User identity mapping method and user identity mapping device based on operator gateway log
A technology of user identification and operator network, applied in the field of network communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
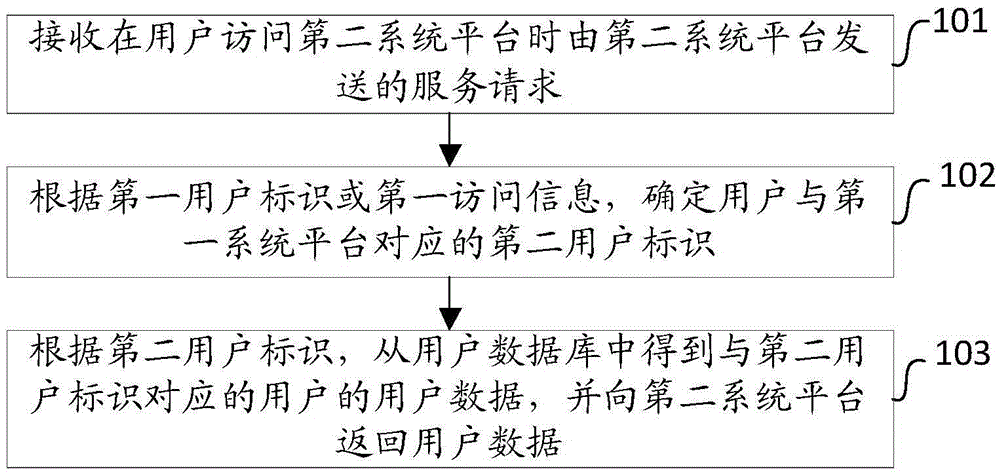
[0030] Such as figure 1 As shown, it is a flow chart of the steps of the method for user identification mapping based on operator gateway logs in the first embodiment of the present invention, including the following steps:
[0031] Step 101, receiving a service request sent by the second system platform when the user accesses the second system platform.
[0032]Specifically, when a user accesses the second system platform, the second system platform sends a service request to the first system platform, wherein the service request includes at least the first user ID corresponding to the user and the second system platform and the user's access to the second system platform. First visit information of the platform. In this step, the first system platform receives the service request sent by the second system platform. Optionally, the first system platform may be an operator system platform, and the second system platform is an external system platform interfaced with the oper...
no. 2 example
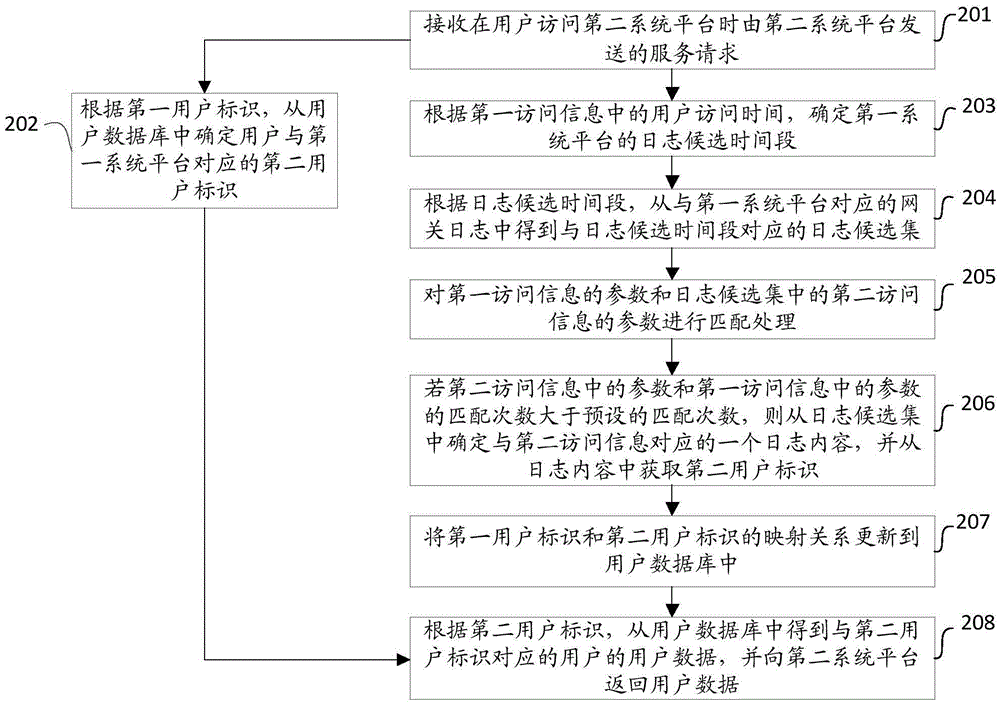
[0039] Such as figure 2 As shown, it is a flow chart of the steps of the method for user identification mapping based on operator gateway logs in the second embodiment of the present invention, including the following steps:
[0040] Step 201: Receive a service request sent by the second system platform when the user accesses the second system platform, and then enter step 202 or step 203.
[0041] In this step, the first system platform enters step 202 or step 203 after receiving the service request sent by the second system platform. Wherein, the service request includes at least the first user identification corresponding to the user and the second system platform and the first access information for the user to access the second system platform. Specifically, the first access information includes: one or more of the user's access time, the Uniform Resource Locator URL or IP address of the user's access, the user's IP address or location information, the browser used by t...
no. 3 example
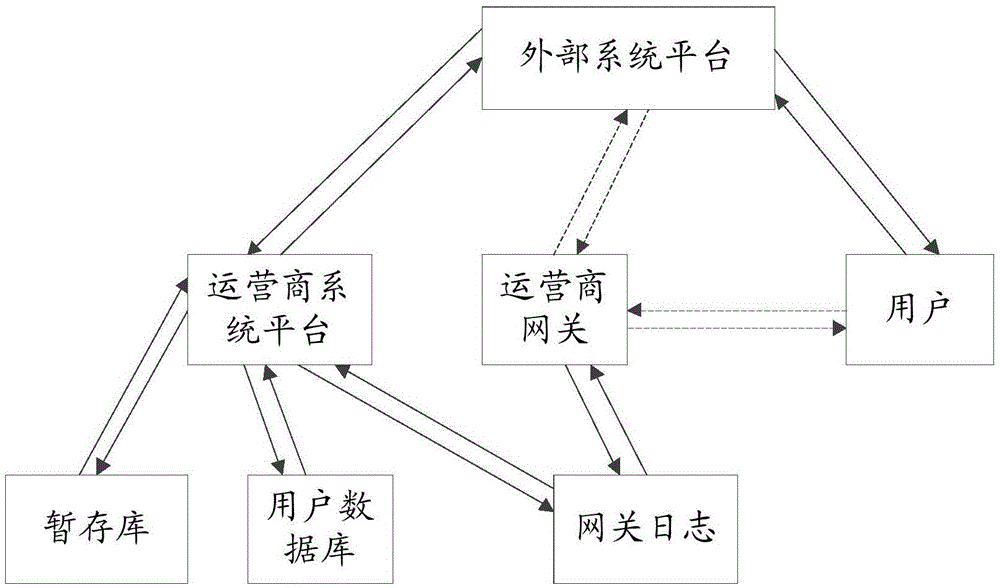
[0063] Such as Figure 4 As shown, it is a structural block diagram of the device for user identification mapping based on operator gateway logs in the third embodiment of the present invention, and the device includes:
[0064] The receiving module 301 is configured to receive a service request sent by the second system platform when the user accesses the second system platform, and the service request at least includes: the first user identification corresponding to the user and the second system platform and the user's access to the second system platform first visit information;
[0065] Obtaining module 302, the user determines the second user identifier corresponding to the user and the first system platform according to the first user identifier or the first access information;
[0066] In the processing module 303, the user obtains the user data corresponding to the second user ID from the user database according to the second user ID, and returns the user data to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com