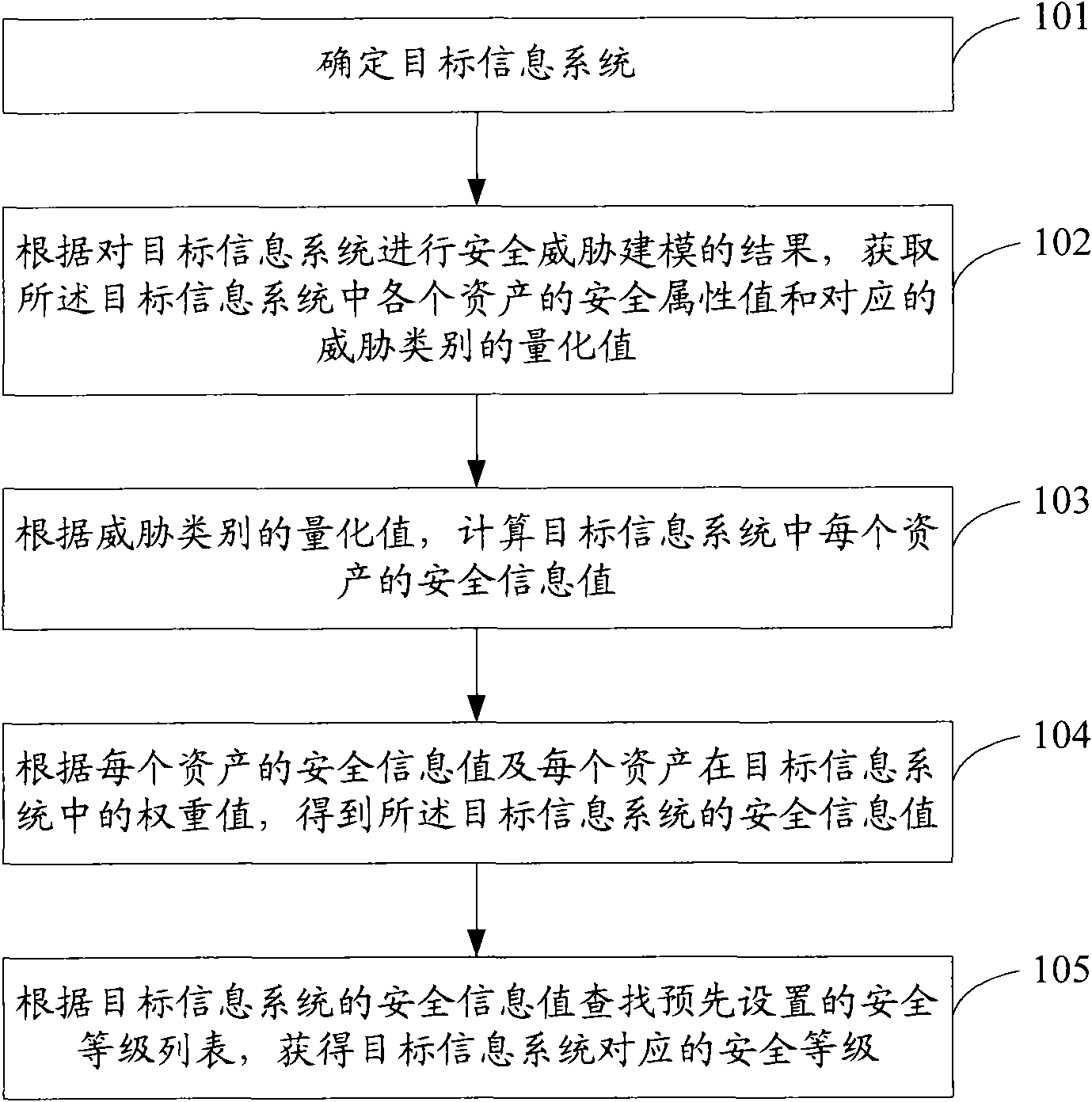
[0063] see figure 1 , which is a flow chart of the first embodiment of the method for security identification of an information system in the present invention:
[0064] Step 101: Determine the target information system.
[0065] Step 102: Obtain the security attribute values of each asset in the target information system and the quantified value of the corresponding threat category according to the result of security threat modeling of the target information system.
[0066] Step 103: Calculate the security information value of each asset in the target information system according to the quantified value of the threat category.
[0067] Step 104: Obtain the security information value of the target information system according to the security information value of each asset and the weight value of each asset in the target information system.
[0068] Step 105: Search the preset security level list according to the security information value of the target information system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com