Lattice-based multi-identity fully homomorphic encryption method
A technology of fully homomorphic encryption and encryption algorithm, applied in the direction of homomorphic encrypted communication, public key of secure communication, secure communication device, etc., can solve the problem that identity calculation cannot meet the needs of big data and cloud computing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
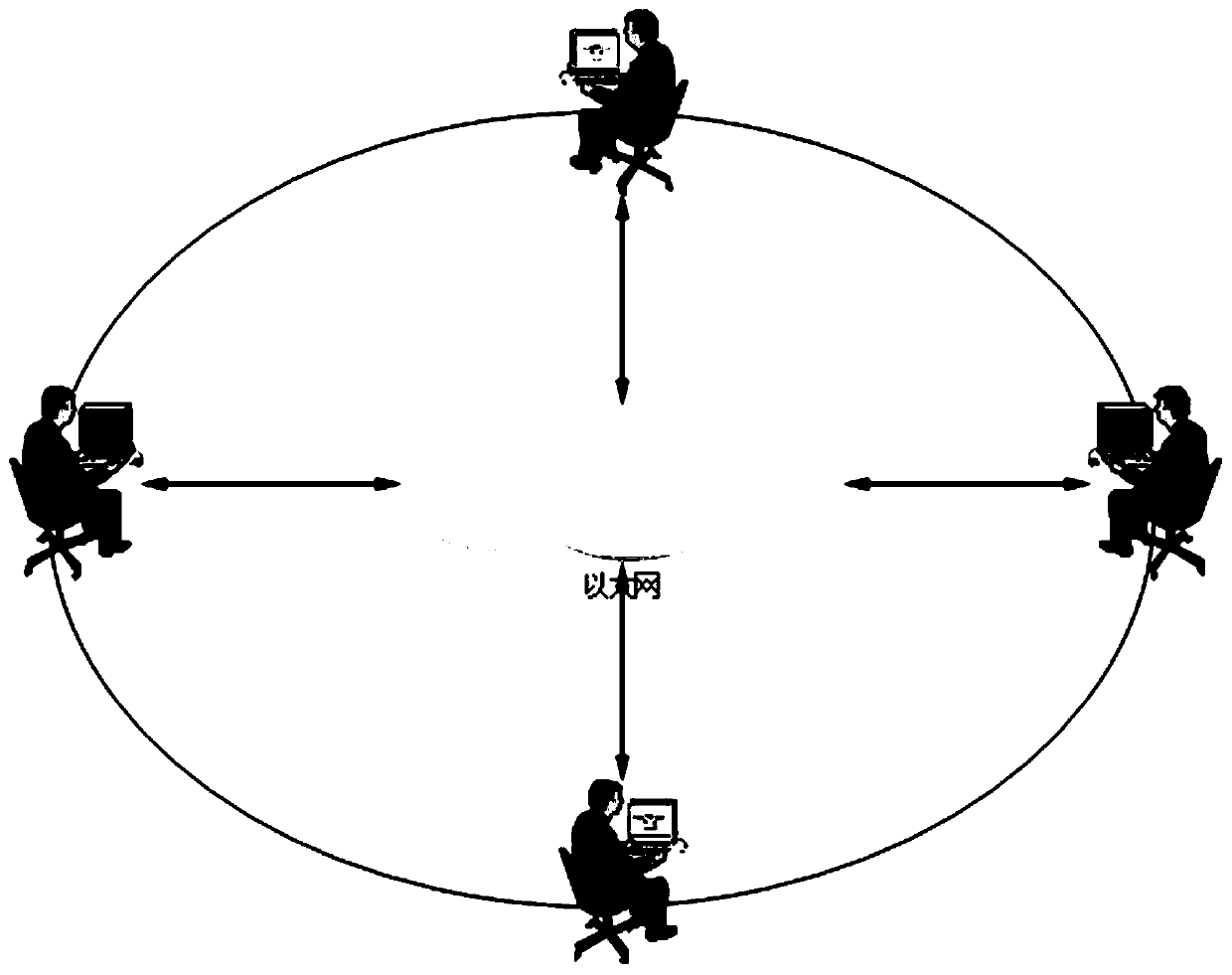
[0066] Attached below figure 1 The technical solution described in the present invention is described in detail.
[0067] The technical solution described in the invention is applied to the server-client communication system, the client encrypts its plaintext information and uploads it to the server, and the server performs statistical calculations on the ciphertext data. The communication between them can adopt wireless communication or wired communication.
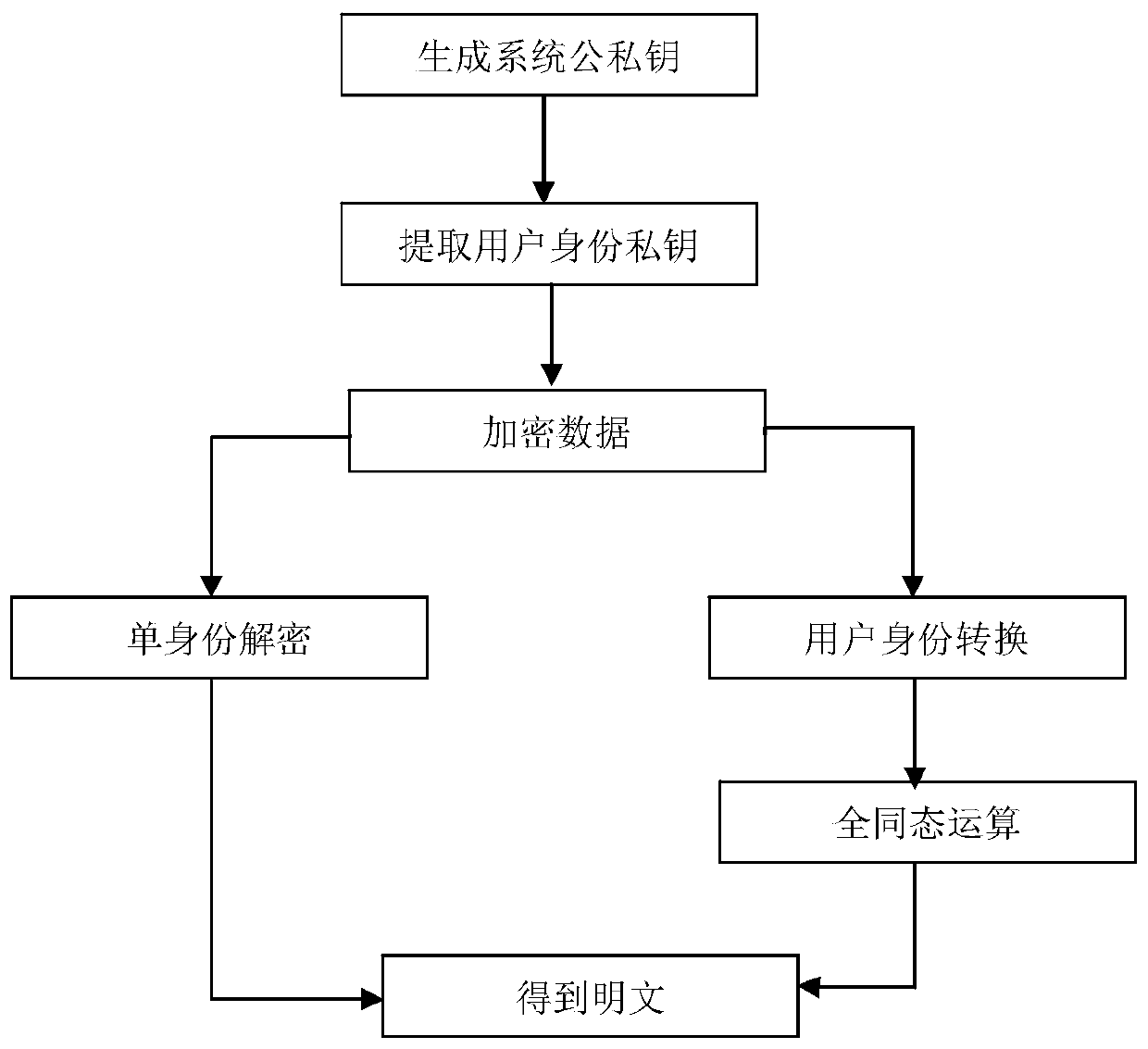
[0068] In the system initialization stage, the server-side public and private keys and the client-side identity key are generated. Client R and client S encrypt and upload their plaintext information to the server through their own systems. Client J needs to obtain the ciphertext from the server and first convert it into its own The ciphertext is then decrypted to obtain the plaintext.
[0069] The identity key of client J as the decryption party is sk Jid , client R’s identity key sk Rid , the identity key of client...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com